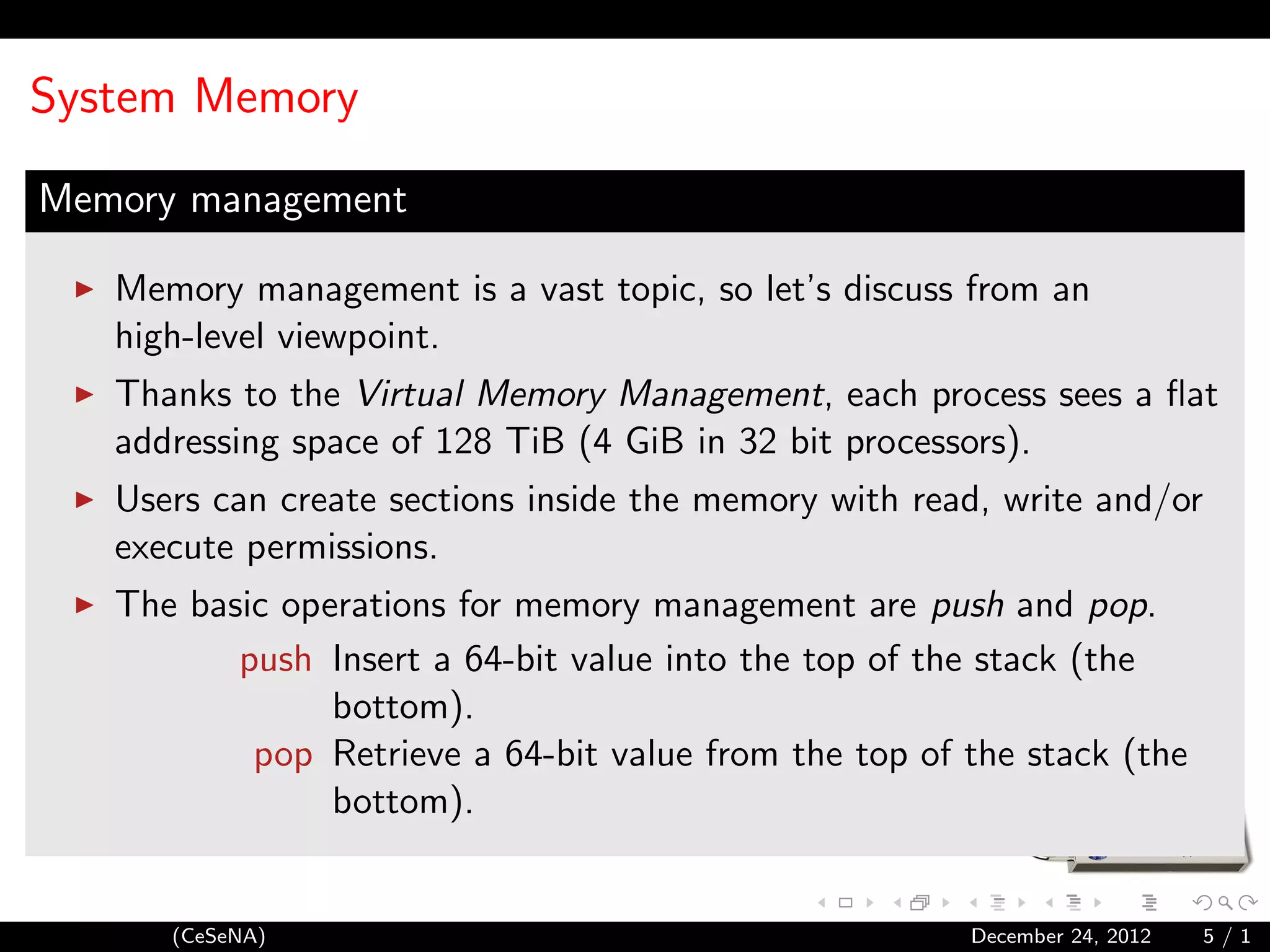
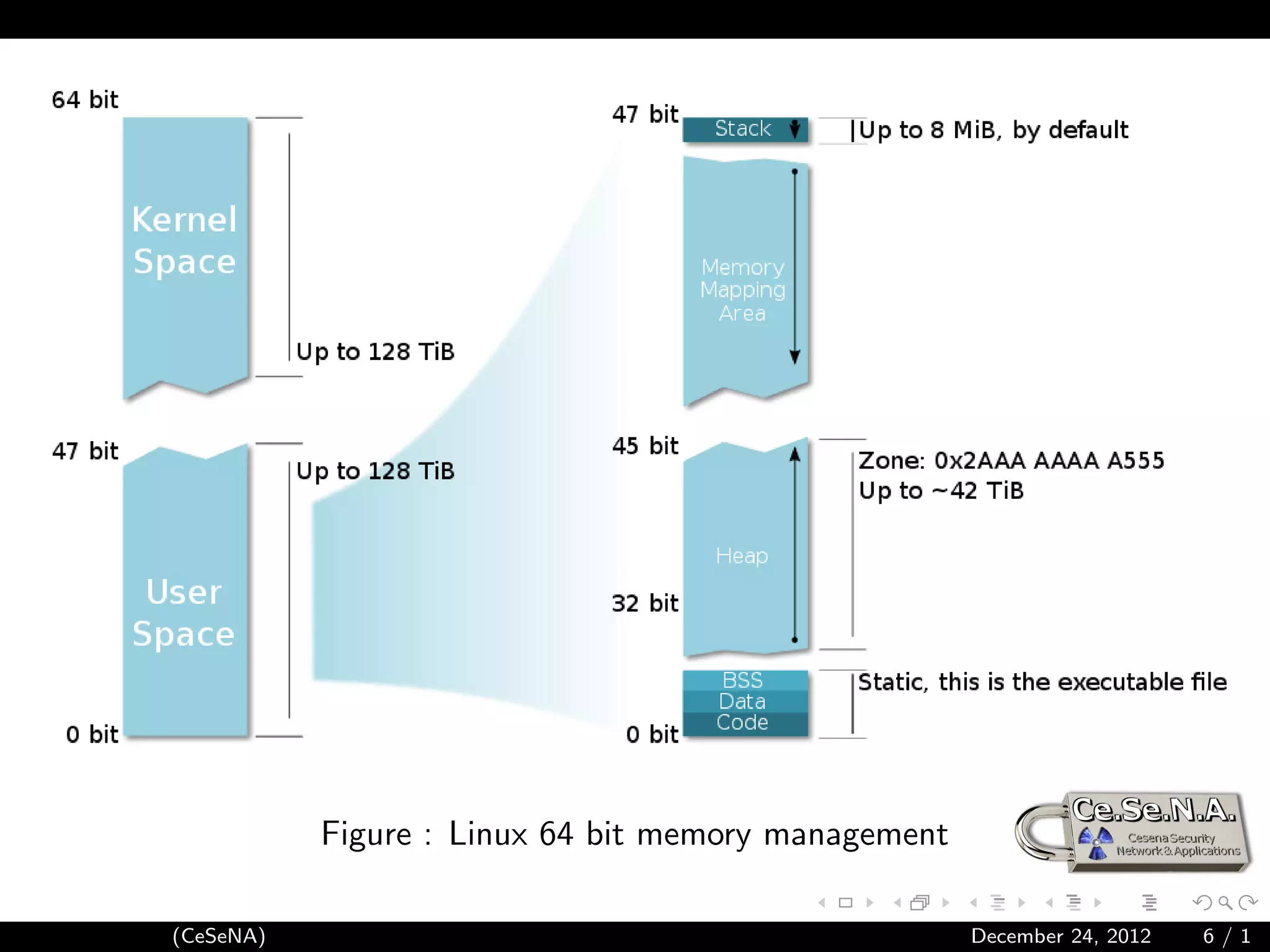
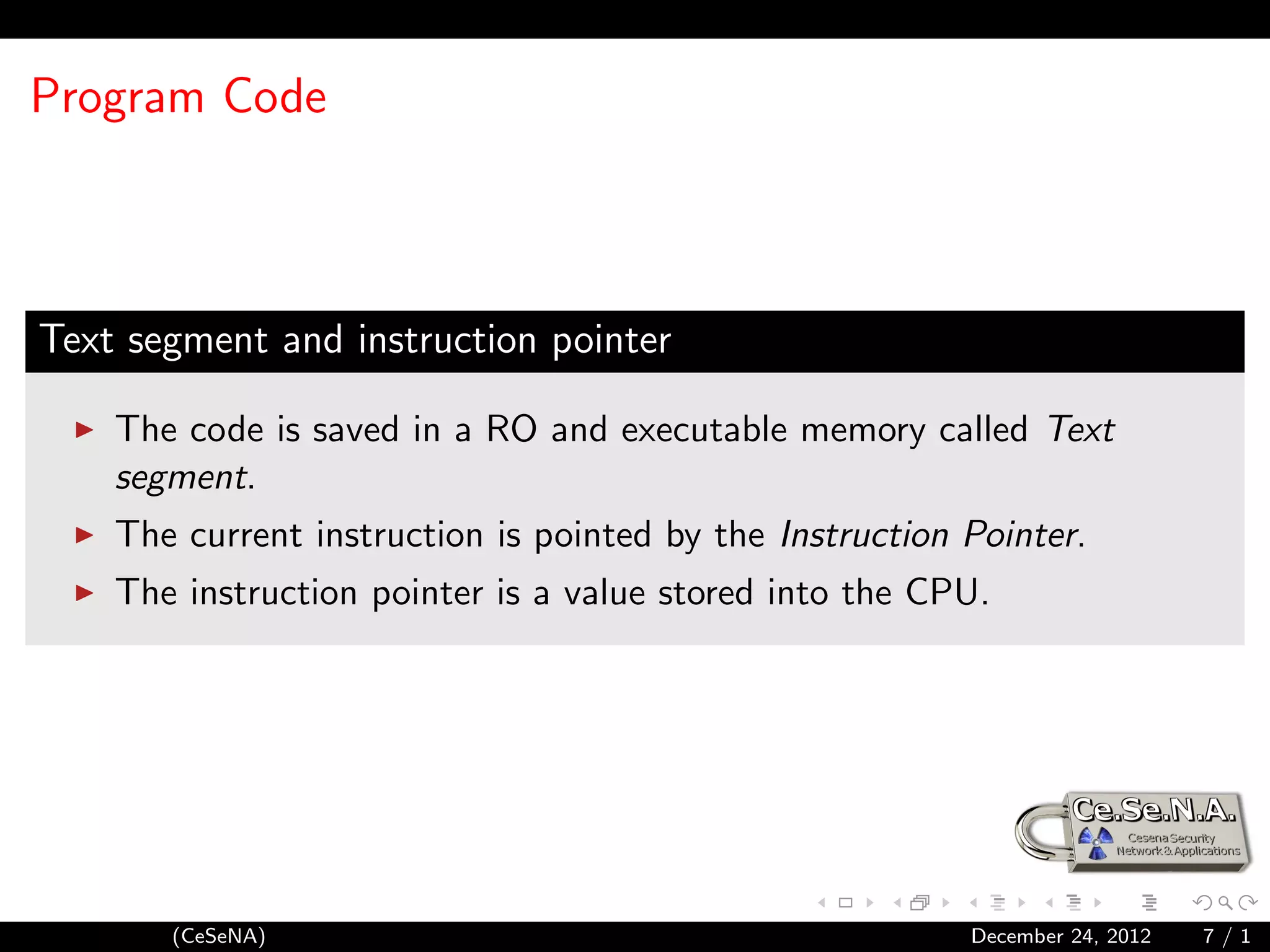
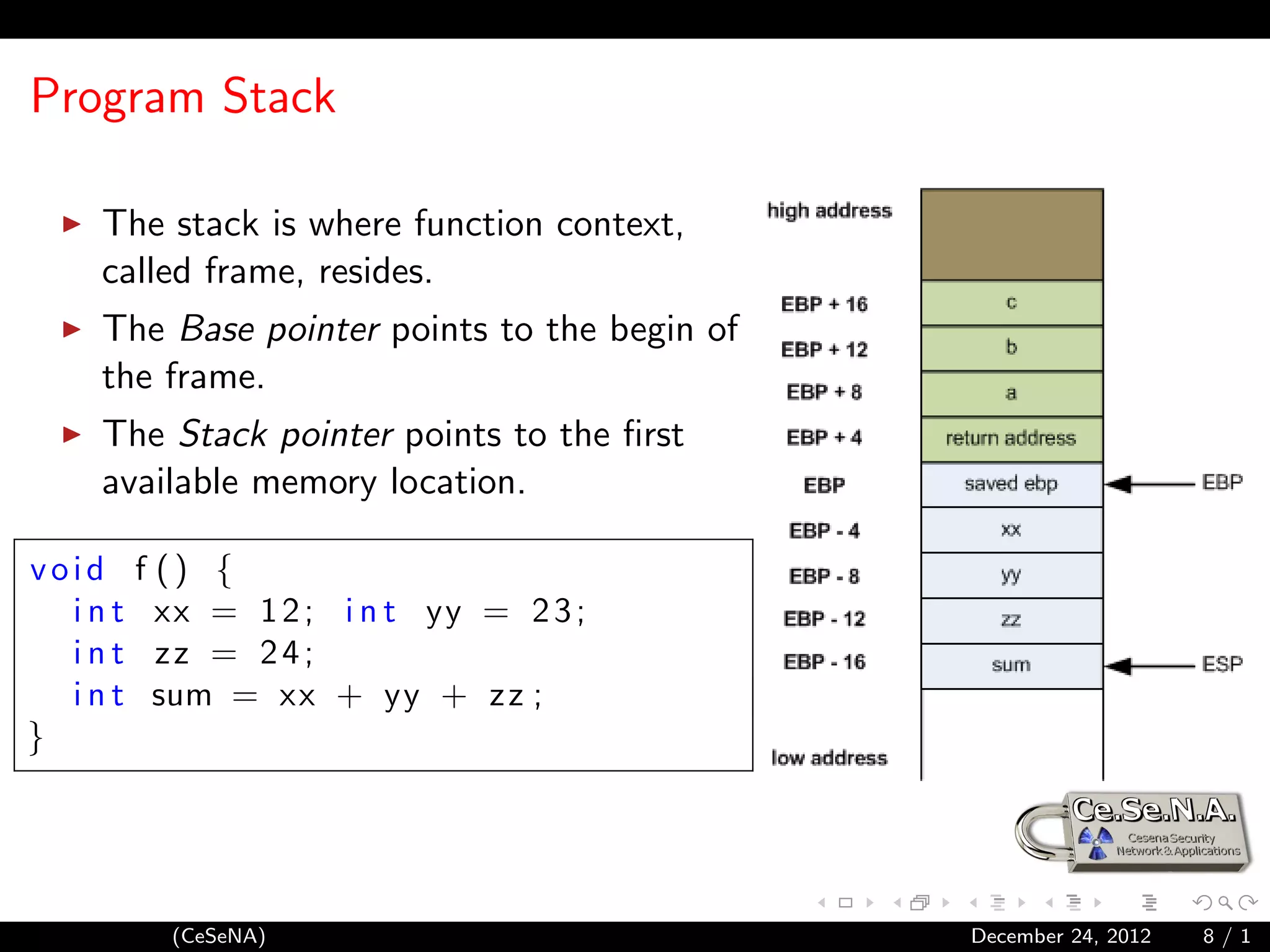
This document provides an introduction to shellcoding, which involves exploiting software vulnerabilities to insert and execute a custom payload. It discusses prerequisites like assembly language and memory structure. Key topics covered include the program stack, calling conventions, system calls, and writing shellcodes to reference data, print to stdout, and execute a program. The document concludes by outlining the steps to create a reverse shell shellcode that connects back to an attacker's server.






![Writing shellcodes
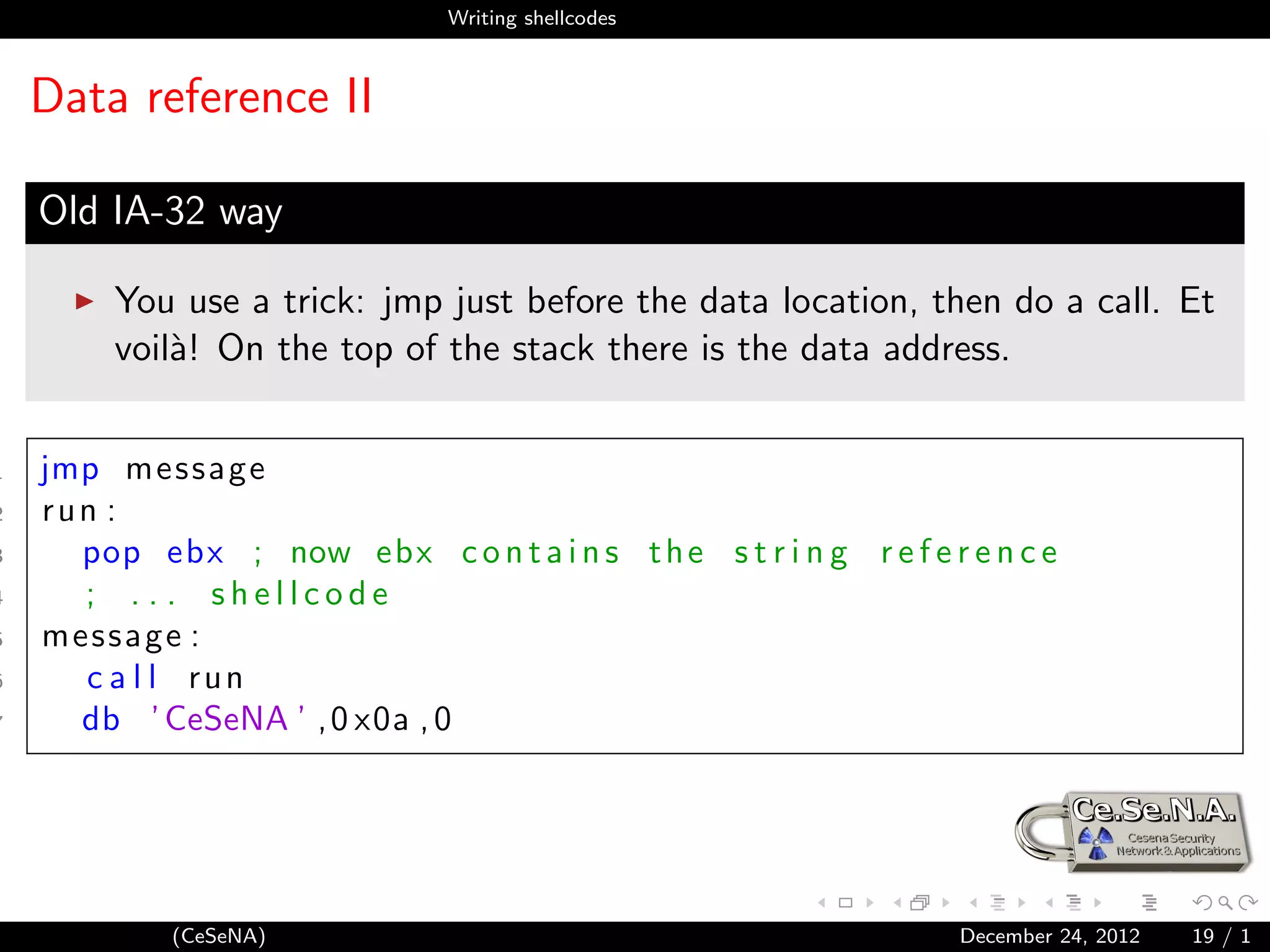
Data reference III
New IA-64 way
IA-64 introduces the RIP relative addressing.
1 l e a r d i , [ r e l message ] ; now ebx c o n t a i n s
2 ; the s t r i n g r e f e r e n c e
3 ; . . . shellcode
4
5 message db ’ CeSeNA ’ , 0 x0a , 0
(CeSeNA) December 24, 2012 20 / 1](https://image.slidesharecdn.com/main-130110033847-phpapp02/75/Shellcoding-an-Introduction-20-2048.jpg)
![Writing shellcodes
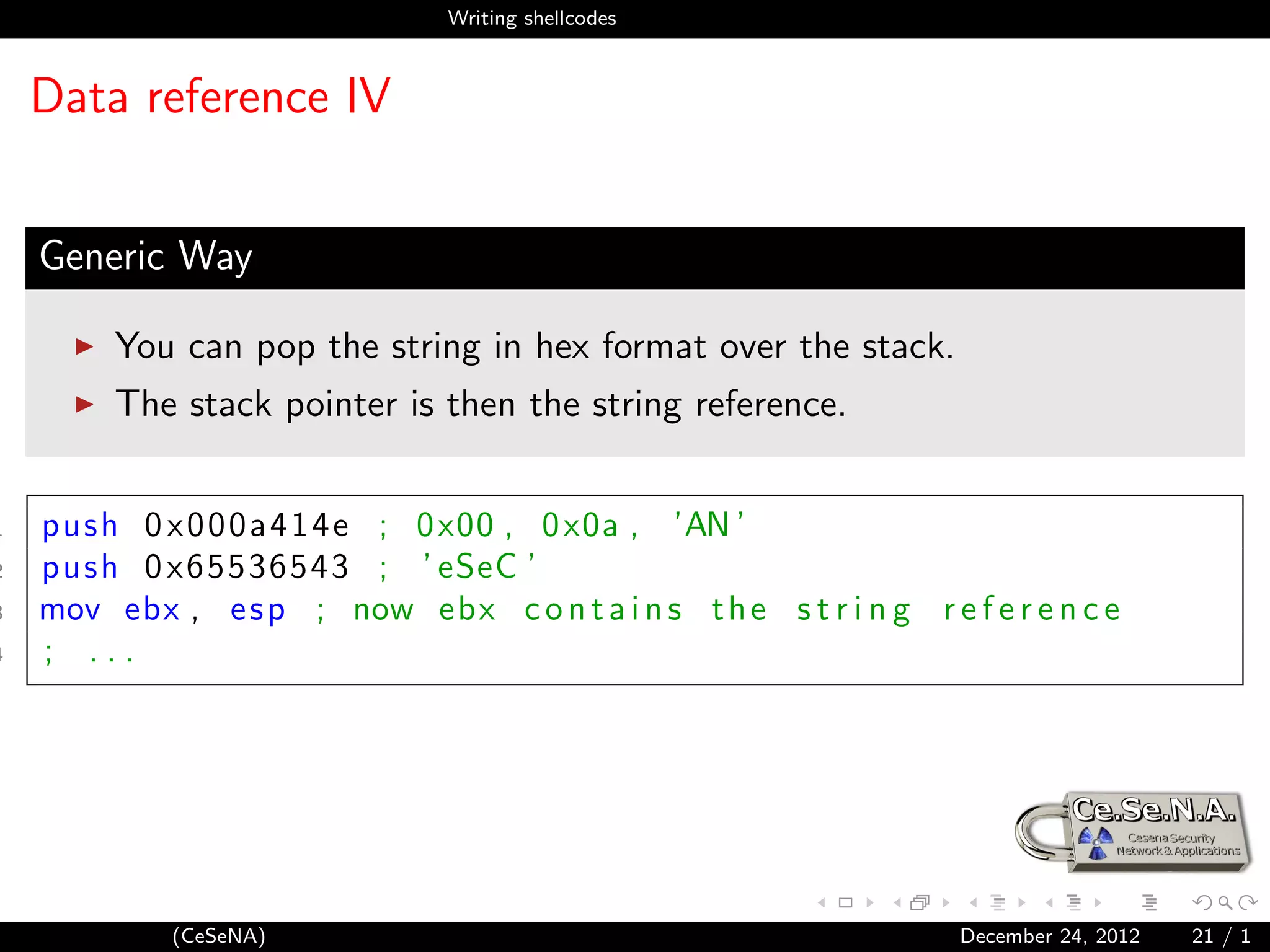
Execute a program
1 unistd 64 . h
2 #d e f i n e N R e x e c v e 59
3 syscall .h
4 i n t k e r n e l e x e c v e ( const char ∗ filename ,
5 const char ∗ const argv [ ] ,
6 c o n s t c h a r ∗ c o n s t envp [ ] ) ;
Exercise 3: A real shellcode, exec a shell!
4 HaXoRs
4 g33k
4 n00bz
(CeSeNA) December 24, 2012 23 / 1](https://image.slidesharecdn.com/main-130110033847-phpapp02/75/Shellcoding-an-Introduction-23-2048.jpg)
![Writing shellcodes
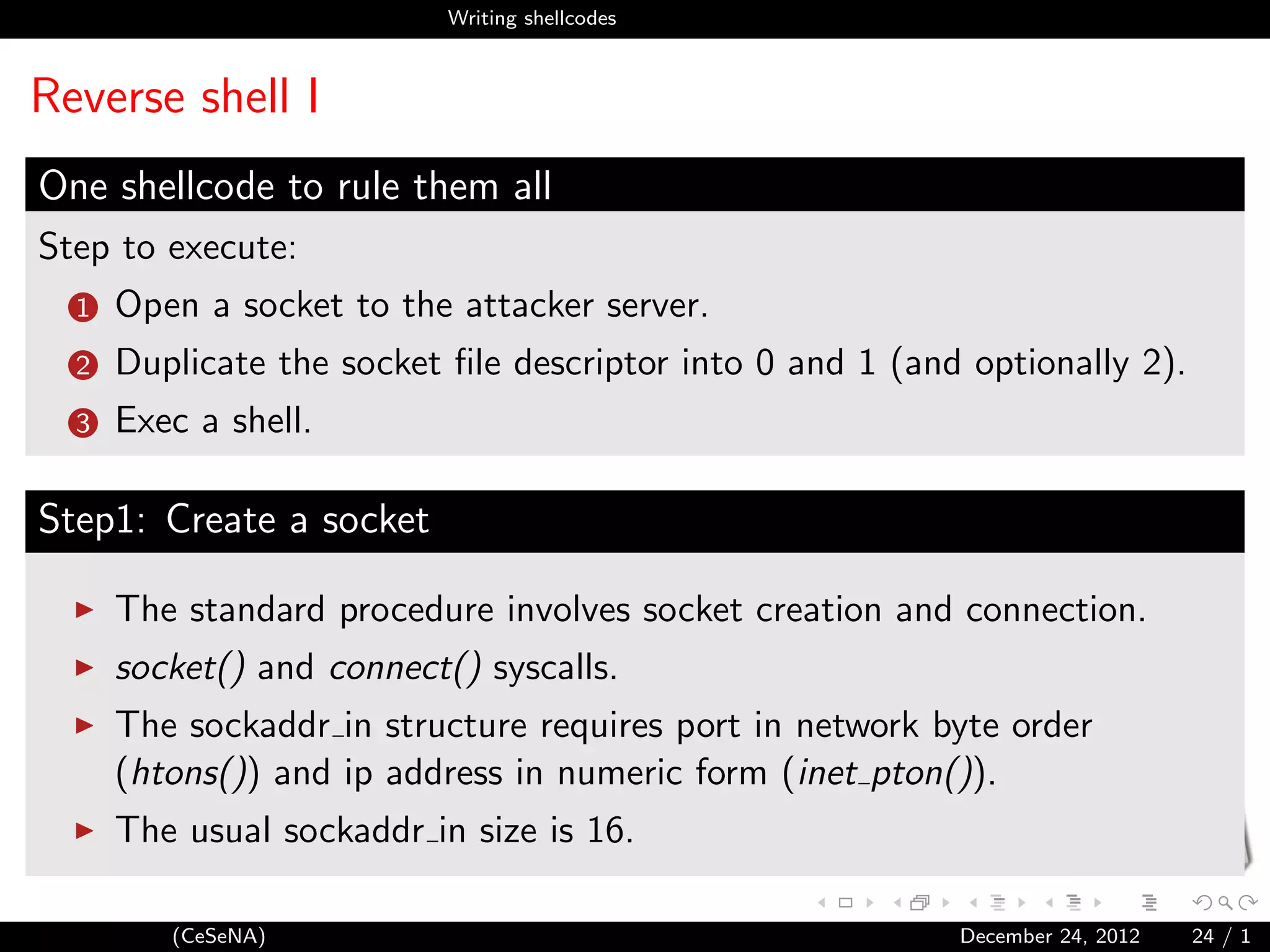
Reverse shell II
1 l o n g s y s s o c k e t ( i n t domain ,
2 i n t type ,
3 int protocol ) ;
4 l o n g s y s c o n n e c t ( i n t fd ,
5 s t r u c t sockaddr user ∗,
6 int addrlen ) ;
1 struct sockaddr in {
2 short s i n f a m i l y ; // AF INET
3 unsigned short s i n p o r t ; // n e t w o r k o r d e r ( h t o n s ( ) )
4 struct in addr s i n a d d r ; // As 32 b i t
5 char sin zero [8];
6 };
(CeSeNA) December 24, 2012 25 / 1](https://image.slidesharecdn.com/main-130110033847-phpapp02/75/Shellcoding-an-Introduction-25-2048.jpg)
![Writing shellcodes
String payload
zero-bytes problem
If the payload is red as a string, C interprets a zero byte as string
terminator, cutting the shellcode.
Zero-bytes presence is caused by data and addresses:
mov rax, 11h is equivalent to mov rax, 0000000000000011h.
lea rax, [rel message] is equivalent to lea rax, [rip + 0000. . . xxh].
execve for instance, requires a null terminated string and some null
parameters.
Solutions are quite straightforward:
Use xor operation to zero a register.
Use when possible smaller part of registers (e.g.: rax → eax → ax →
[ah,al])
Use add operation: immediate operators are not expanded.
Place not-null marker in strings and substitute them inside the code.
When using relative addressing, place the message above: offset will be
negative [?].
(CeSeNA) December 24, 2012 29 / 1](https://image.slidesharecdn.com/main-130110033847-phpapp02/75/Shellcoding-an-Introduction-29-2048.jpg)
![Writing shellcodes
Zero-byte removal example
; S e t r a x = 60 h ; S e t t o 0 a mem a r e a
xor rax , rax n u l l db ’ x x x x ’
mov a l , 60 x o r rbx , r b x
mov [ r e l n u l l ] , ebx
; S e t r d i = 12 h
xor rdi , r d i ; terminate s t r i n g with 0
add r d i , 12 h message db ’ CeSeNA ’ , ’ x ’
x o r rbx , r b x
l e a r d i , [ r e l message ]
mov [ r d i +7] , b l
; Negative refe rence
message db ’ CeSeNA ’ , ’ x ’
l e a r d i , [ r e l message ]
(CeSeNA) December 24, 2012 30 / 1](https://image.slidesharecdn.com/main-130110033847-phpapp02/75/Shellcoding-an-Introduction-30-2048.jpg)
