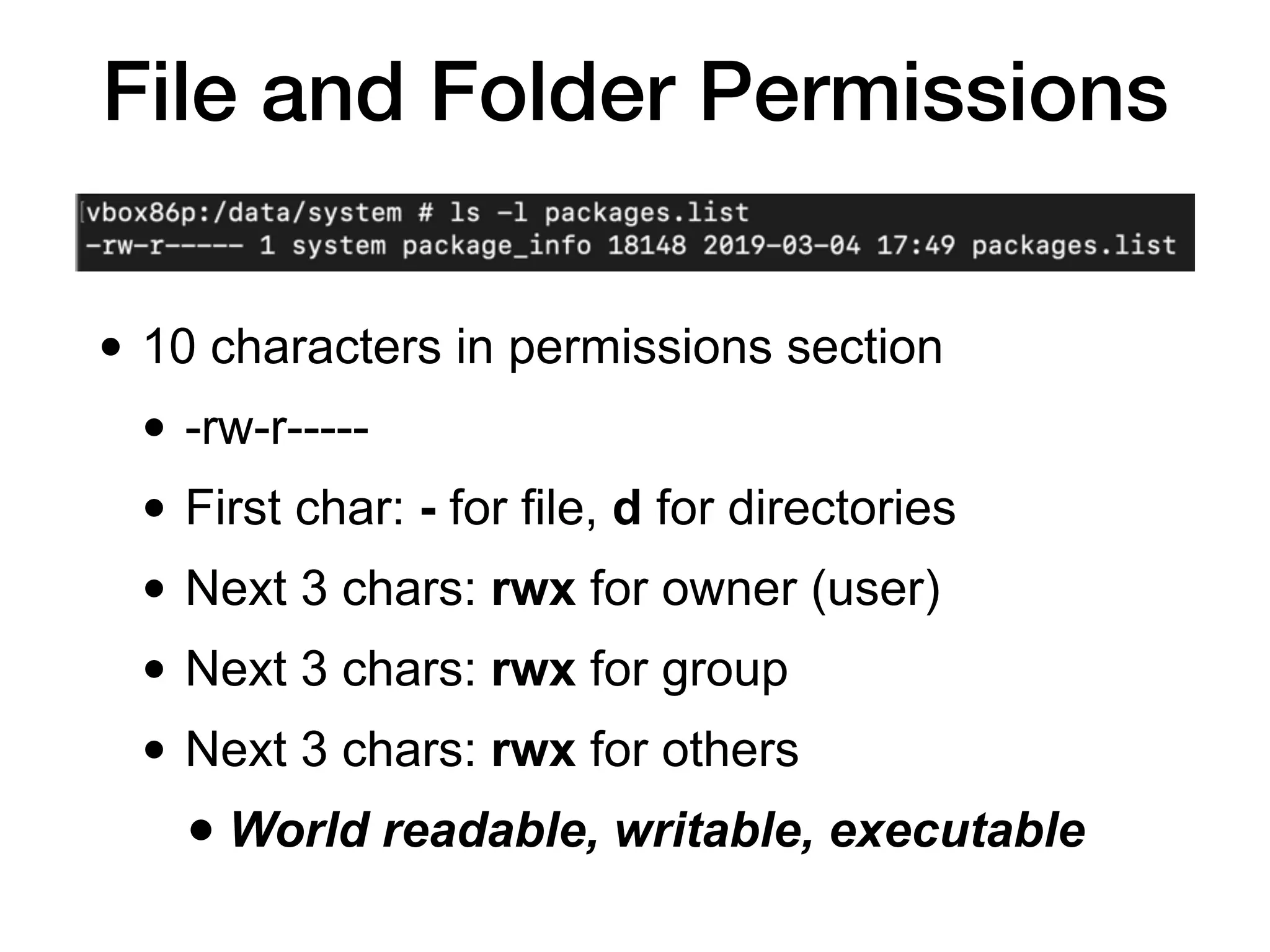
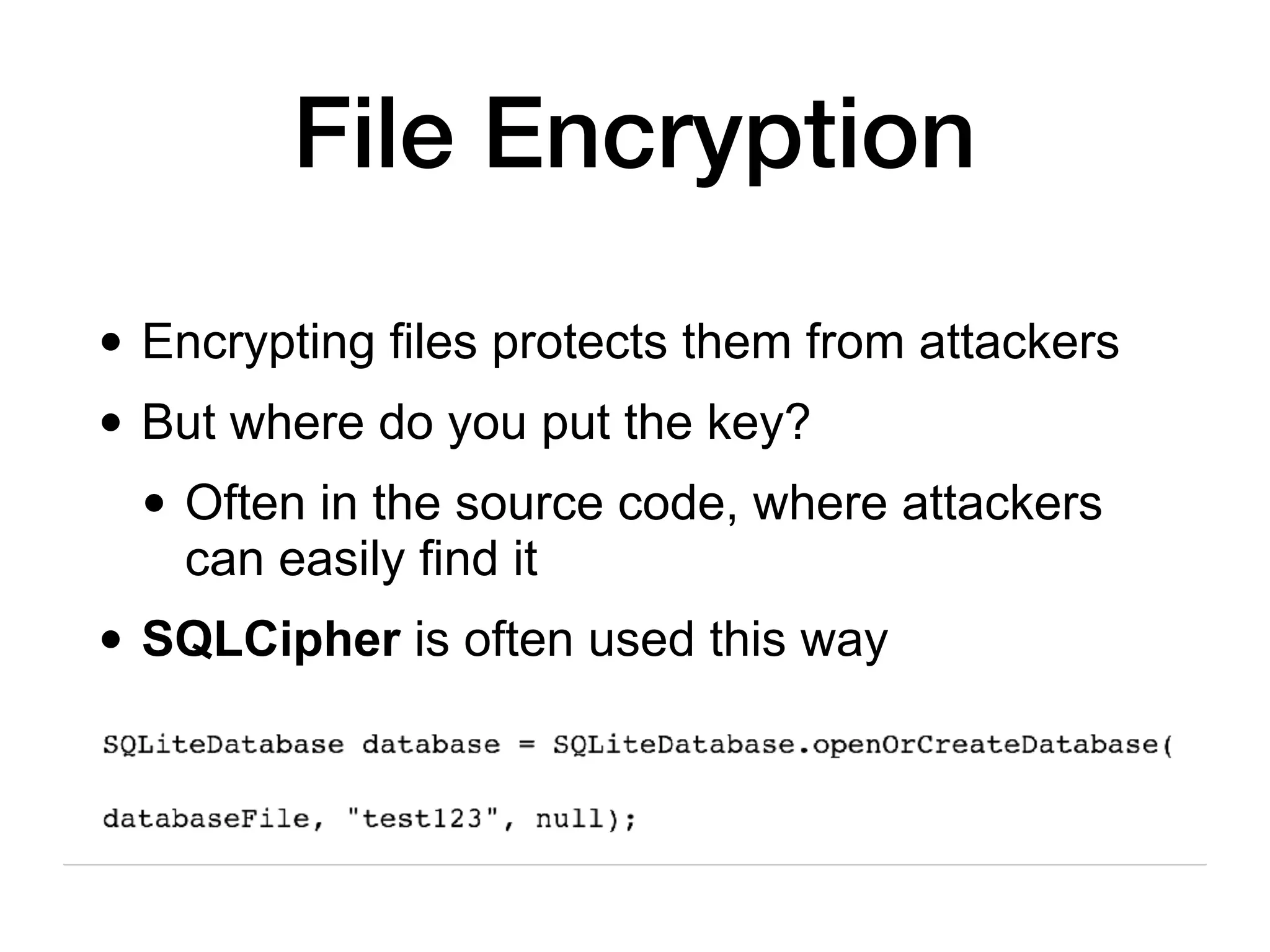
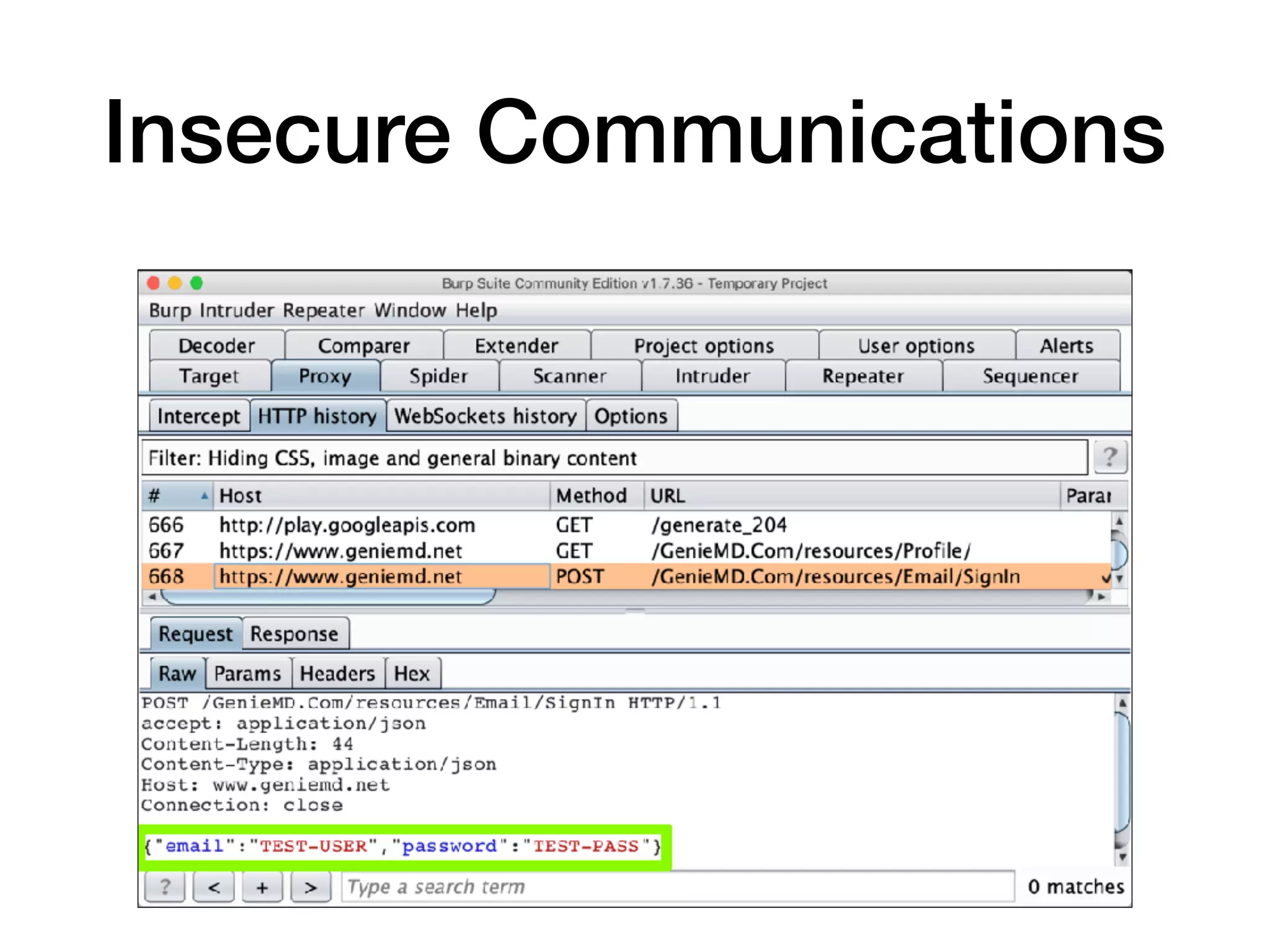
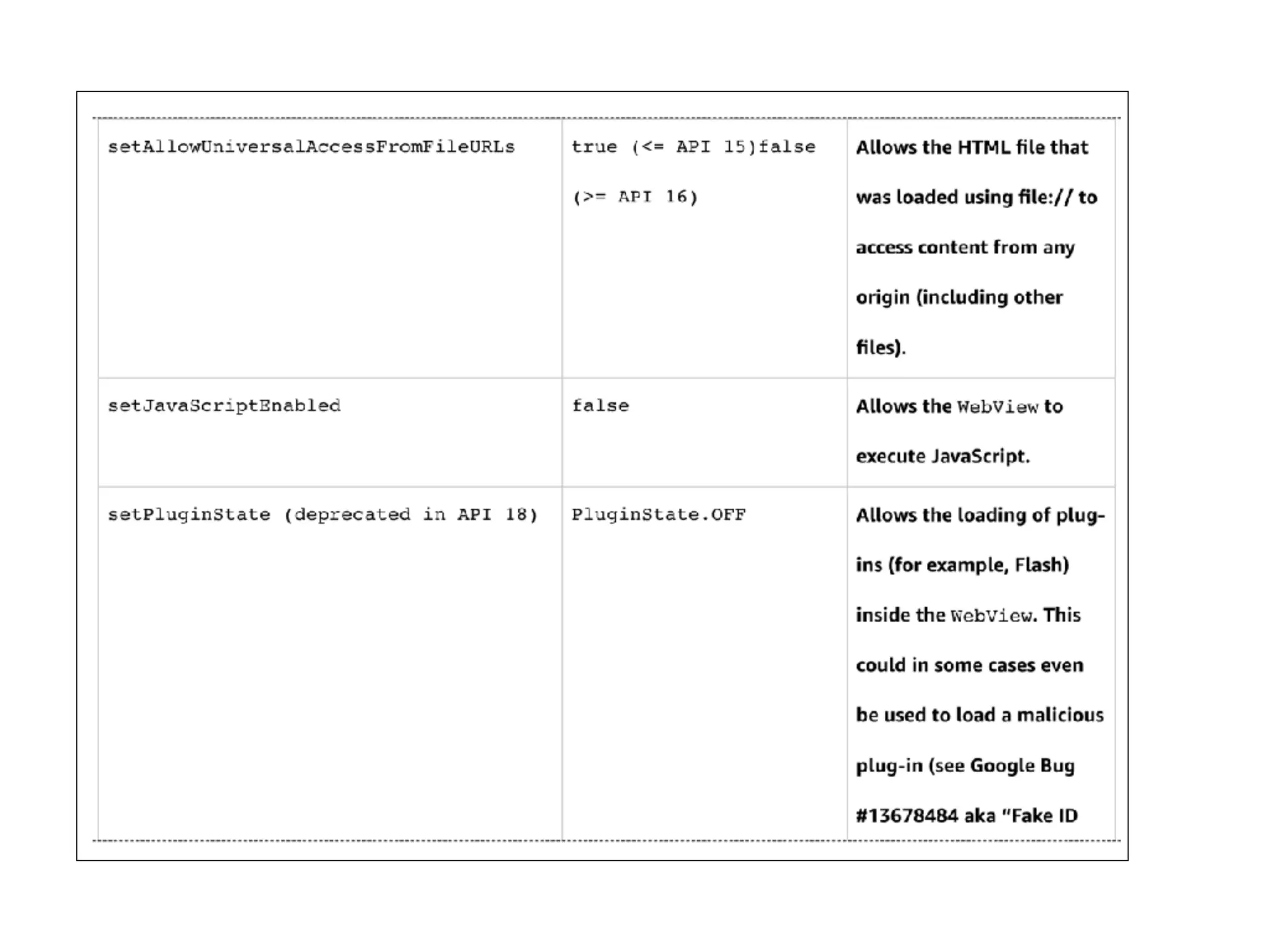
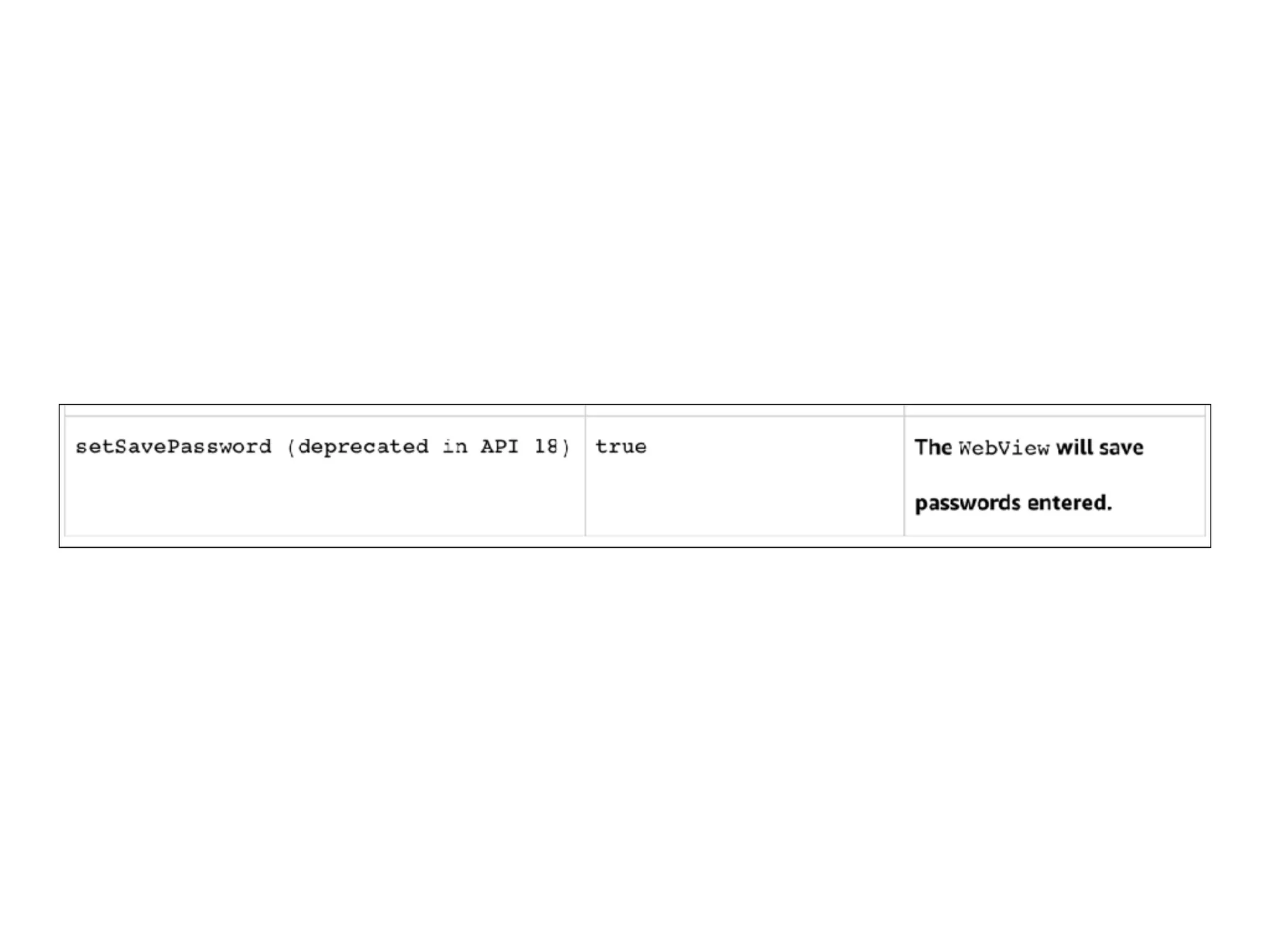
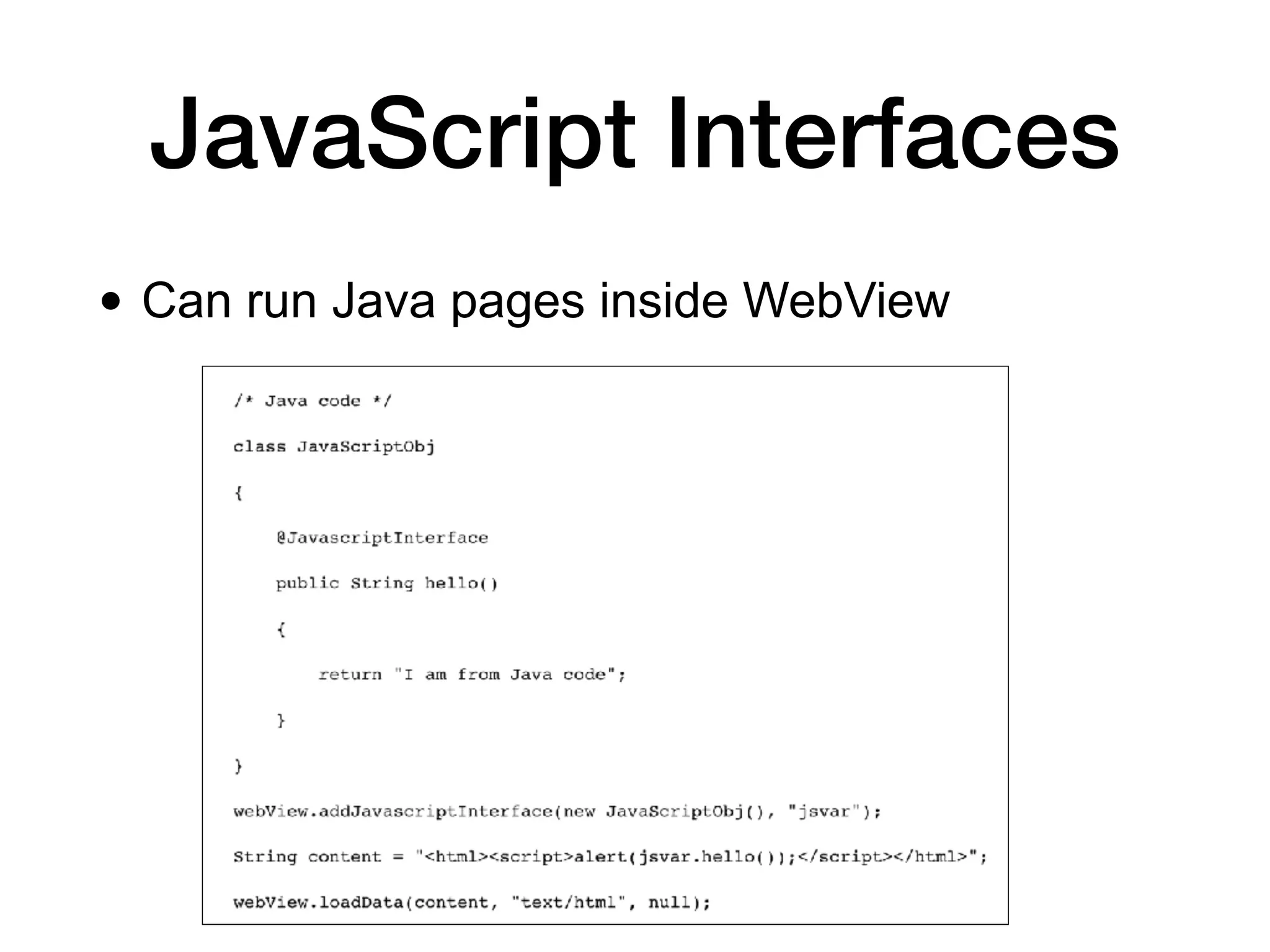
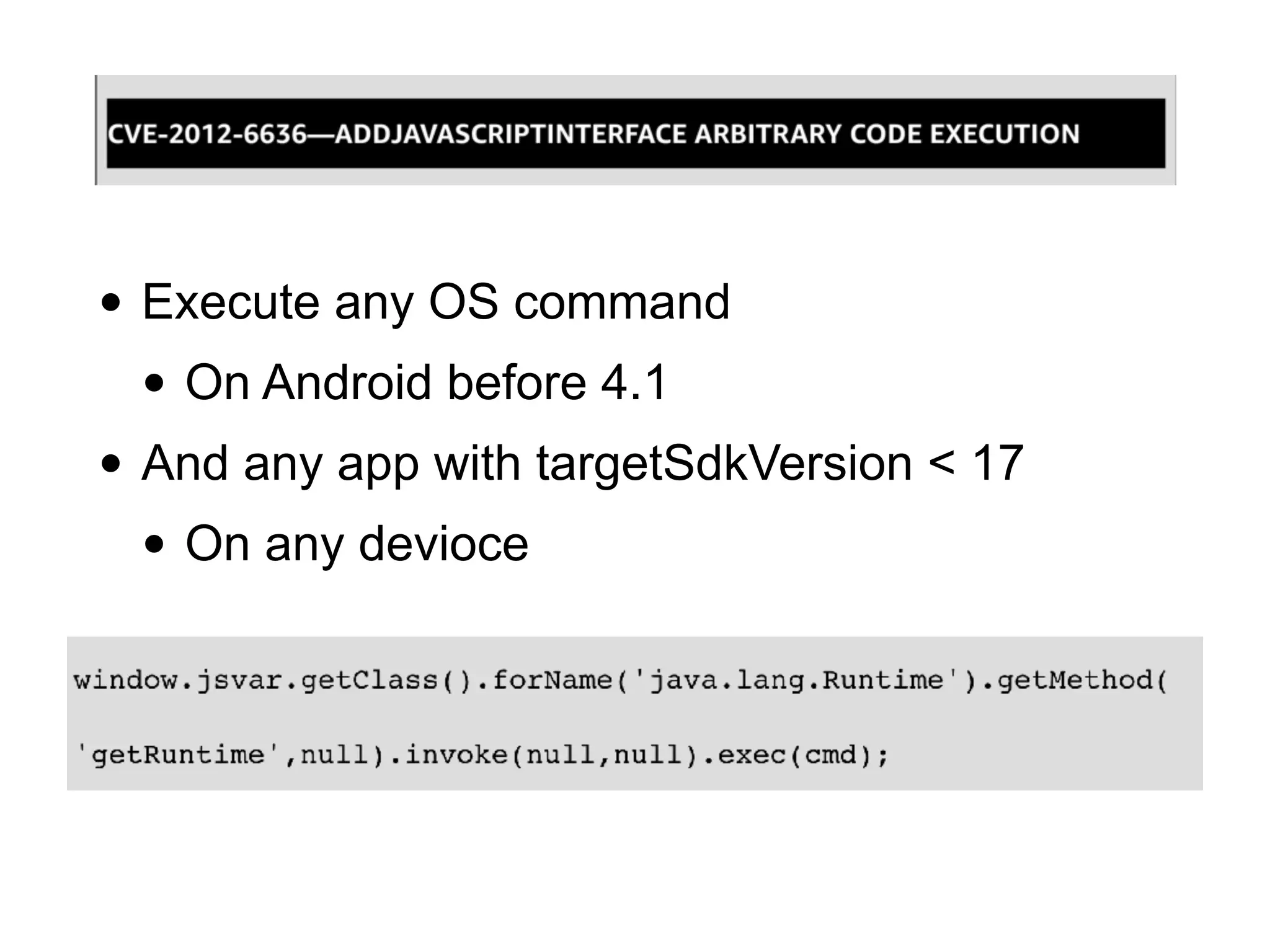
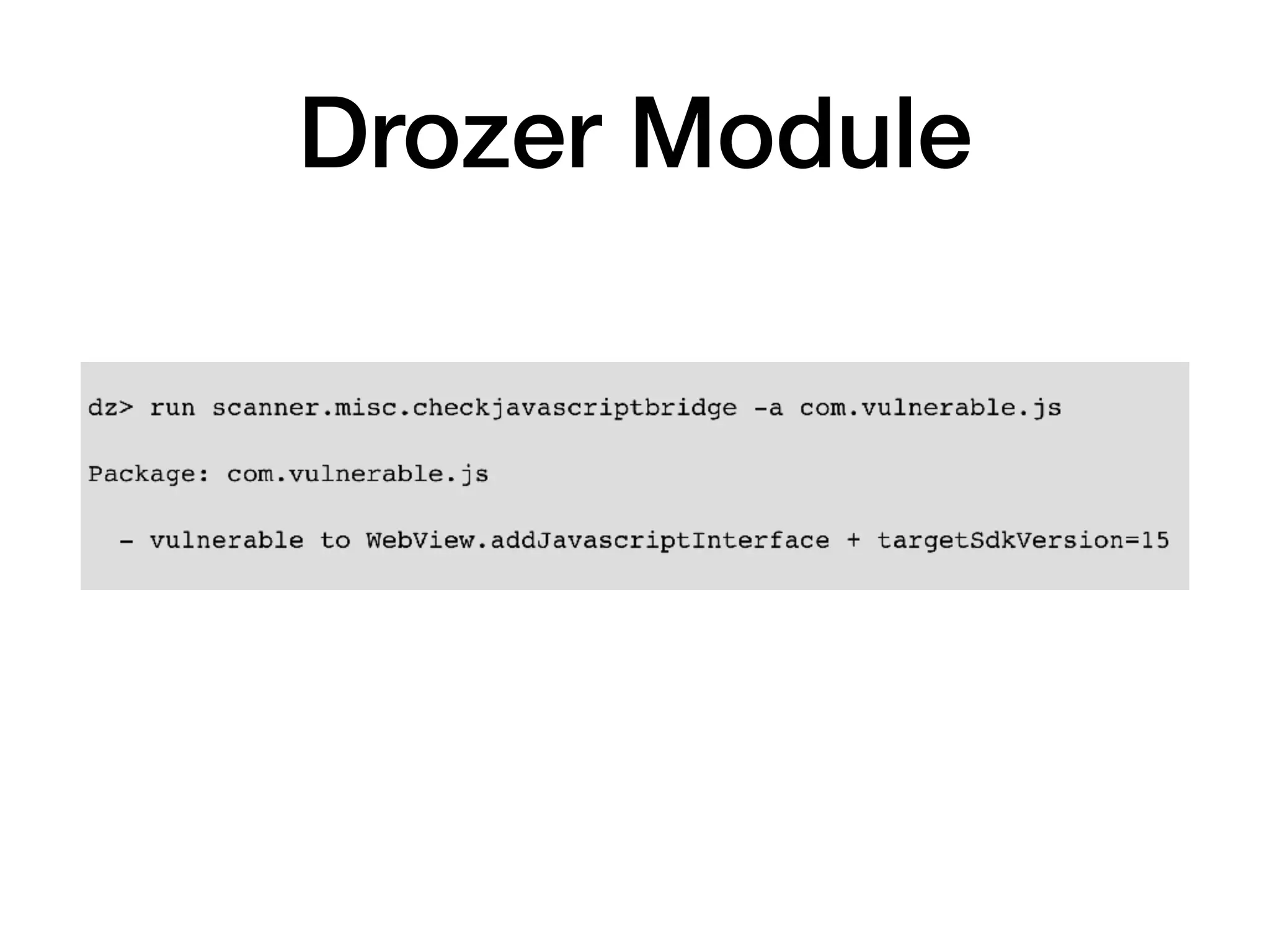
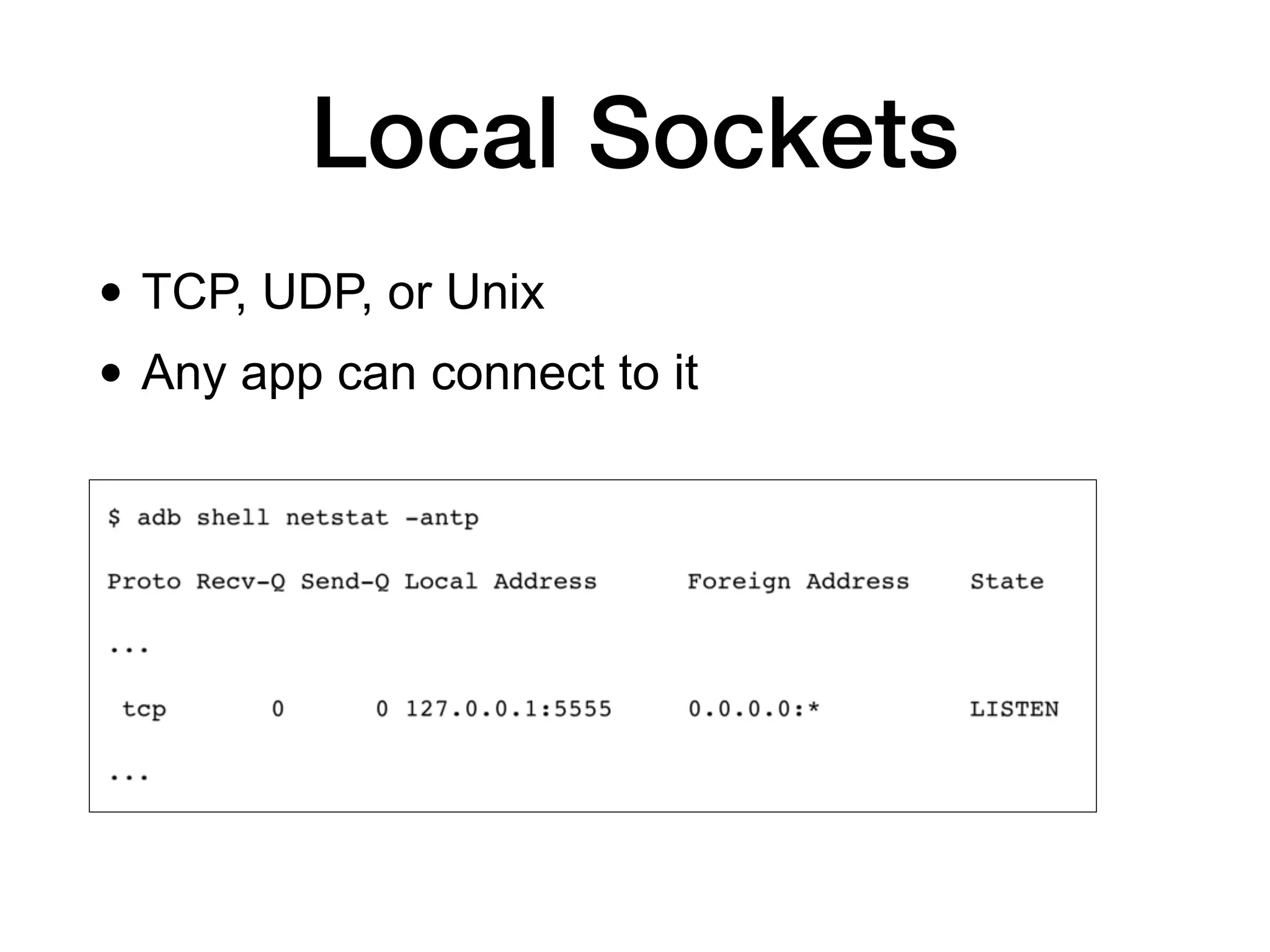
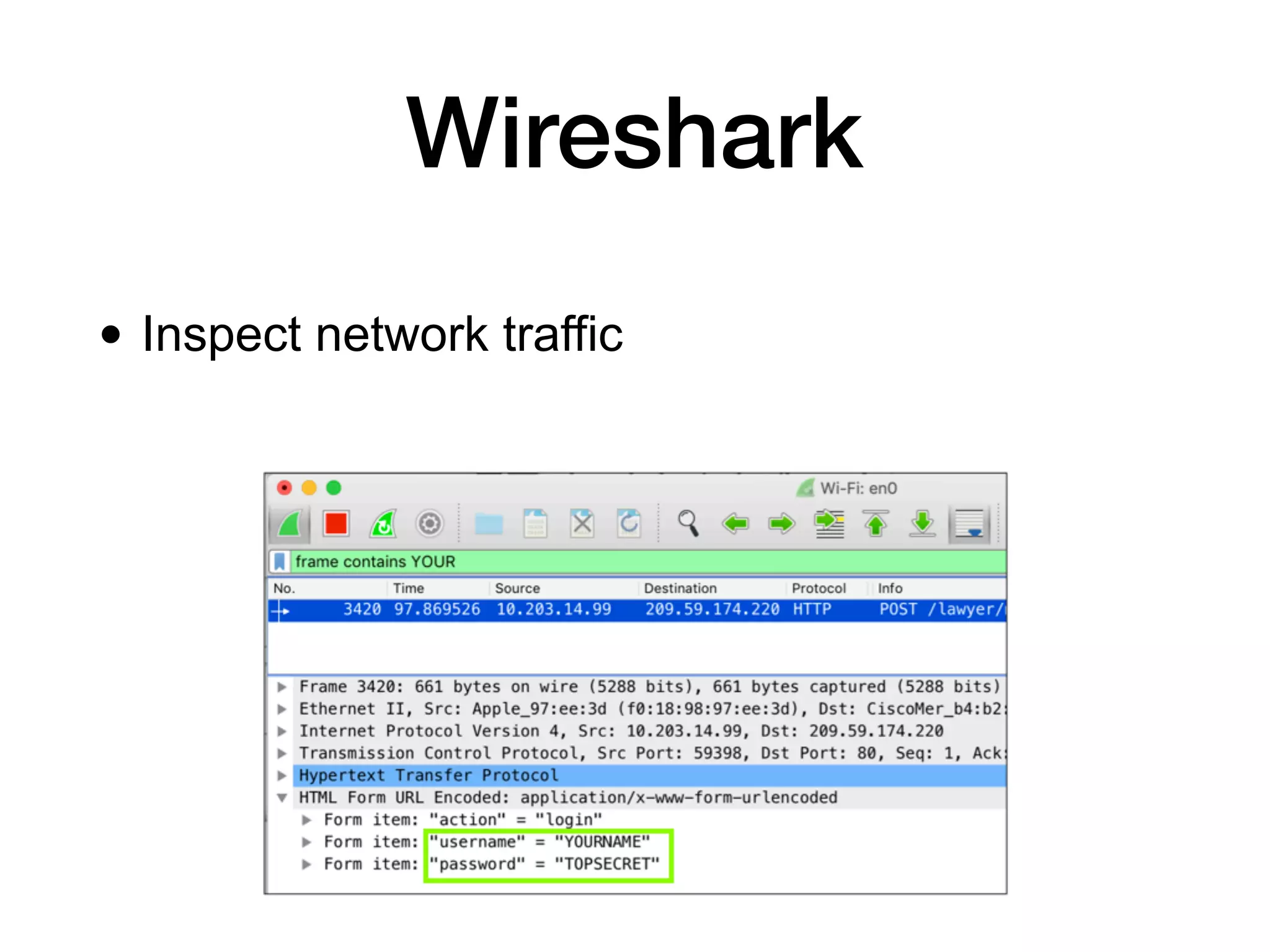
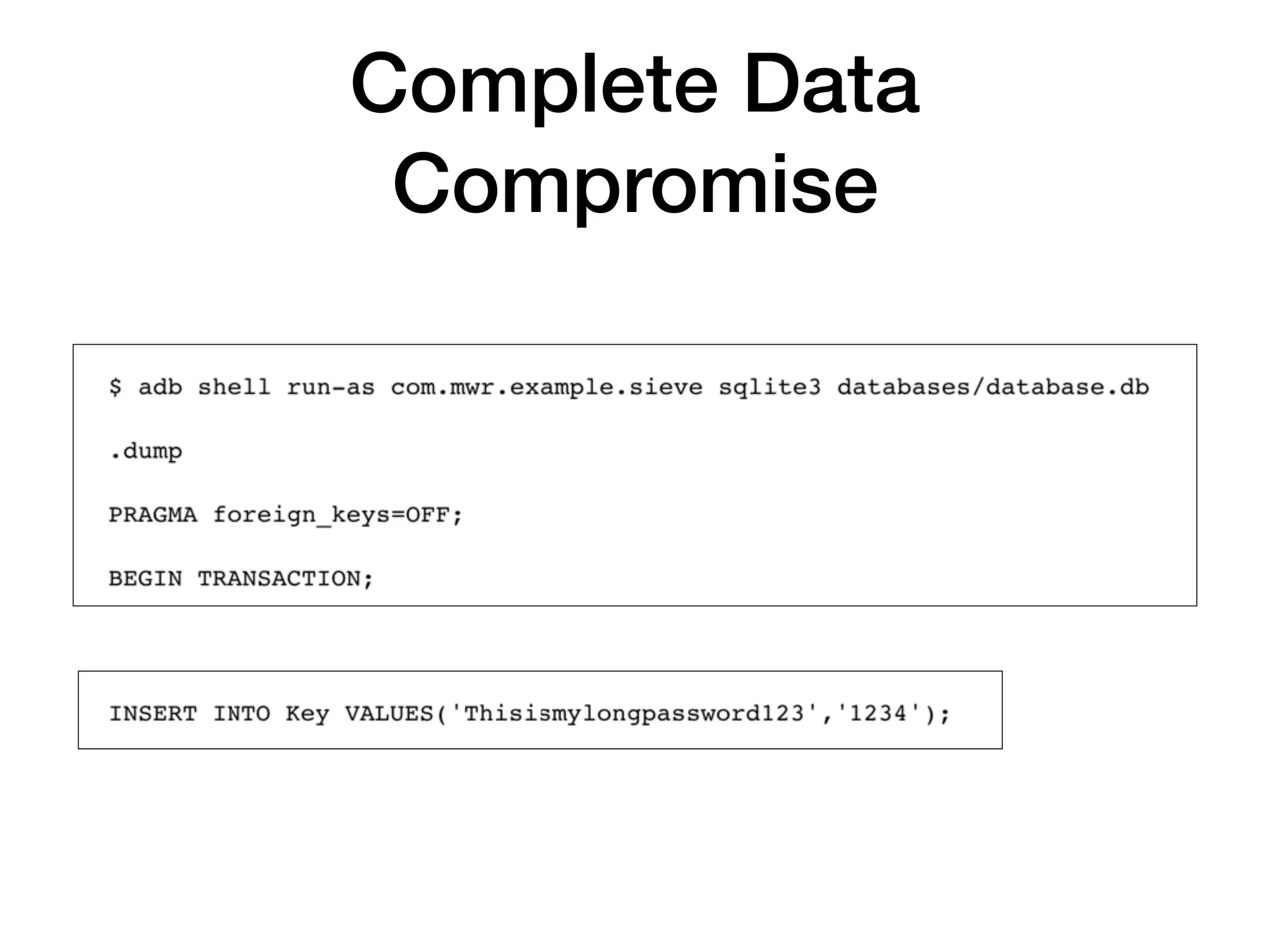
This document discusses various techniques for attacking Android applications, focusing on exploiting storage access, insecure communications, and application vulnerabilities. Key topics include permission management, file encryption, SQL database vulnerabilities, and misconfigured app attributes. It also highlights testing techniques and tools for analyzing and enhancing app security.