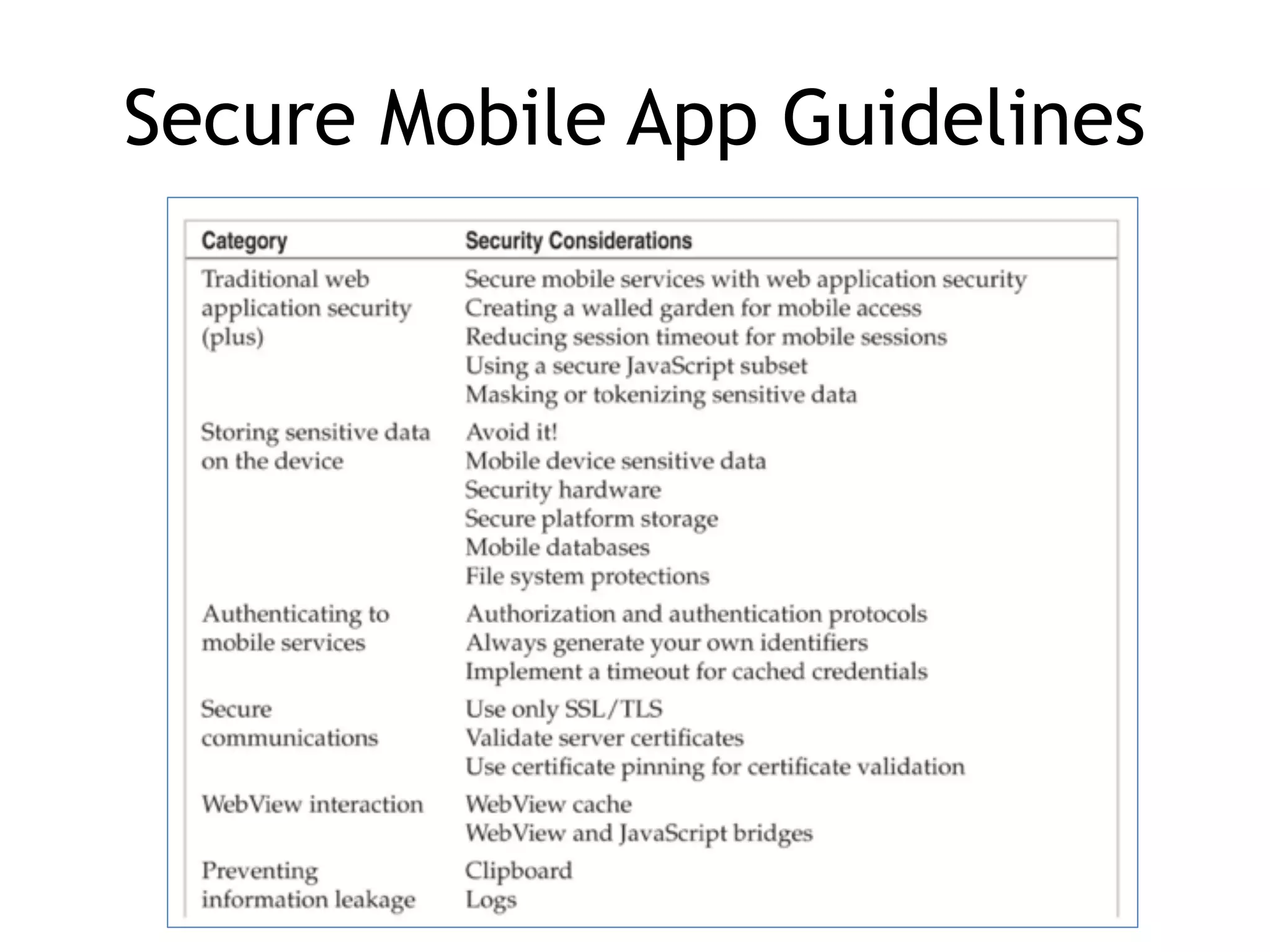
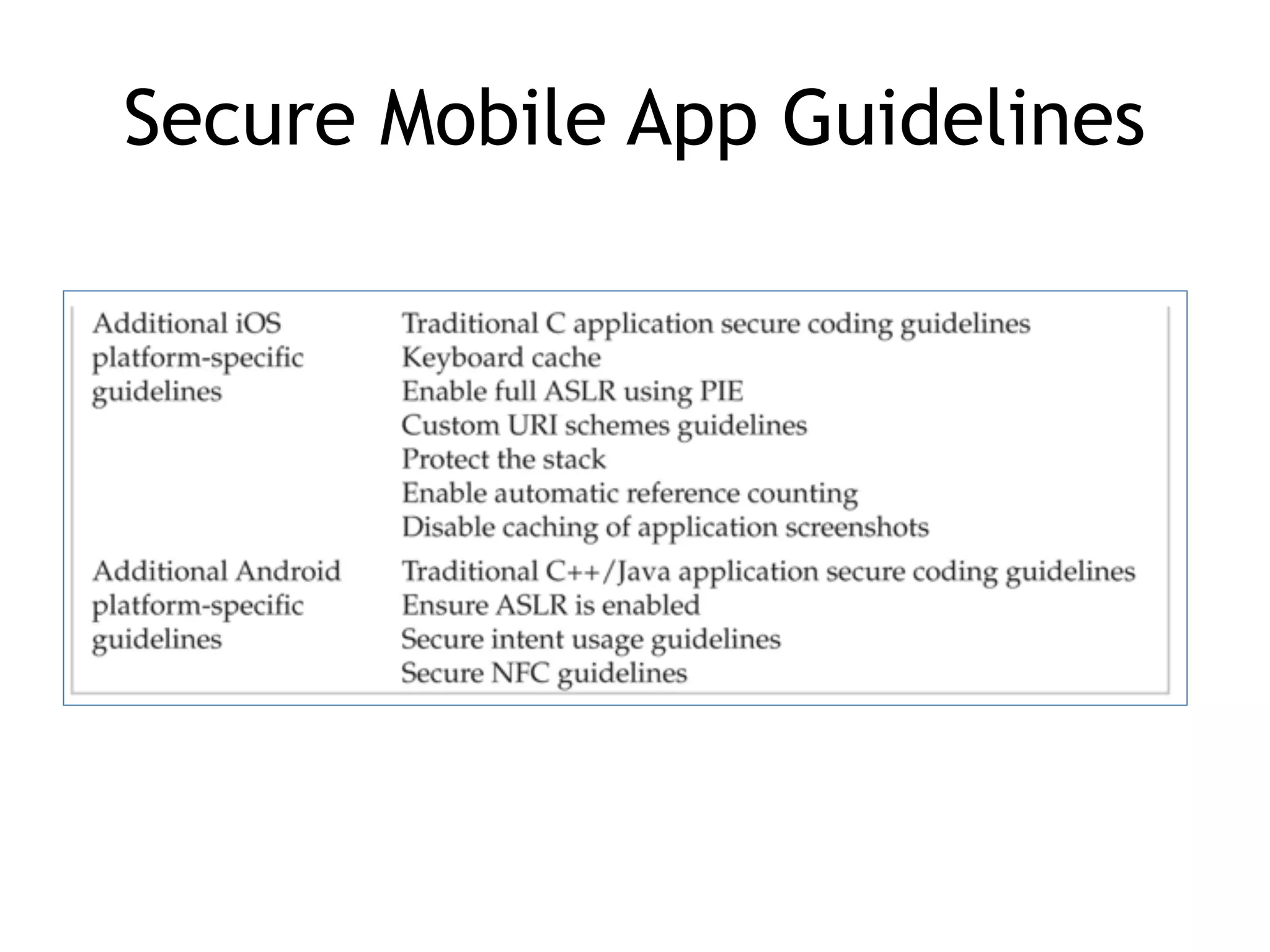
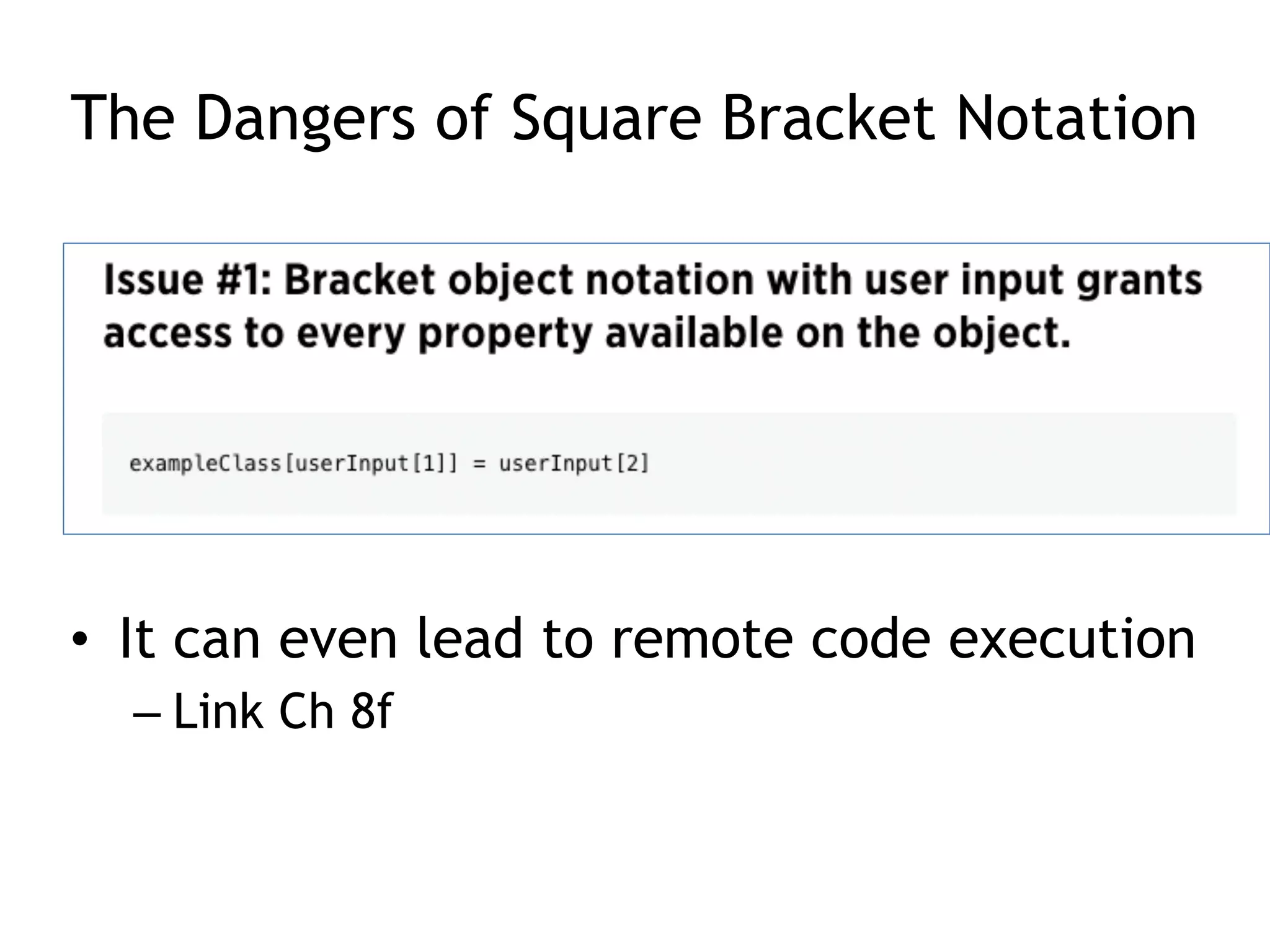
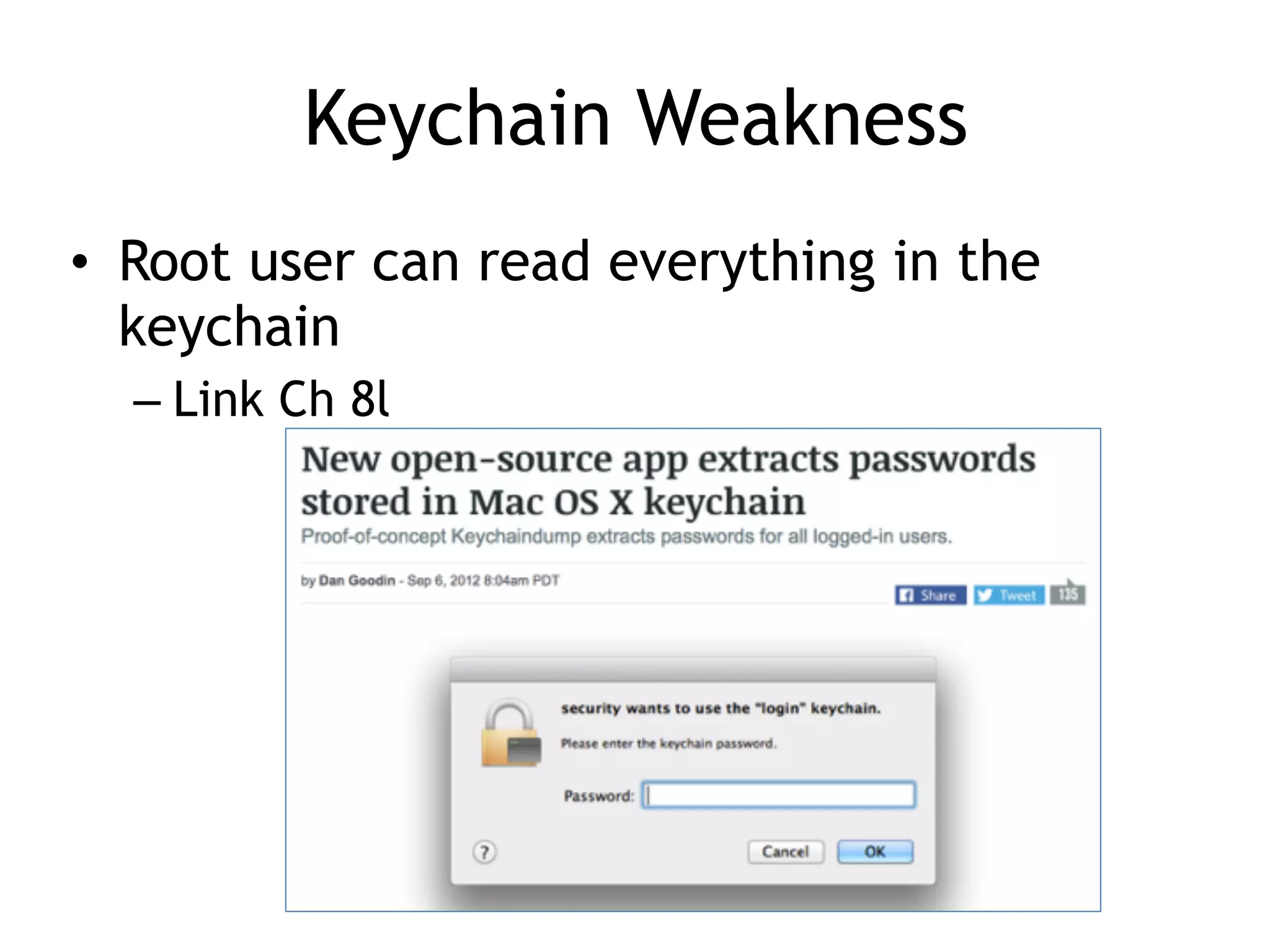
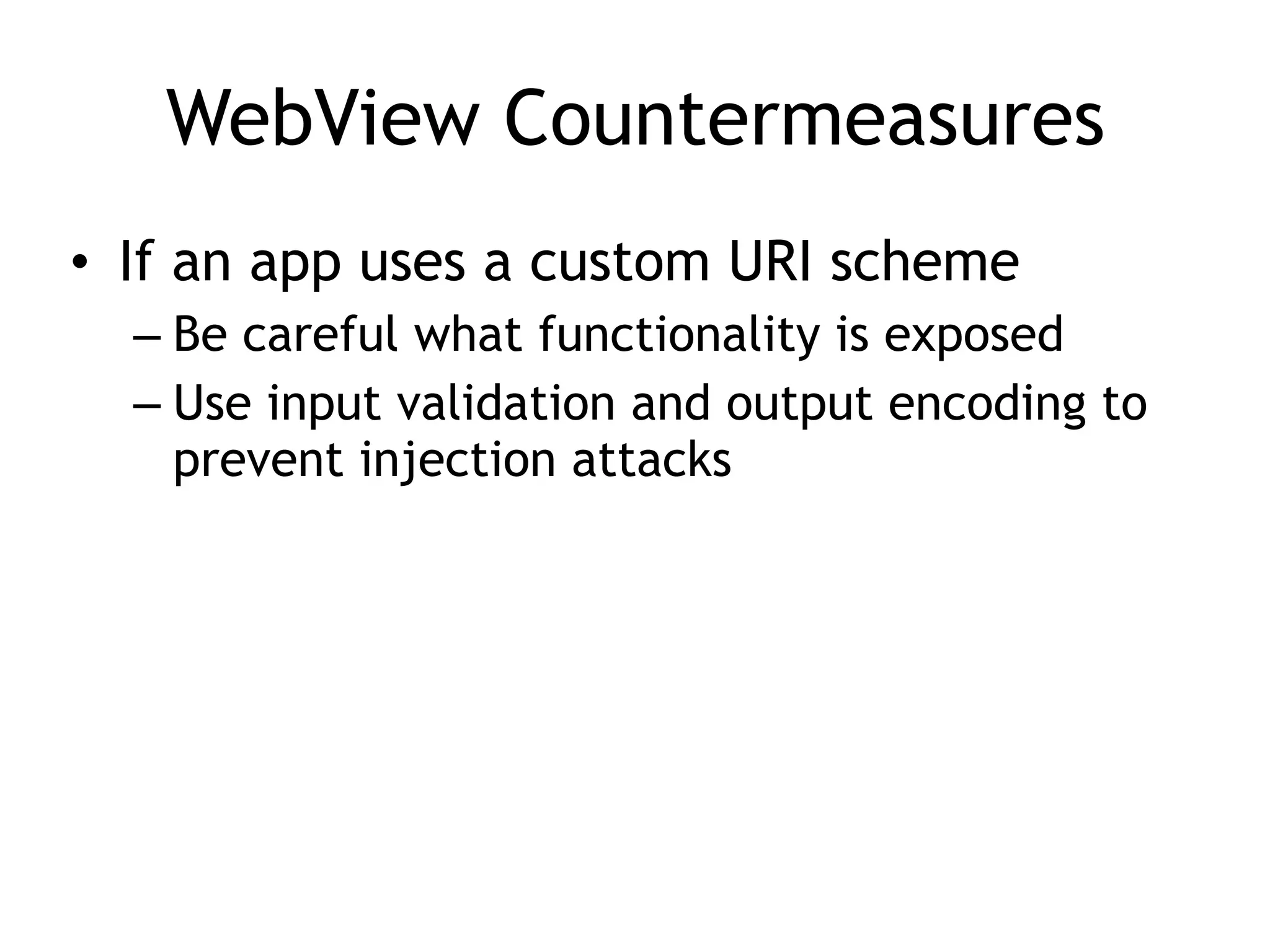
This document discusses threat modeling and guidelines for securing mobile applications. It covers conducting threat modeling as a pencil-and-paper exercise to identify security risks and prioritize mitigations. Guidelines are provided for both native mobile apps and mobile web apps, including storing sensitive data securely, authenticating to mobile services, securing communications, and preventing information leakage. Platform-specific guidelines are also outlined for iOS and Android.