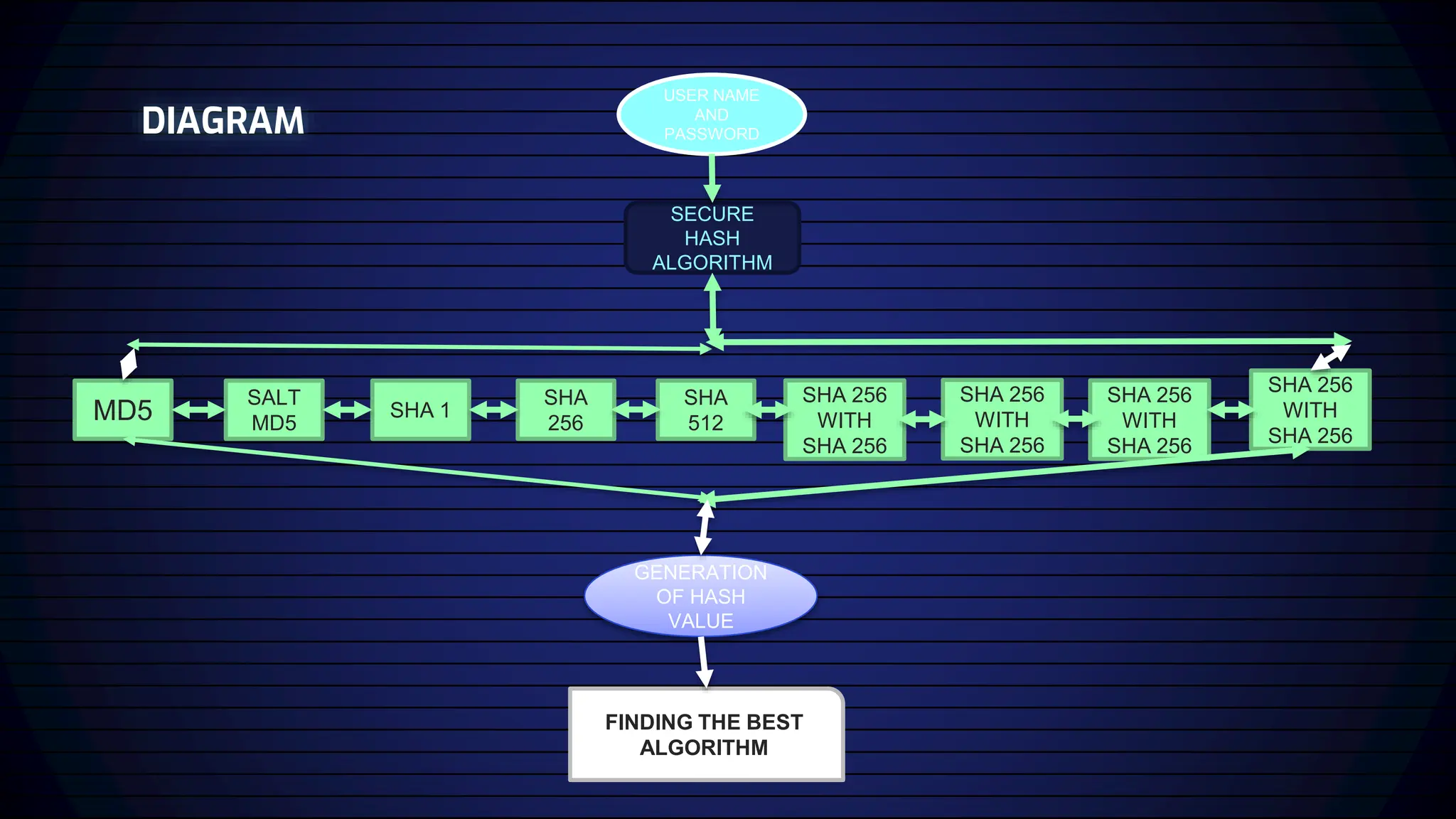
This paper proposes using a double hashing algorithm approach to strengthen password security when storing passwords. It analyzes established hashing algorithms like SHA-1, MD-5, and SHA-512, and also introduces four new hashing functions that combine existing algorithms, such as SHA-256 with SHA-256. The paper develops a system to generate hash values for input passwords using nine different hashing algorithms and store the results in separate MySQL tables to facilitate comparison of hash strengths. This allows thorough examination of how various algorithms impact the security of stored password hashes.







![REFERENCES
● [1]. Long, Sihan. "A Comparative Analysis of the Application of Hashing Encryption
Algorithms for MD5, SHA-1, and SHA-512." Journal of Physics: Conference Series, vol.
1314, IOP Publishing, 2019.
● [2]. De Guzman, Froilan E., Bobby D. Gerardo, and Ruji P. Medina. "Implementation of
enhanced secure hash algorithm towards a secured web portal." 2019 IEEE 4th
International Conference on Computer and Communication Systems (ICCCS), pp. 189-192.
IEEE, 2019.
● [3]. Sharma, Arvind K., and S. K. Mittal. "Cryptography & Network Security Hash Function
Applications, Attacks and Advances: A Review." 2019 Third International Conference on
Inventive Systems and Control (ICISC), IEEE, 2019.
● This paper is from Comparative Analysis of Password Storage Security using Double
Secure Hash Algorithm by Savarala Chethana, Sreevathsa Sree Charan, Vemula Srihitha,
D. Radha, Kavitha C. R.](https://image.slidesharecdn.com/project-240213061002-b0386cbf/75/Comparative-hash-algorithm-power-point-presentation-10-2048.jpg)