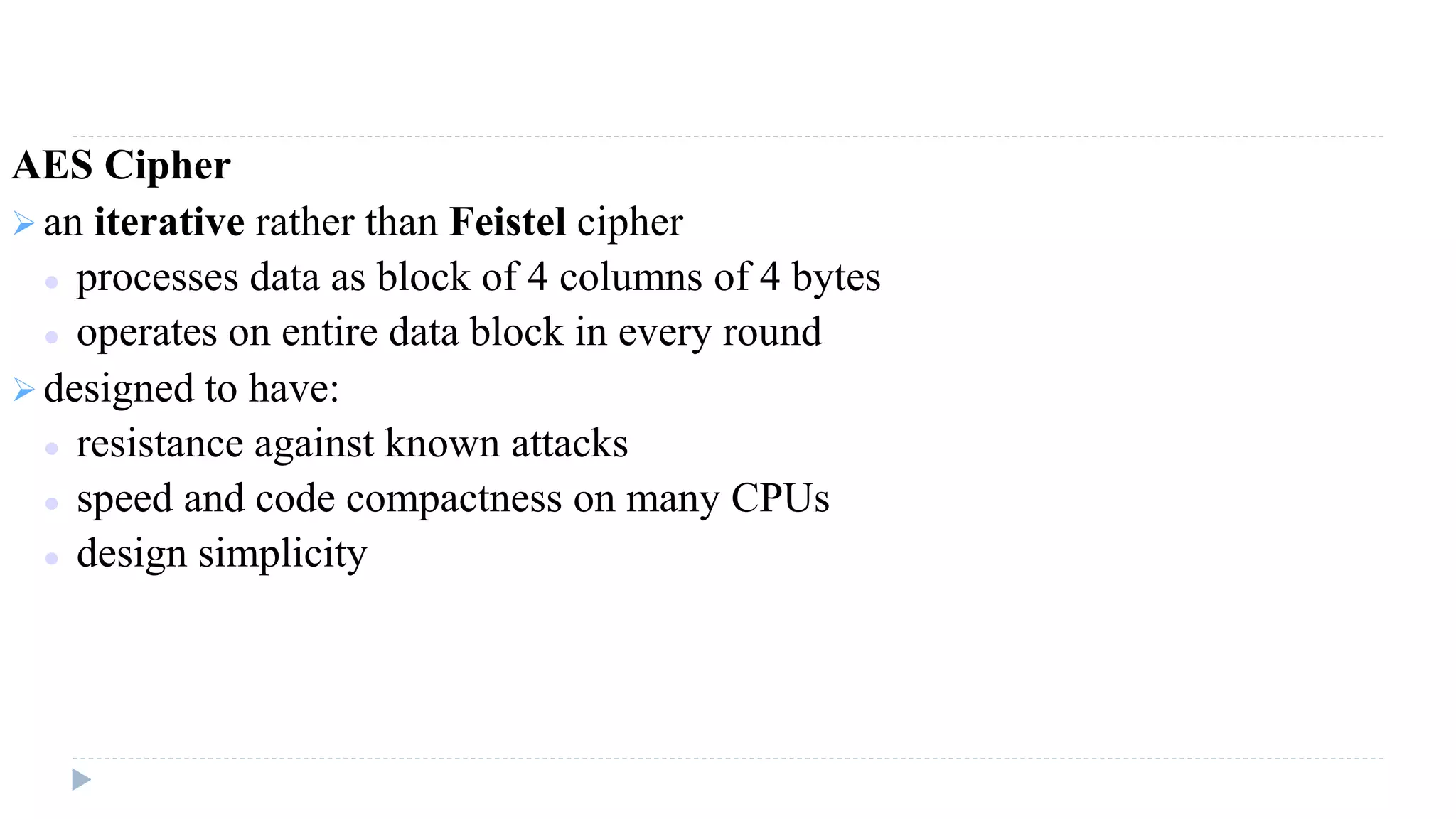
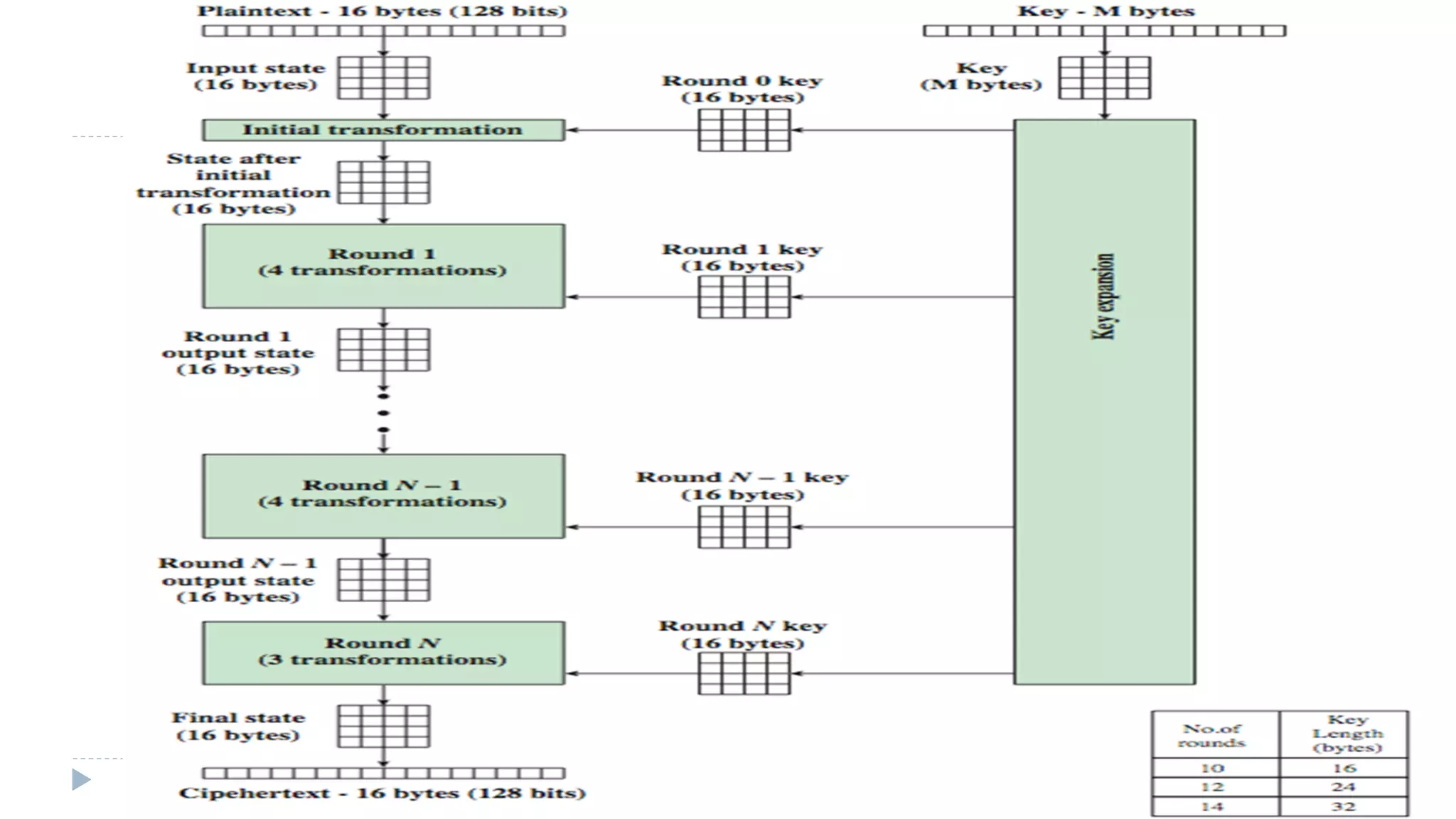
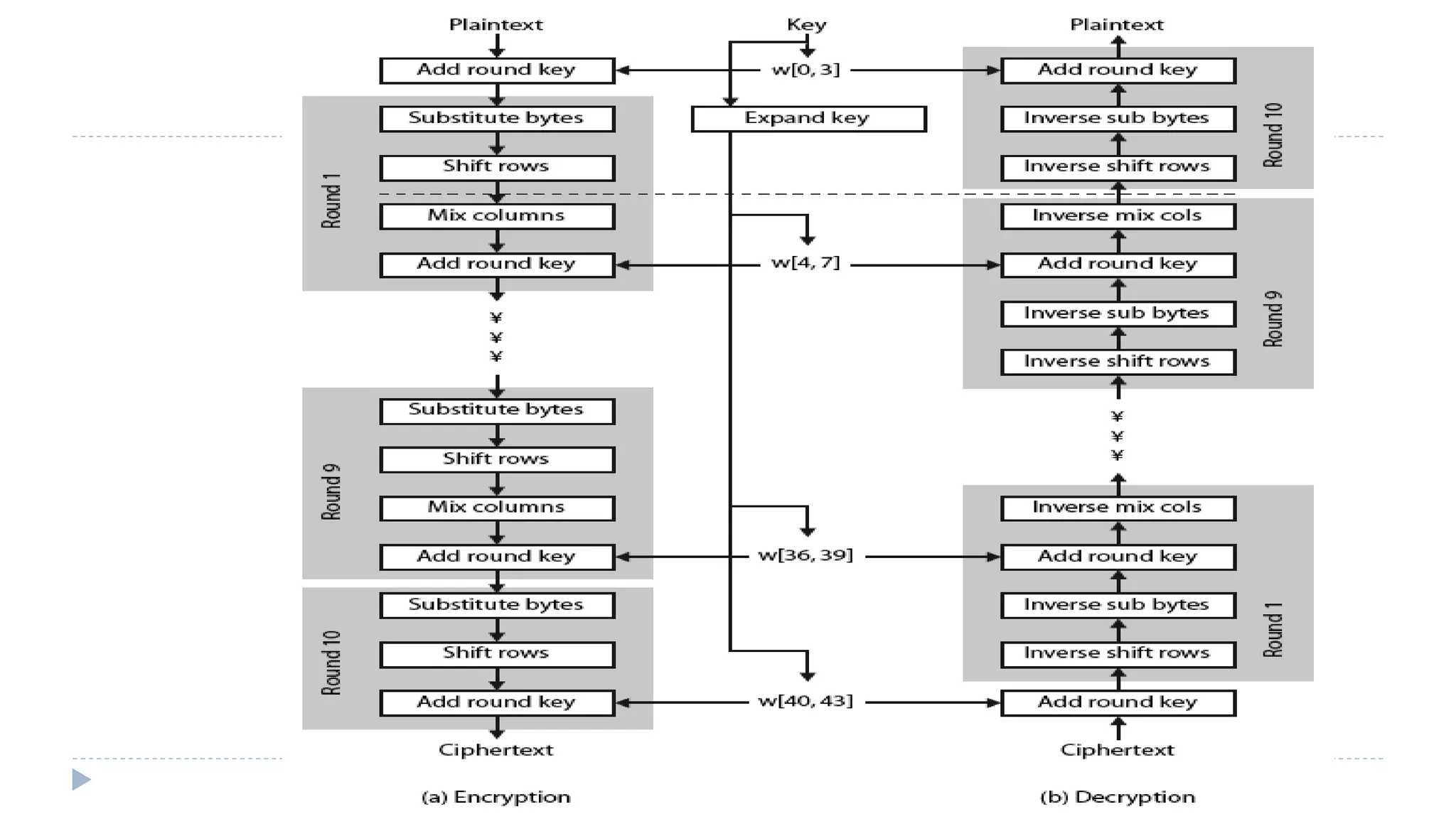
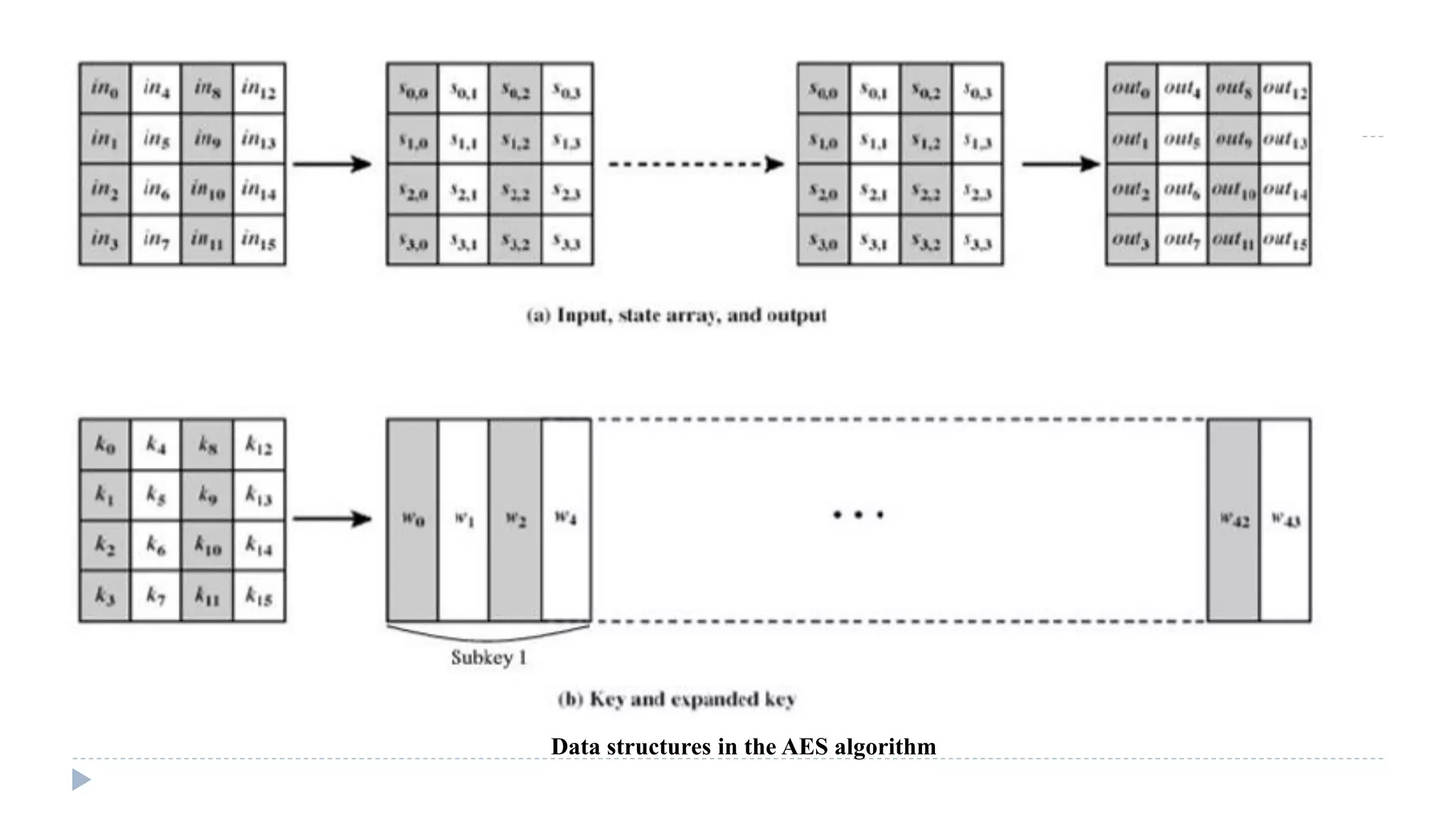
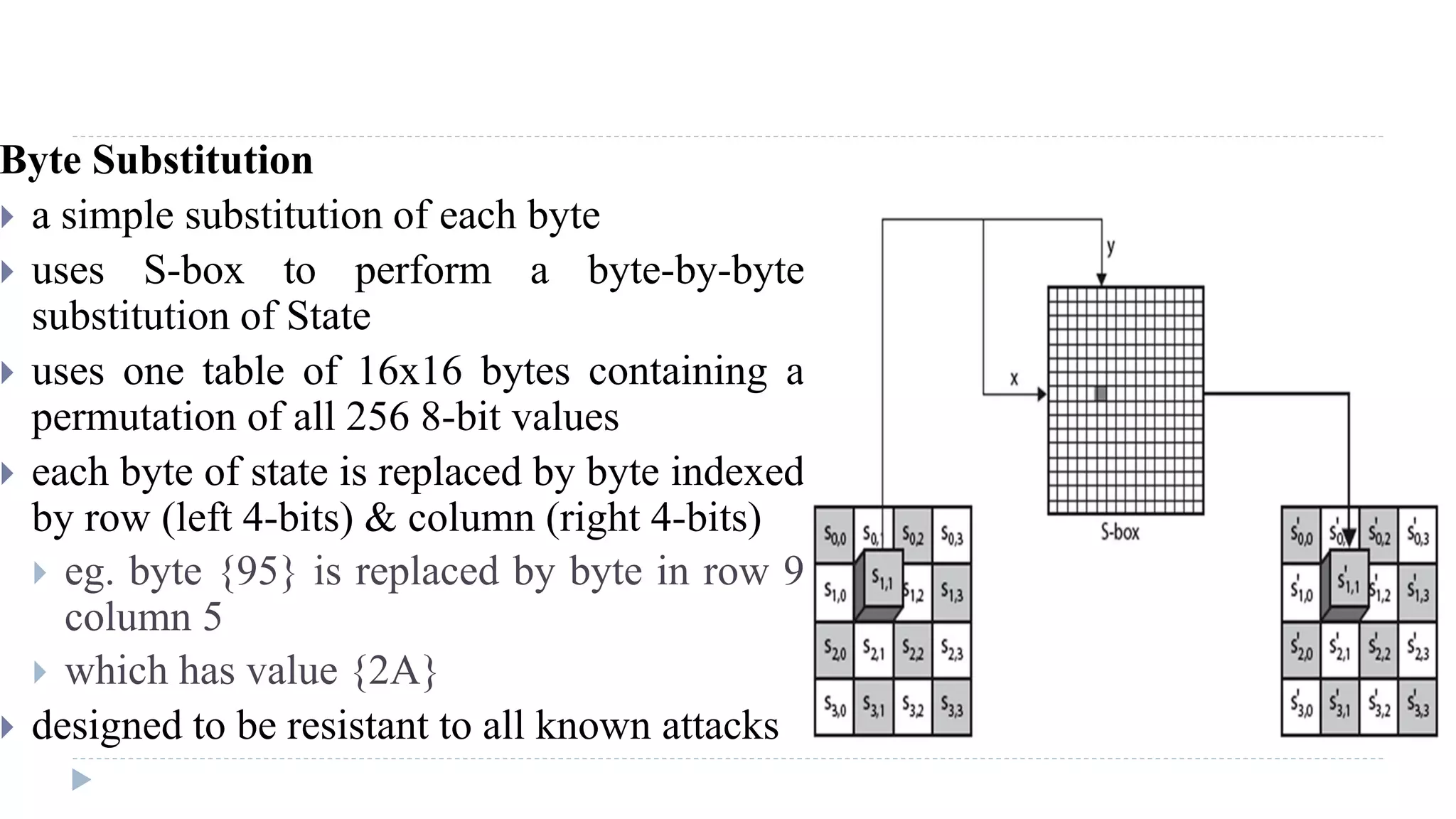
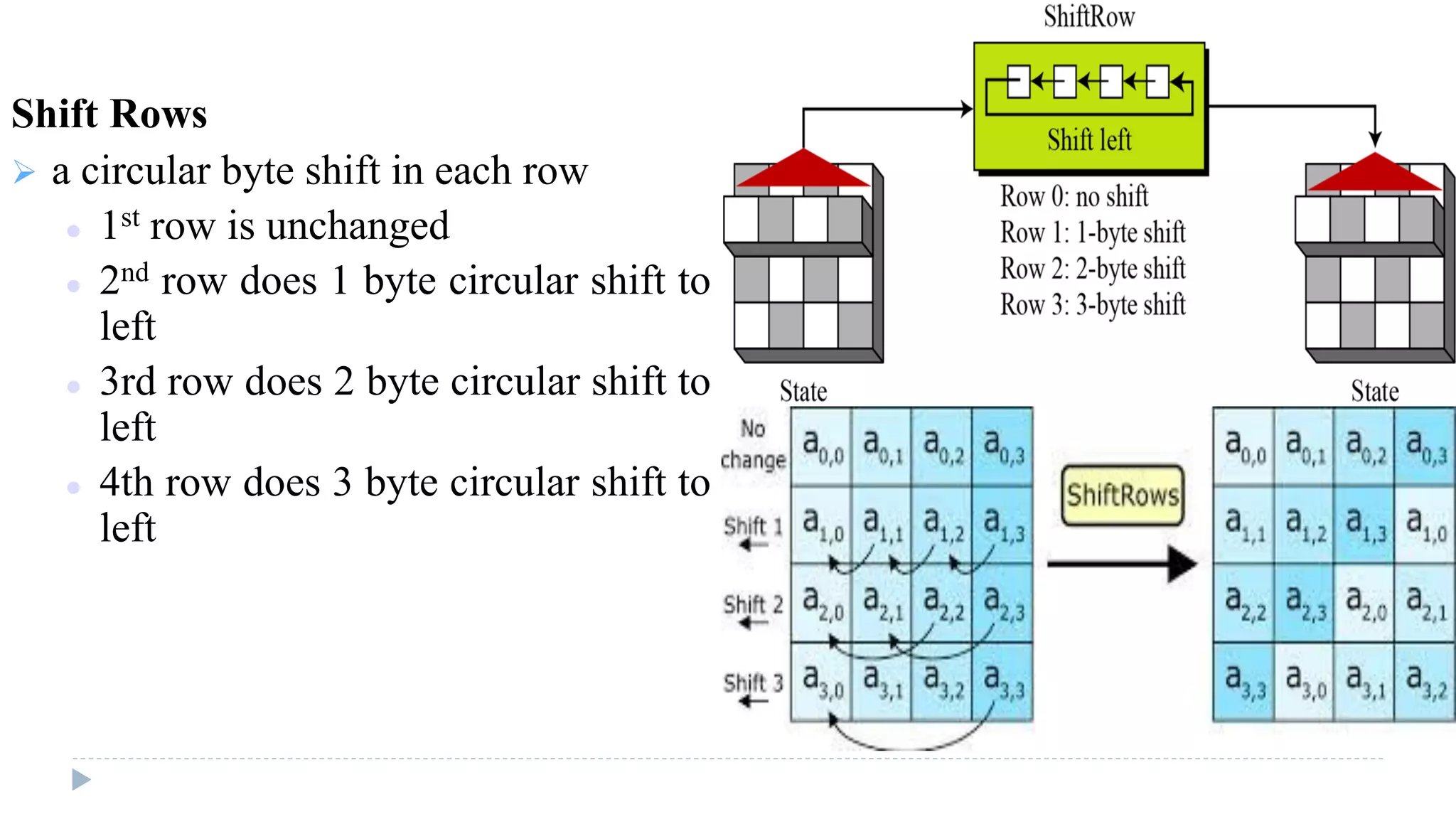
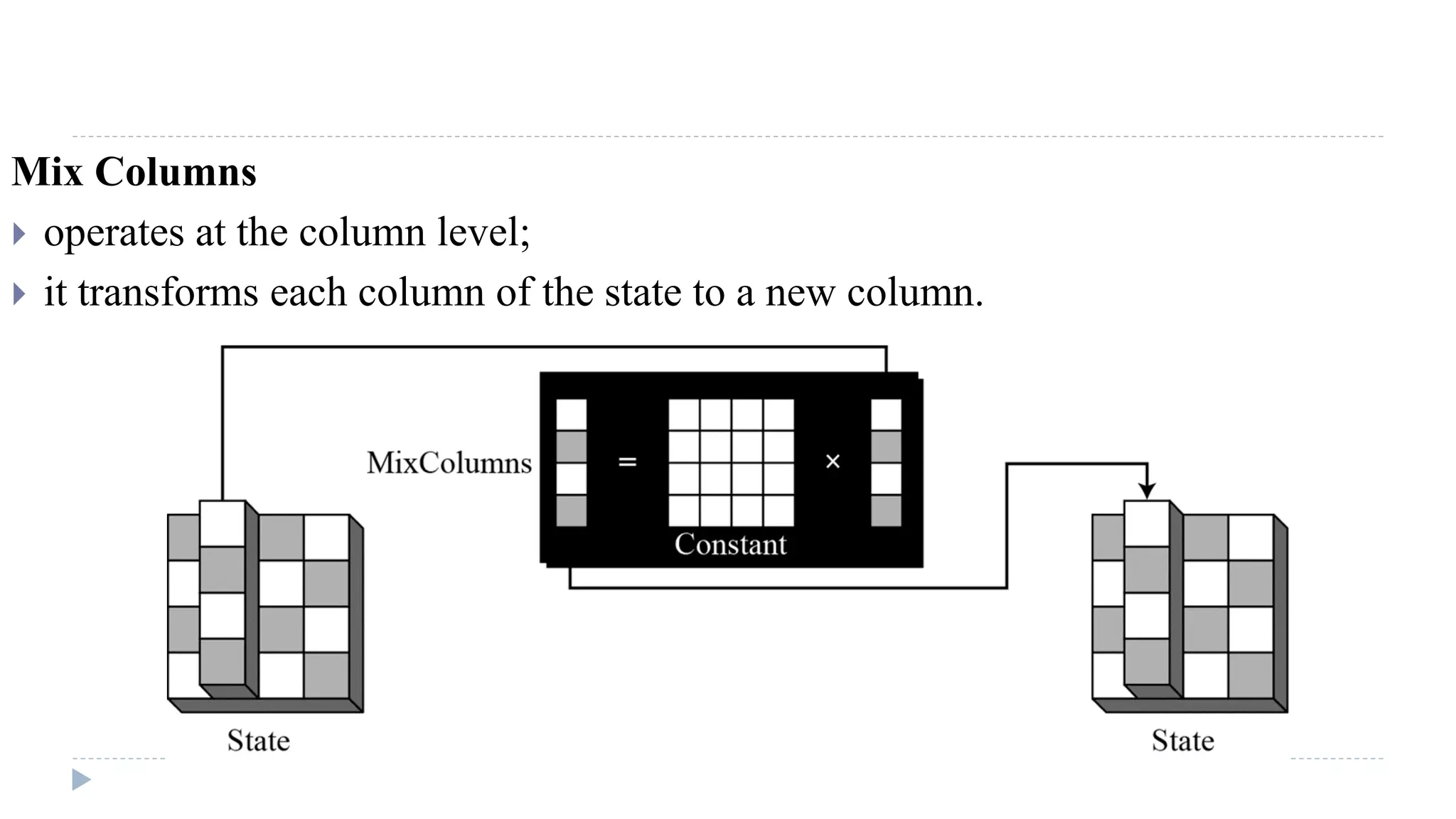
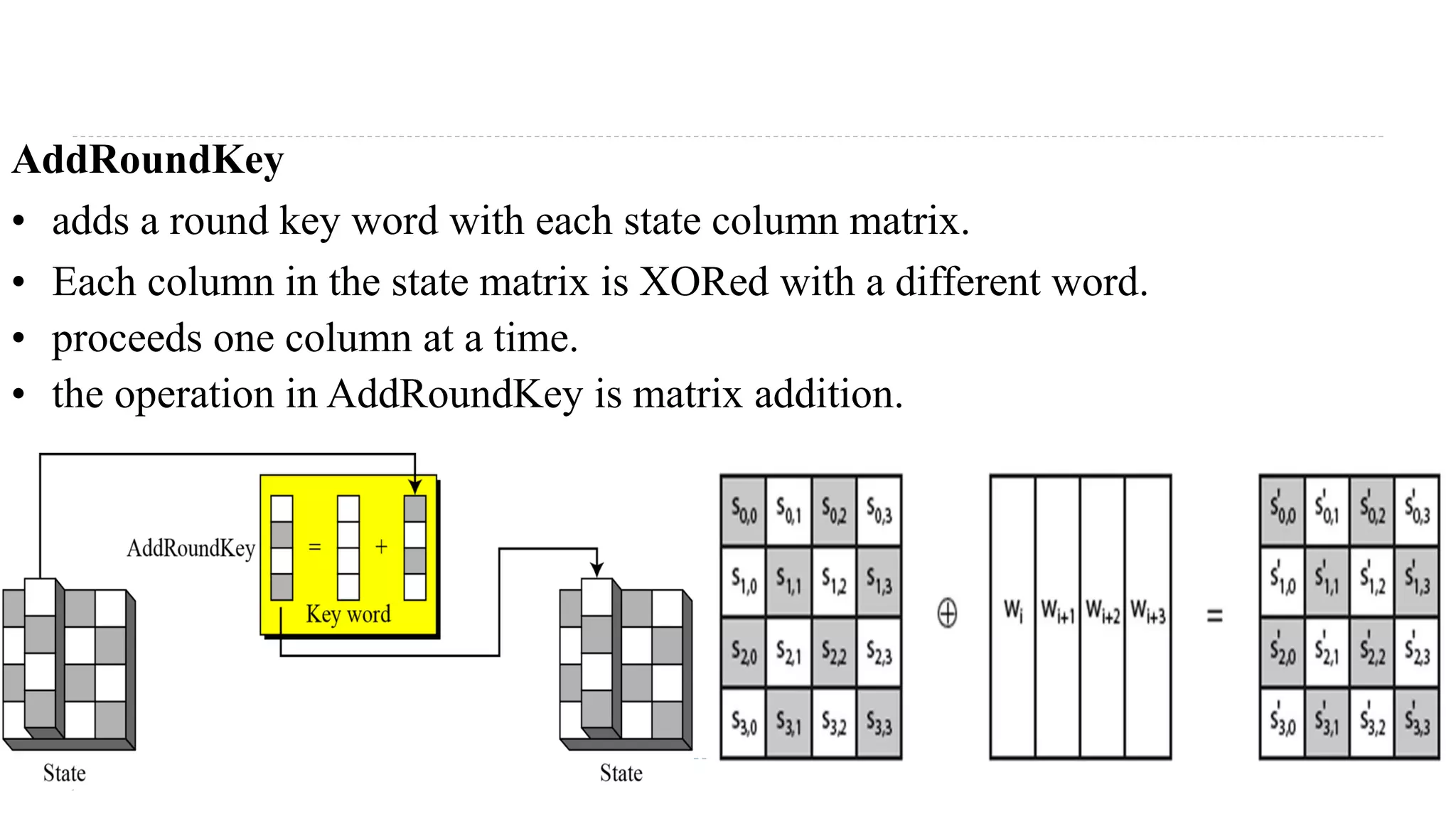
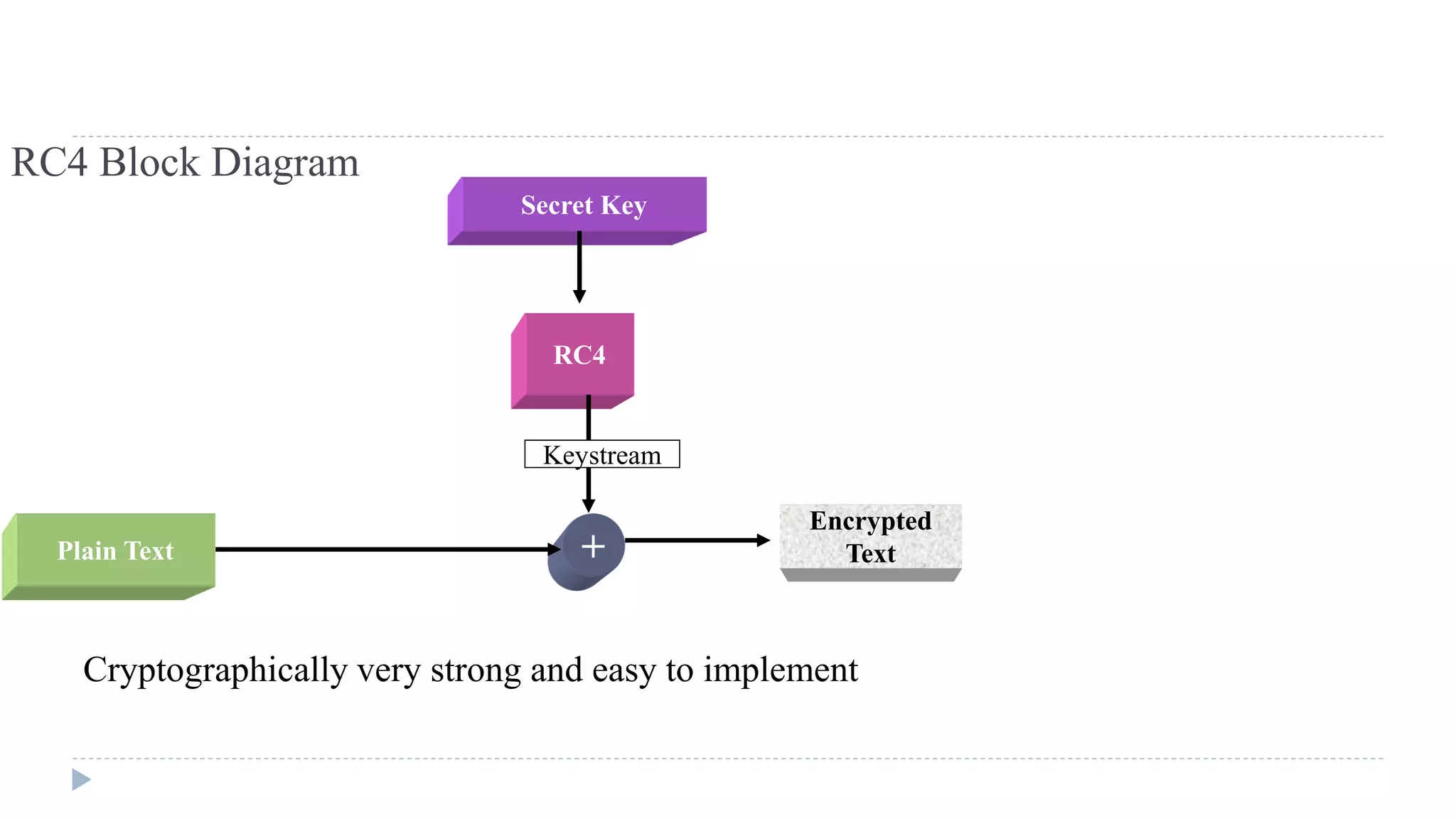
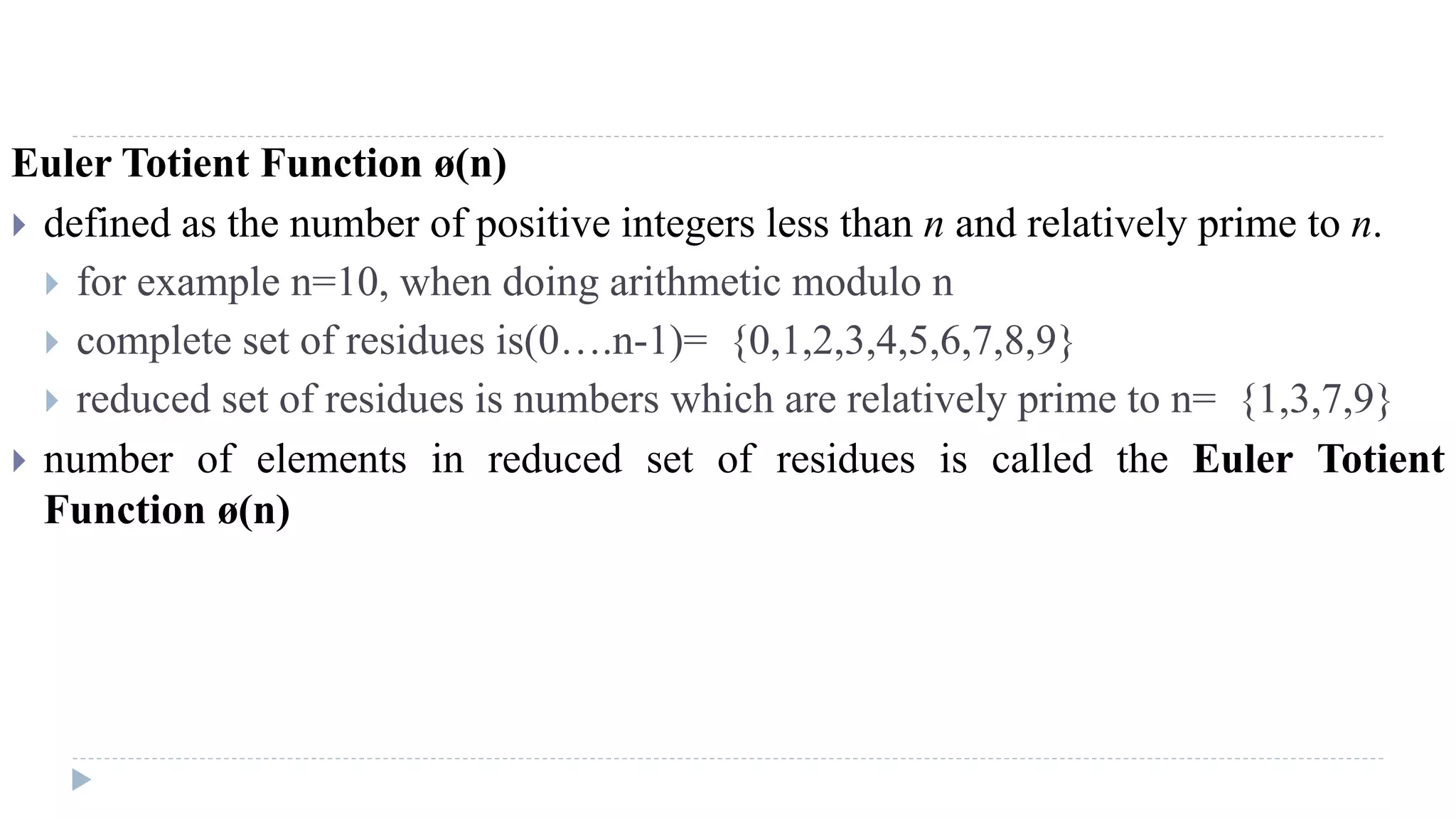
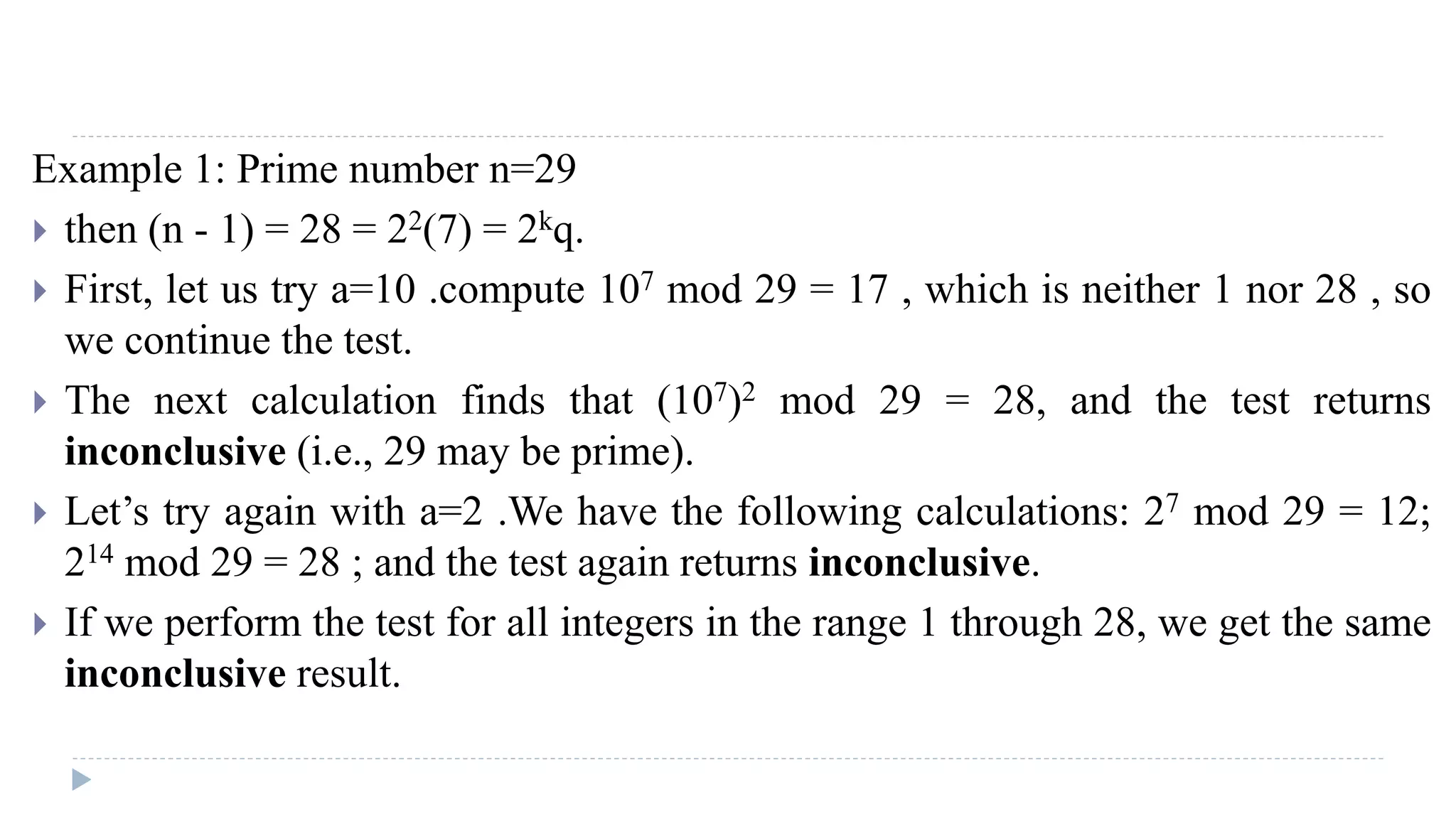
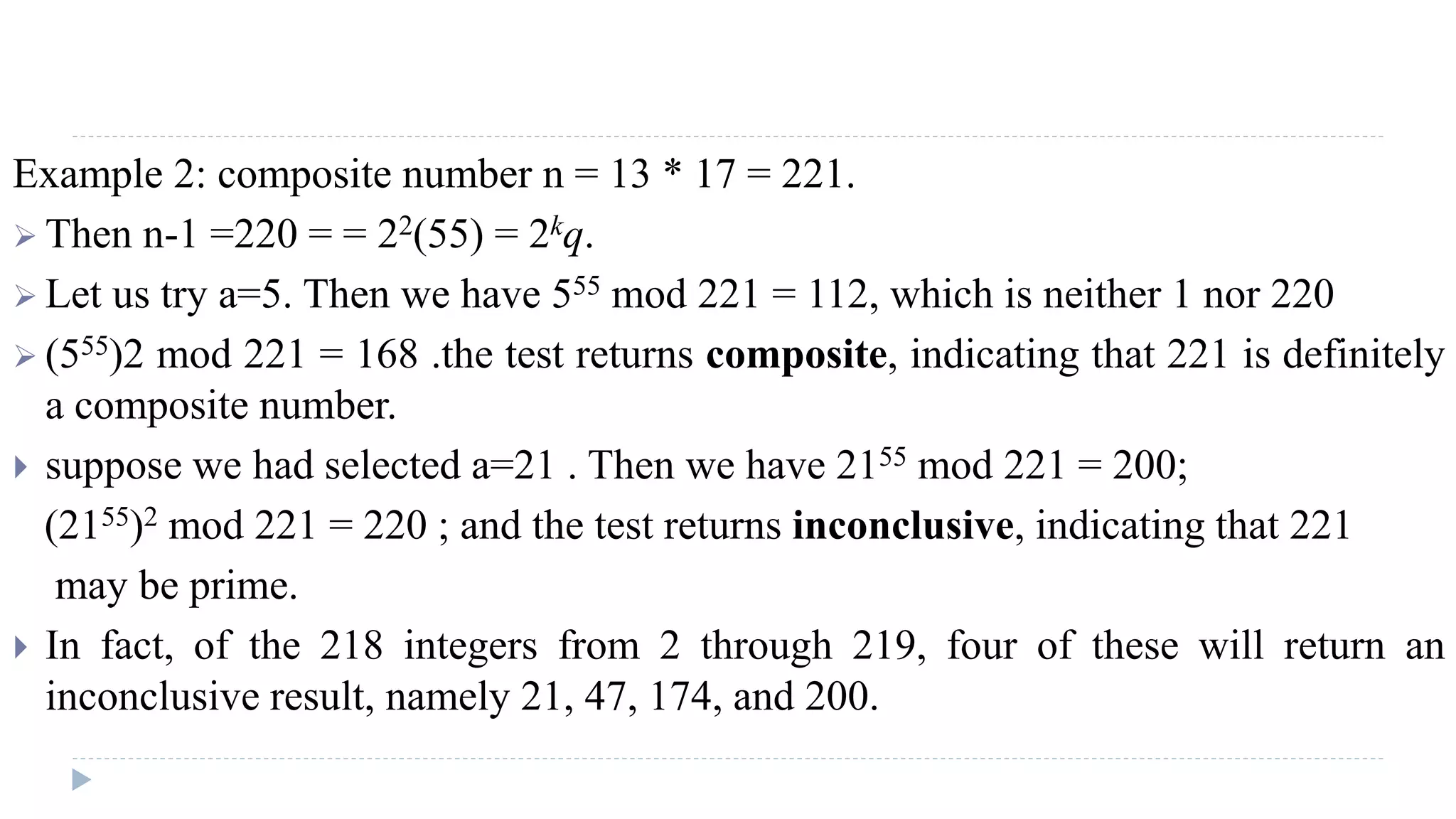
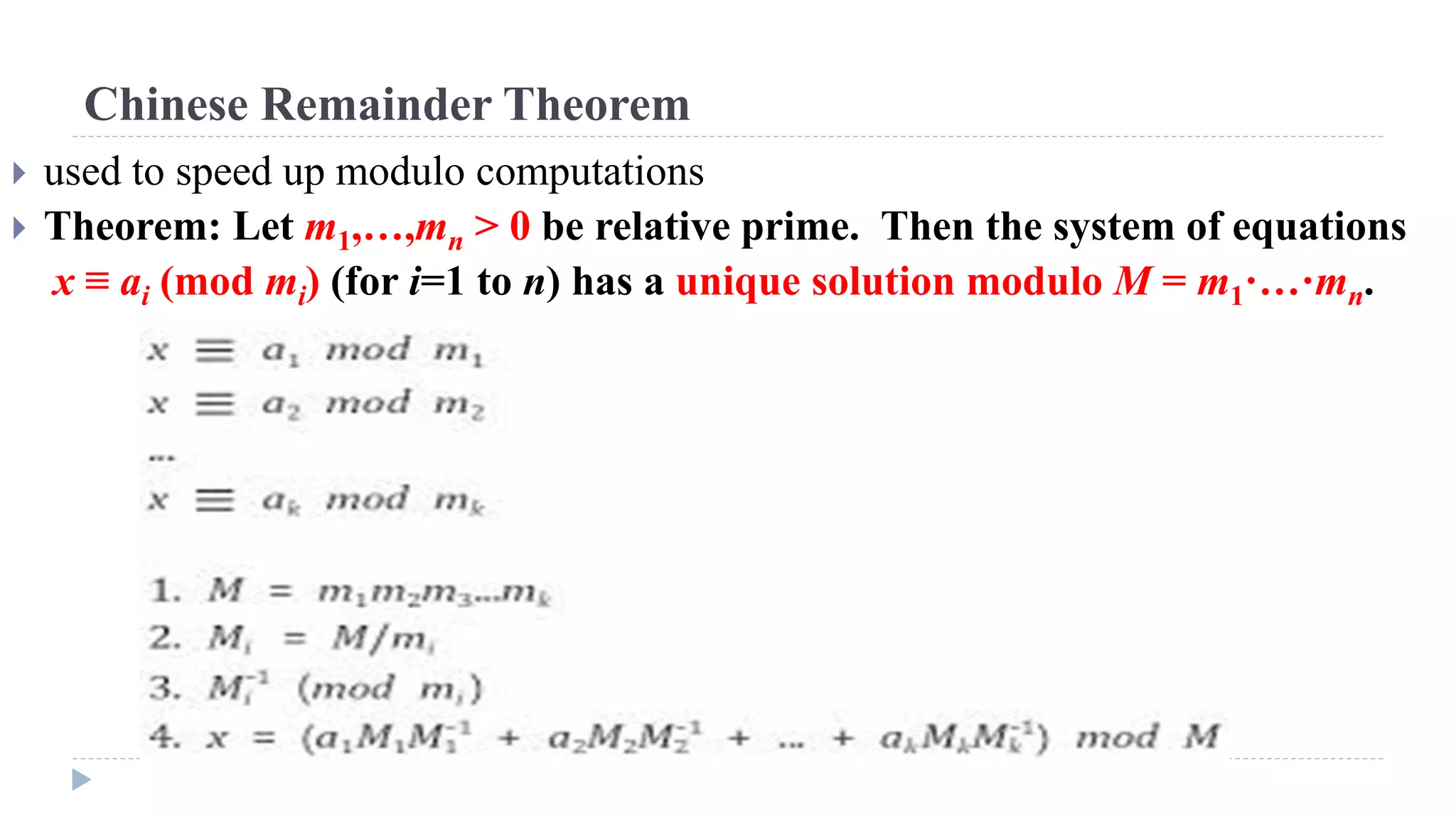
The document provides an in-depth overview of the Advanced Encryption Standard (AES), focusing on its design, structure, and security features. AES, a symmetric block cipher developed by Rijmen-Daemen, is intended to replace DES and 3DES, offering resistance to known cryptographic attacks and efficient performance. It details various encryption processes, key expansion, and modes of operation, alongside other encryption methods like RC4 and the importance of key distribution in symmetric encryption.












![The KSA
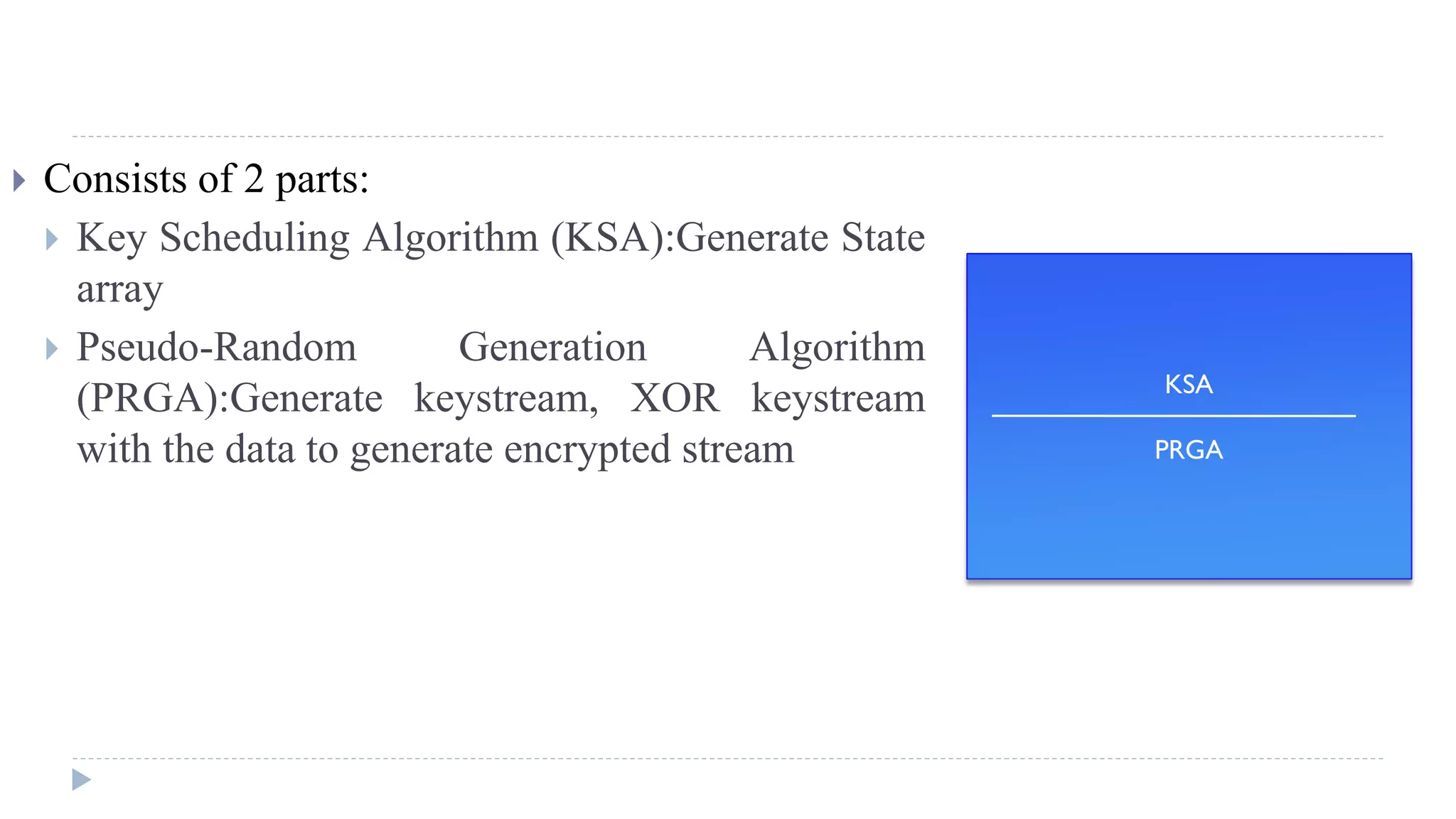
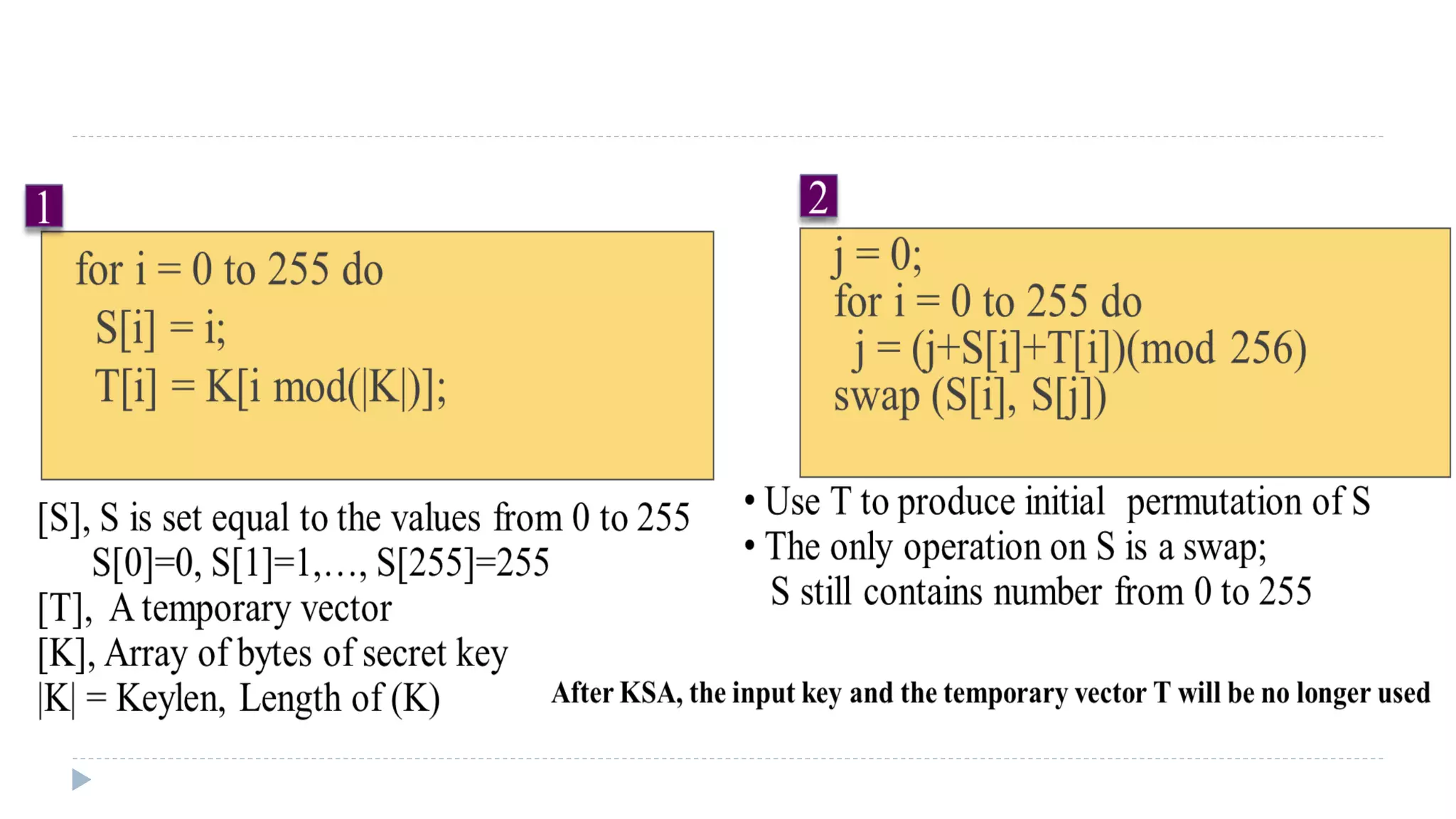
Use the secret key to initialize and permutation of state vector S, done in two
steps
A variable-length key of from 1 to 256 bytes (8 to 2048 bits) is used to initialize a
256-byte state vector S, with elements S[0],S[1], Á ,S[255].
At all times, S contains a permutation of all 8-bit numbers from 0 through 255.](https://image.slidesharecdn.com/computersecurity-module2-150310001407-conversion-gate01/75/Computer-security-module-2-40-2048.jpg)
![The PRGA Generate key stream k , one by one
XOR S[k] with next byte of message to encrypt/decrypt
i = j = 0;
While (more_byte_to_encrypt)
i = (i + 1) (mod 256);
j = (j + S[i]) (mod 256);
swap(S[i], S[j]);
k = (S[i] + S[j]) (mod 256);
Ci = Mi XOR S[k];
Sum of shuffled pair selects "stream key" value from permutation](https://image.slidesharecdn.com/computersecurity-module2-150310001407-conversion-gate01/75/Computer-security-module-2-42-2048.jpg)



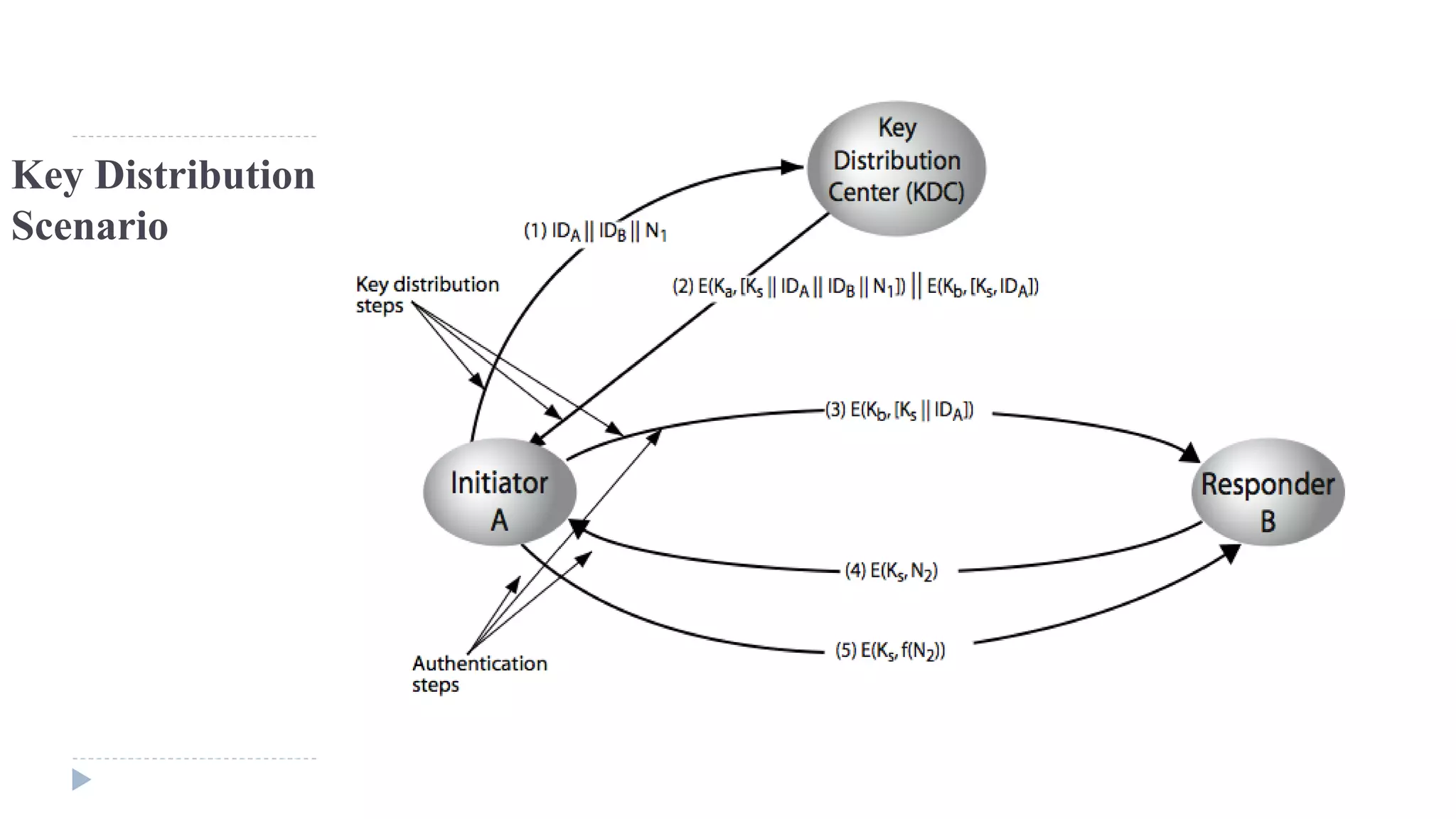

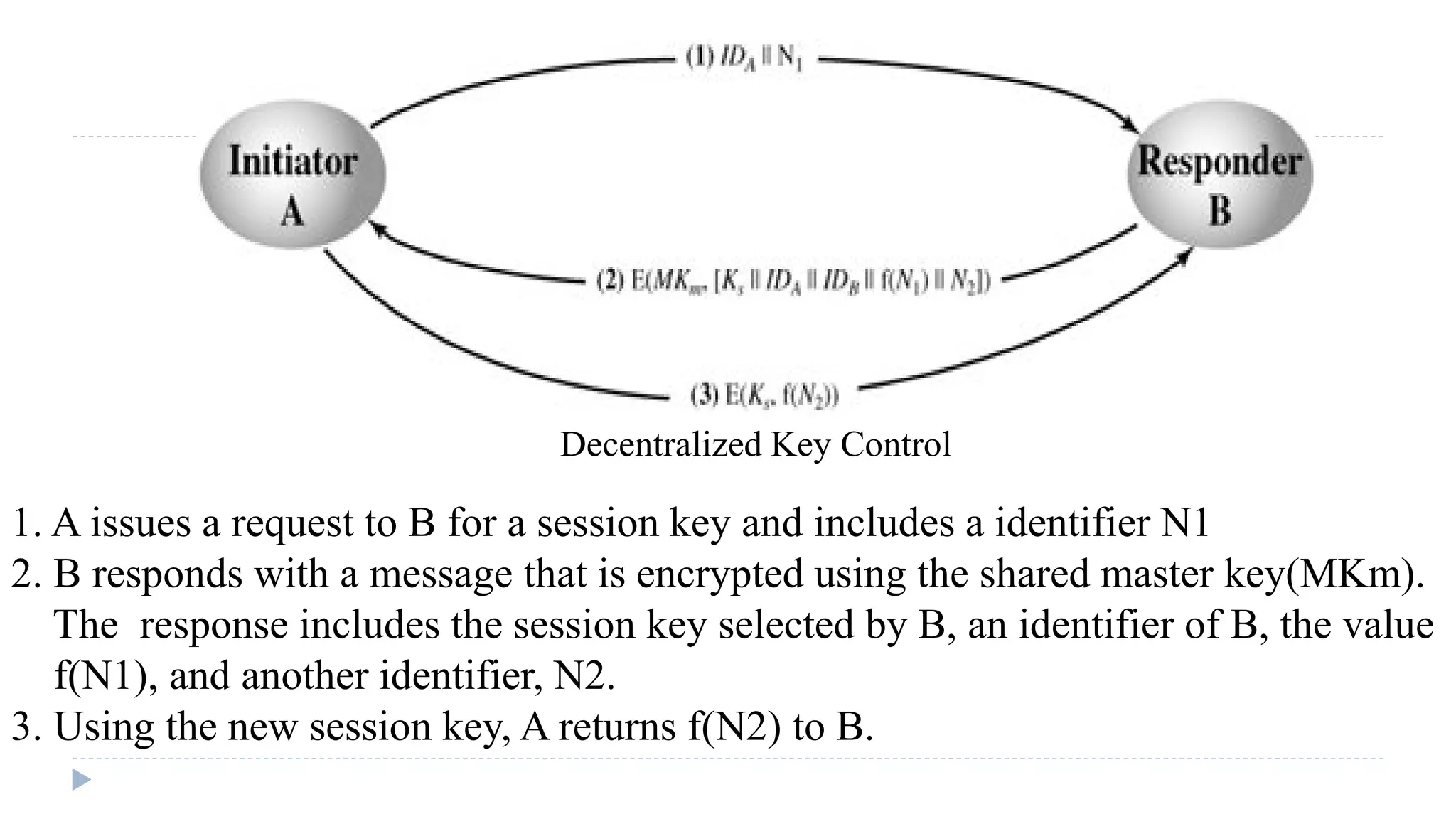
![3. A stores the session key for use in the upcoming session and forwards to B
the information that originated at the KDC for B, namely, E(Kb, [Ks || IDA]).
4. Using the newly minted session key for encryption, B sends a identifier N2, to A.
5. Also using Ks, A responds with f(N2), where f is a function that performs some
transformation on N2 (e.g., adding one).](https://image.slidesharecdn.com/computersecurity-module2-150310001407-conversion-gate01/75/Computer-security-module-2-55-2048.jpg)















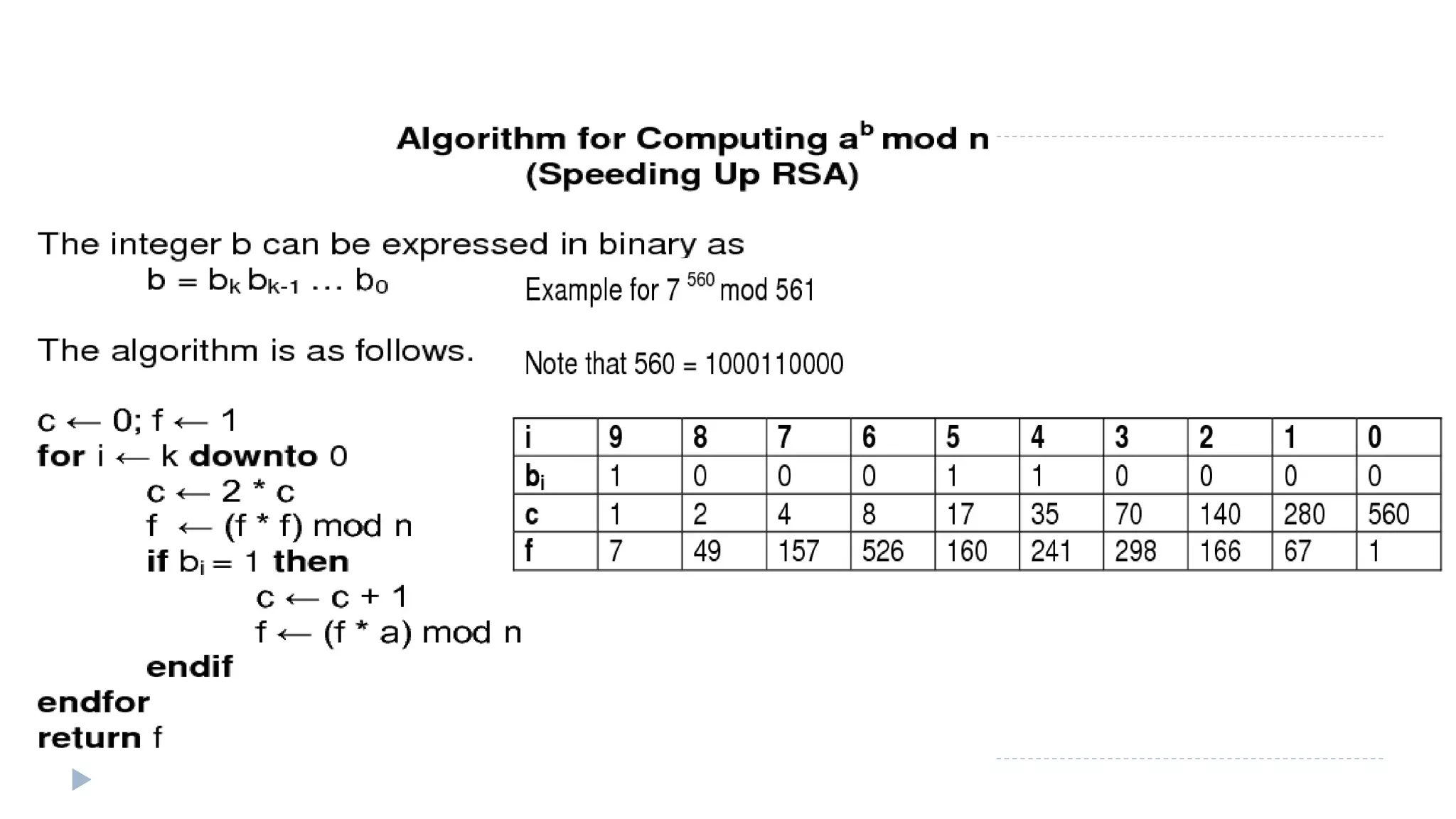
![Exponentiation
can use the Square and Multiply Algorithm
a fast, efficient algorithm for exponentiation
x11 mod n=
x11 = x1+2+8 = (x)(x2)(x8)
=[(x mod n) × (x2 mod n) × (x8 mod n)] mod n
e.g. 75 = 71 mod 11 × 74 mod 11 = 21 mod 11 = 10 mod 11](https://image.slidesharecdn.com/computersecurity-module2-150310001407-conversion-gate01/75/Computer-security-module-2-88-2048.jpg)