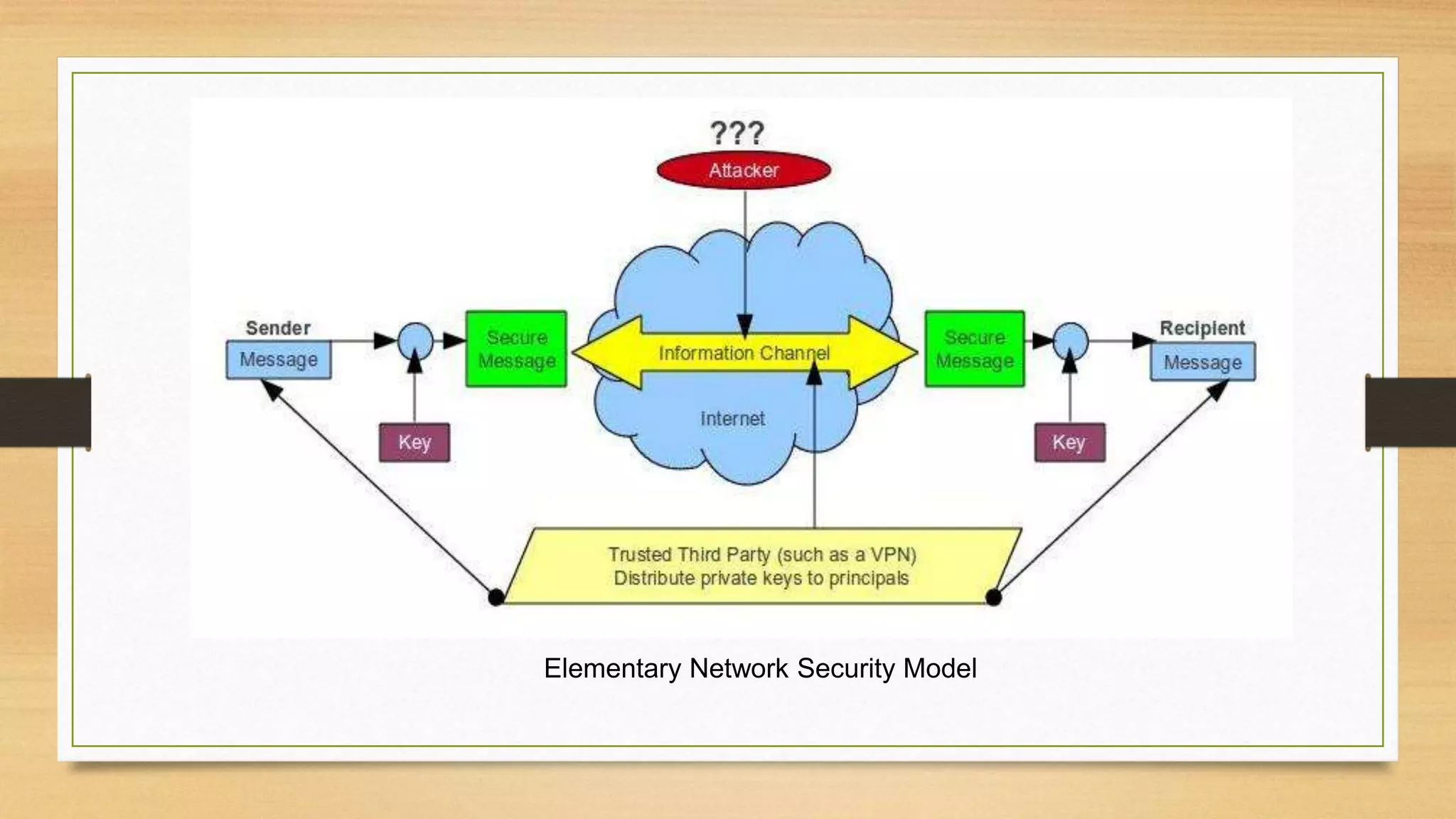
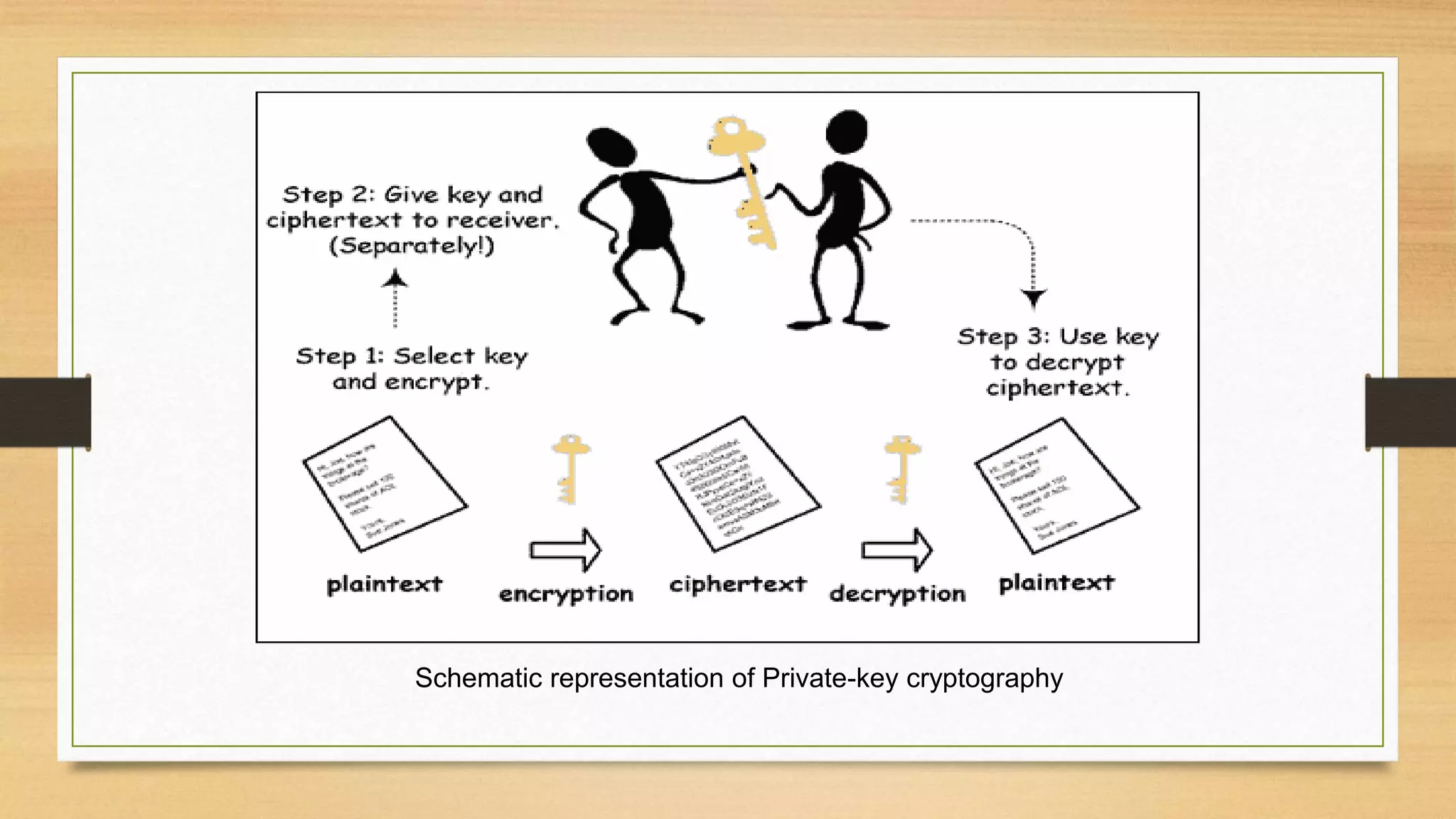
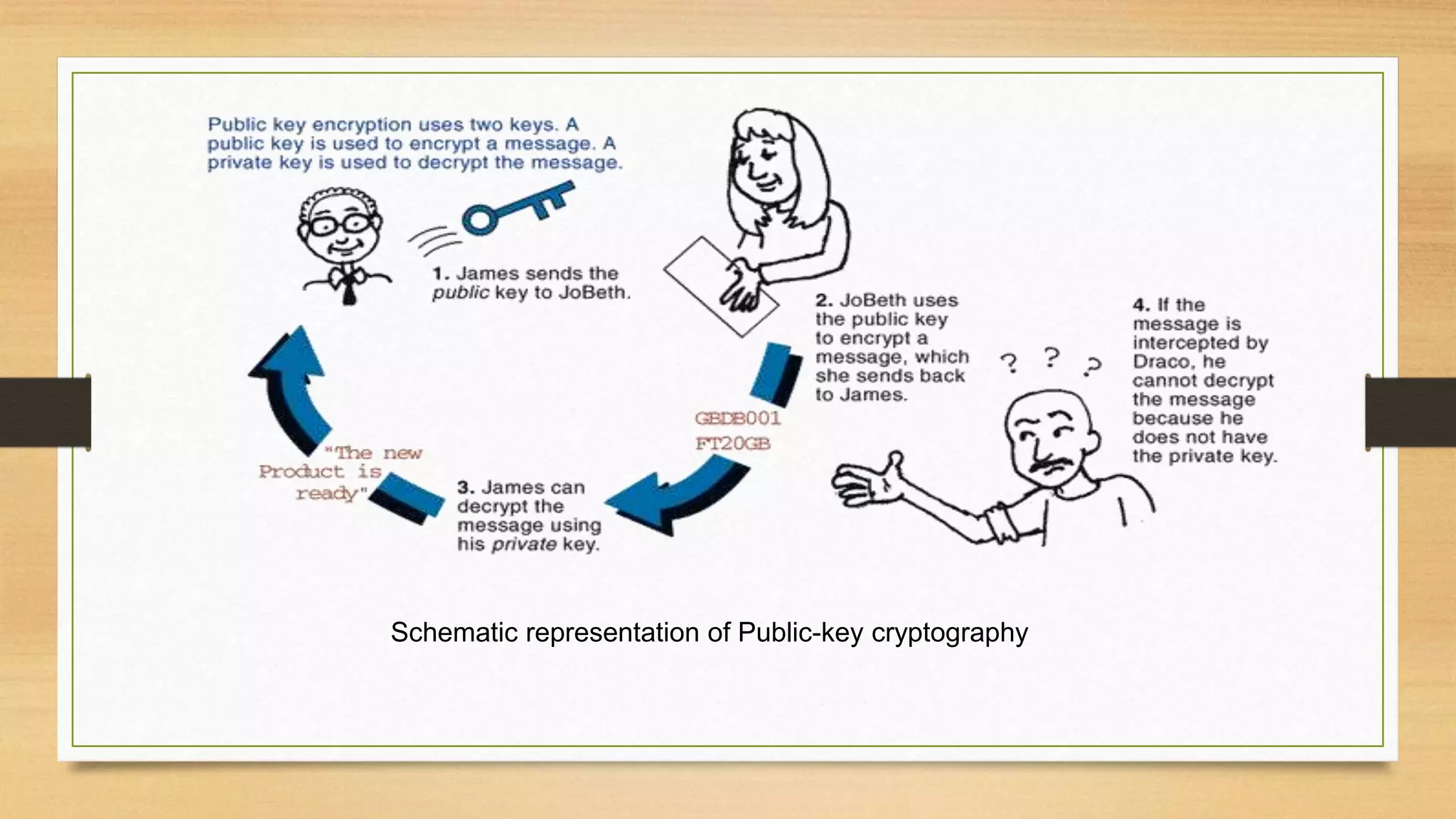
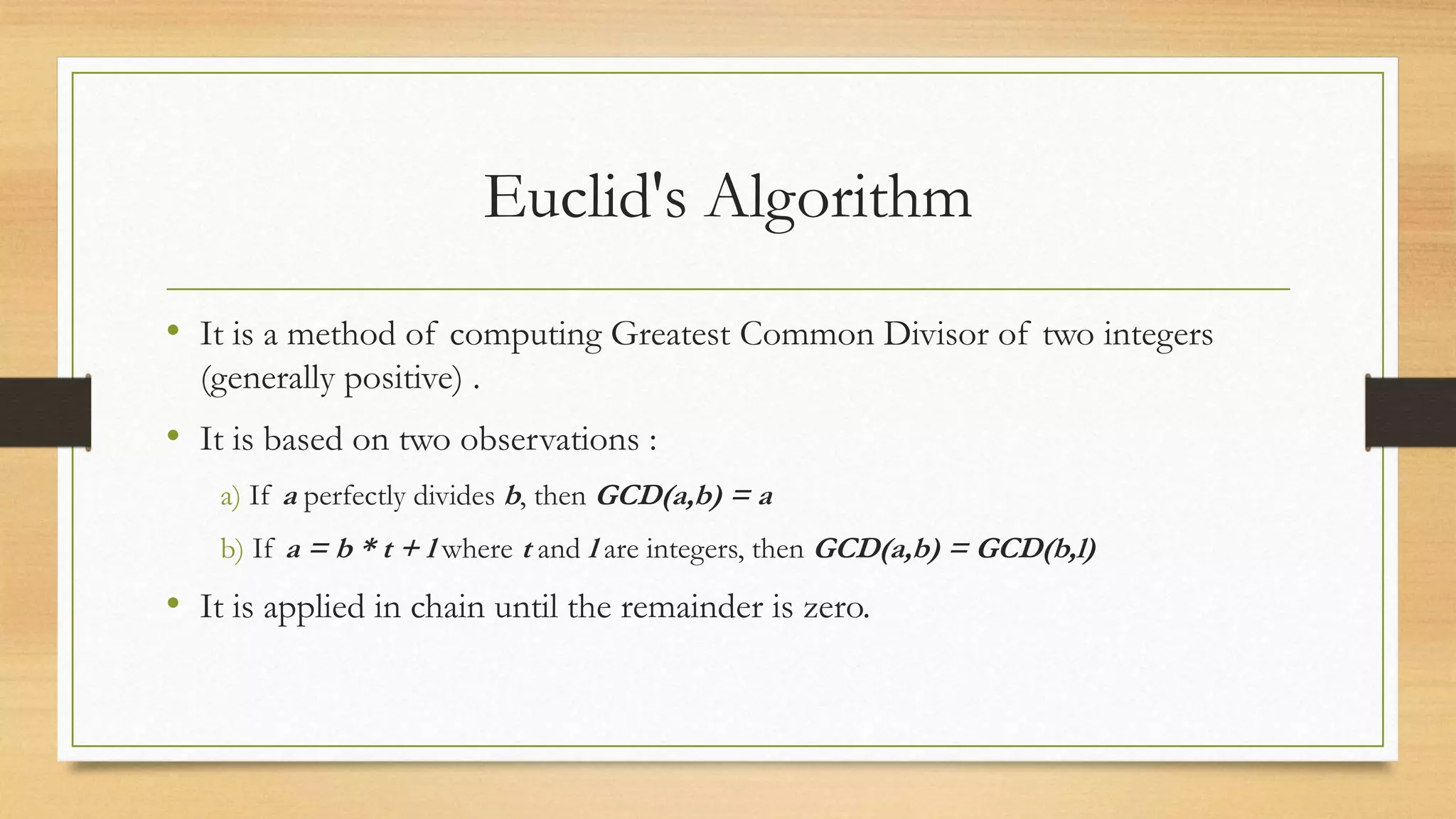
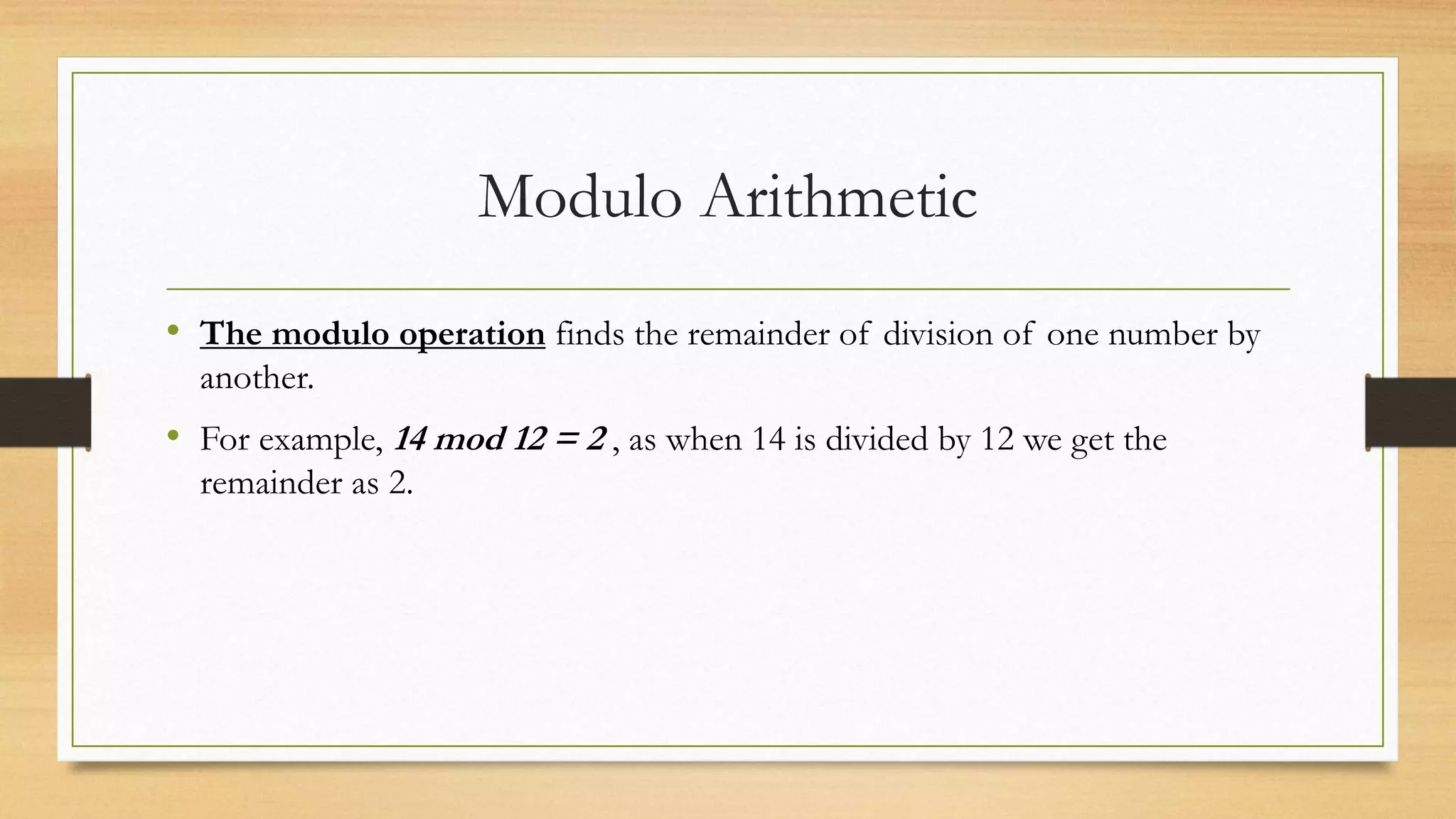
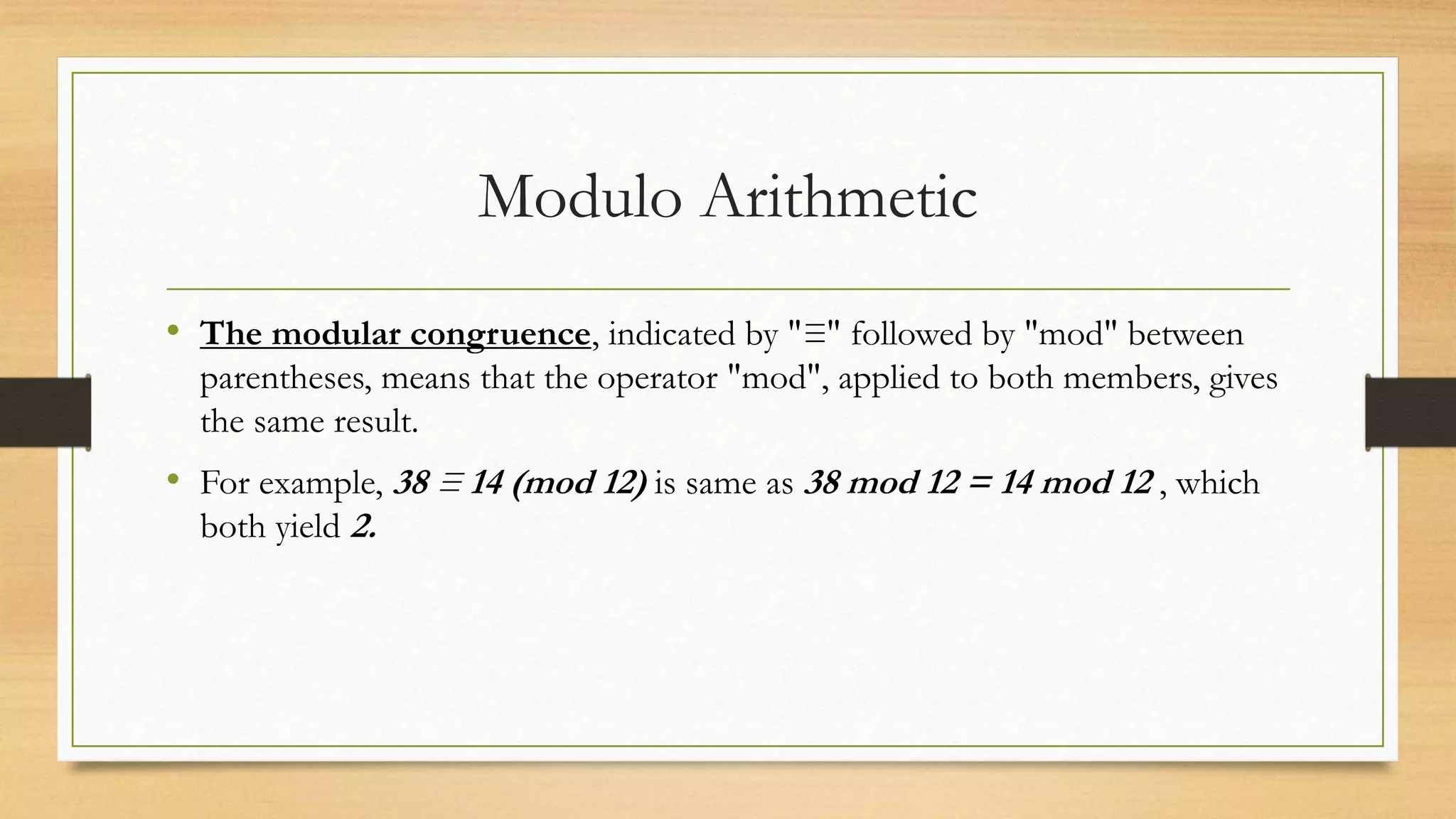
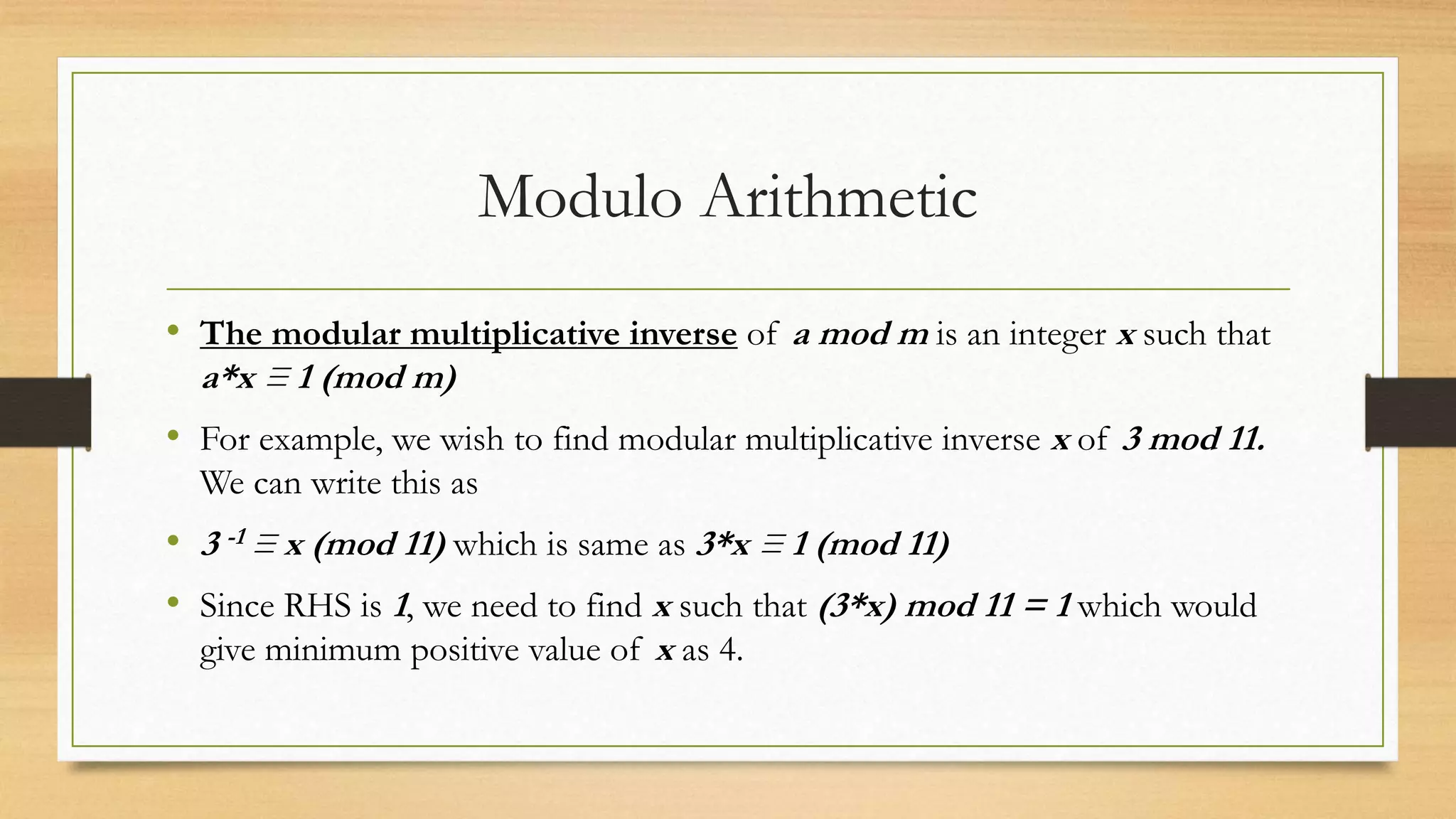
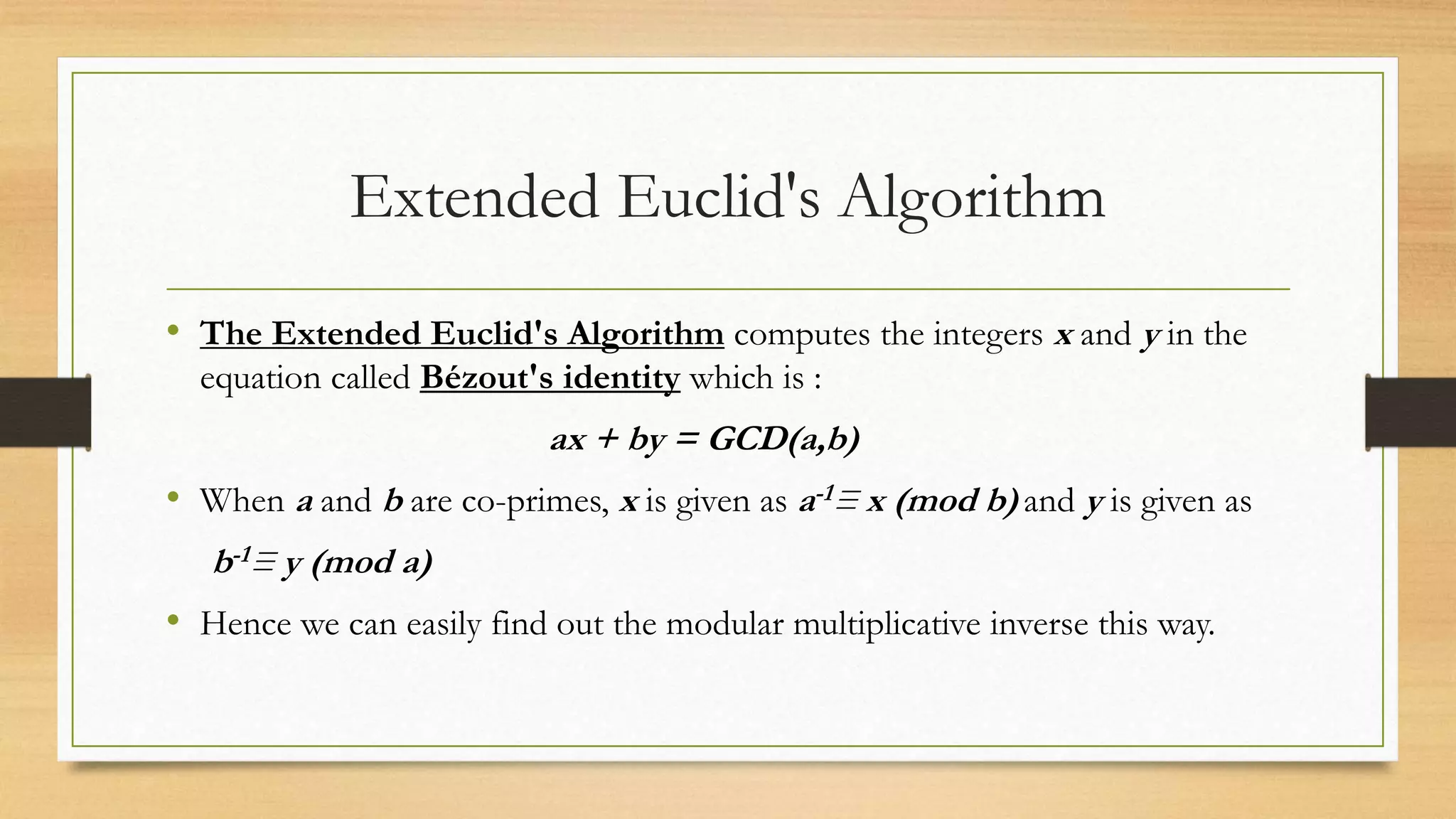
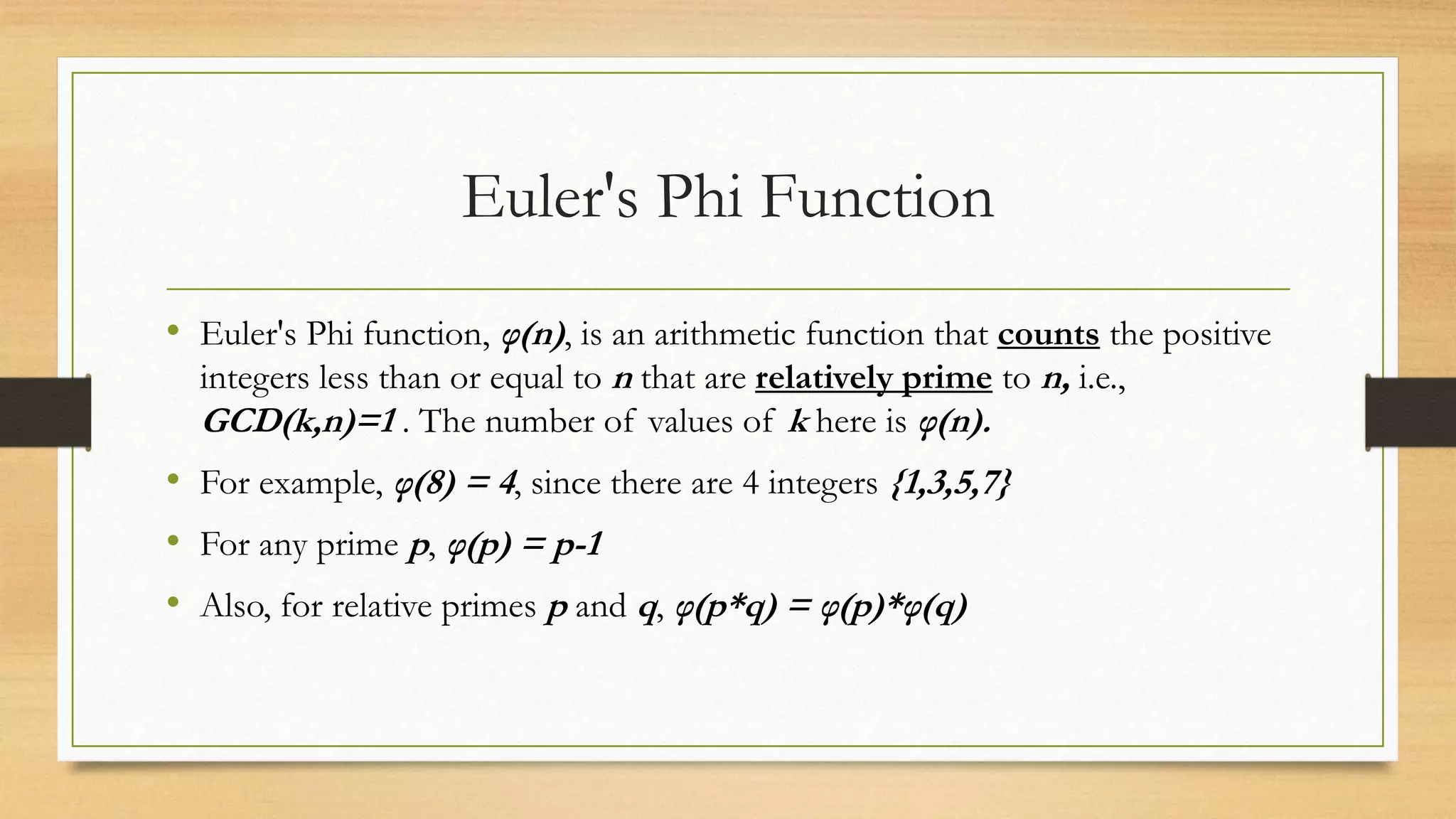
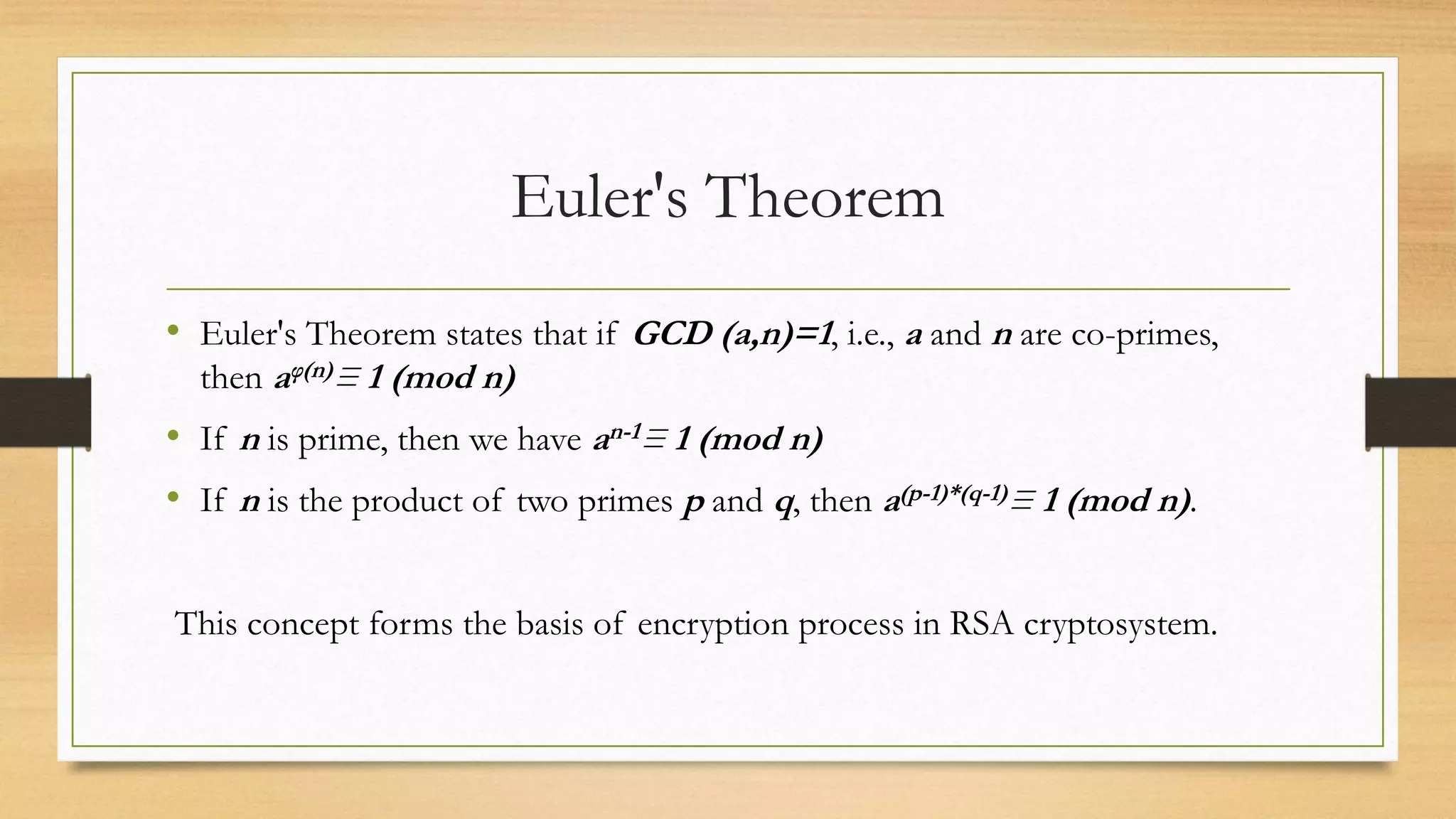
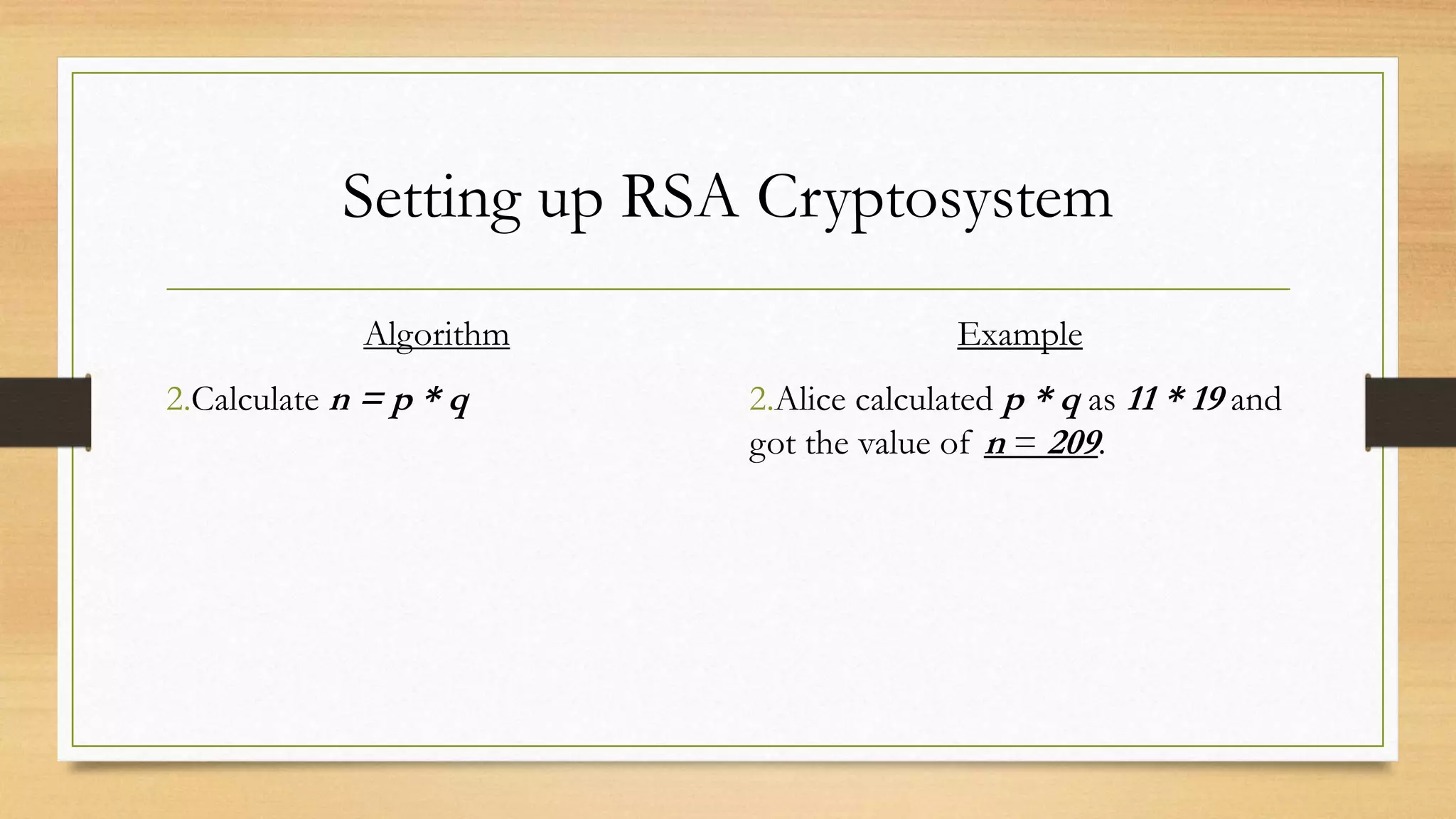
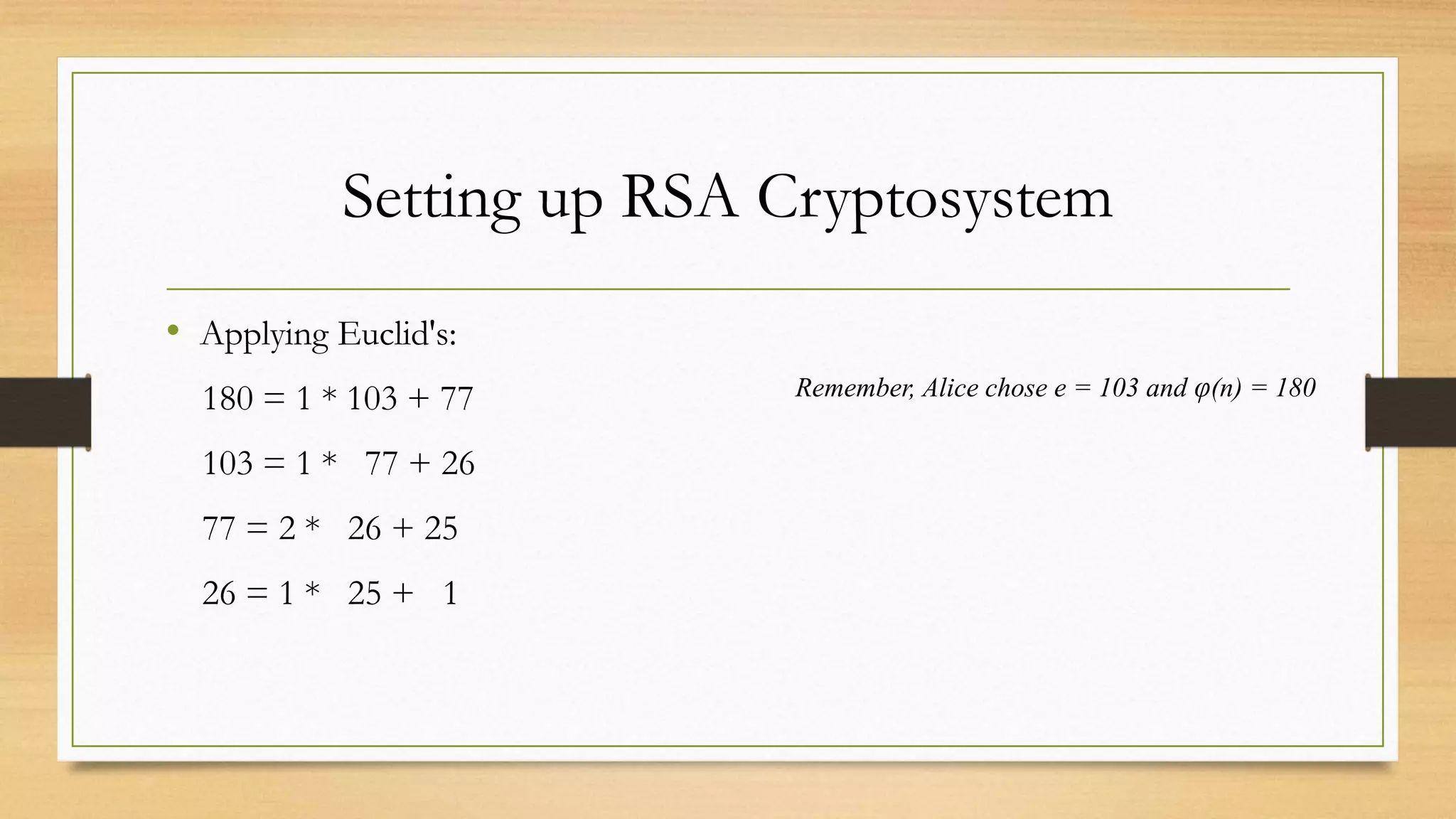
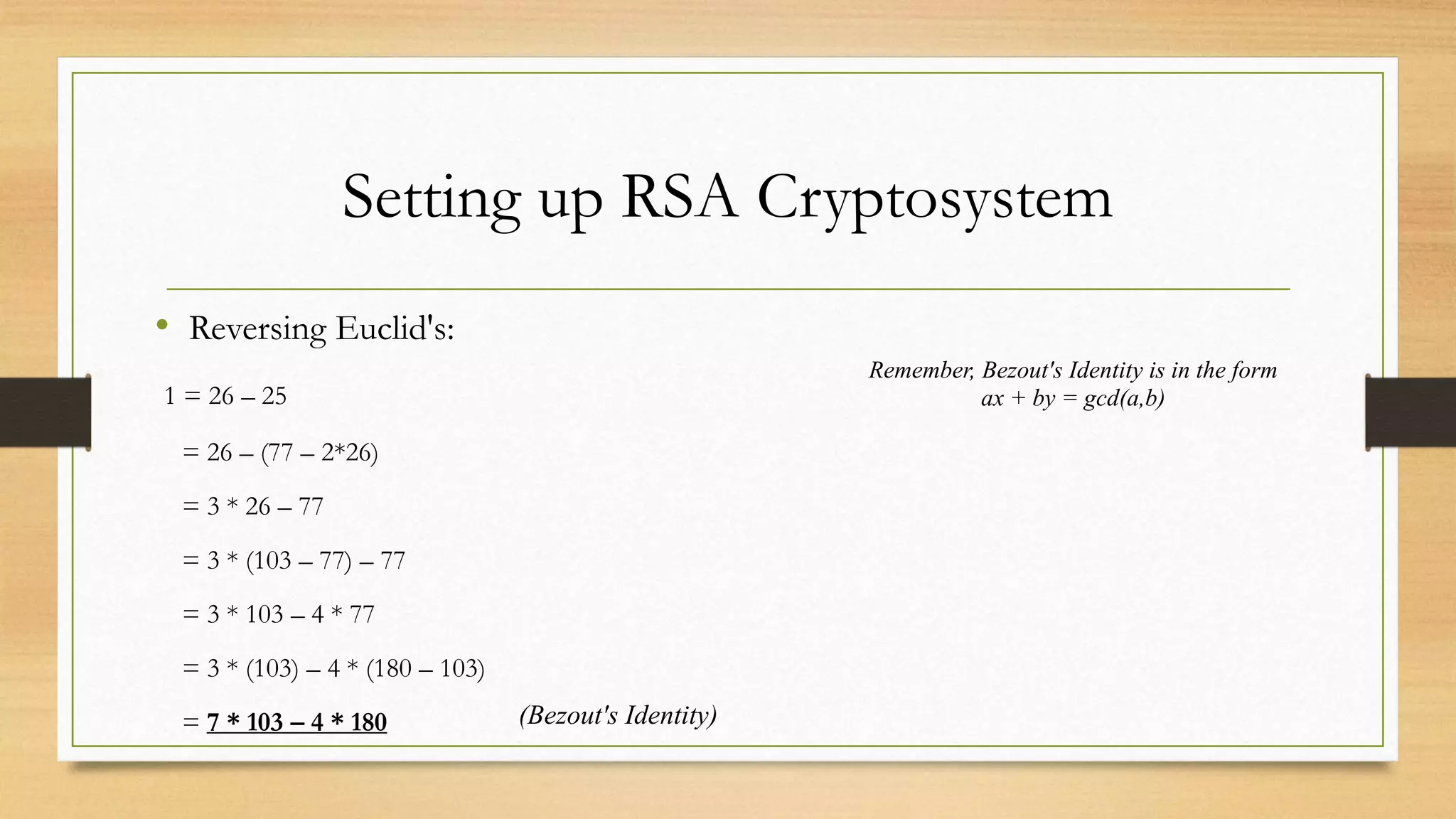
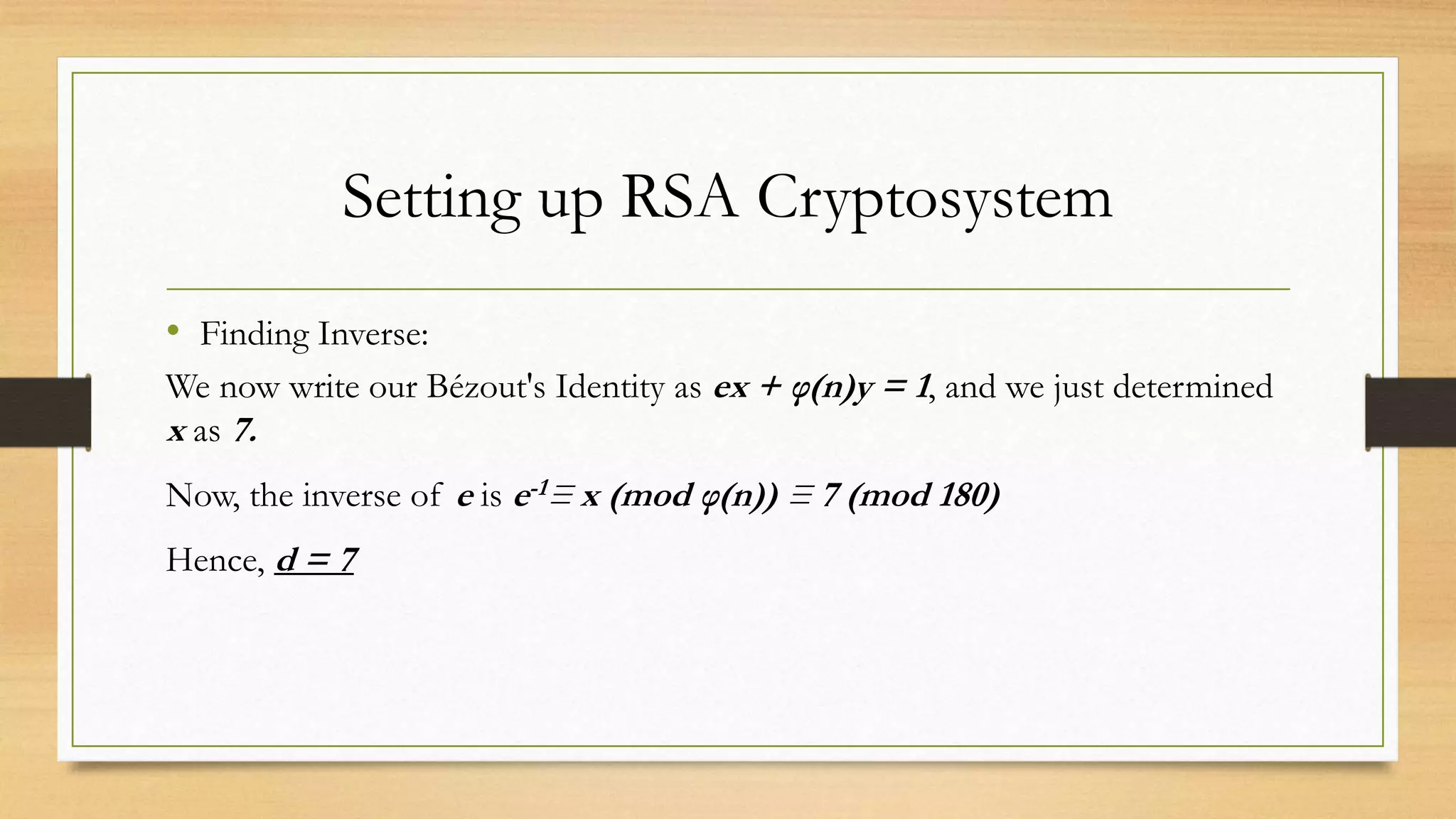
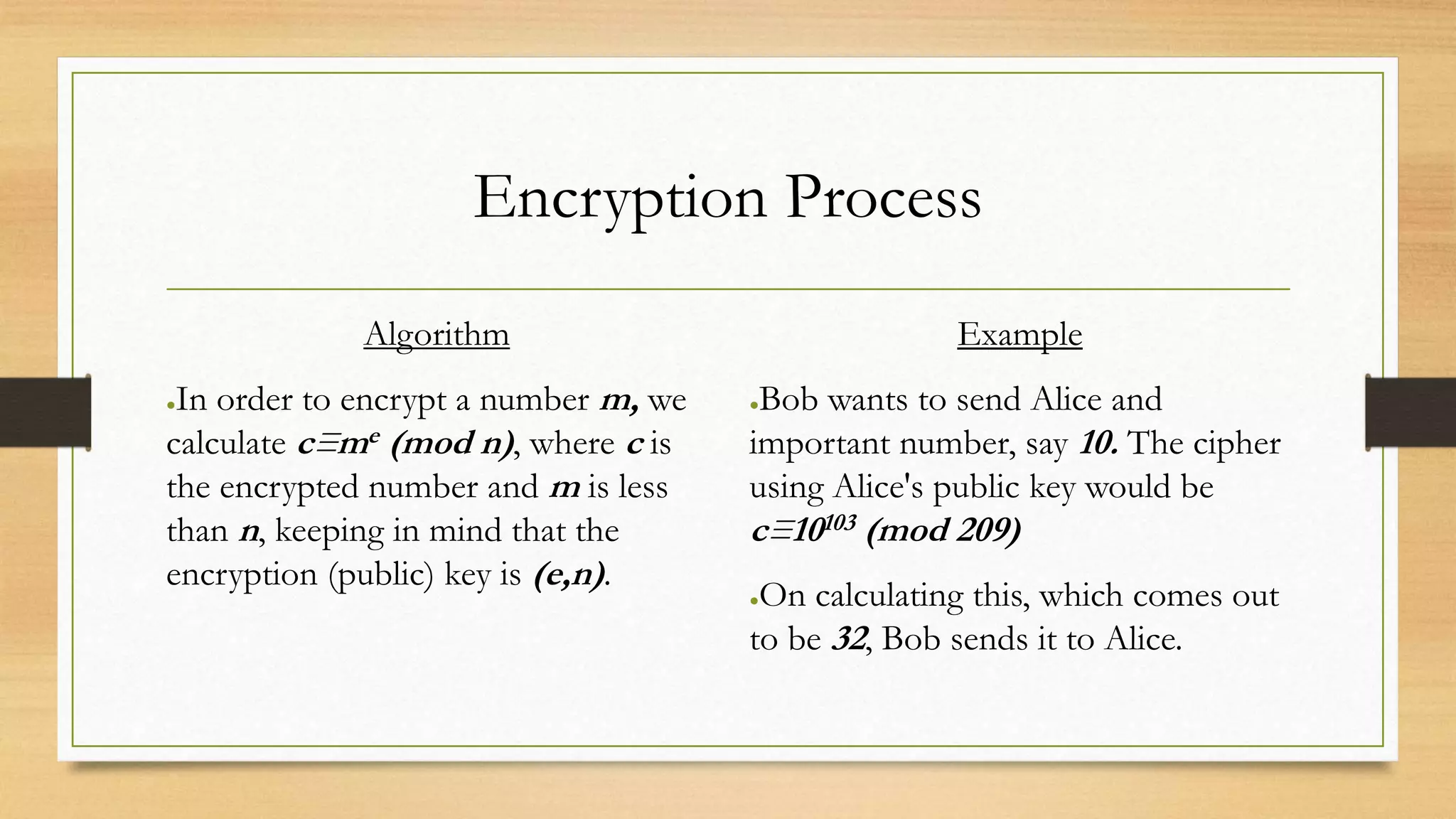
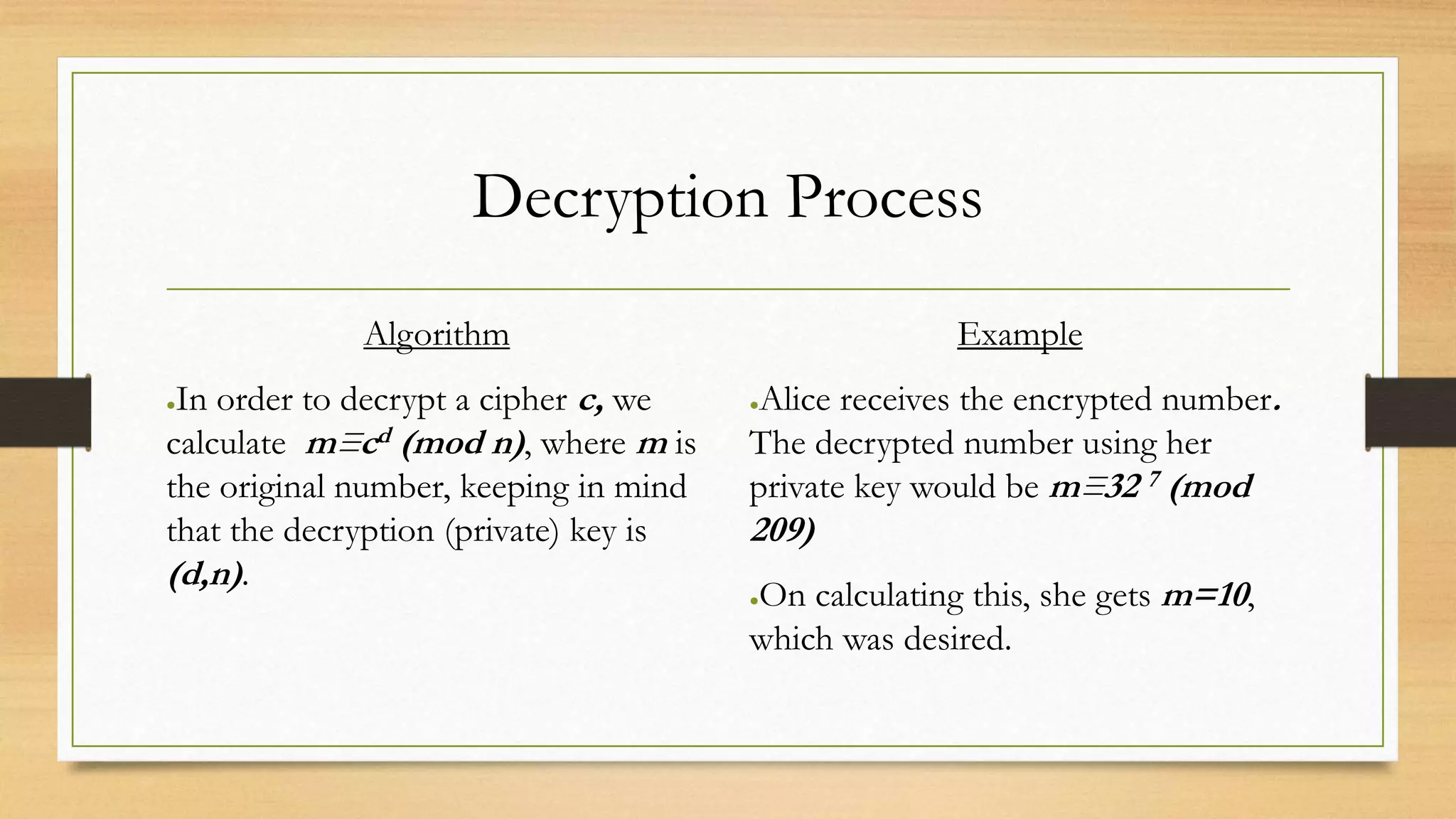
The document covers cryptography and its importance, particularly focusing on the RSA cryptosystem, a public key cryptosystem developed in 1976. It explains the mathematical foundations behind RSA, including Euclid's algorithm, modulo arithmetic, and Euler's theorem, and outlines the process for generating keys and encrypting/decrypting messages. It emphasizes the role of cryptography in securing electronic transactions and communication in modern technology.