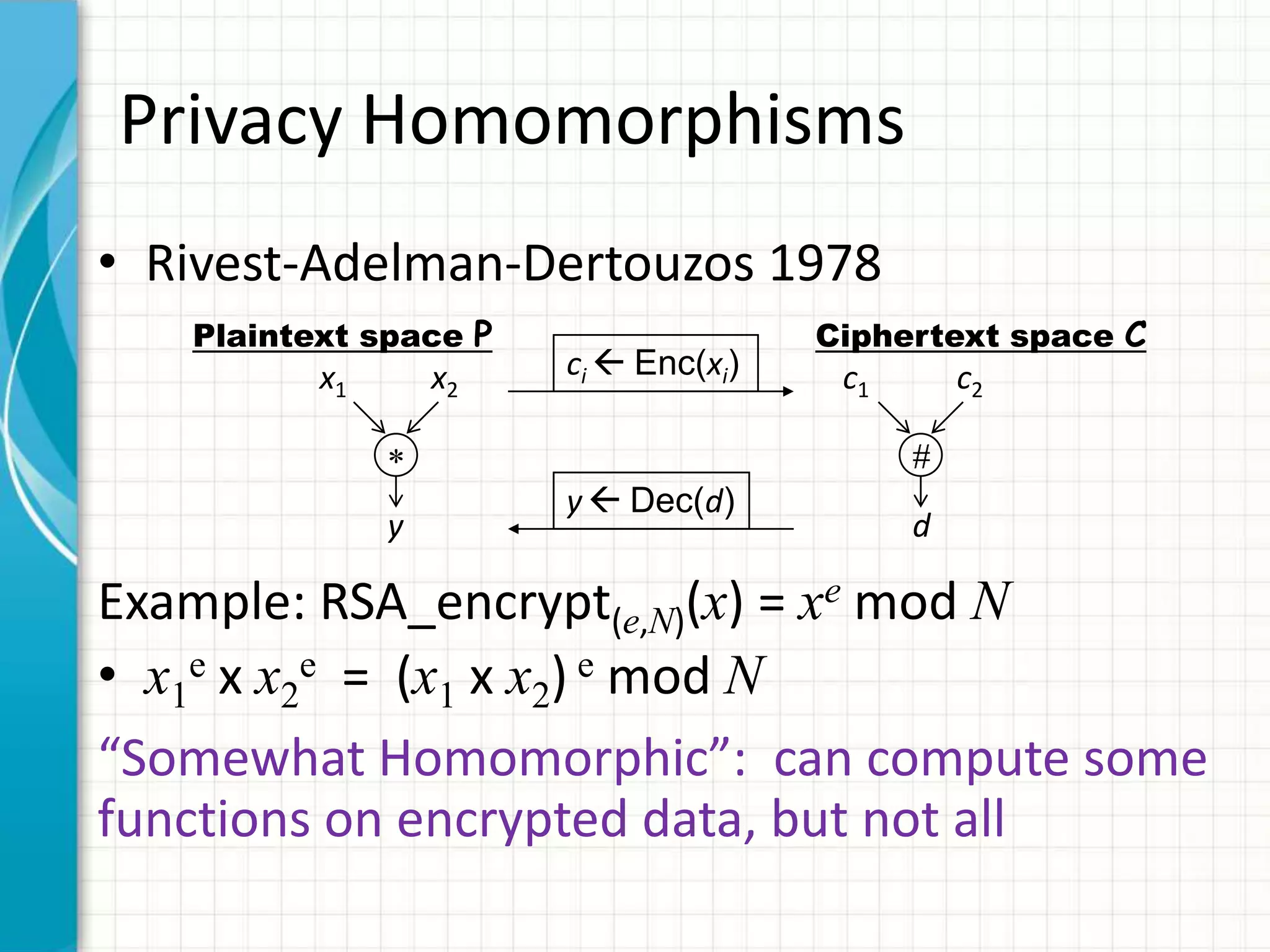
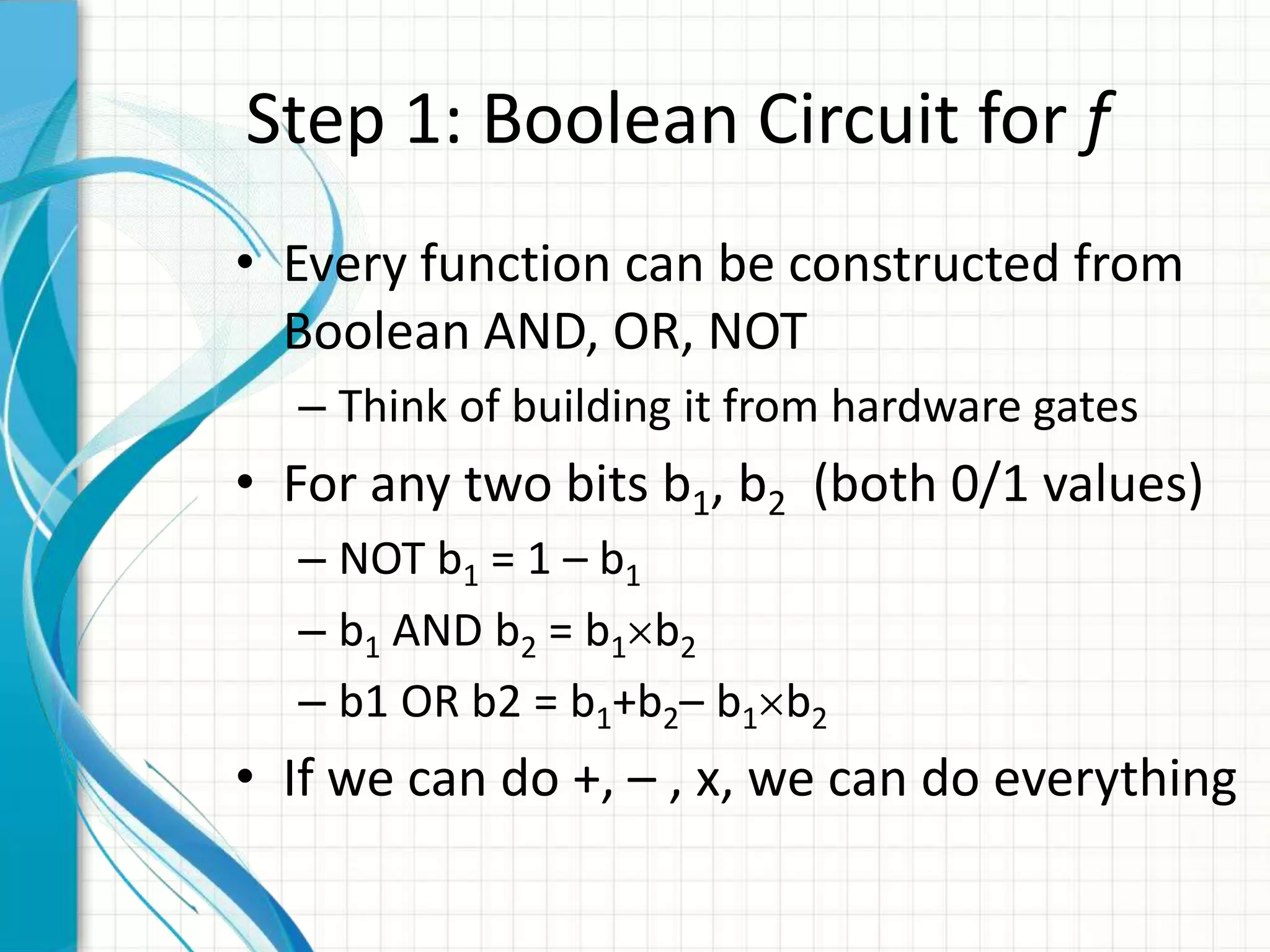
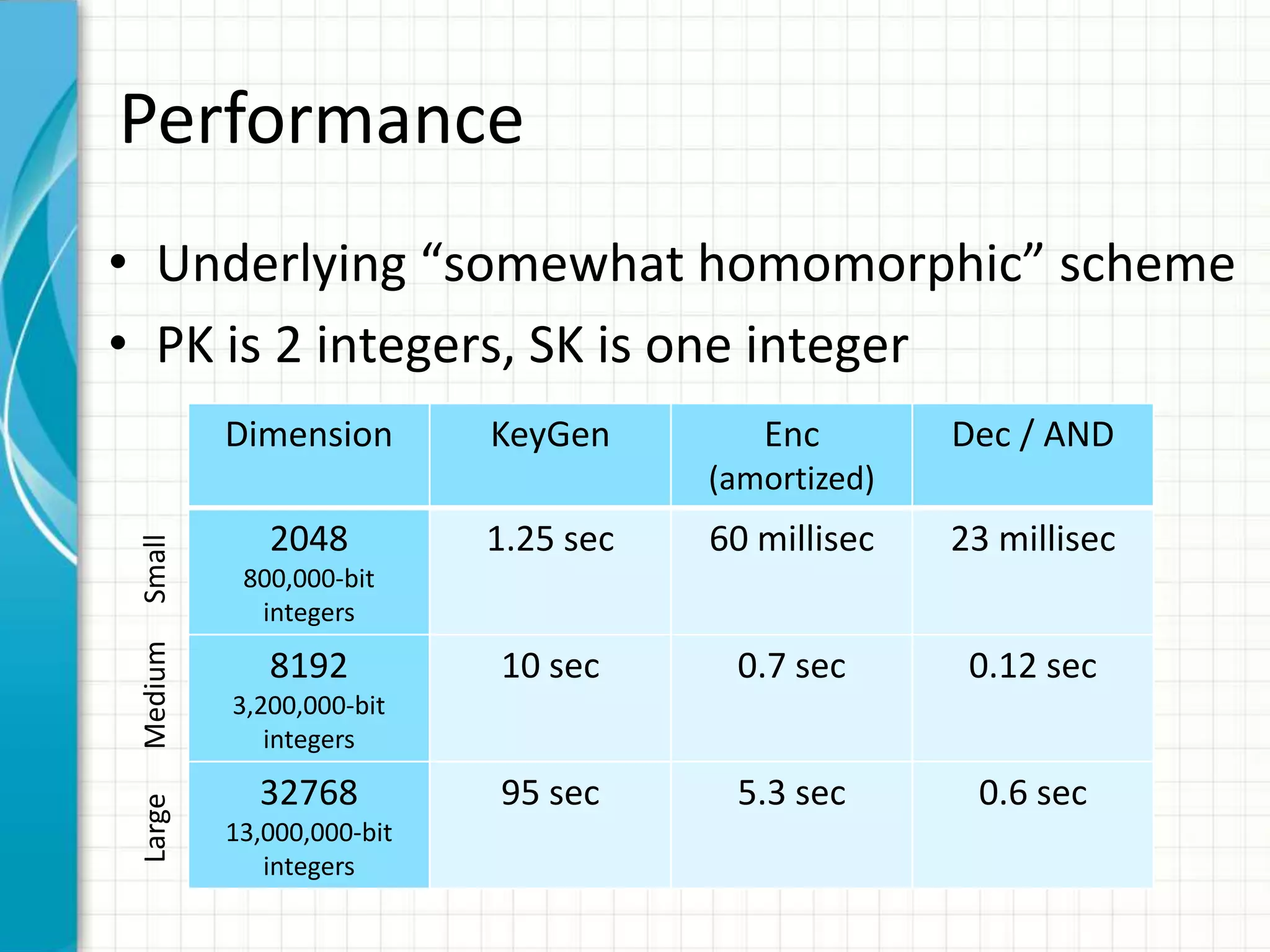
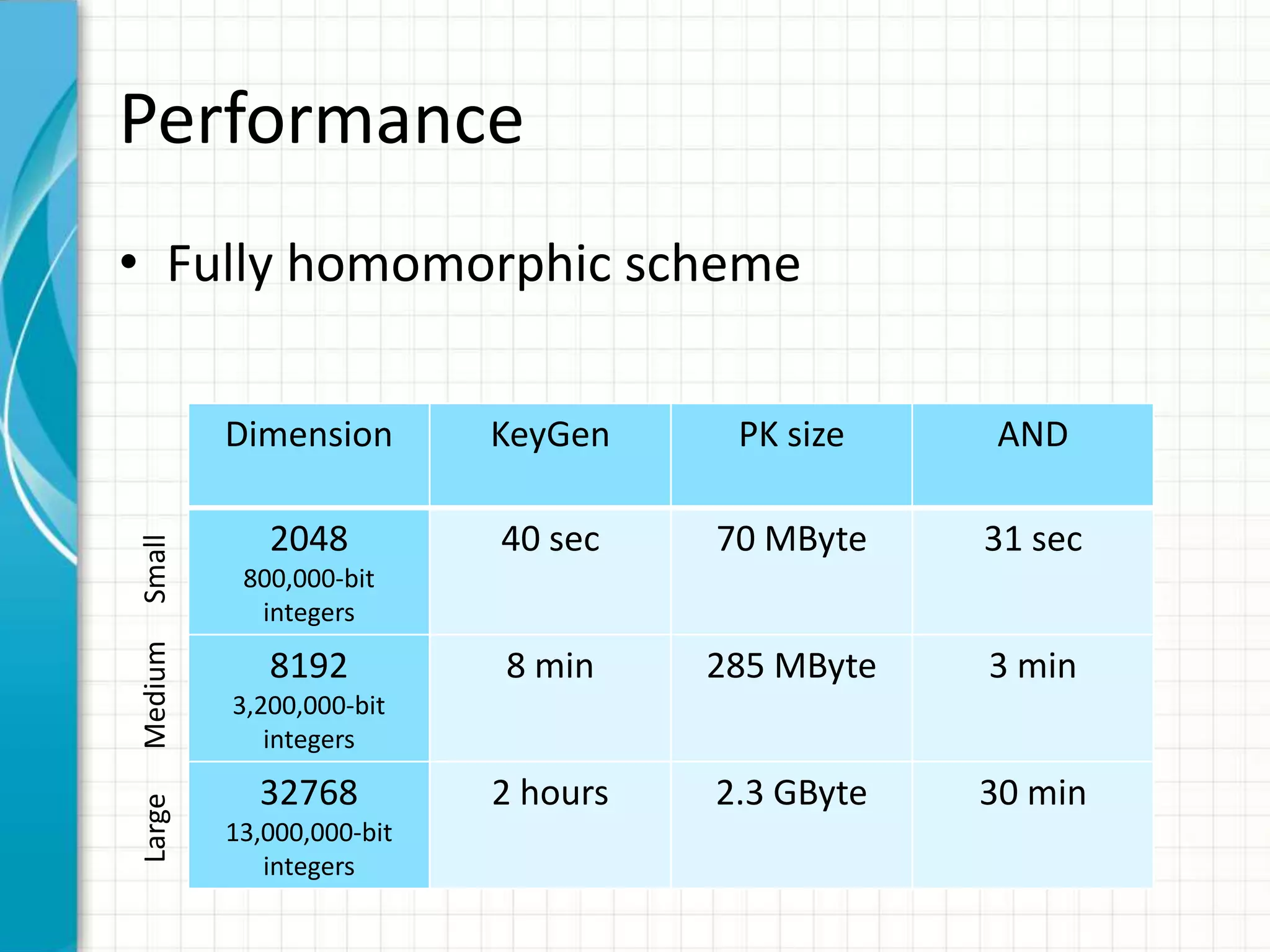
The document discusses the concept of computing on encrypted data, allowing for processing without revealing the data itself. It covers techniques such as homomorphic encryption, which enables the computation of arbitrary functions on encrypted data, and outlines the steps required to achieve this. Challenges related to performance and the practicality of current solutions are also highlighted, with suggestions for potential applications and improvements.


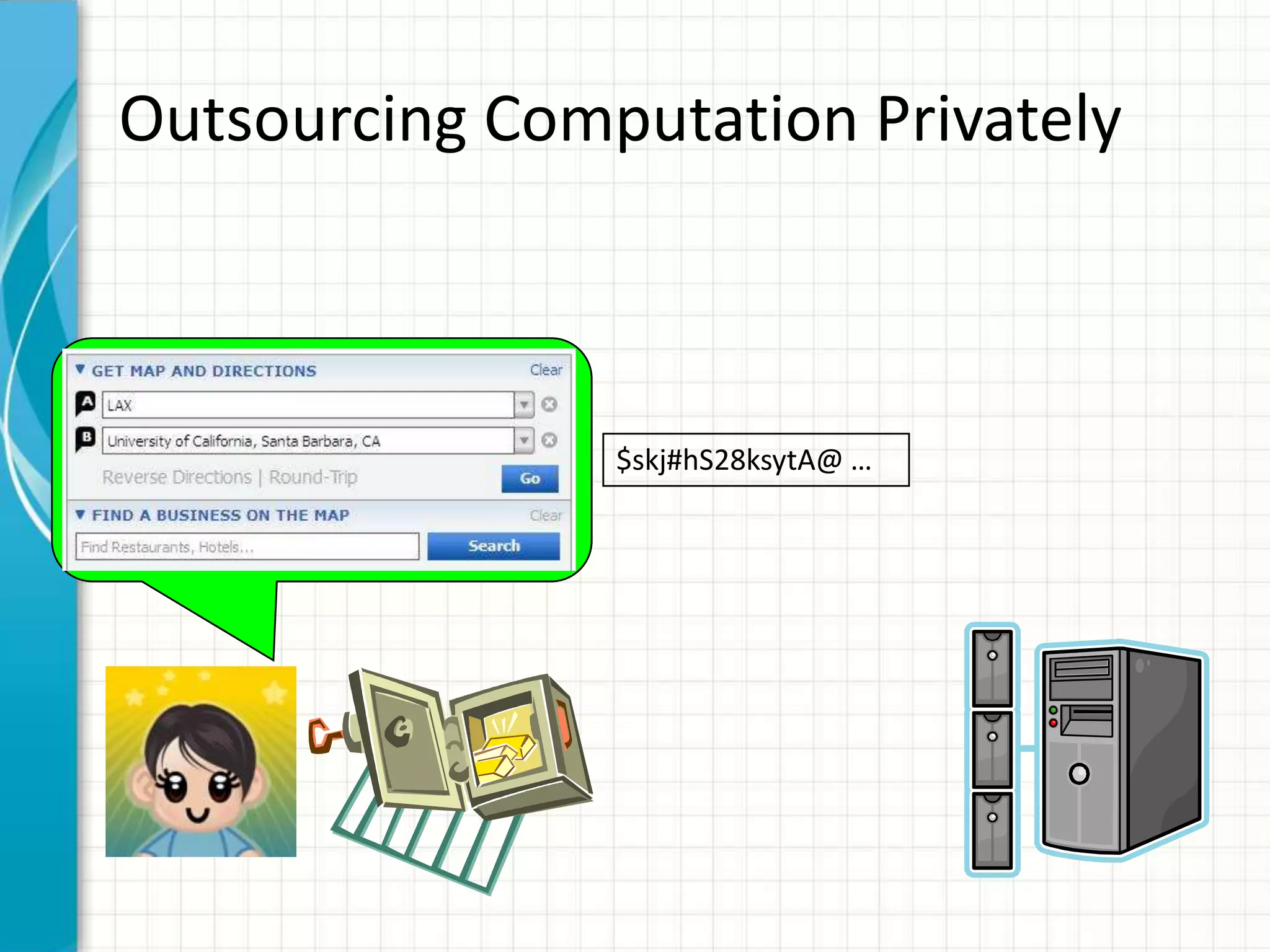
![Outsourcing Computation Privately
“I want to delegate the computation to the cloud,
“I wantthe cloud the computation to the cloud”
but to delegate shouldn’t see my input”
Enc(x) f
Enc[f(x)]
Client Server/Cloud
(Input: x) (Function: f)](https://image.slidesharecdn.com/computingonencrypteddata-120110095125-phpapp02/75/Computing-on-Encrypted-Data-5-2048.jpg)
![Outsourcing Computation Privately
$kjh9*mslt@na0
&maXxjq02bflx
m^00a2nm5,A4.
pE.abxp3m58bsa
(3saM%w,snanba
nq~mD=3akm2,A
Z,ltnhde83|3mz{n
dewiunb4]gnbTa*
kjew^bwJ^mdns0](https://image.slidesharecdn.com/computingonencrypteddata-120110095125-phpapp02/75/Computing-on-Encrypted-Data-7-2048.jpg)
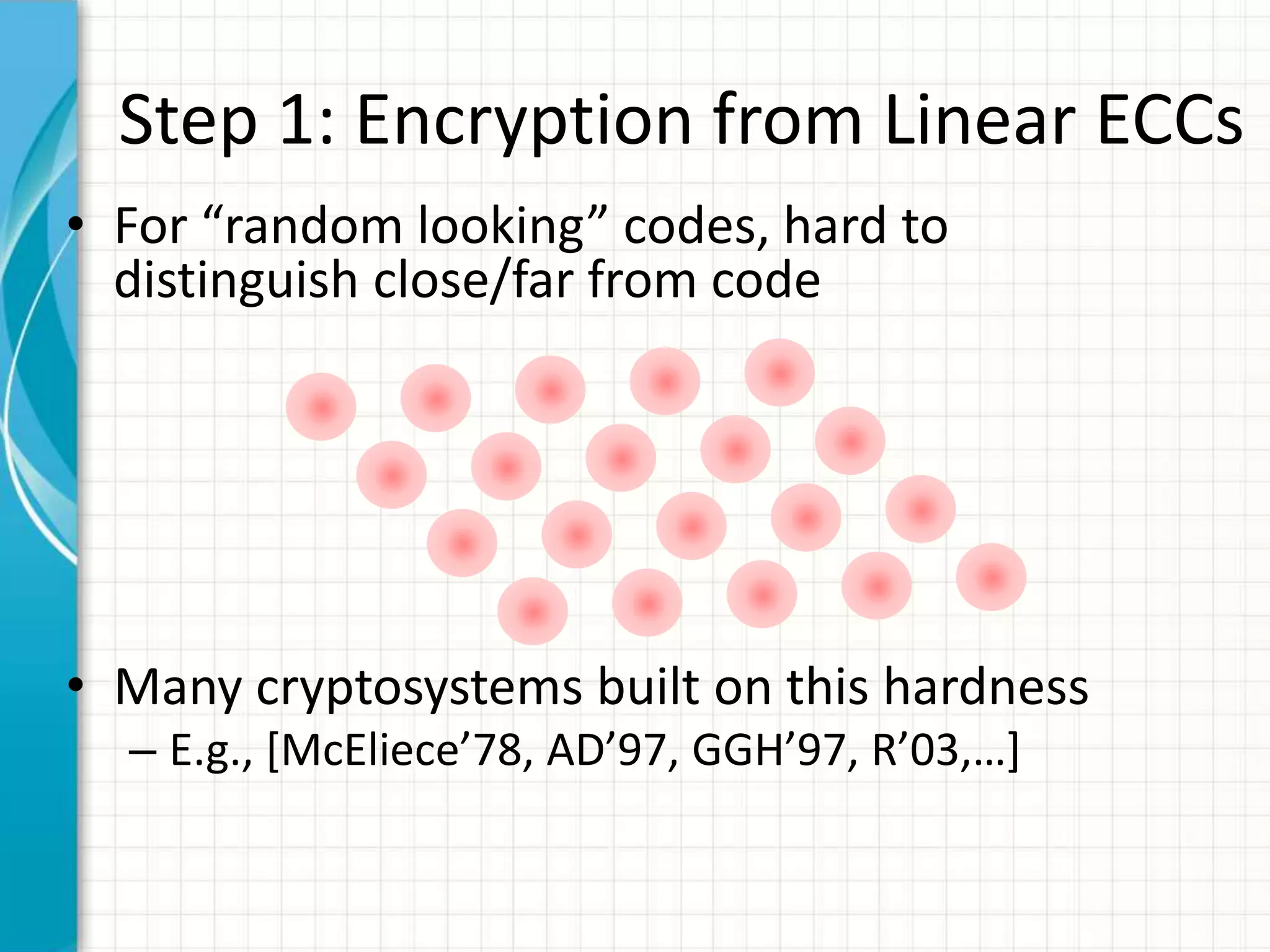
![“Fully Homomorphic” Encryption
• Encryption for which we can compute arbitrary
functions on the encrypted data
Enc(x) Eval f
Enc(f(x))
• Another example: private information retrieval
i Enc(i) A[1 … n]
Enc(A[i])](https://image.slidesharecdn.com/computingonencrypteddata-120110095125-phpapp02/75/Computing-on-Encrypted-Data-9-2048.jpg)







![The [Gentry 2009] blueprint
Evaluate any function in four “easy” steps
• Step 1: Encryption from linear ECCs
– Additive homomorphism Error-Correcting Codes
• Step 2: ECC lives inside a ring
– Also multiplicative homomorphism
– But only for a few operations (low-degree poly’s)
• Step 3: Bootstrapping
– Few ops (but not too few) any number of ops
• Step 4: Everything else
– “Squashing” and other fun activities](https://image.slidesharecdn.com/computingonencrypteddata-120110095125-phpapp02/75/Computing-on-Encrypted-Data-24-2048.jpg)

![Example: Integers mod p [vDGHV 2010]
p N
• Code determined by a secret integer p
– Codewords: multiples of p
• Good representation: p itself
• Bad representation: ri << p
– N = pq, and also many xi = pqi + ri
• Enc(0): subset-sum(xi’s)+r mod N
– r is new noise, chosen by encryptor
• Enc(1): random integer mod N](https://image.slidesharecdn.com/computingonencrypteddata-120110095125-phpapp02/75/Computing-on-Encrypted-Data-27-2048.jpg)
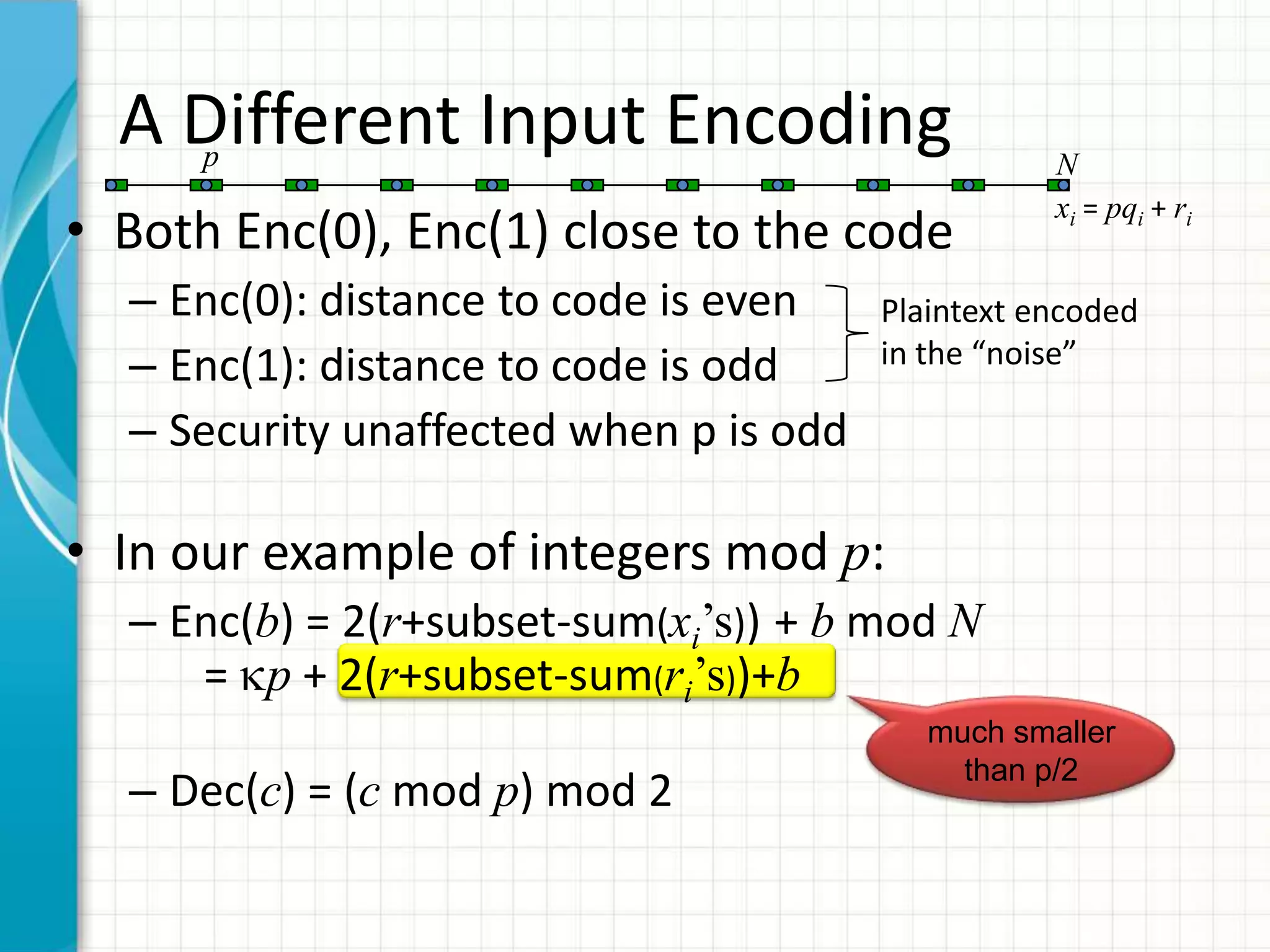
![Example: Integers mod p [vDGHV 2010]
p N
xi = pqi + ri
• Secret-key is p, public-key is N and the xi’s
• ci = Encpk(bi) = 2(r+subset-sum(xi’s)) + b mod N
= kip + 2ri+bi
– Decsk(ci) = (ci mod p) mod 2
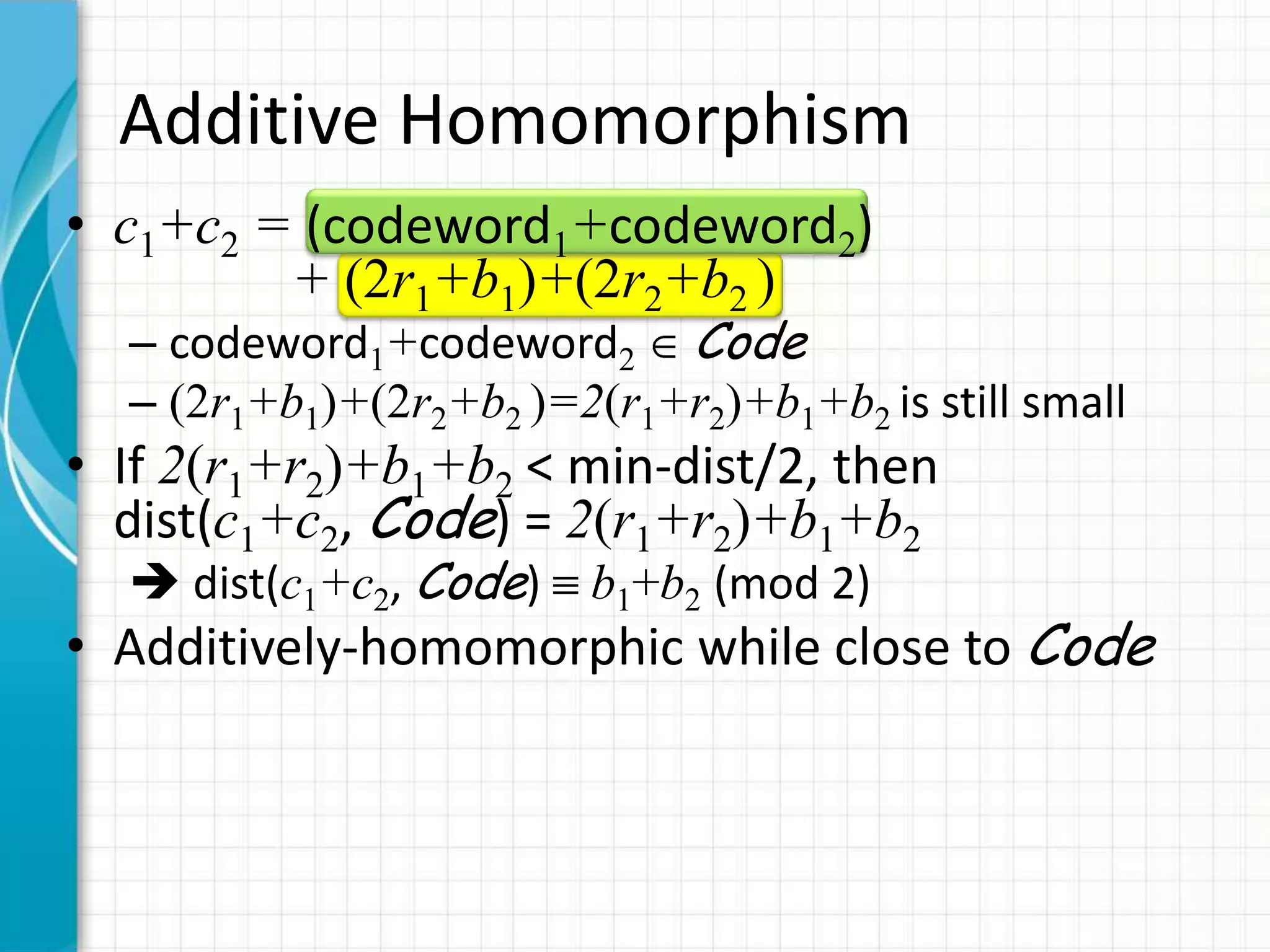
• c1+c2 mod N = (k1p+2r1+b1)+(k2p+2r2+b2) – kqp
= k’p + 2(r1+r2) + (b1+b2)
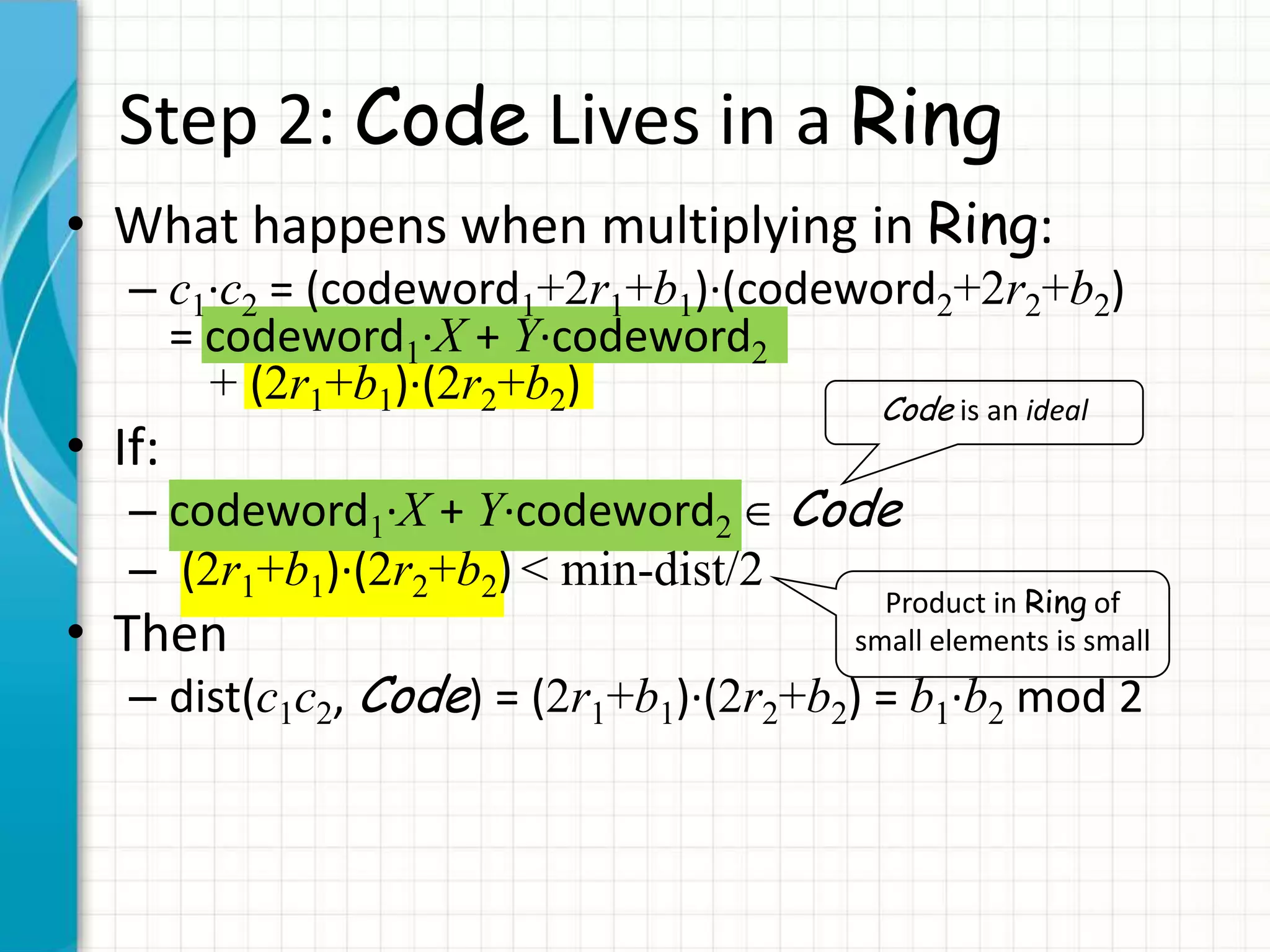
• c1c2 mod N = (k1p+2r1+b1)(k2p+2r2+b2) – kqp
= k’p + 2(2r1r2+r1b2+r2b1)+b1b2
• Additive, multiplicative homomorphism
– As long as noise < p/2](https://image.slidesharecdn.com/computingonencrypteddata-120110095125-phpapp02/75/Computing-on-Encrypted-Data-31-2048.jpg)
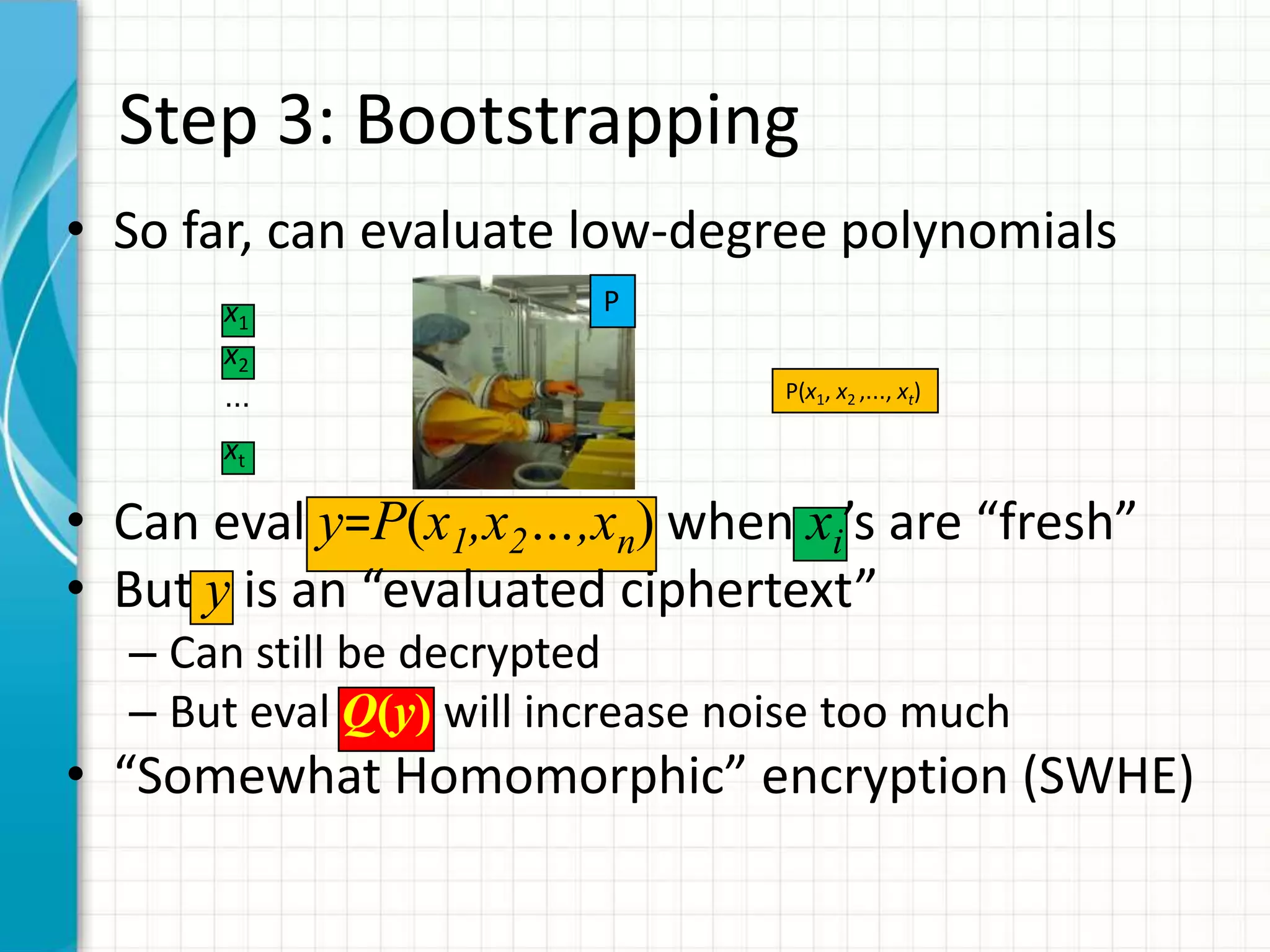
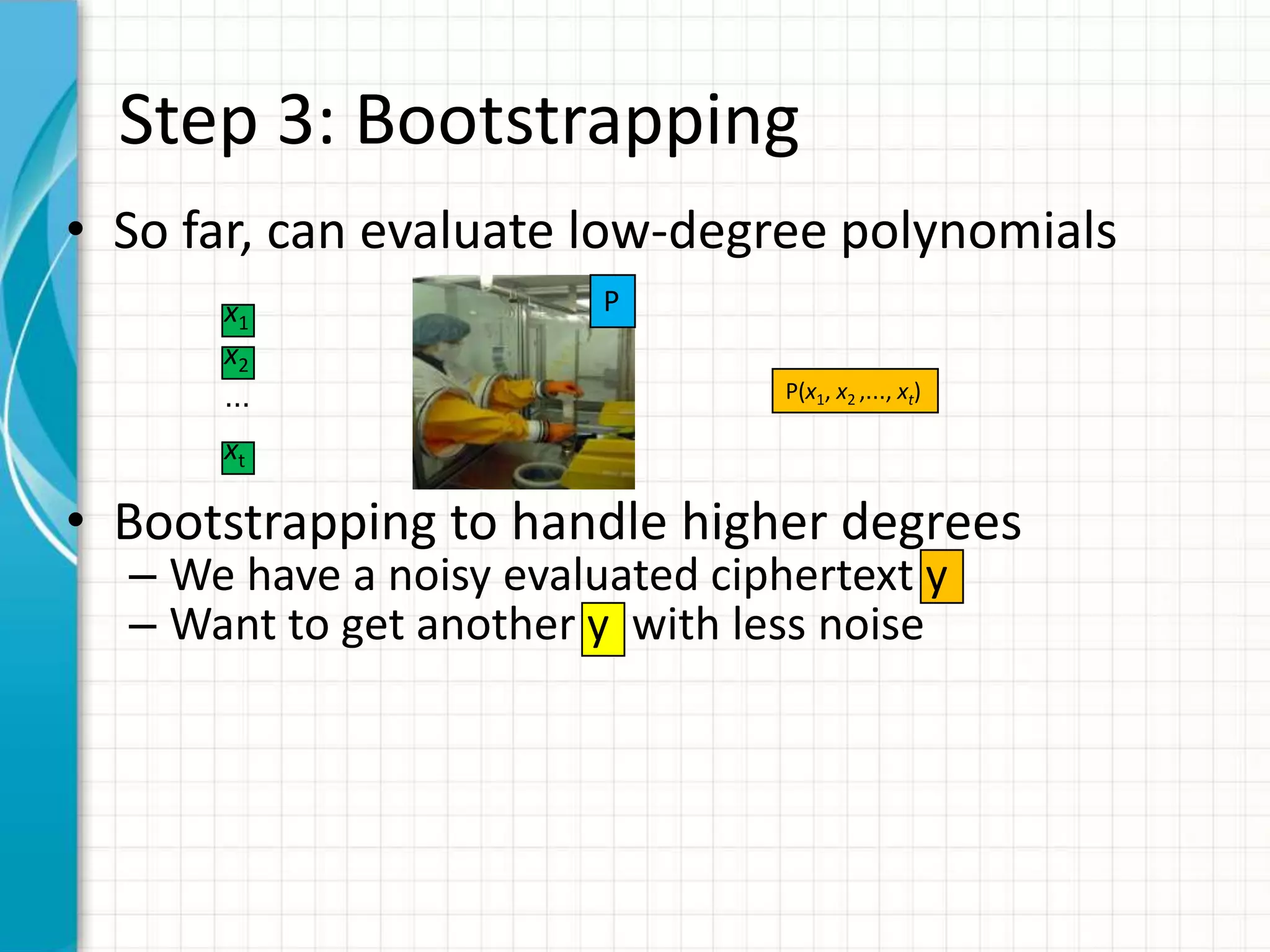
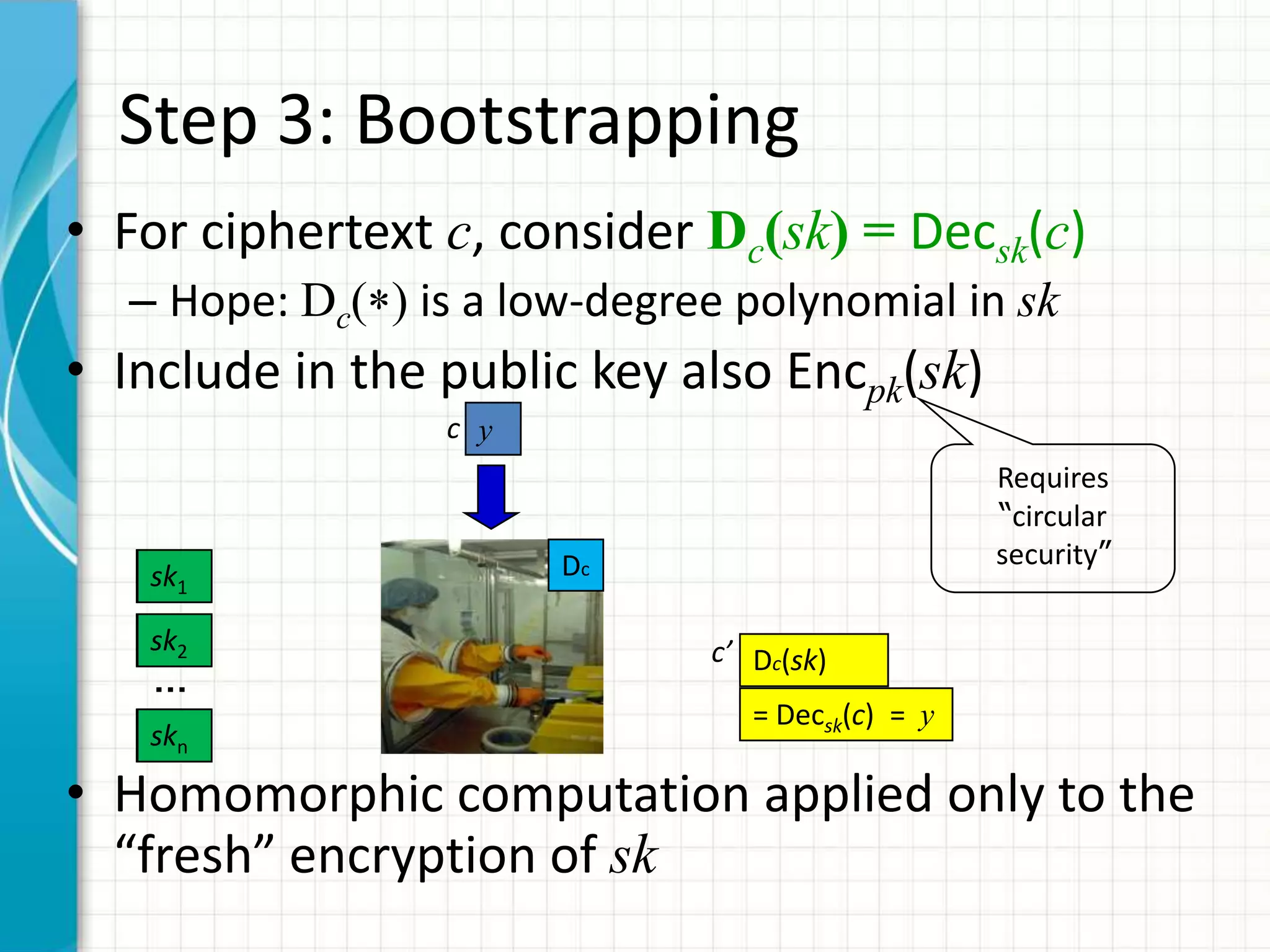
![Step 4: Everything Else
• Cryptosystems from *G’09, vDGHV’10, BG’11a]
cannot handle their own decryption
• Tricks to “squash” the decryption
procedure, making it low-degree
– Nontrivial, requires putting more information
about the secret key in the public key
– Requires yet another assumption, namely hardness
of the Sparse-Subset-Sum Problem (SSSP)
– I will not talk about squashing here](https://image.slidesharecdn.com/computingonencrypteddata-120110095125-phpapp02/75/Computing-on-Encrypted-Data-38-2048.jpg)