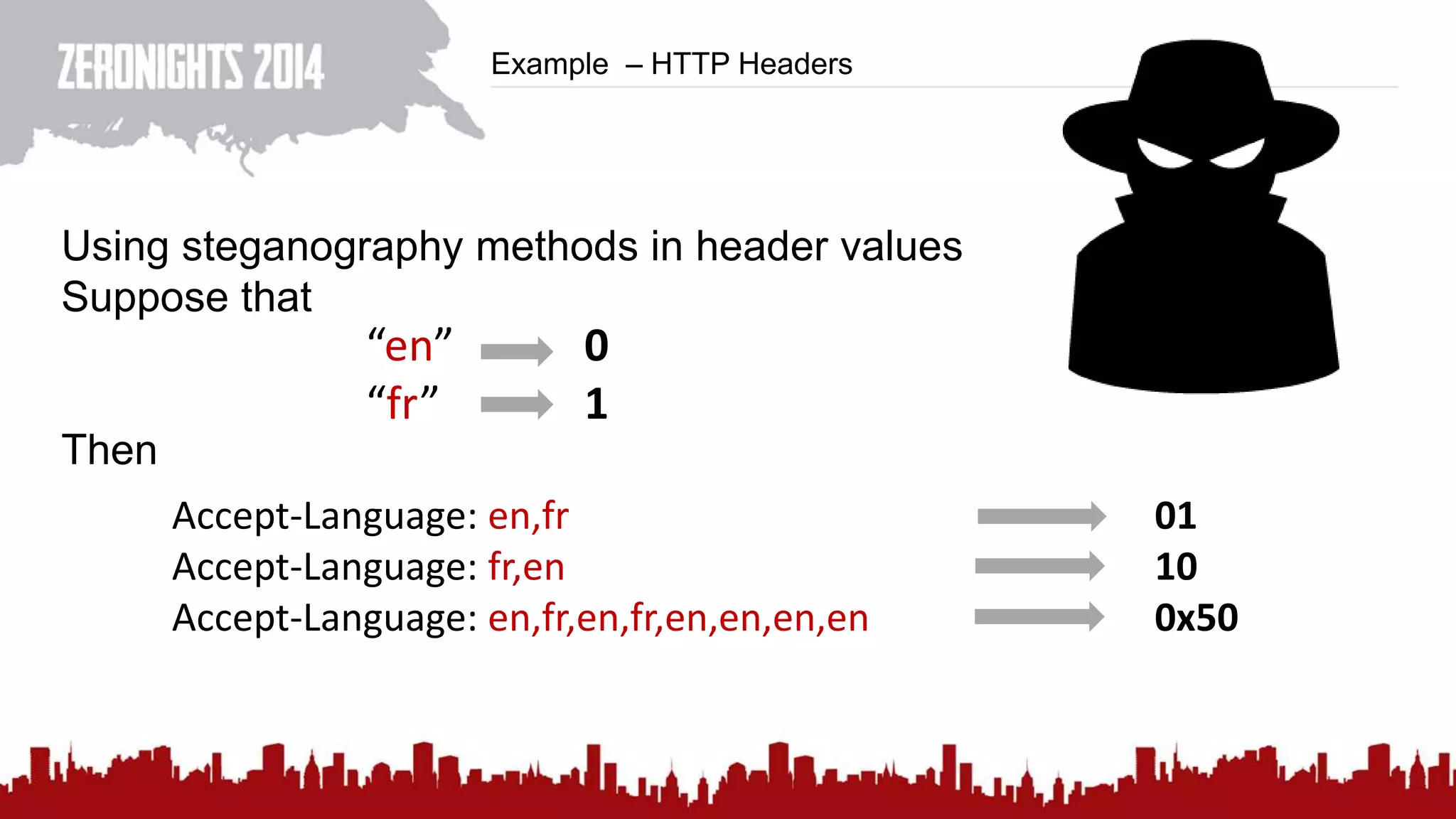
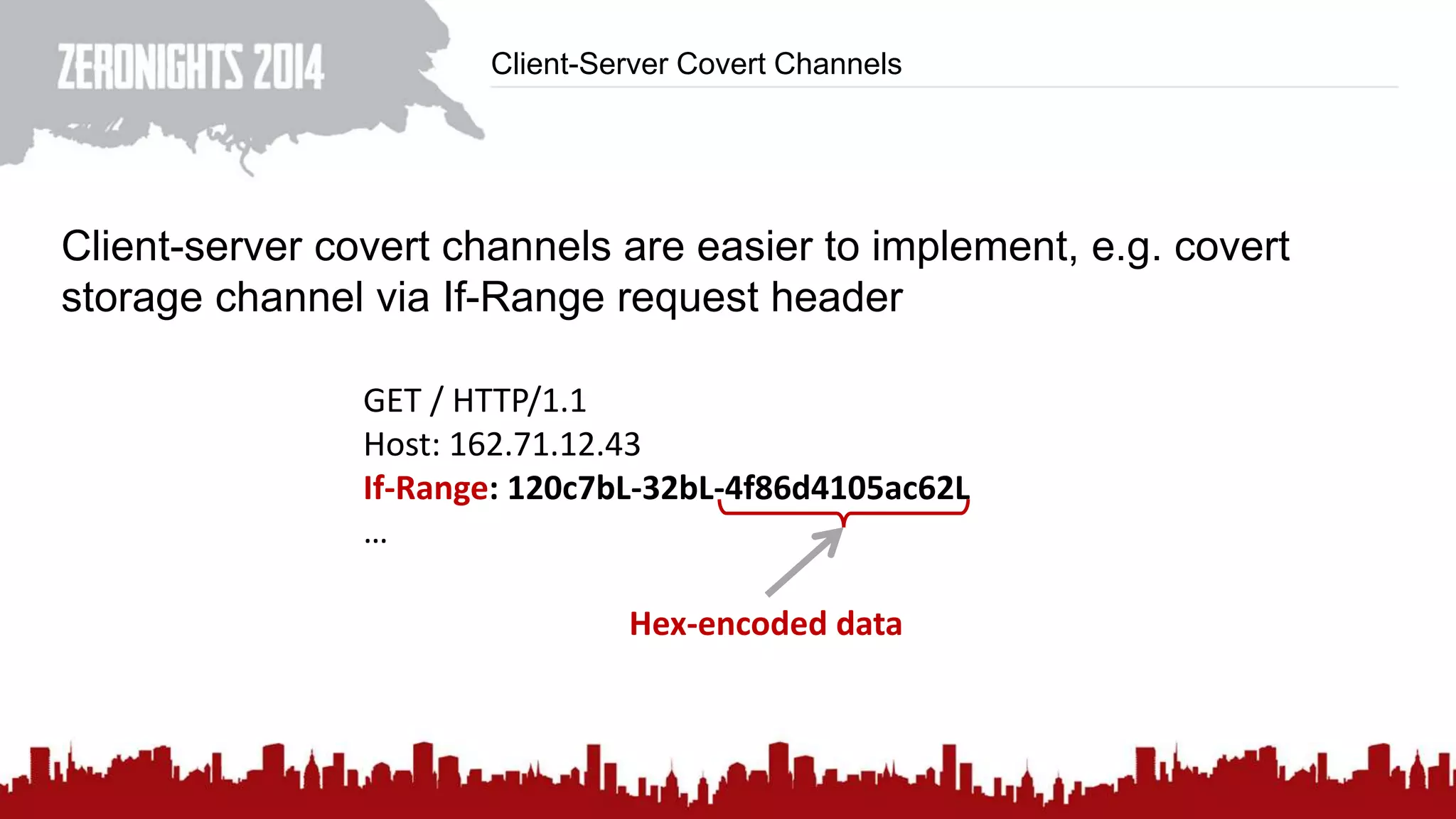
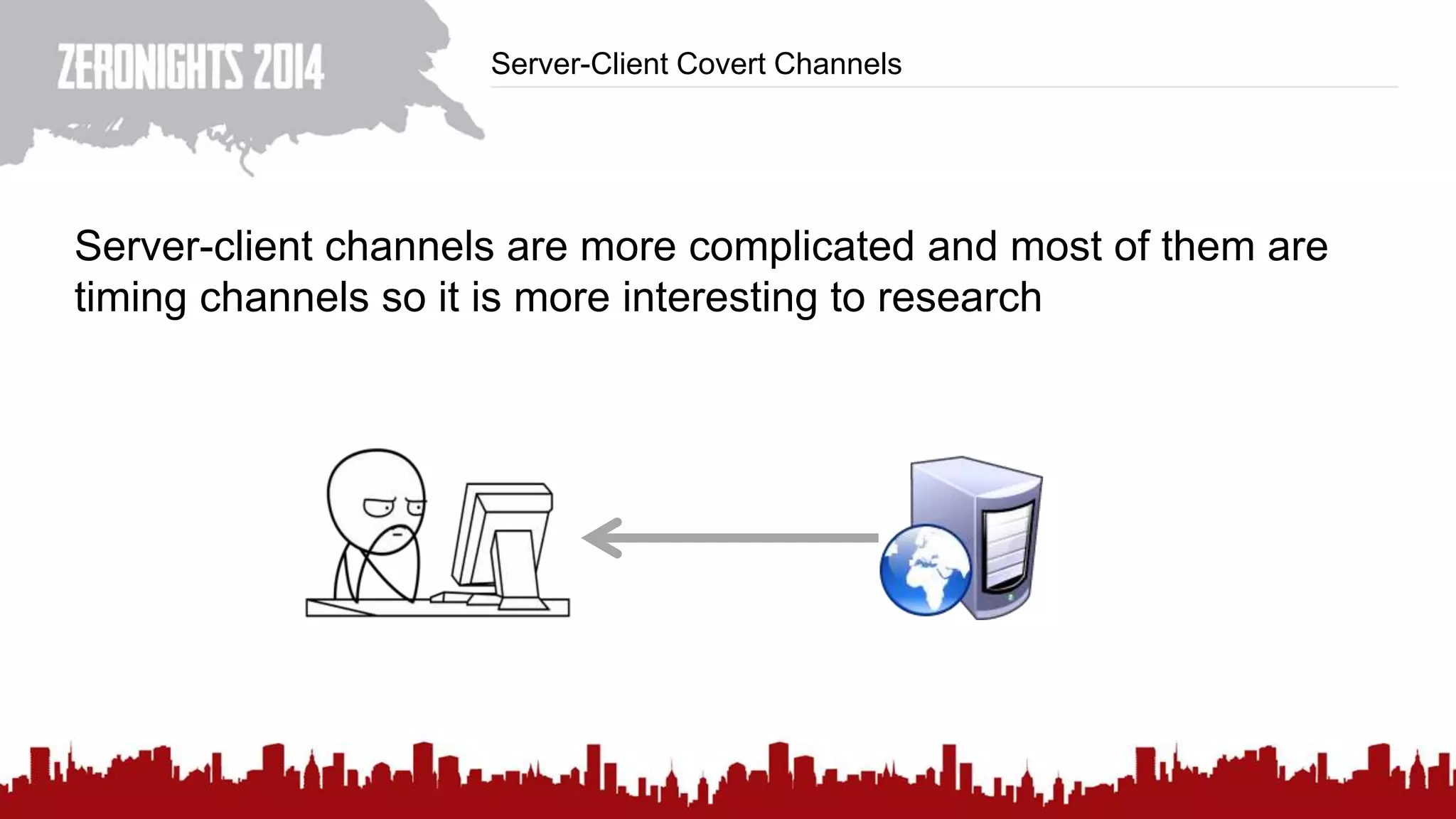
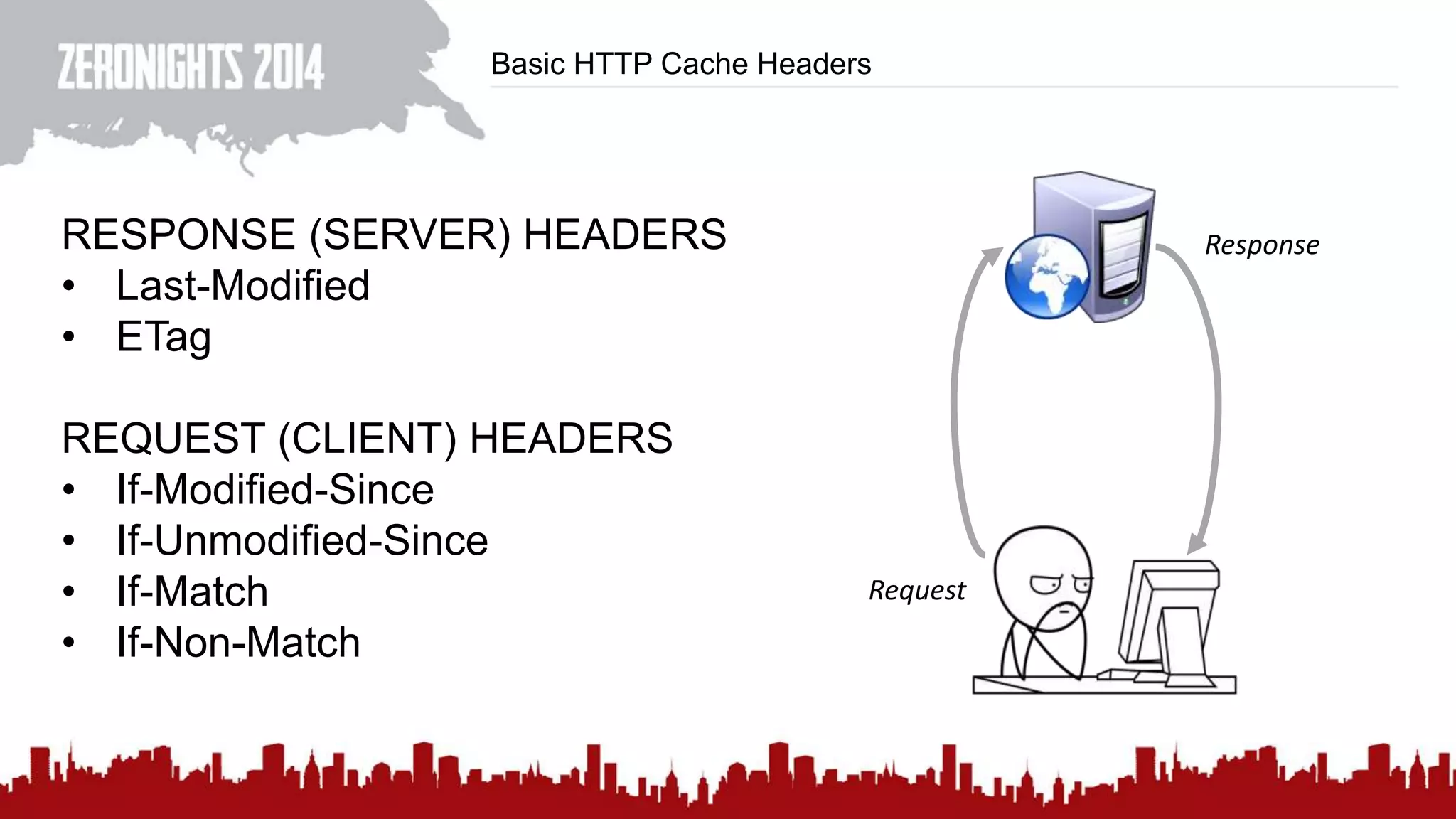
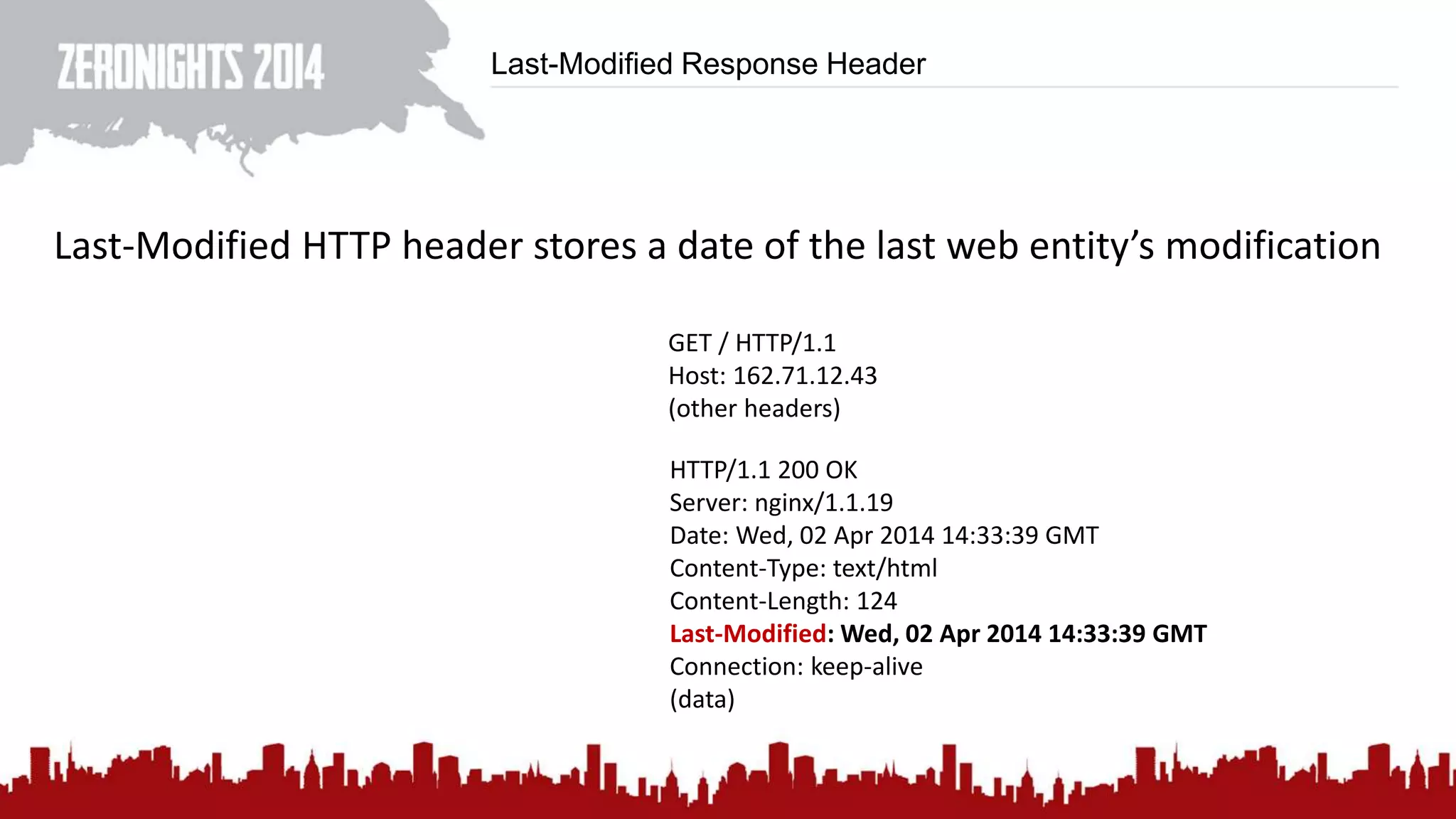
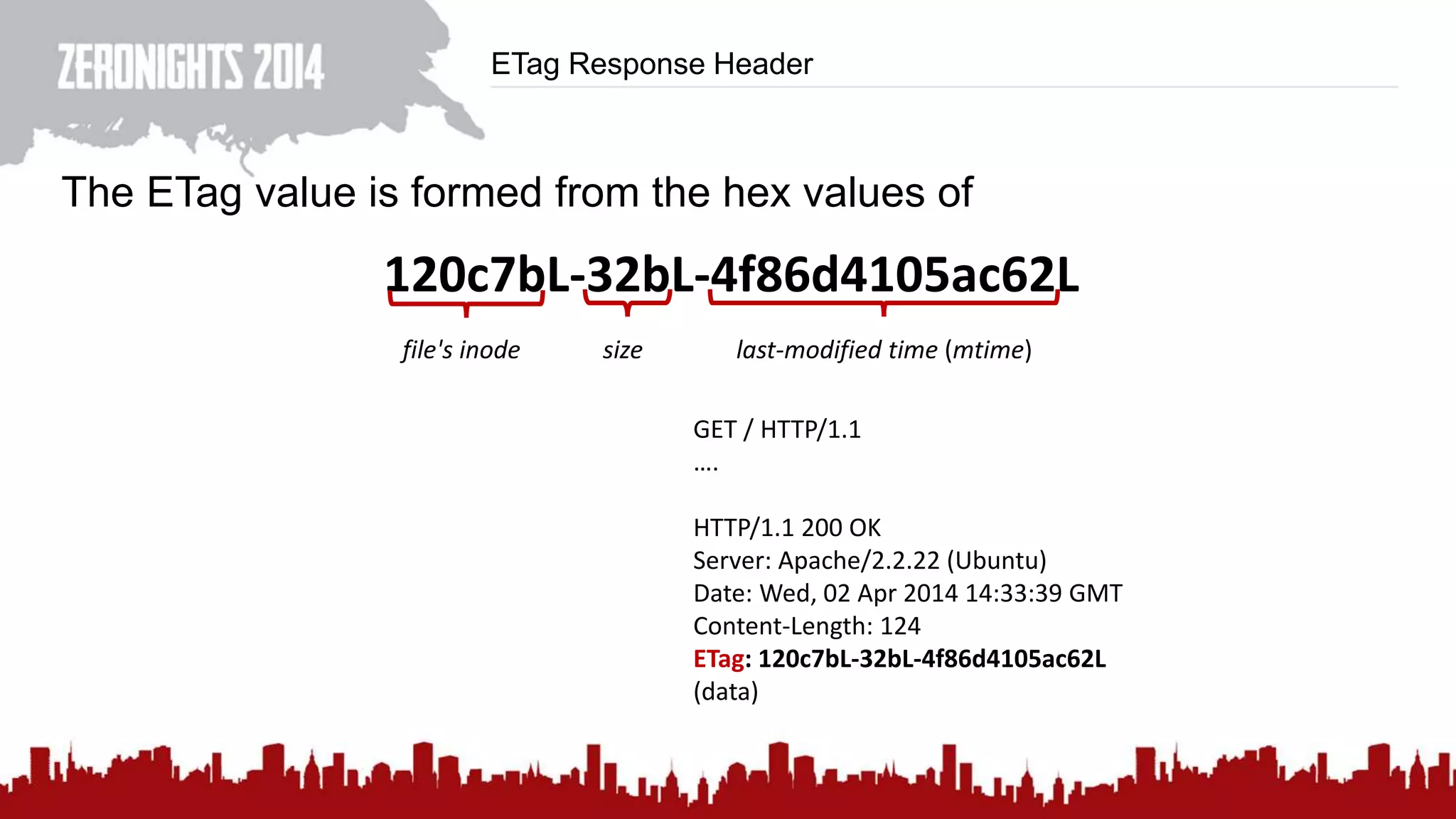
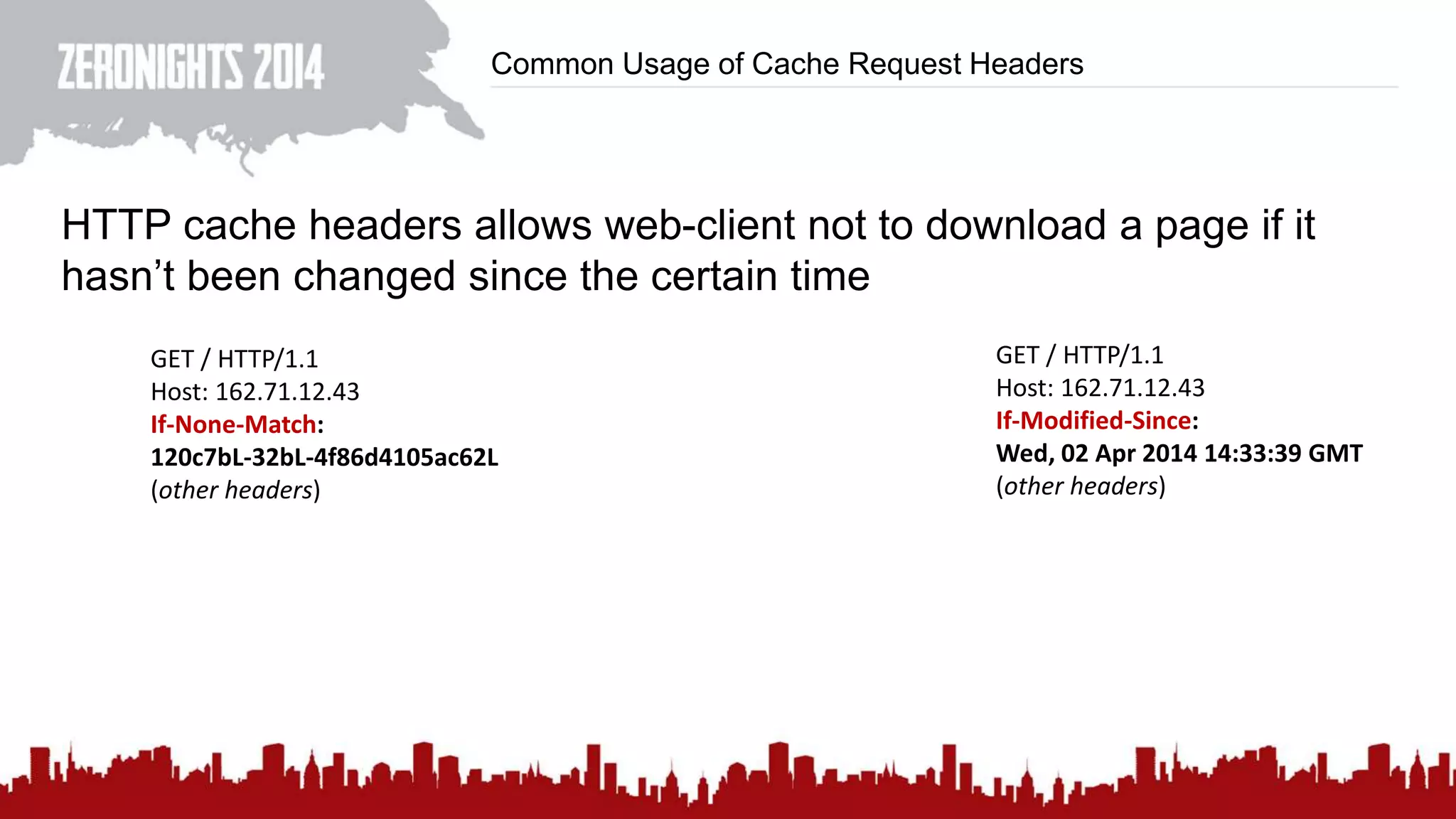
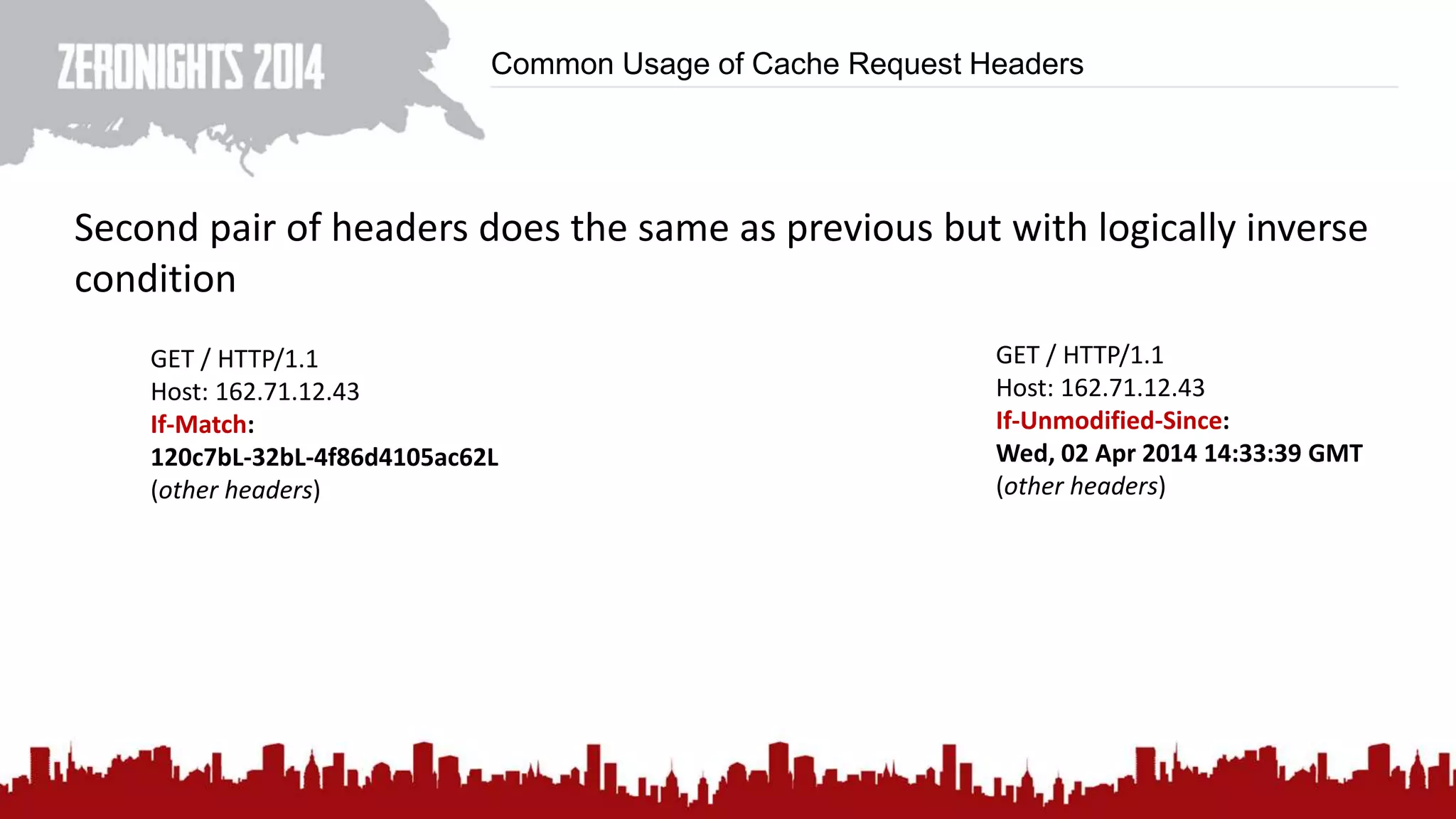
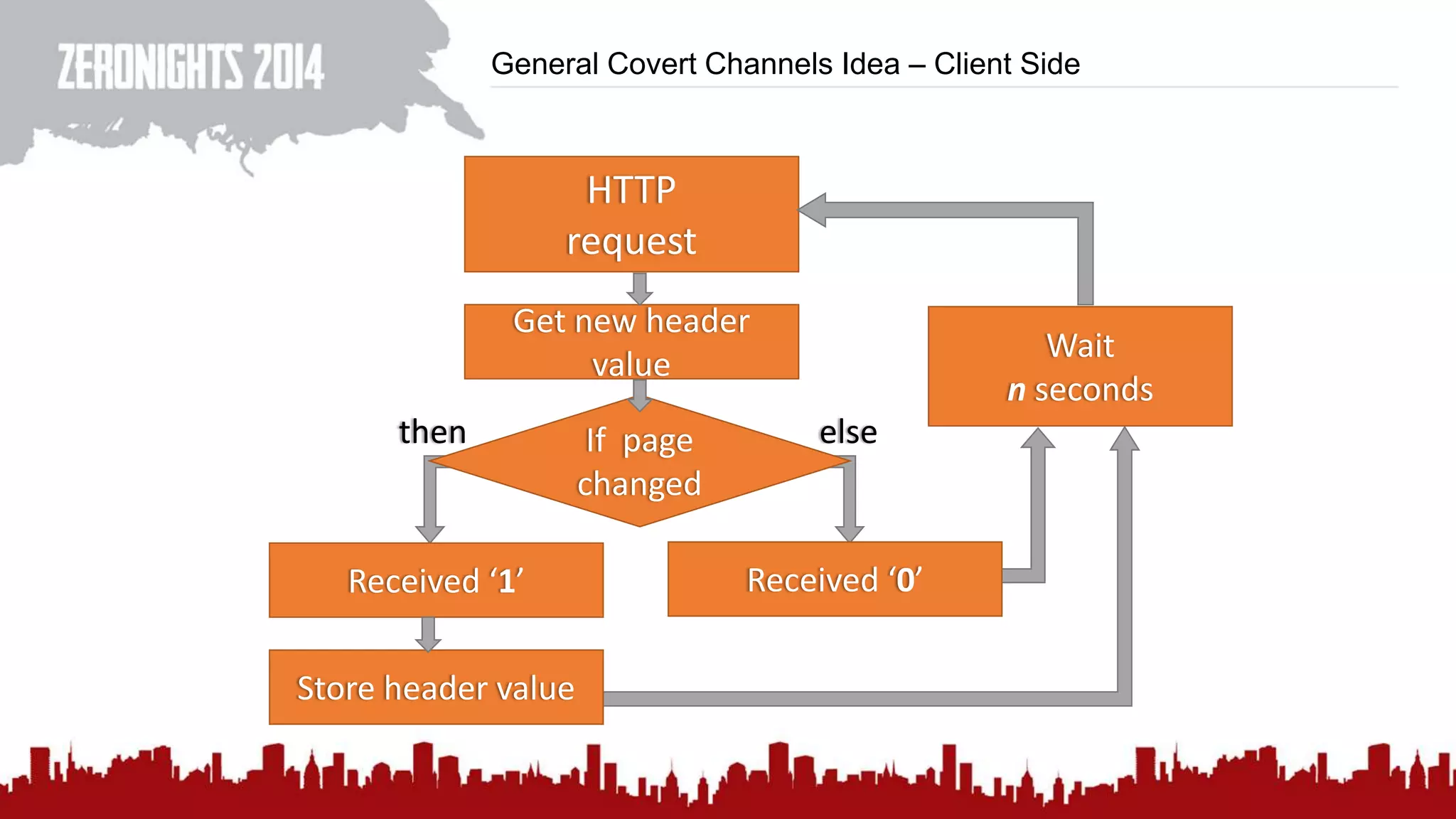
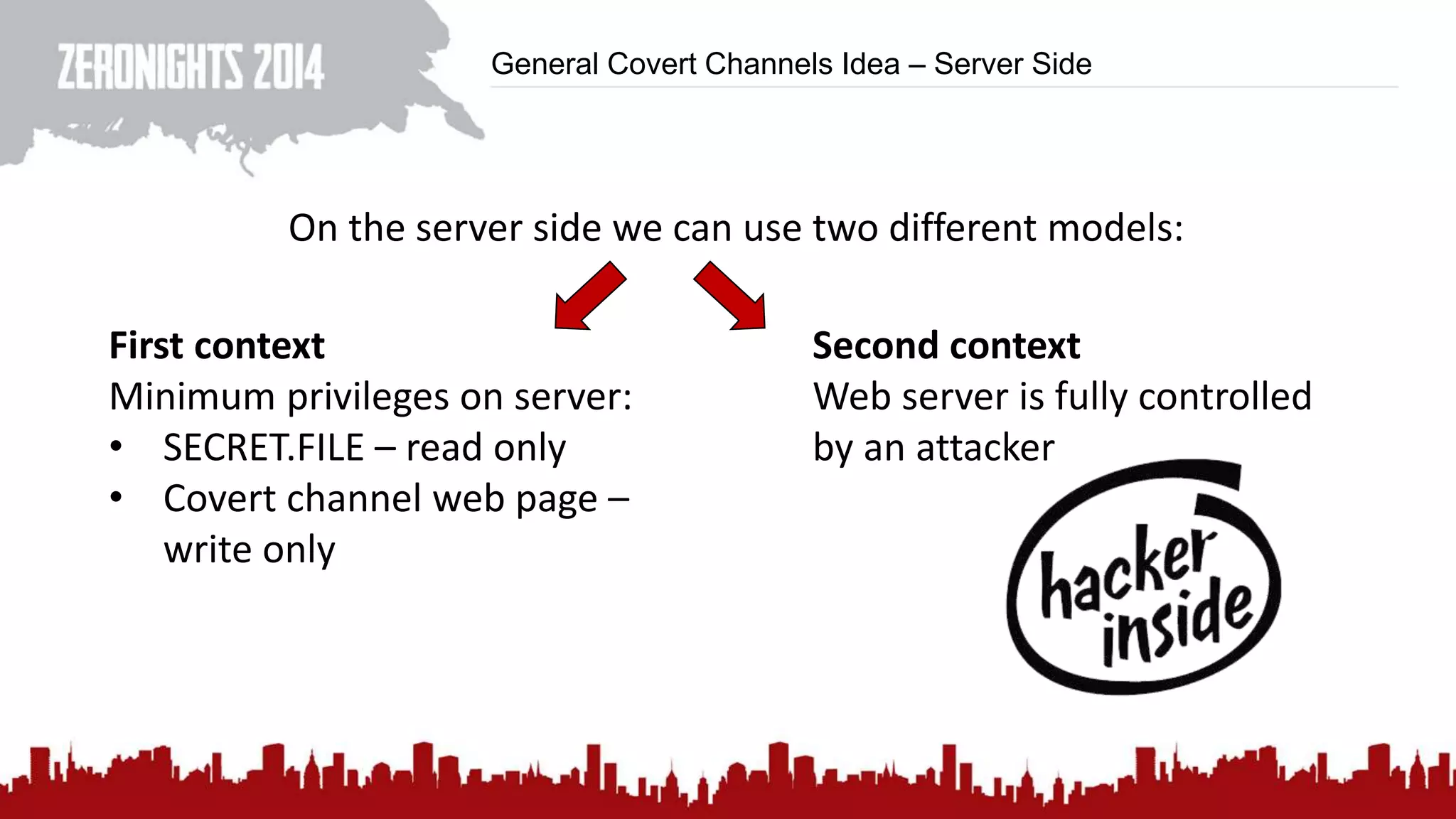
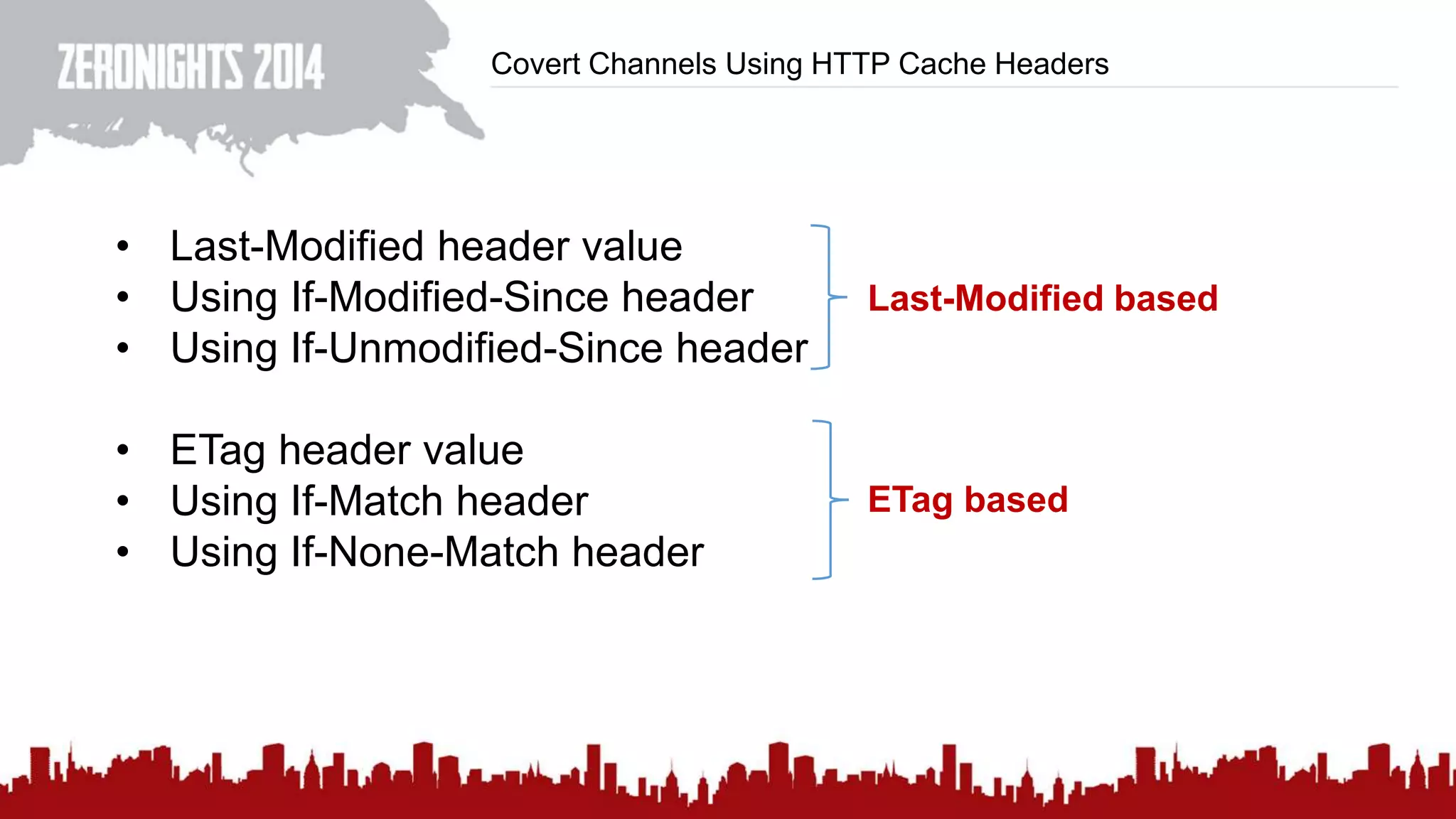
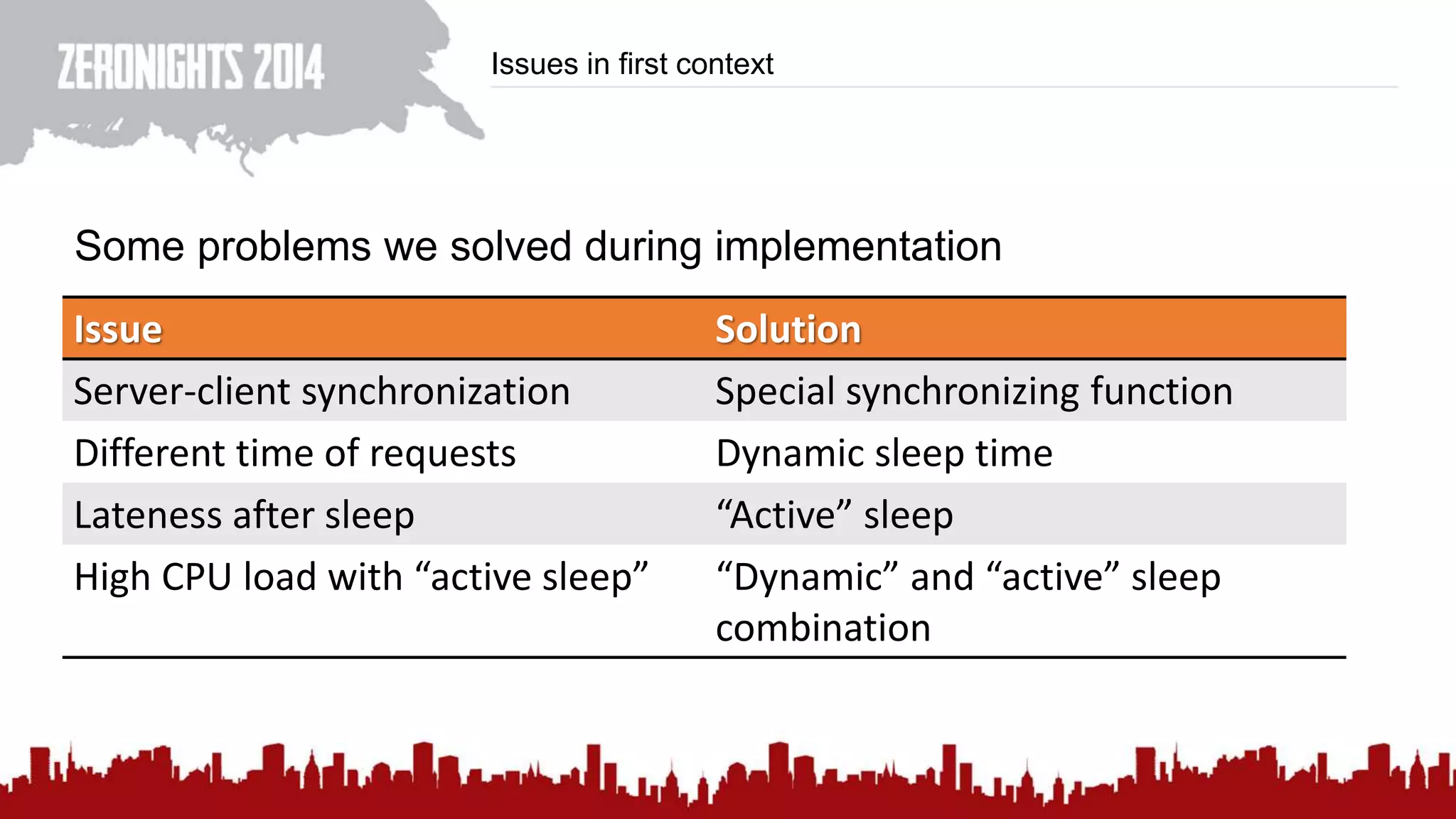
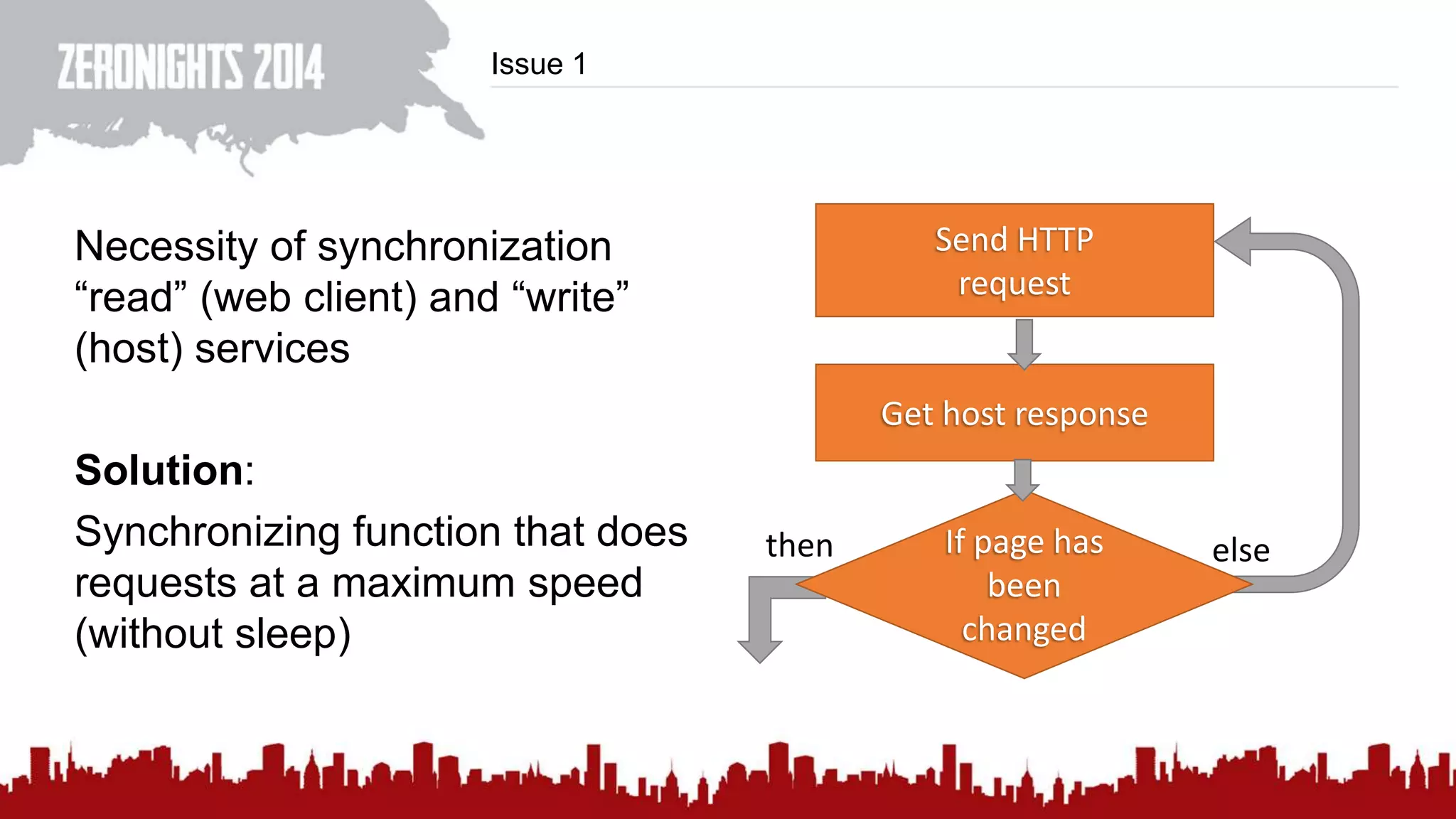
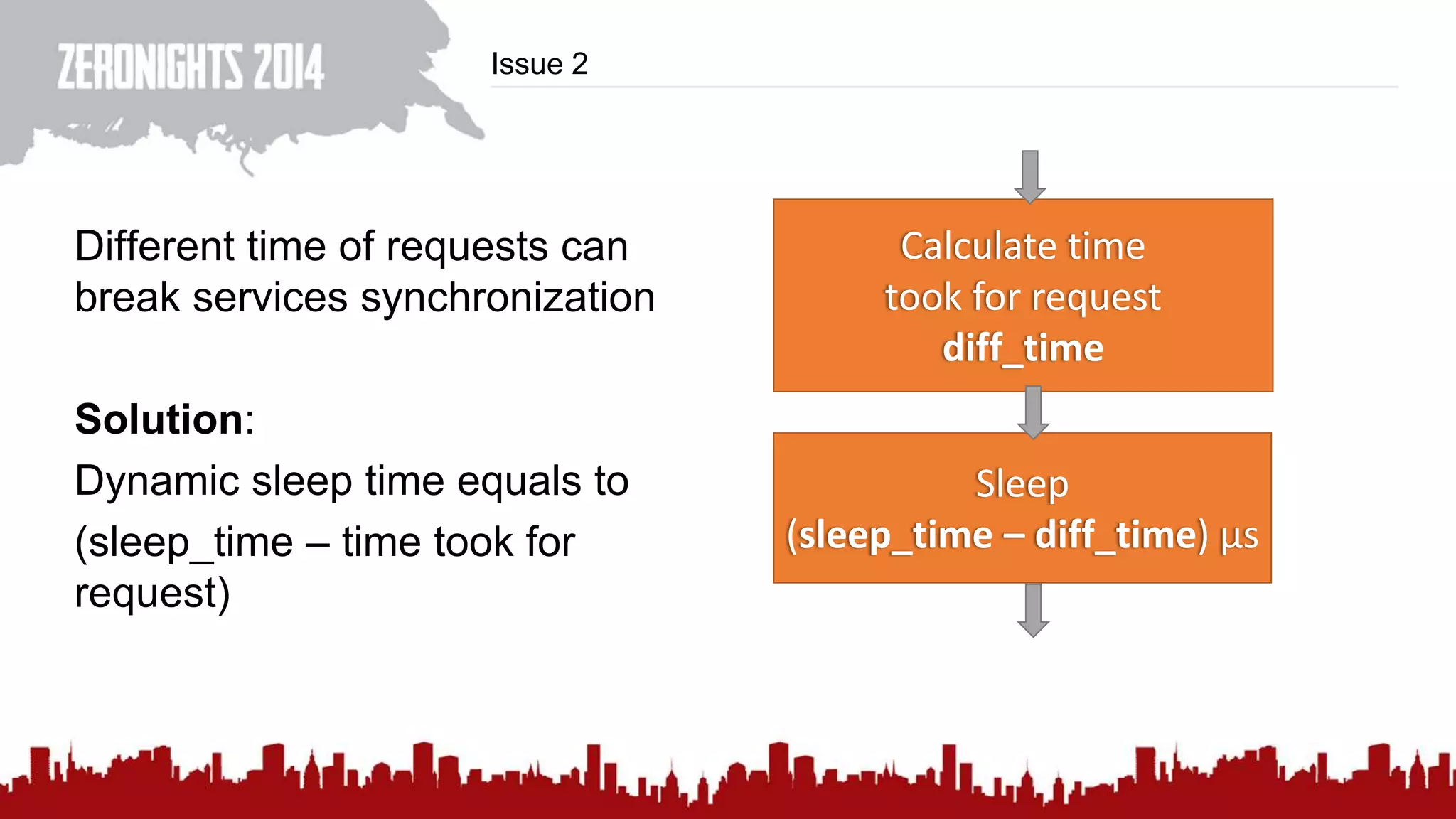
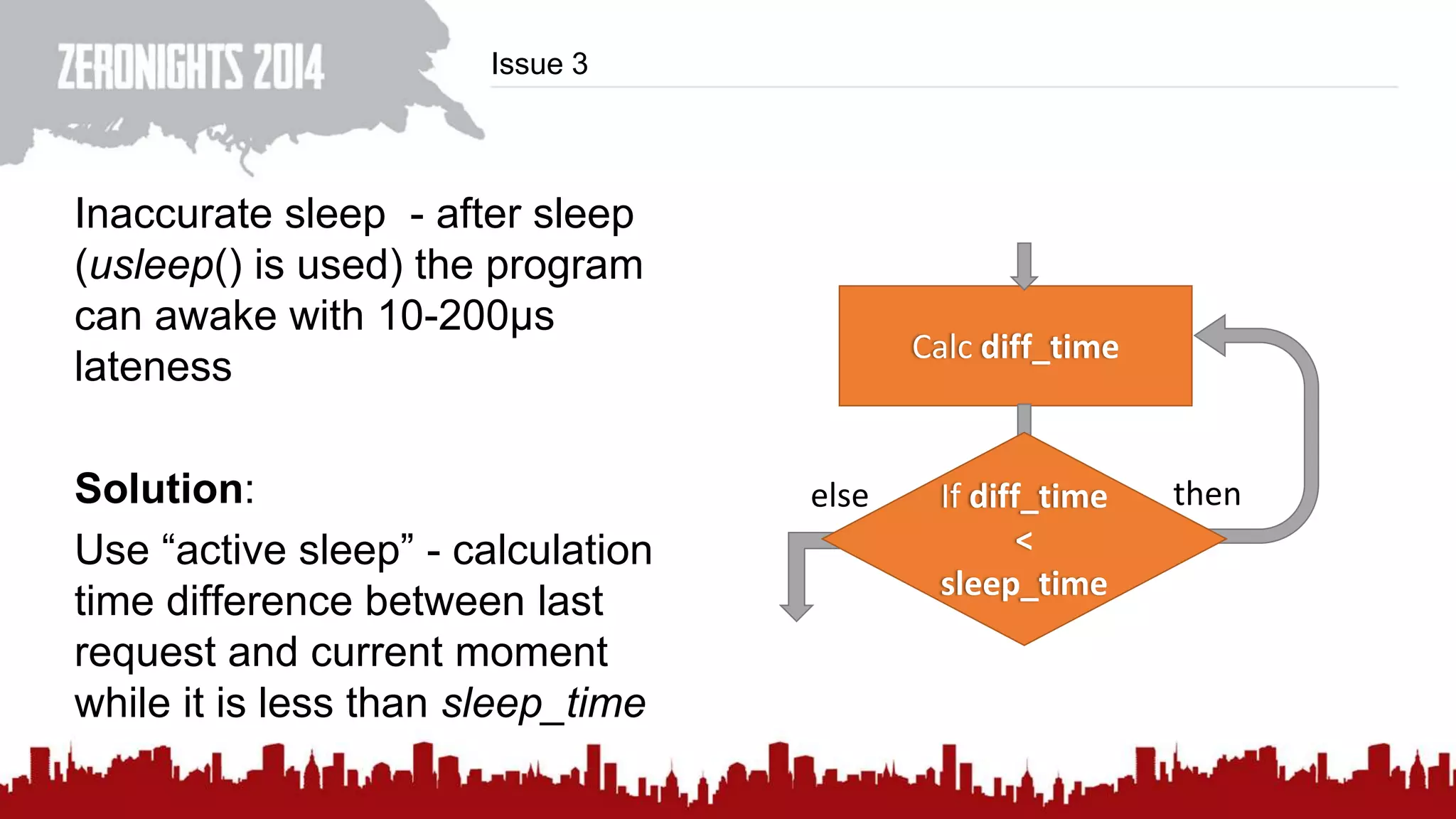
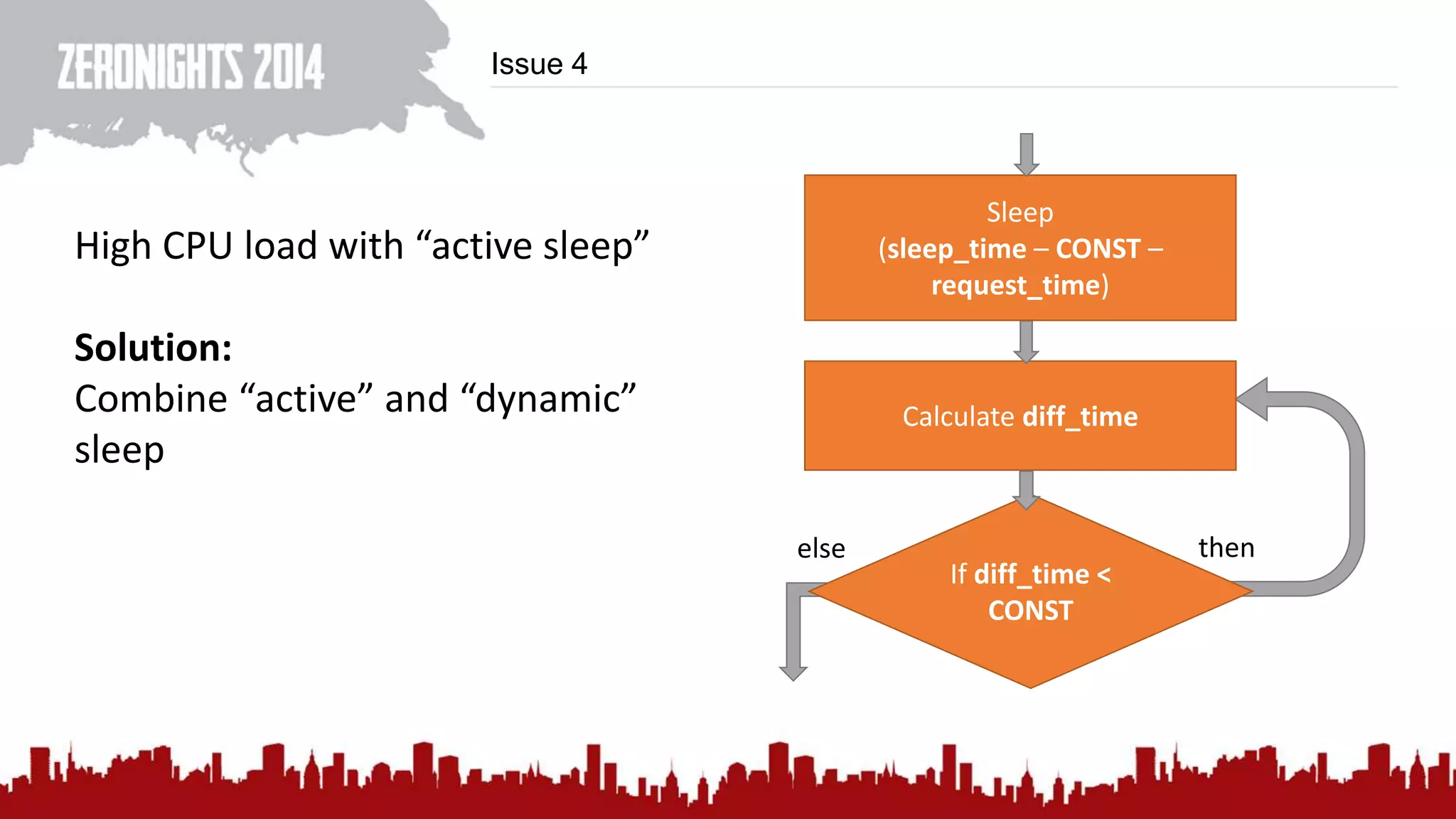
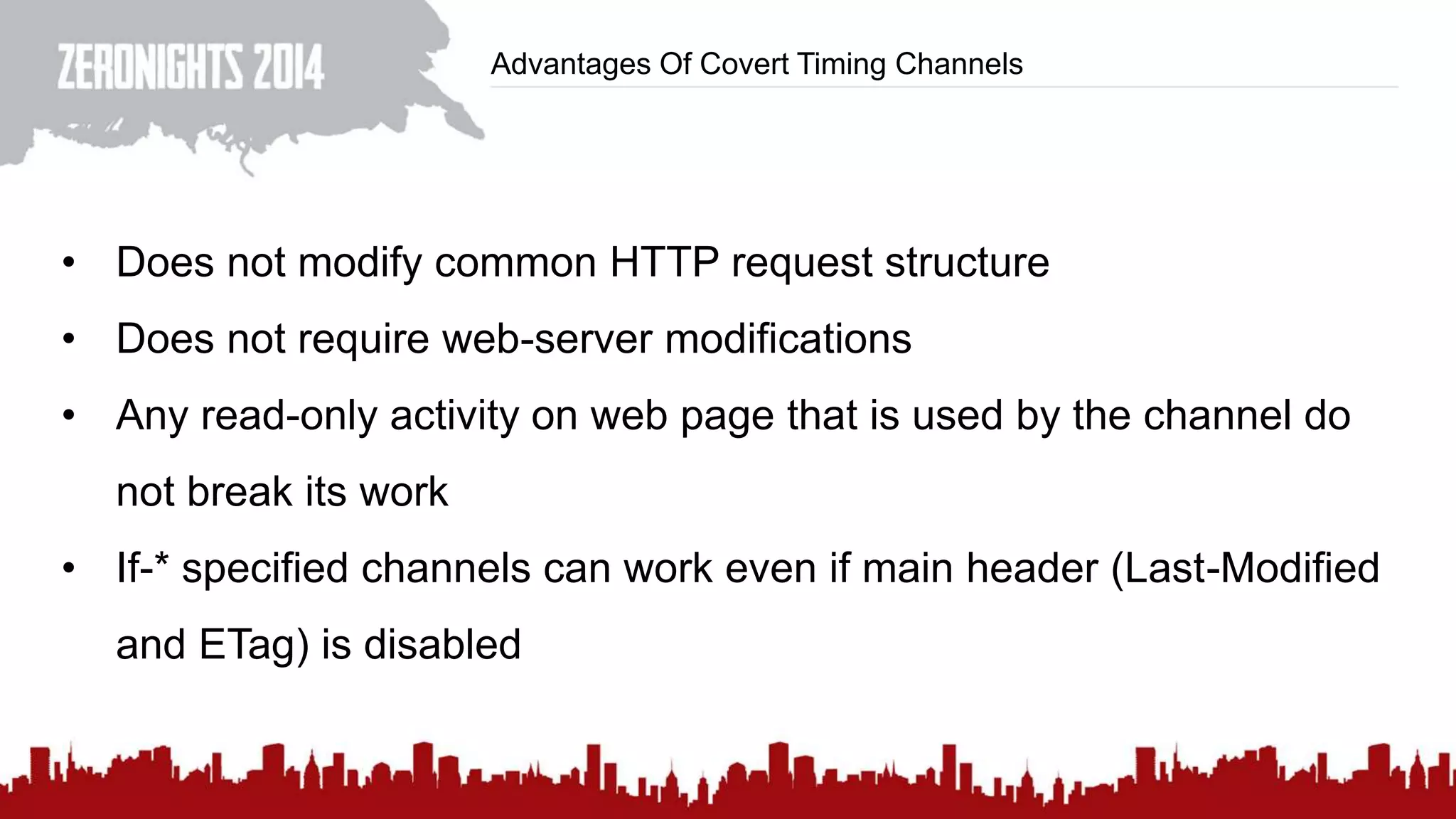
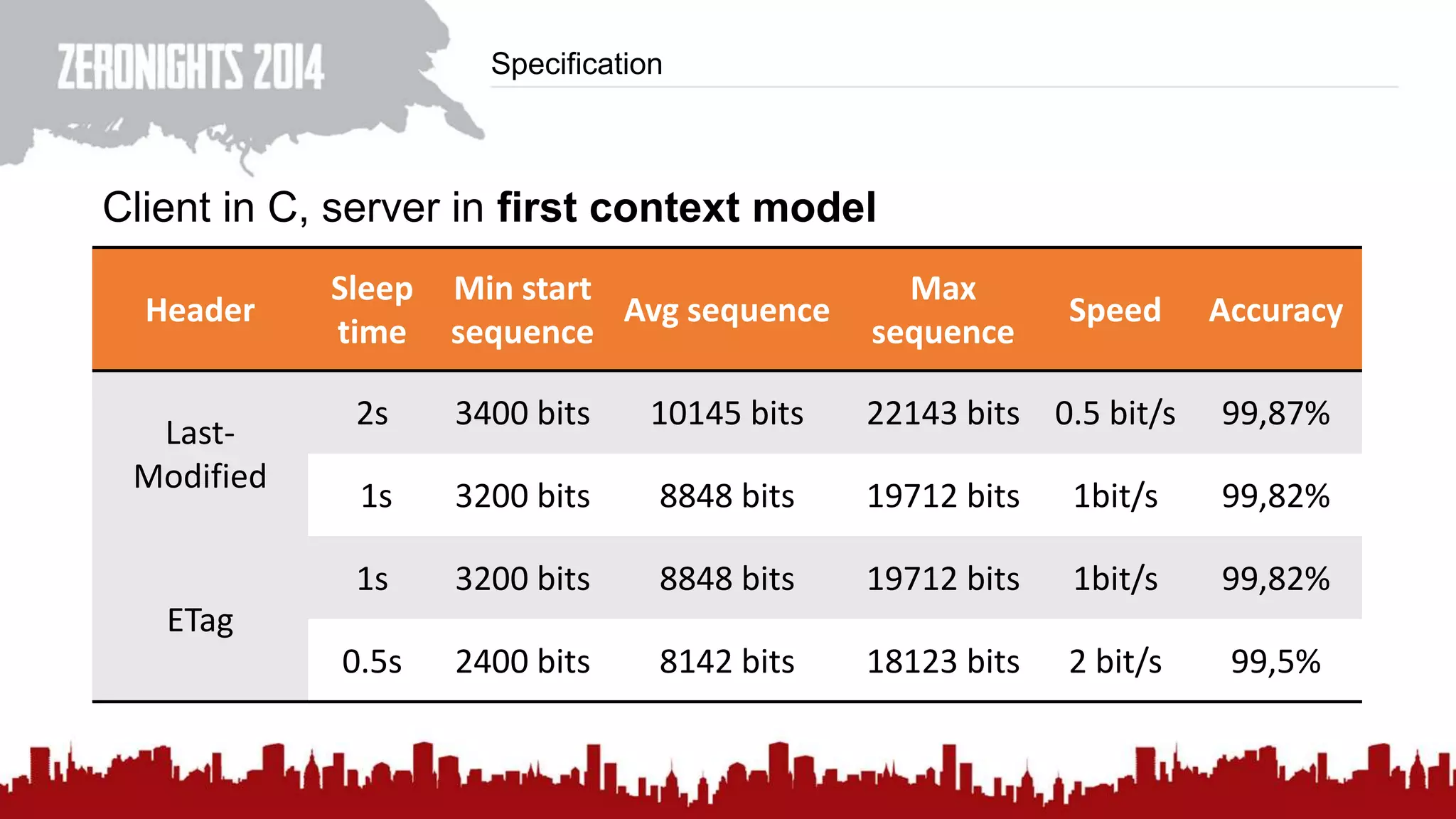
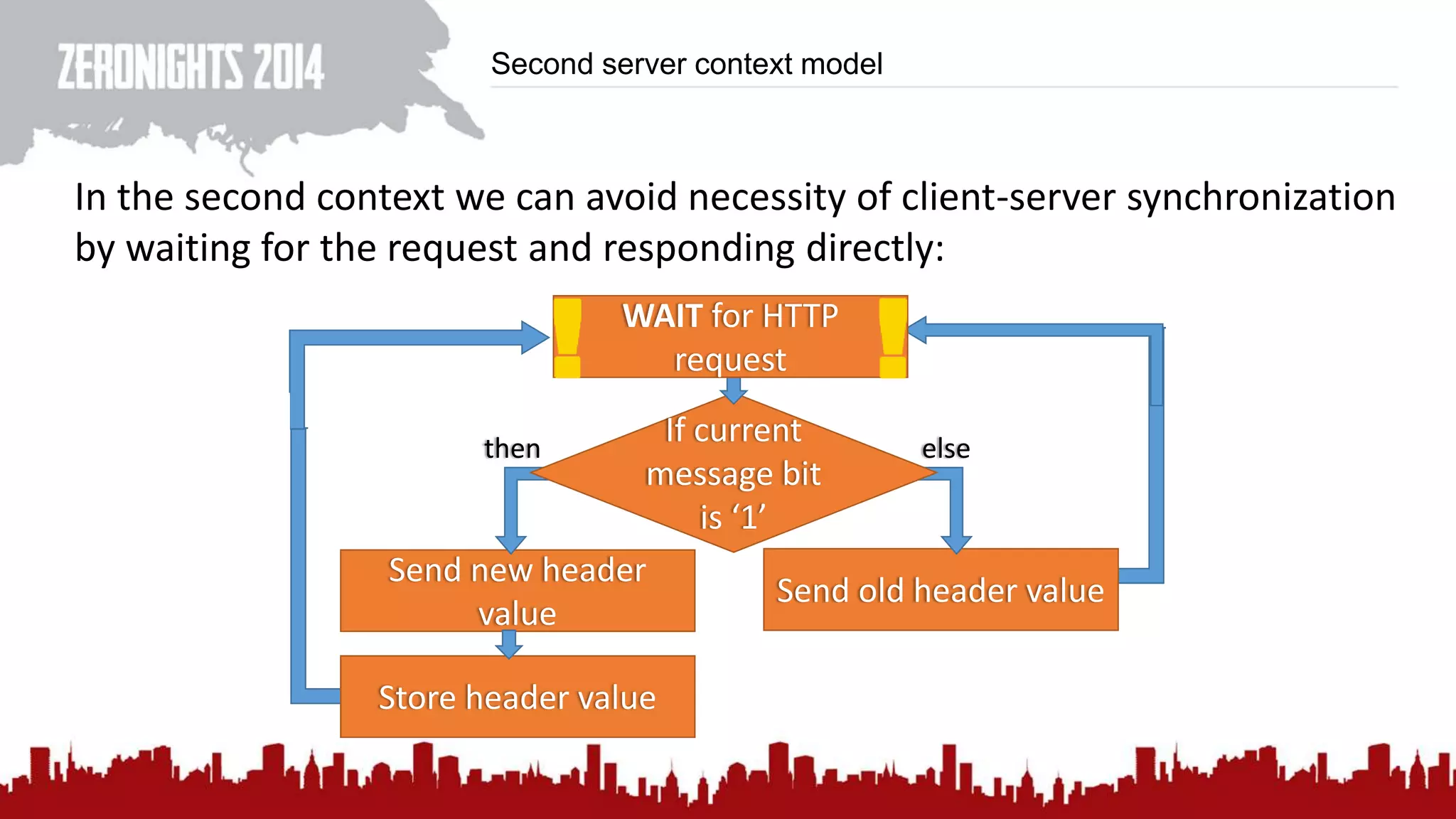
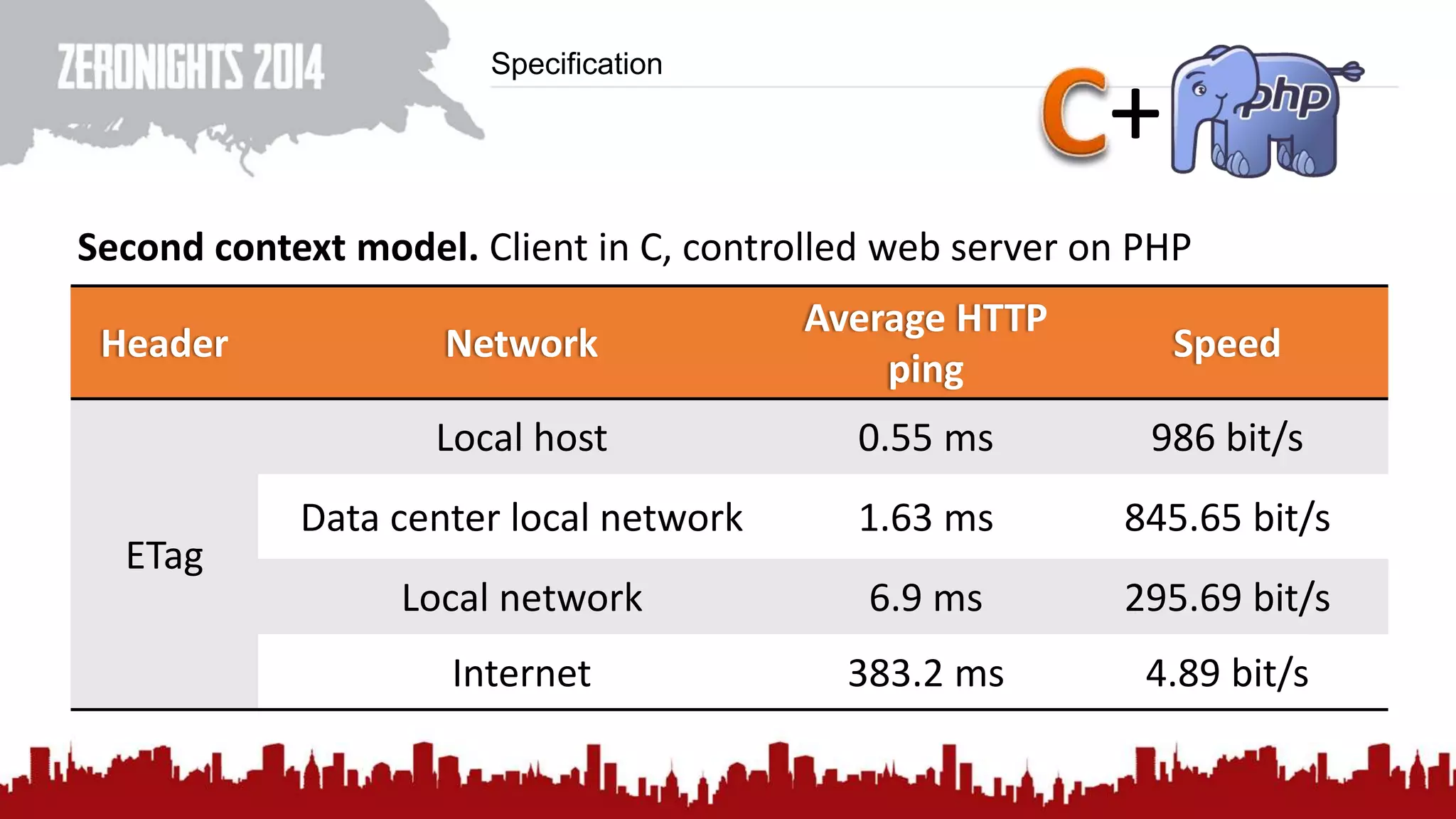
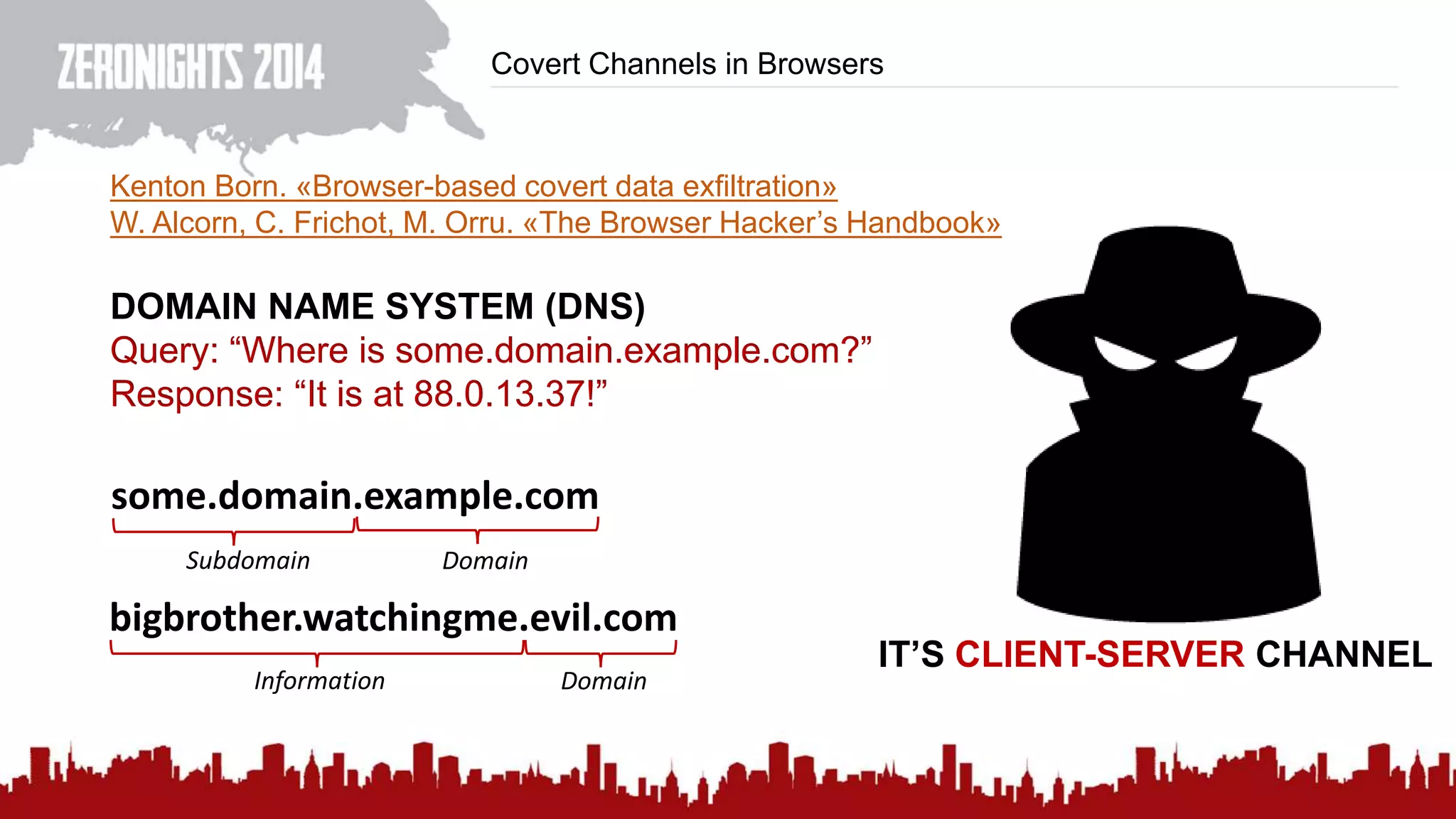
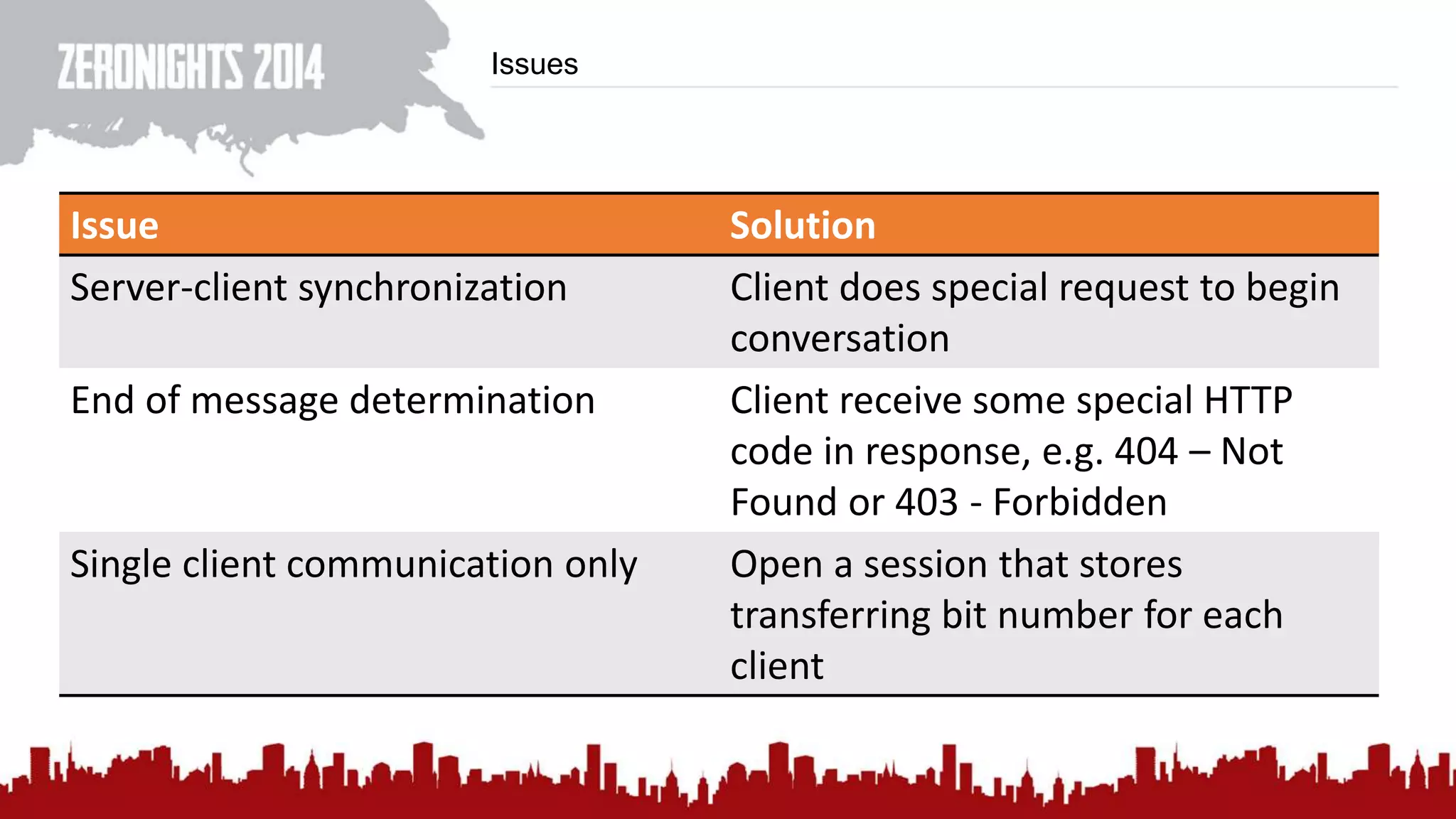
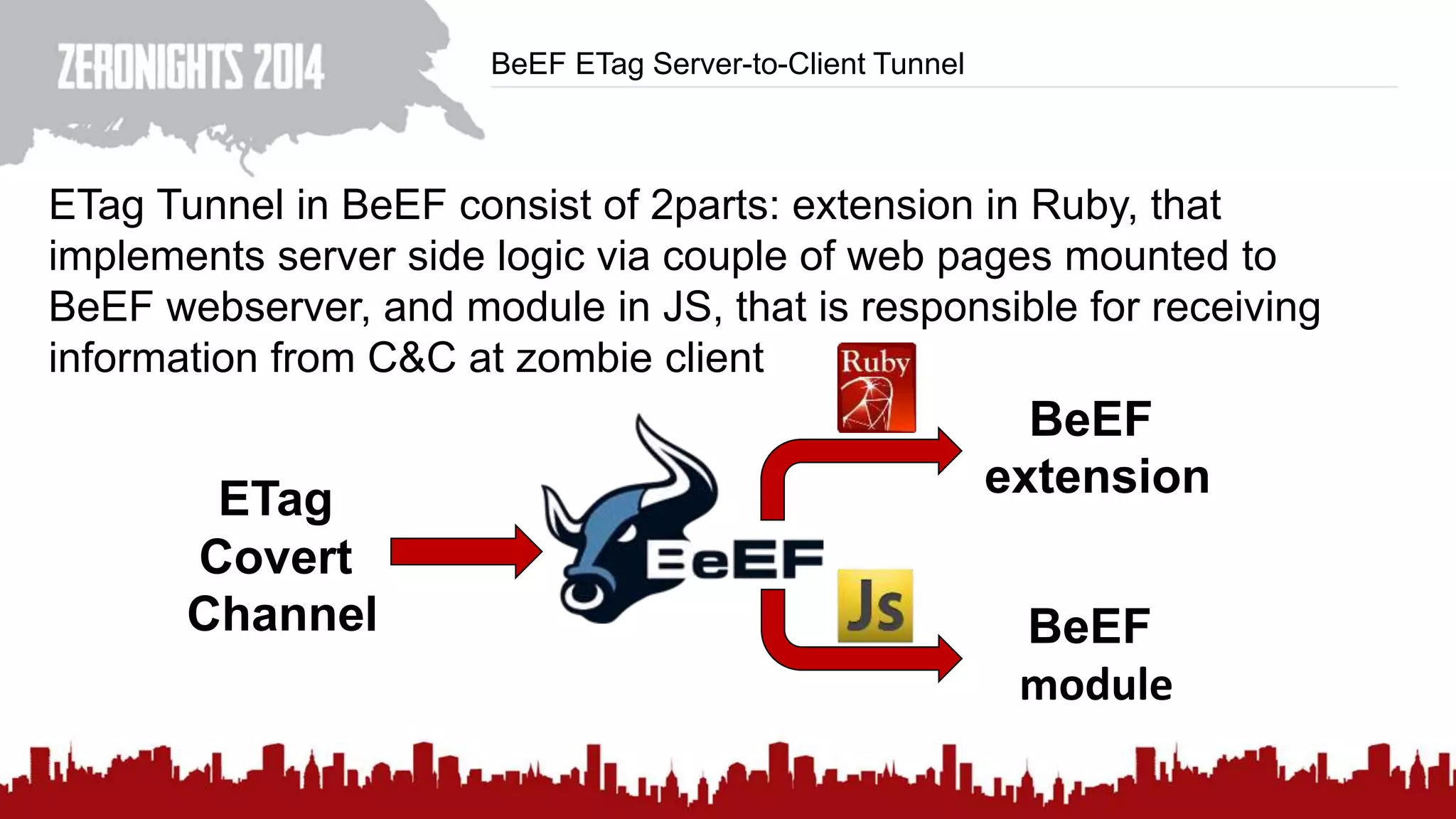
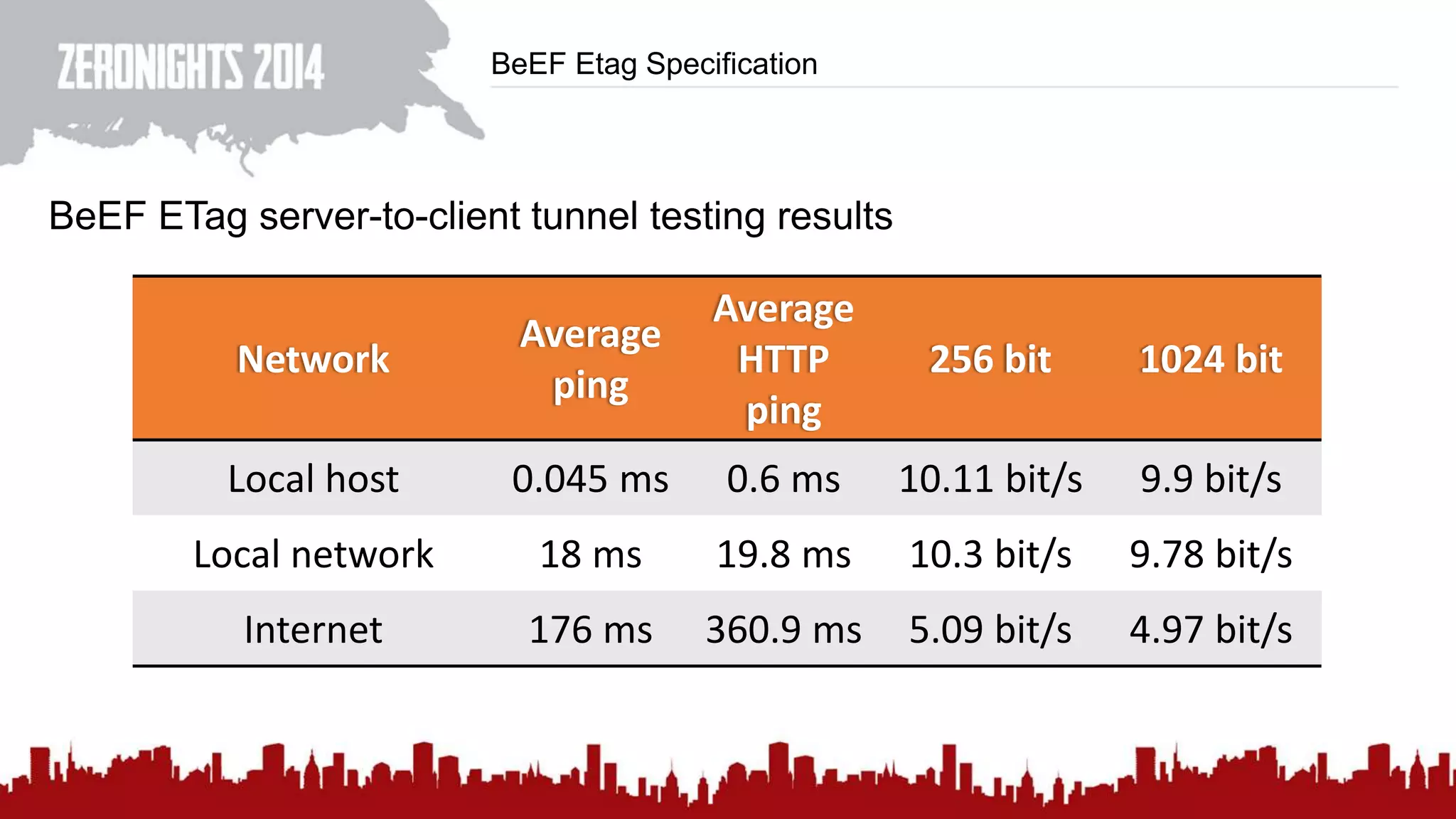
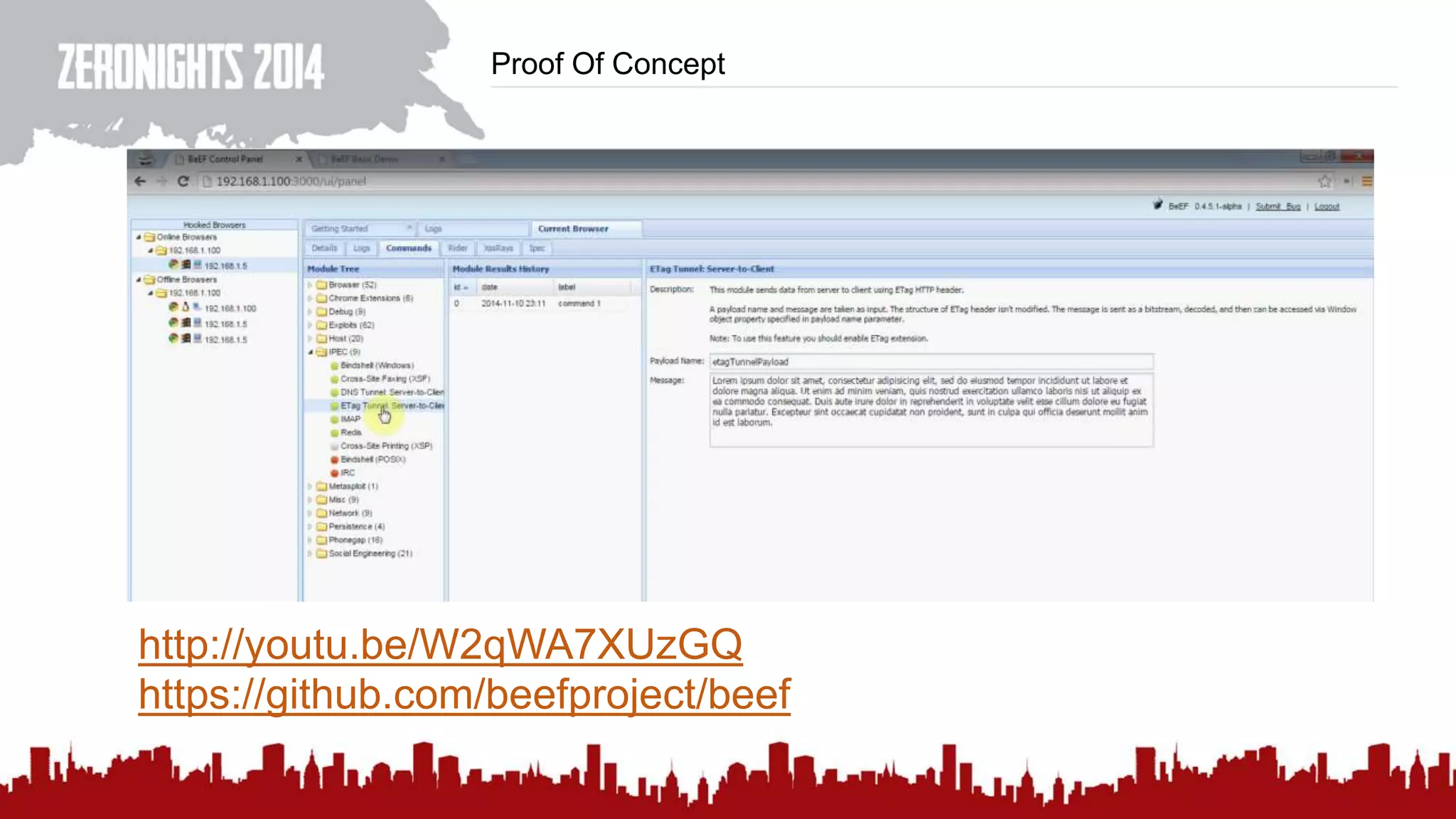
This document discusses using HTTP cache headers to create covert timing channels for transmitting information between hosts without detection. It provides examples of encoding data in the Accept-Language header and describes how headers like Last-Modified and ETag can be used to transmit bits by checking if the page has changed. Issues in implementation are addressed, like needing synchronization. Evaluation shows channels can transmit over 1 bit/second over local networks and around 5 bits/second over the internet. Browser-based channels in JavaScript are also proposed.