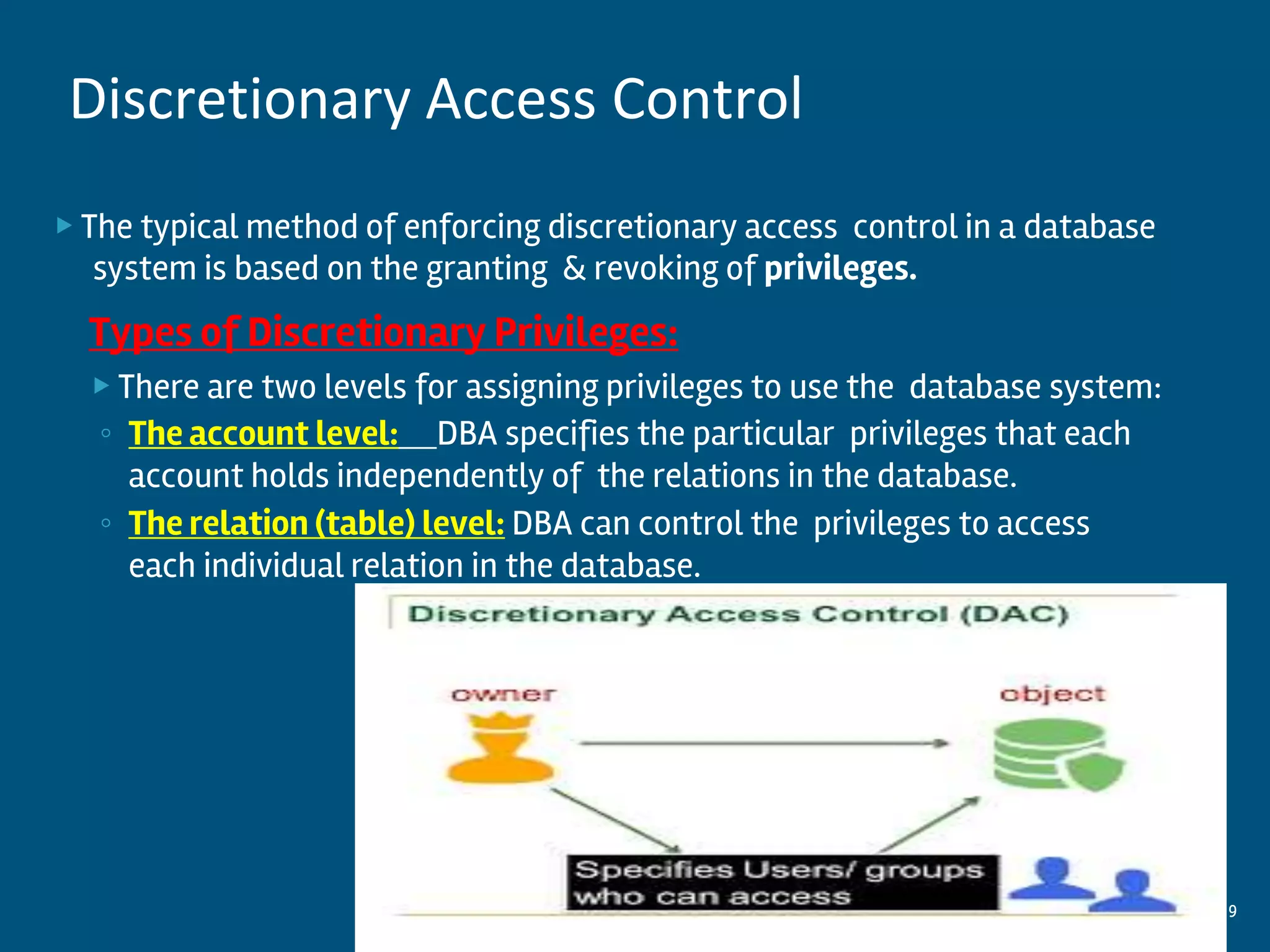
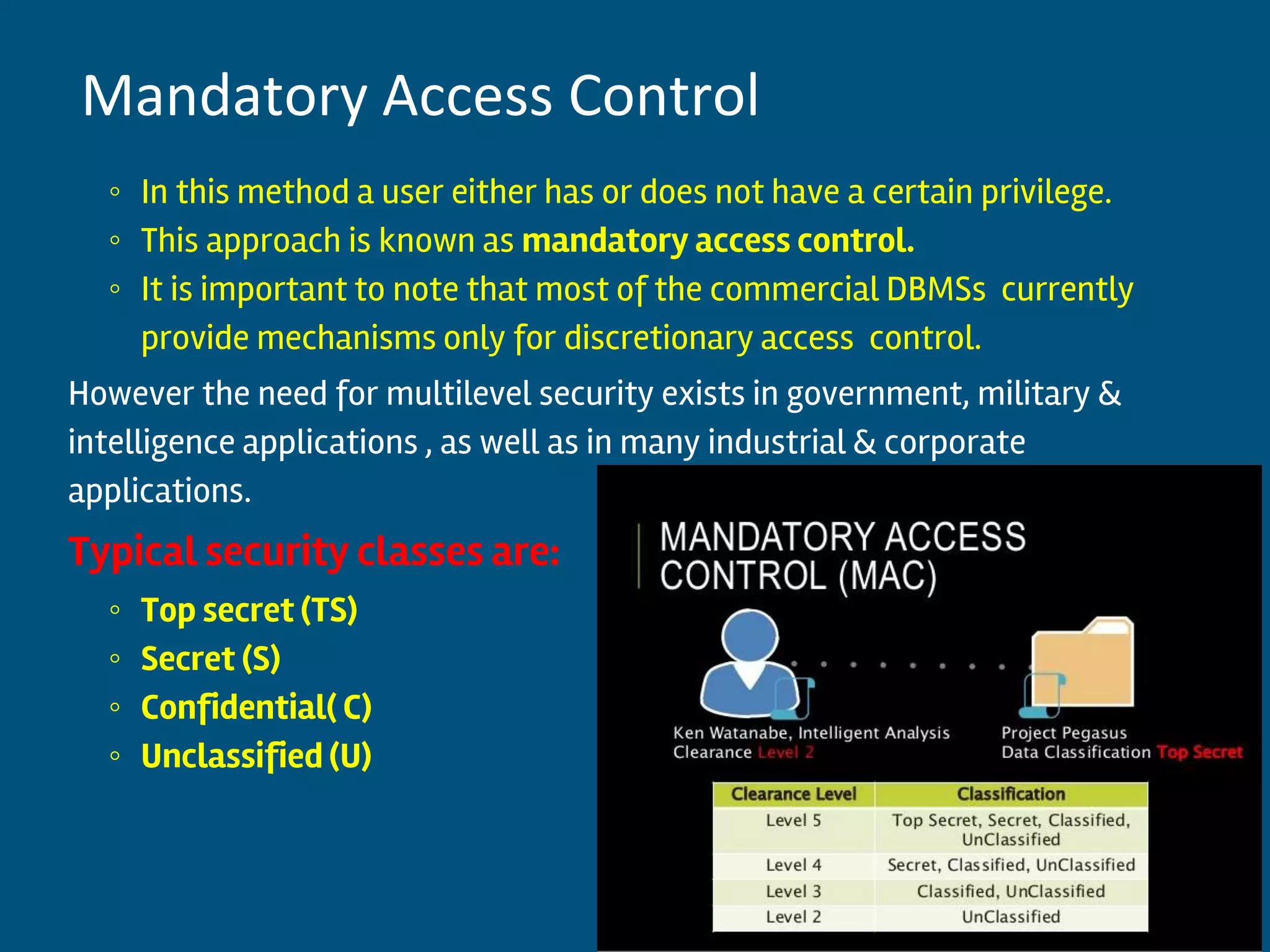
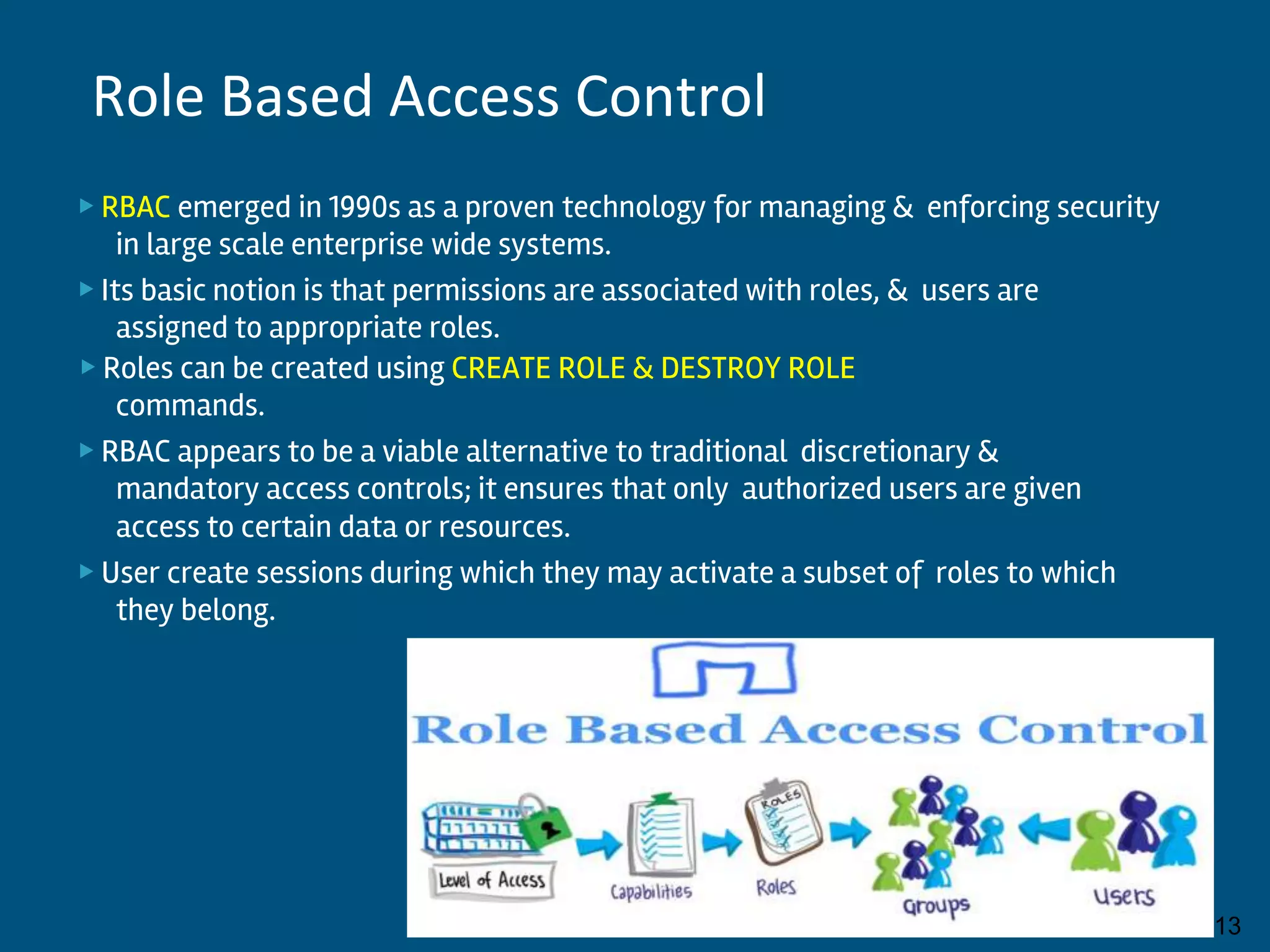
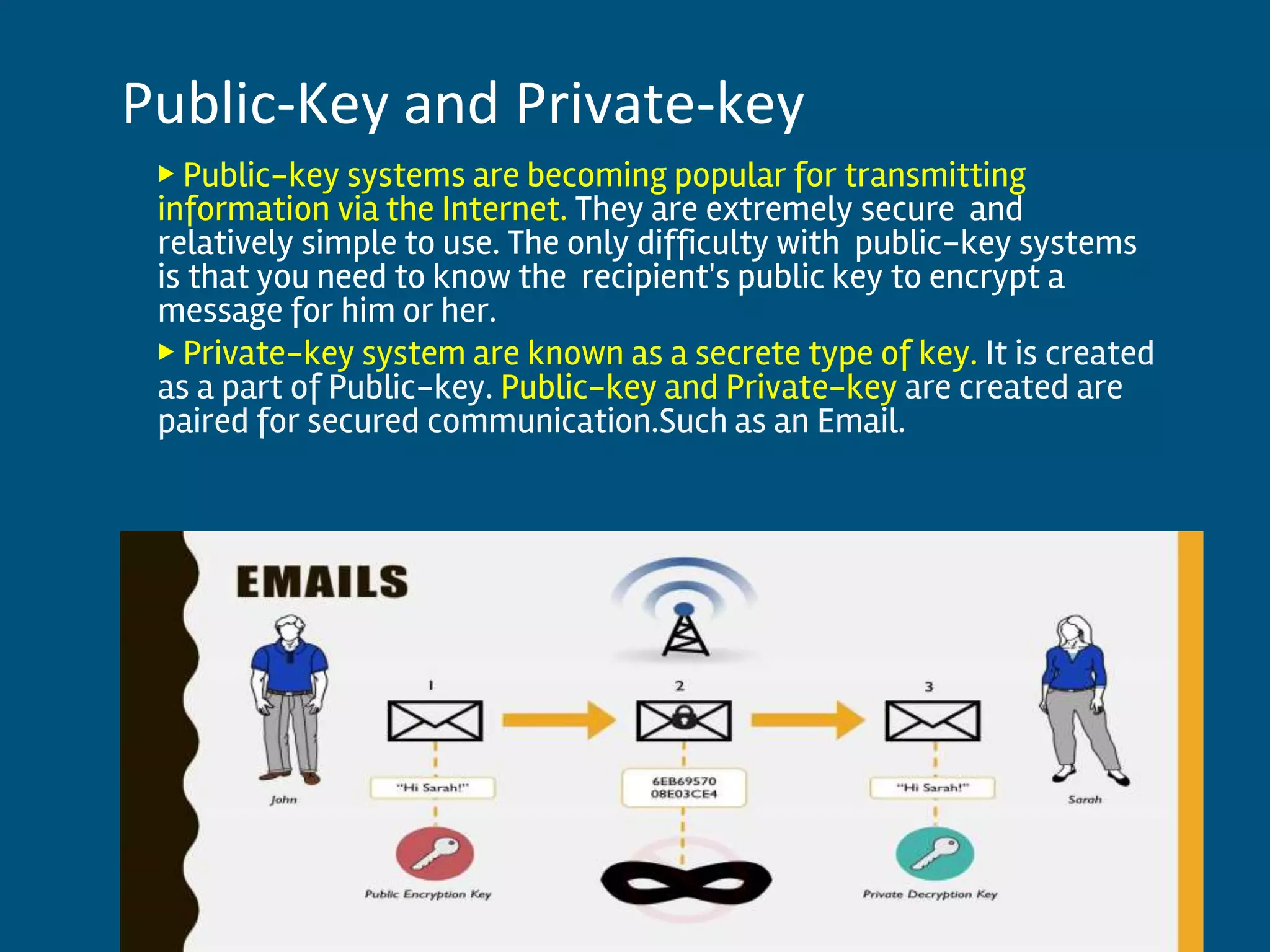
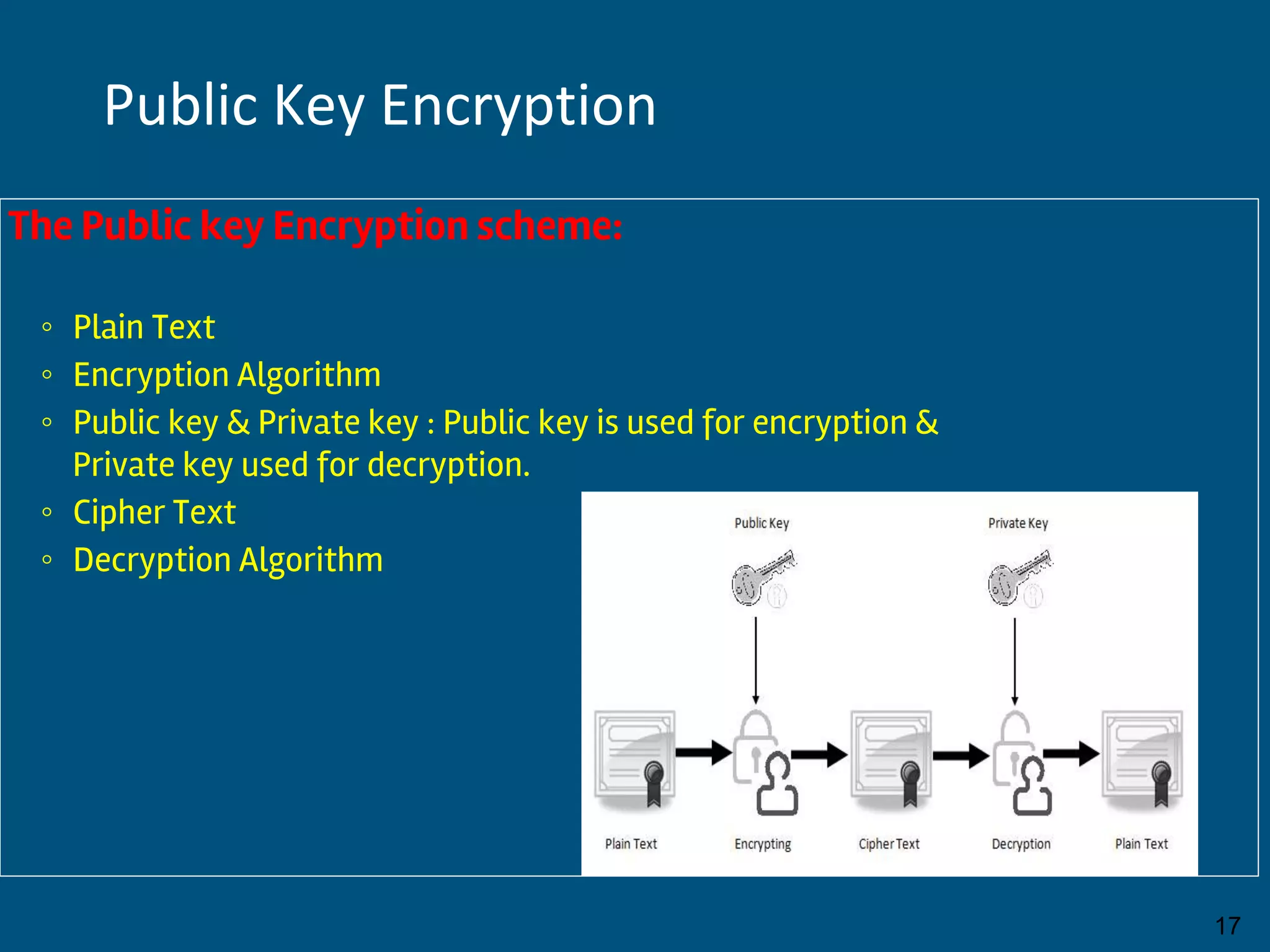
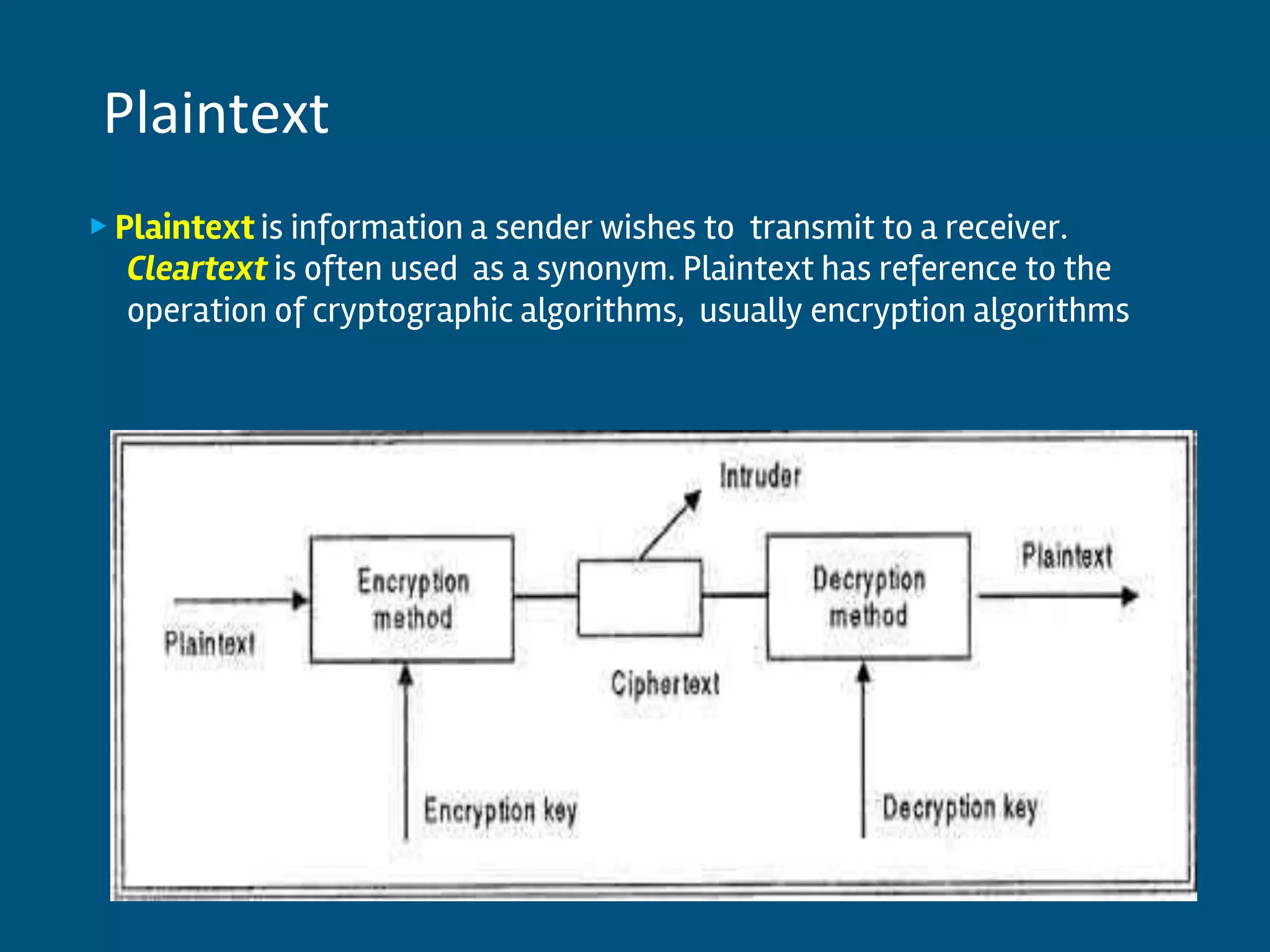
This document discusses database security and privacy. It covers various types of security including discretionary access control based on granting and revoking privileges, mandatory access control and role-based access control. It also discusses threats to database security such as loss of integrity, availability and confidentiality. Methods to protect against these threats include access control, flow control, encryption and decryption. The document also covers public key infrastructure and encryption standards such as DES and AES.