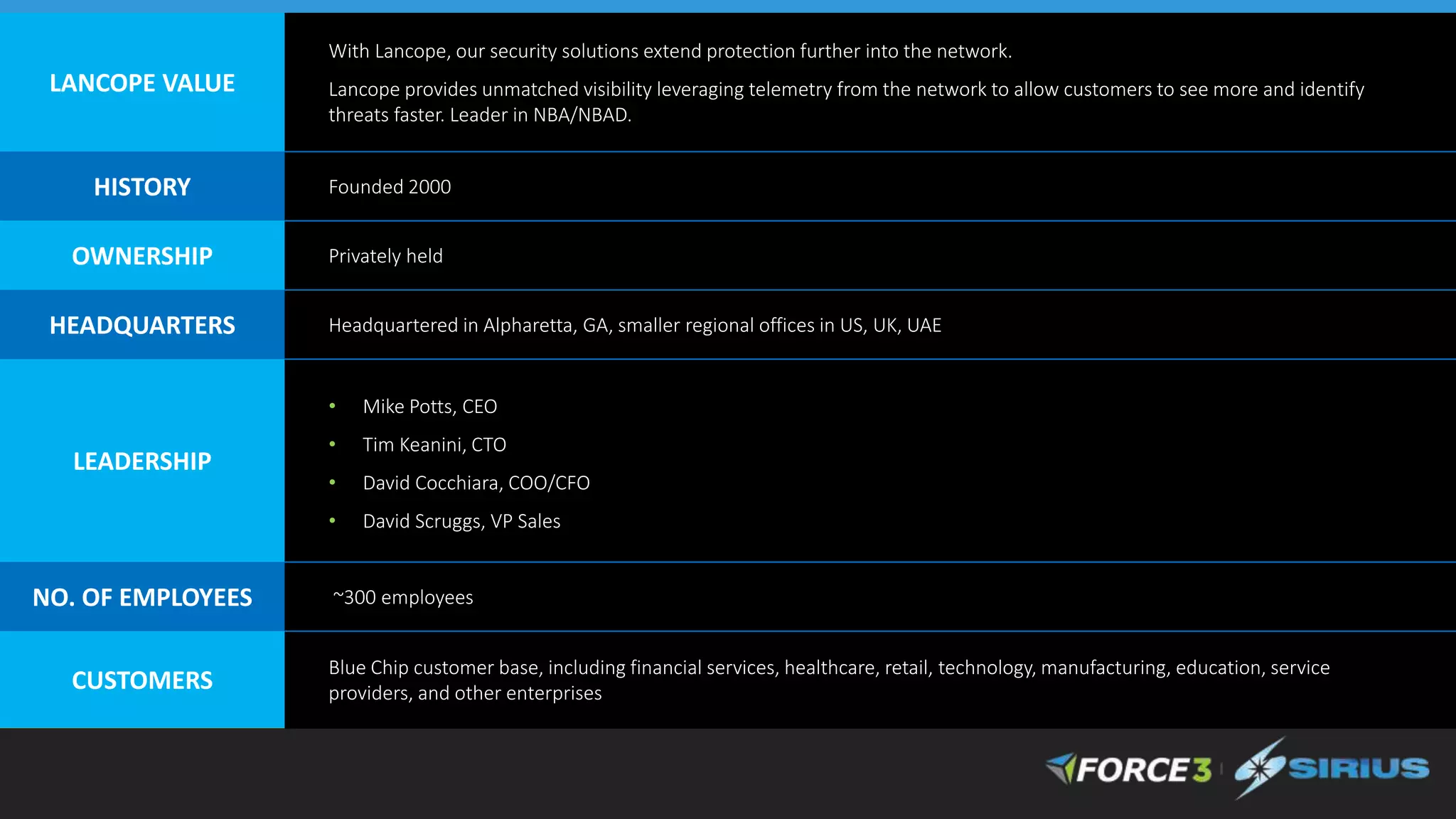
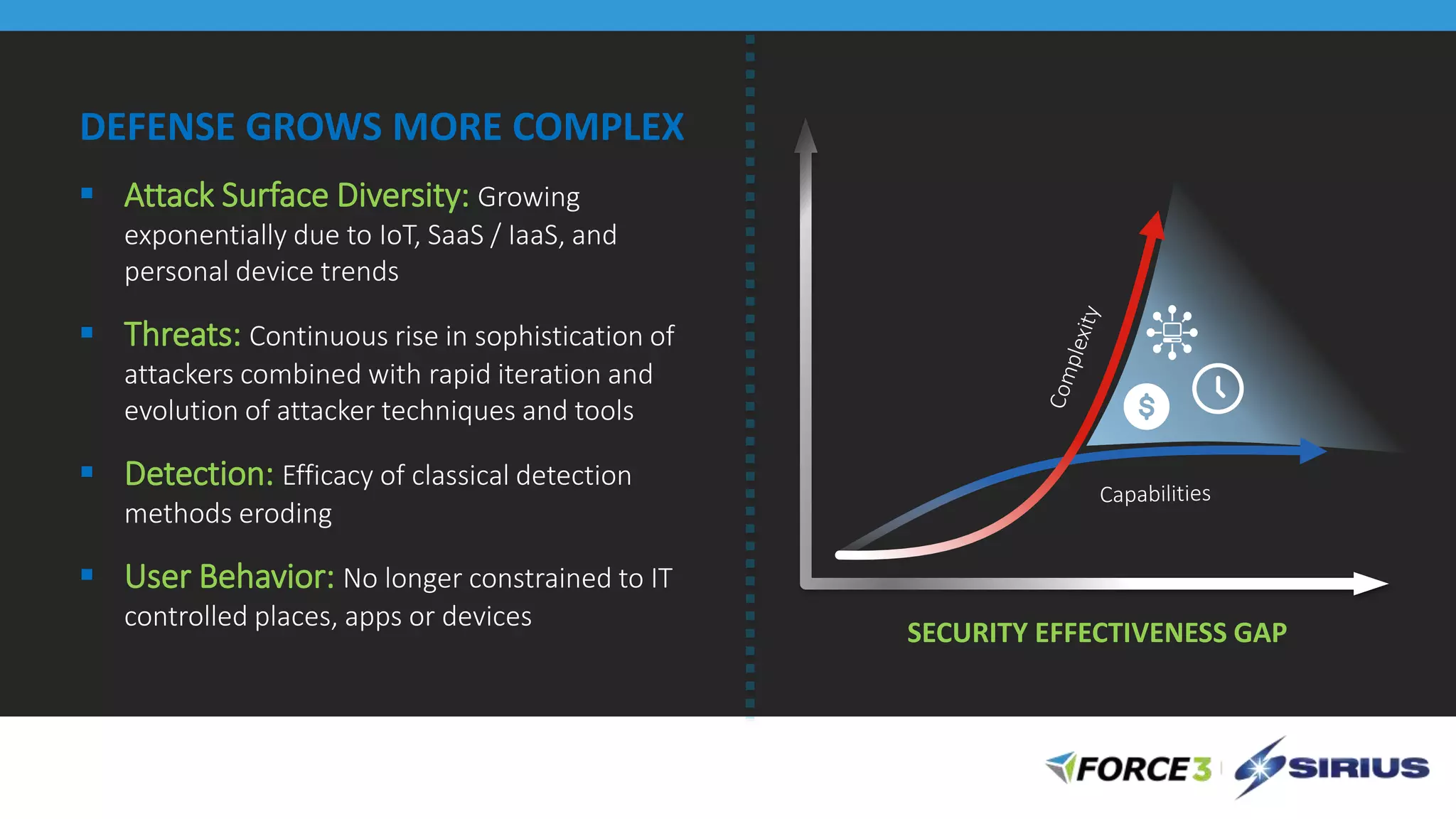
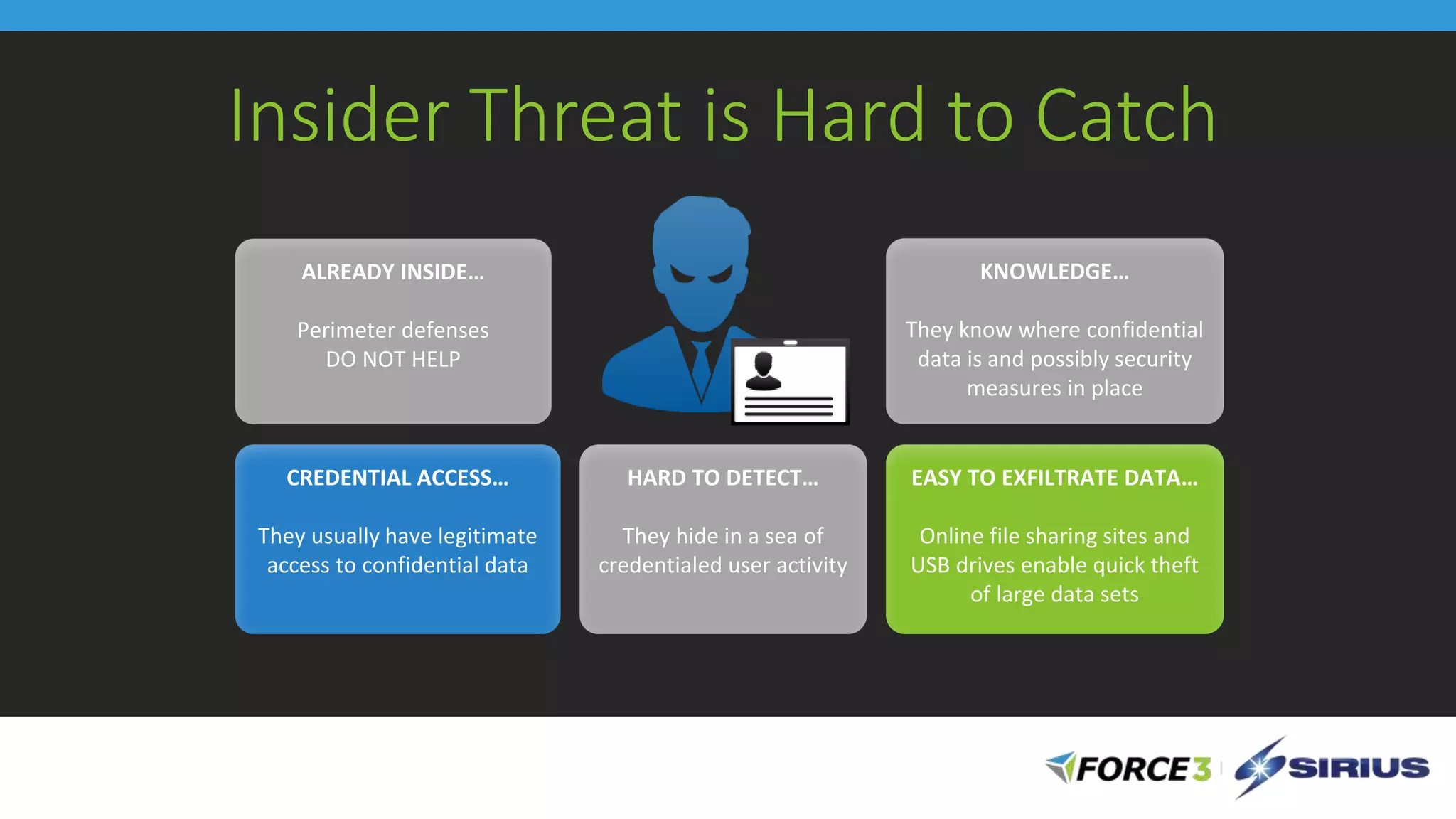
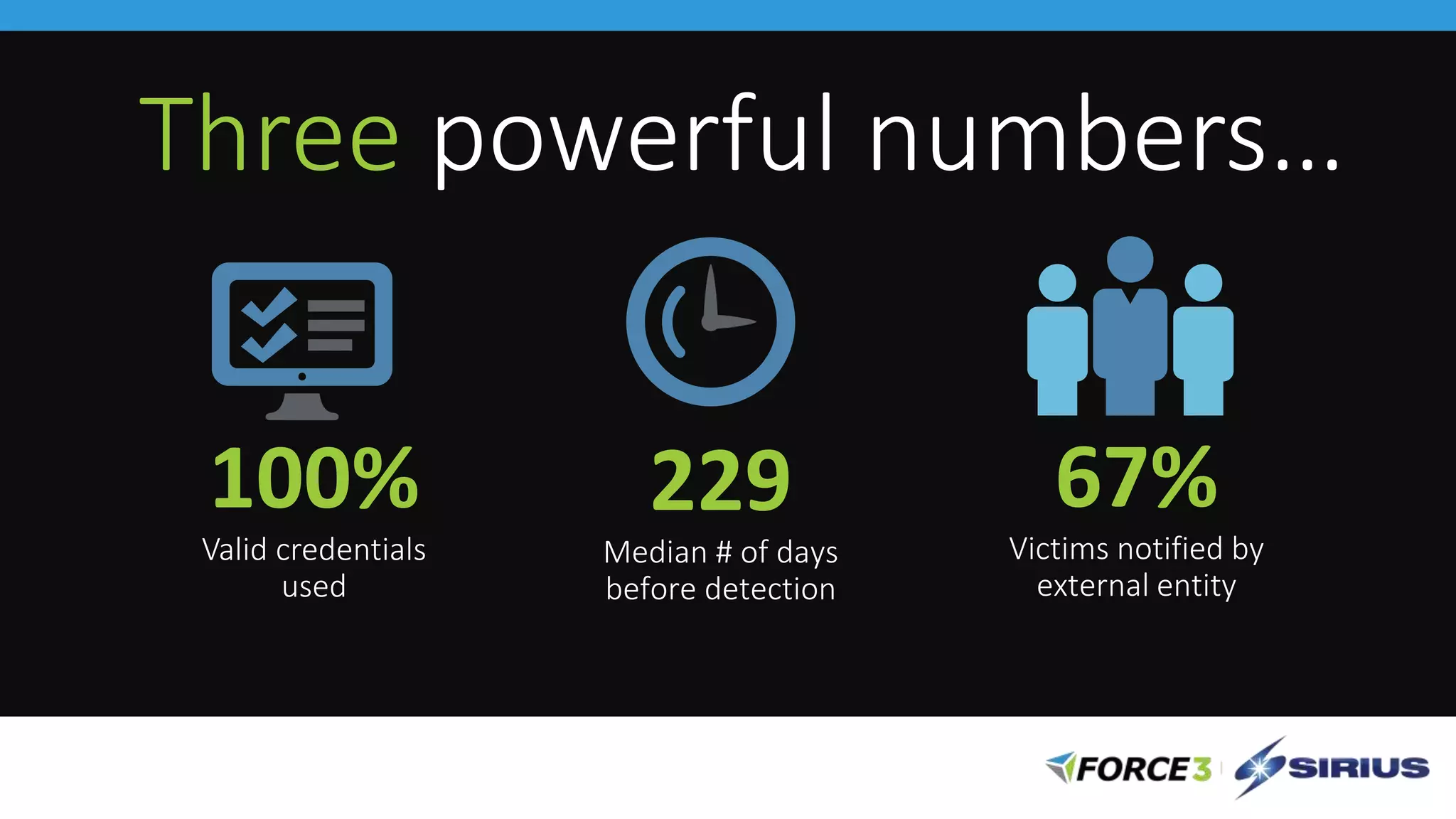
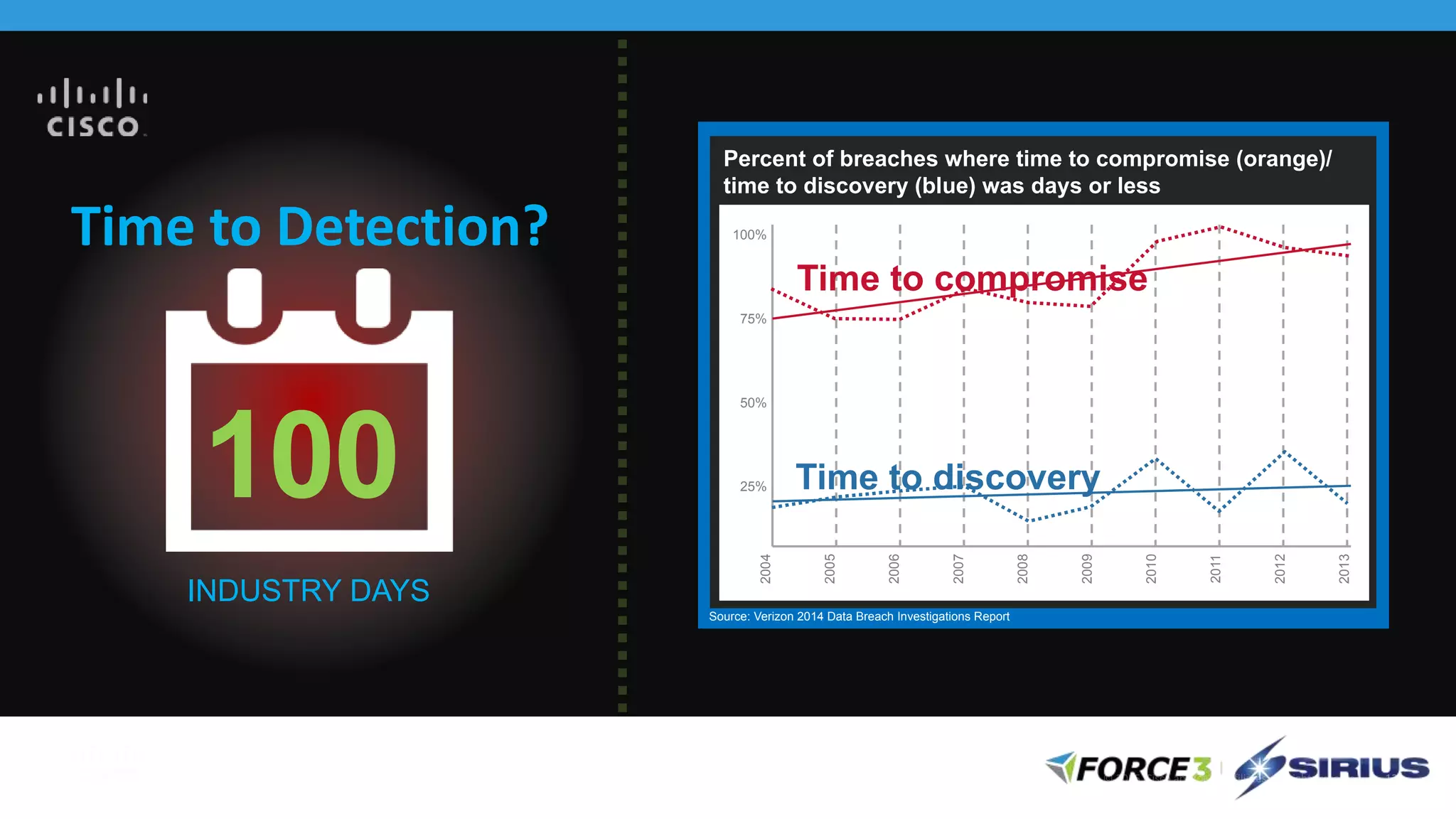
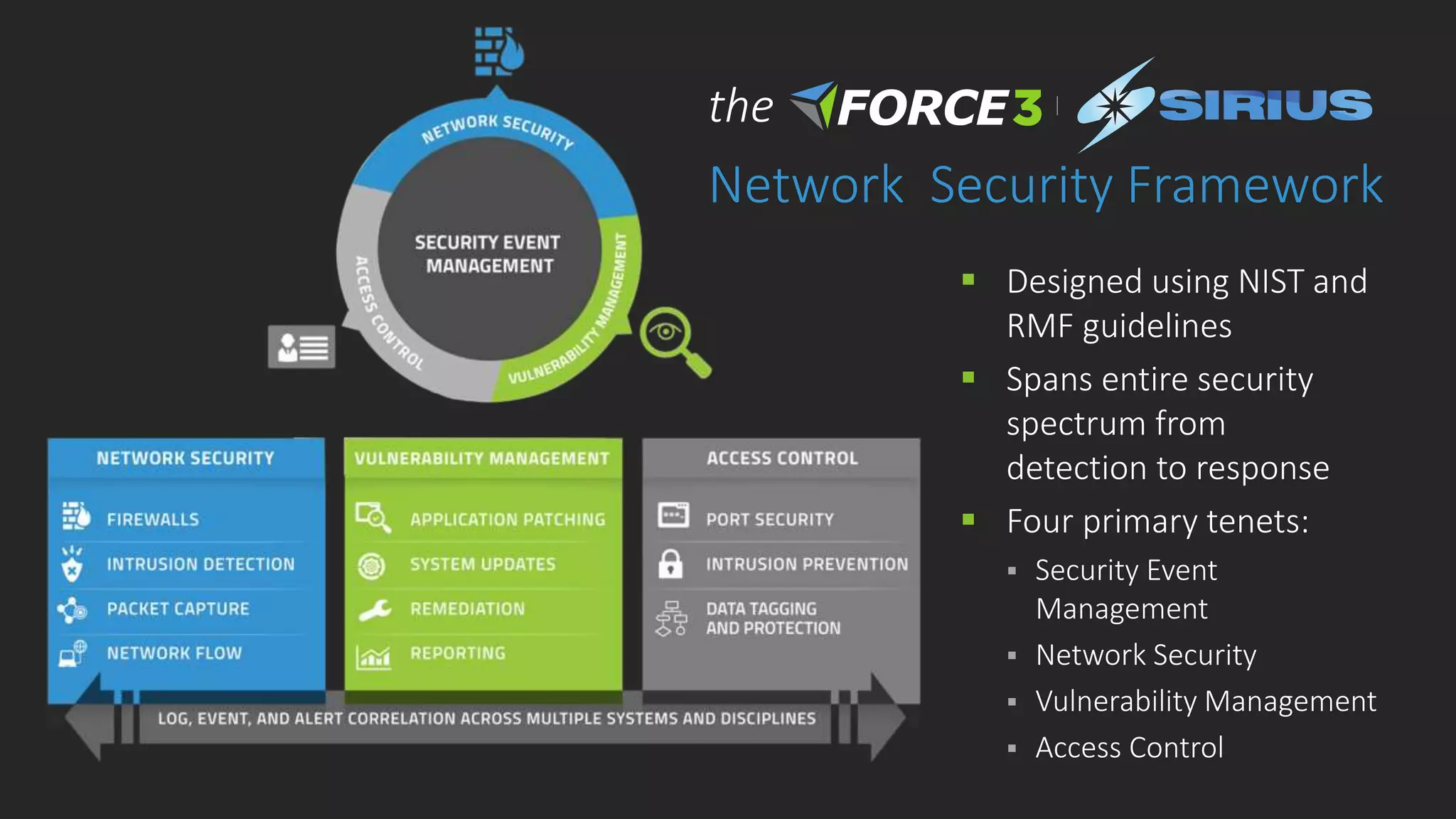
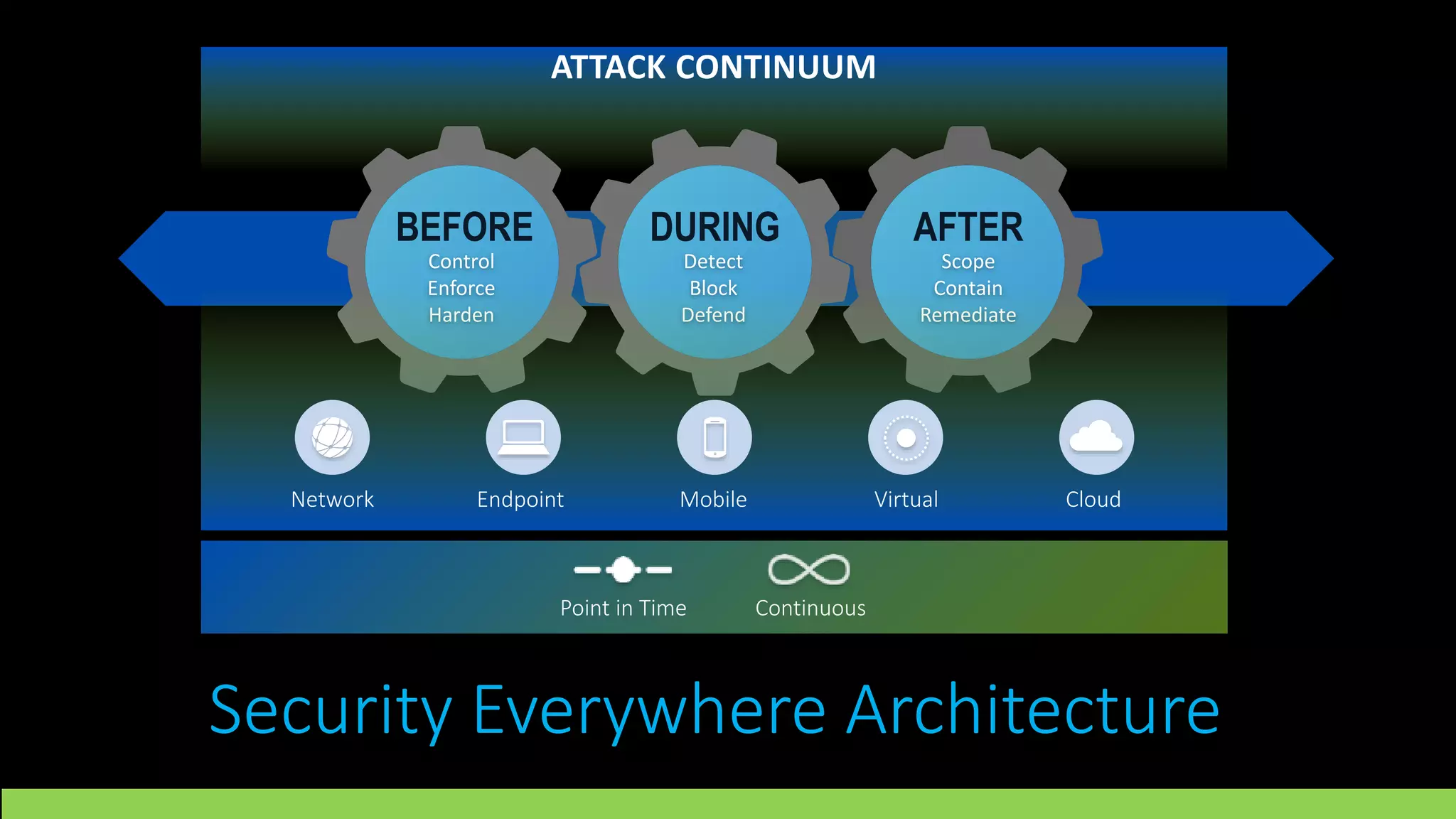
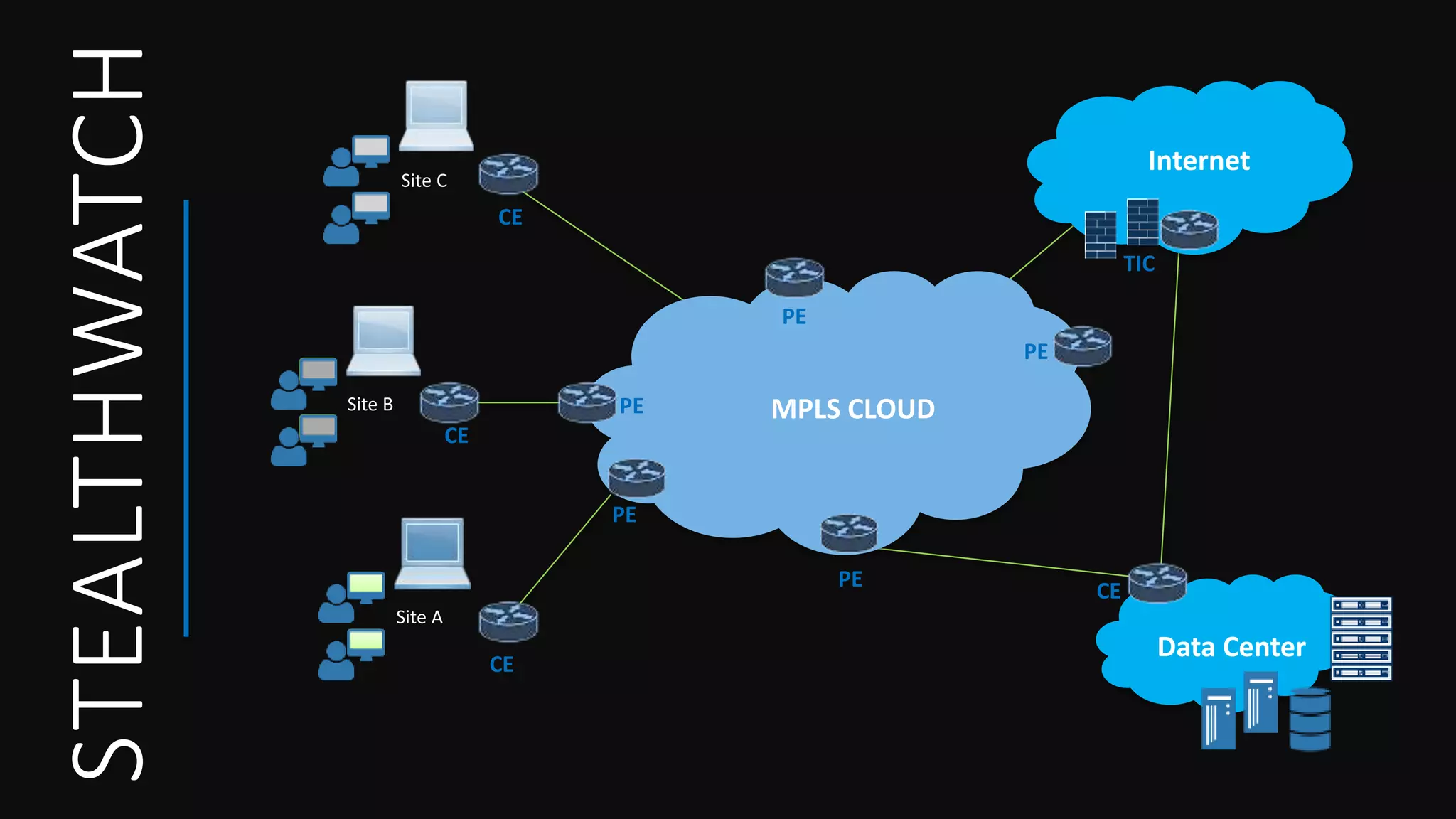
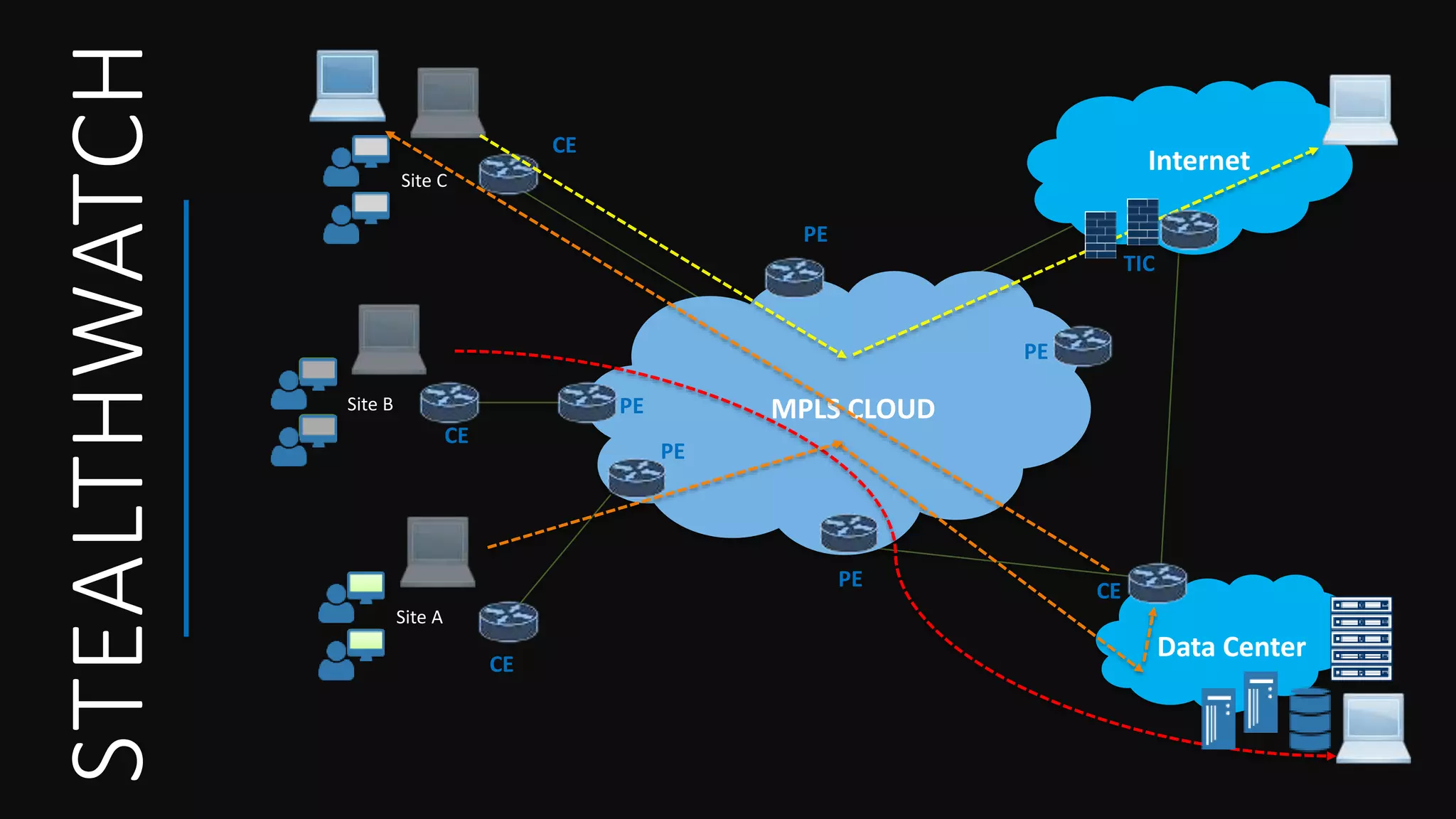
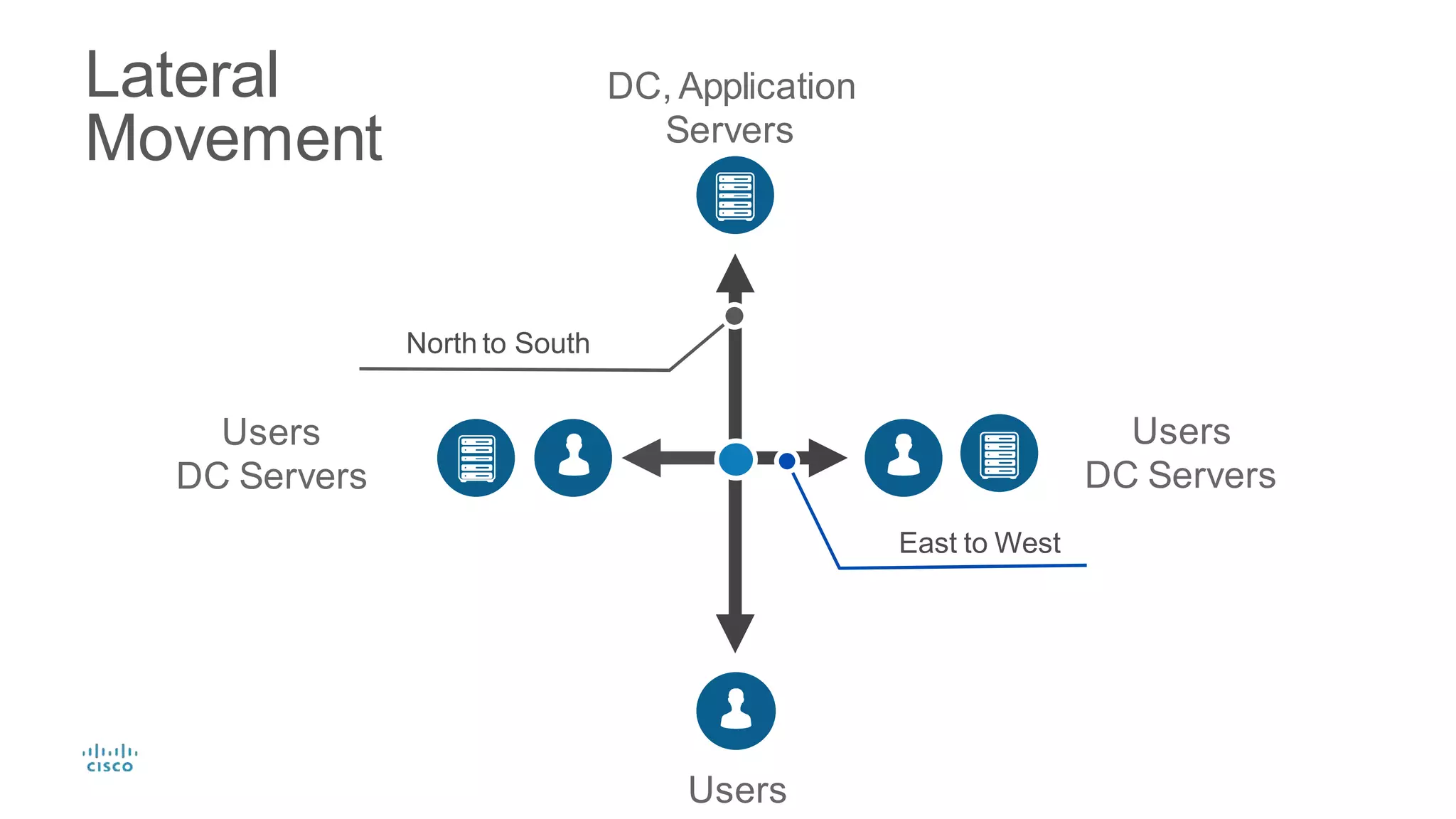
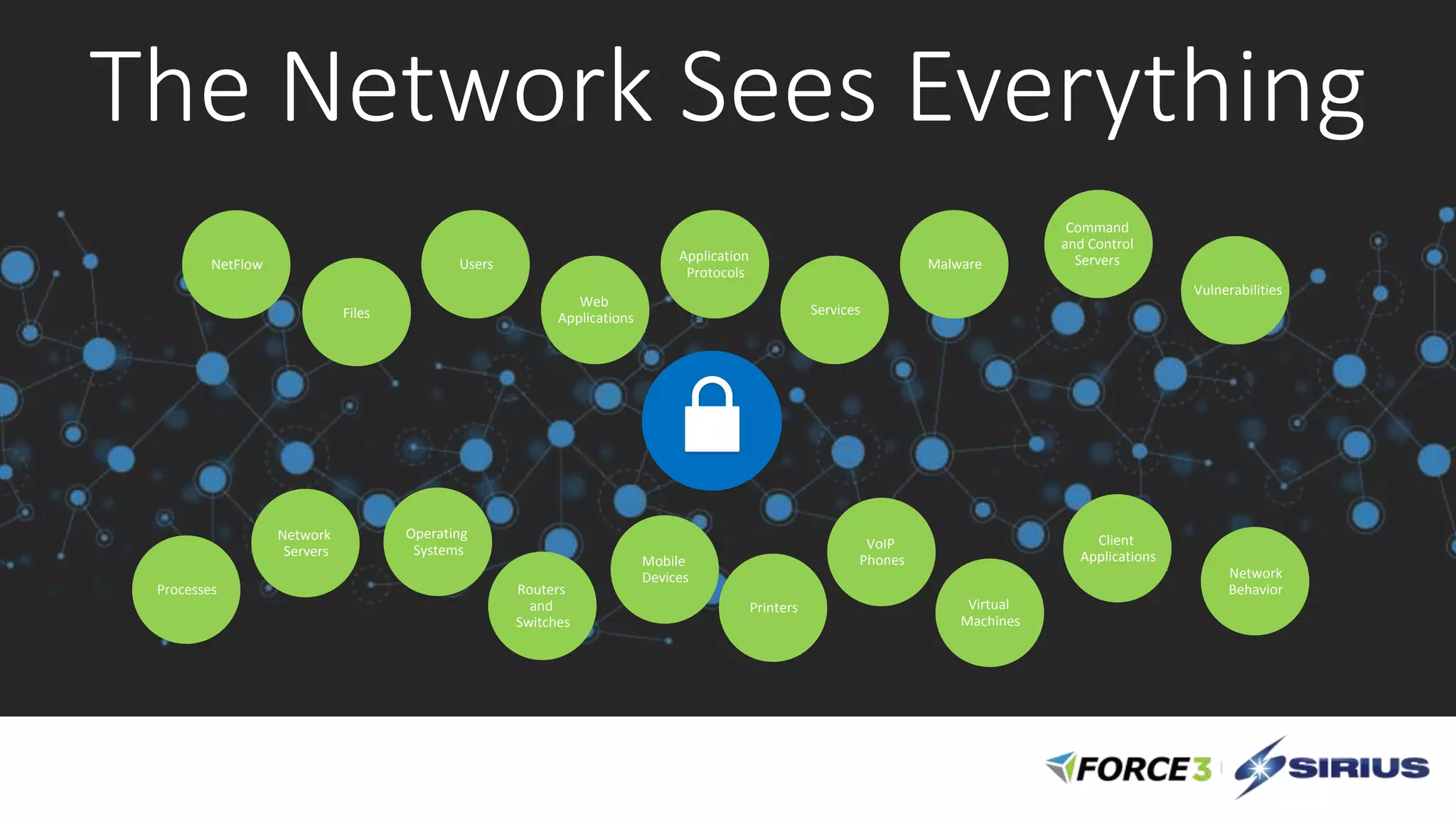
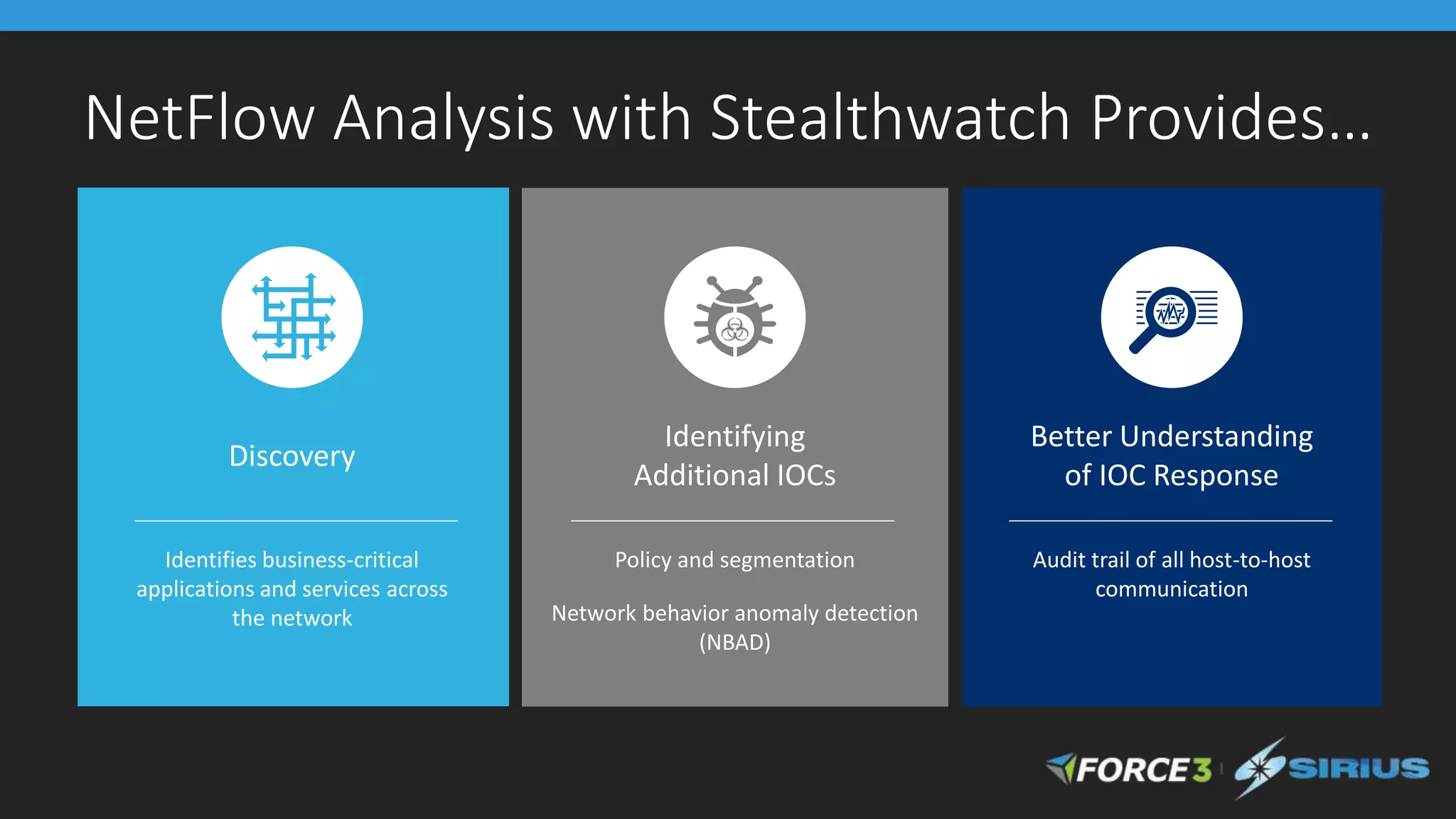
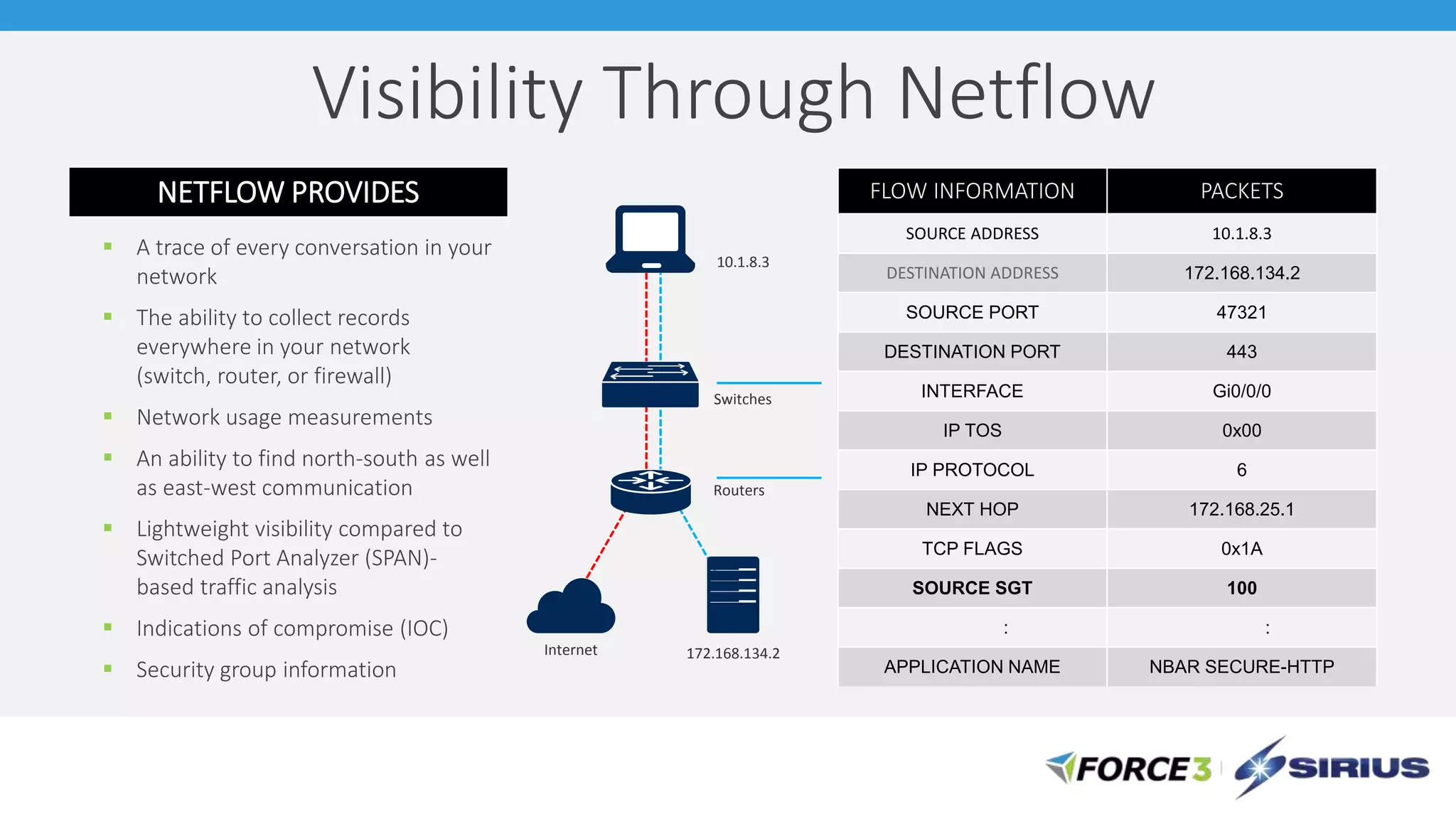
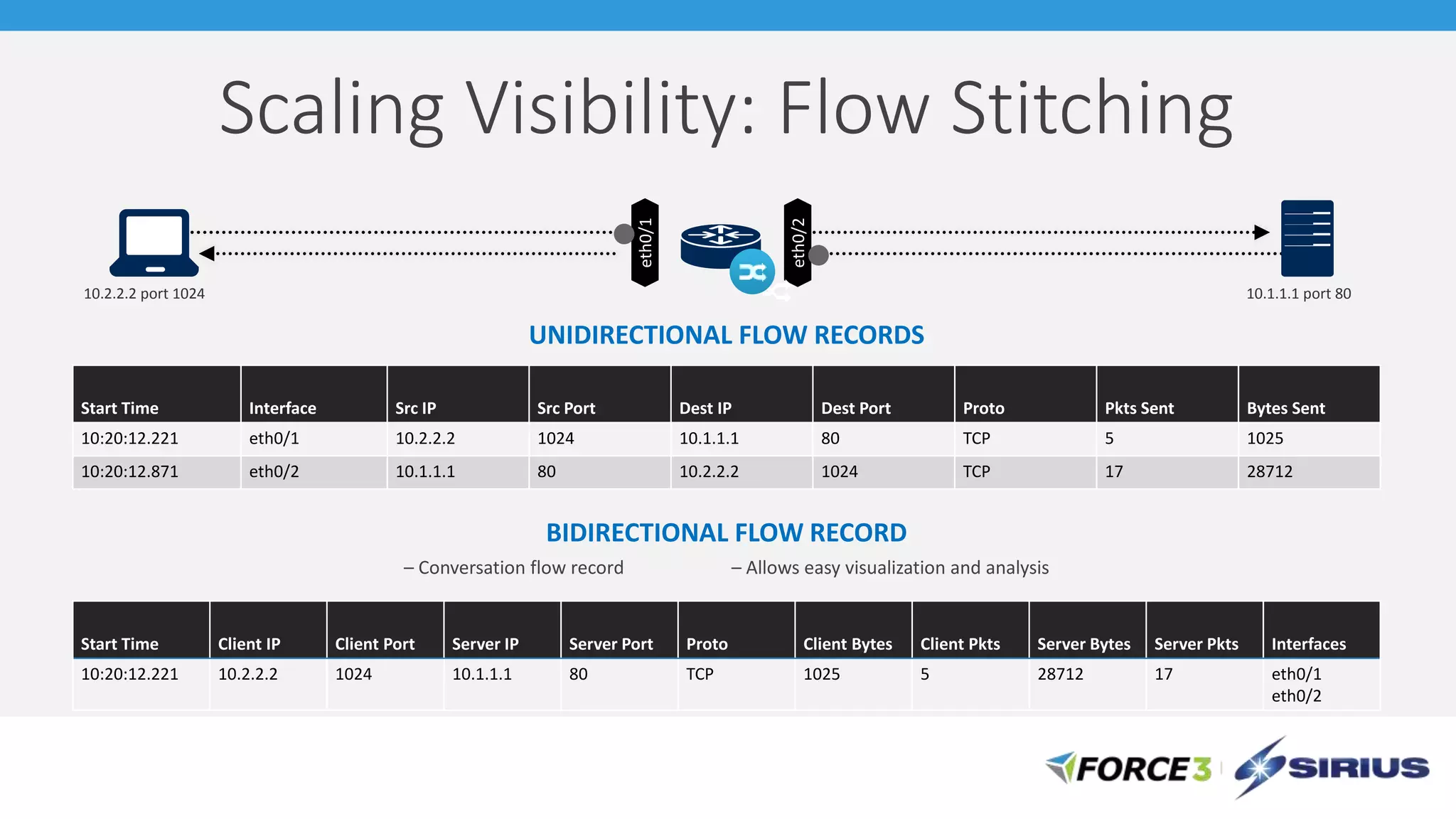
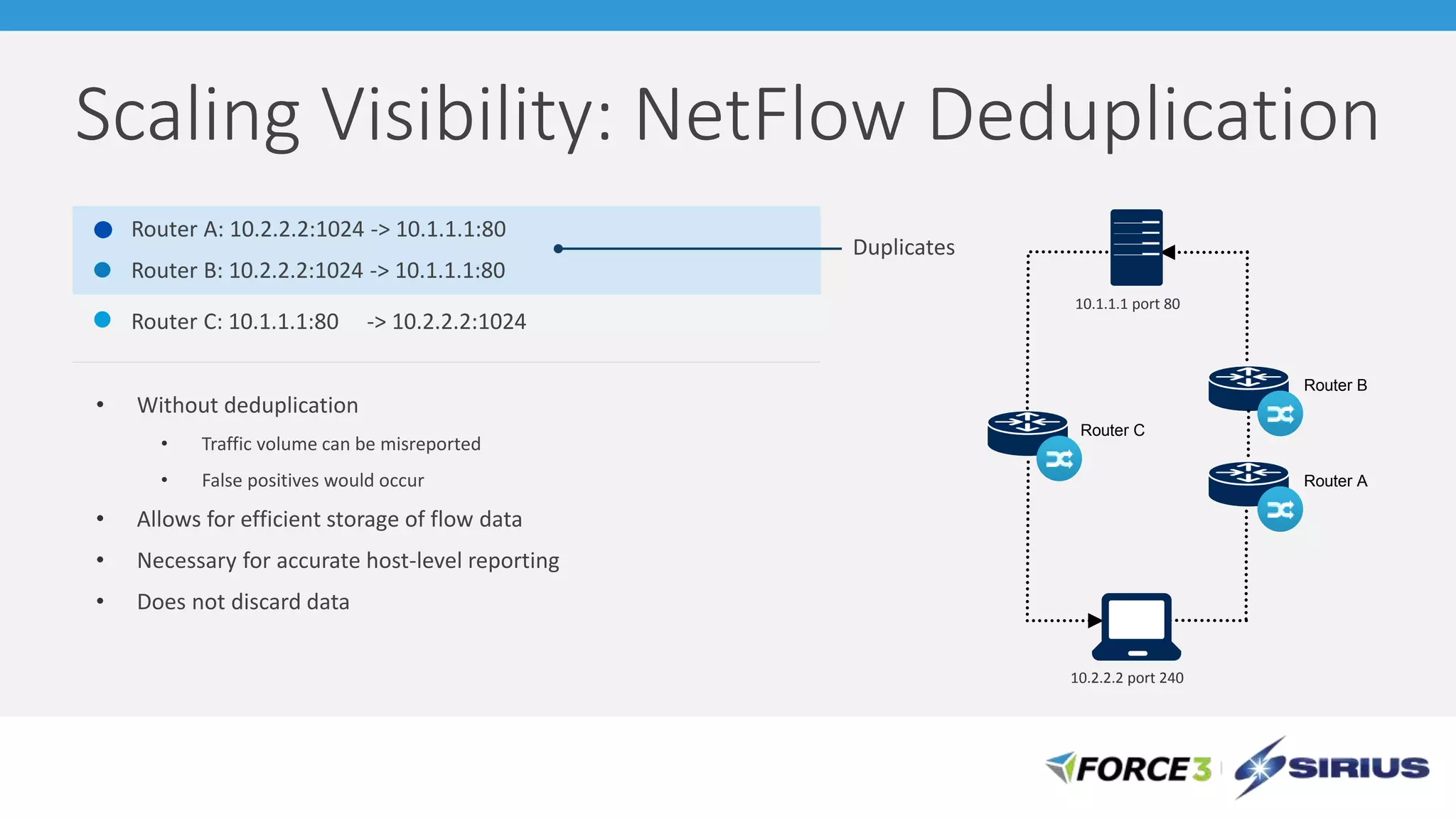
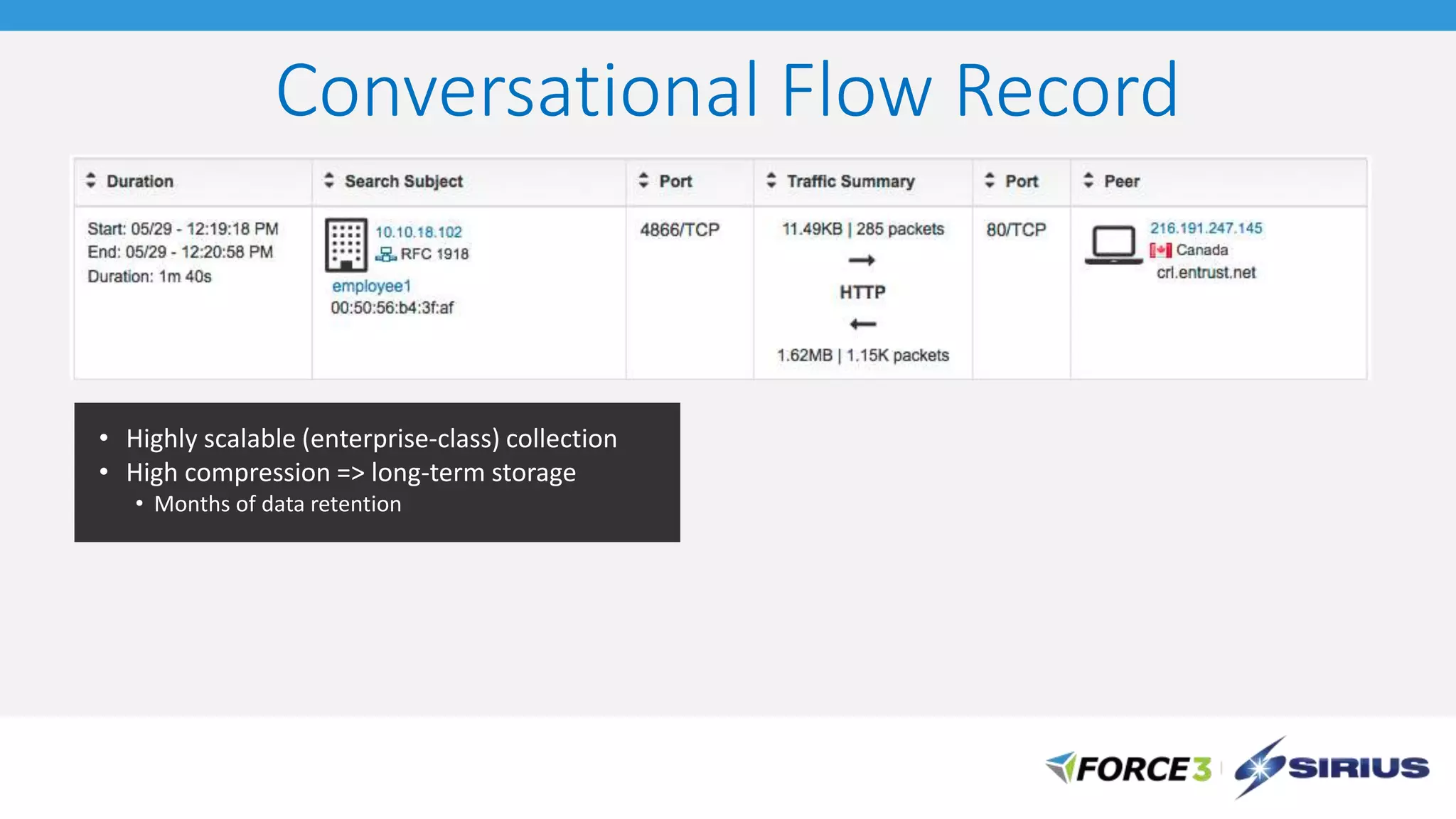
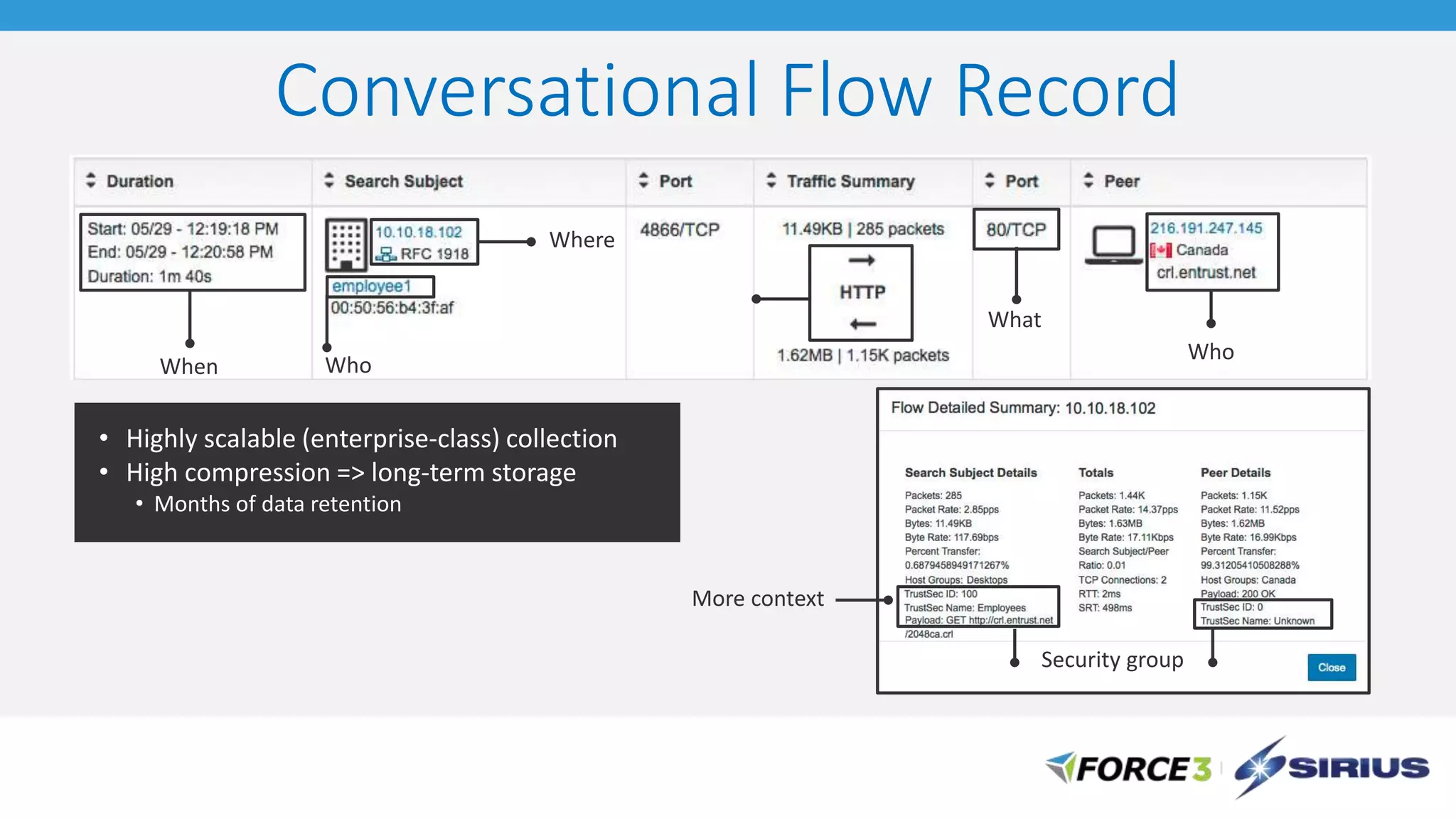
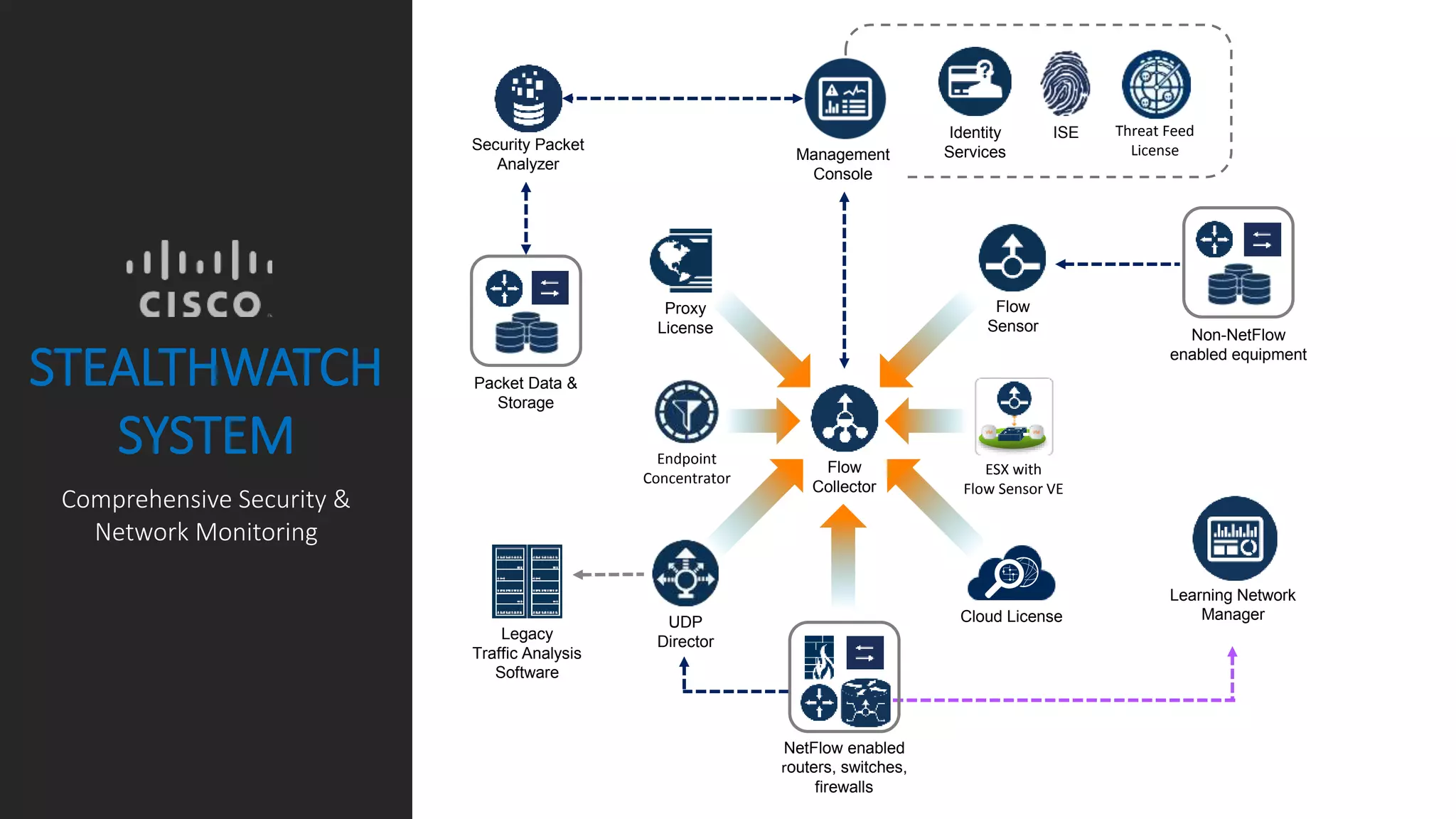
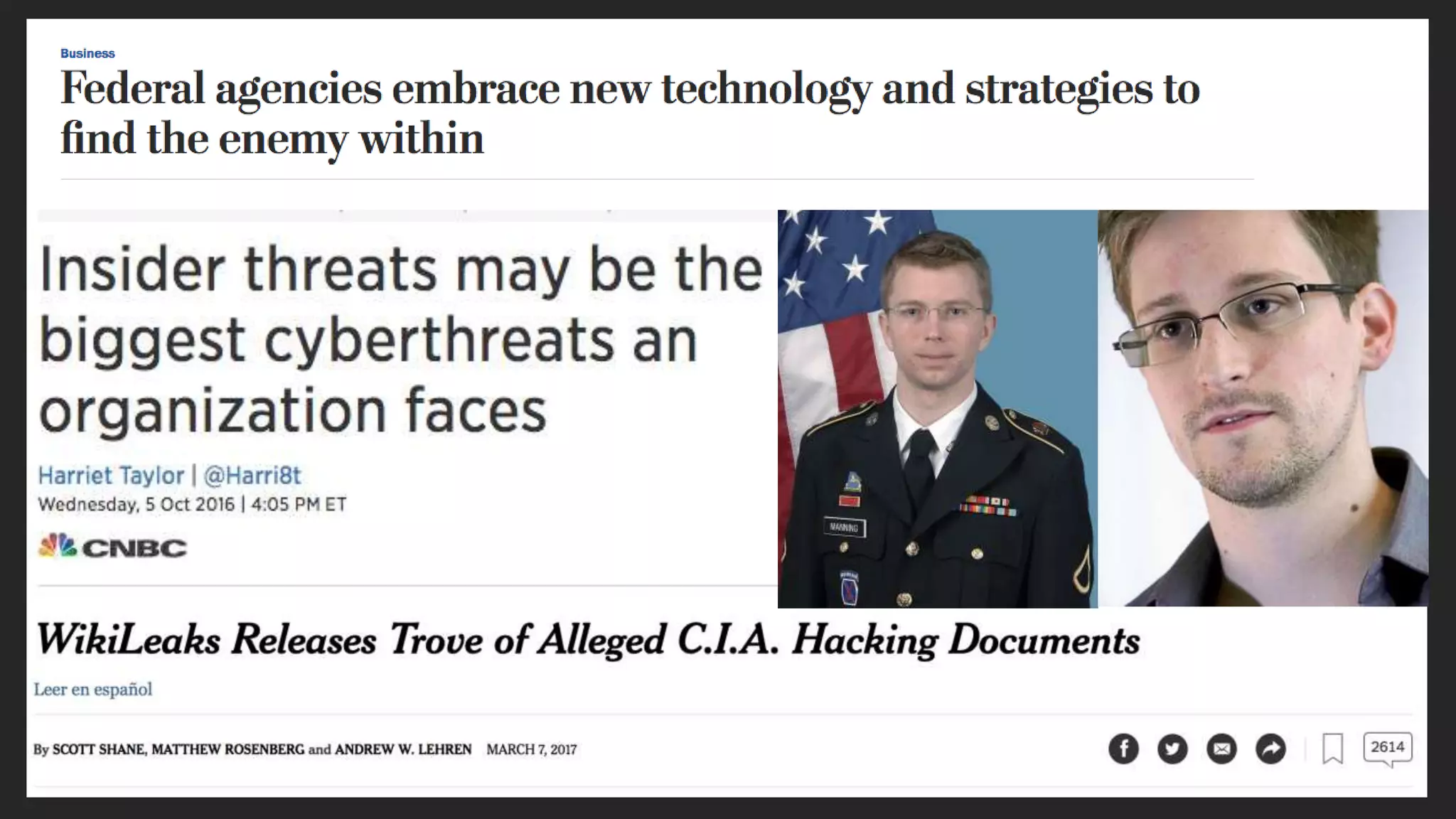
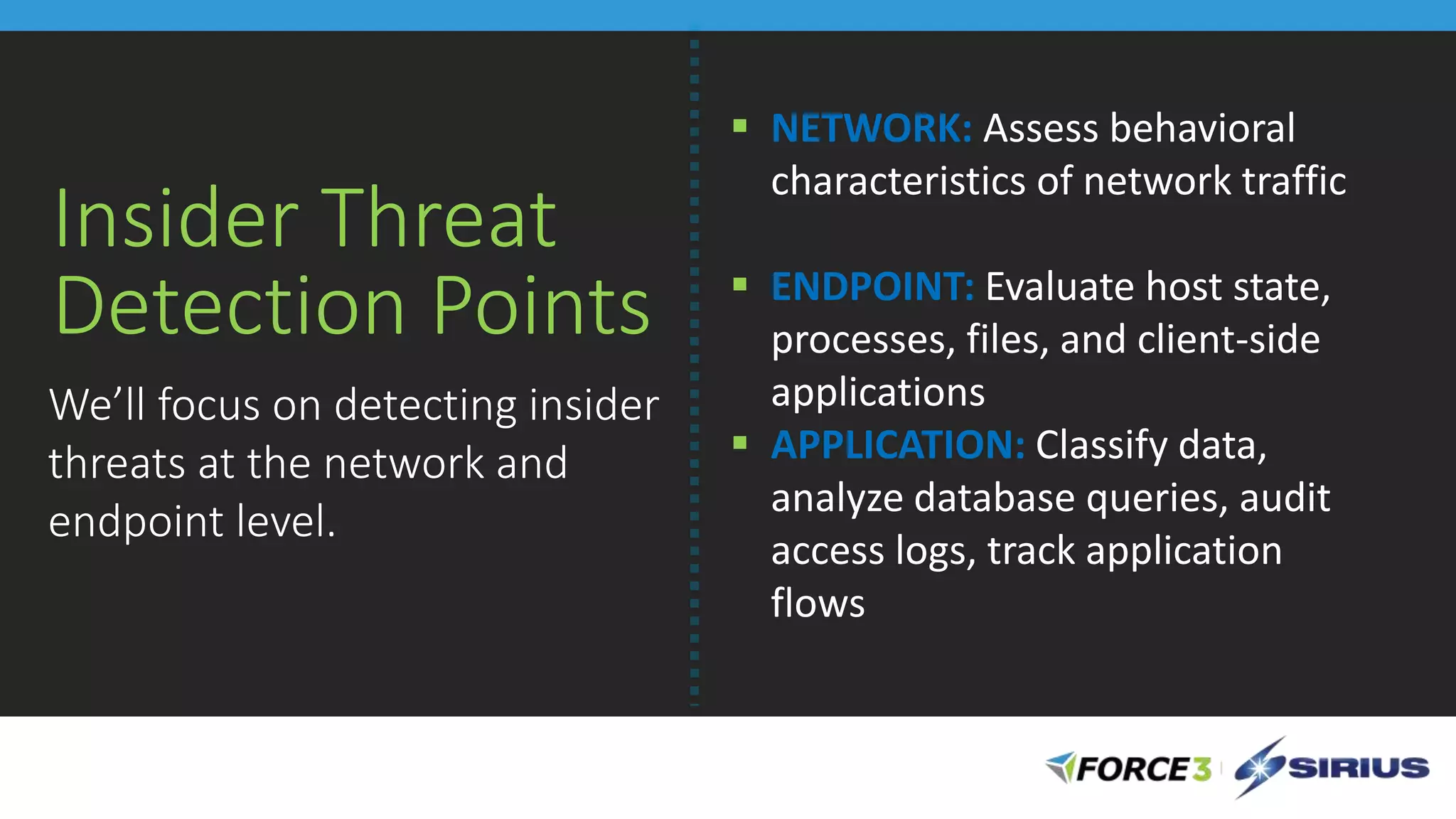
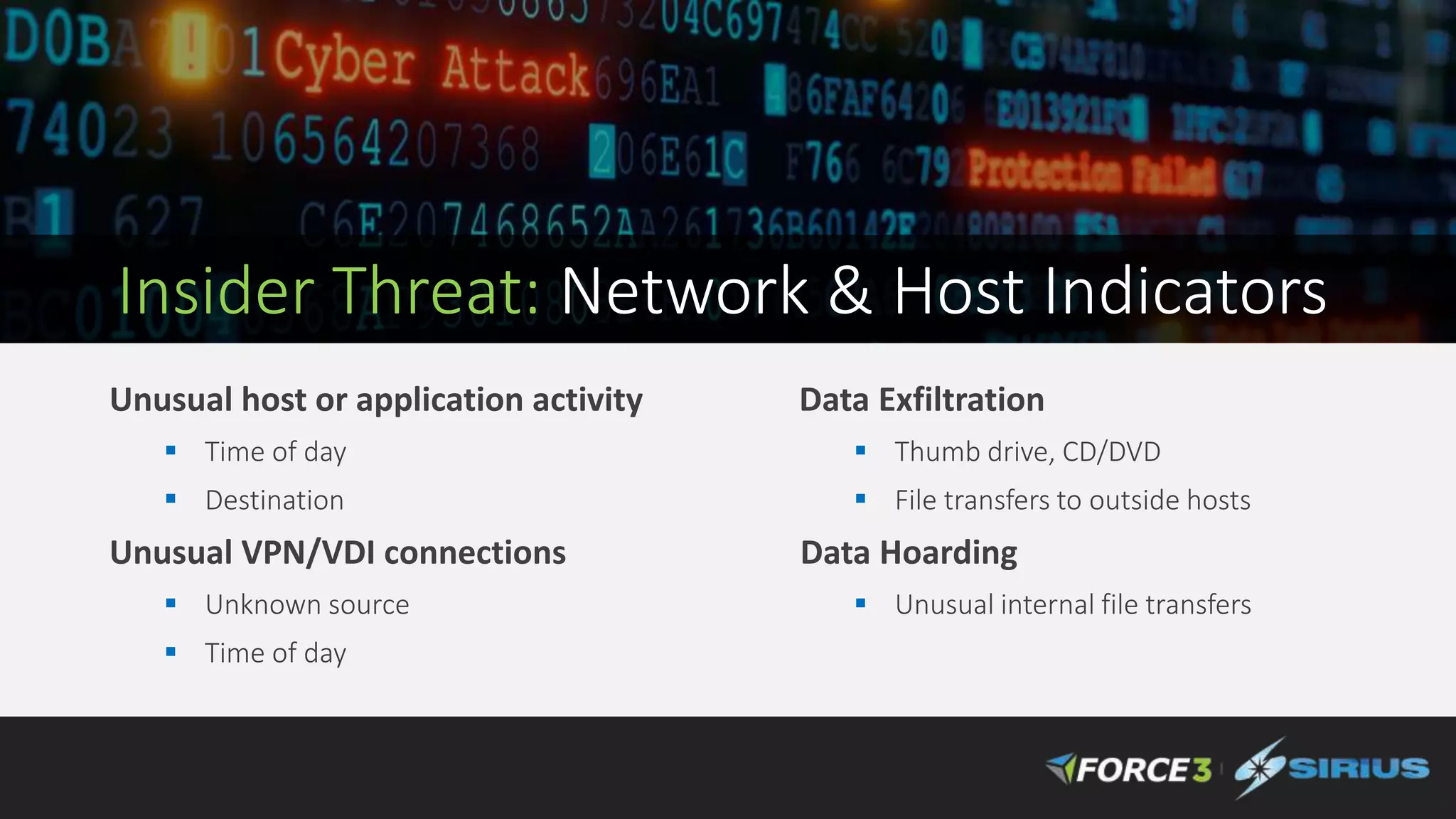
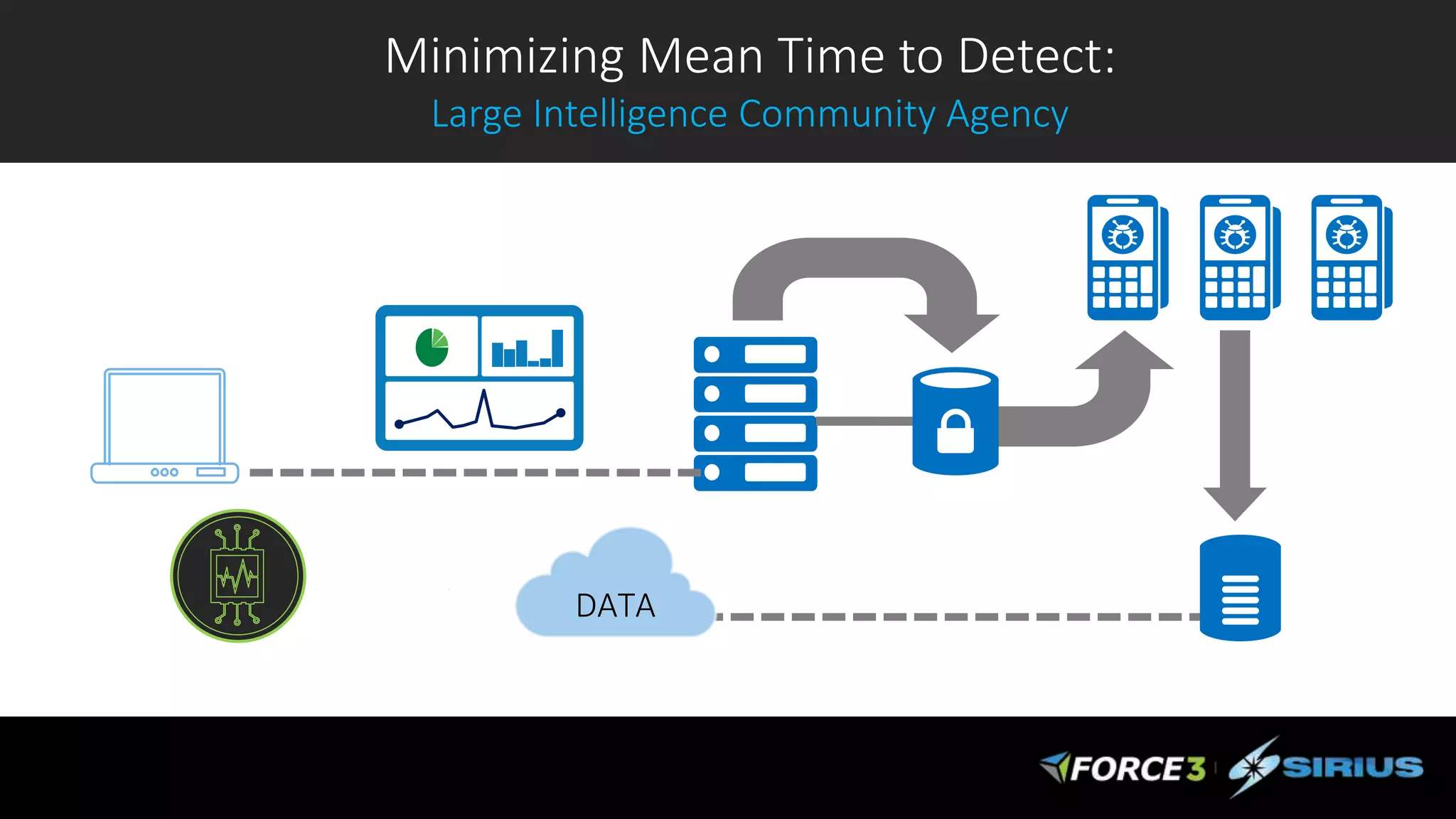
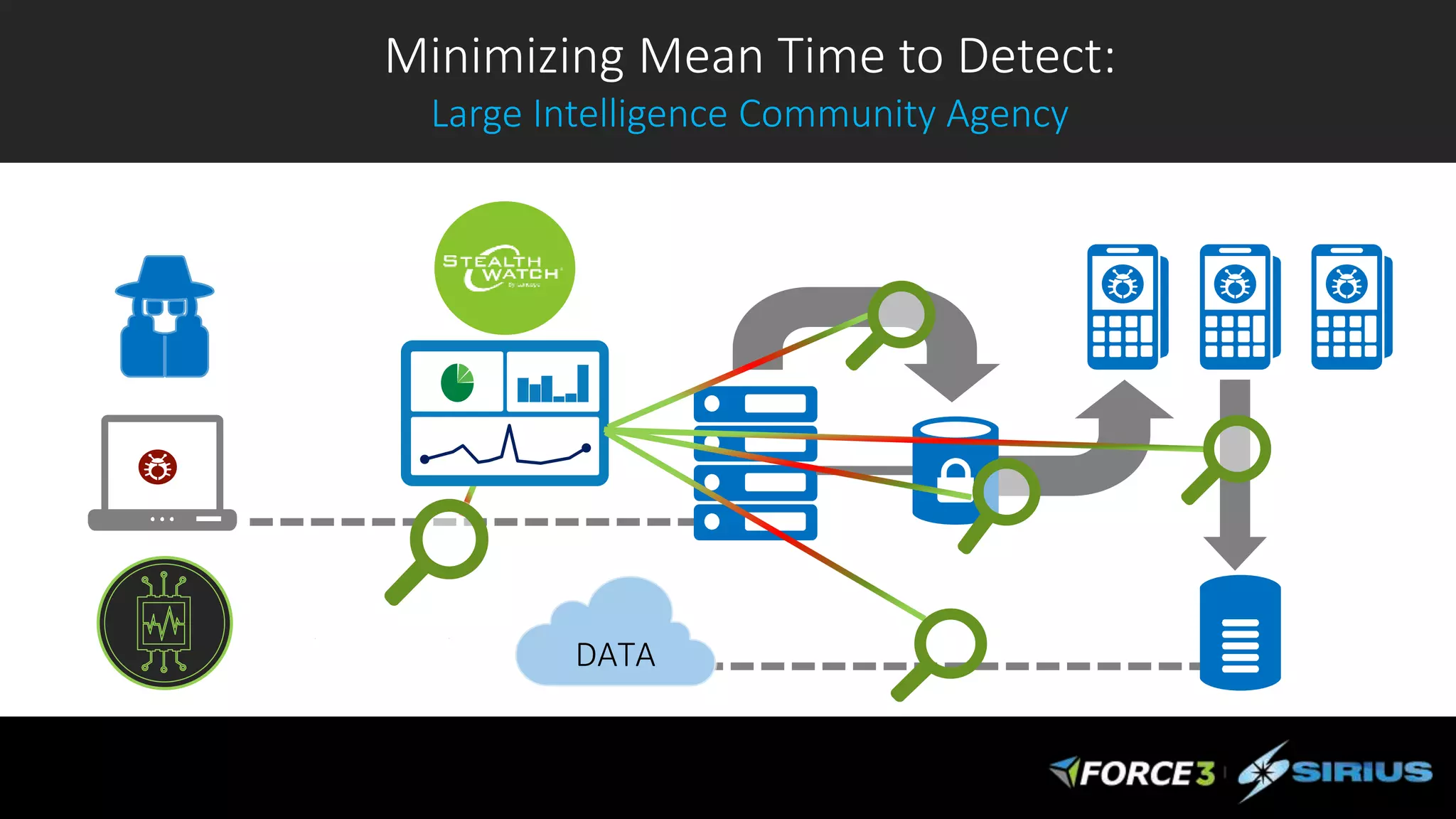
Cisco Stealthwatch provides enhanced network visibility and security analytics designed to detect insider threats and malicious activities quickly. Leveraging NetFlow analytics, it helps organizations identify threats within their networks by analyzing behavior patterns and incident detection across various infrastructure components. The document outlines the current state of security, highlighting the growing complexity of attacks and emphasizing the importance of visibility for effective threat management.