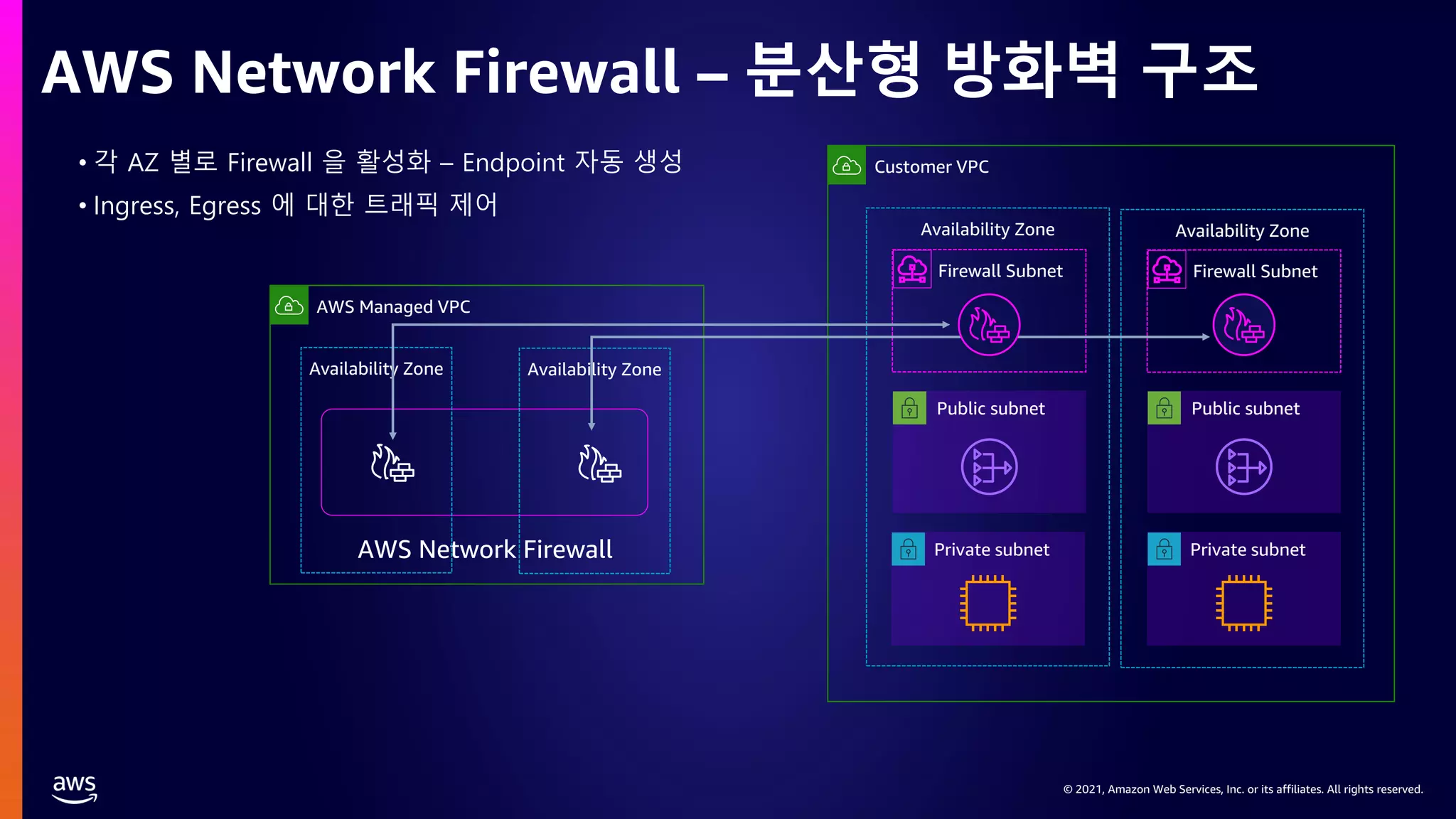
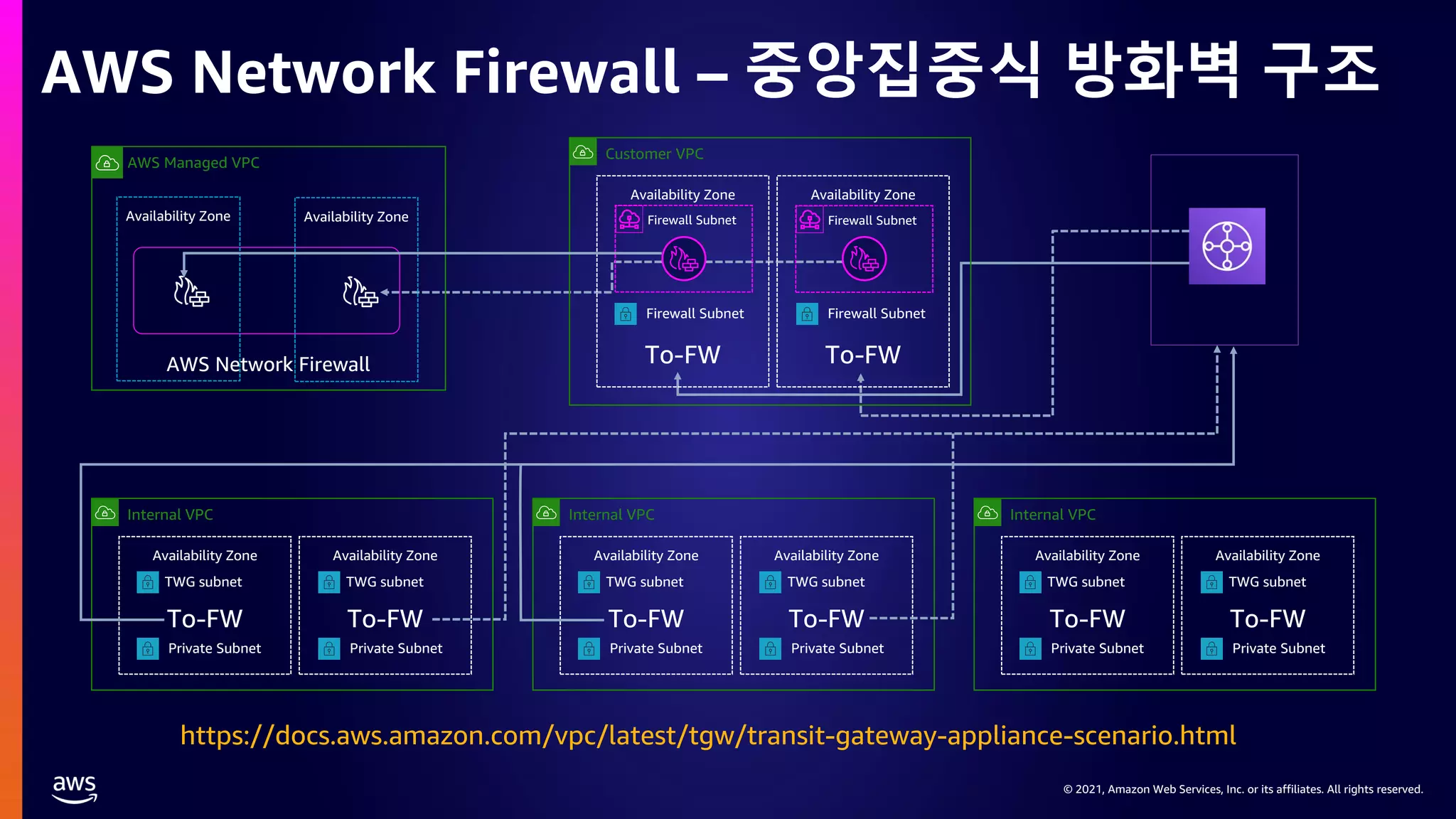
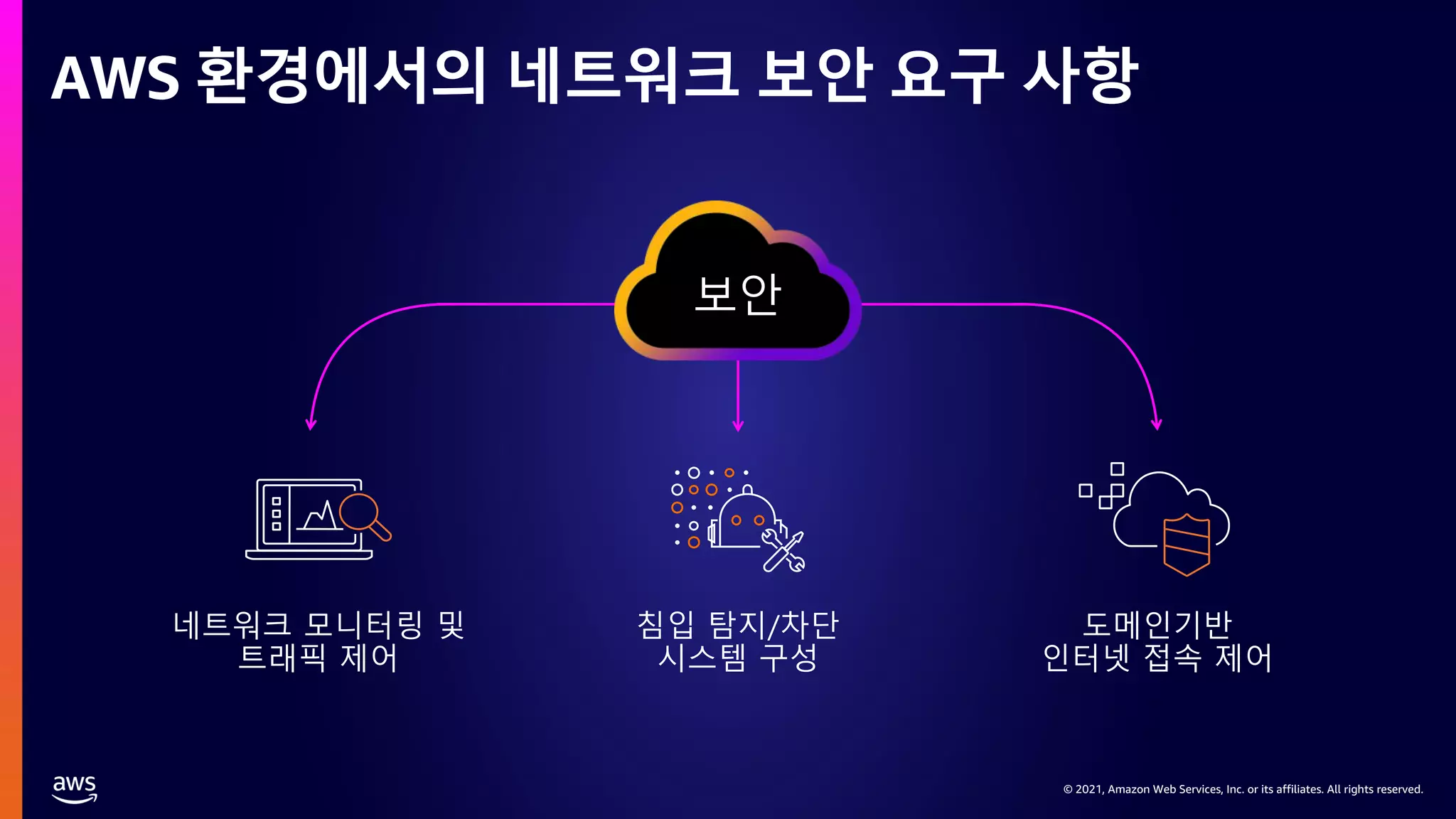
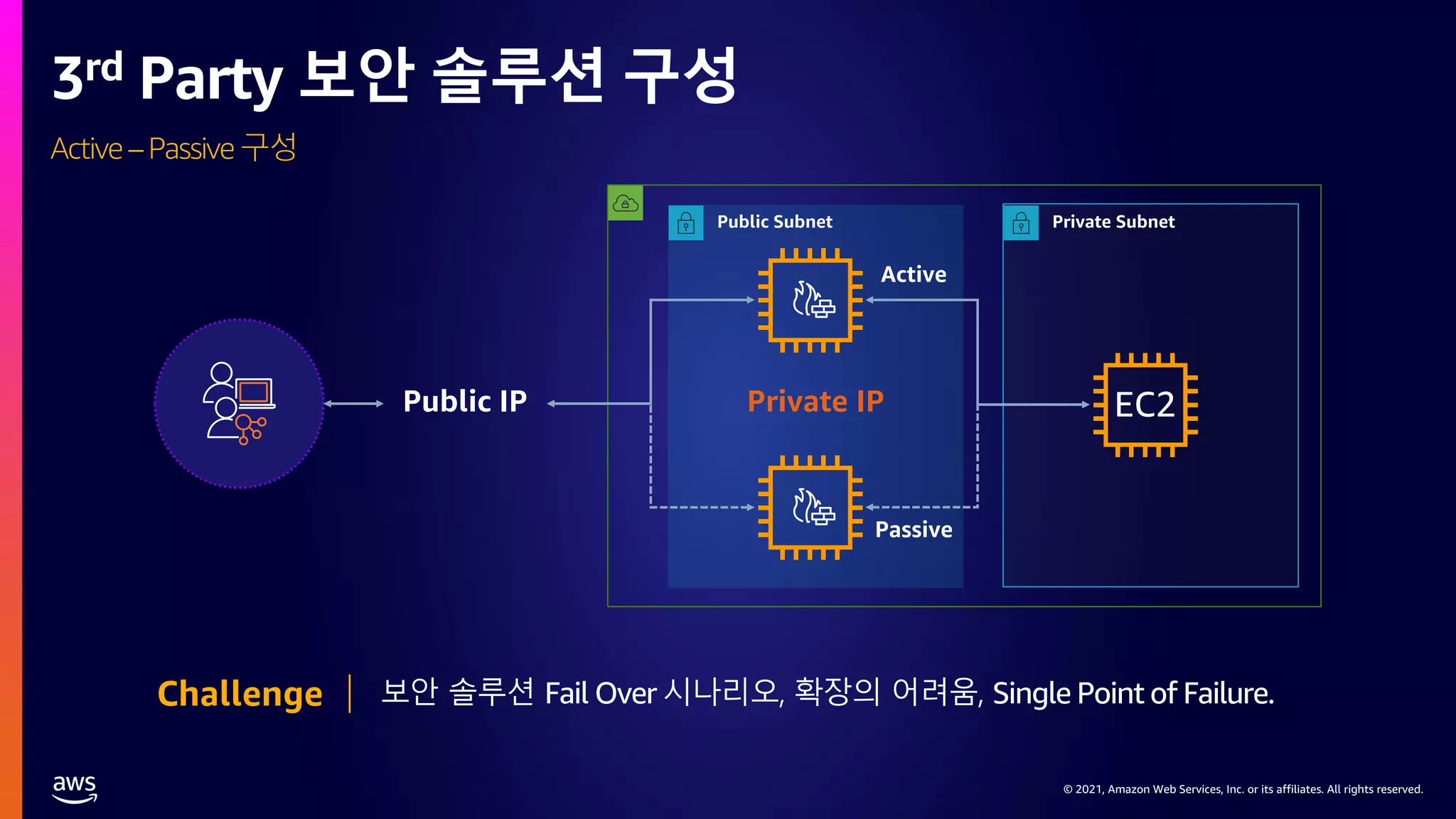
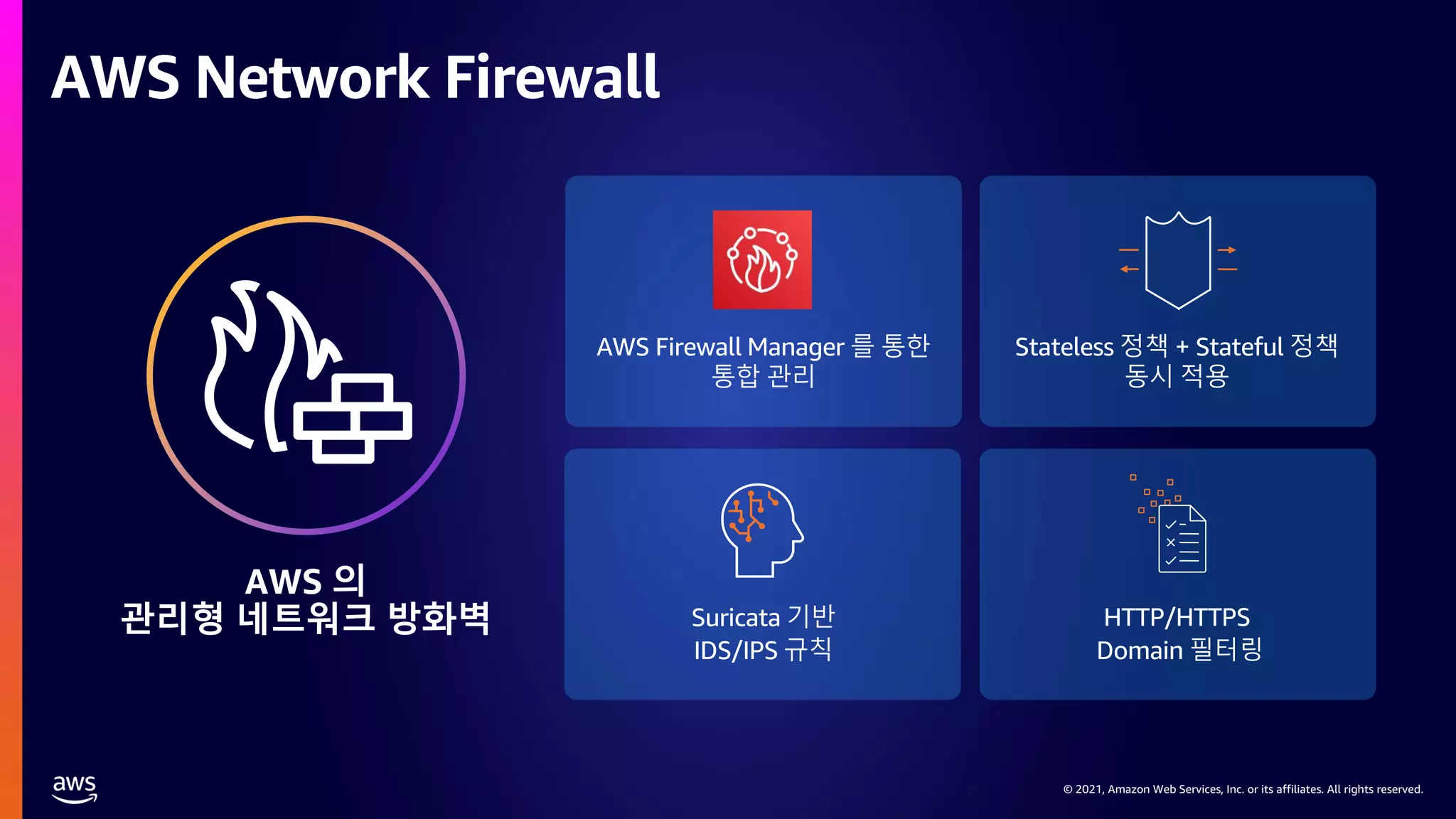
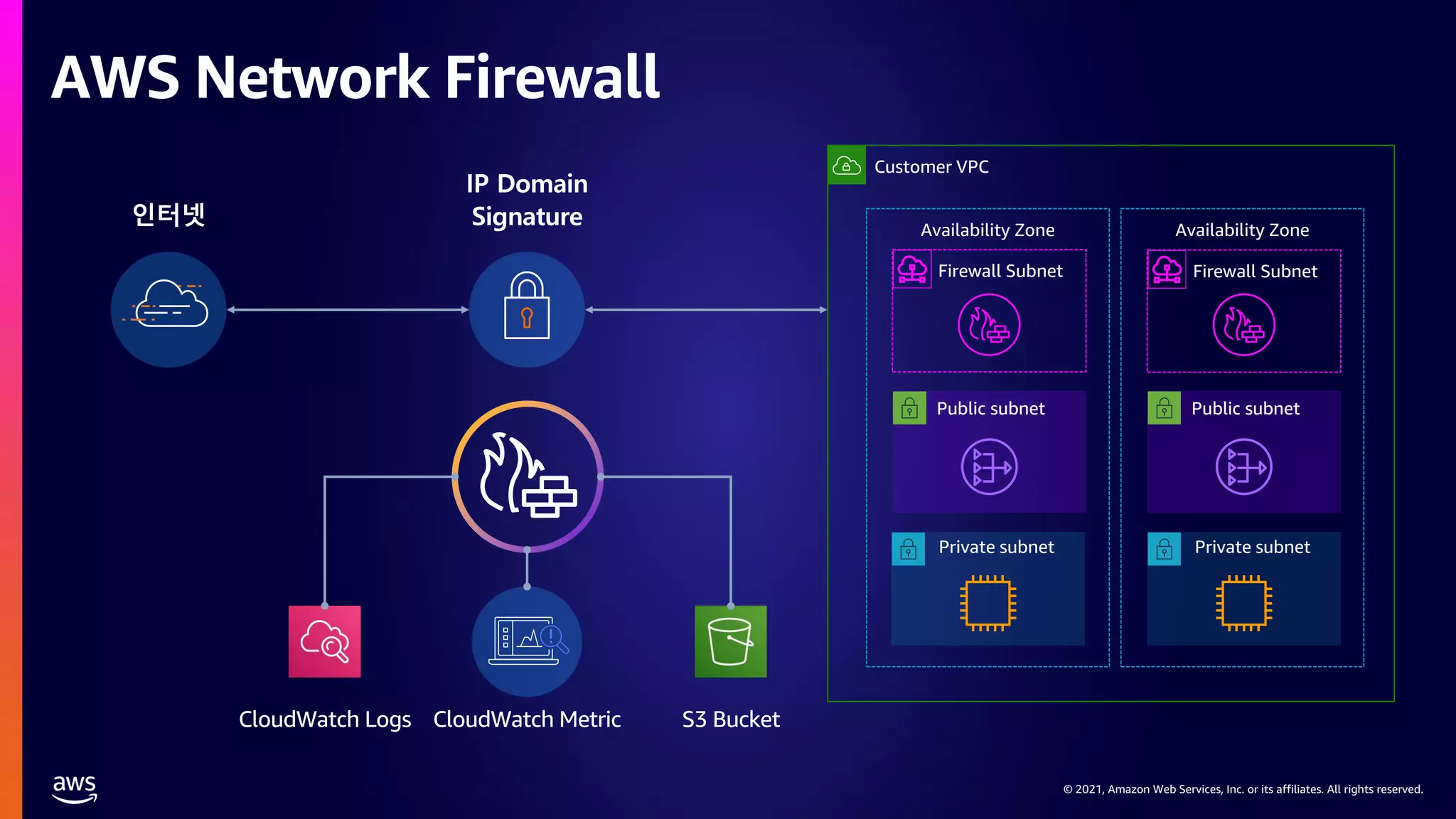
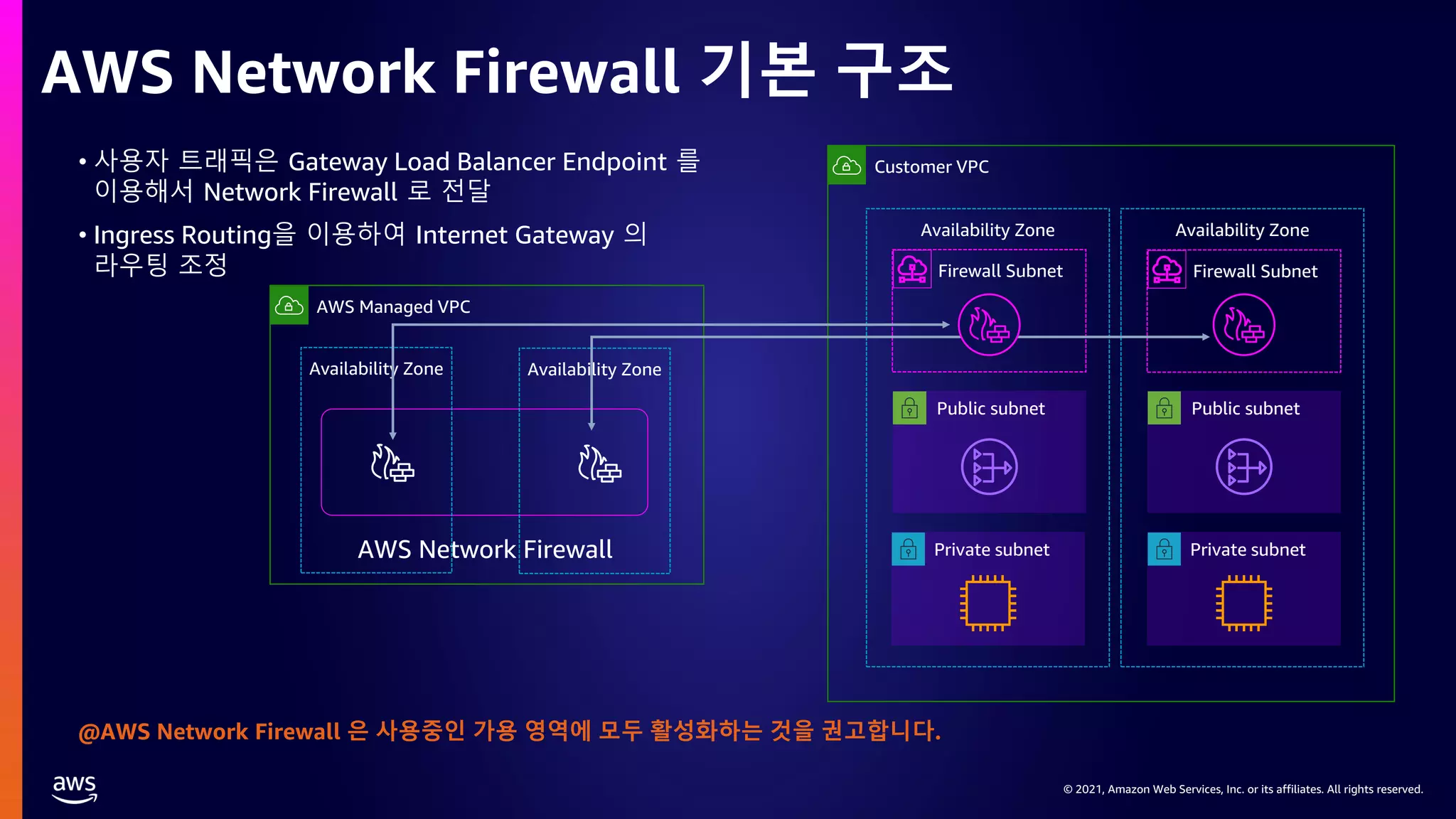
This document provides an overview of AWS network security solutions, focusing on the AWS Gateway Load Balancer and AWS Network Firewall. It discusses various configurations, routing requirements, and the application of stateless and stateful rules for securing AWS environments. Key topics include the integration of 3rd party security solutions, the structure of security rules, and best practices for achieving secure network architecture on AWS.









![© 2021, Amazon Web Services, Inc. or its affiliates. All rights reserved.
© 2021, Amazon Web Services, Inc. or its affiliates. All rights reserved.
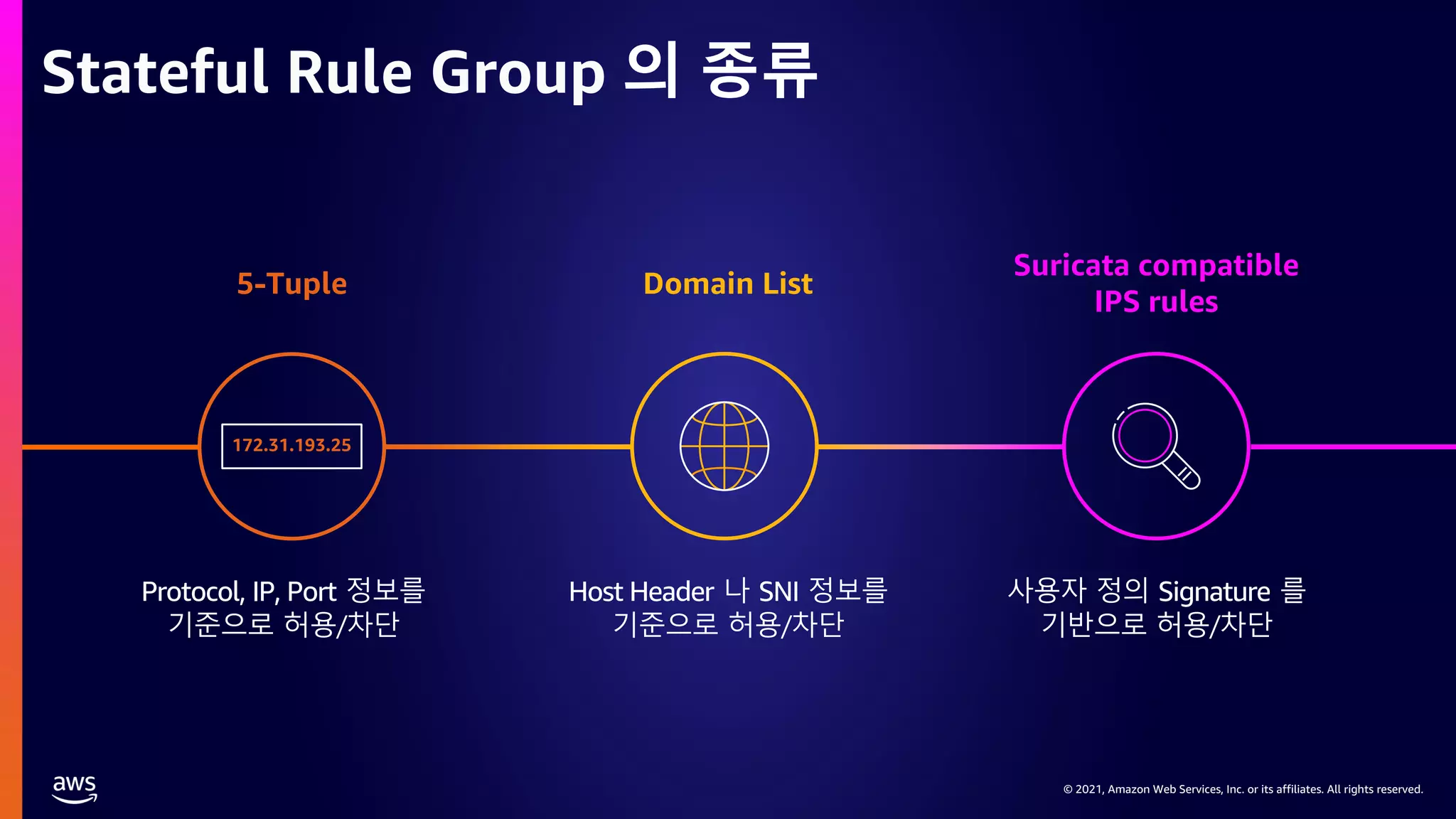
Stateless 규칙의 적용 예시
"RuleDefinition": {
"MatchAttributes": {
"Sources": [
{
"AddressDefinition": "10.1.0.0/16"
}
],
"Destinations": [
{
"AddressDefinition": "214.21.233.12/32"
},
{
"AddressDefinition": "213.32.11.91/32"
}
], "SourcePorts": [
{
"FromPort": 0,
"ToPort": 65535
}
],
"DestinationPorts": [
{
"FromPort": 80,
"ToPort": 80
}
],
"Protocols": [
6
"TCPFlags": [
{
"Flags": [
"SYN"
],
"Masks": [
"SYN",
"ACK"
]
}
]
},
"Actions": [
"aws:pass"
]
},
"Priority": 1
}
리스트 지정
가중치 적용
TCP Flag 검사
범위 지정](https://image.slidesharecdn.com/aws-210817111819/75/AWS-AWS-AWS-Summit-Seoul-2021-19-2048.jpg)
![© 2021, Amazon Web Services, Inc. or its affiliates. All rights reserved.
© 2021, Amazon Web Services, Inc. or its affiliates. All rights reserved.
Stateful 규칙의 적용 예시
"StatefulRules": [
{
"Action": "DROP",
"Header": {
"Protocol": "ICMP",
"Source": "Any",
"SourcePort": "Any",
"Direction": "FORWARD",
"Destination": "10.0.0.0/16",
"DestinationPort": "Any"
},
"RuleOptions": [
{
"Keyword": "sid:1"
}
]
"RulesSource": {
"RulesSourceList": {
"Targets": [
".google.com"
],
"TargetTypes": [
"HTTP_HOST",
"TLS_SNI"
],
"GeneratedRulesType": "ALLOWLIST"
}
}
"RuleGroup": {
"RulesSource": {
"RulesString": "drop tcp any any -> any any (msg:"Drop TCP Traffic"; flow:from_client, established;
sid:1000;)"
}
}
Domain 검사
Signature 검사
IP 검사](https://image.slidesharecdn.com/aws-210817111819/75/AWS-AWS-AWS-Summit-Seoul-2021-21-2048.jpg)


![© 2021, Amazon Web Services, Inc. or its affiliates. All rights reserved.
© 2021, Amazon Web Services, Inc. or its affiliates. All rights reserved.
변수를 이용한 IPS 규칙 생성
{
"RuleVariables": {
"IPSets": {
"HTTP_SERVERS": {
"Definition": [
"10.0.2.0/24",
"10.0.1.19"
]
}
},
"PortSets": {
"HTTP_PORTS": {
"Definition": ["80", "8080"]
}
}
},
"RulesSource": {
"RulesString": "alert tcp $EXTERNAL_NET any -> $HTTP_SERVERS
$HTTP_PORTS (msg:".htpasswd access attempt";
flow:to_server,established; content:".htpasswd"; nocase; sid:210503;
rev:1;)"
}
}
AWS CLI = aws network-firewall create-rule-group --rule-group-name
"RuleVariable-Group" --type STATEFUL --rule-group file://rulefile.json --
capacity 1000
정책 요건 – 지정된 IP Group 과 Port Group 을
이용하여 IPS 규칙을 생성한 후 적용
규칙 생성 – Rule Variable 을 이용한 규칙은 AWS
CLI 를 이용하여 생성할 수 있음
참고! Rule Variable 을 이용한 규칙은 생성 이후
Rule Variable 값을 Management Console 에서는
확인할 수 없으며 AWS CLI 를 이용하여 확인 가능](https://image.slidesharecdn.com/aws-210817111819/75/AWS-AWS-AWS-Summit-Seoul-2021-28-2048.jpg)