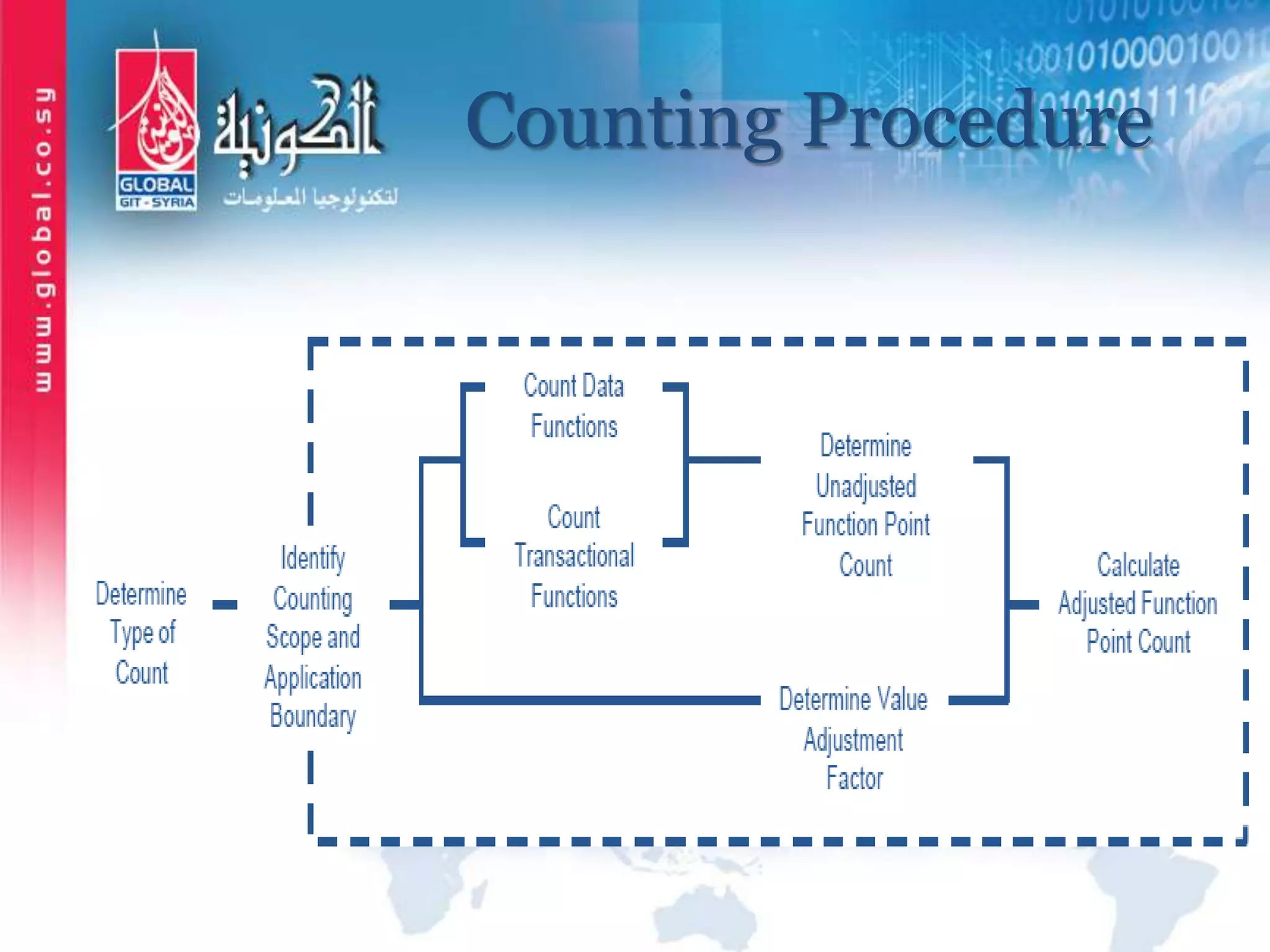
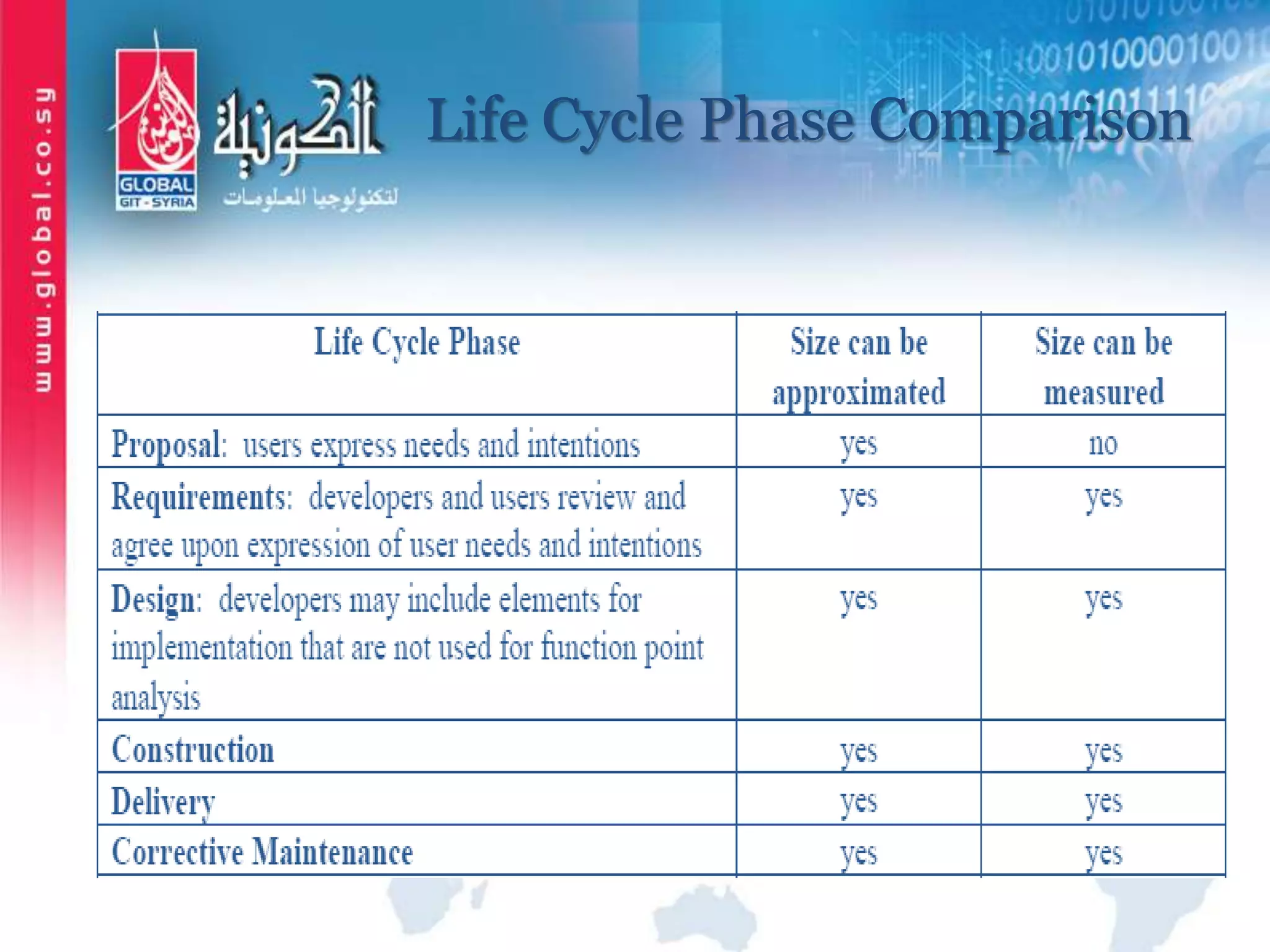
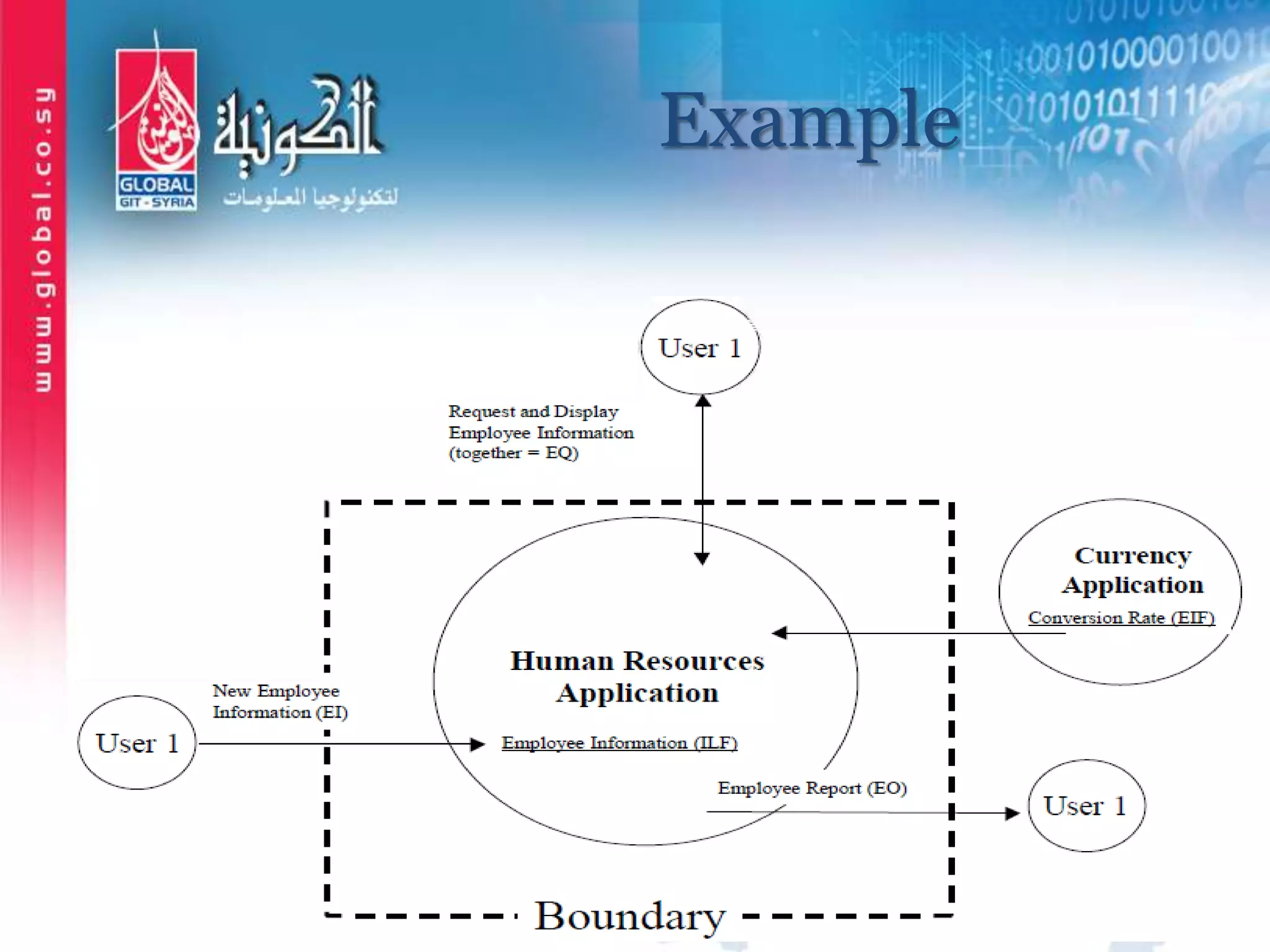
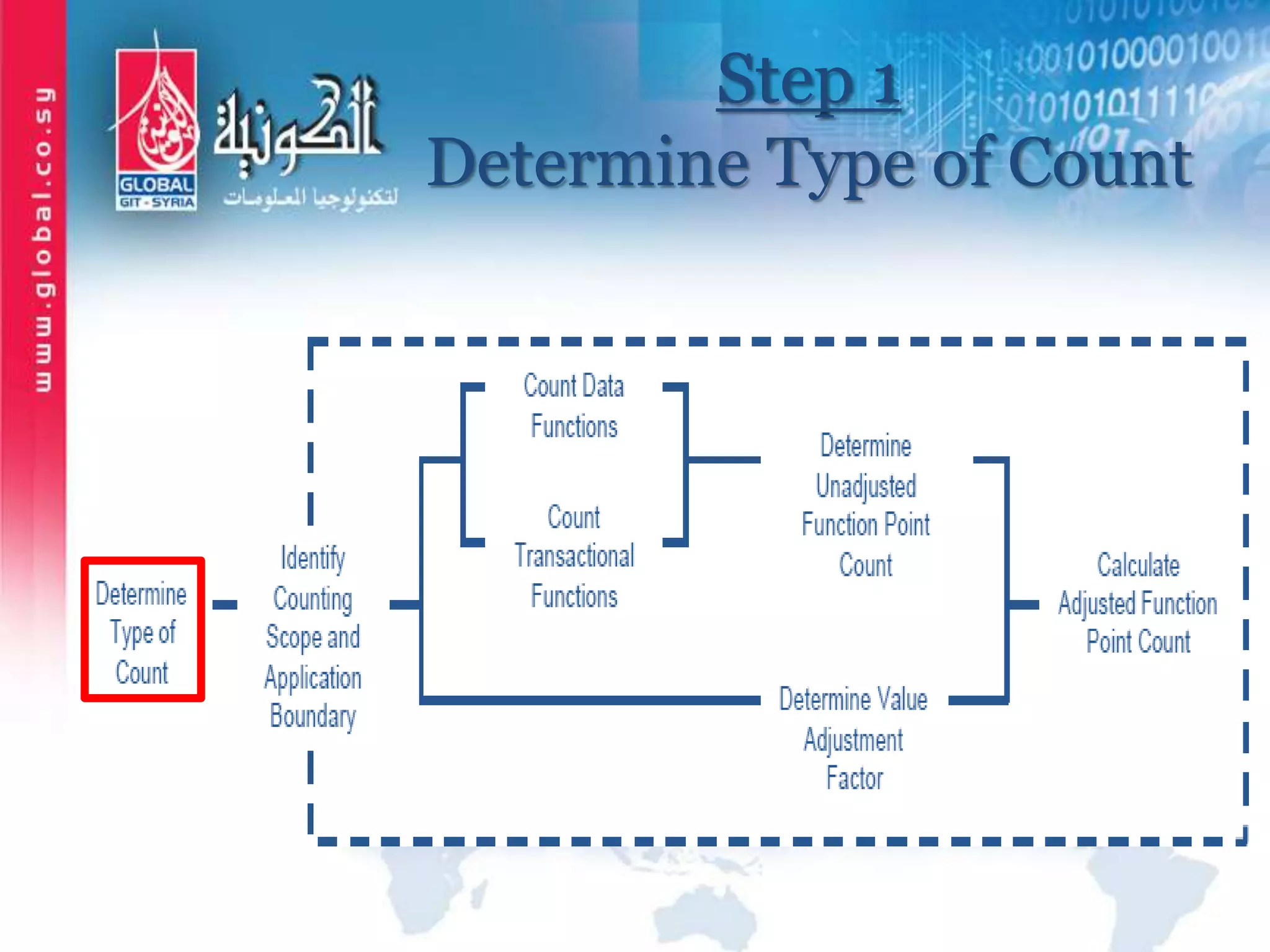
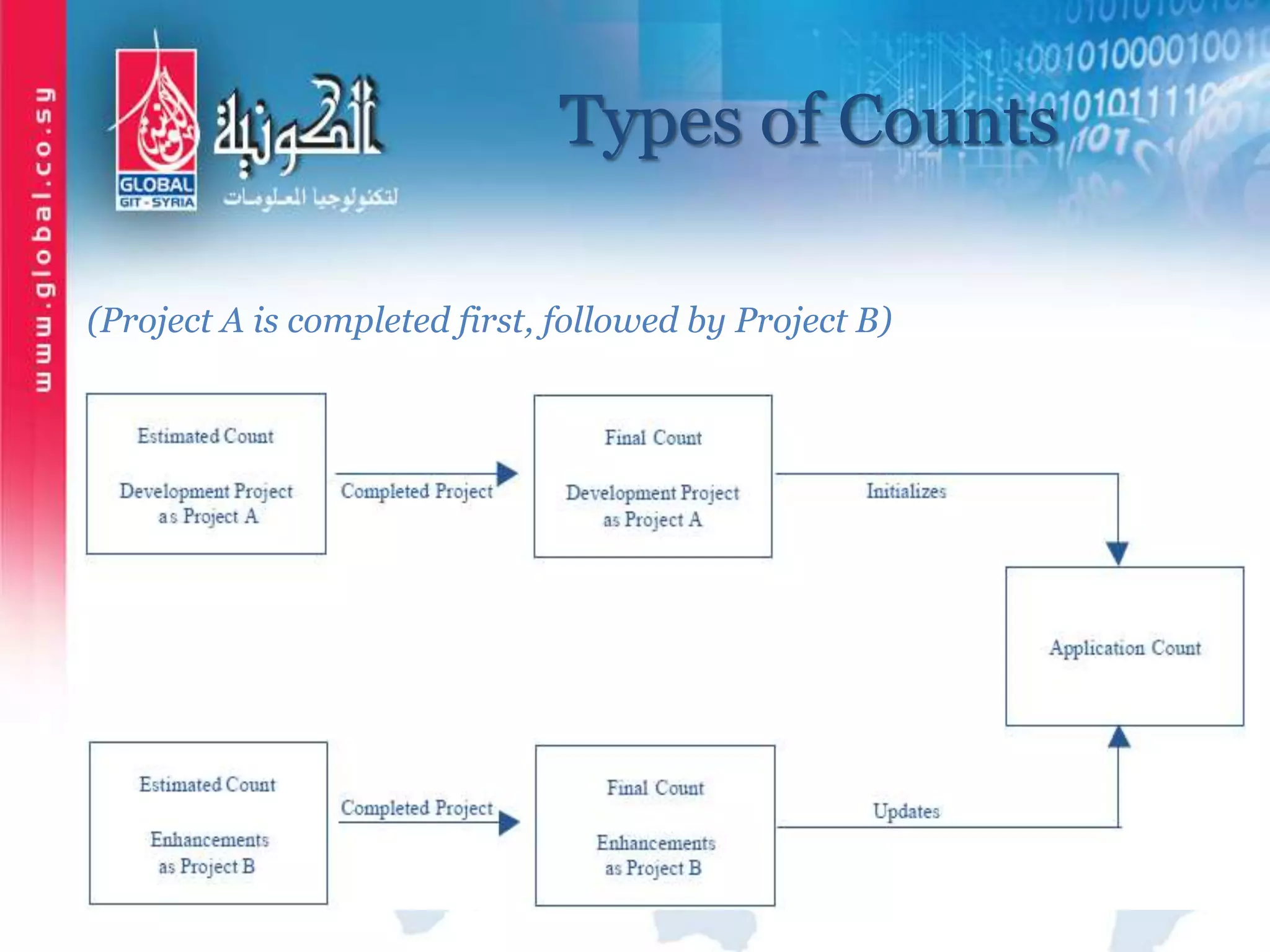
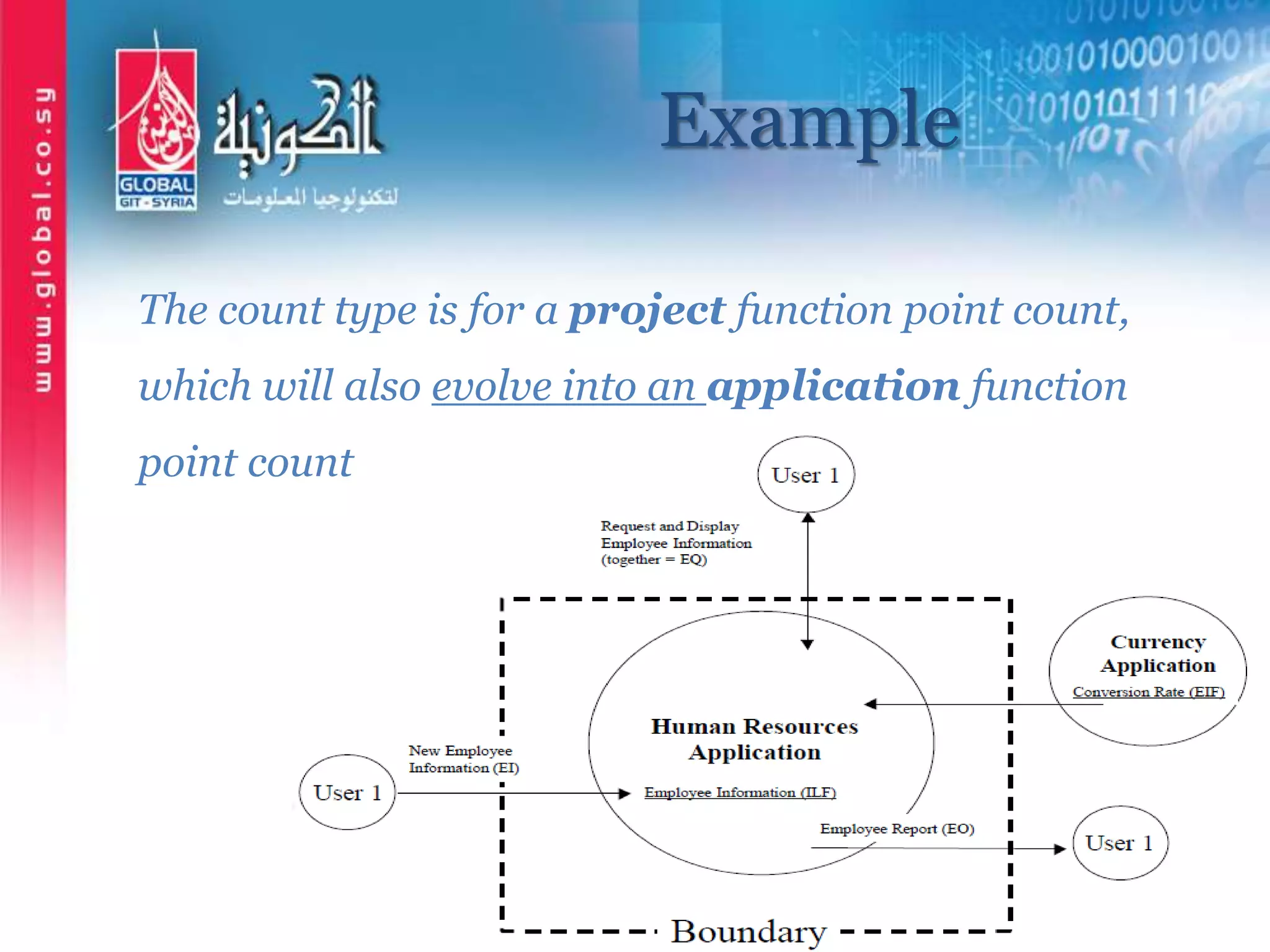
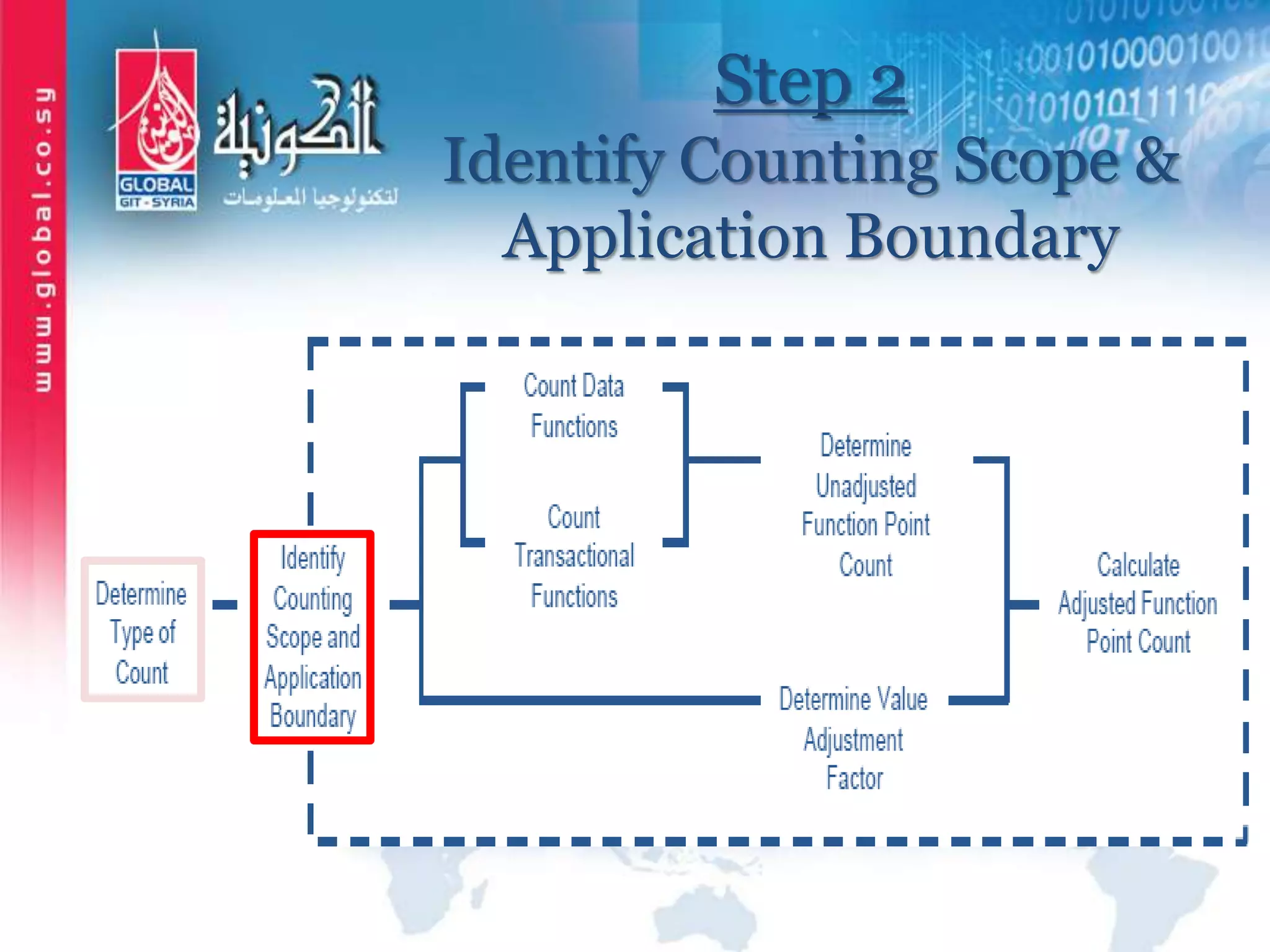
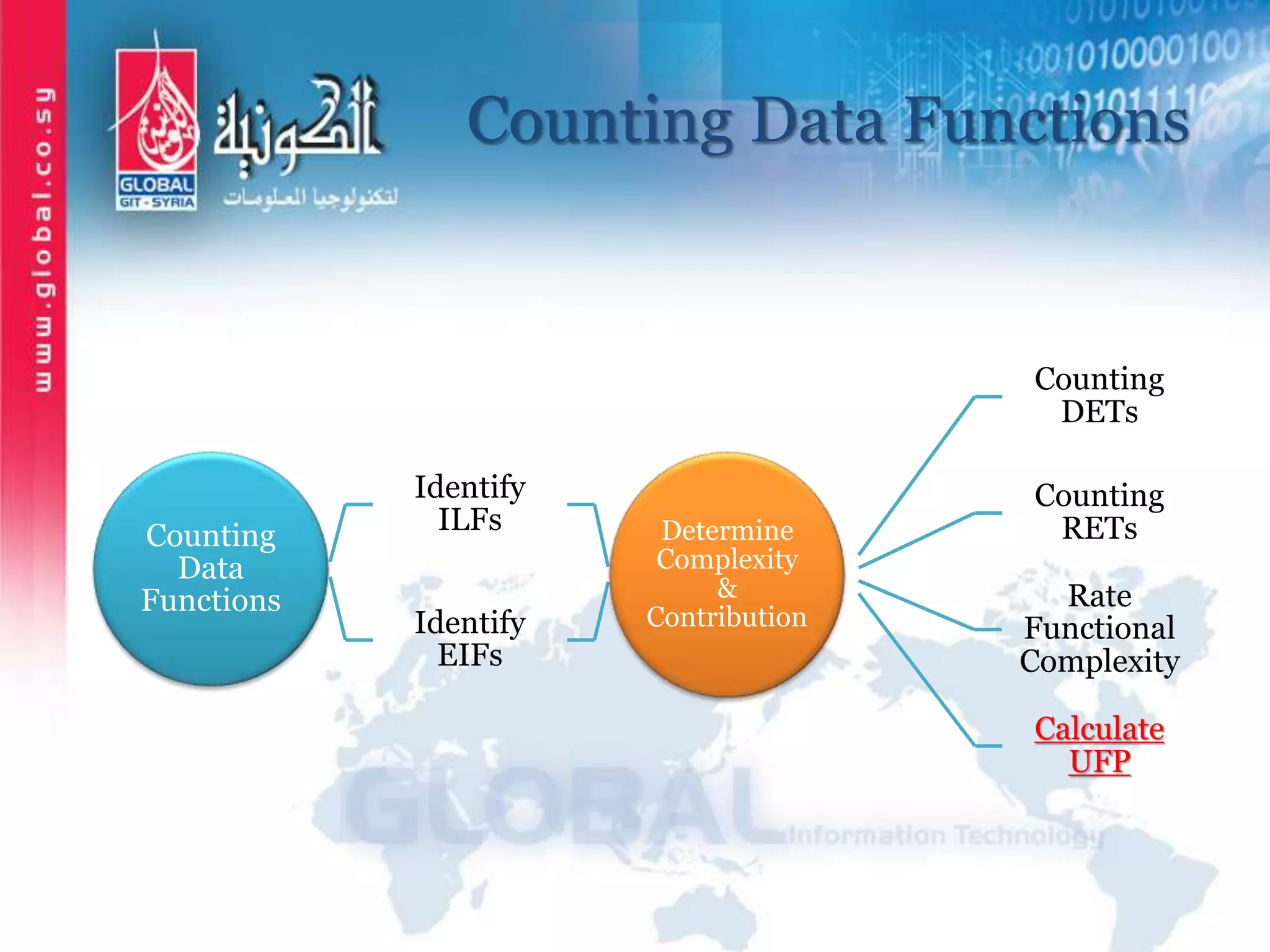
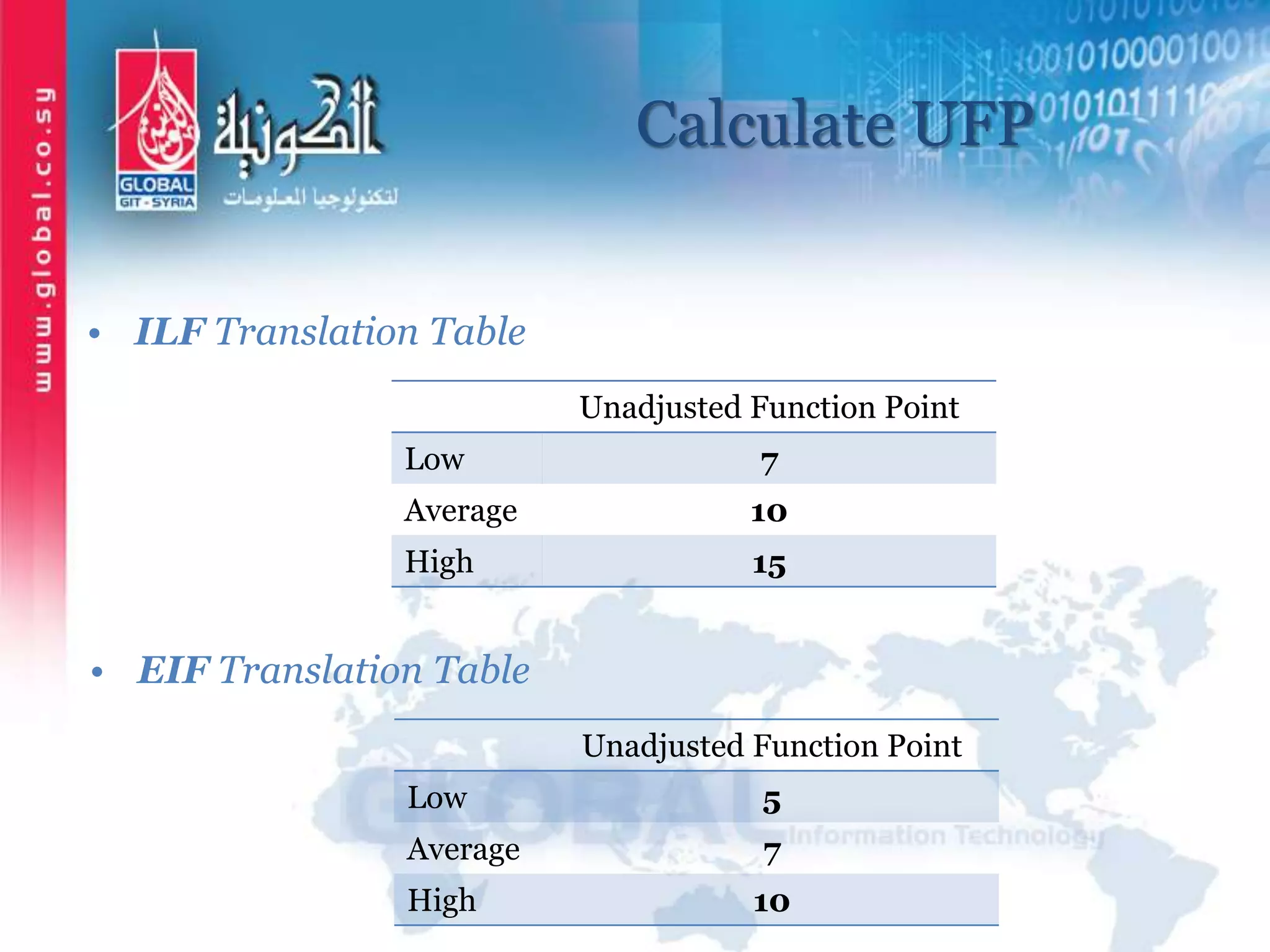
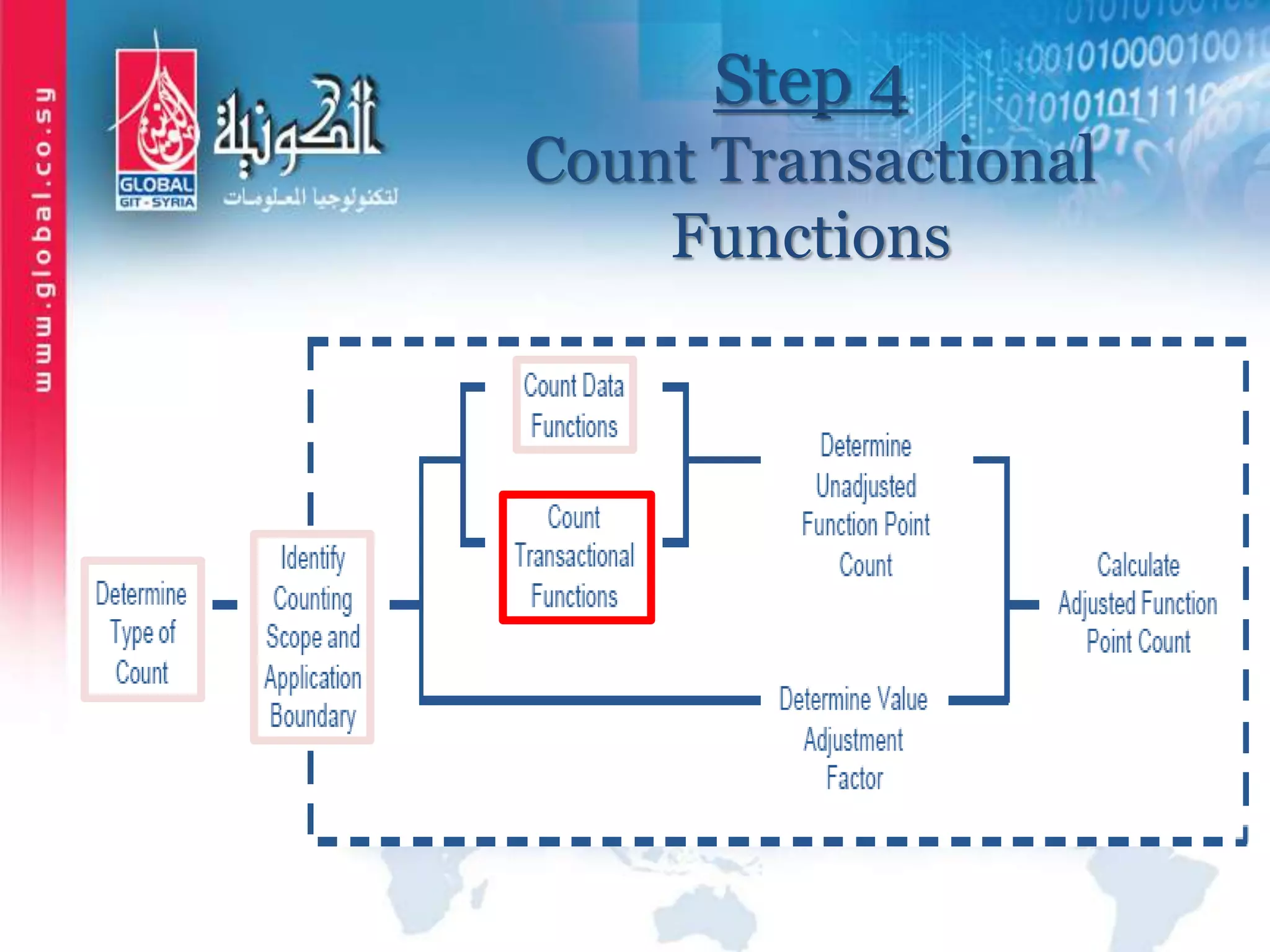
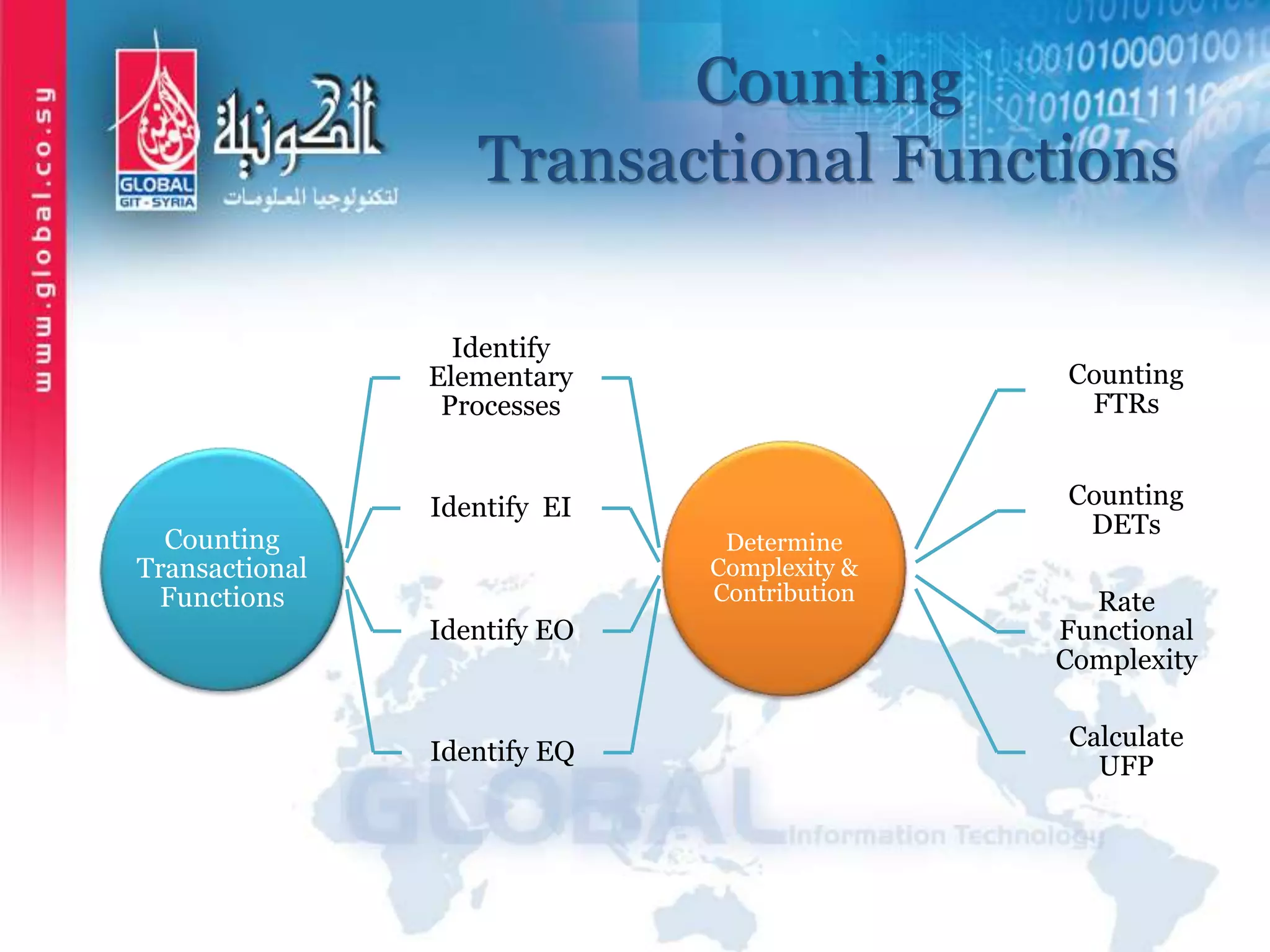
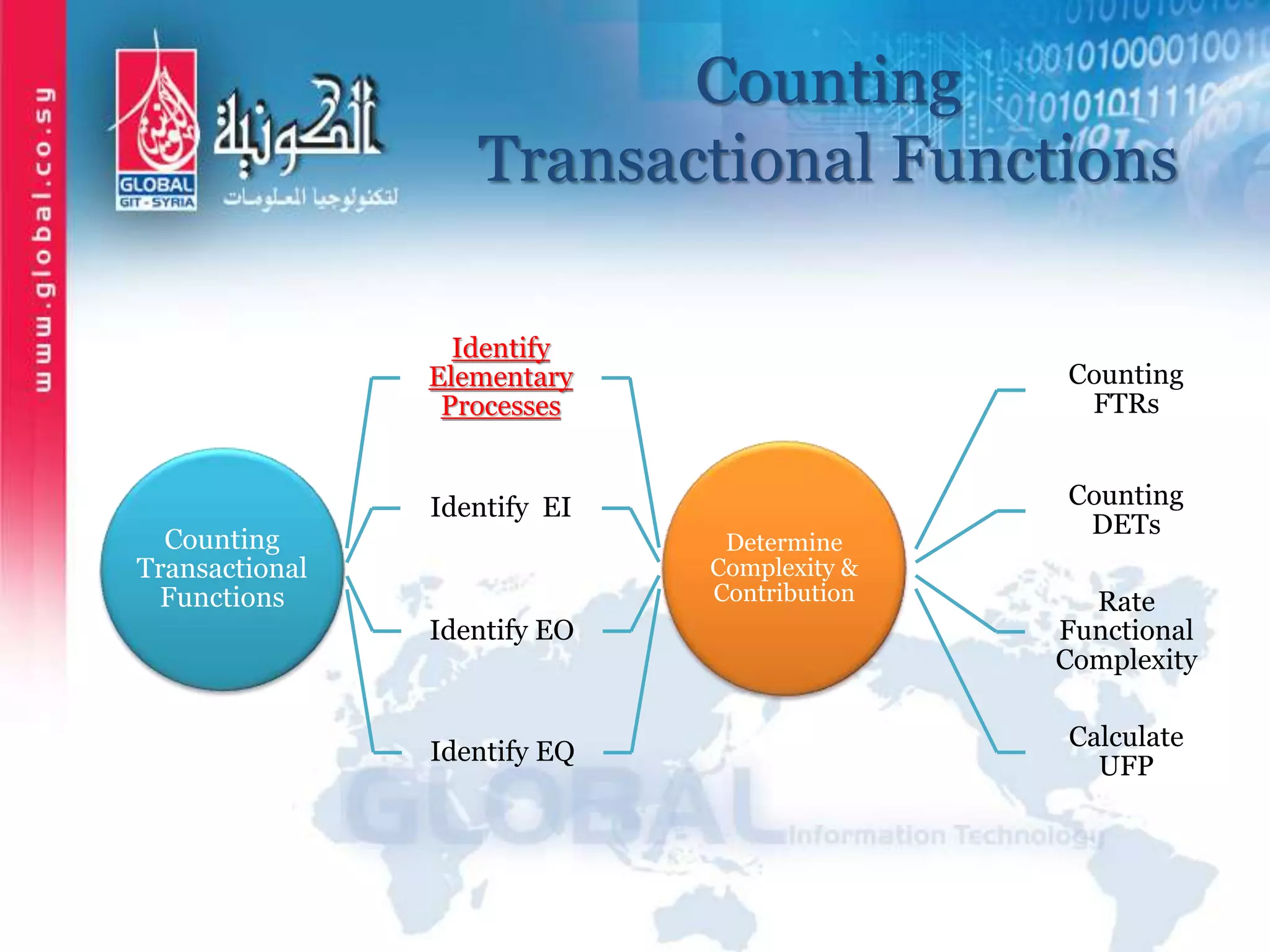
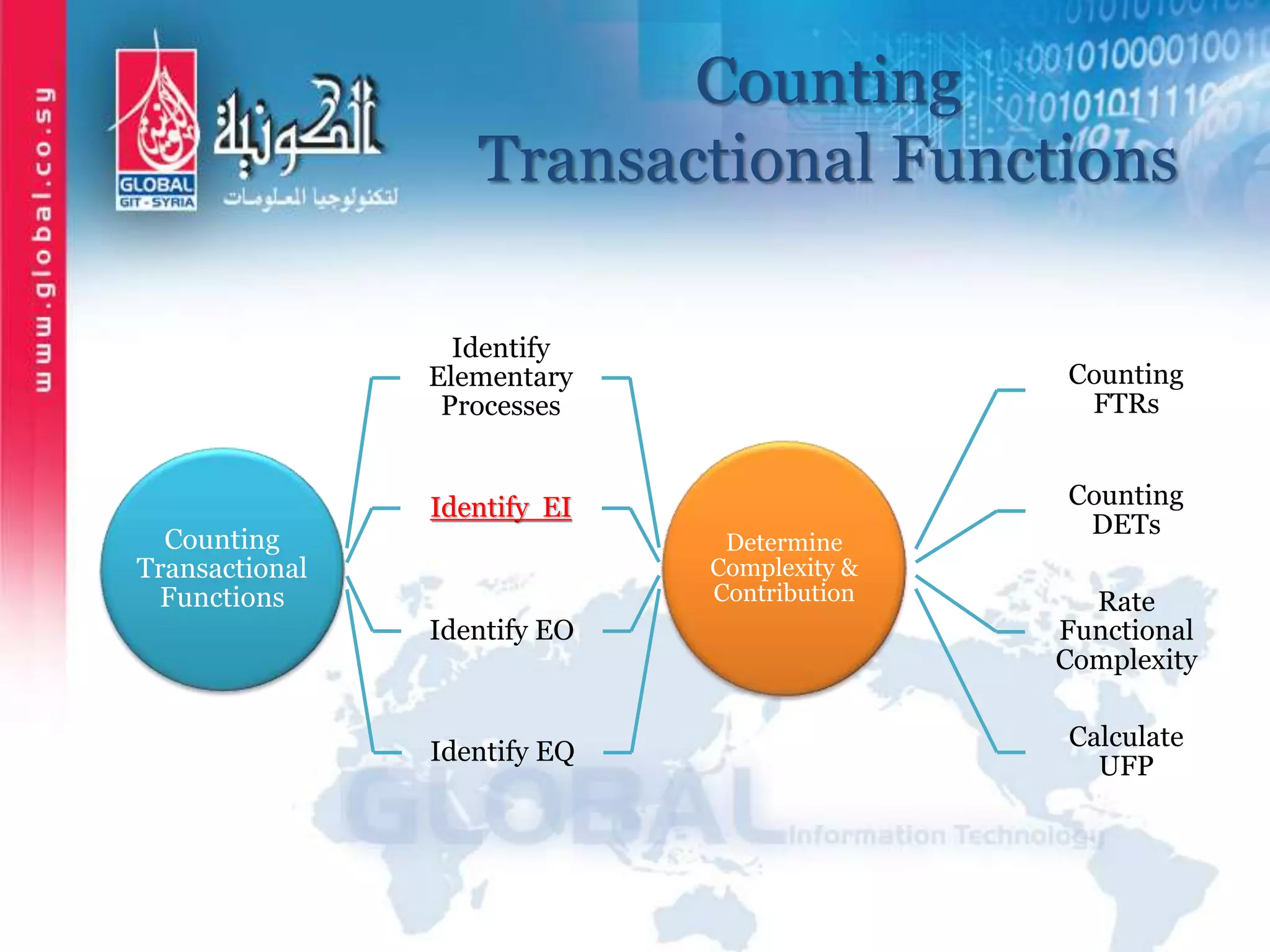
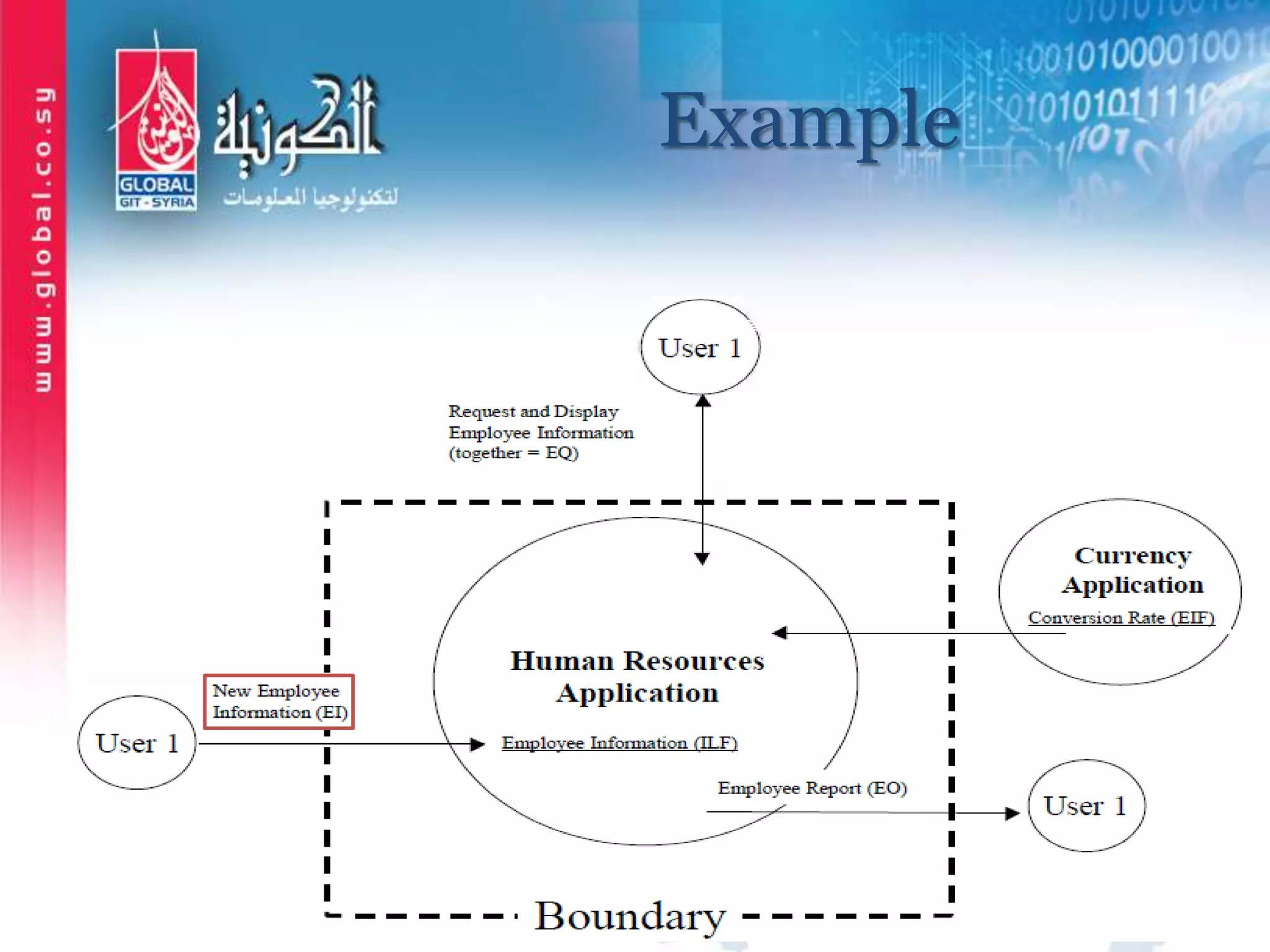
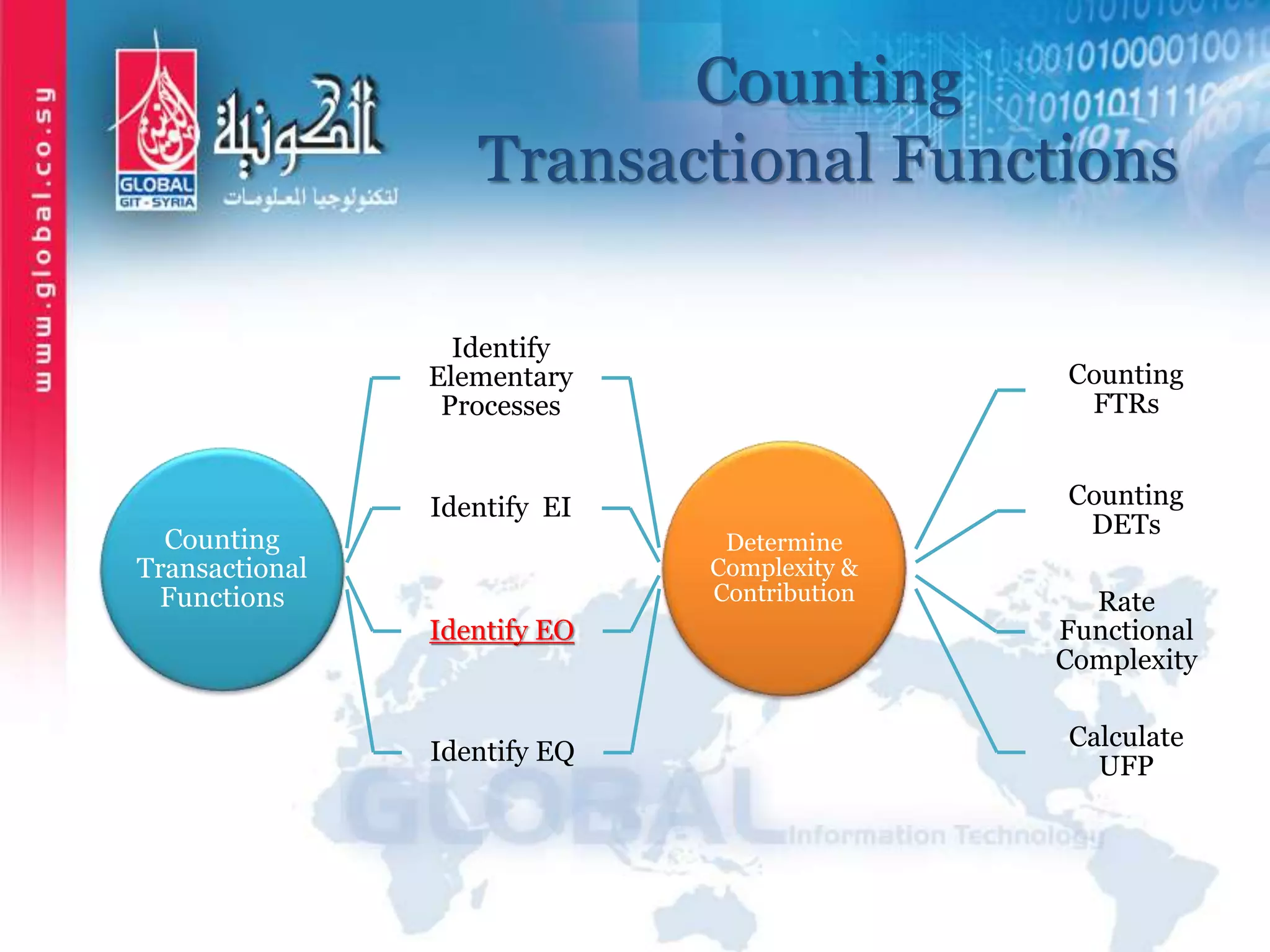
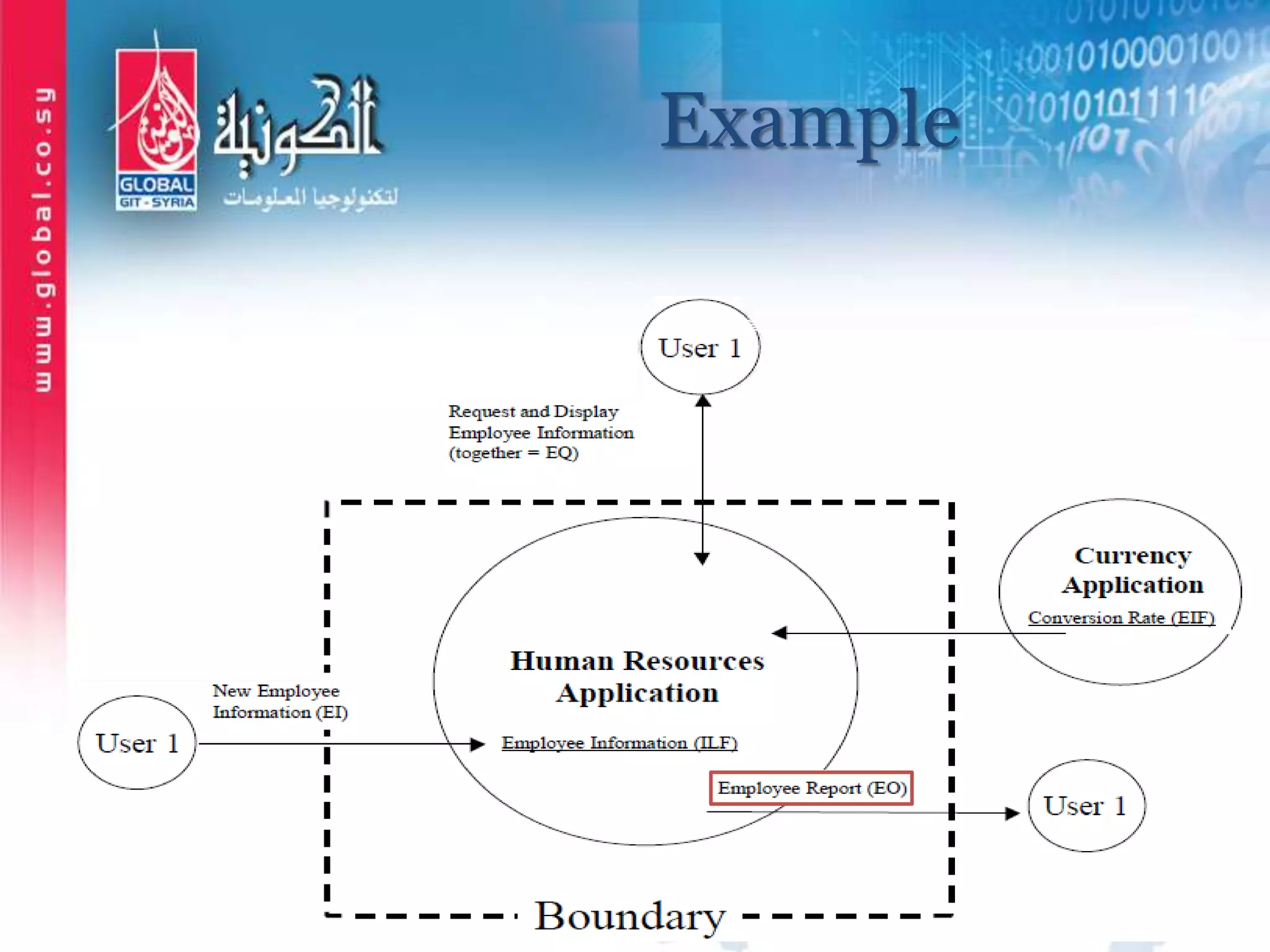
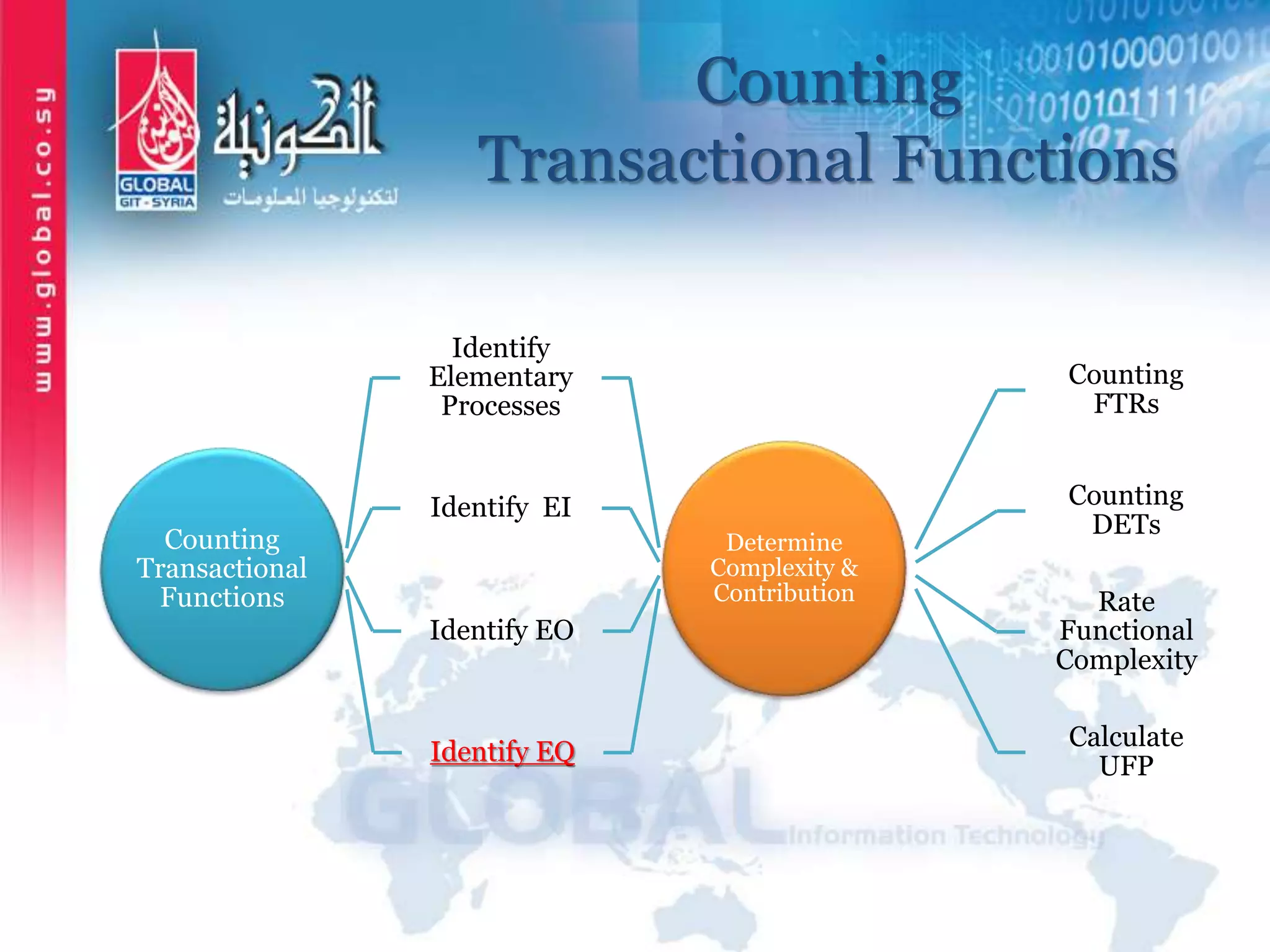
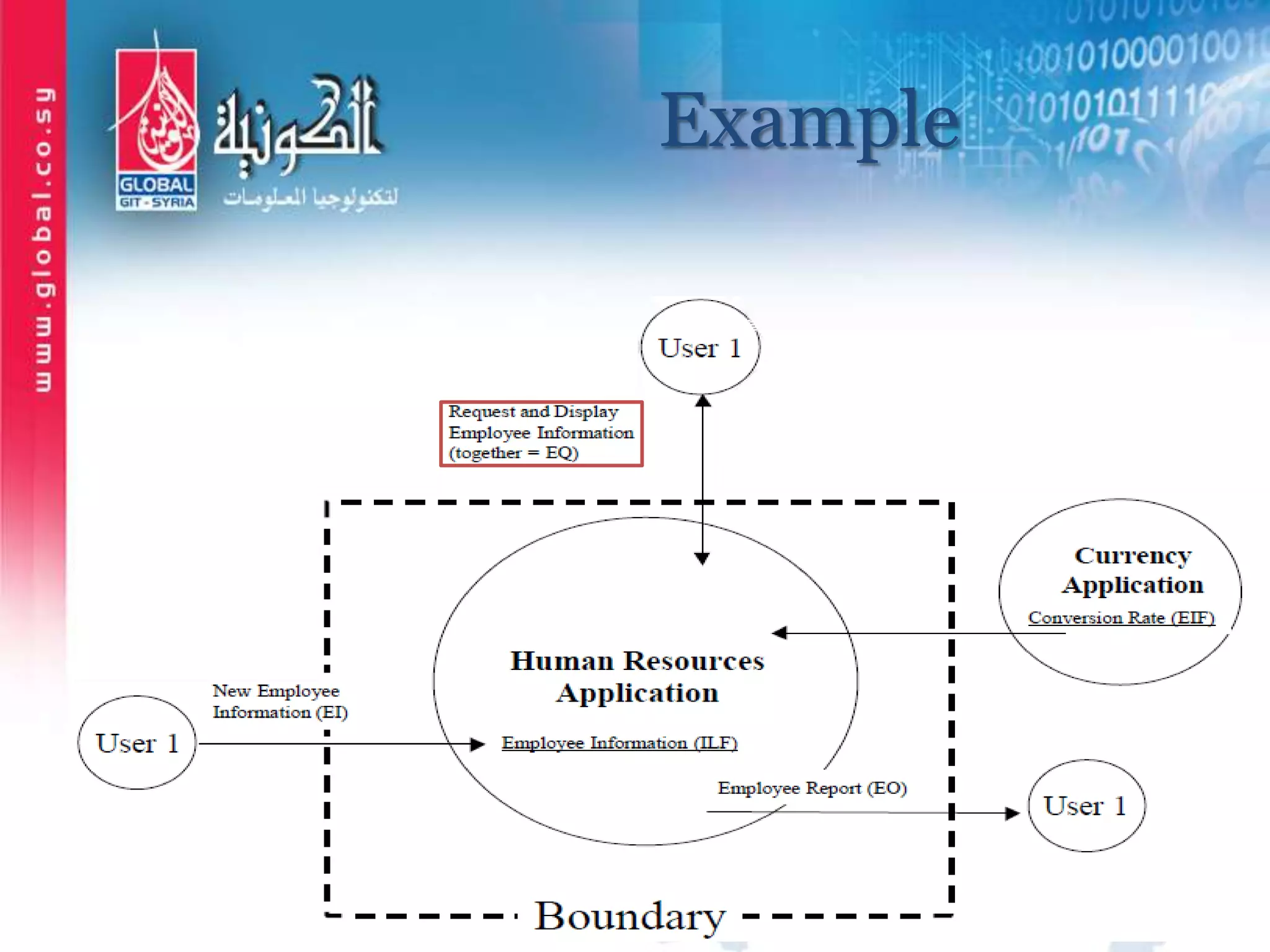
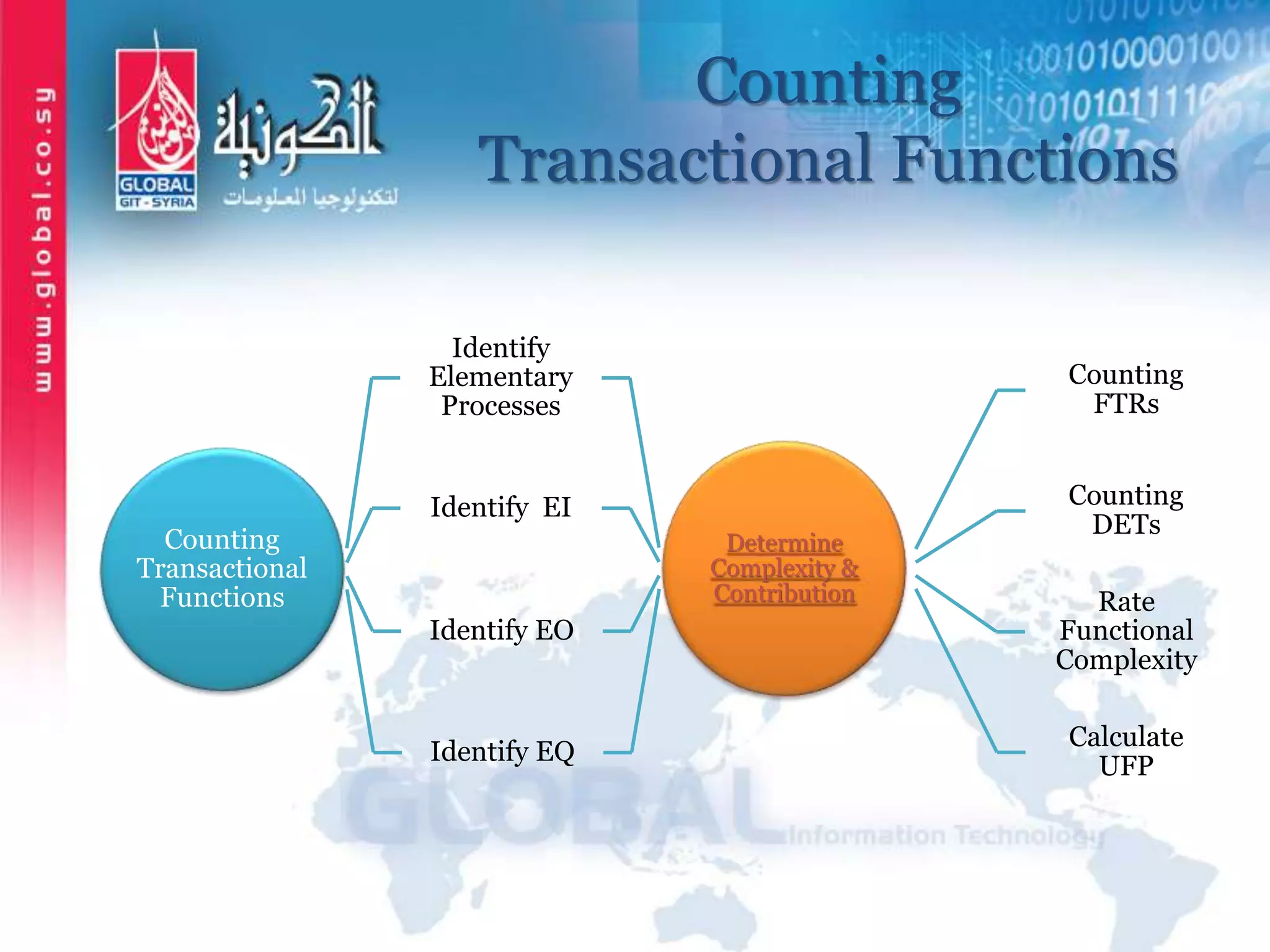
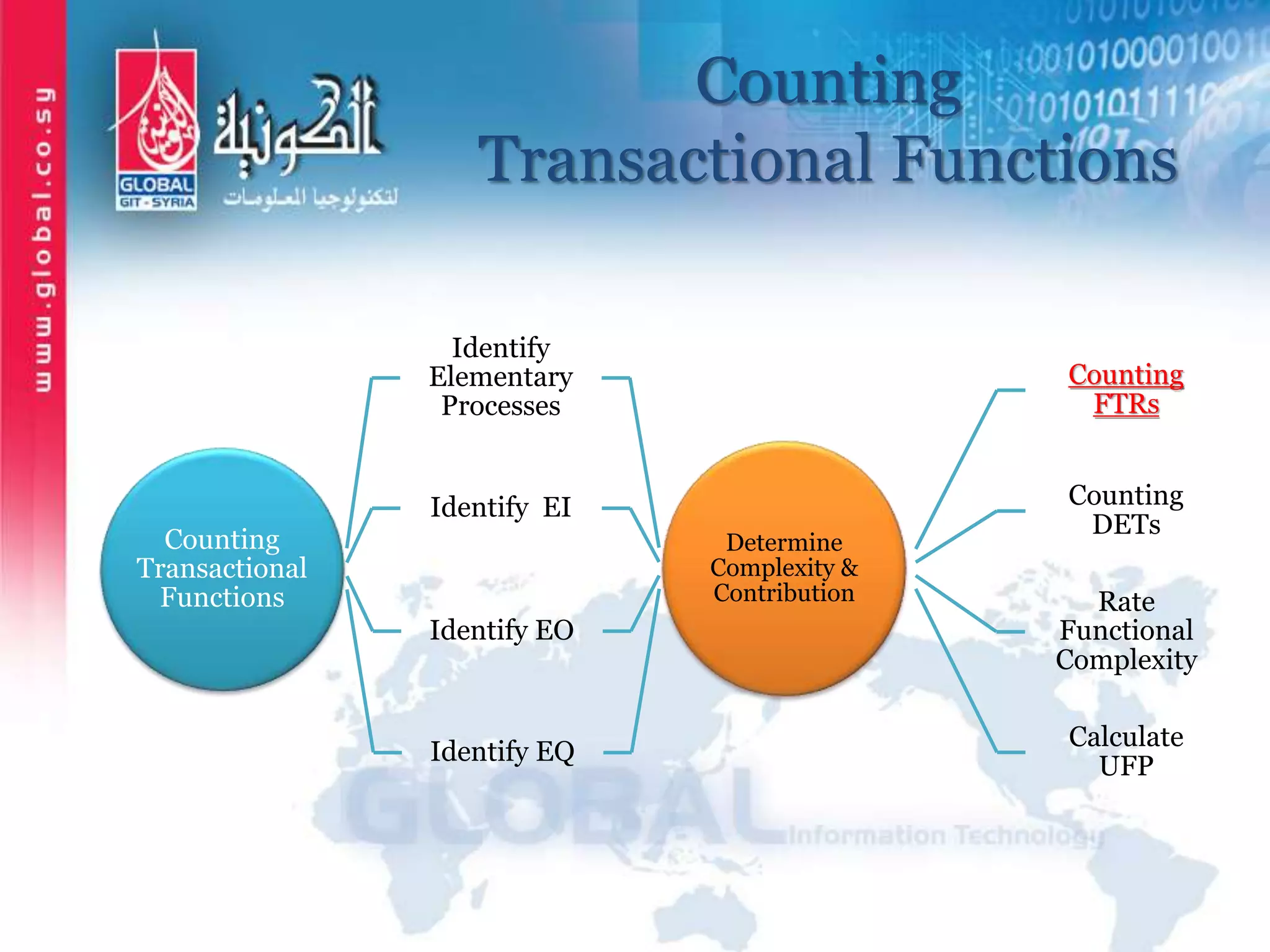
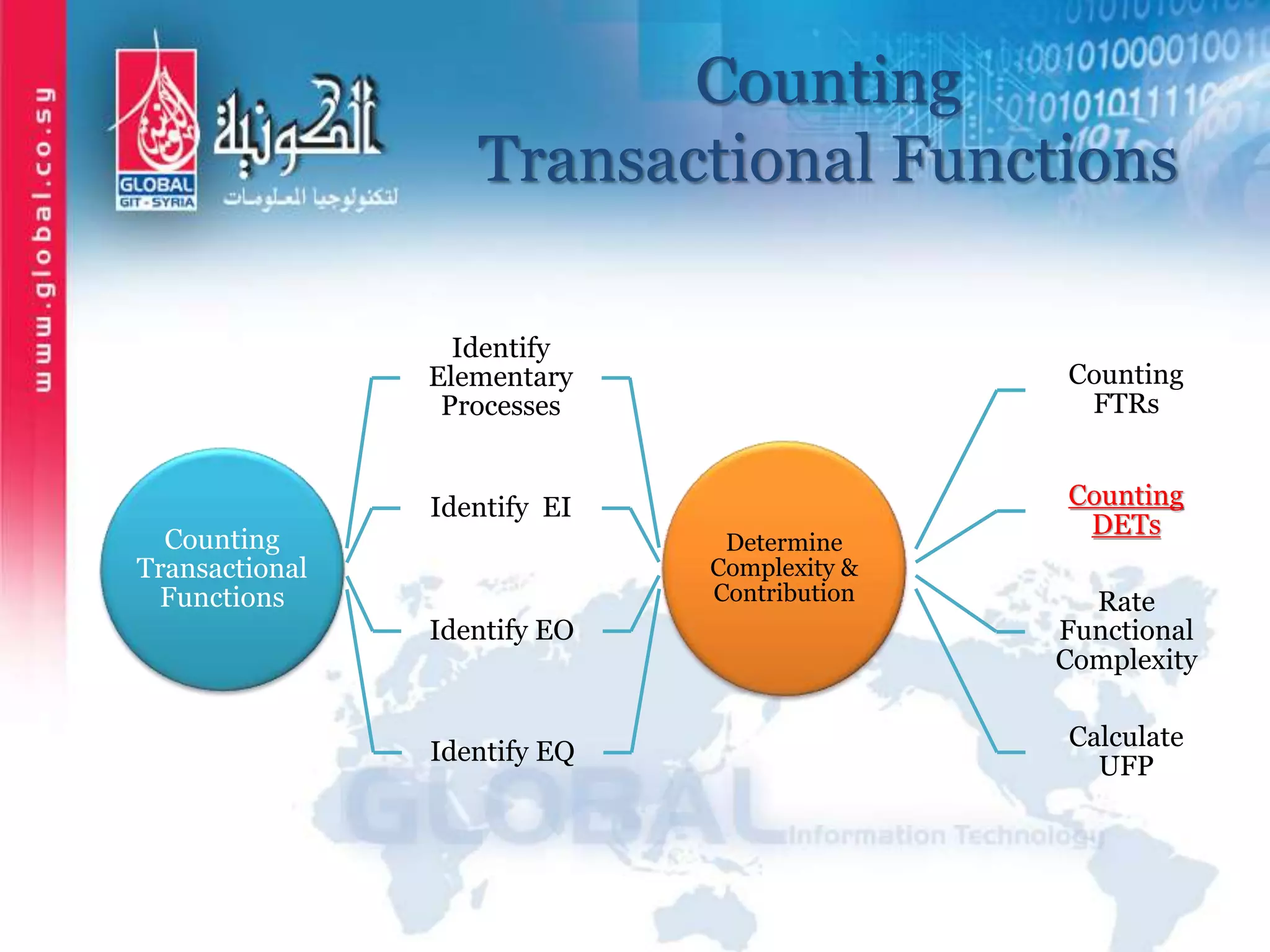
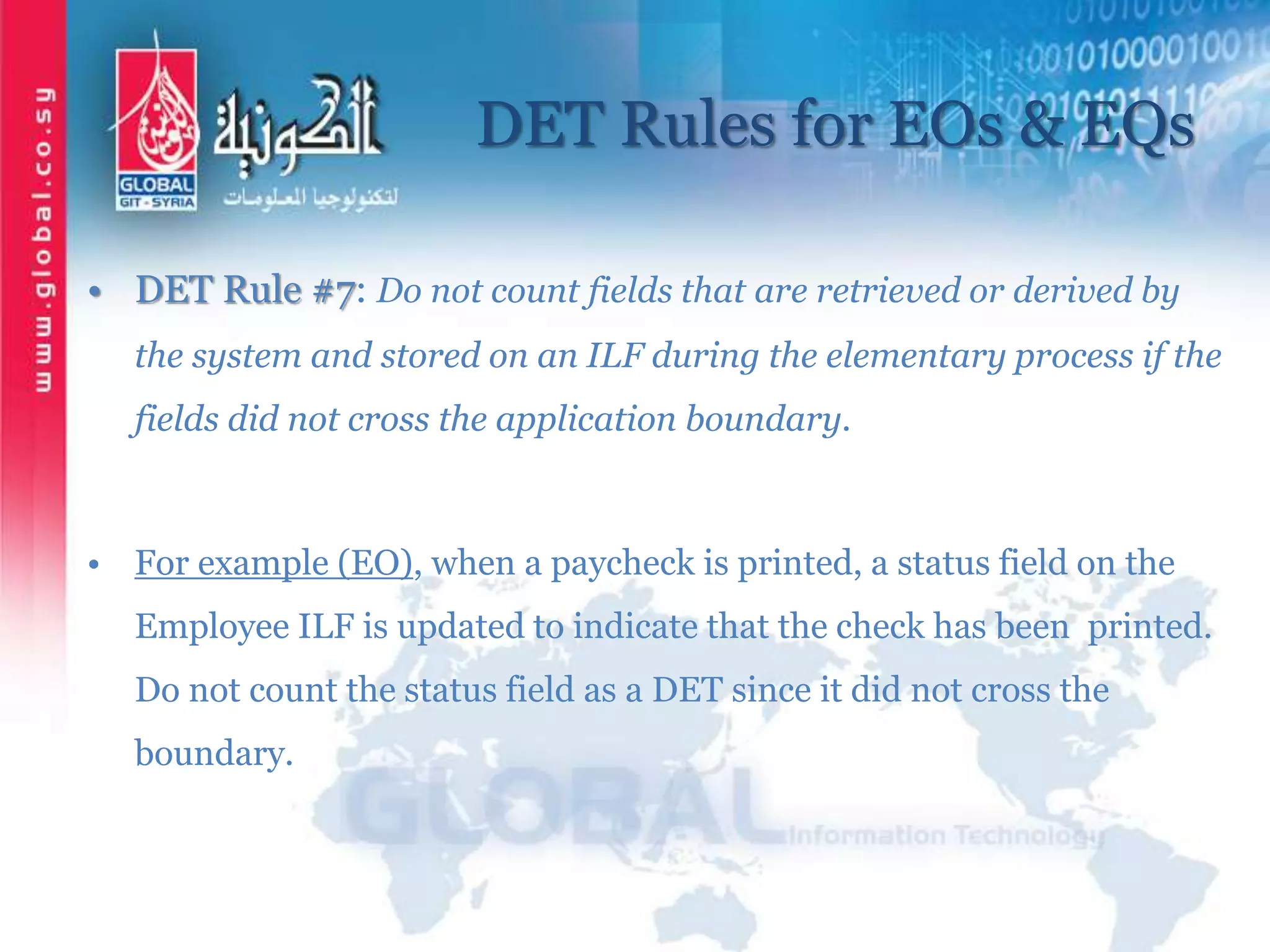
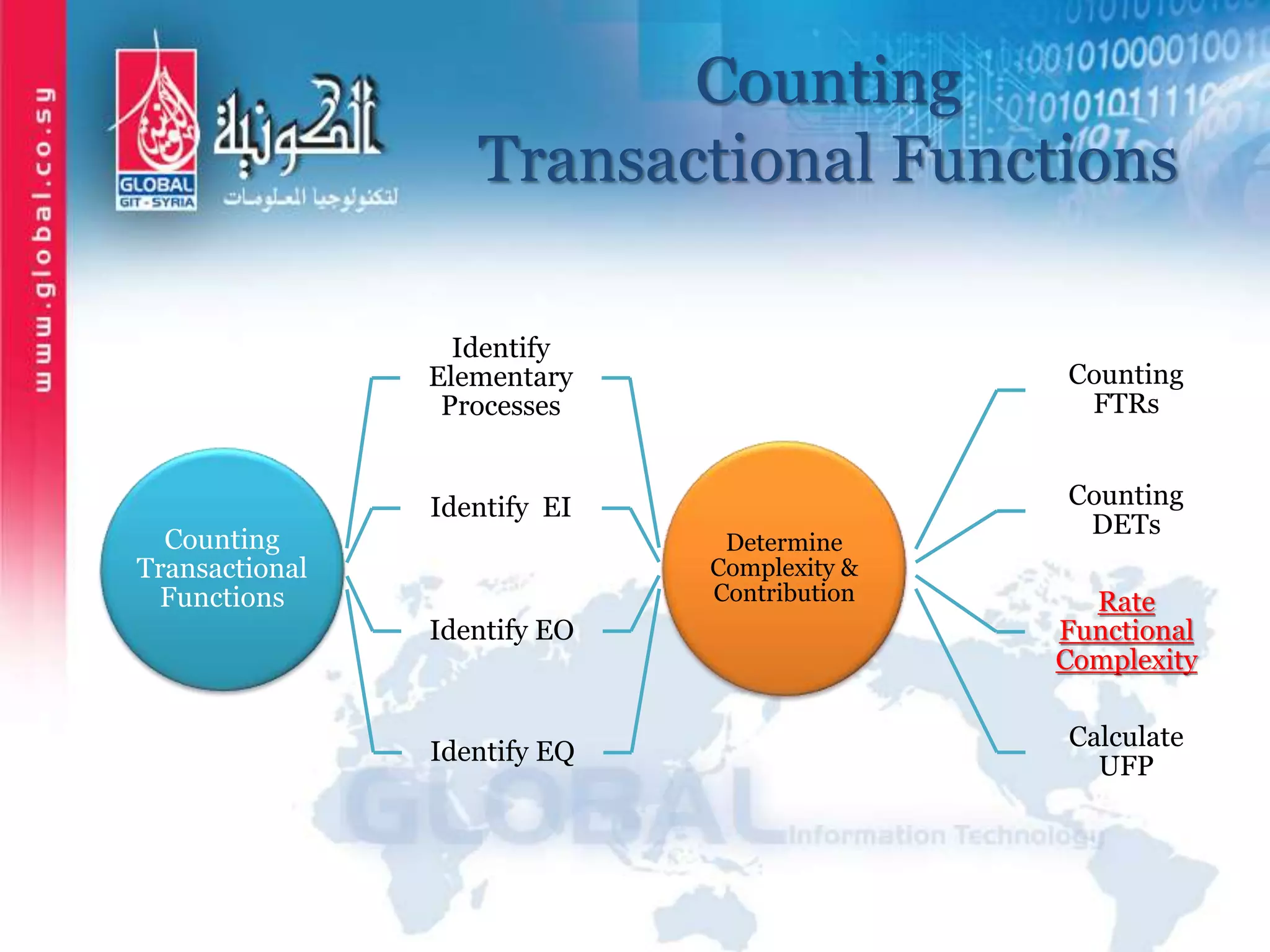
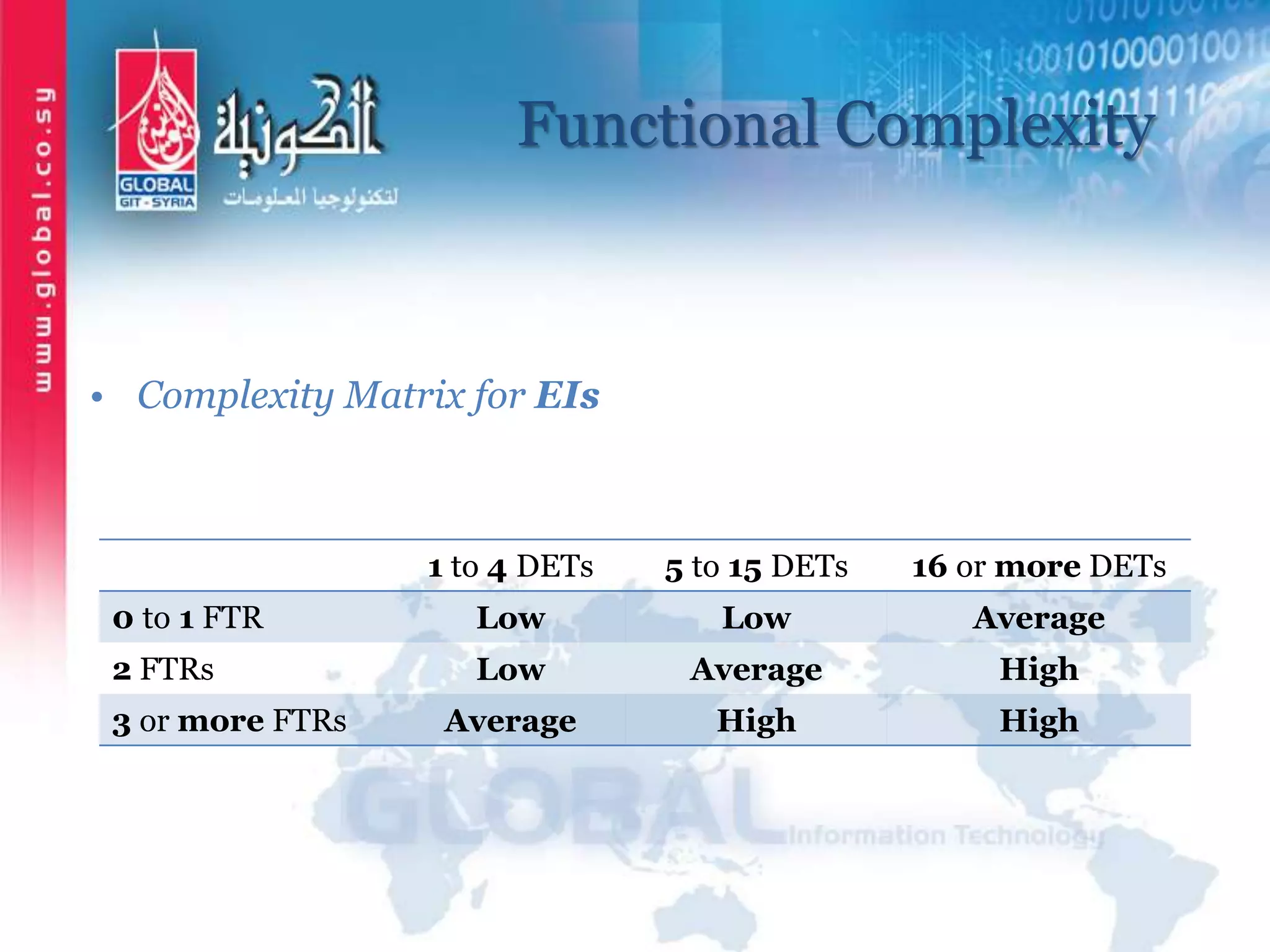
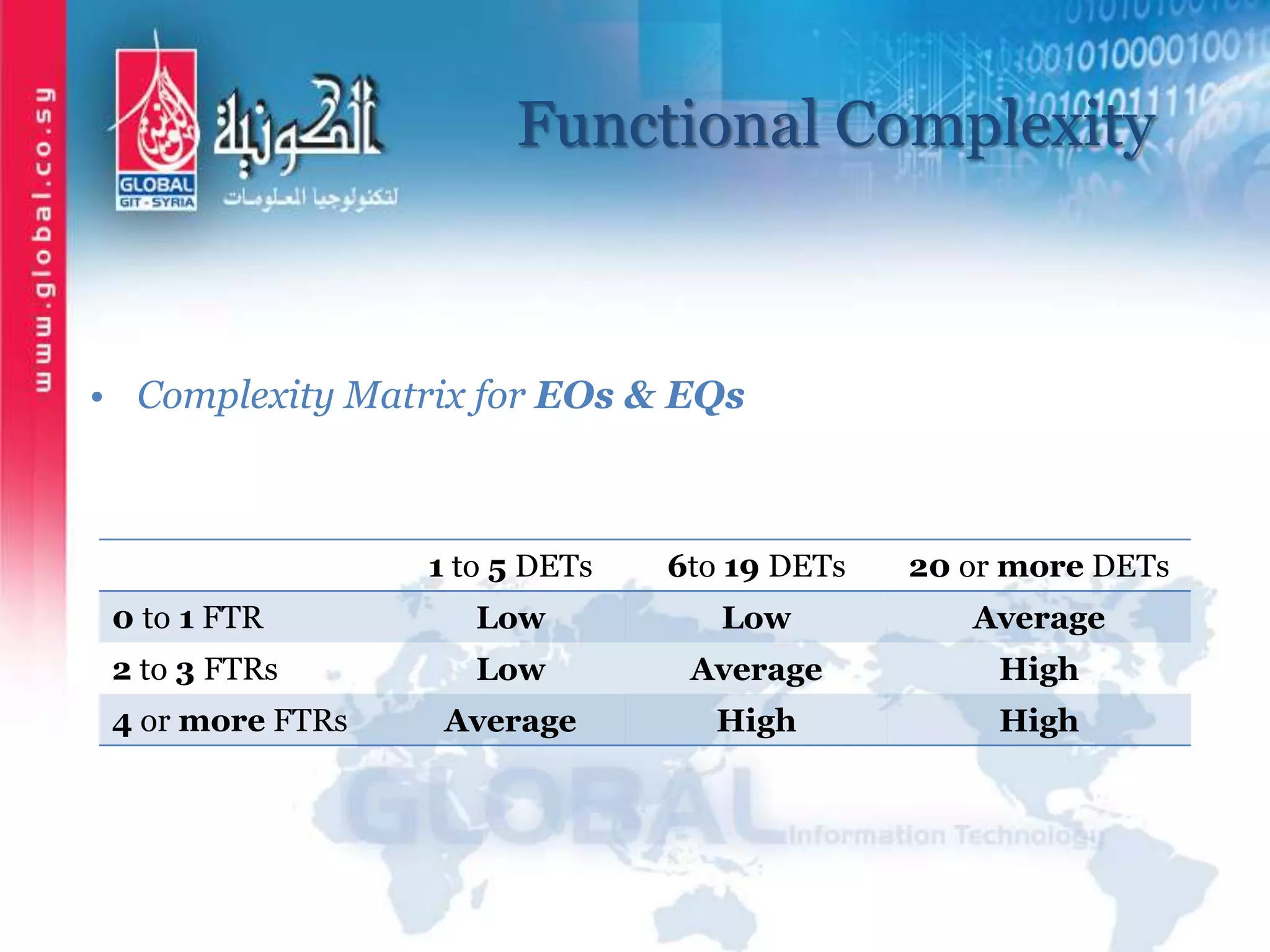
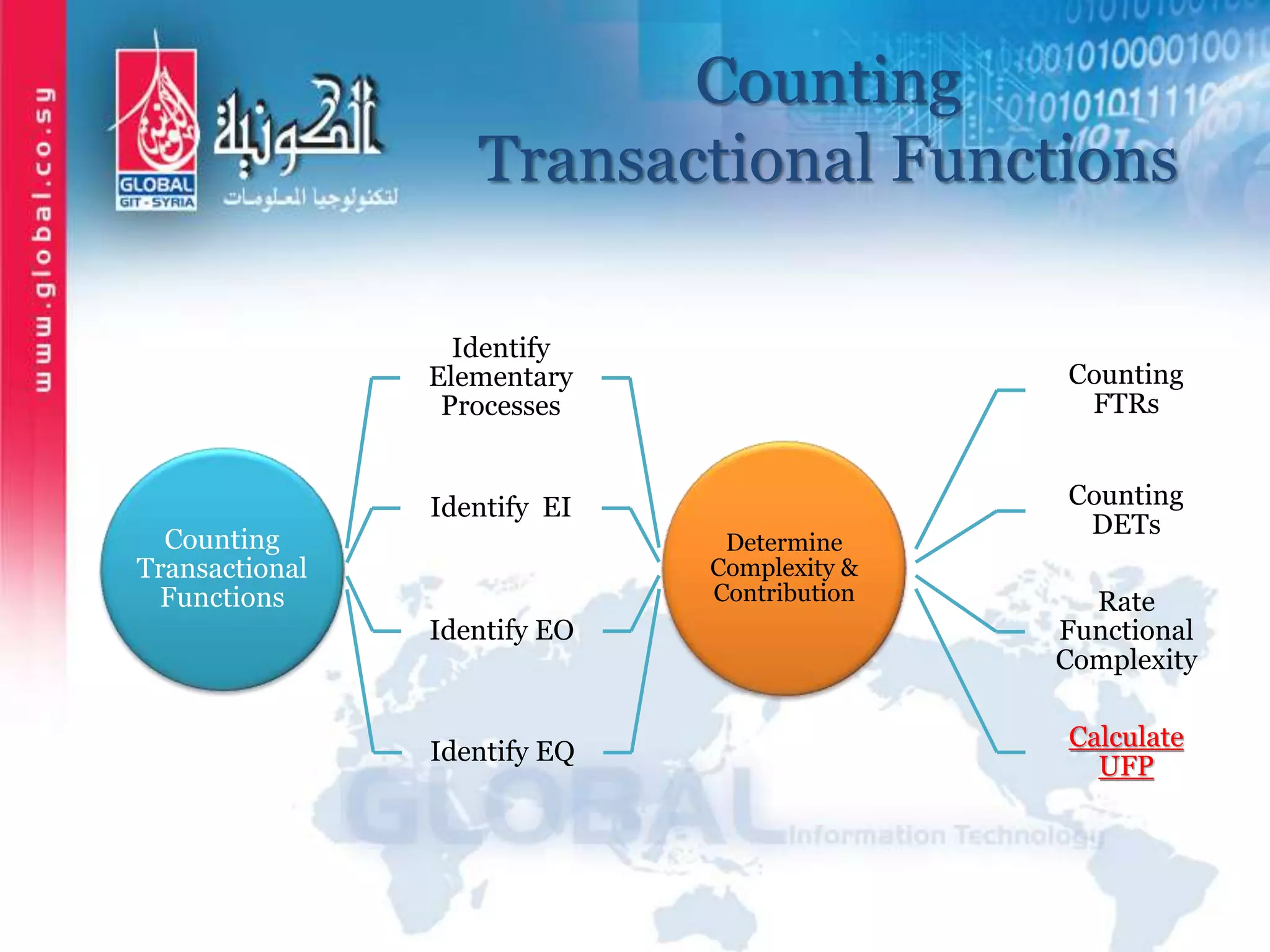
The document outlines function point analysis (FPA) as a standardized method for measuring software development from a user perspective, focusing on quantifying the functionality delivered to users. It details the procedures for counting function points, including identifying application boundaries, counting data functions, and transactional functions, as well as the rules and examples associated with each counting process. Additionally, it highlights the benefits of FPA, such as aiding in project estimation, evaluating application value, and enabling software comparisons.






































































![Function Point Formula
EFP = [(ADD + CHGA + CFP) * VAFA] + (DEL* VAFB)
Where:
• EFP is the enhancement project function point count.
• ADD is the unadjusted function point count of those functions that
were or will be added by the enhancement project.
• CHGA is the unadjusted function point count of those functions that
were or will be modified by the enhancement project. This number
reflects the size of the functions after the modifications.](https://image.slidesharecdn.com/functionpointcountingpractices-150505052544-conversion-gate02/75/Function-Point-Counting-Practices-121-2048.jpg)
![Function Point Formula
EFP = [(ADD + CHGA + CFP) * VAFA] + (DEL* VAFB)
Where:
• CFP is the function point count of those functions added by the
conversion.
• VAFA is the value adjustment factor of the application after the
enhancement project is complete.
• DEL is the unadjusted function point count of those functions that were
or will be deleted by the enhancement project.
• VAFB is the value adjustment factor of the application before the
enhancement project begins.](https://image.slidesharecdn.com/functionpointcountingpractices-150505052544-conversion-gate02/75/Function-Point-Counting-Practices-122-2048.jpg)



![Reflect Enhancement Projects
AFP = [(UFPB + ADD + CHGA) - (CHGB + DEL)] * VAFA
Where:
• AFP is the application's adjusted function point count.
• UFPB is the application's unadjusted function point count before the
enhancement project begins.
• ADD is the unadjusted function point count of those functions that were
added by the enhancement project.
• CHGA is the unadjusted function point count of those functions that
were changed by the enhancement project. This number reflects the size
of the functions after the changes.](https://image.slidesharecdn.com/functionpointcountingpractices-150505052544-conversion-gate02/75/Function-Point-Counting-Practices-126-2048.jpg)
![Reflect Enhancement Projects
AFP = [(UFPB + ADD + CHGA) - (CHGB + DEL)] * VAFA
Where:
• CHGB is the unadjusted function point count of those functions that
were changed by the enhancement project. This number reflects the
size of the functions before the changes were made.
• DEL is the unadjusted function point count of those functions that
were deleted by the enhancement project.
• VAFA is the value adjustment factor of the application after the
enhancement project is complete.](https://image.slidesharecdn.com/functionpointcountingpractices-150505052544-conversion-gate02/75/Function-Point-Counting-Practices-127-2048.jpg)
