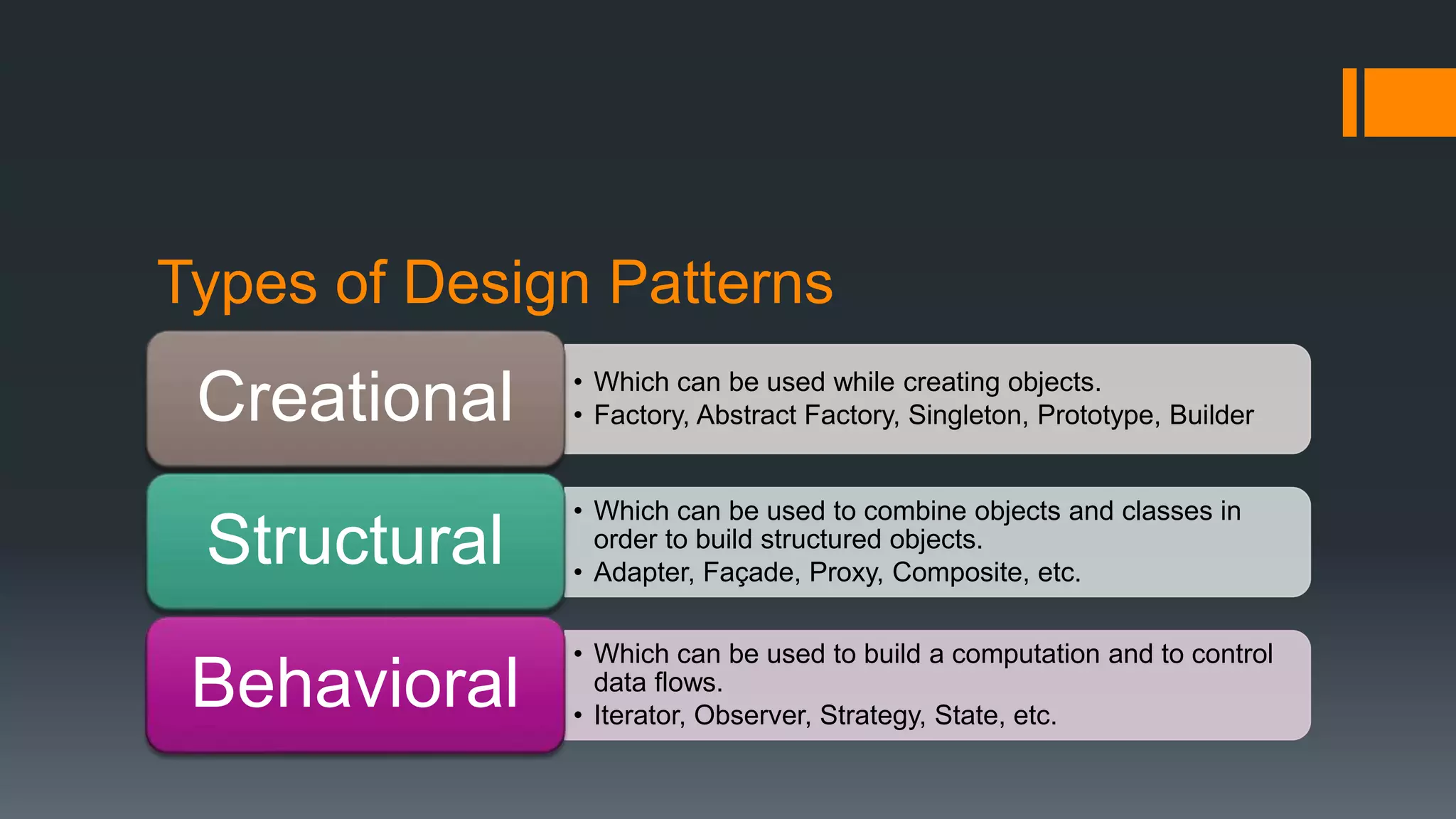
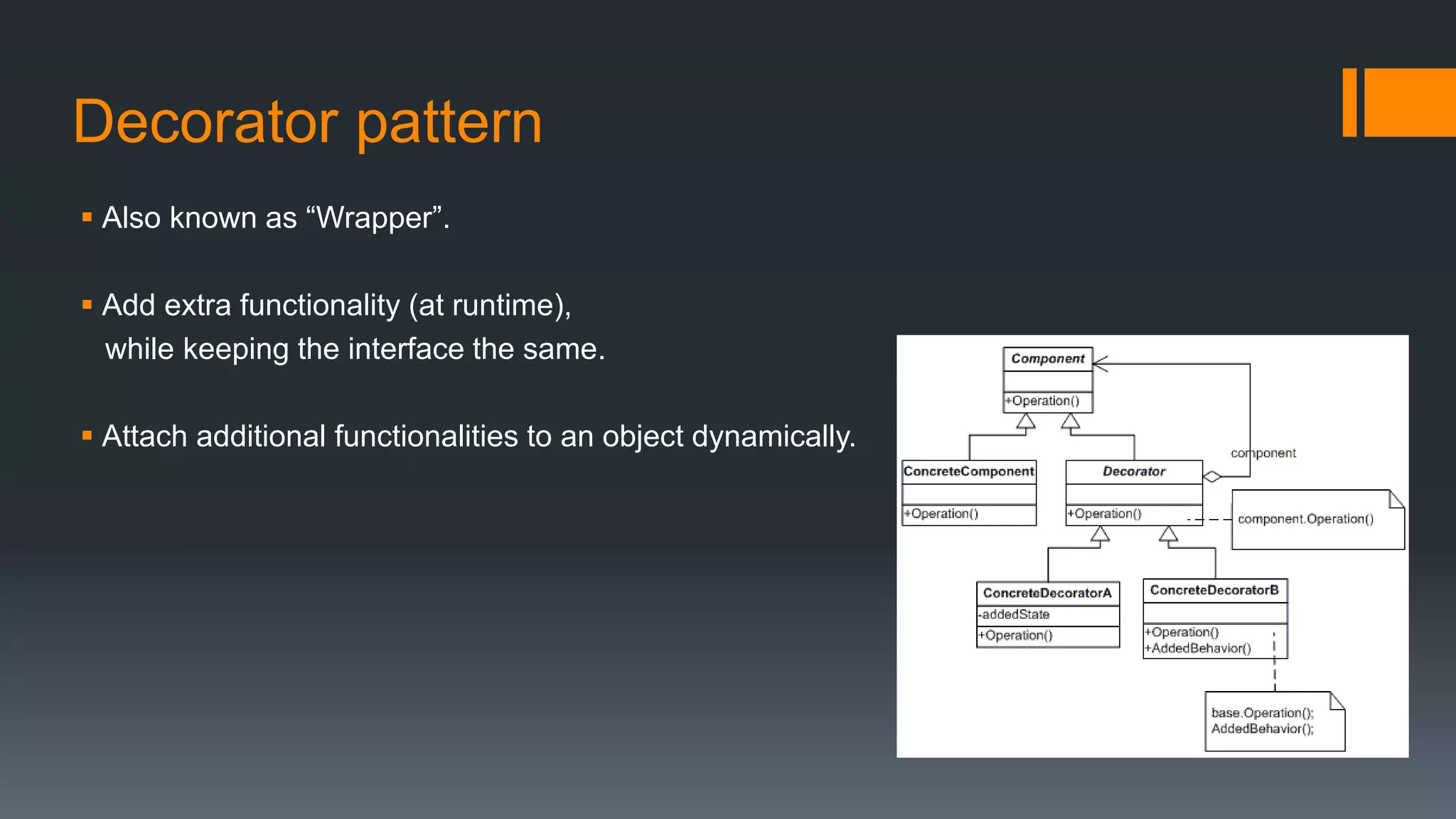
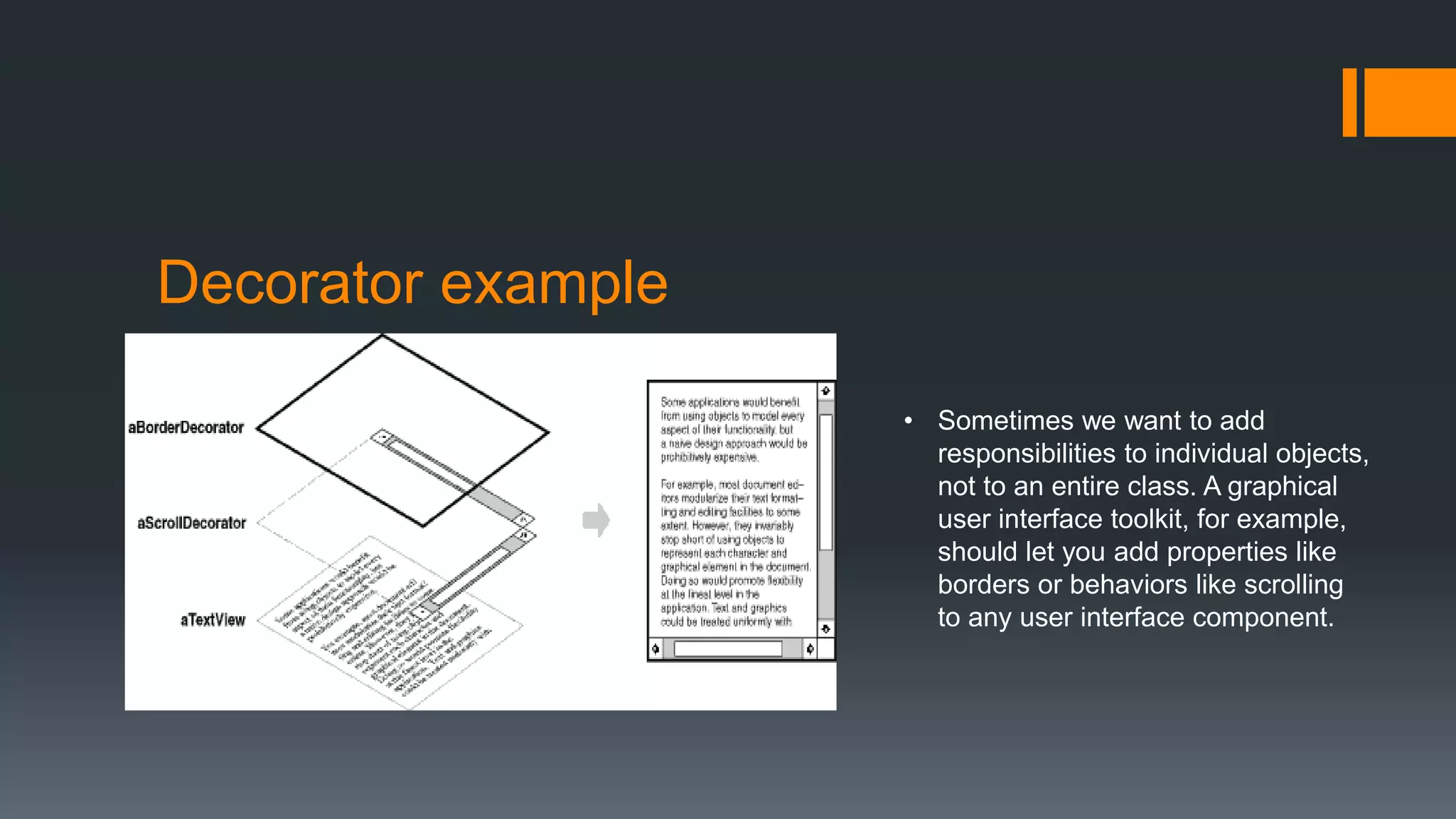
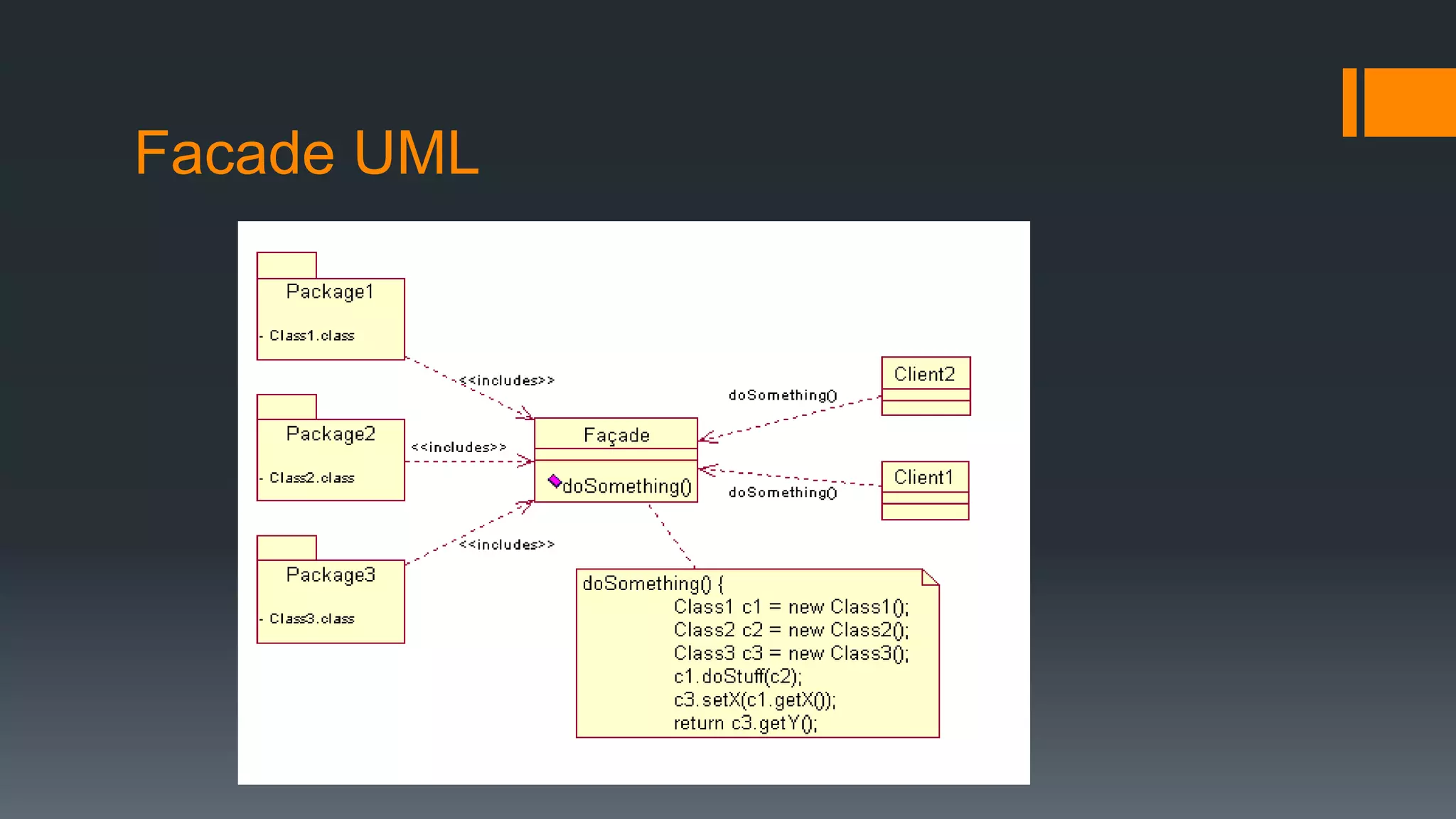
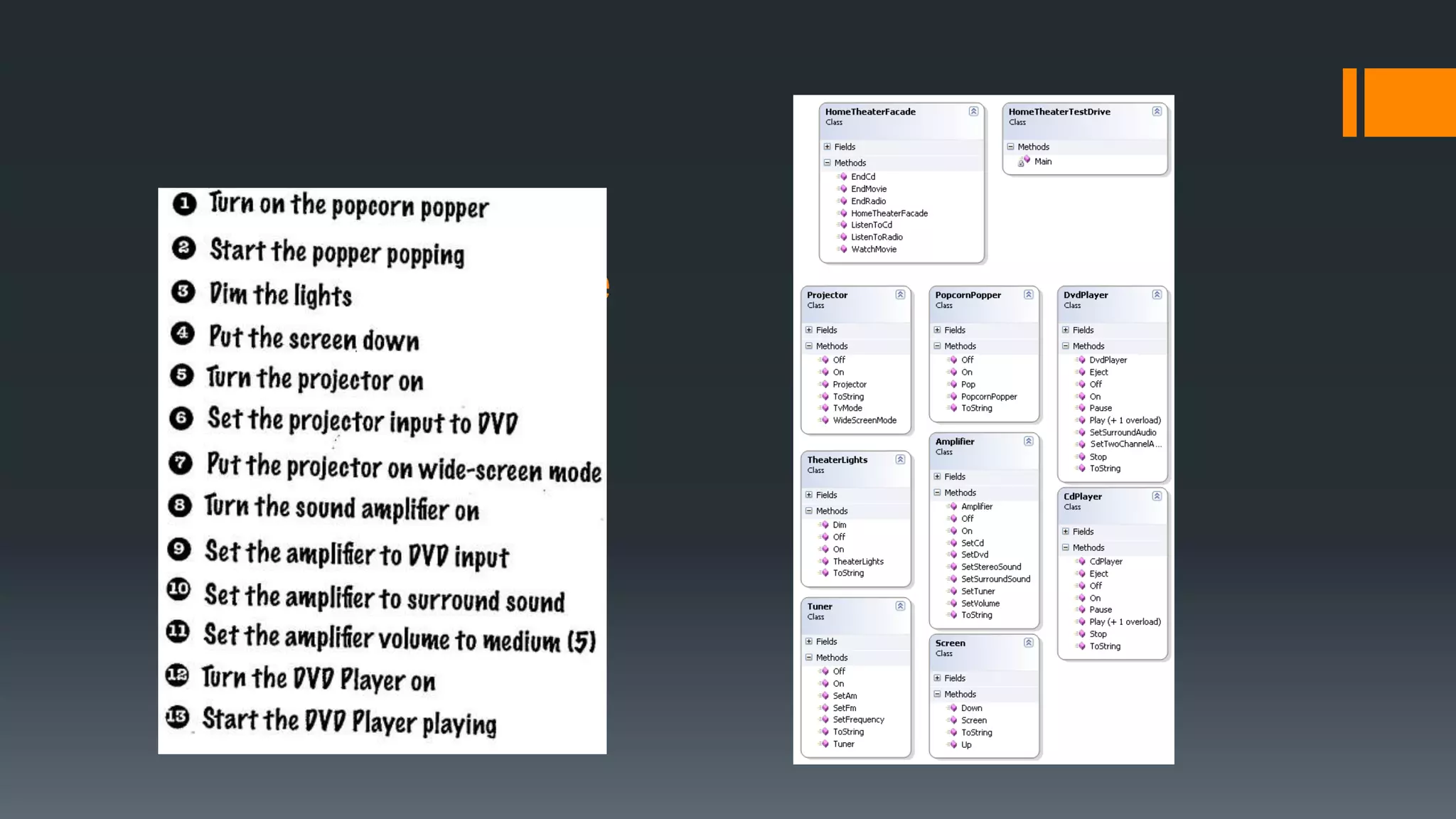
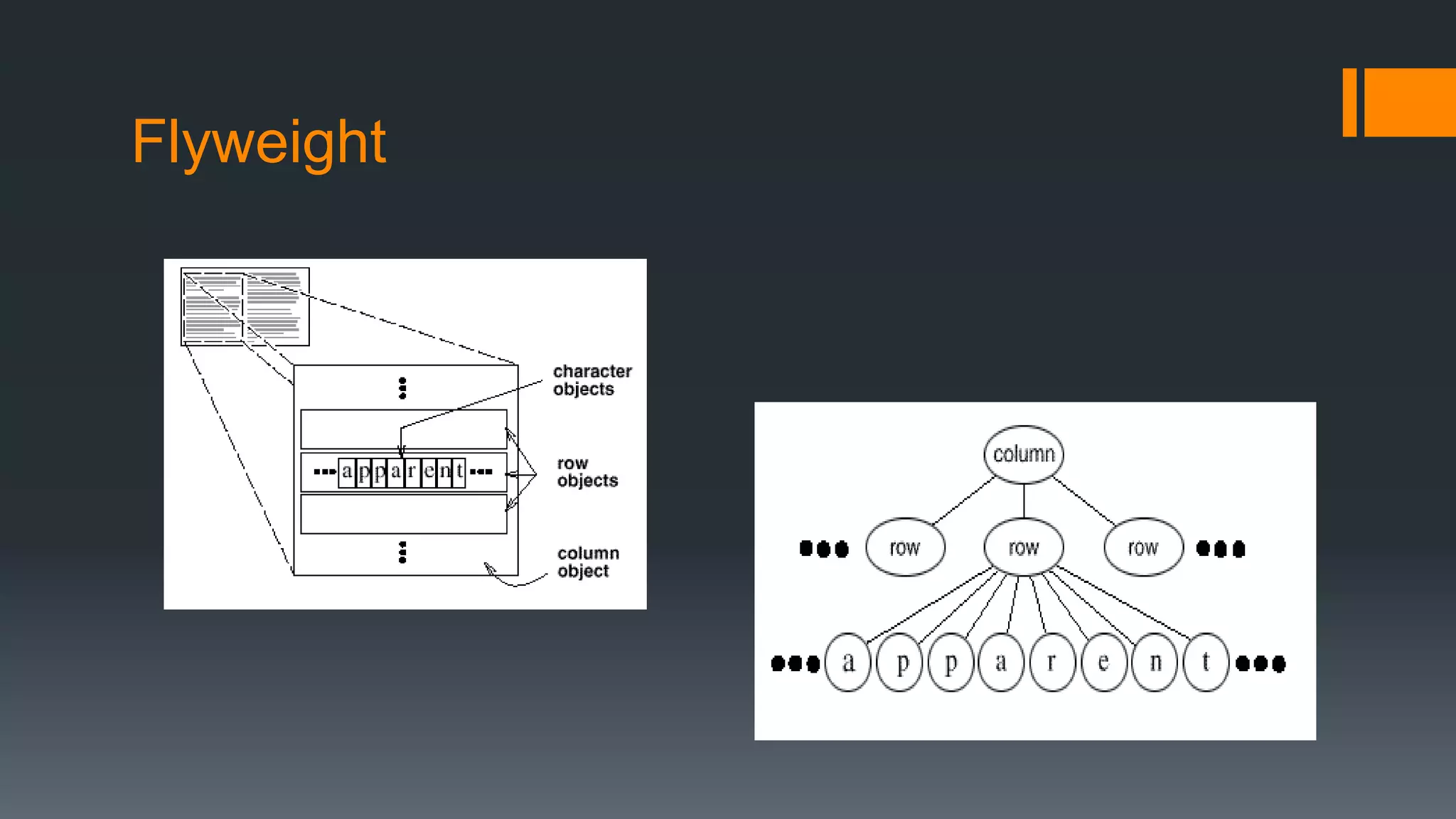
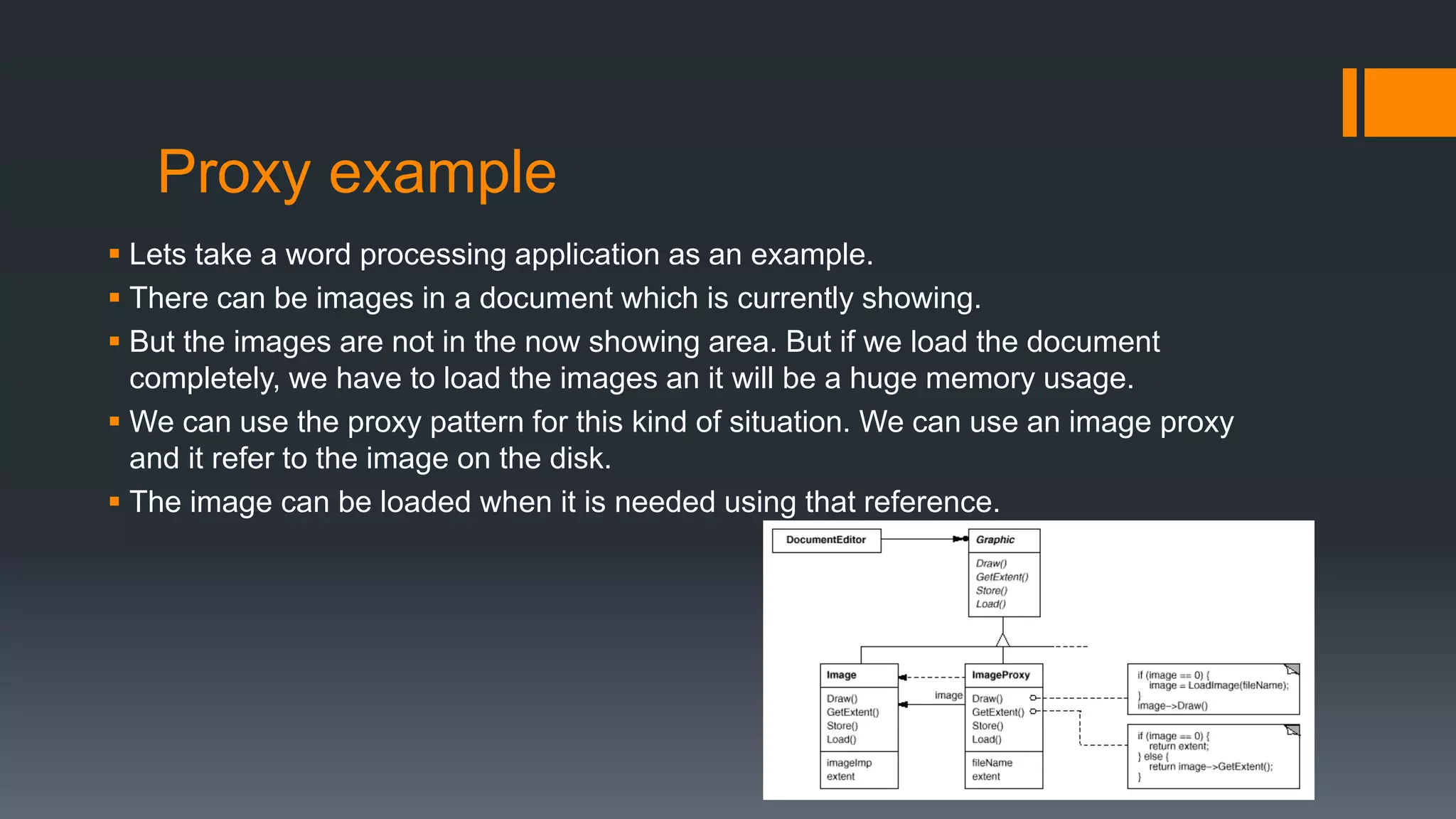
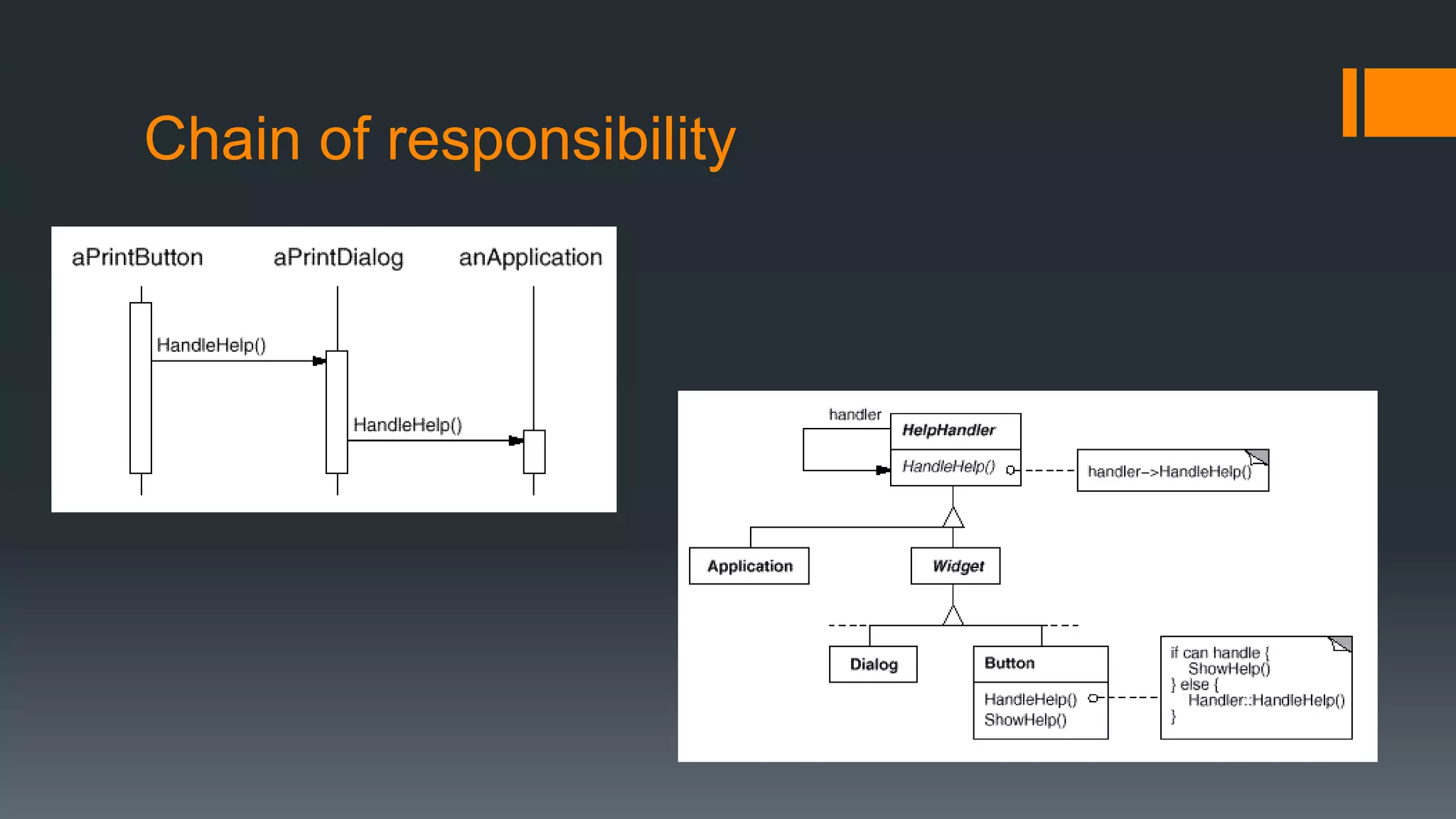
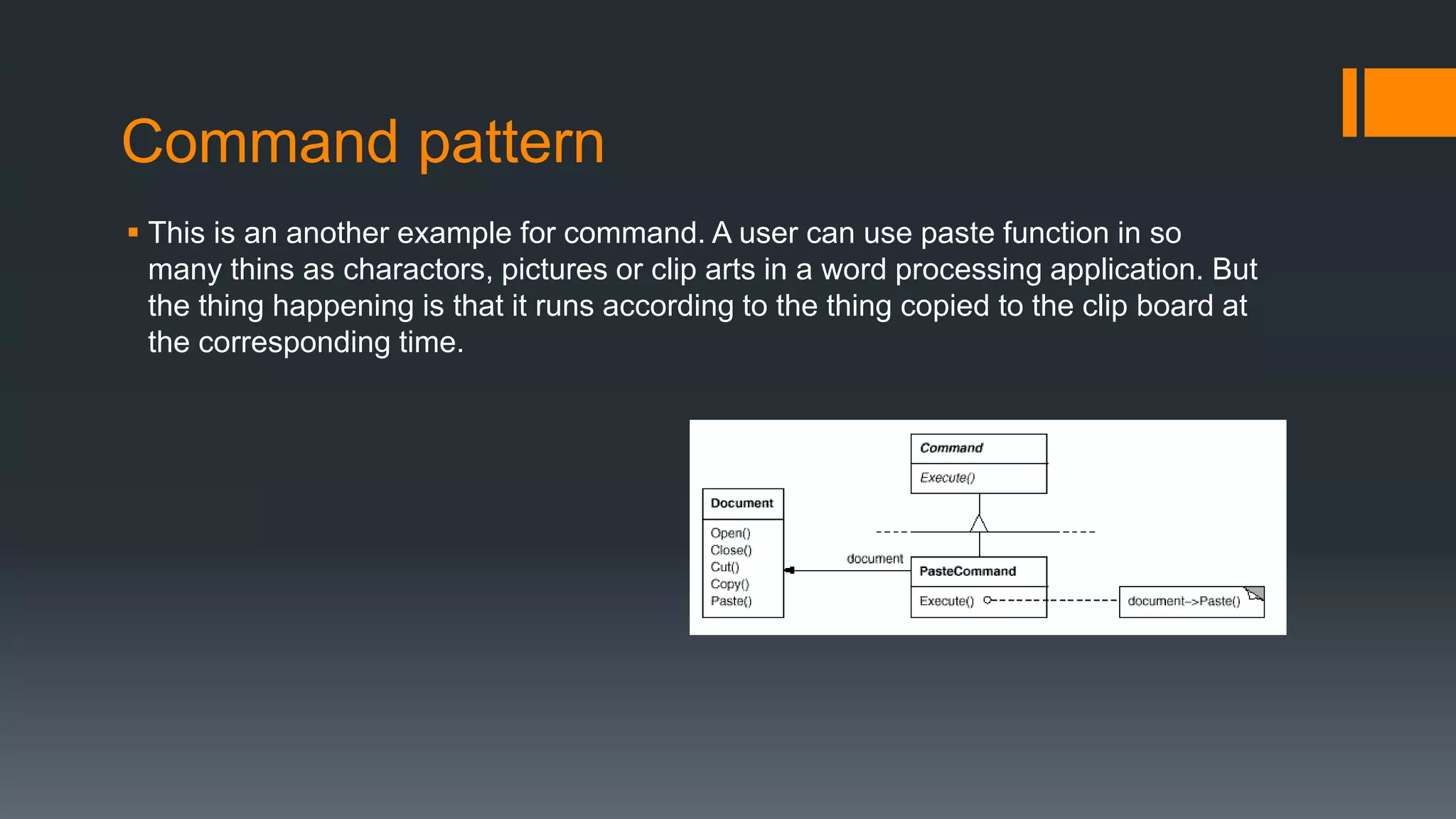
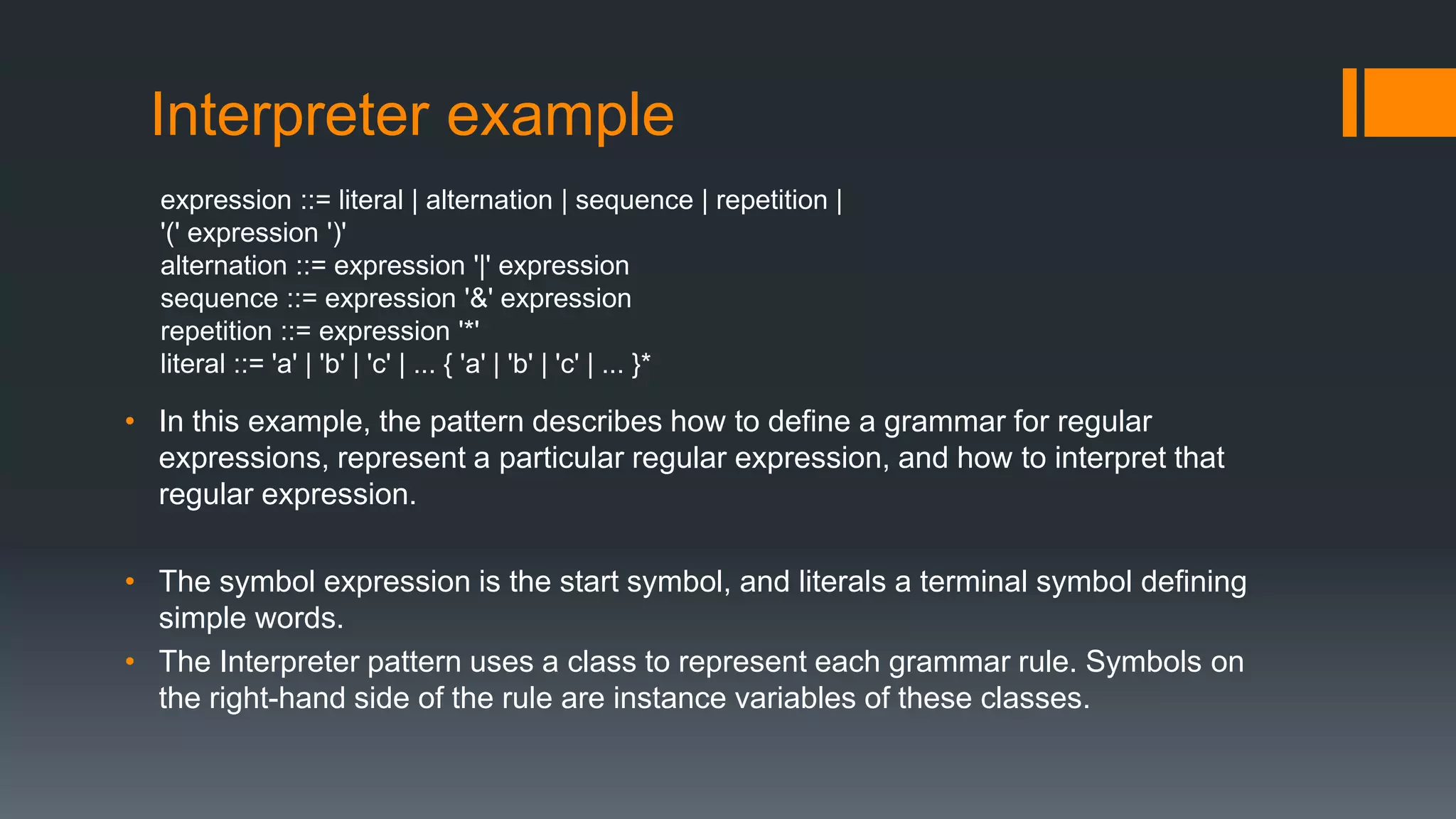
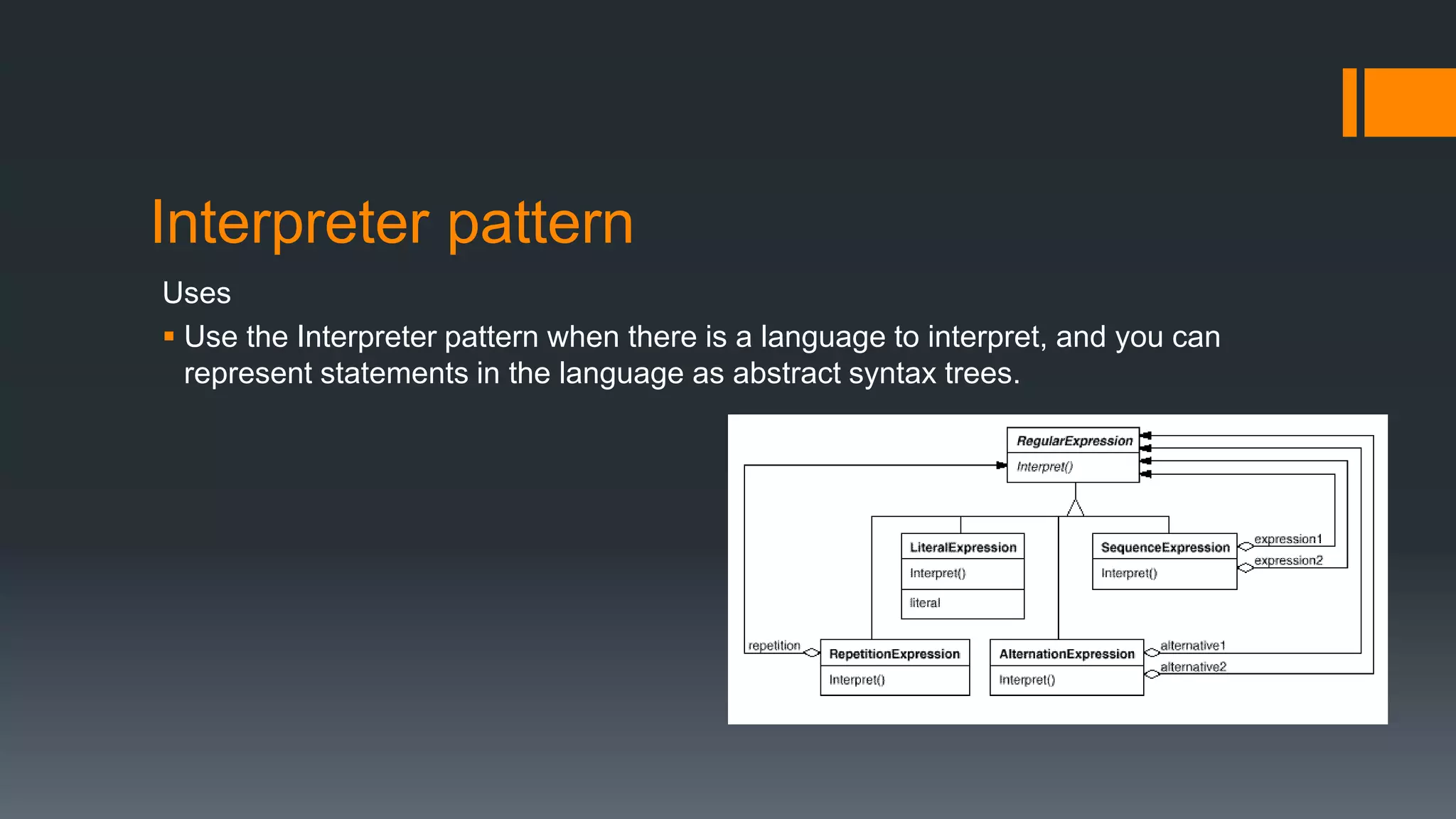
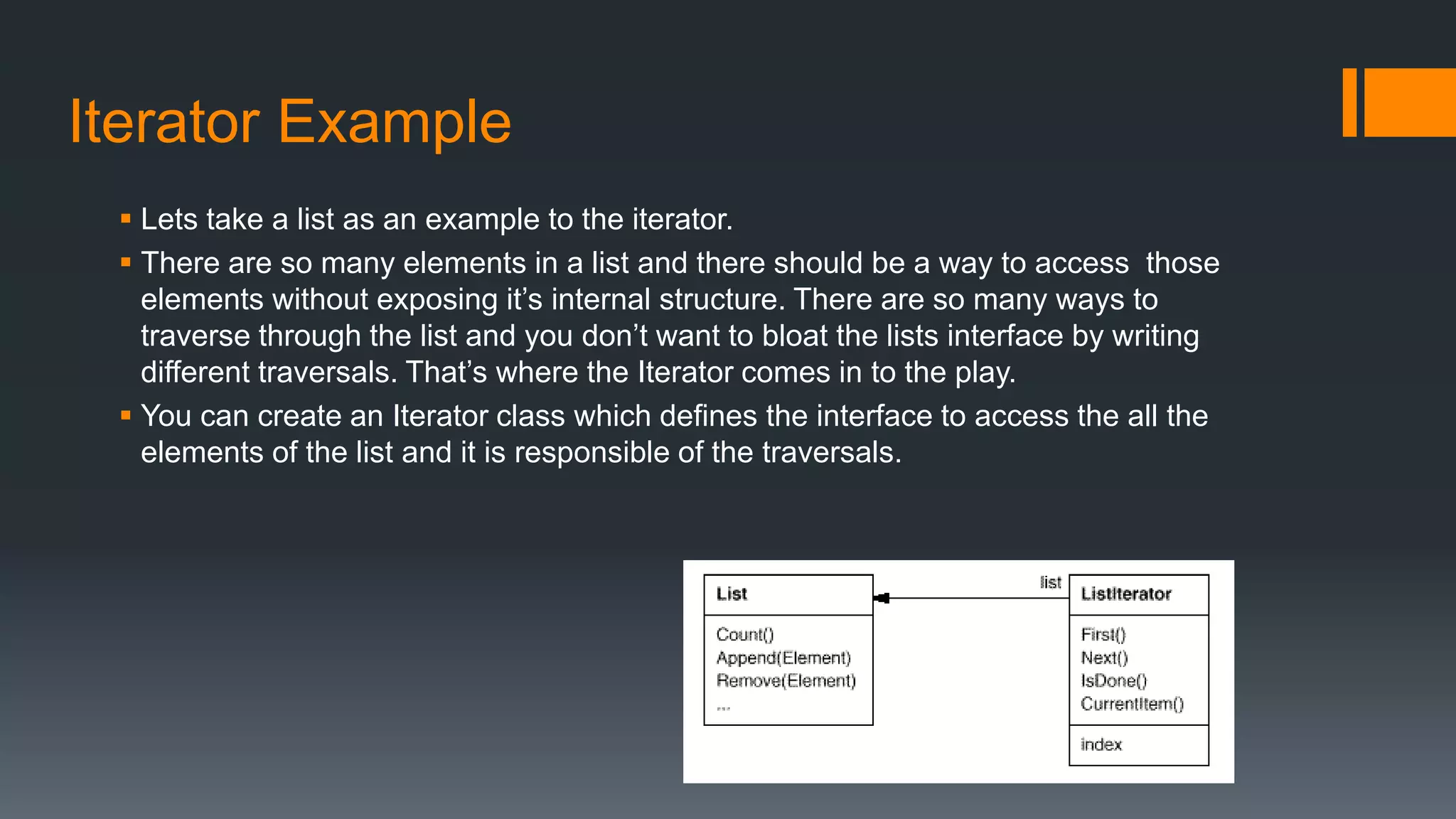
This document provides an overview of several design patterns including Creational patterns (Factory, Abstract Factory, Singleton, Prototype, Builder), Structural patterns (Adapter, Facade, Proxy, Composite), and Behavioral patterns (Iterator, Observer, Strategy, State). It then discusses specific patterns in more detail, including Decorator, Flyweight, Proxy, Facade, Chain of Responsibility, Command, Interpreter, and Iterator patterns. For each pattern it provides a definition, example, and discussion of applicability.