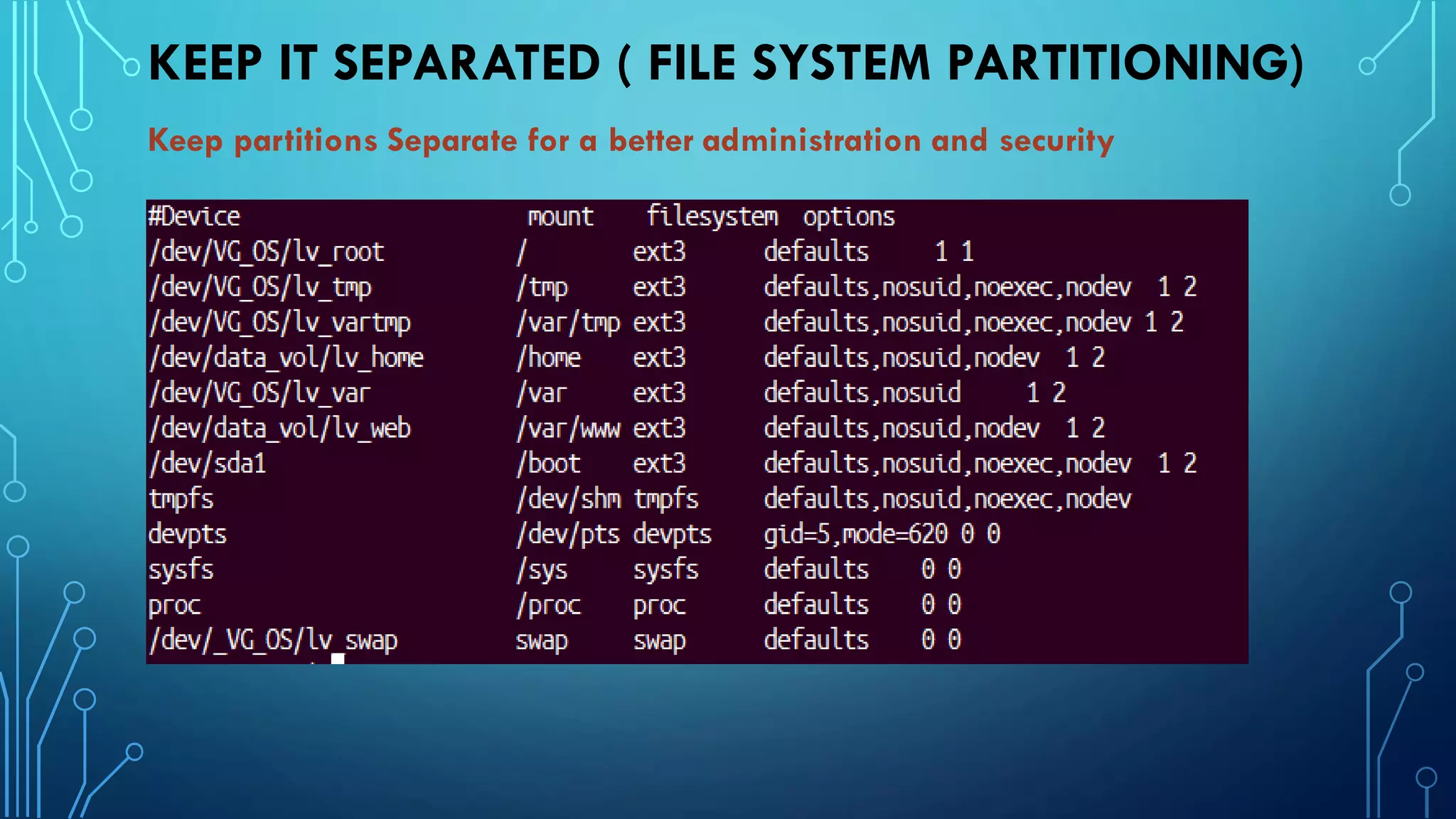
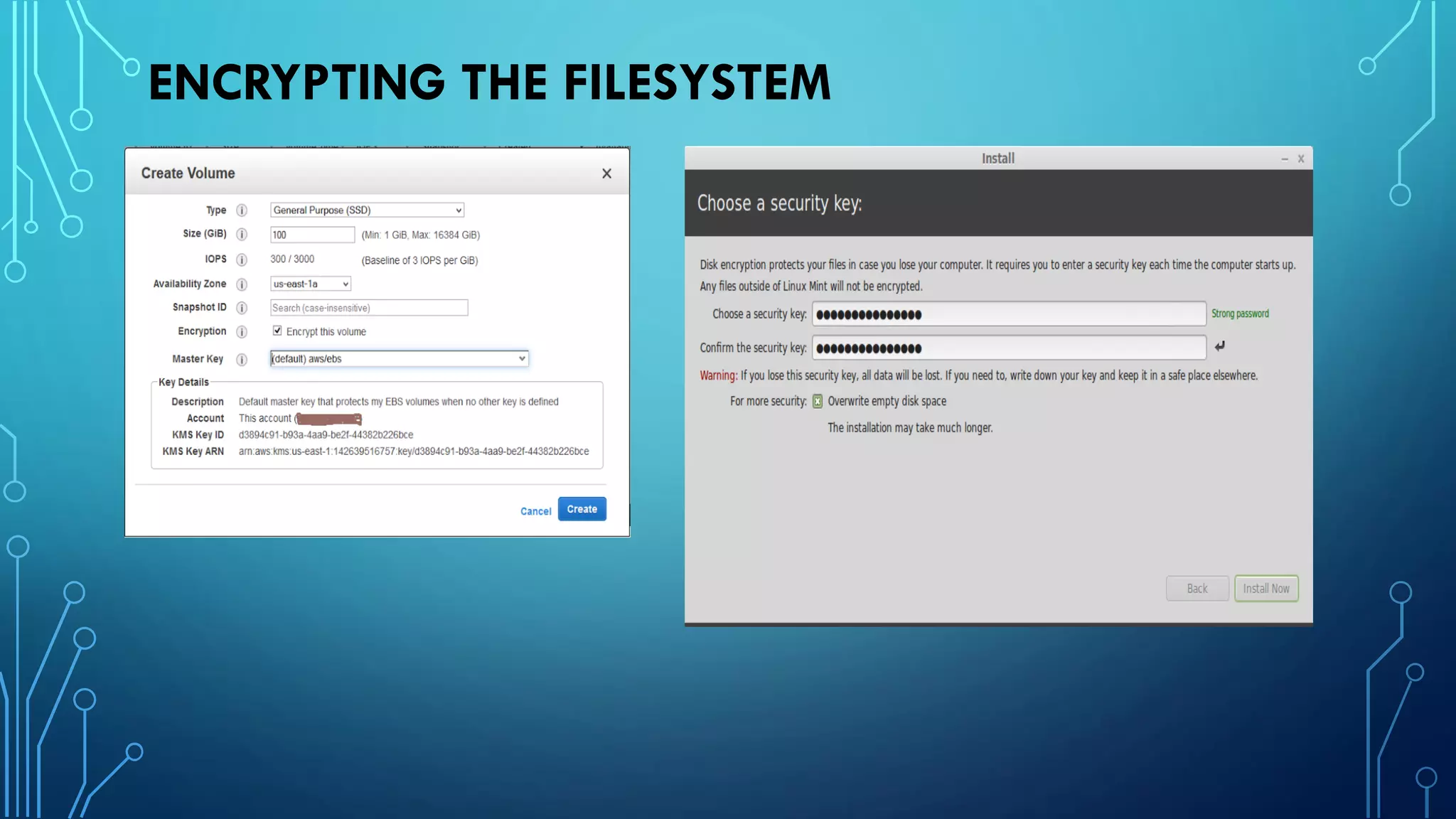
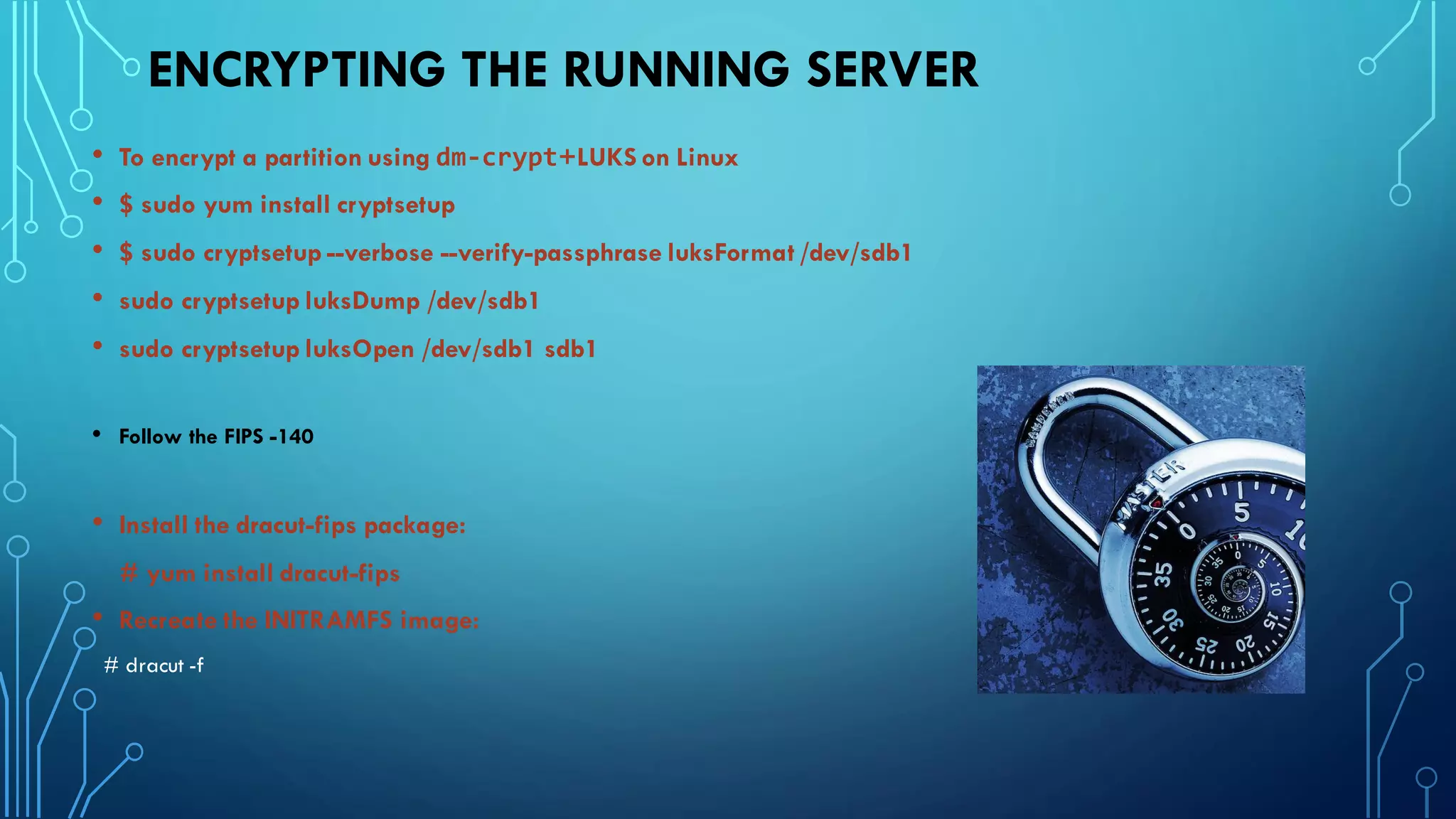
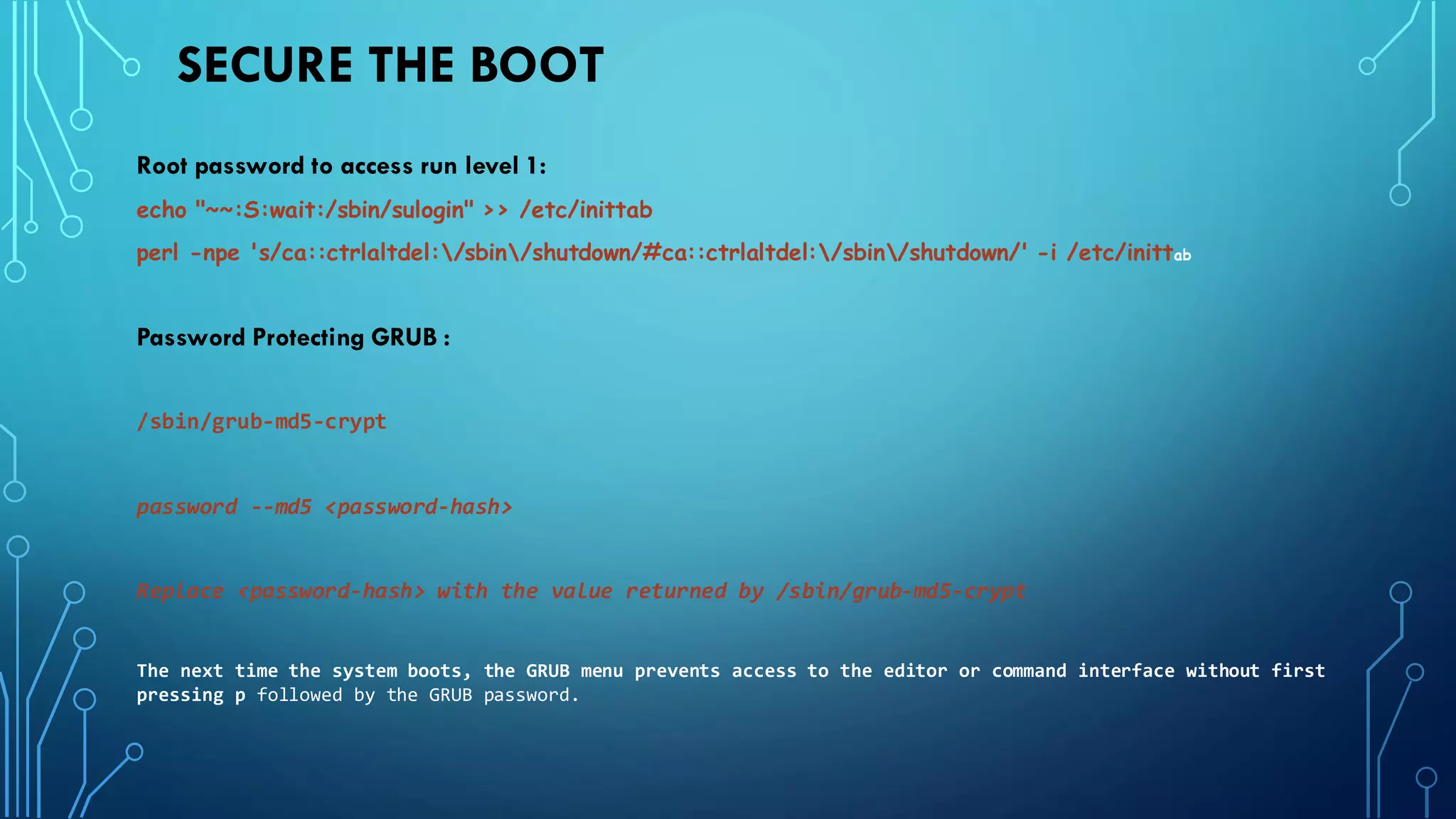
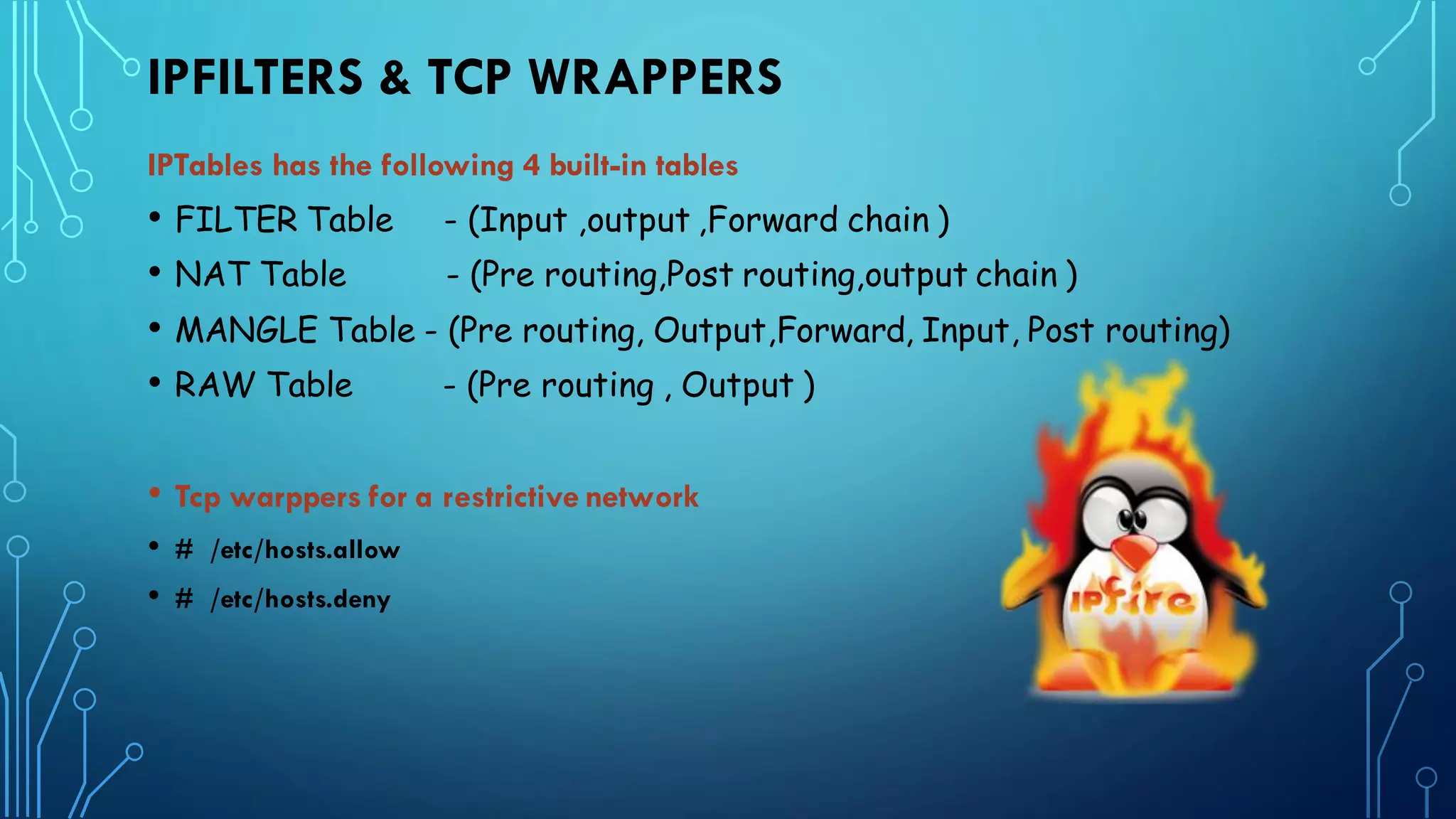
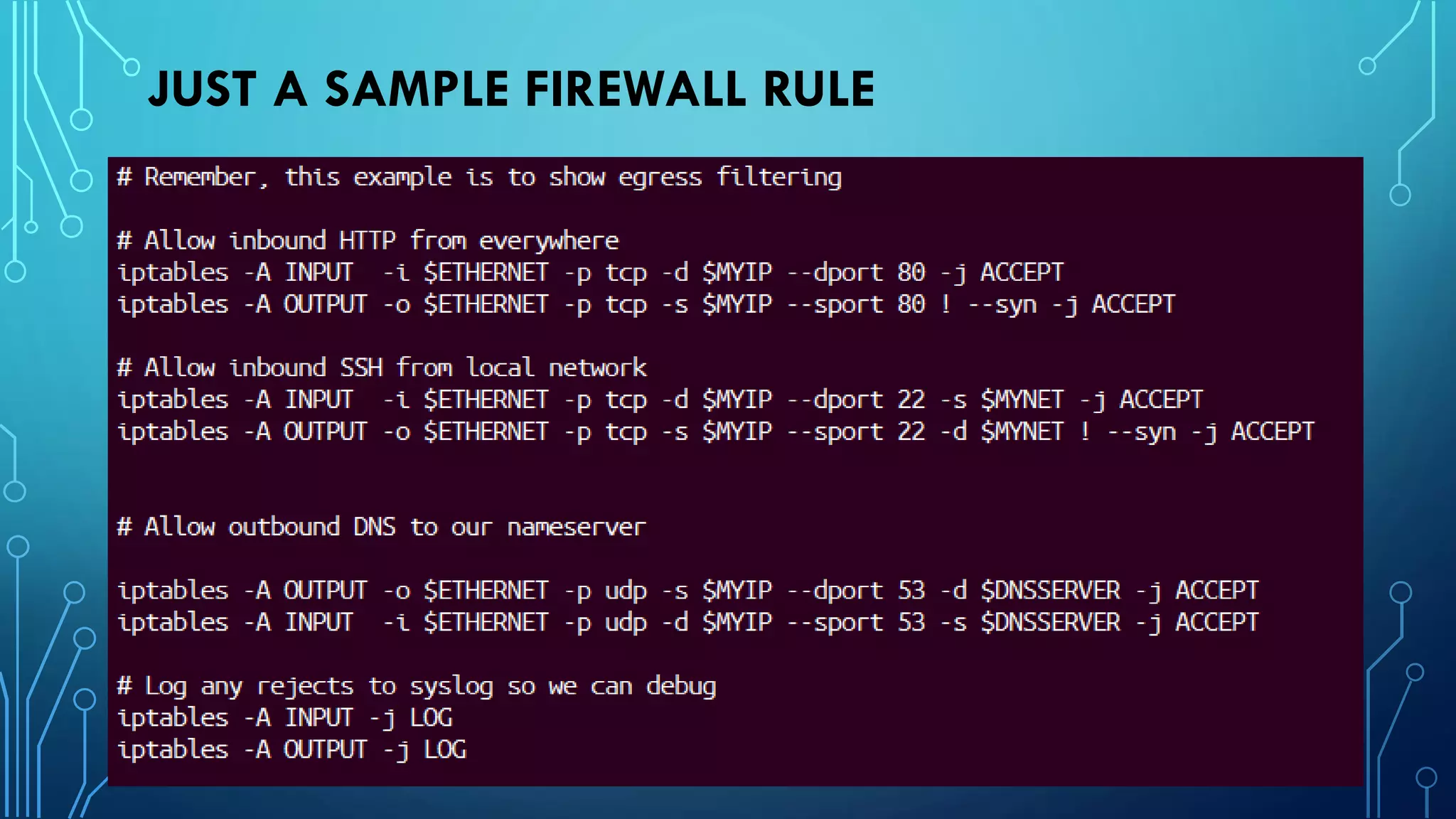
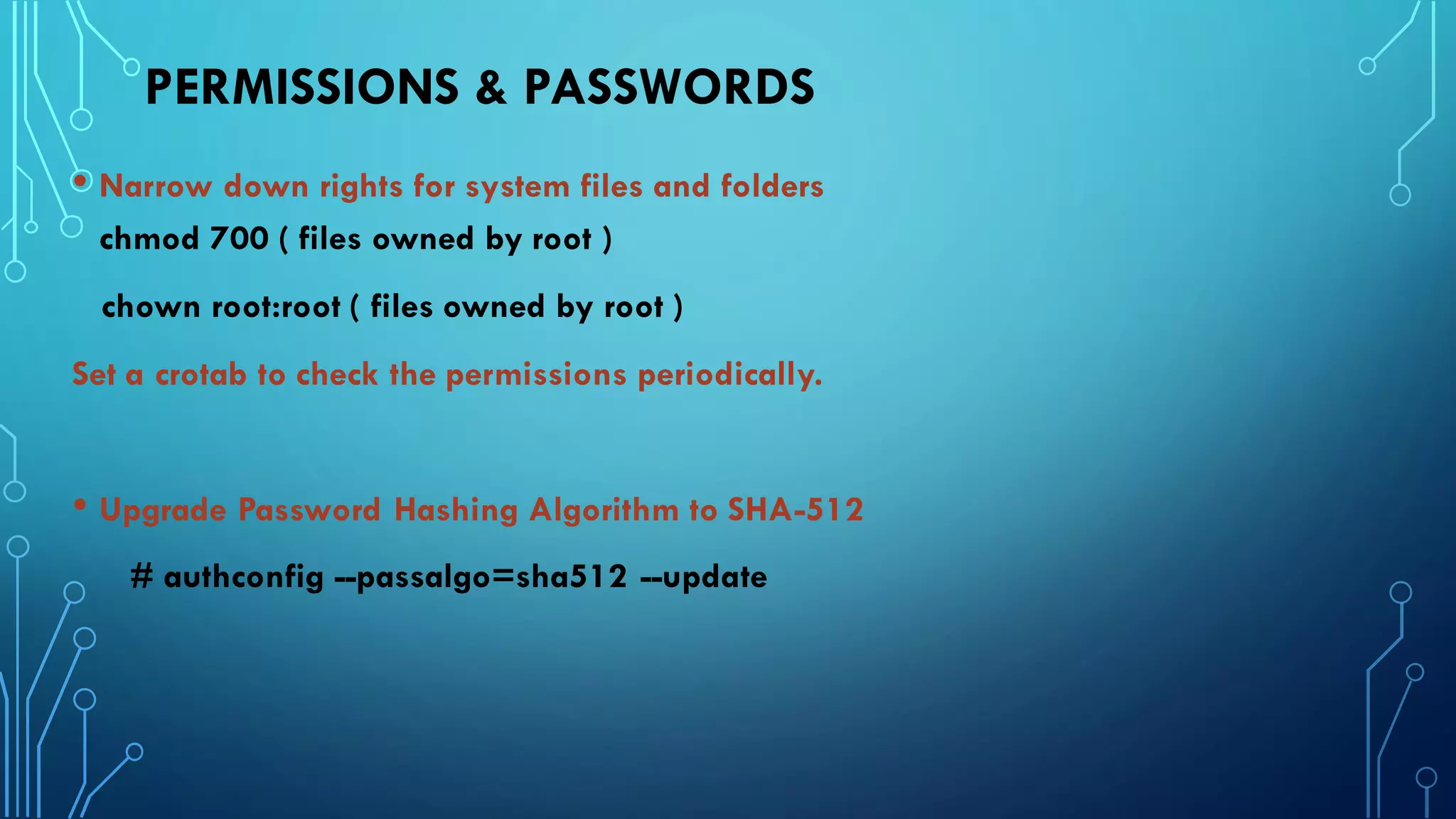
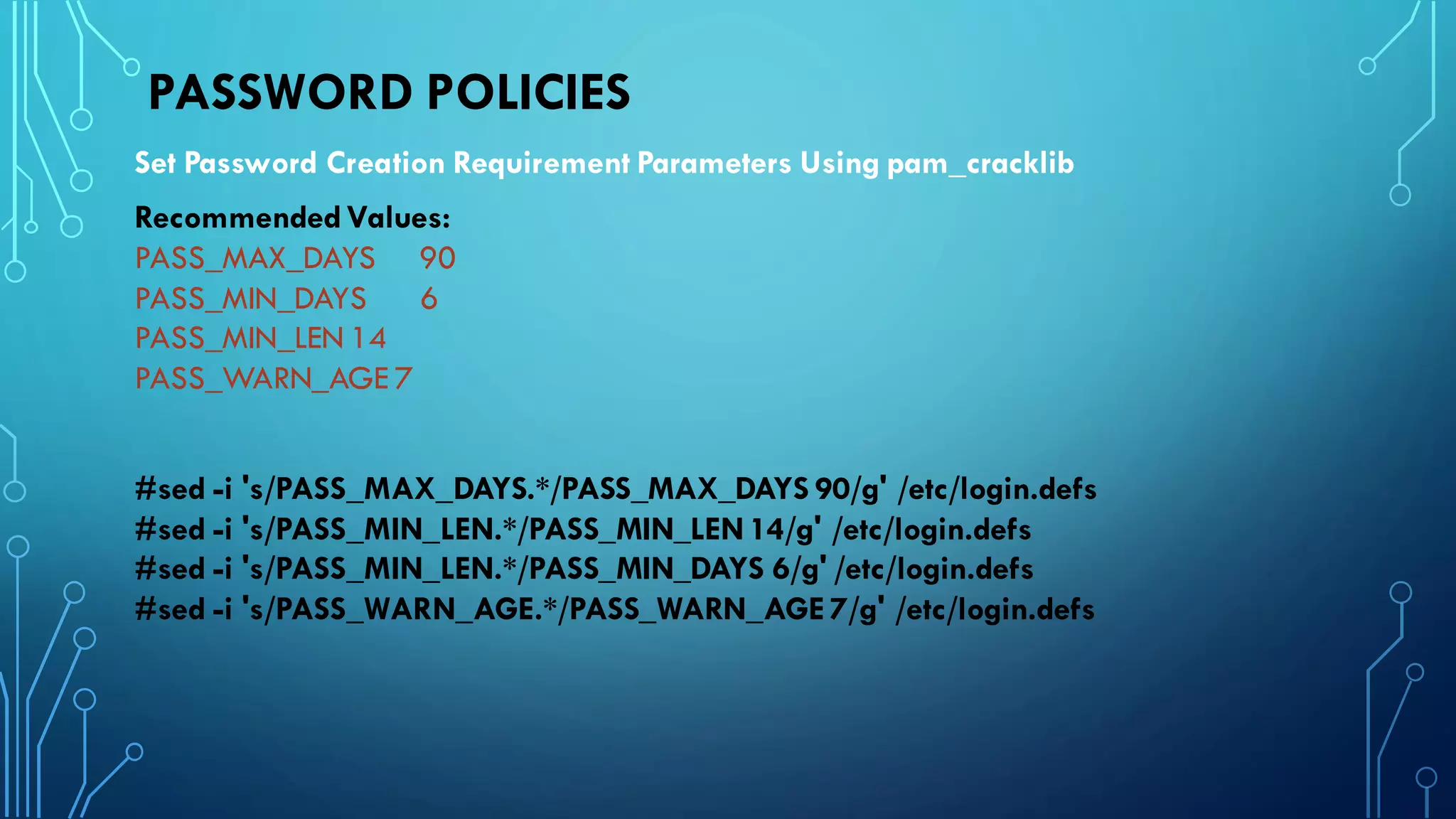
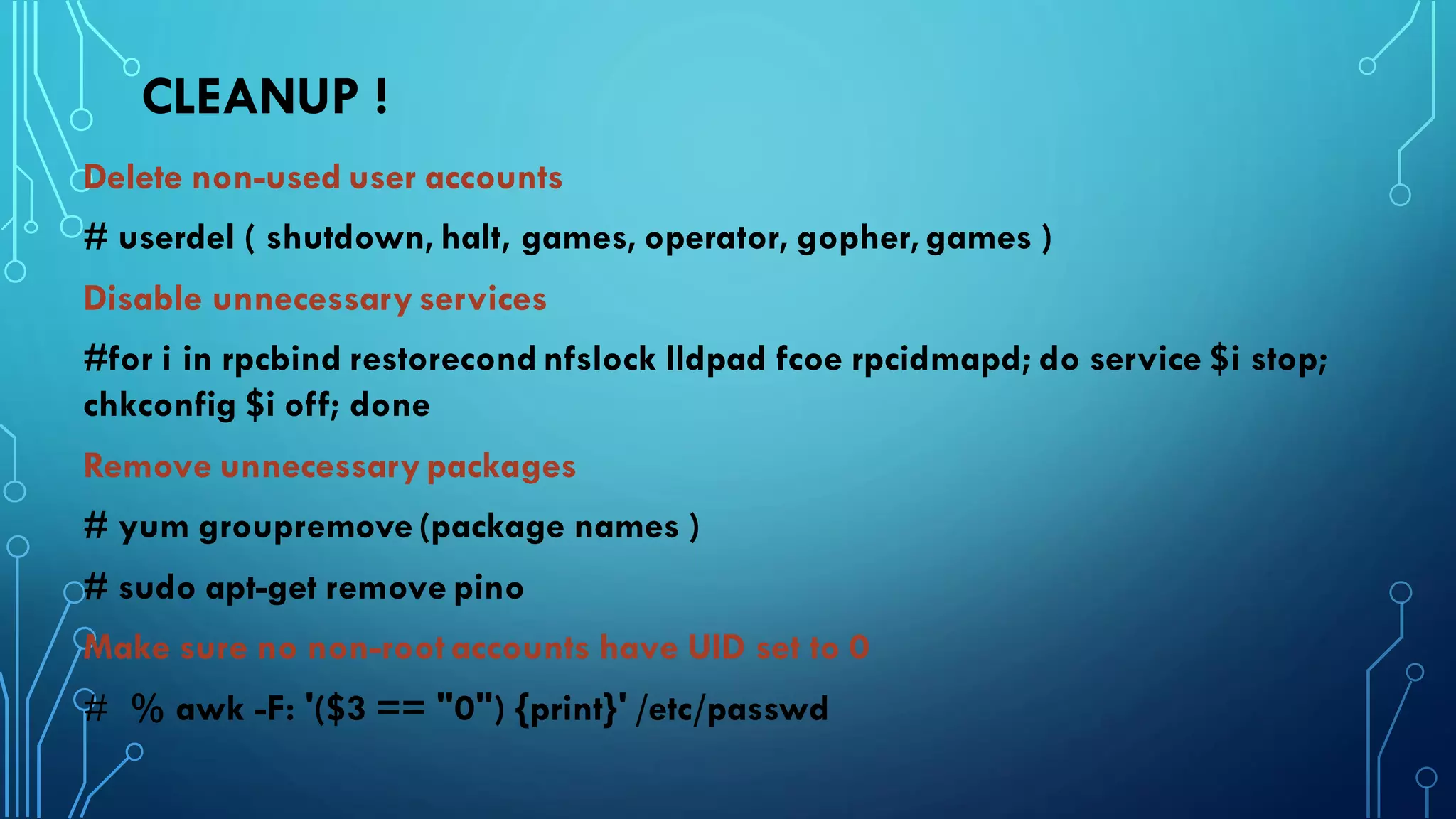
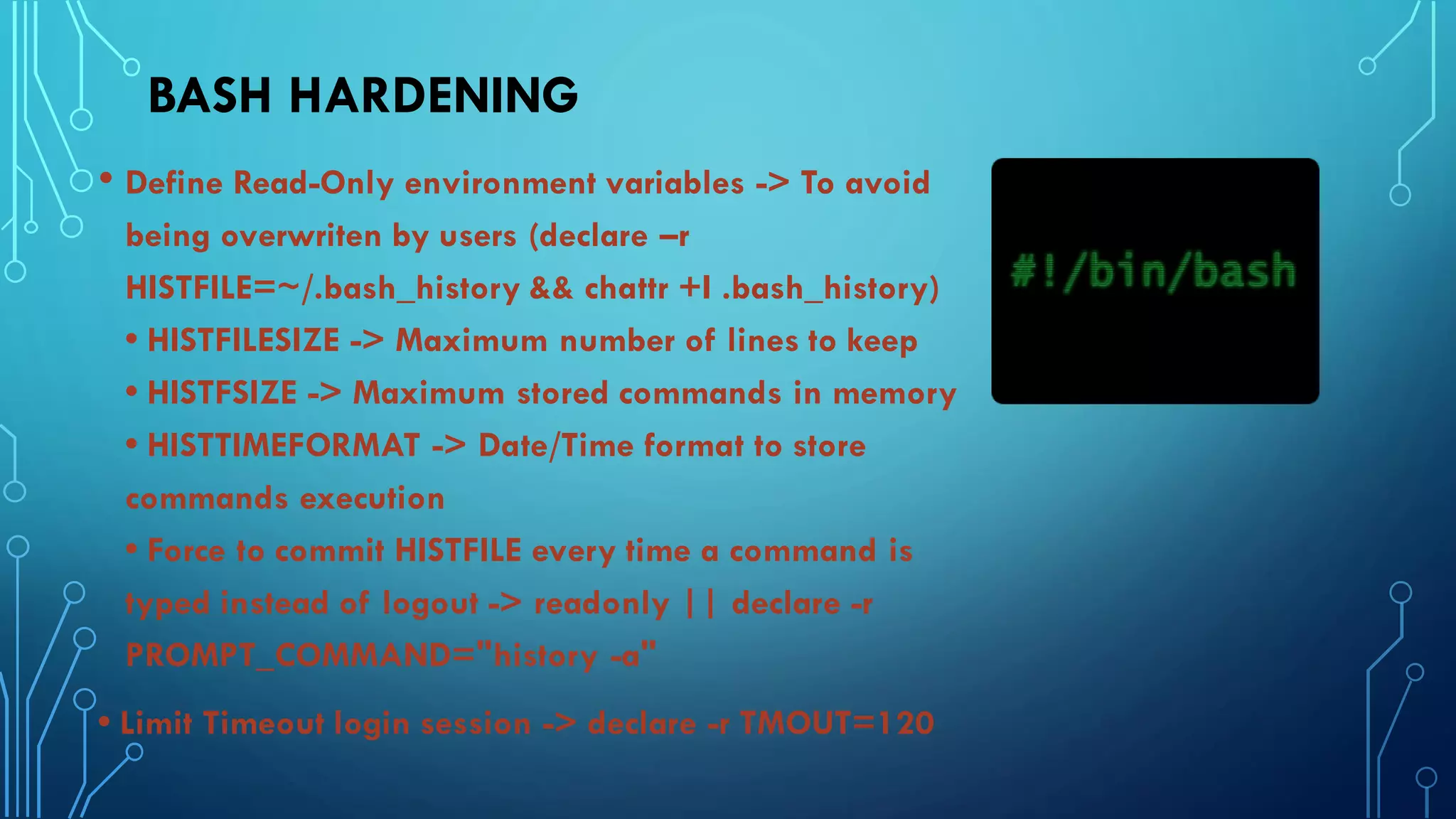
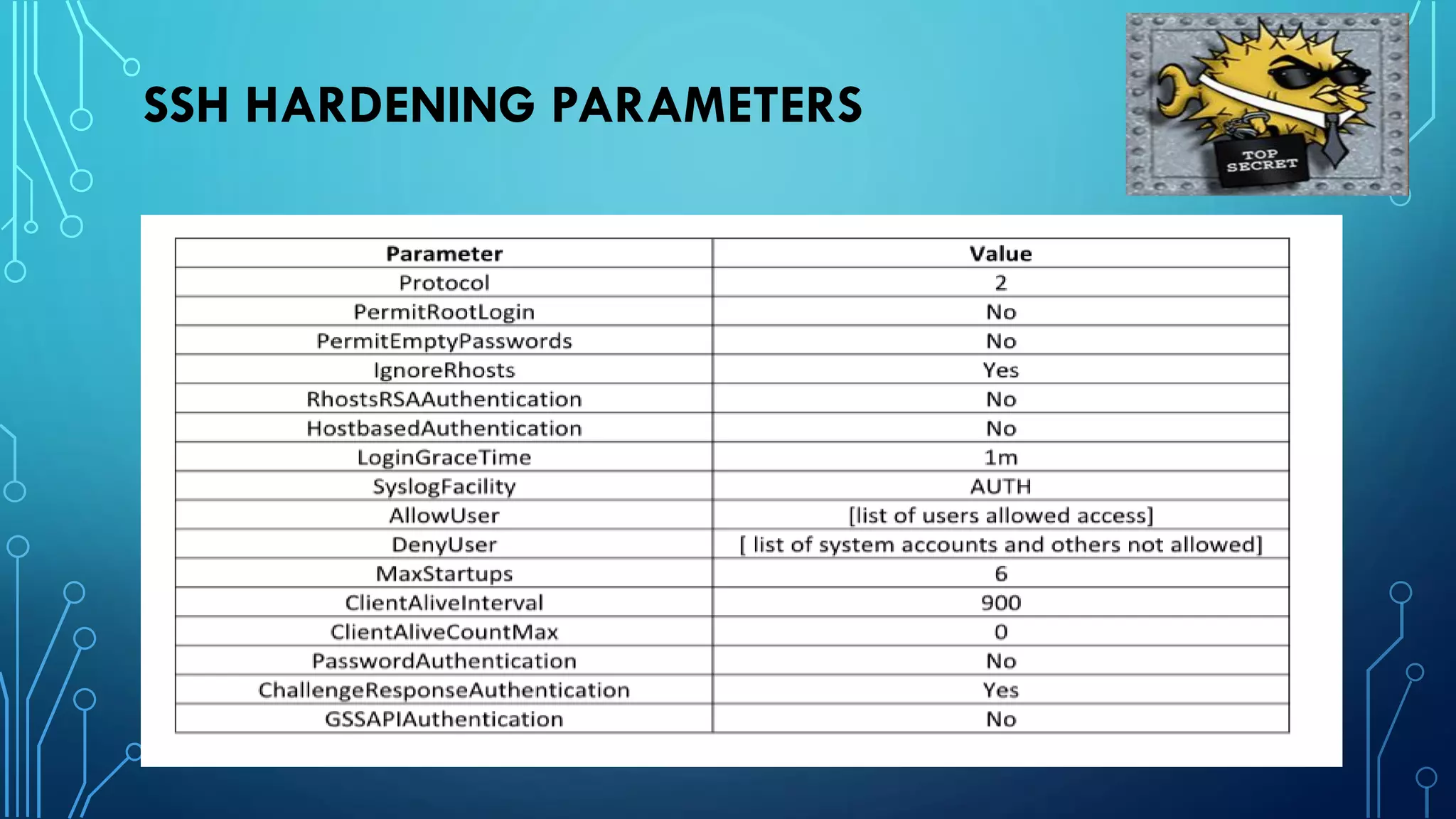
This document provides guidance on hardening a Linux server for security. It recommends following the CIS and NSA security benchmarks. It suggests choosing a server-oriented Linux distribution, keeping partitions and filesystems separate, encrypting partitions and the running server, securing the boot process, using iptables and TCP wrappers for firewalls, restricting root access and using sudo, enforcing password policies, removing unnecessary packages and services, securing remote administration like SSH, disabling unnecessary Linux modules, and implementing auditing and integrity checks.










![KEY BASED AUTHENTICATION
# ssh-keygen
Created directory '/home/username/.ssh'. Enter
passphrase (empty for no passphrase): Enter same
passphrase again:
Your identification has been saved in
/home/username/.ssh/id_rsa. Your public key has
been saved in /home/username/.ssh/id_rsa.pub. The
key fingerprint is:
a9:49:2e:2a:5e:33:3e:a9:de:4e:77:11:58:b6:90:26
username@remote_host The key's randomart image is:
+--[ RSA 2048]----+ | ..o | | E o= . | | o. o | |
.. | | ..S | | o o. | | =o.+. | |. =++.. | |o=++.
| +-----------------+](https://image.slidesharecdn.com/null-hardeninglinux-150913110901-lva1-app6892/75/Linux-Hardening-nullhyd-22-2048.jpg)




