The document is a disclaimer for an educational presentation on machine learning that will be given by Hendri Karisma. It states that the presentation is intended for educational purposes only and does not replace independent professional judgment. It also notes that any opinions or information presented are those of the individual participants and may not reflect the views of the company, and that the company does not endorse or approve the content.

















![Fraud Detection
Payment Fraud (phishing,
account take-over, carding)
System abuse (promo, content,
account, logistic and payment
methods especially COD)
Fraud not only result in financial
losses but also produce some
reputational risk.
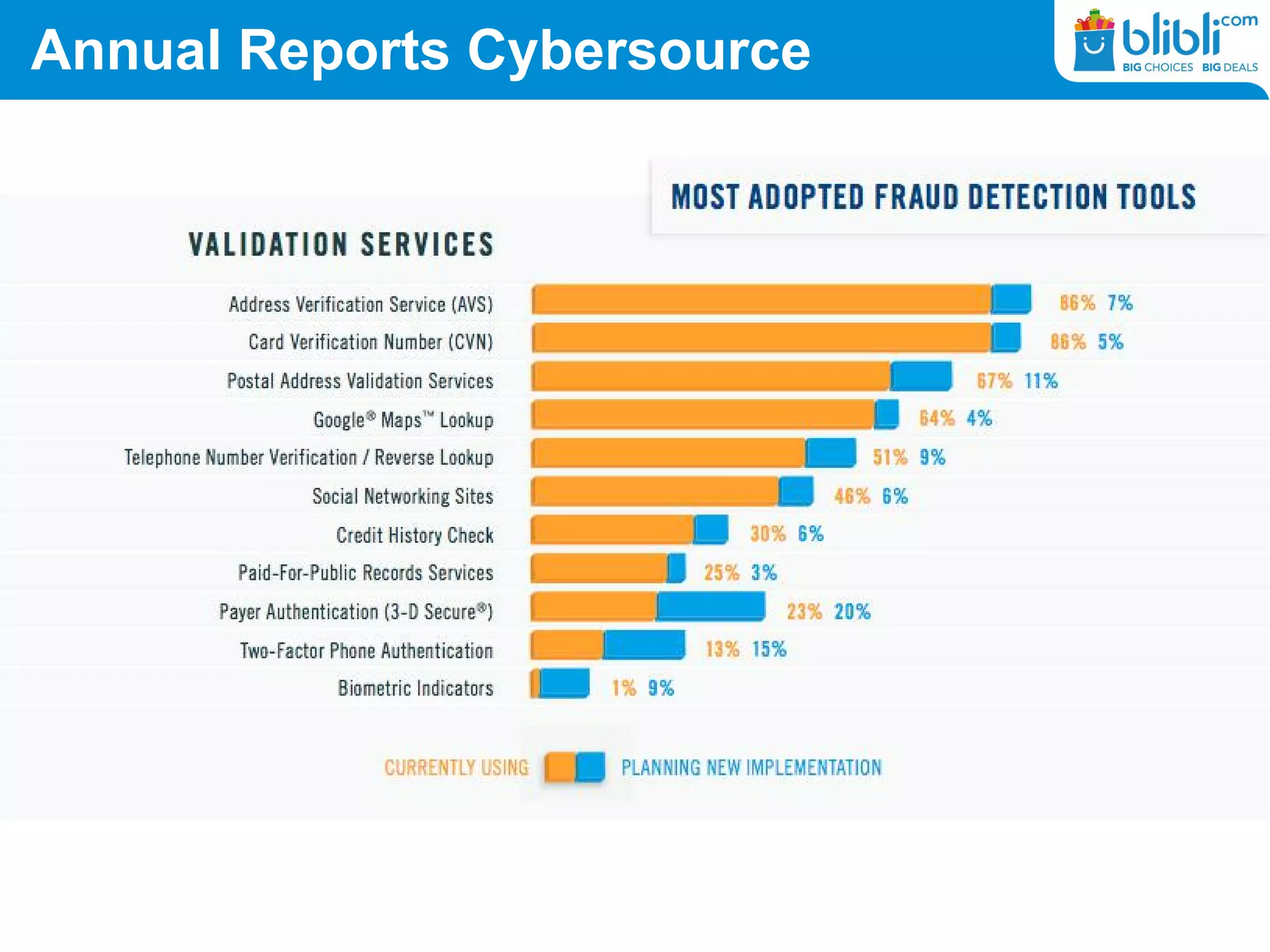
Some security measures has
been taken by bank or another
multinational finance service.
[E. Duman et al, 2013]](https://image.slidesharecdn.com/aimlshare-191023044428/75/Machine-Learning-an-Introduction-and-cases-56-2048.jpg)