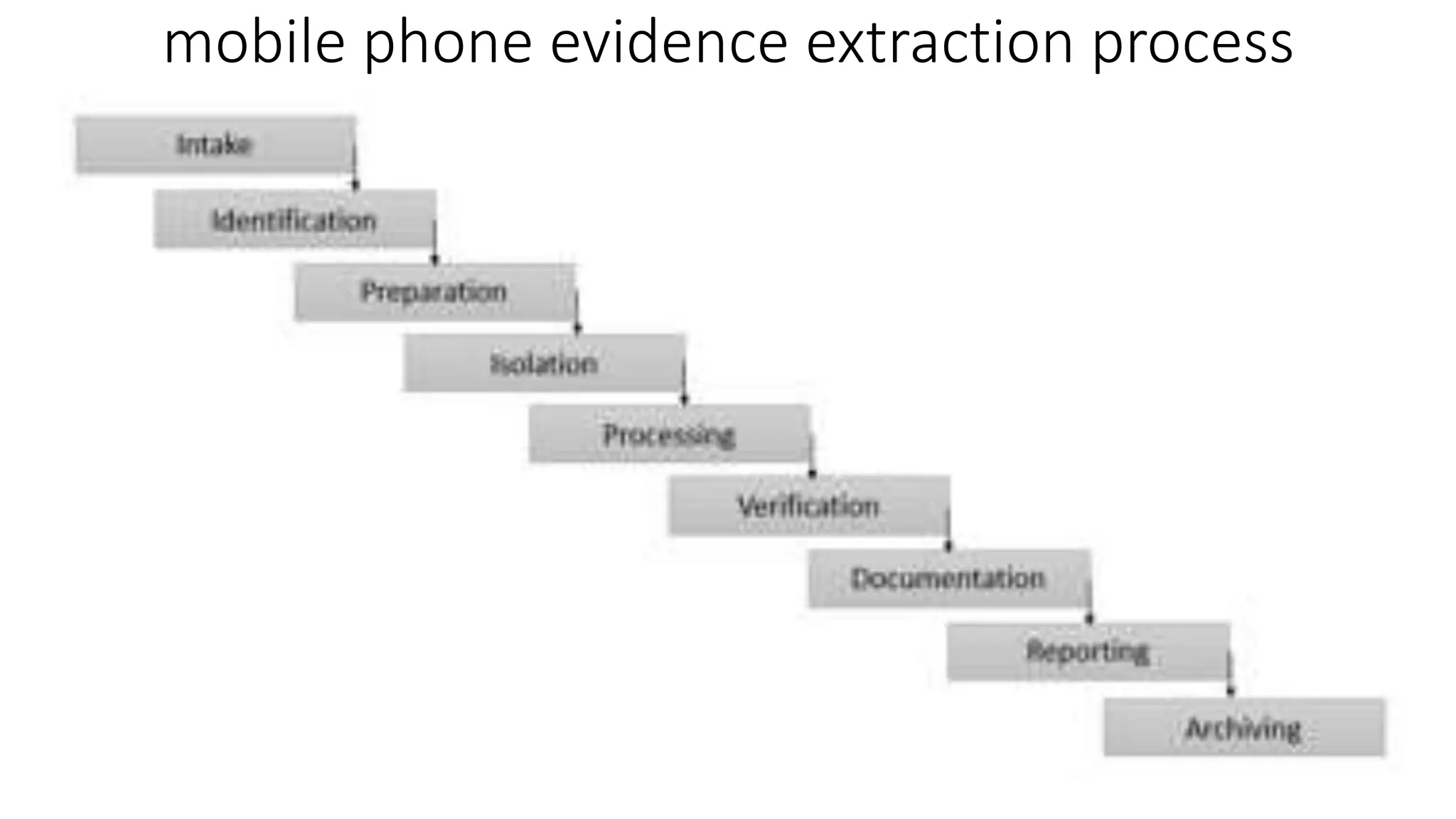
Mobile forensics involves the collection, analysis, and preservation of digital evidence from mobile devices to aid in cybercrime investigations. Given the ubiquity of mobile devices, this field addresses various challenges such as legal compliance, data integrity, and device security features. Key processes include evidence intake, identification, isolation, processing, verification, documentation, and archiving of digital data from these devices.