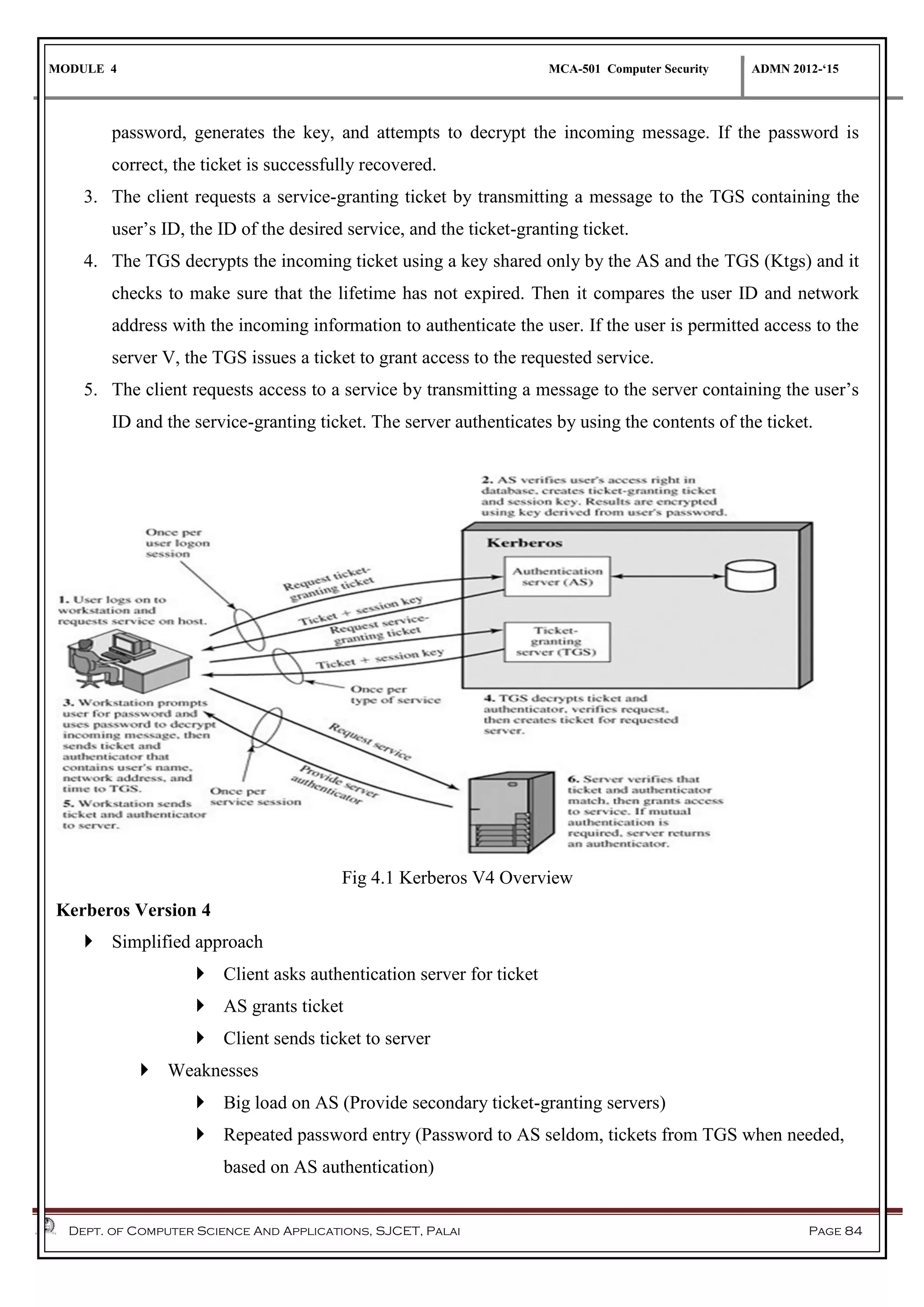
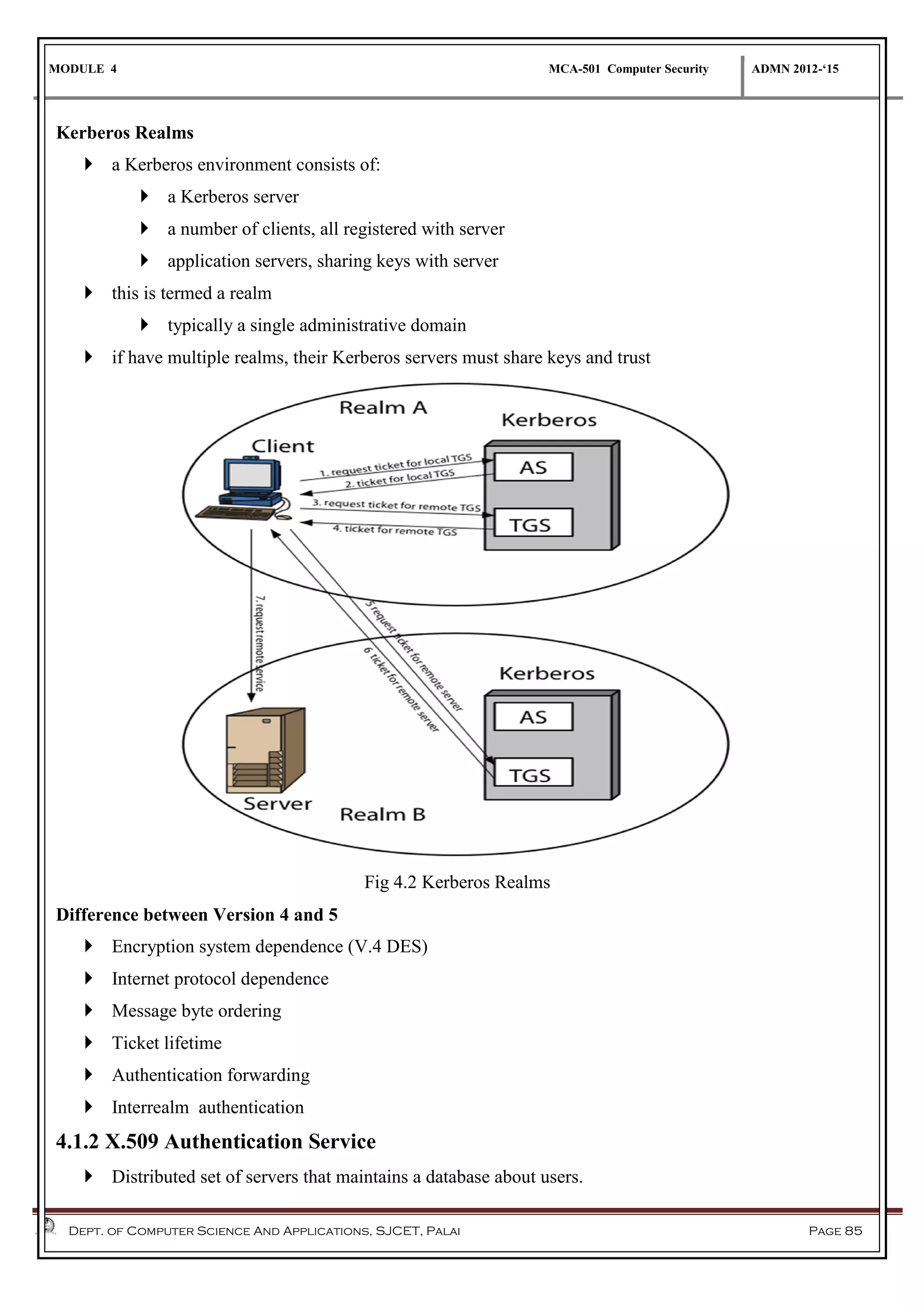
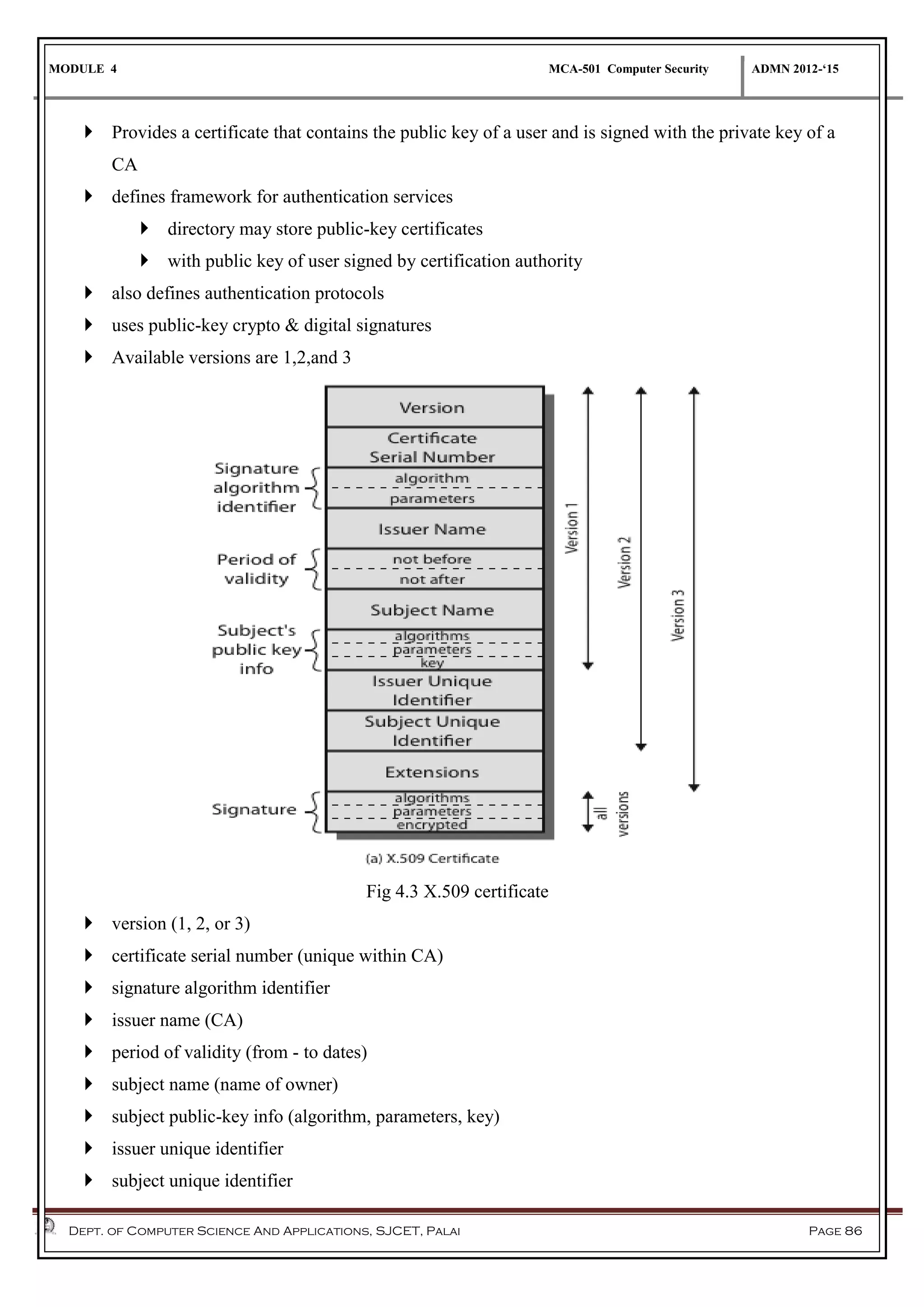
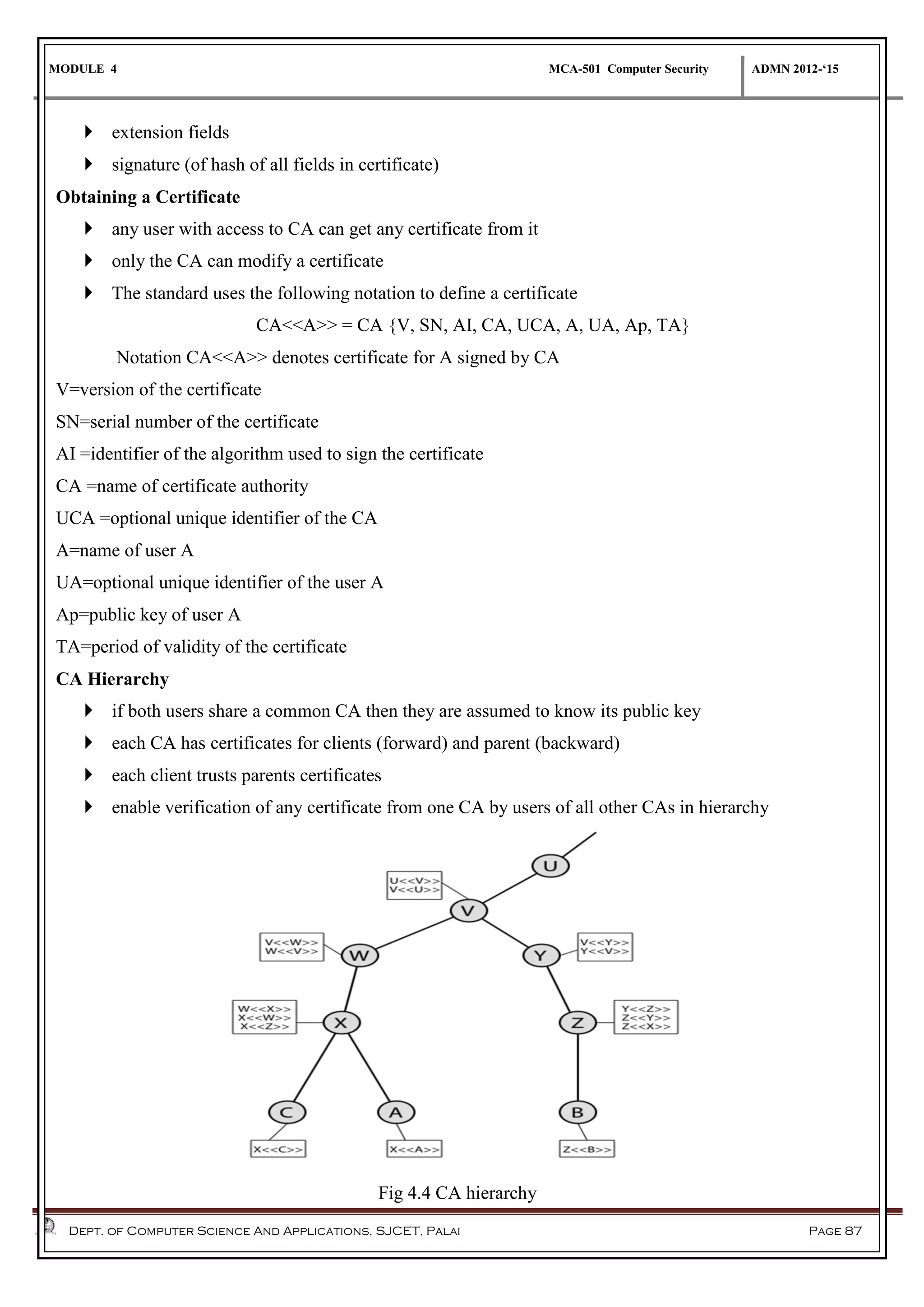
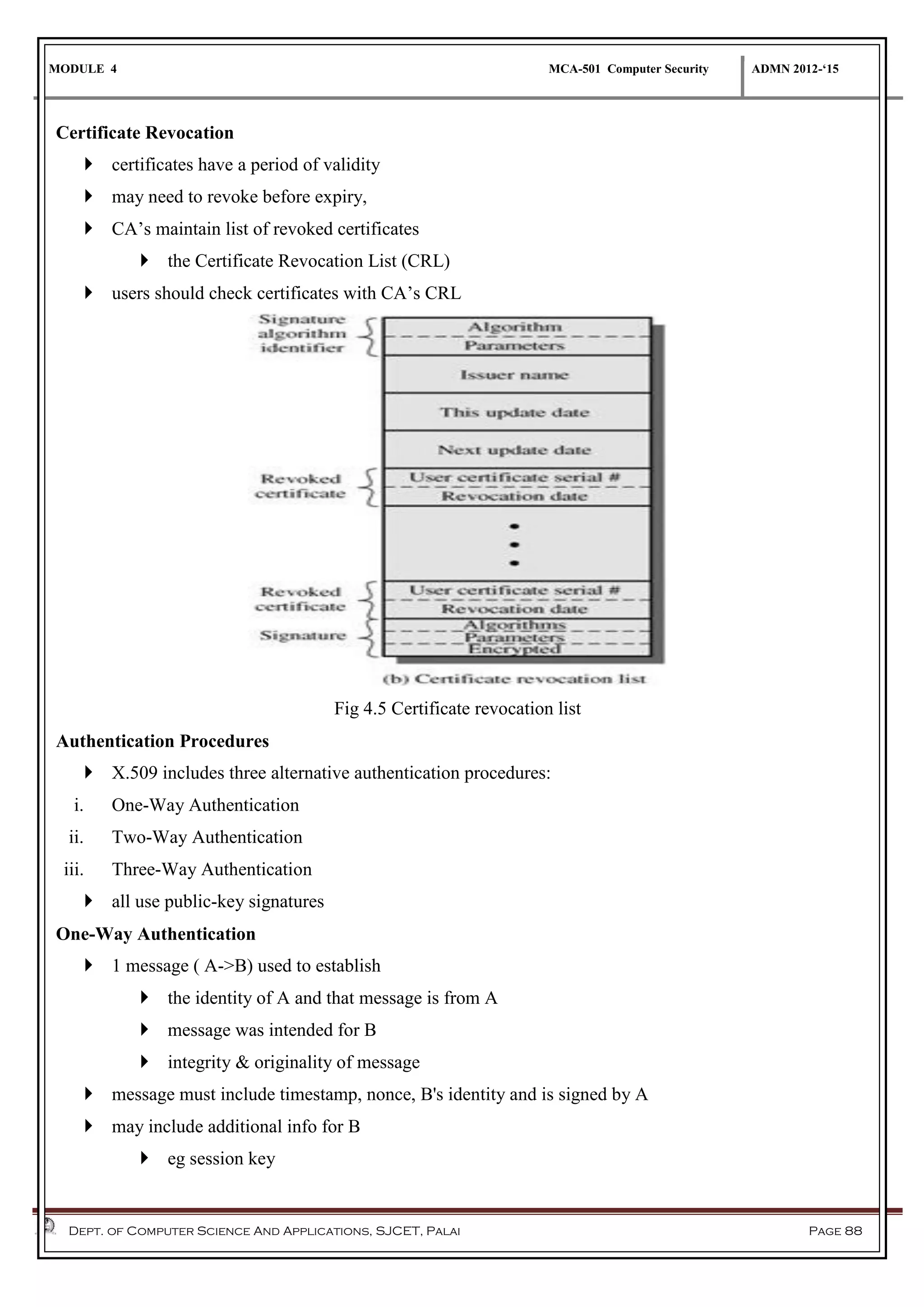
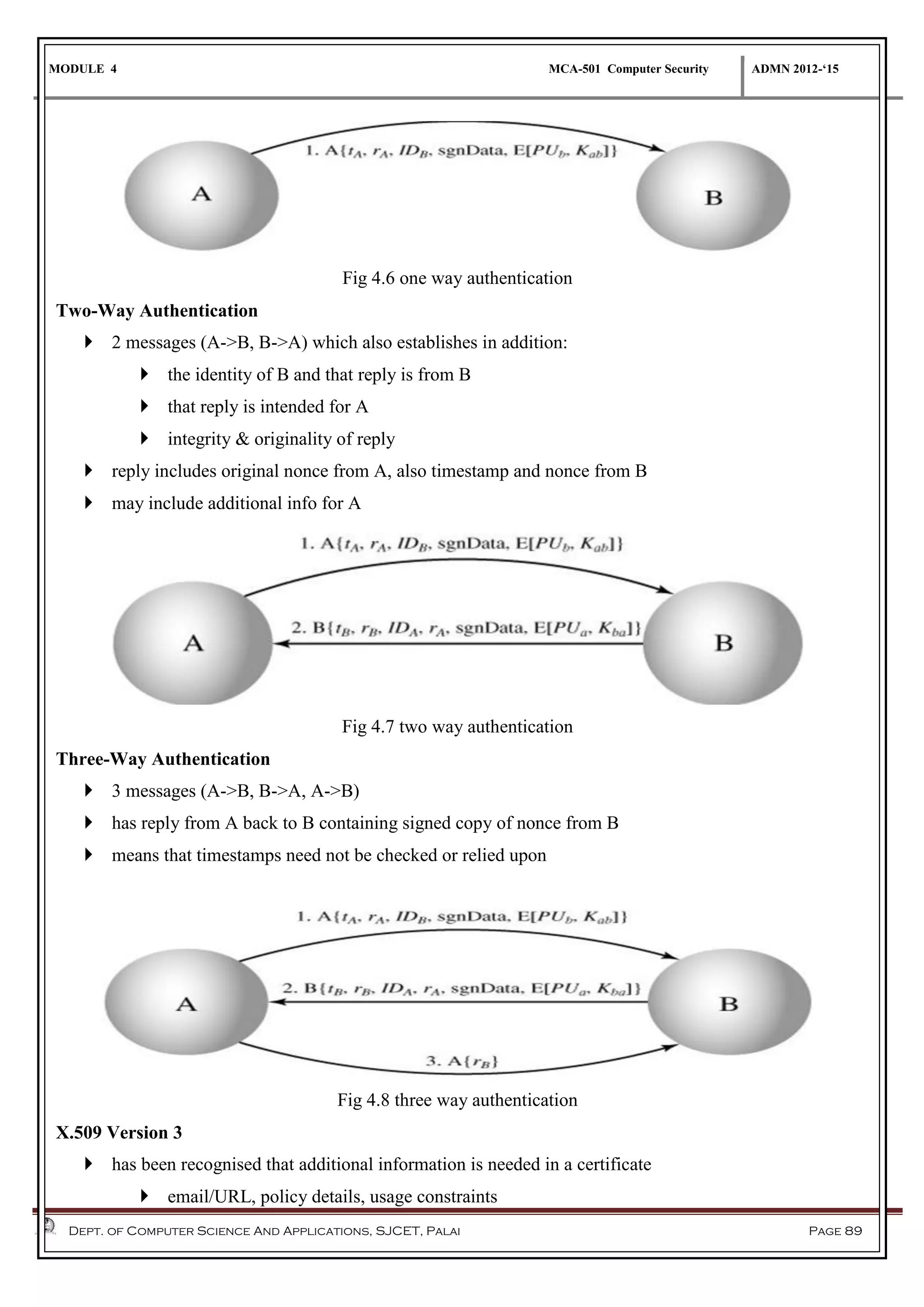
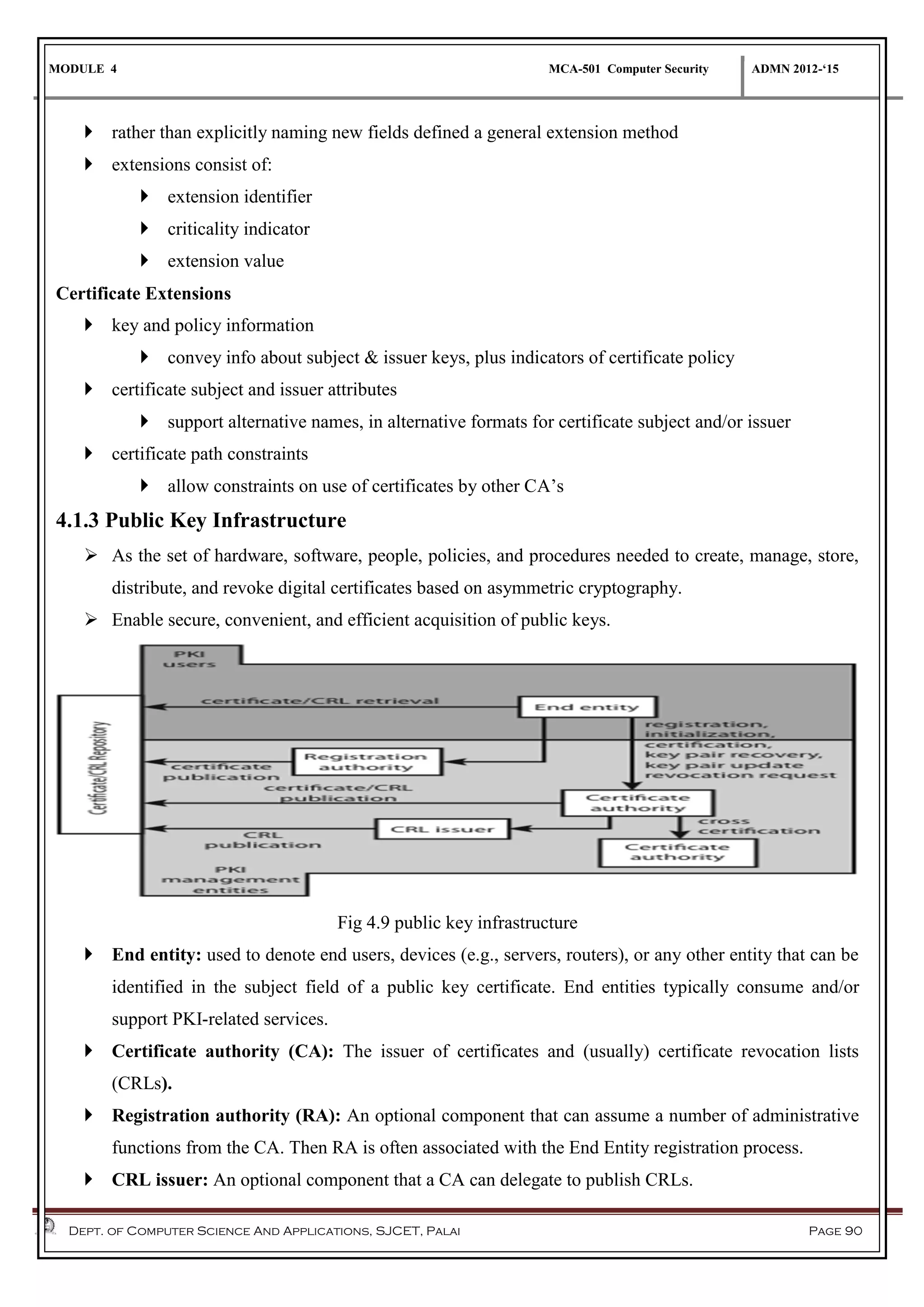
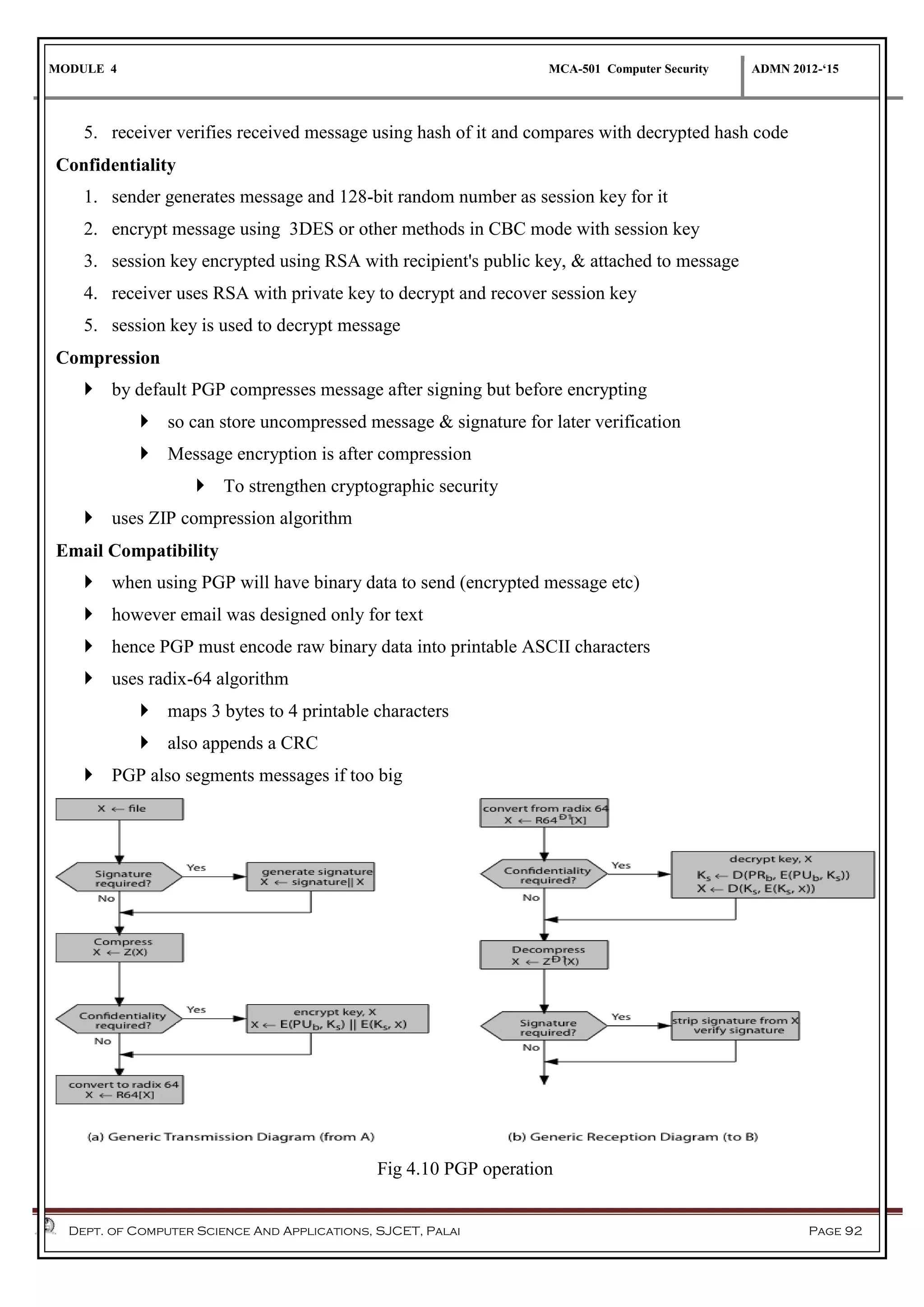
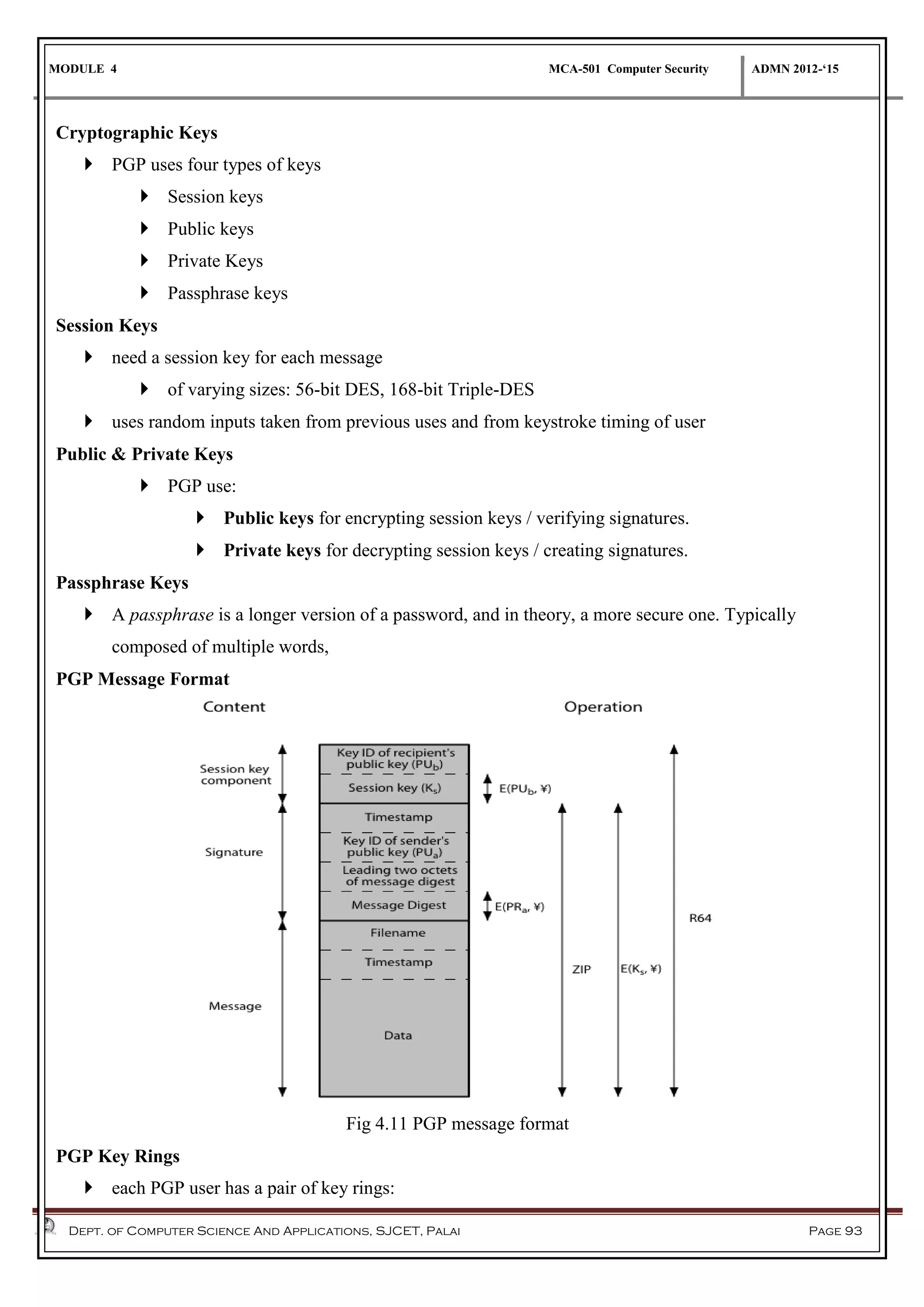
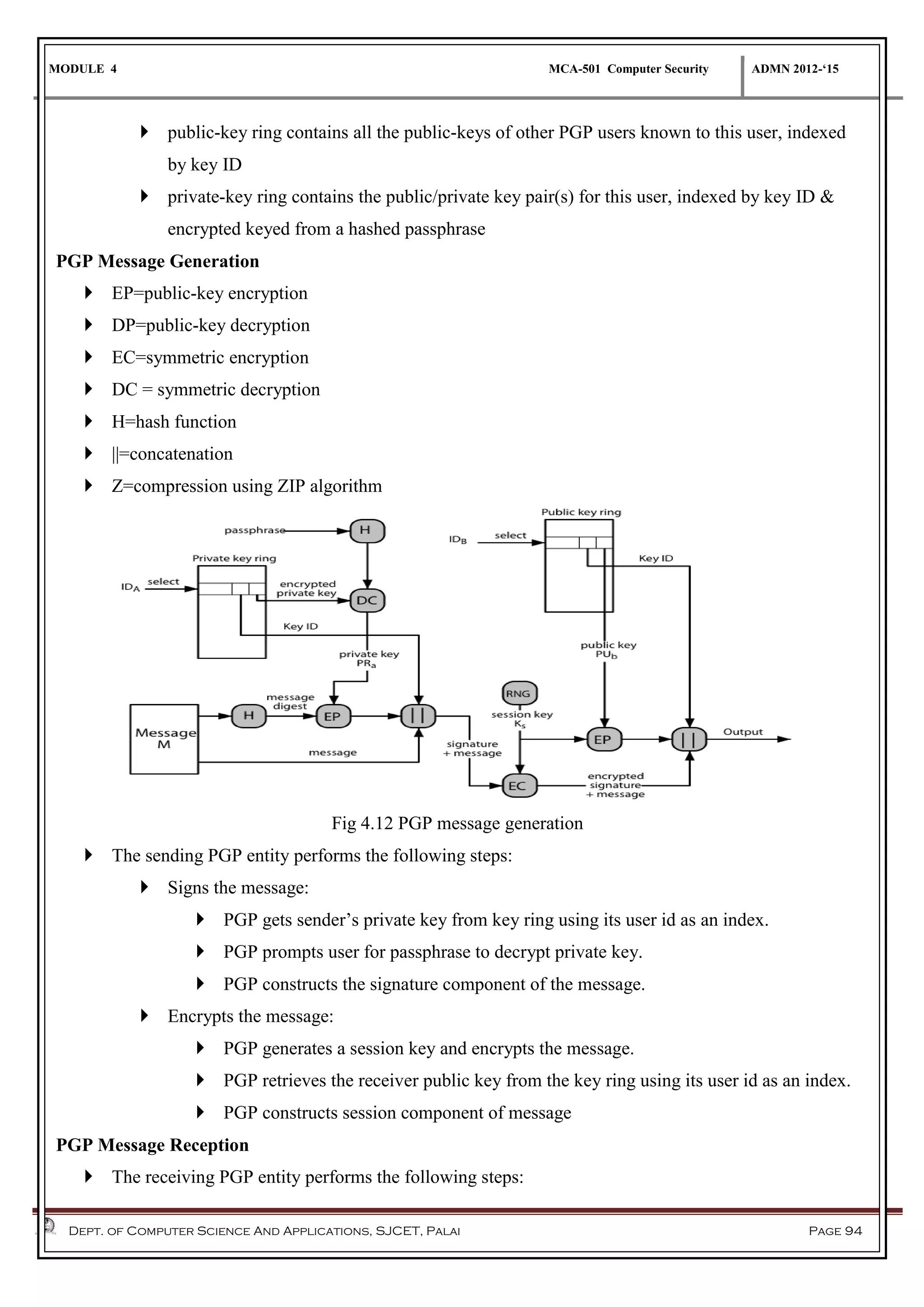
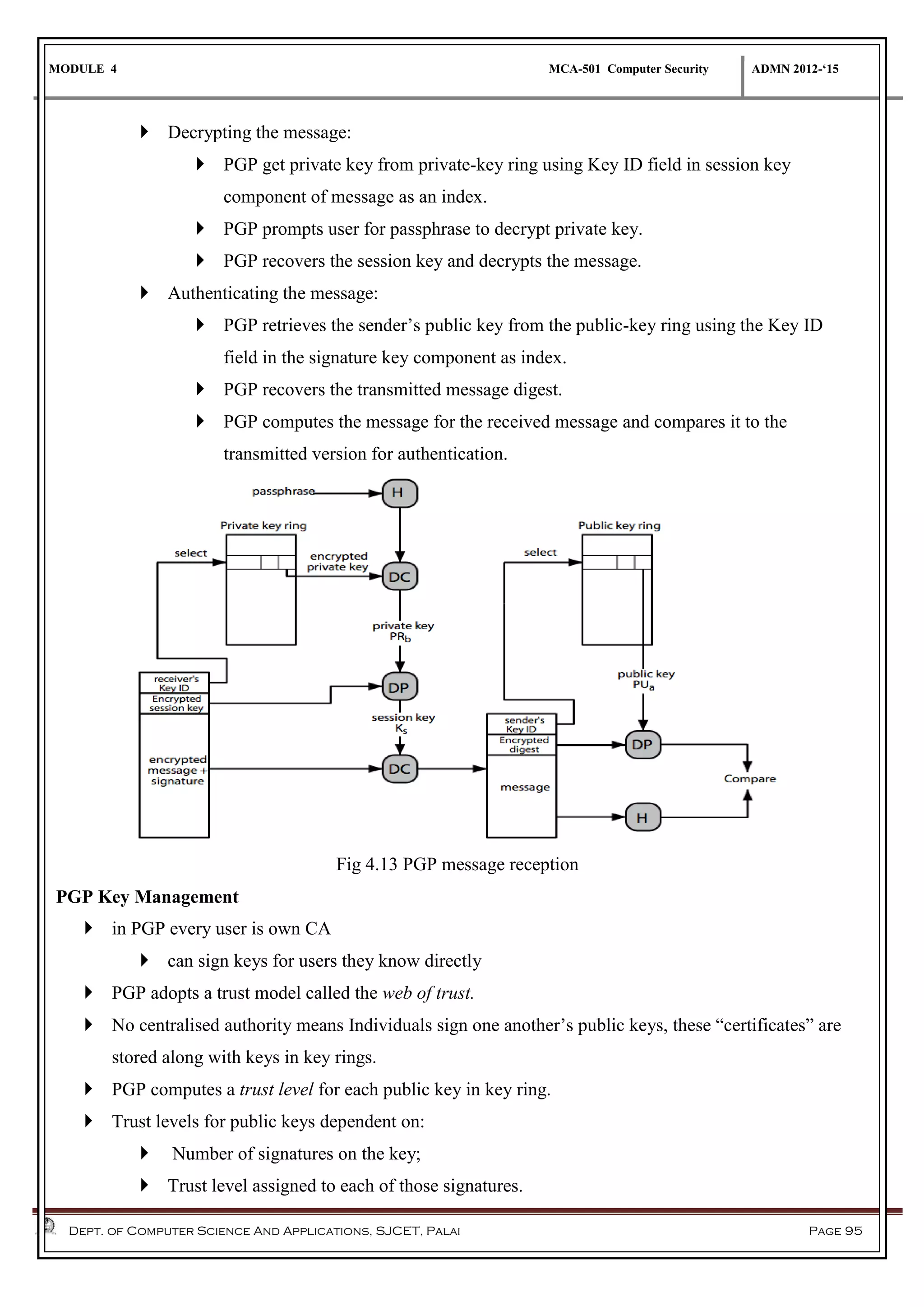
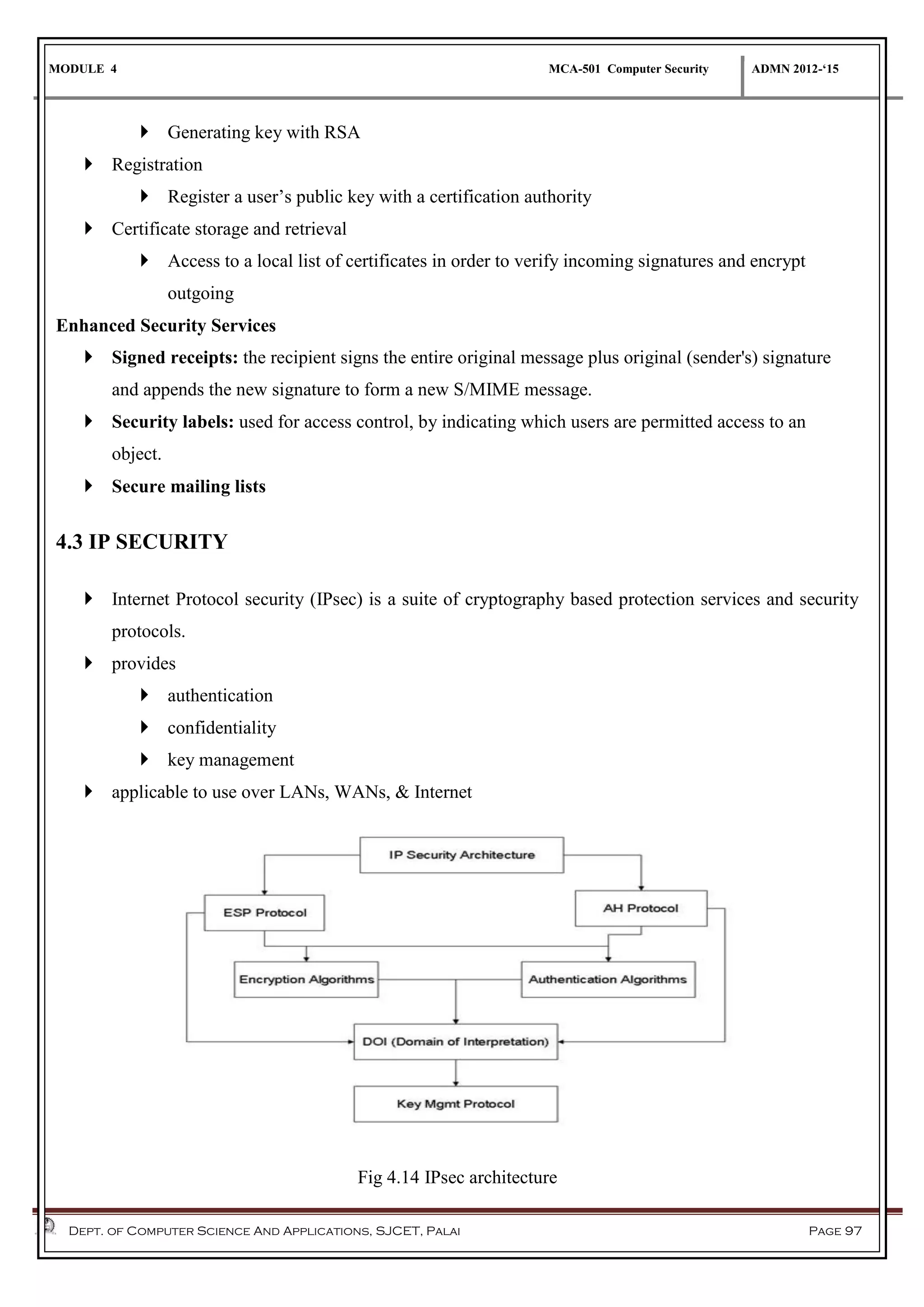
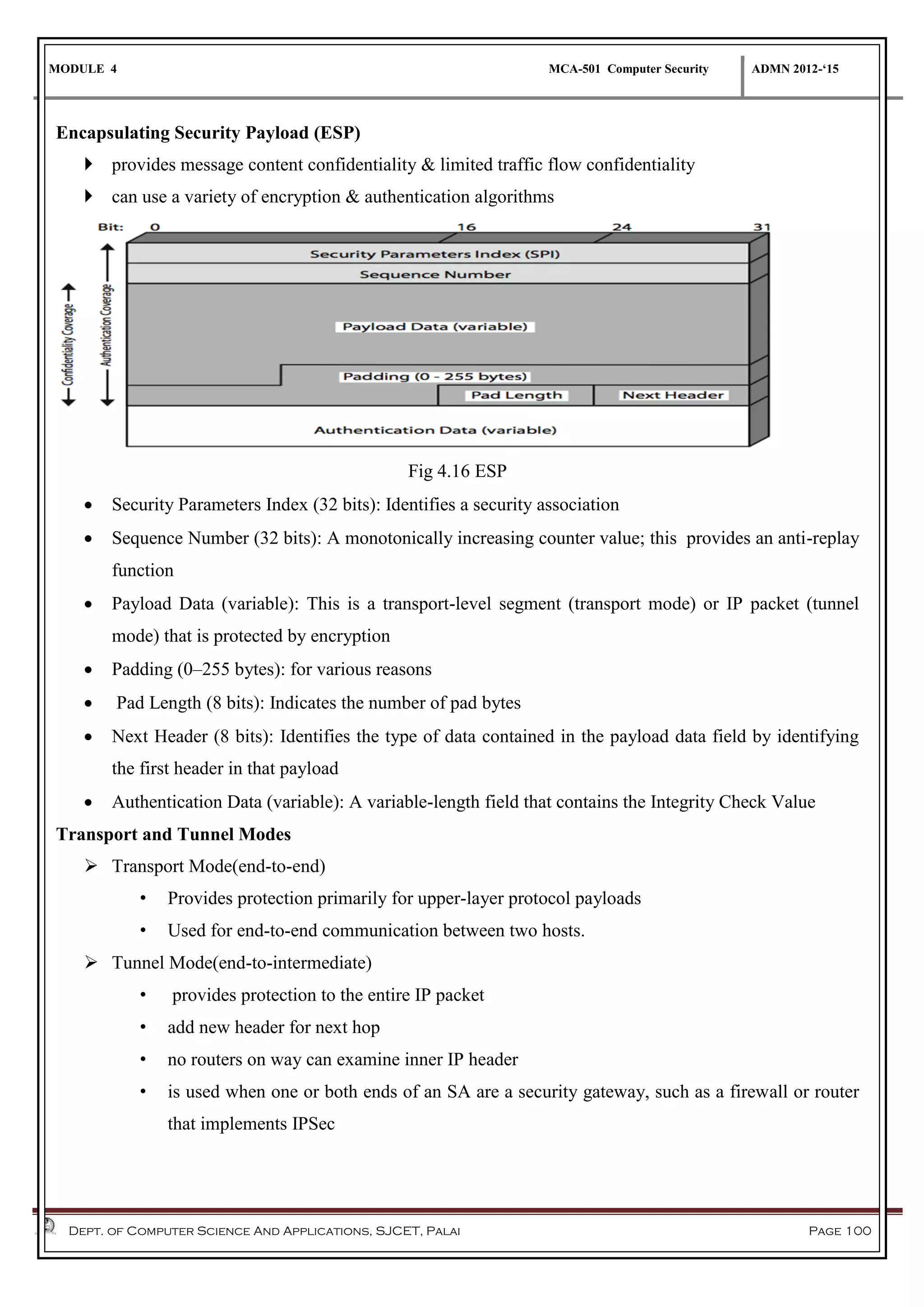
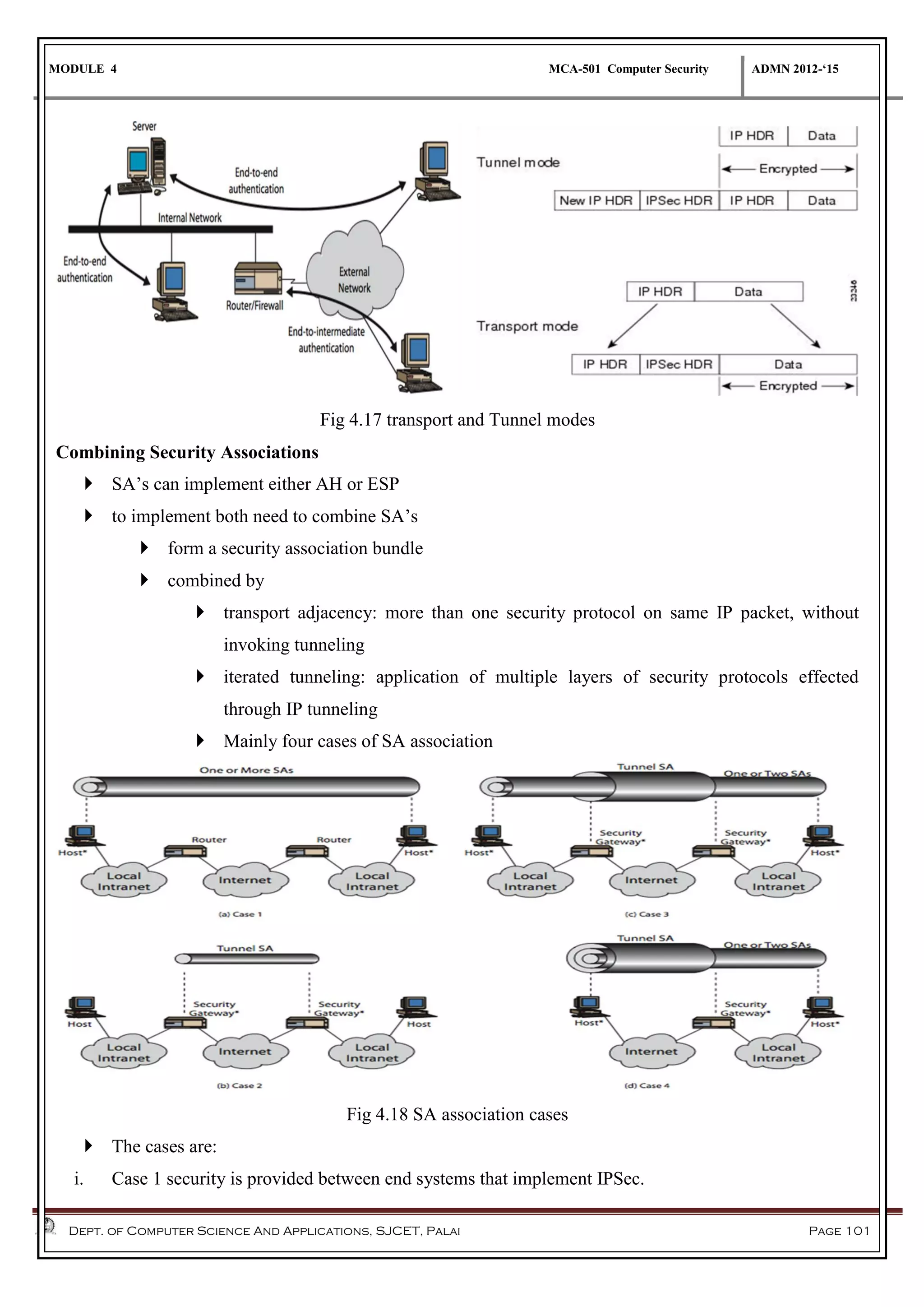
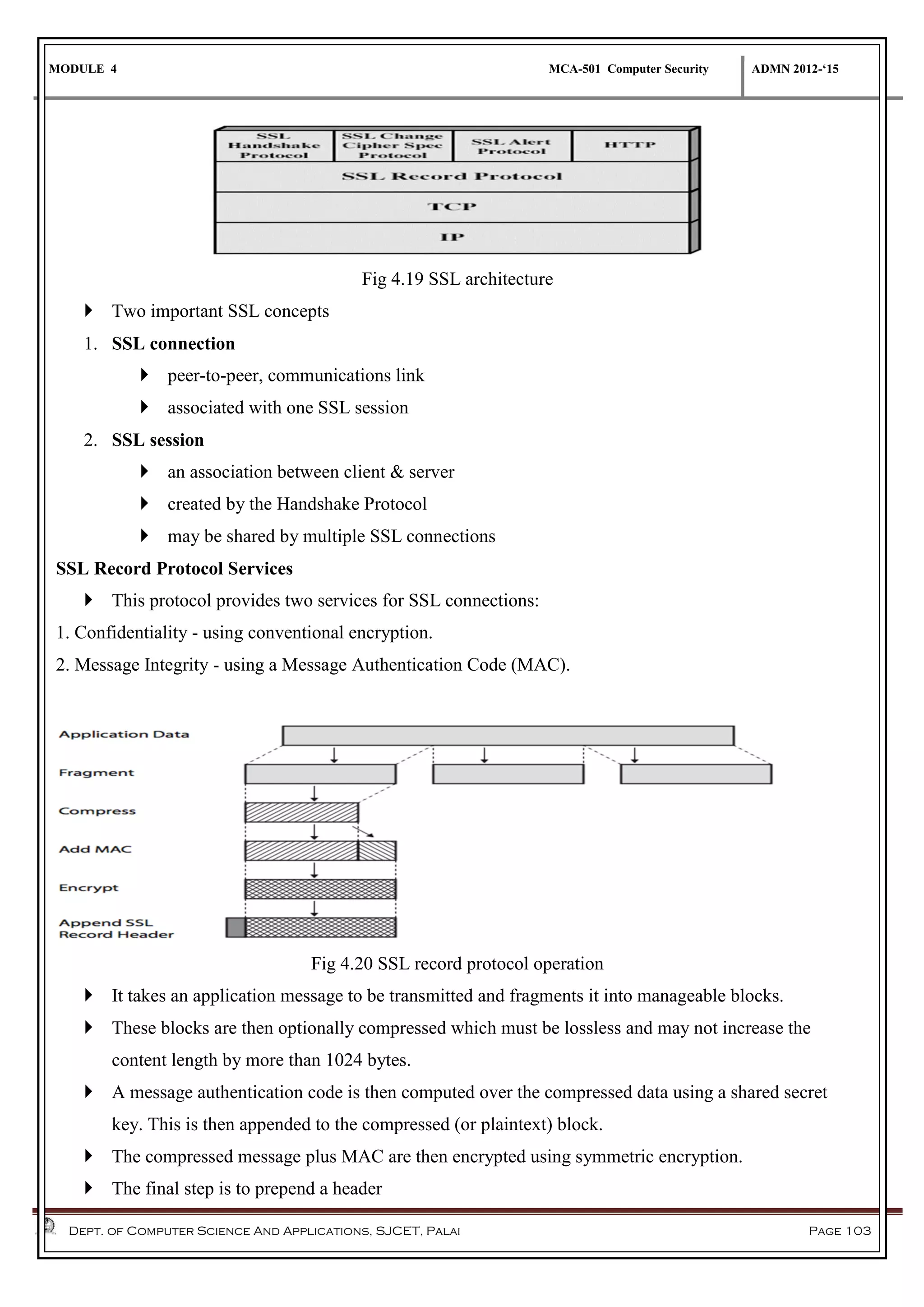
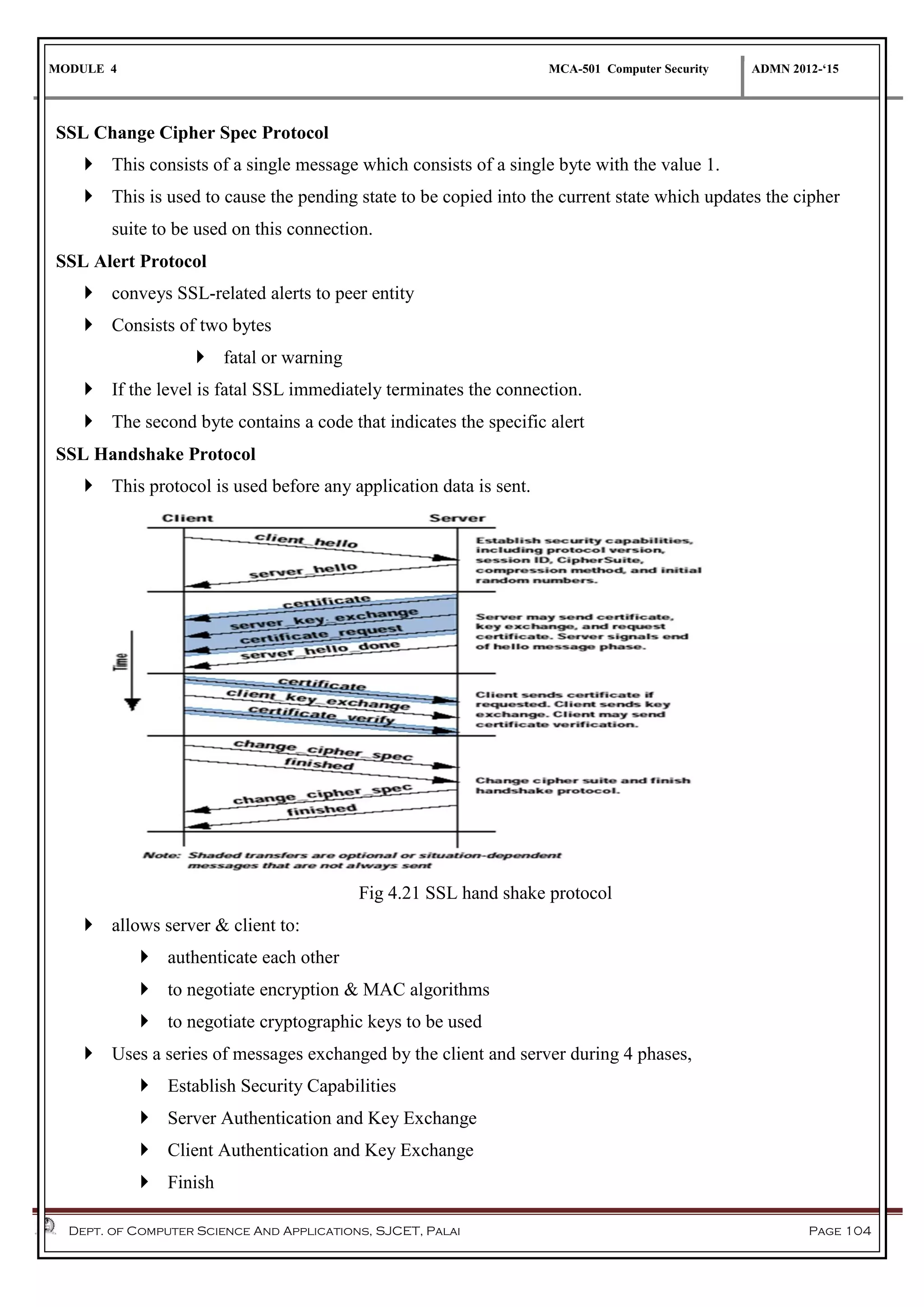
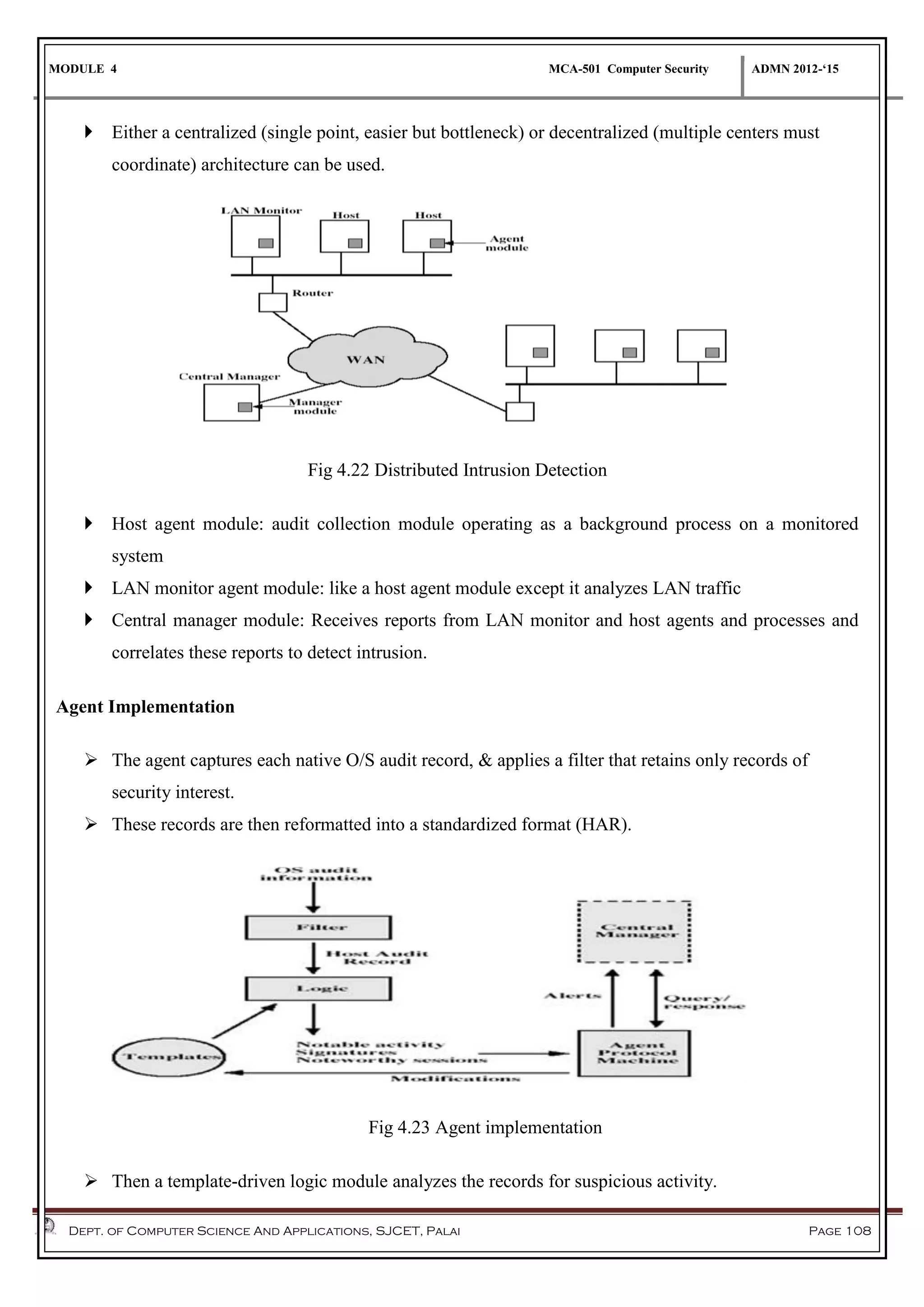
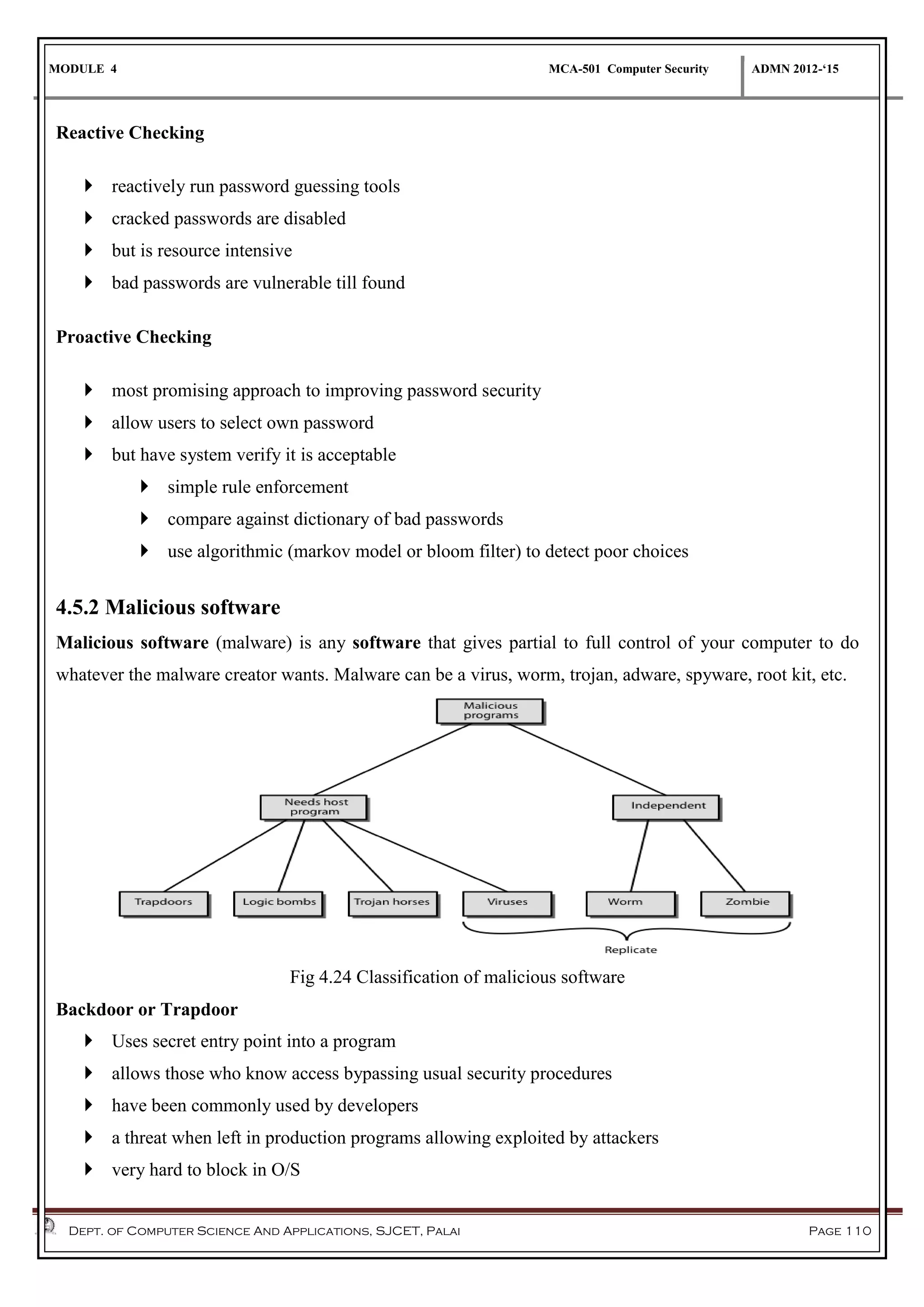
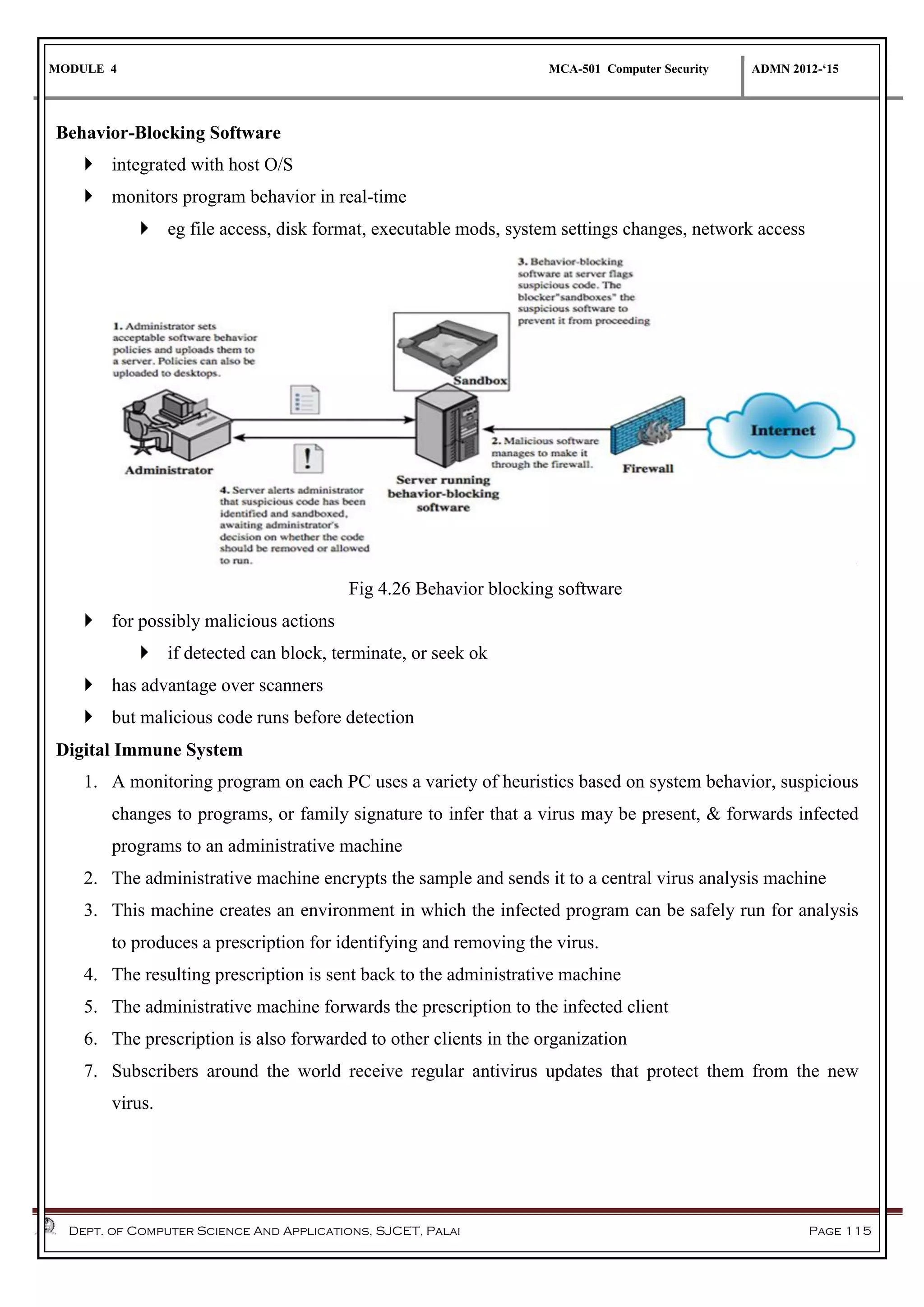
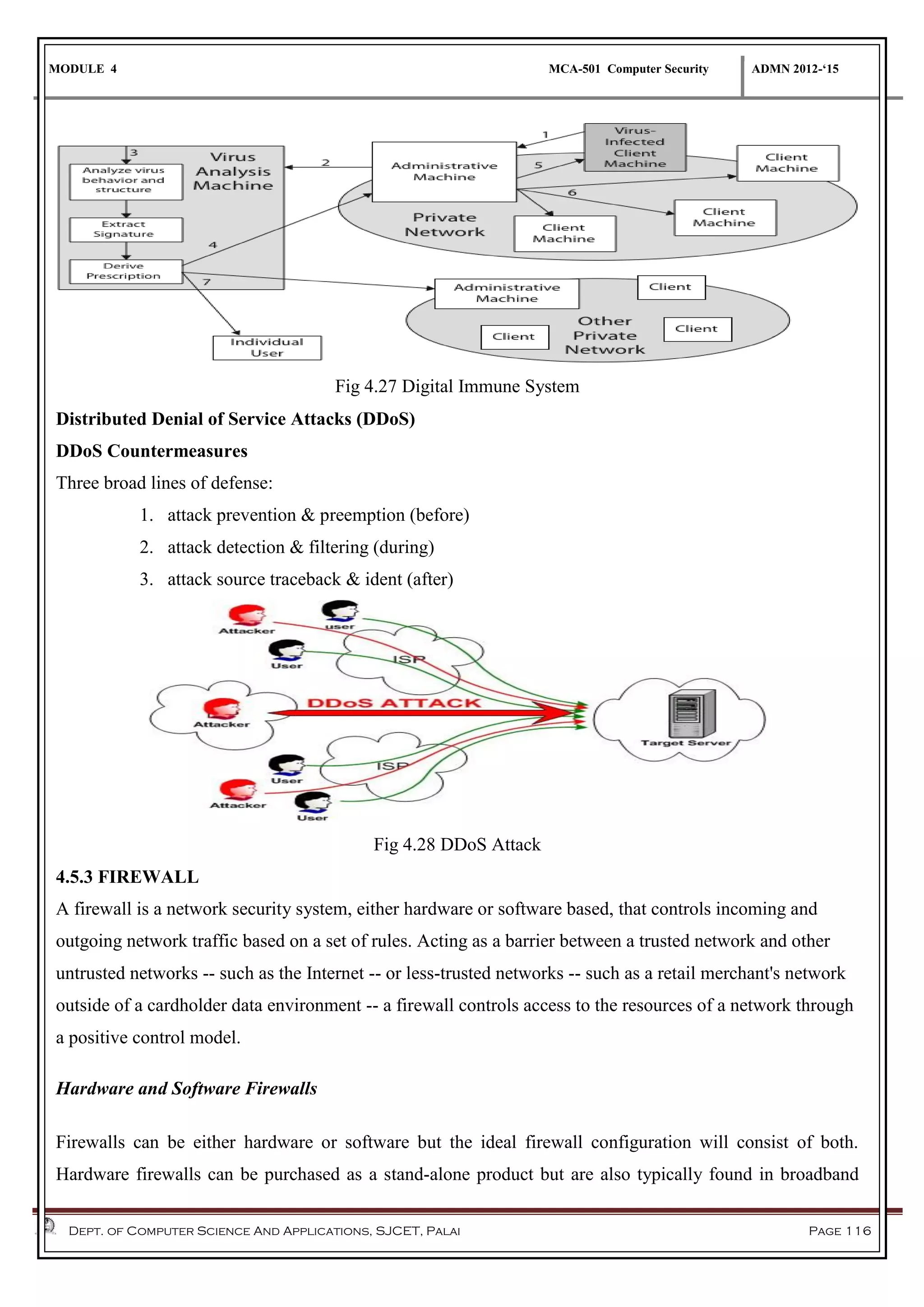
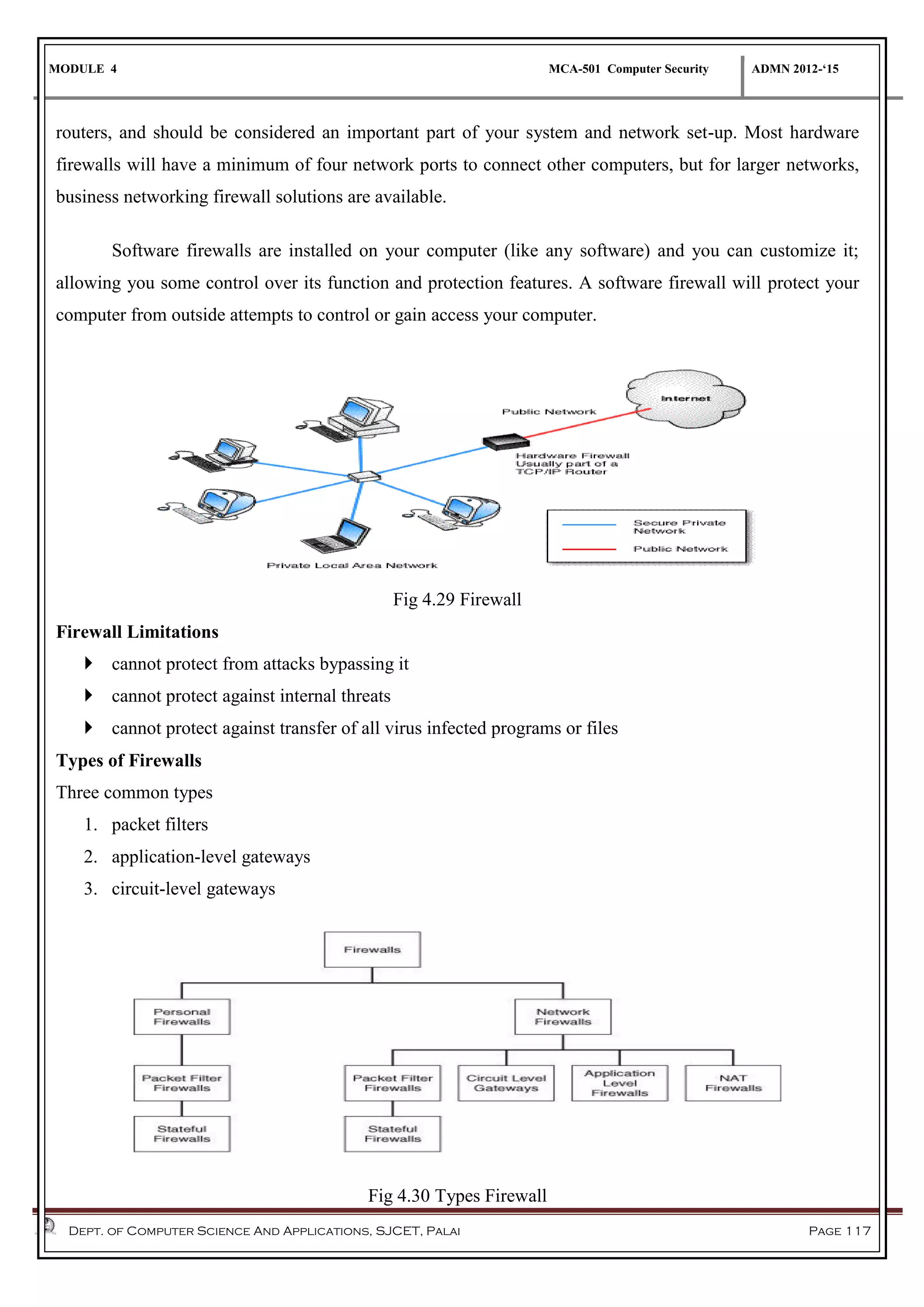
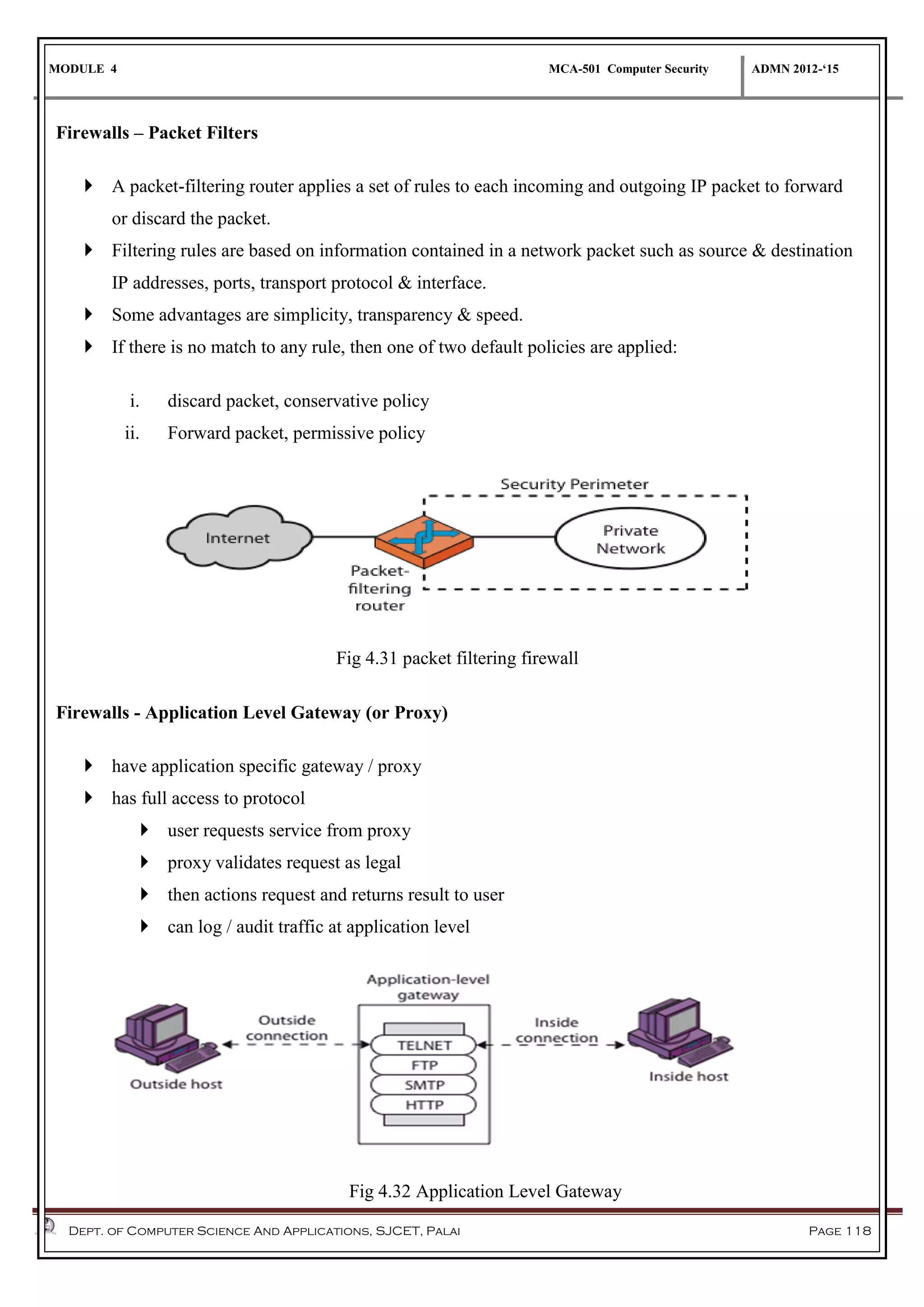
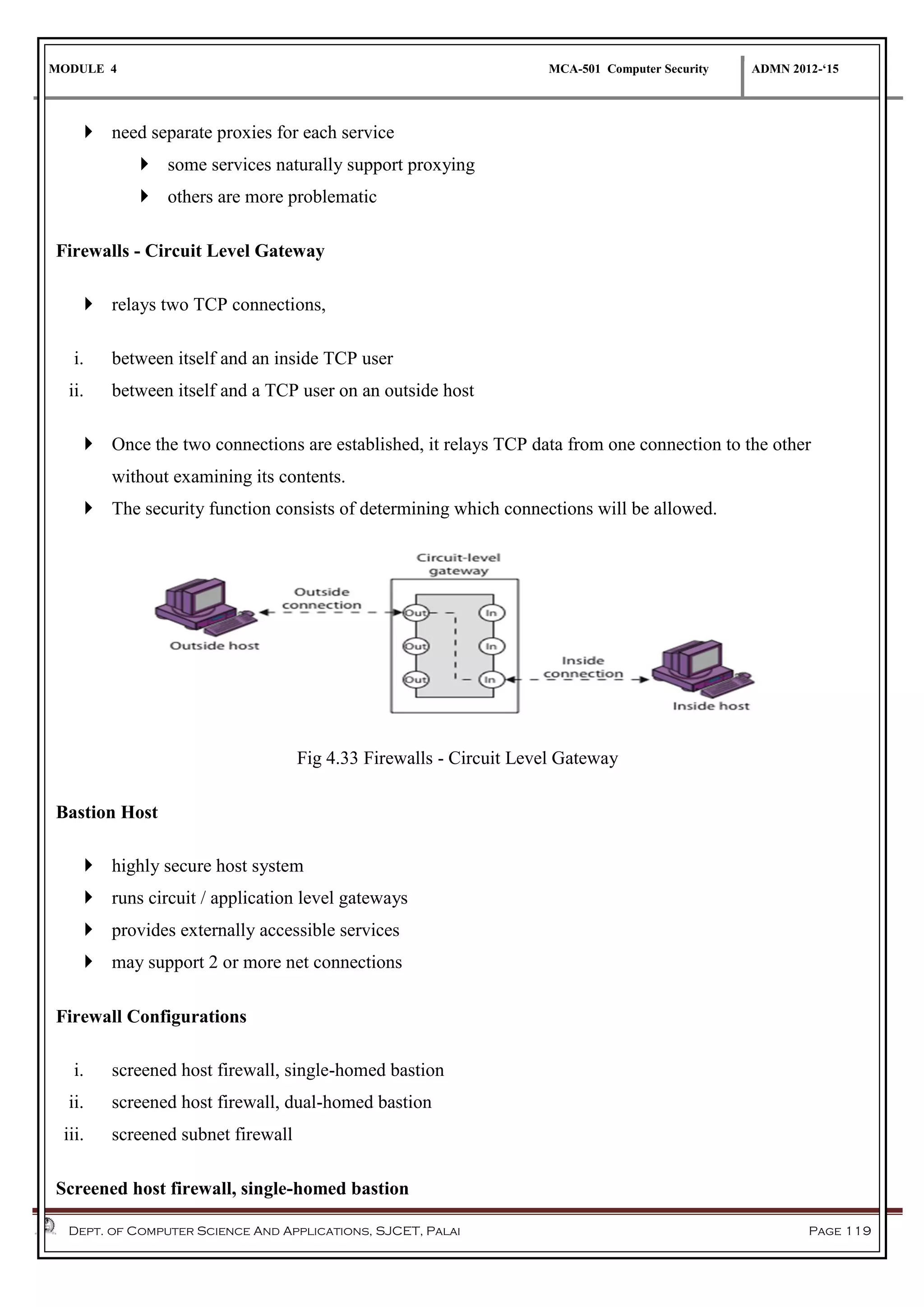
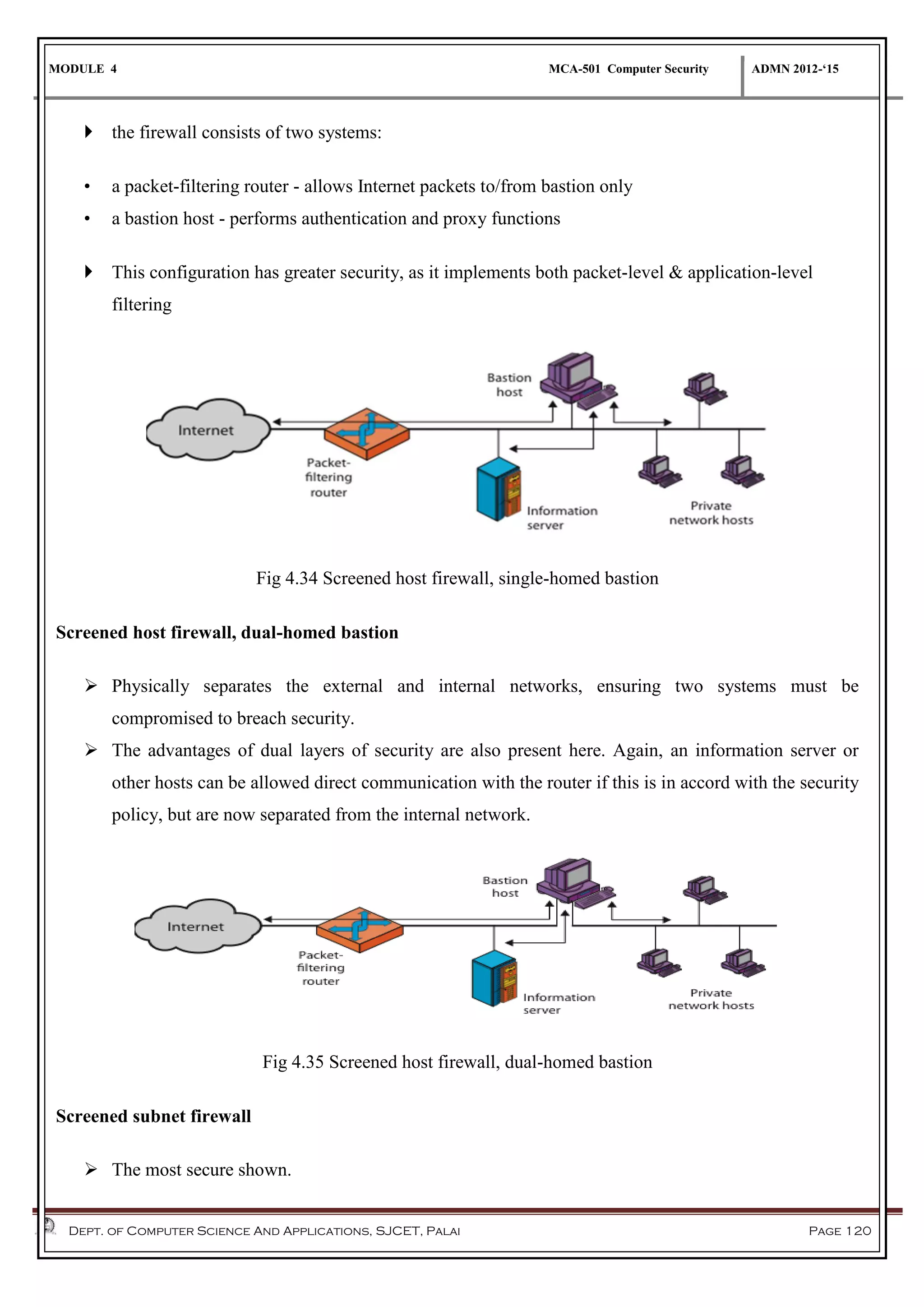
The document discusses network security methods, focusing on Kerberos authentication as a centralized system for secure user access in distributed networks, highlighting its versions, operational procedures, and structural components. It also covers the X.509 authentication service for user identity verification through public key certificates and details alternative authentication procedures, including one, two, and three-way authentication. Furthermore, it examines email security enhancements, particularly through PGP and S/MIME, addressing confidentiality, authentication, integrity, and key management processes.