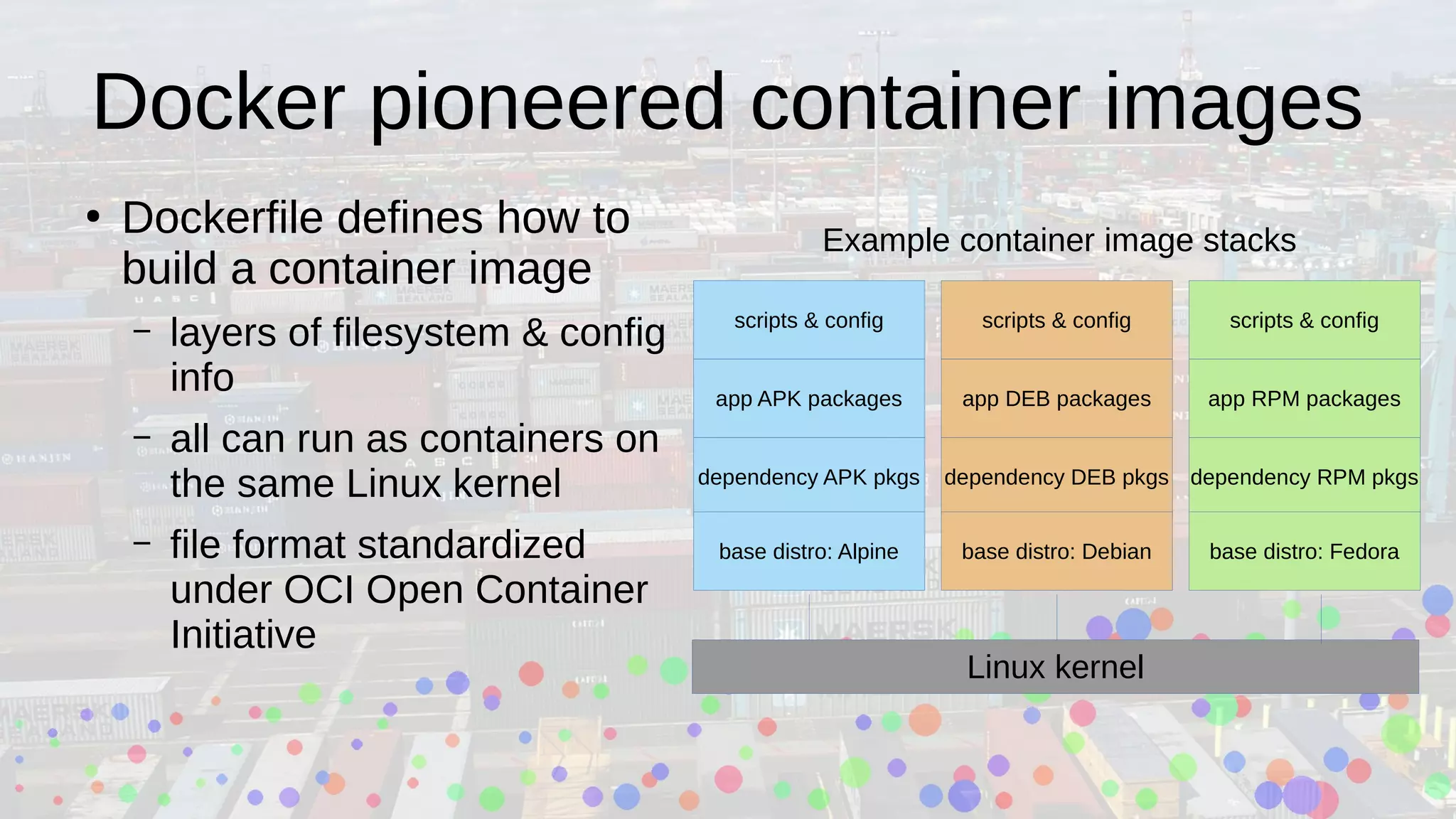
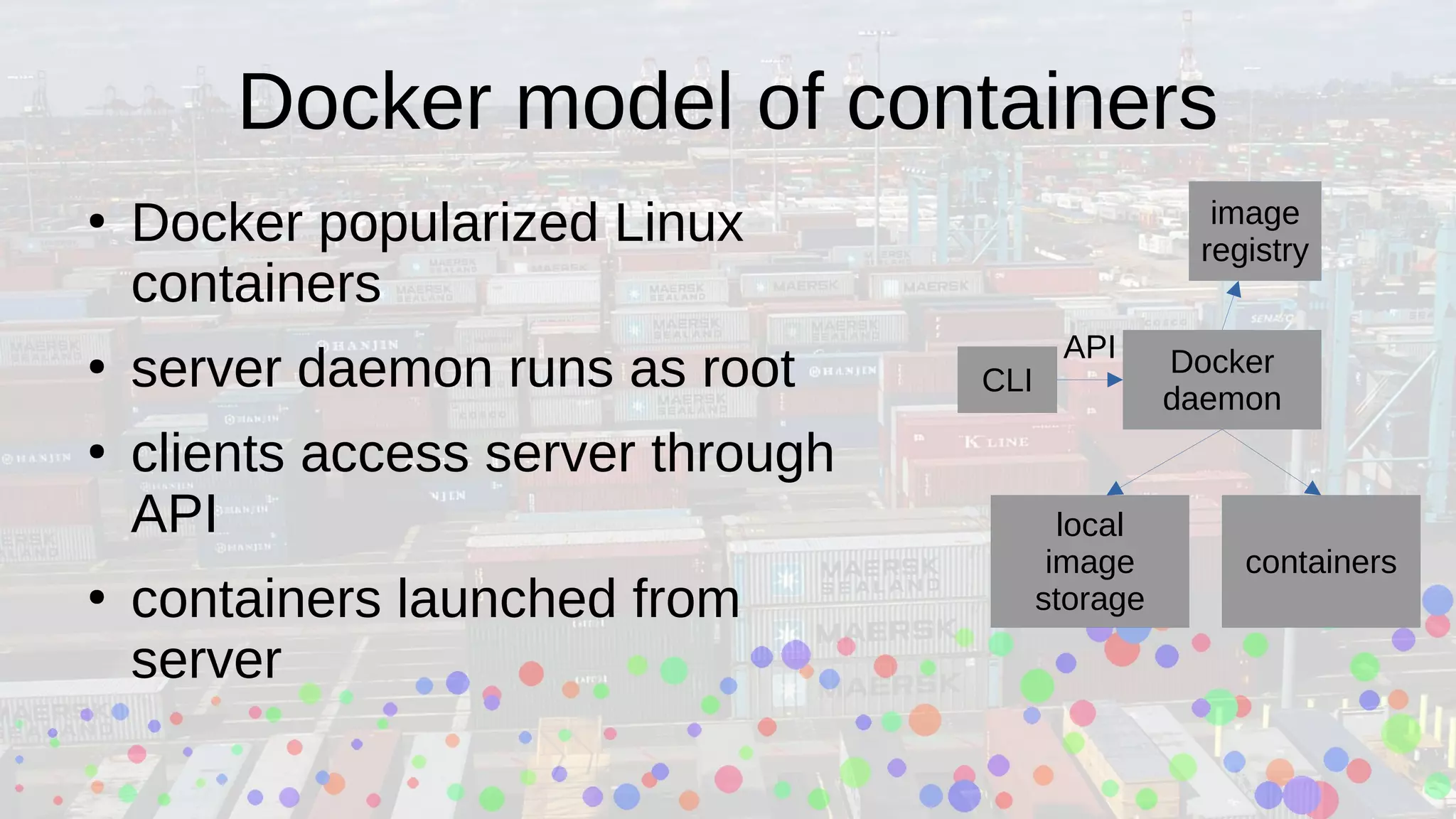
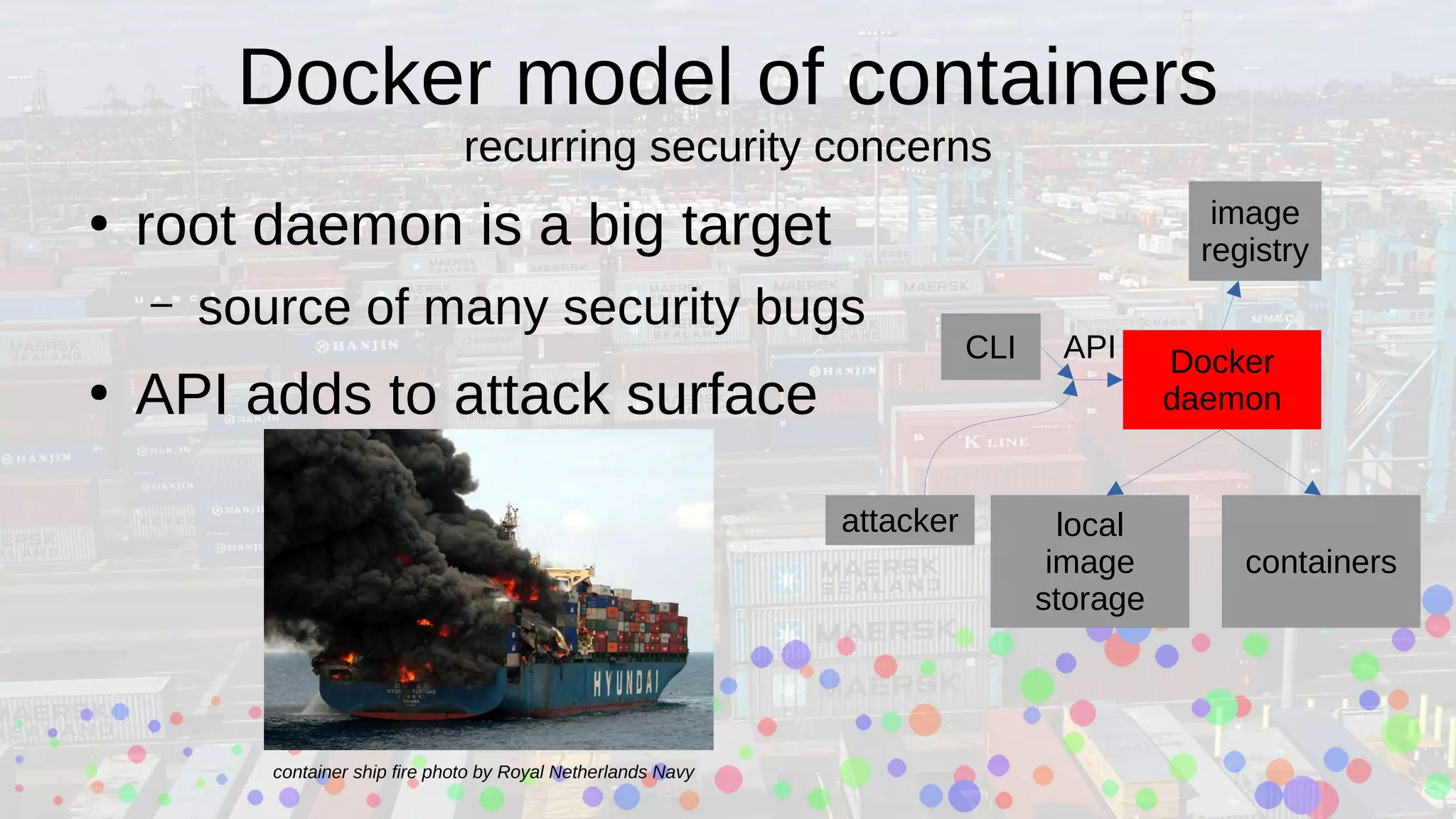
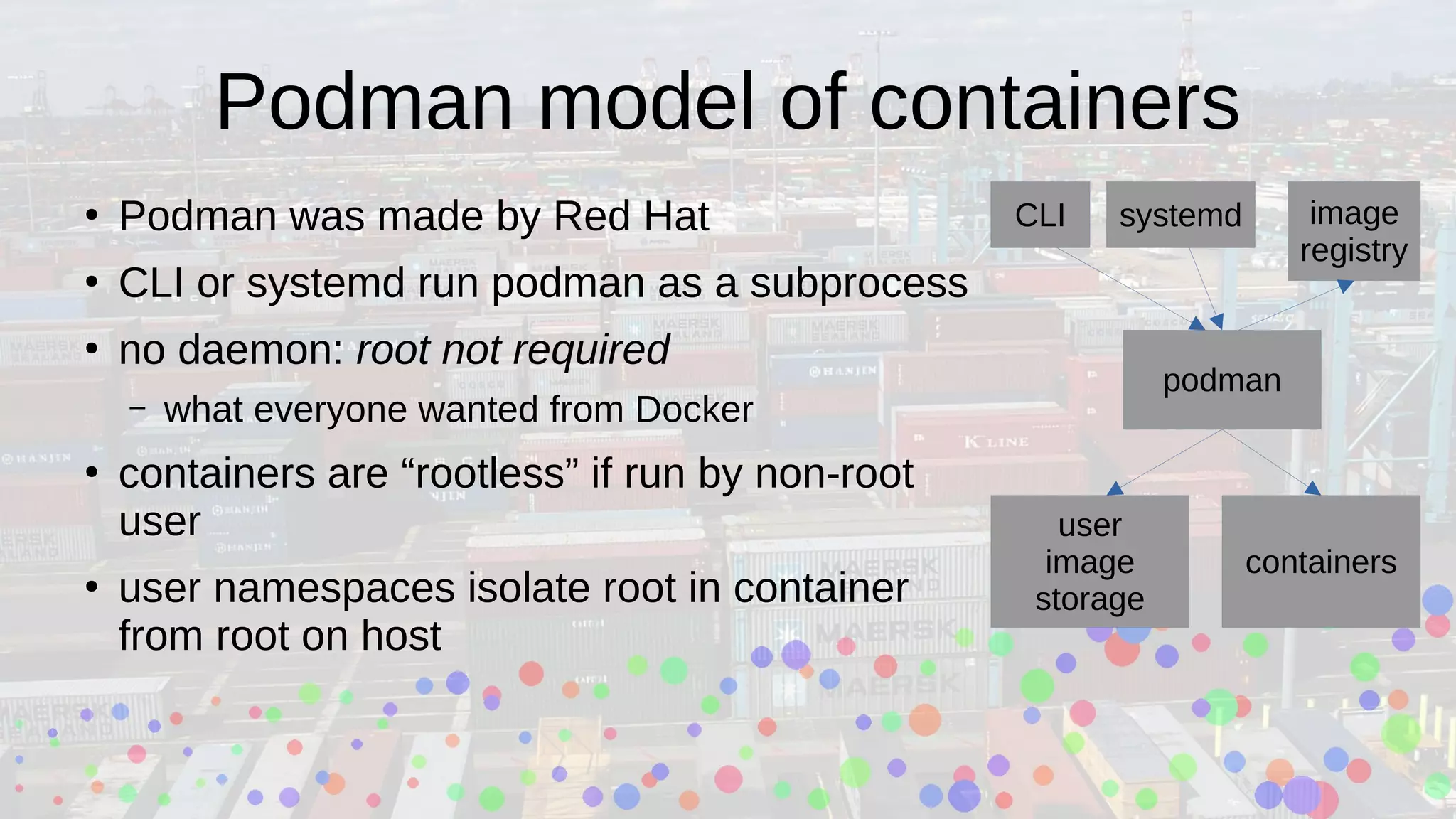
Ian Kluft presented a wrapper module around the open-source Buildah tool at the Silicon Valley Perl Monthly Meeting, facilitating container image creation using Perl scripts in a containerized environment. The presentation explained Linux containerization concepts, including cgroups and namespaces, and compared Docker with Podman, emphasizing Podman's rootless capability. Buildah offers a command-line interface for building OCI-compatible containers and supports multi-stage builds, making container development more efficient.

![Example: Hello World in C
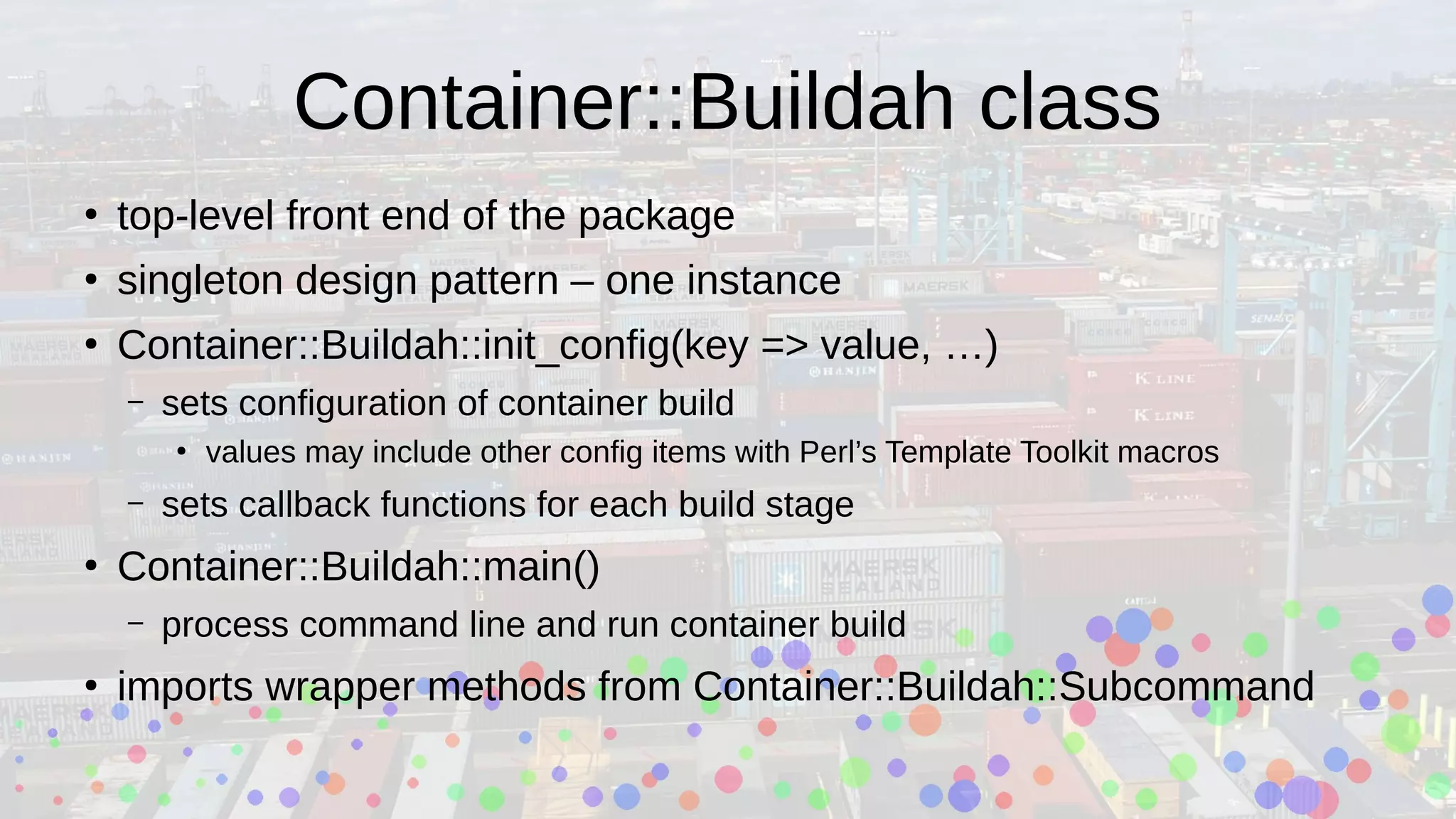
initialization and configuration
use Container::Buildah;
use YAML::XS;
# set paths as constants
# directory for build stage to make its
binaries
my $build_dir = "/opt/hello-build";
# directory for build stage to save product
files
my $bin_dir = "/opt/hello-bin";
# input directory
my $hello_src = "hello.c";
# YAML config file
my $hello_bin = "hello";
# container parameters
Container::Buildah::init_config(
basename => "hello",
base_image => 'docker://docker.io/alpine:[% alpine_version %]',
required_config => [qw(alpine_version)],
stages => {
build => {
from => "[% base_image %]",
func_exec => &stage_build,
produces => [$bin_dir],
},
runtime => {
from => "[% base_image %]",
consumes => [qw(build)],
func_exec => &stage_runtime,
commit => ["[% basename %]:latest"],
},
},
);](https://image.slidesharecdn.com/svperl-container-buildah-2020-10-201002012539/75/New-Perl-module-Container-Buildah-SVPerl-presentation-20-2048.jpg)
![Example: Hello World in C
callbacks for build and runtime stage containers
# container-namespace code for build stage
sub stage_build
{
my $stage = shift;
$stage->debug({level => 1}, "start");
my $input_dir = $cb->get_config('opts', 'inputs');
$stage->run(
# install dependencies
[qw(/sbin/apk add --no-cache binutils gcc musl-dev)],
# create build and product directories
["mkdir", $build_dir, $bin_dir],
);
$stage->config({workingdir => $build_dir});
$stage->copy({dest => $build_dir}, $input_dir."/"
.$hello_src);
$stage->run(
["gcc", "--std=c17", $hello_src, "-o",
"$bin_dir/$hello_bin"],
);
}
# container-namespace code for runtime stage
sub stage_runtime
{
my $stage = shift;
$stage->debug({level => 1}, "start");
my $cb = Container::Buildah->instance();
# container environment
$stage->config({
entrypoint => $bin_dir.'/'.$hello_bin,
});
}
# main
Container::Buildah::main();](https://image.slidesharecdn.com/svperl-container-buildah-2020-10-201002012539/75/New-Perl-module-Container-Buildah-SVPerl-presentation-21-2048.jpg)

