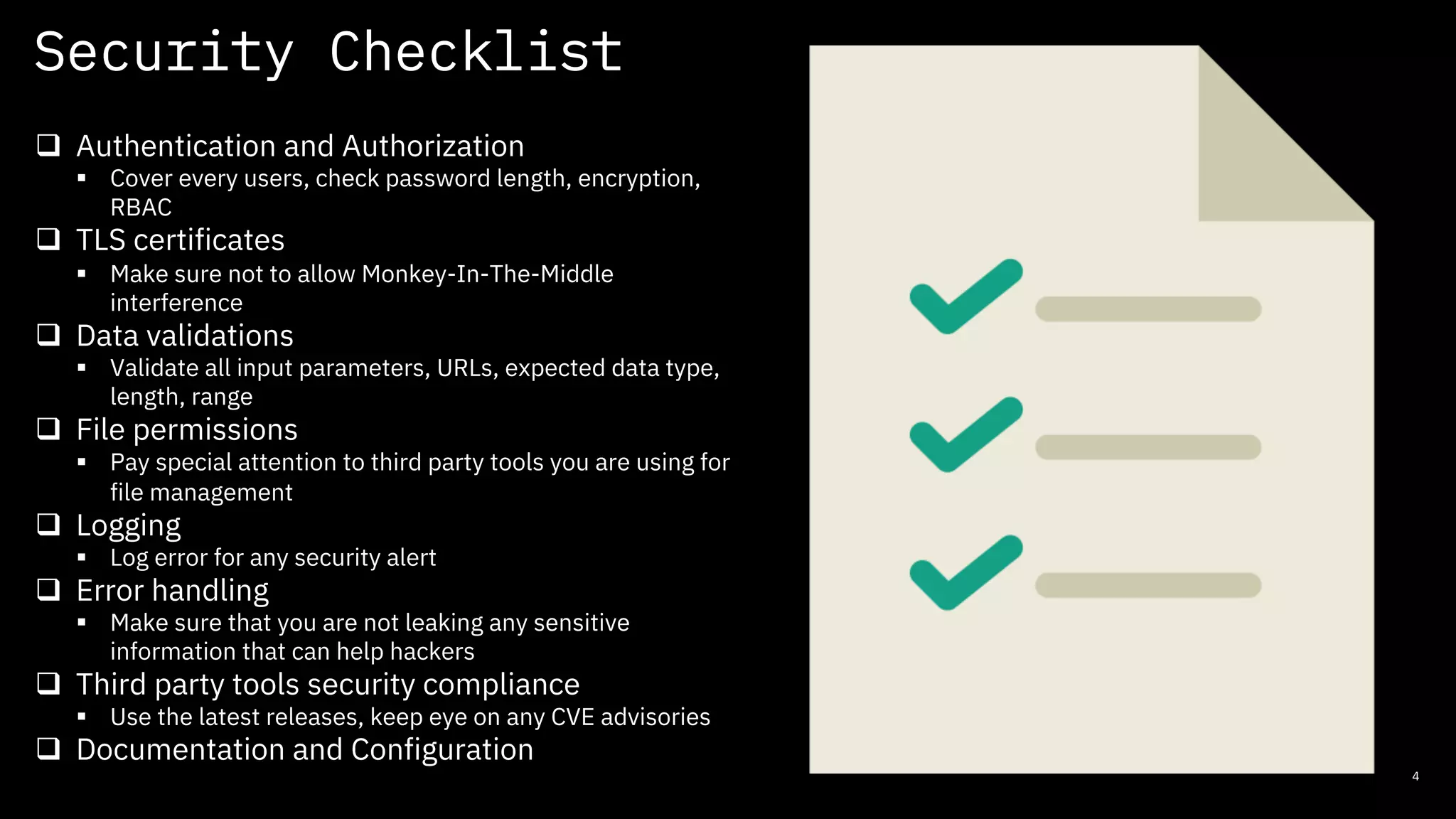
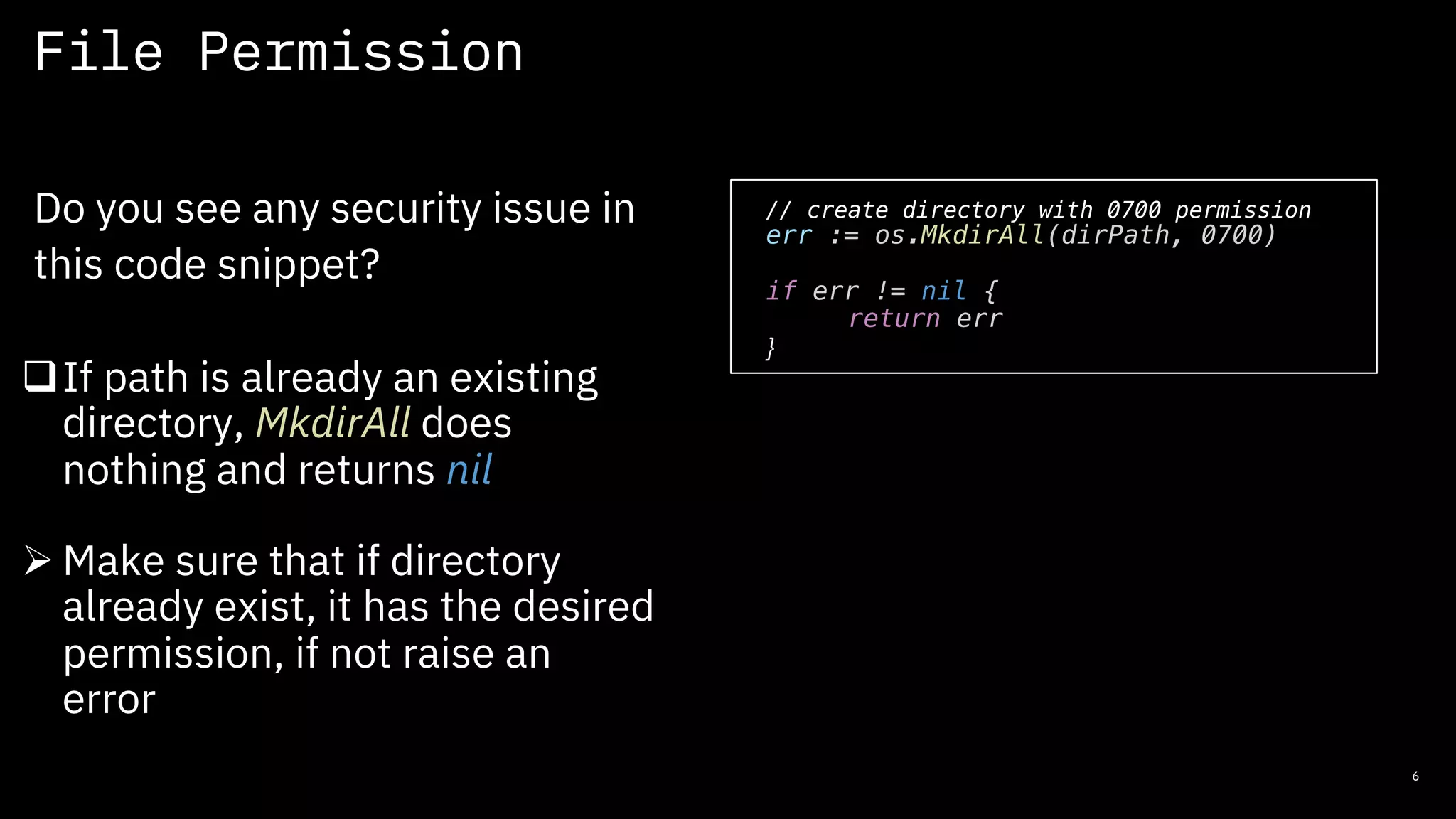
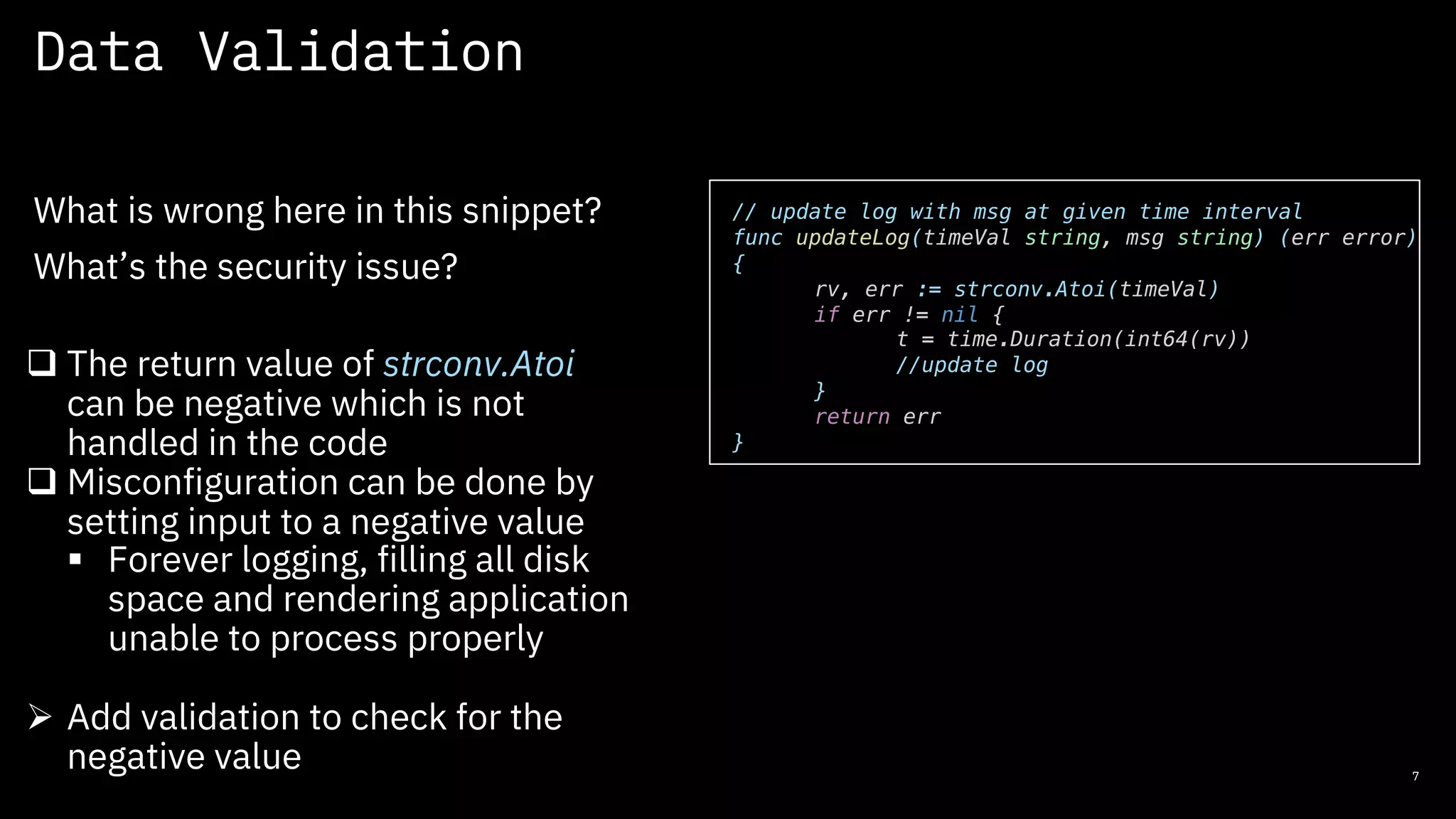
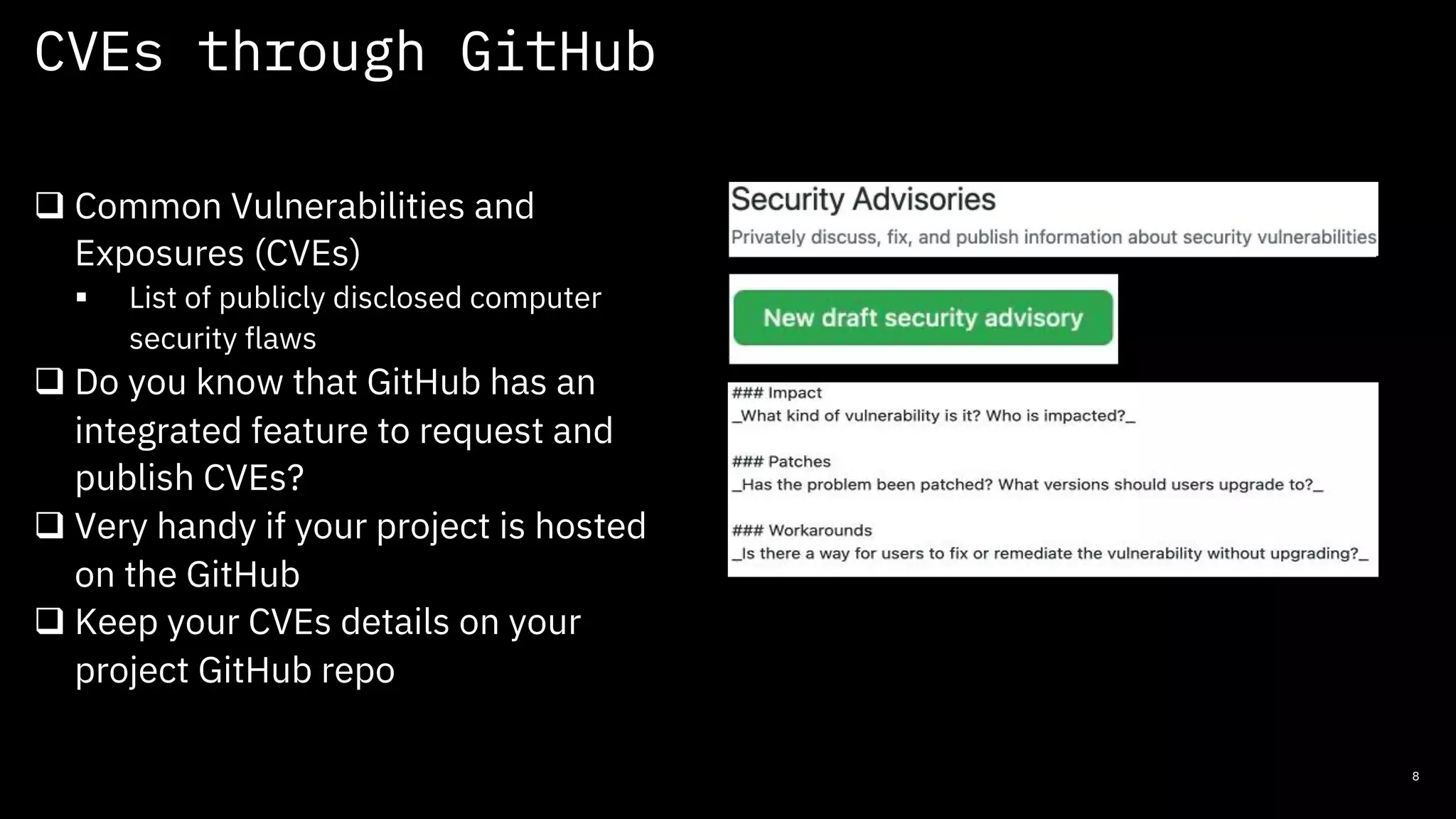
The document discusses secure coding practices for open source software, emphasizing the importance of project maturity, community involvement, and governance for security. It outlines strategies for identifying high-risk areas, performing secure code reviews, and adopting both automated and manual review tools to enhance security. Additionally, it highlights the role of Common Vulnerabilities and Exposures (CVEs) and resources for learning about open source security.