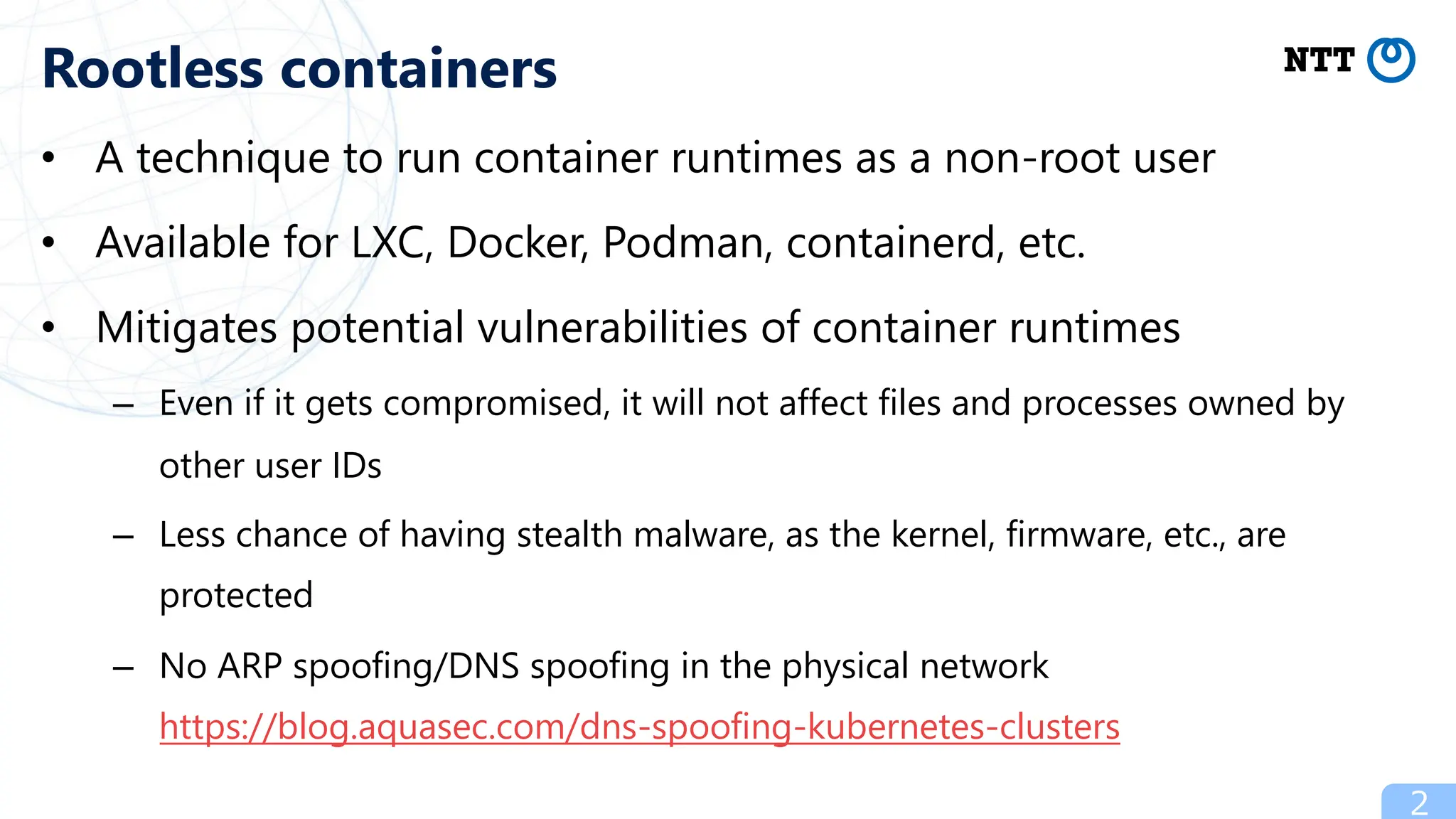
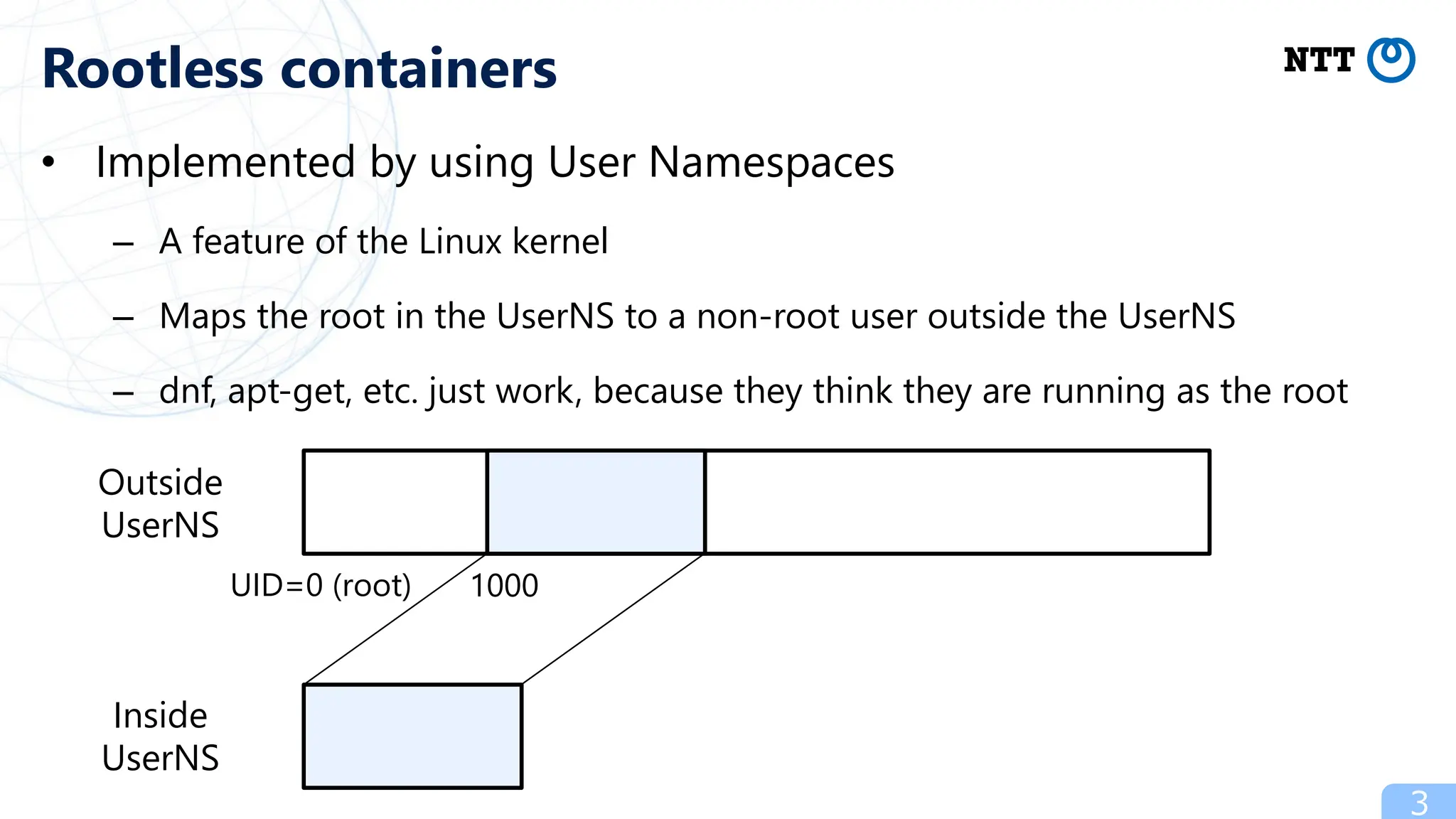
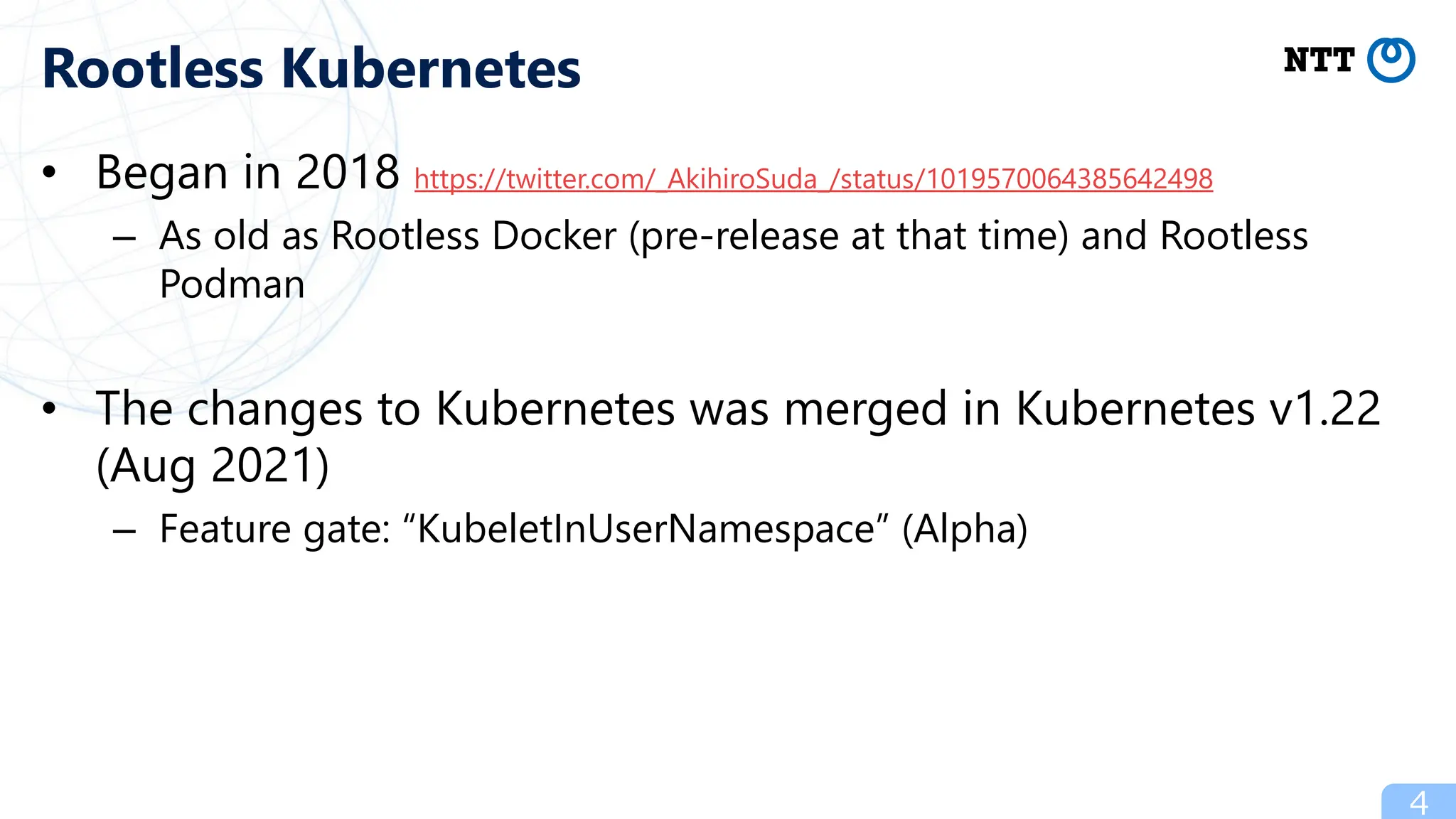
- Kubernetes can run in rootless containers using techniques like Podman, Docker, and containerd which map the root user inside containers to a non-root user on the host for improved security.
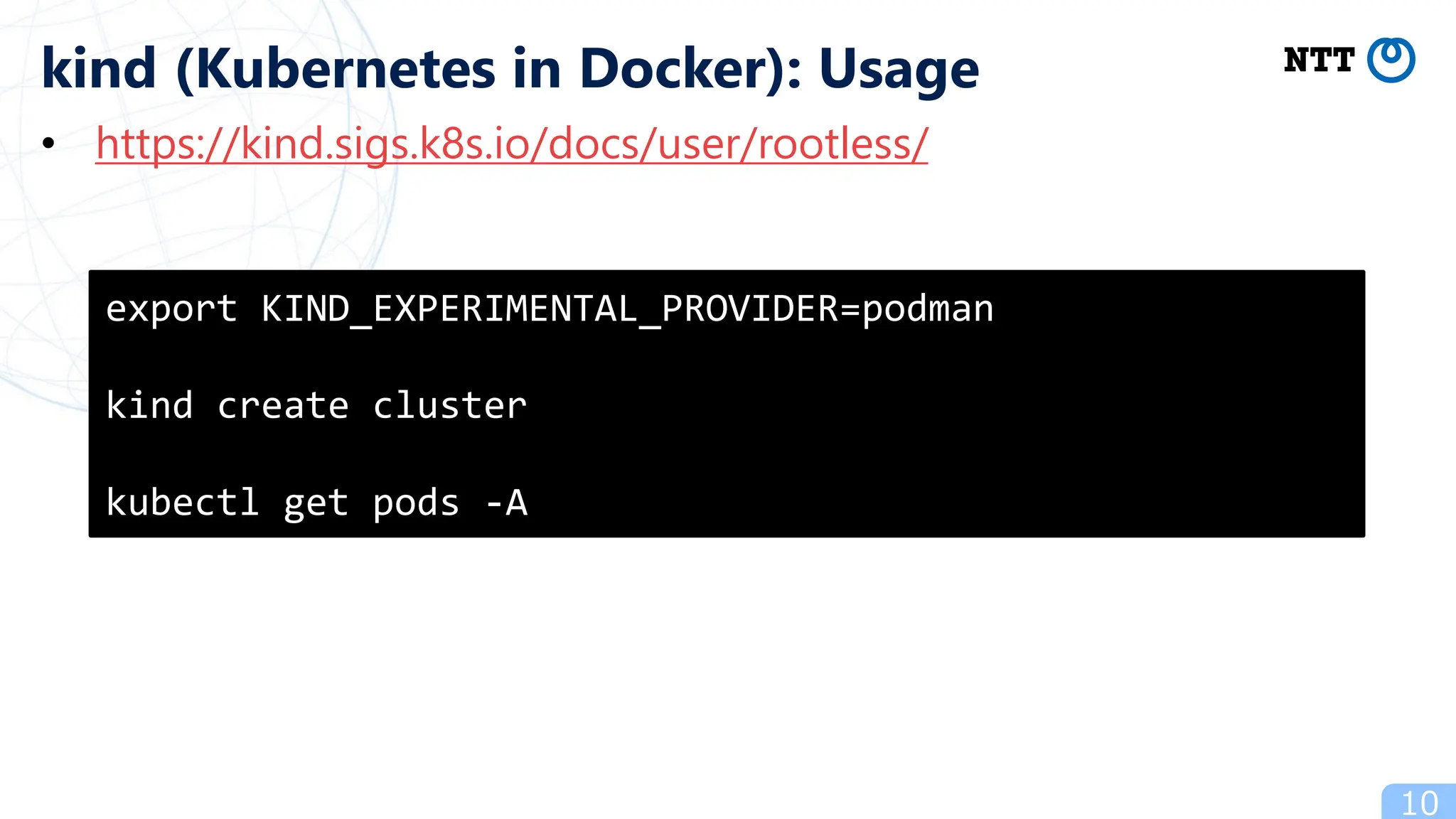
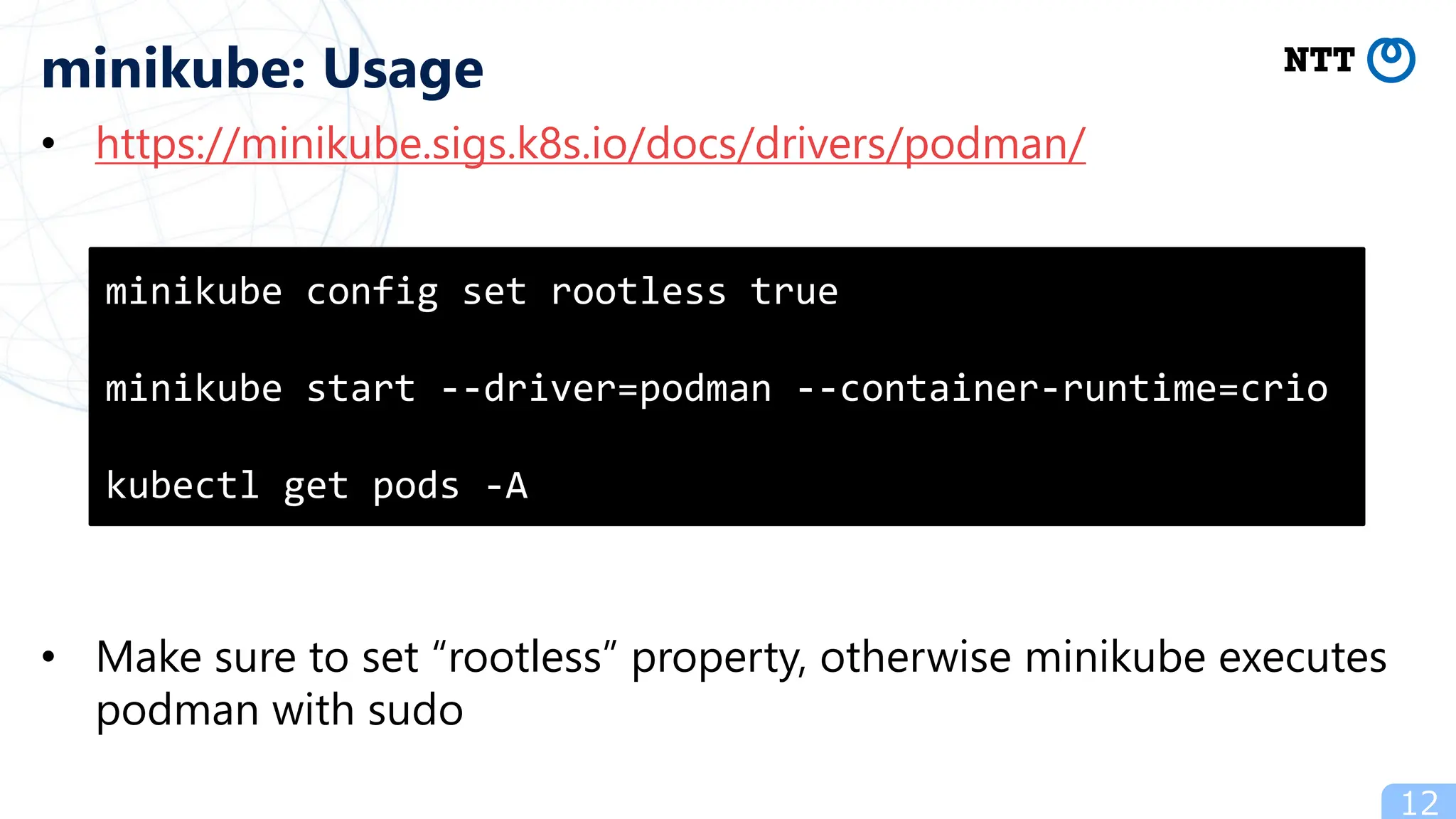
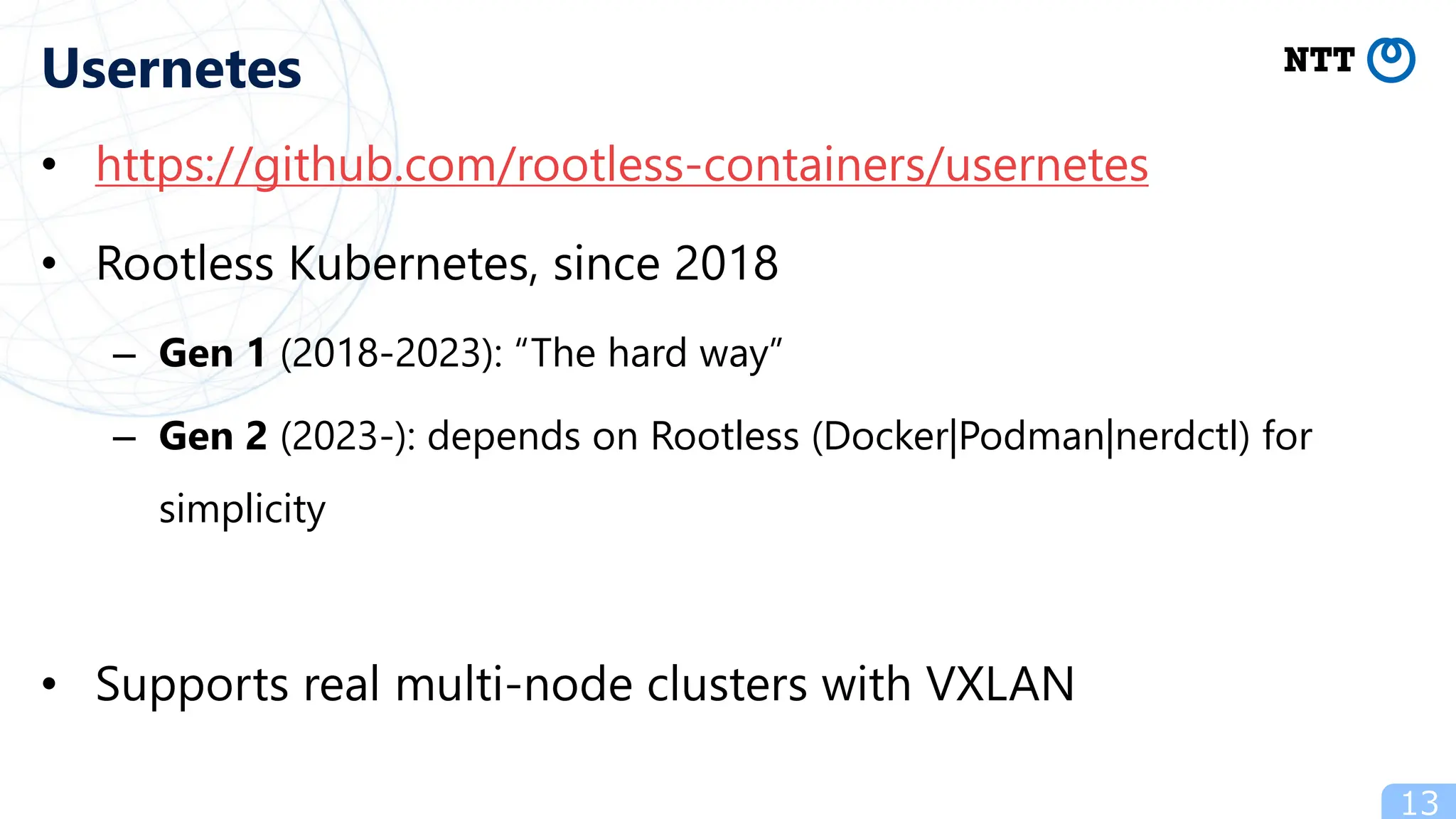
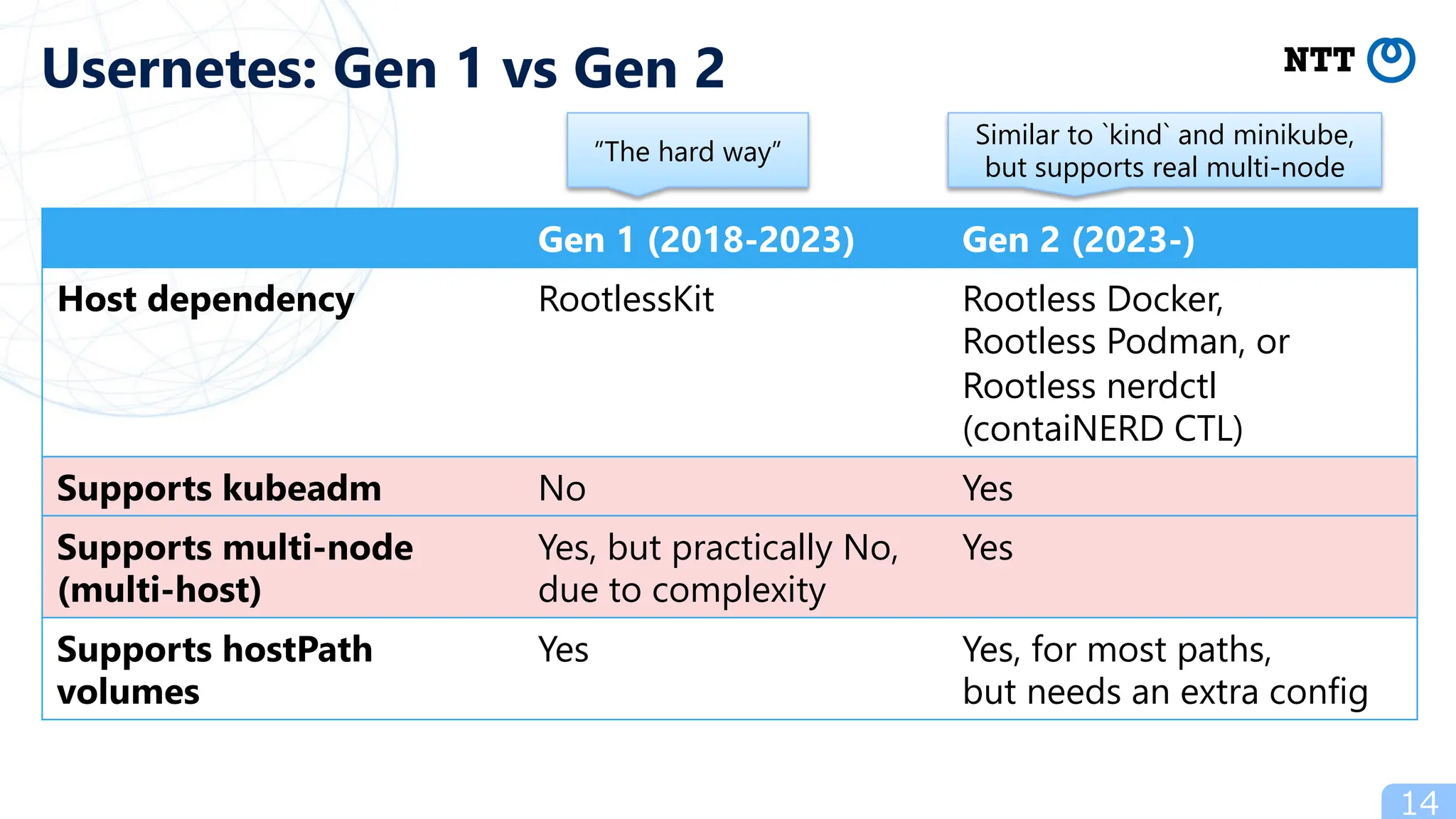
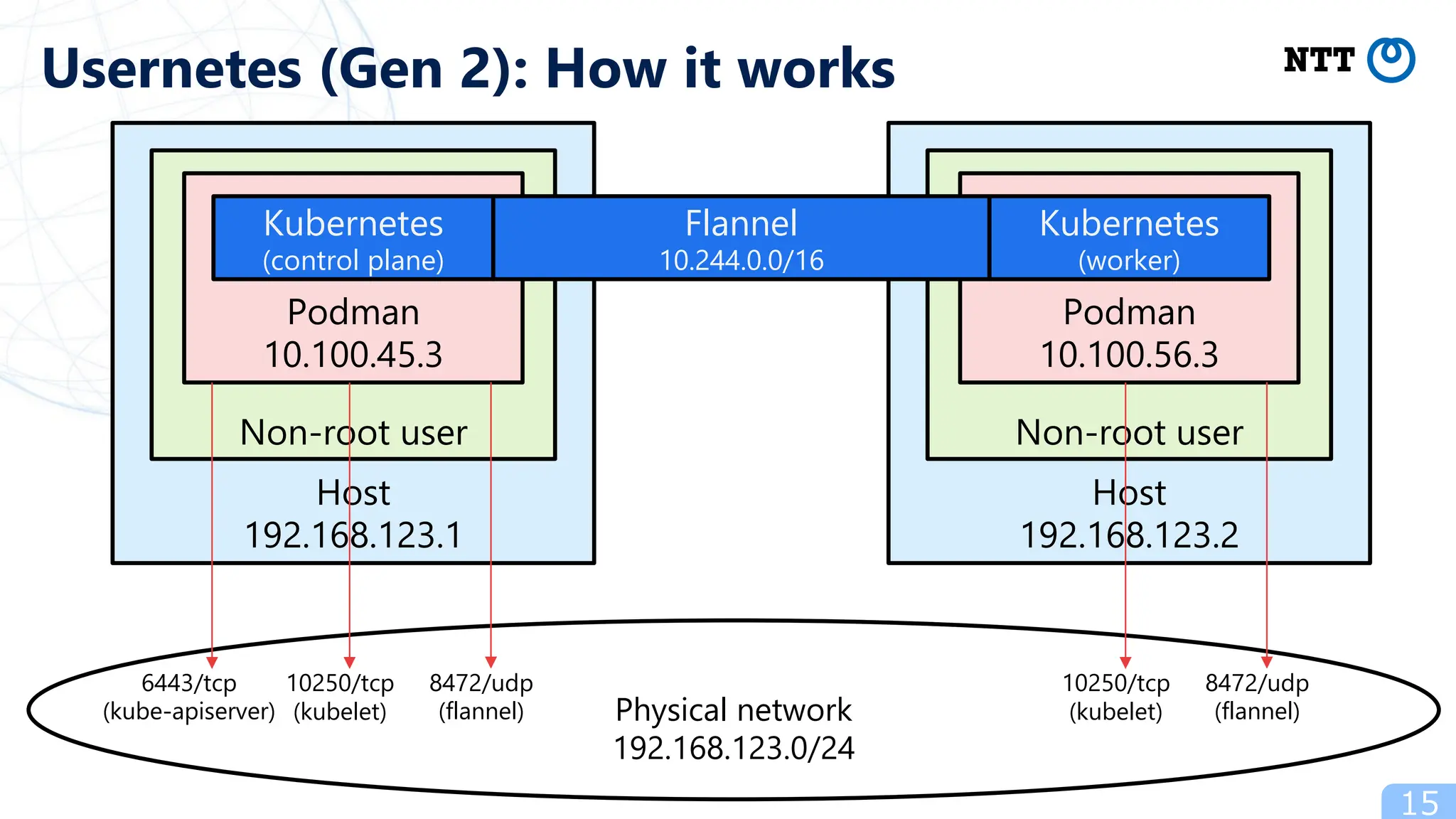
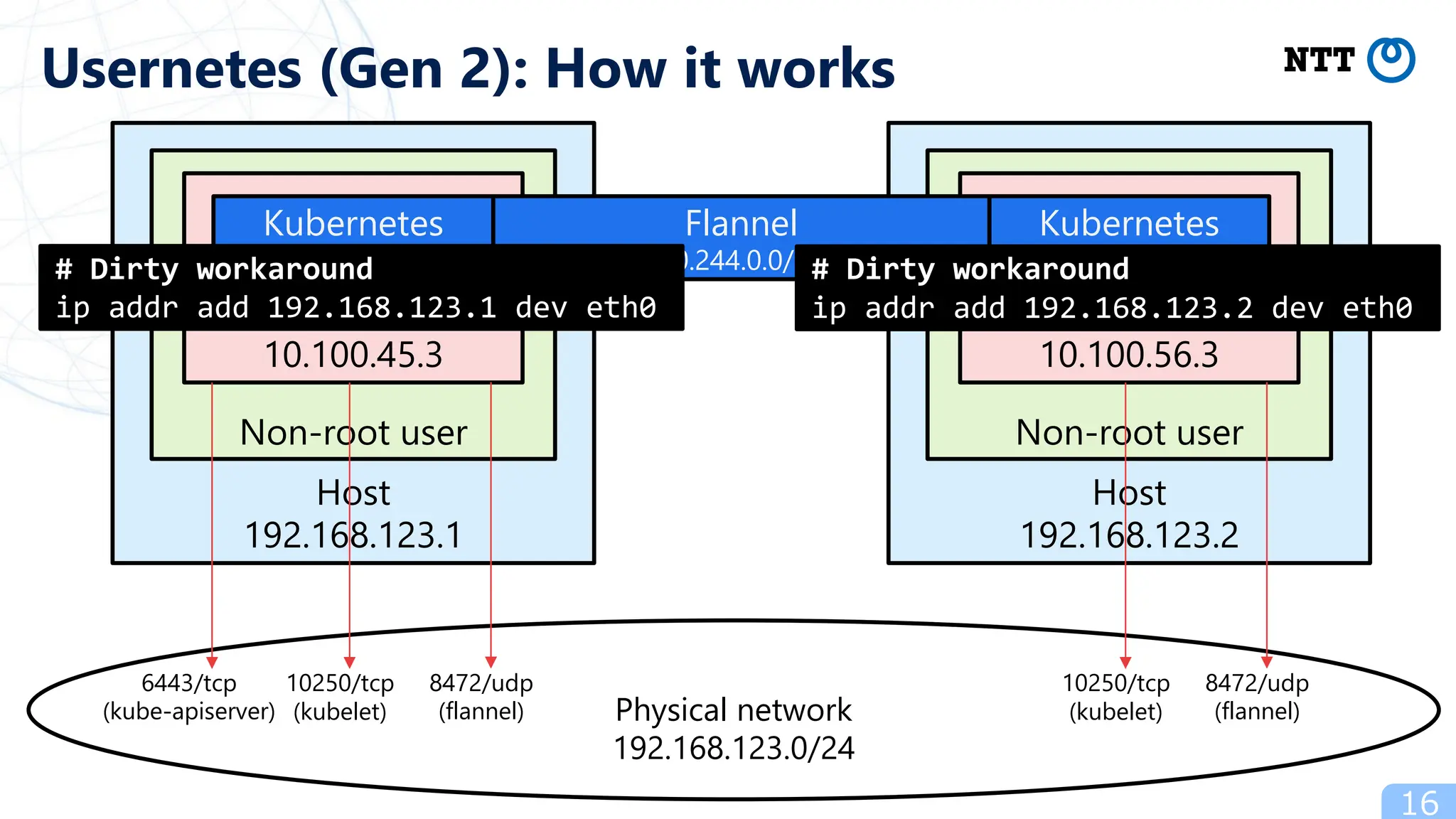
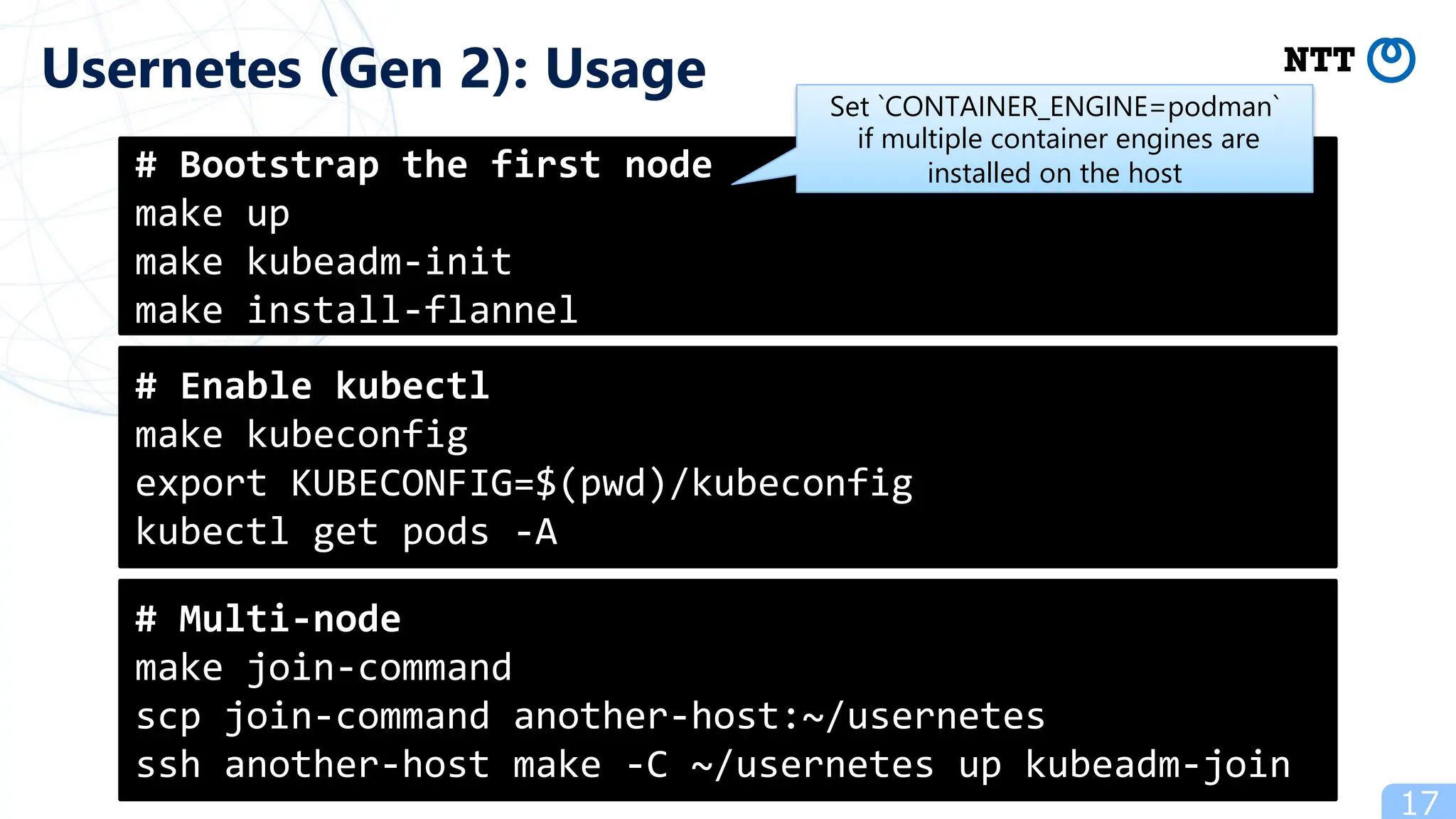
- Popular ways to run rootless Kubernetes include kind, minikube wrapped in Podman containers, and Usernetes which supports real multi-node clusters across multiple hosts using networking like Flannel.
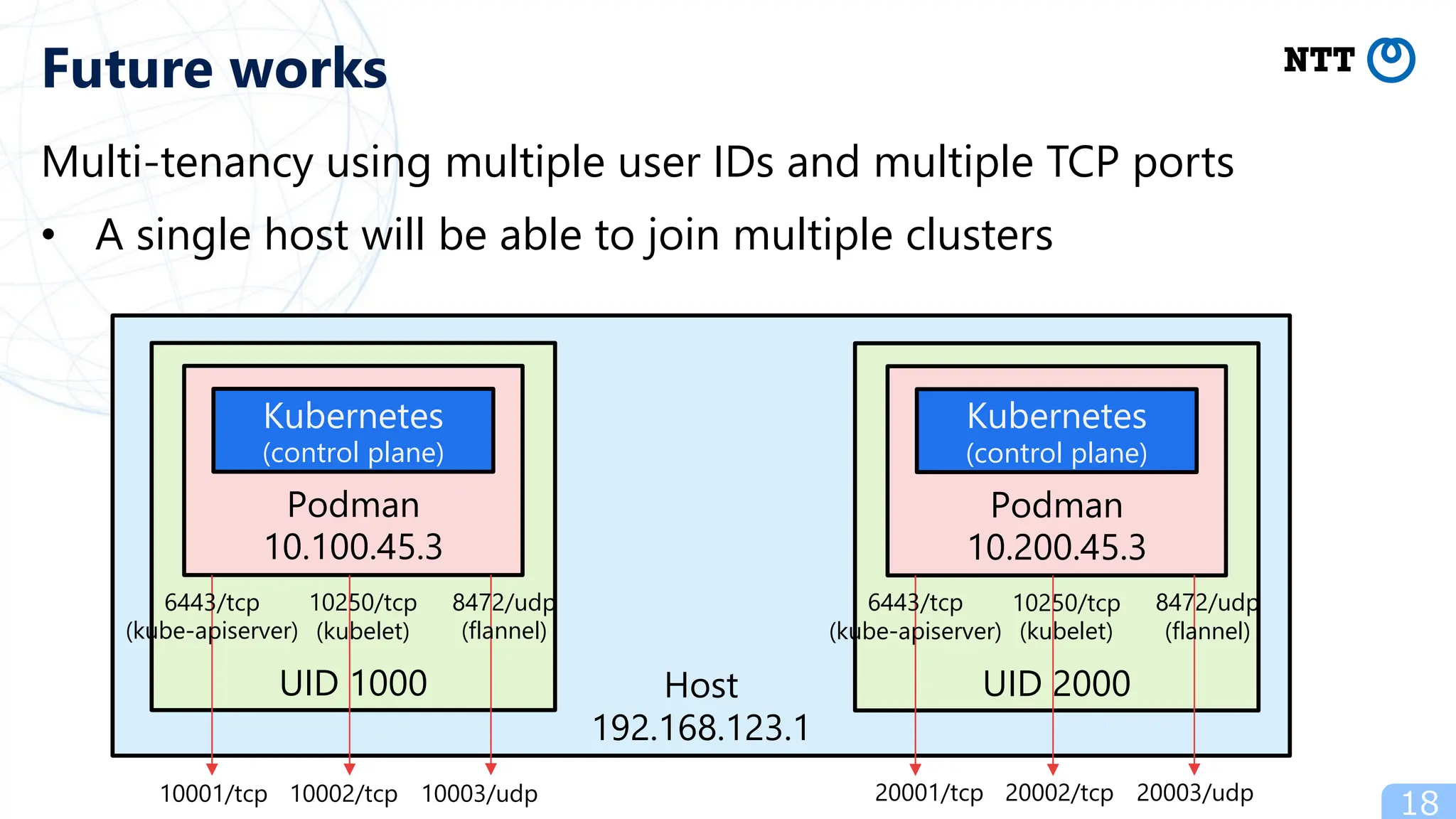
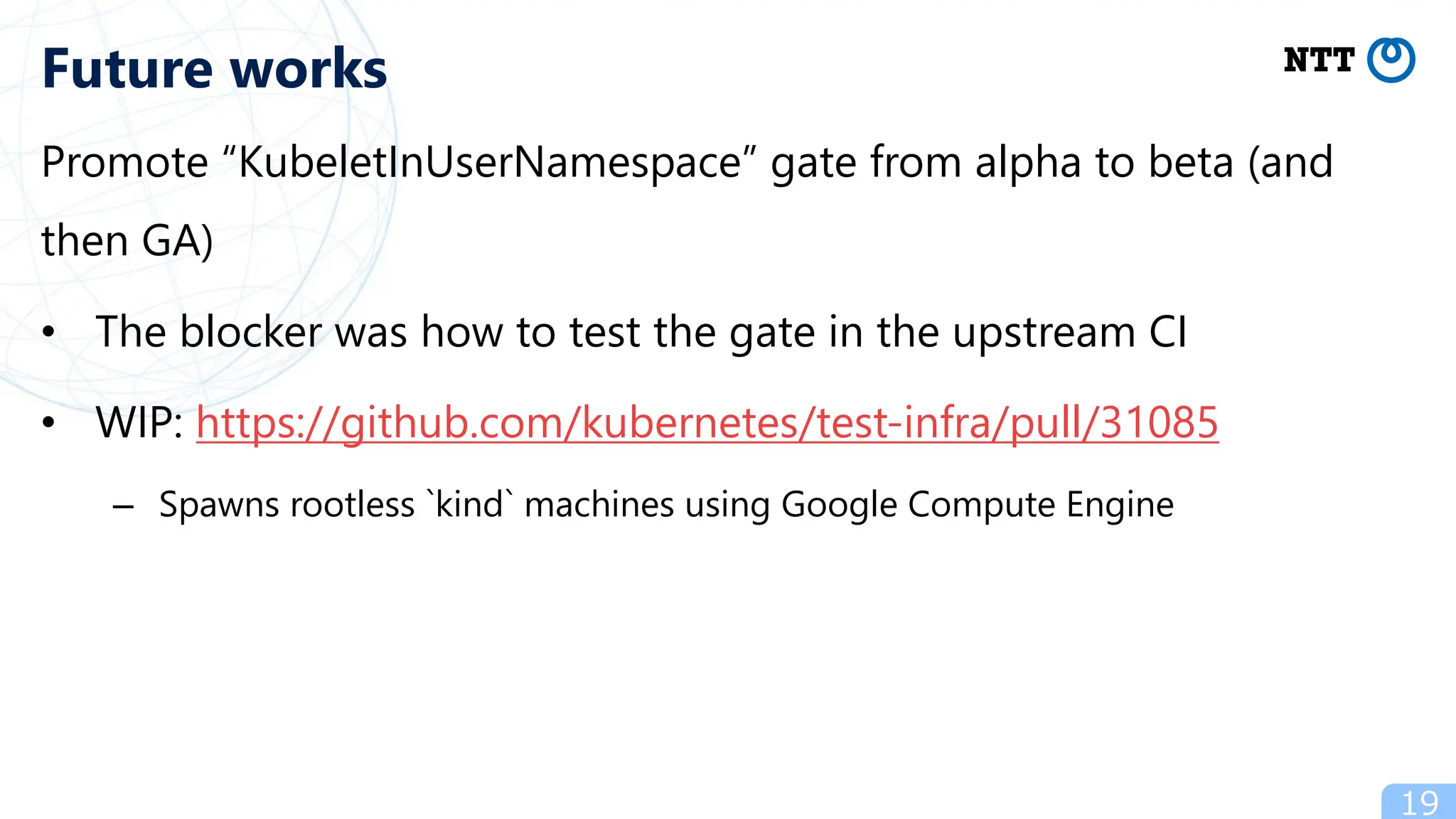
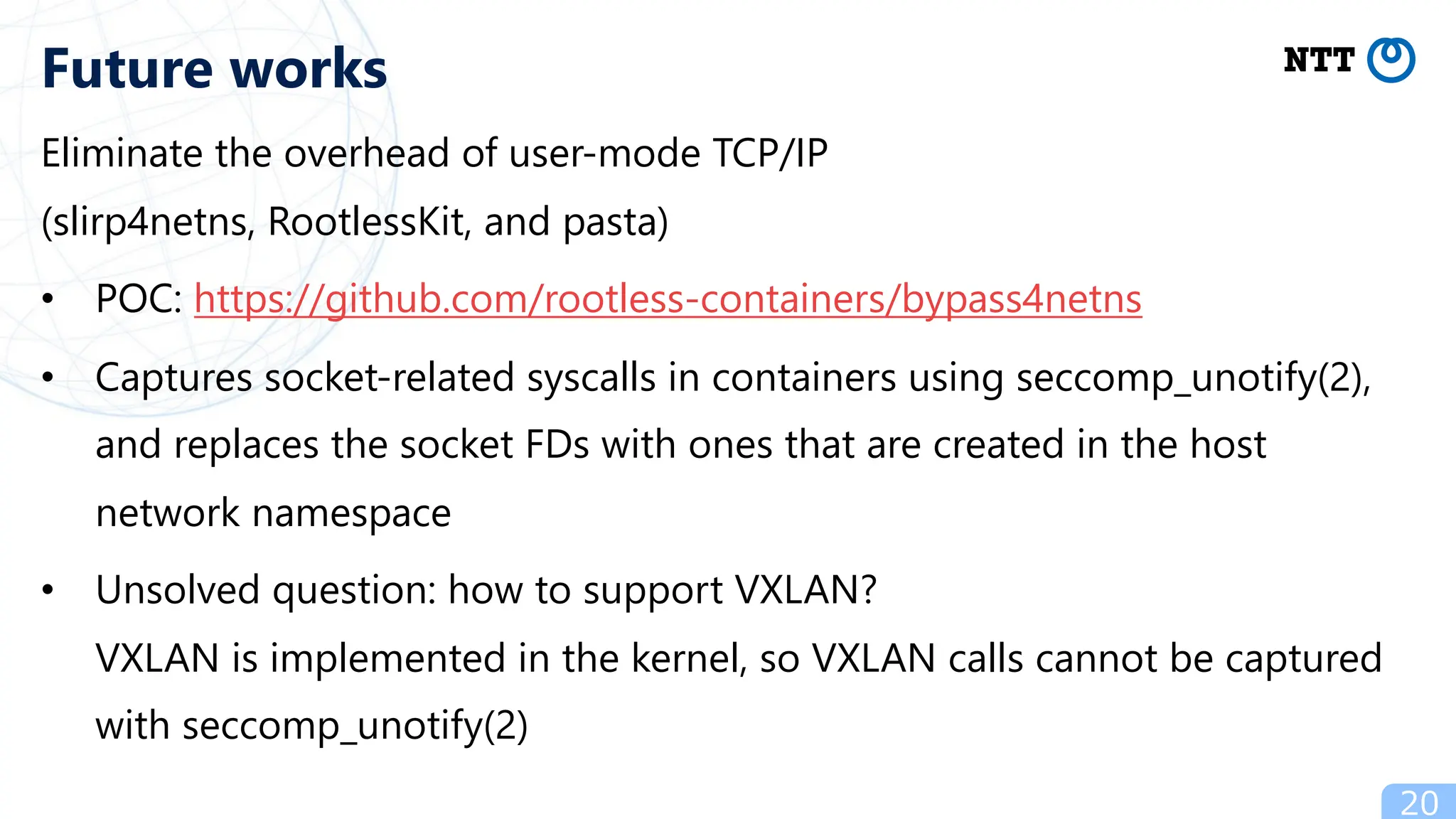
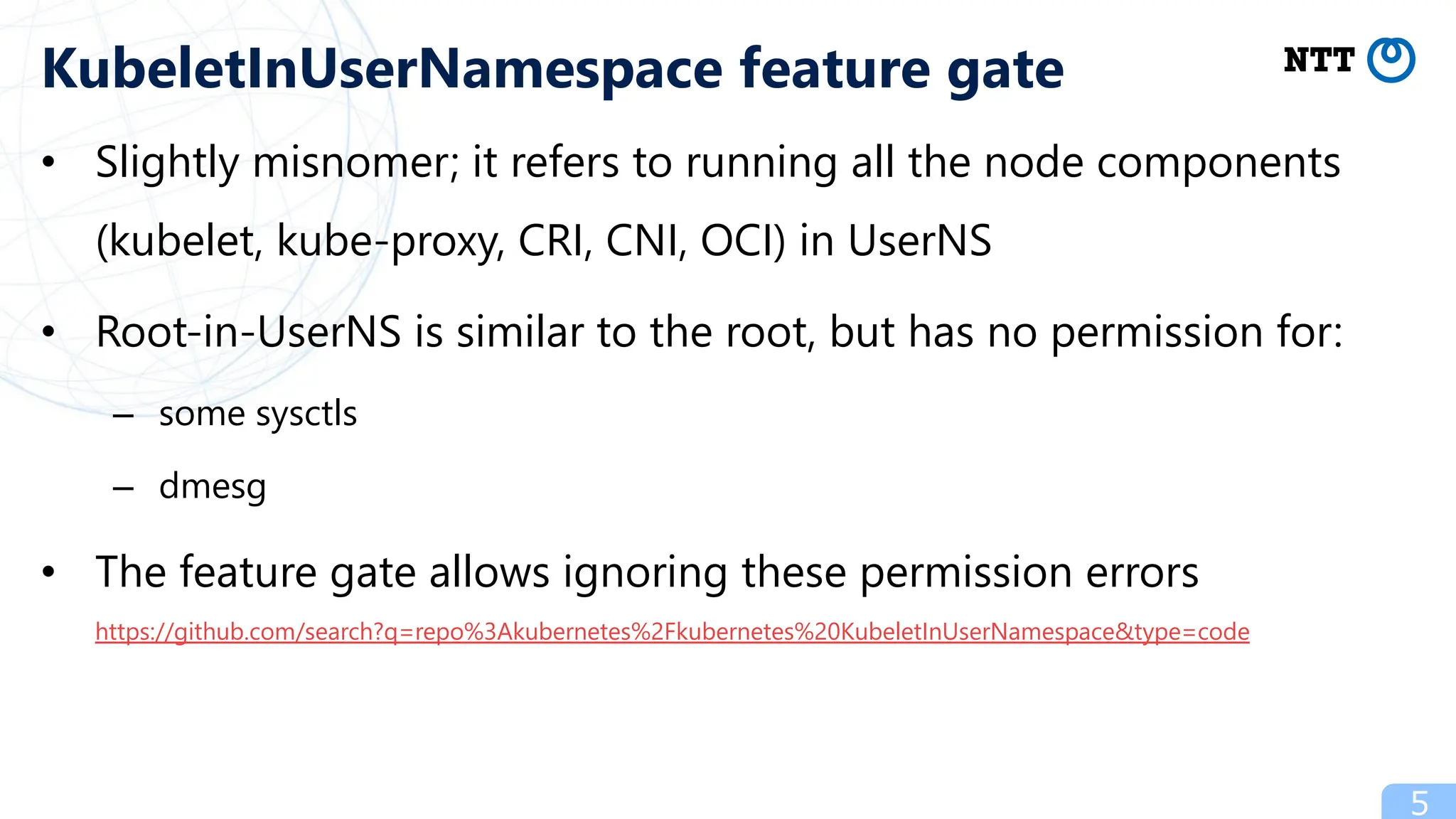
- Future work includes promoting the "KubeletInUserNamespace" feature flag and eliminating overhead of user-mode TCP/IP for containers to improve the rootless Kubernetes experience.

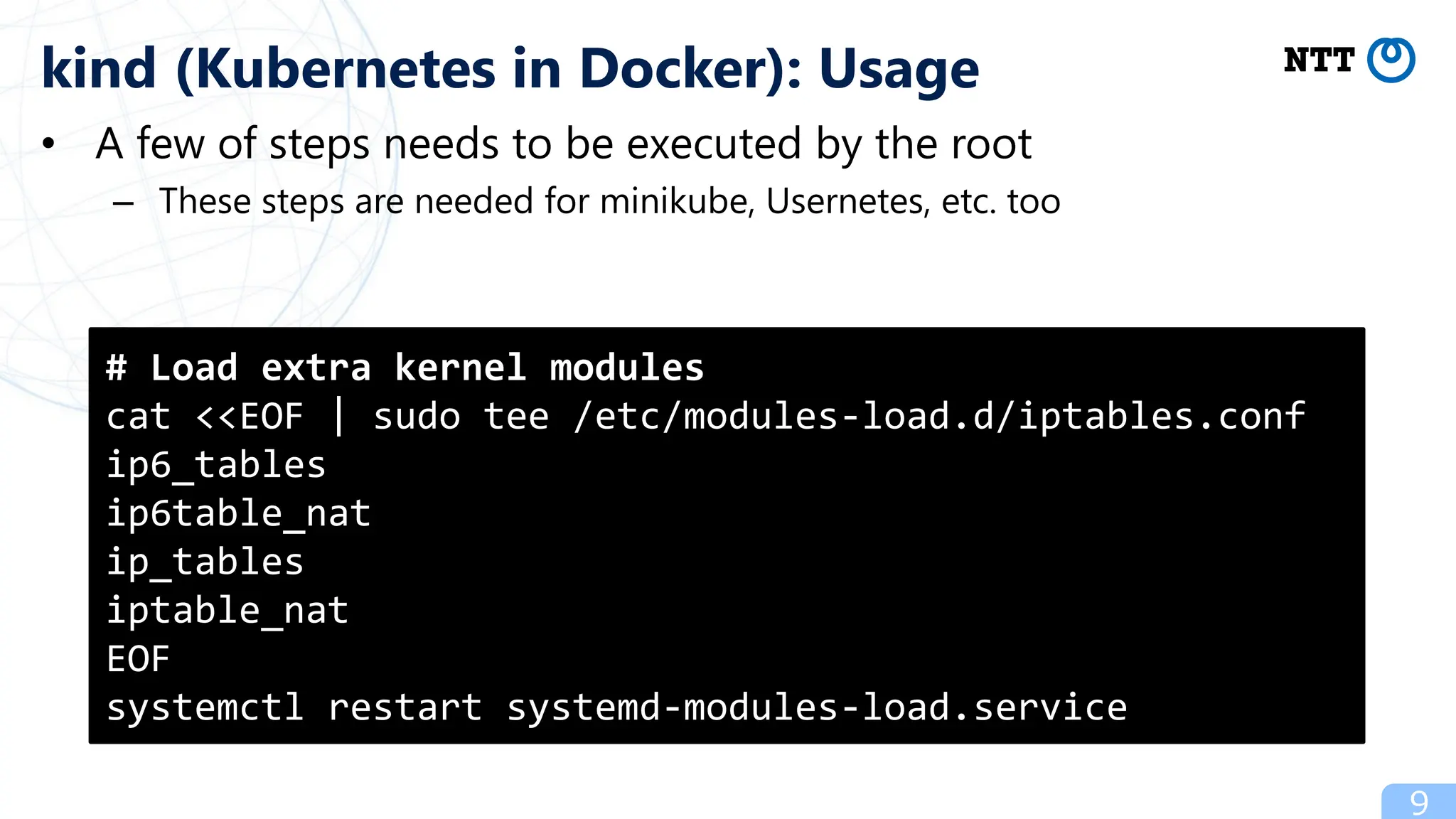
![• A few of steps needs to be executed by the root
– These steps are needed for minikube, Usernetes, etc. too
8
kind (Kubernetes in Docker): Usage
# Allow limiting CPU, memory, etc. via cgroups
cat <<EOF | sudo tee
/etc/systemd/system/user@.service.d/delegate.conf
[Service]
Delegate=cpu cpuset io memory pids
EOF
sudo systemctl daemon-reload
Needs cgroup v2
(RHEL >= 9, etc.)](https://image.slidesharecdn.com/20231116podmanspecialeventkubernetesinrootlesspodman-231117201823-4feac1e3/75/Podman-Special-Event-Kubernetes-in-Rootless-Podman-8-2048.jpg)