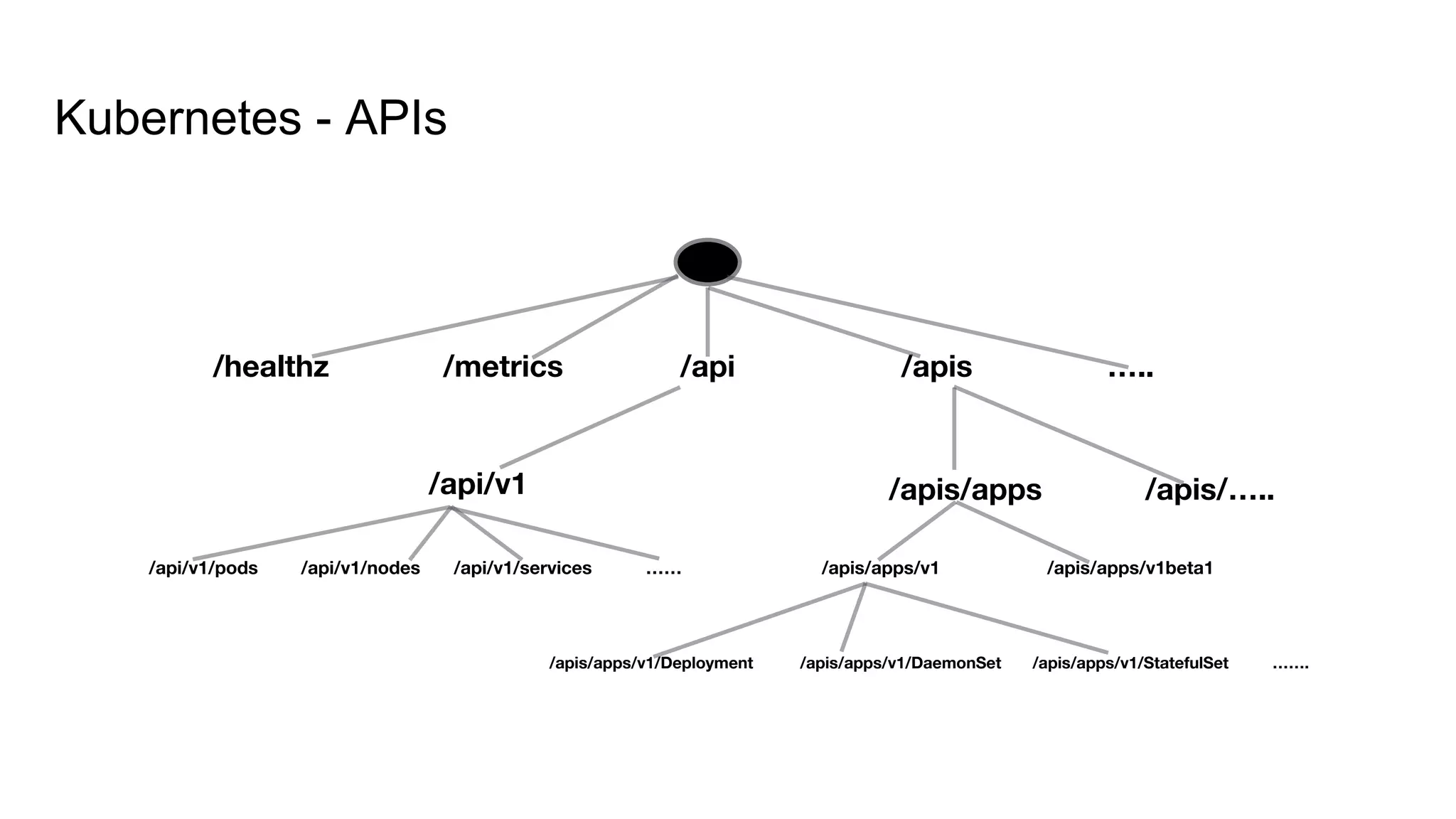
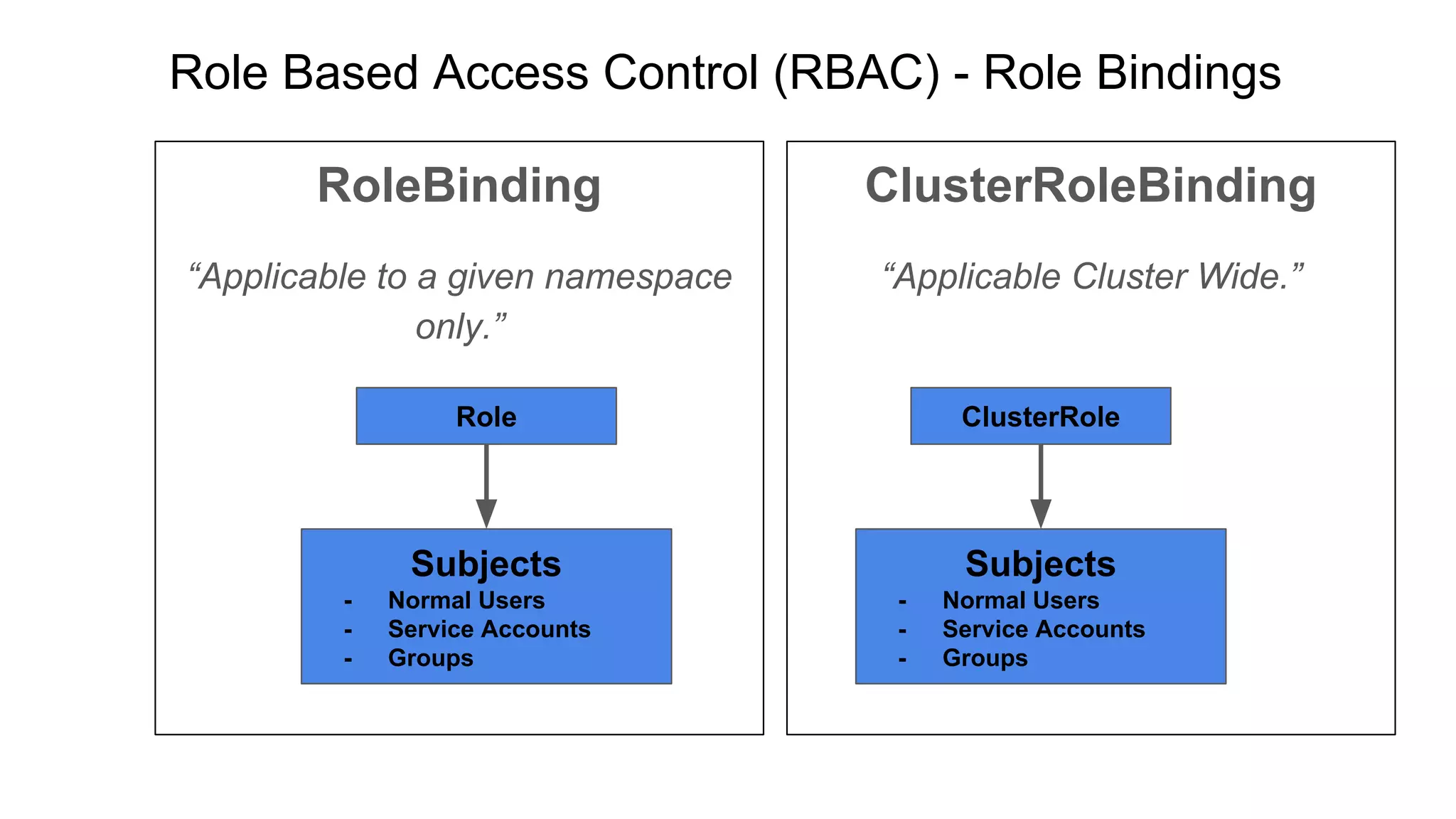
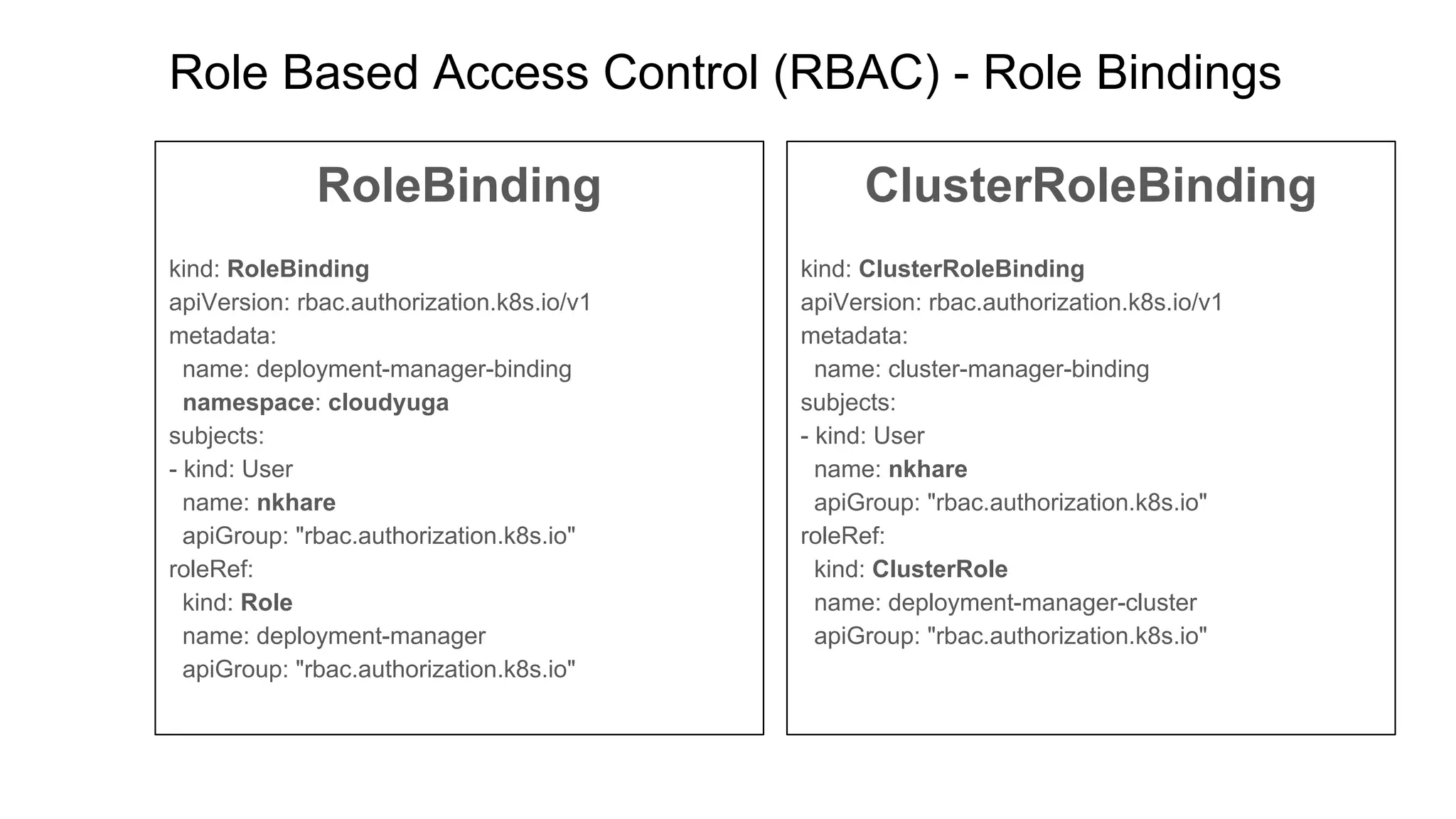
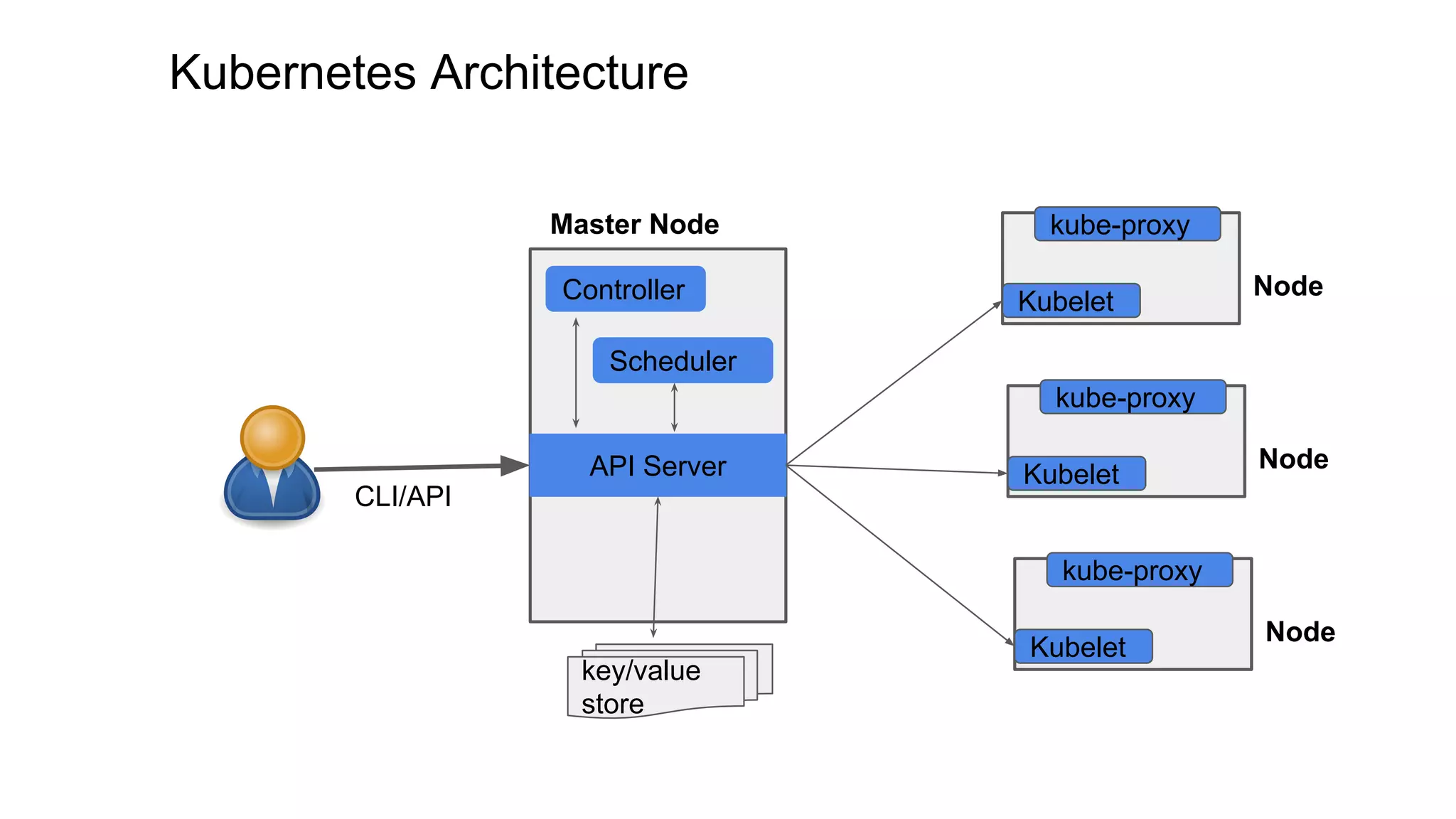
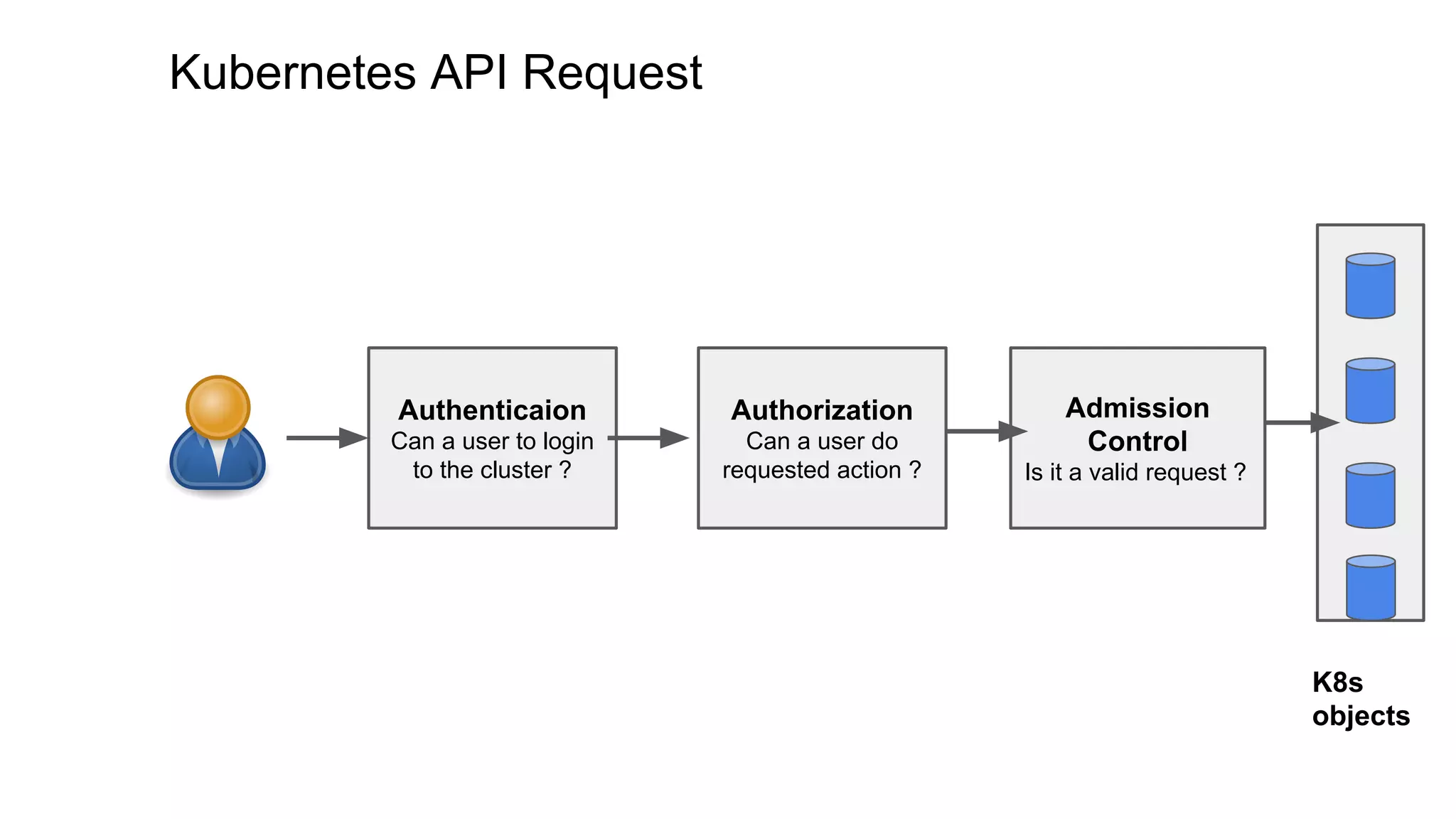
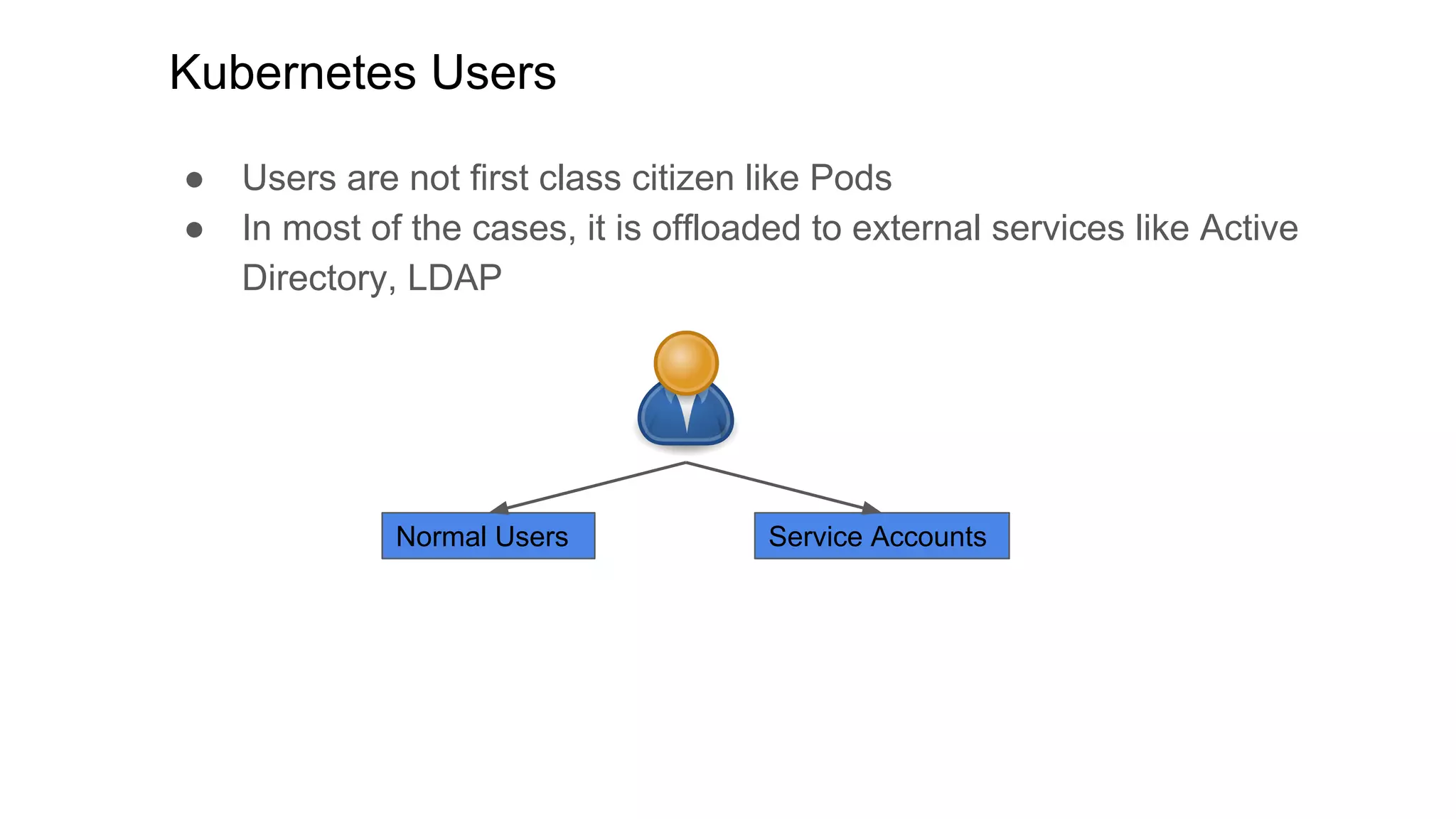
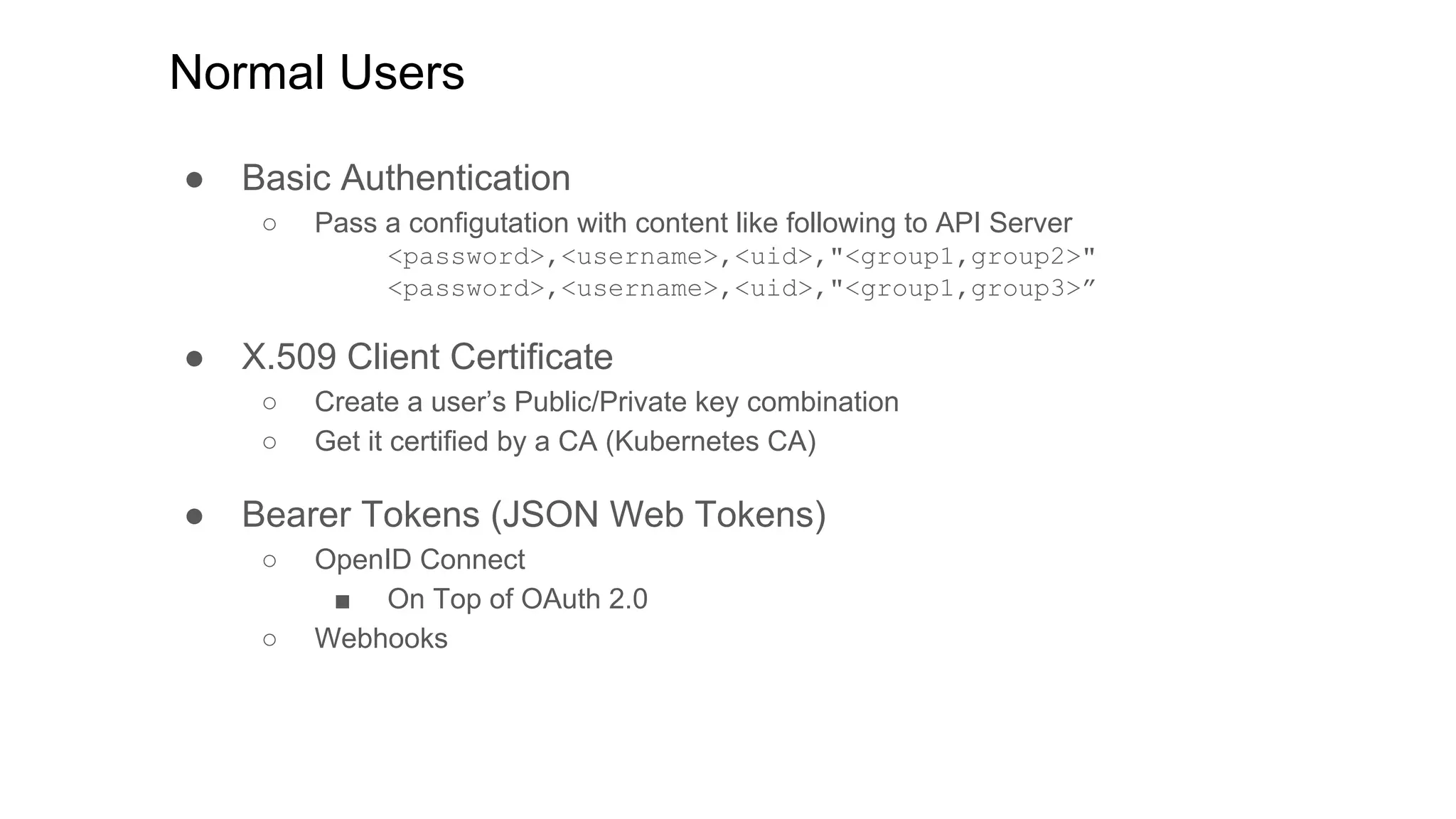
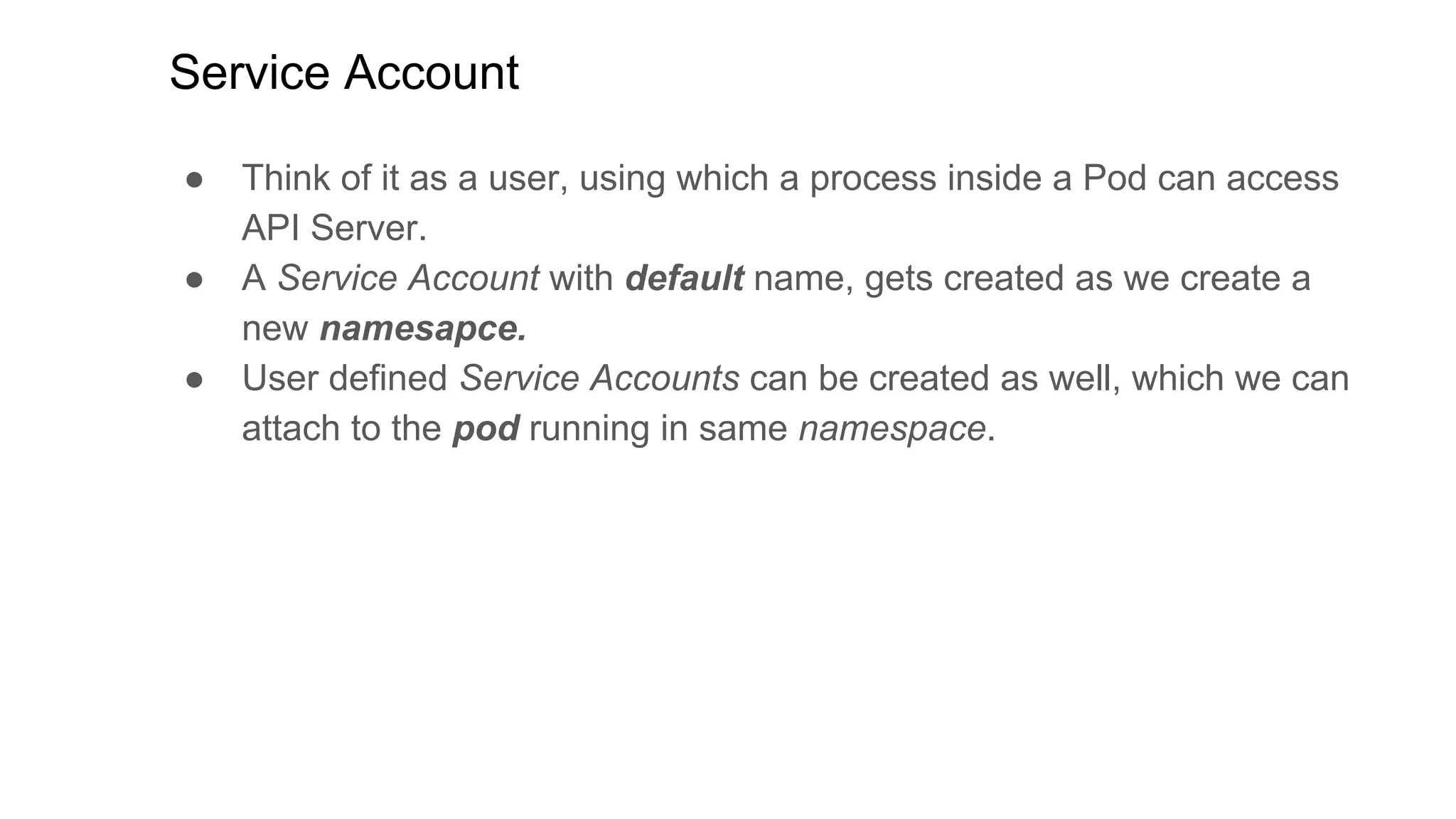
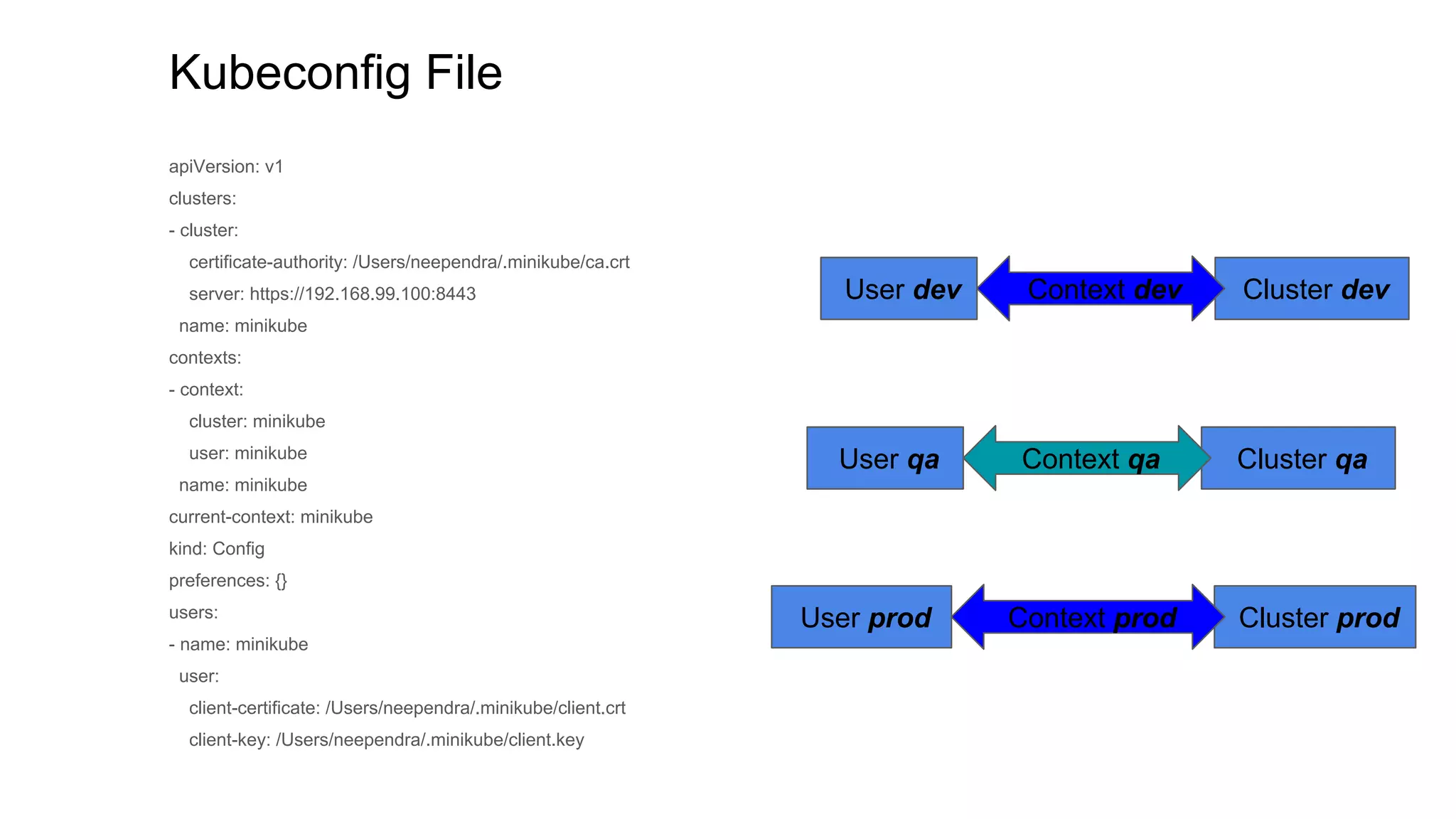
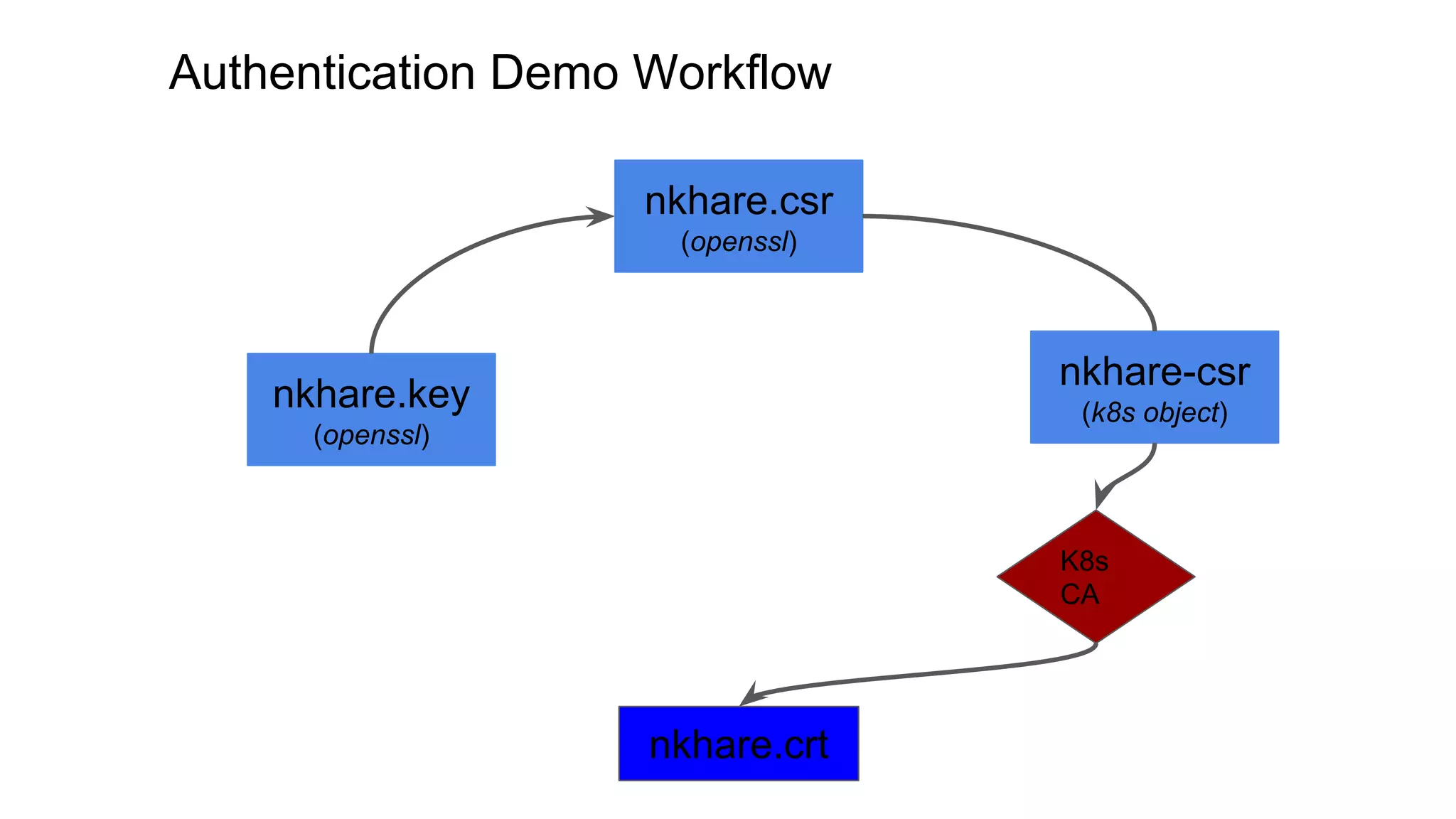
This document discusses user authentication and authorization in Kubernetes. It describes how Kubernetes uses external services like Active Directory and LDAP for user authentication. It also explains the different types of users in Kubernetes including normal users, service accounts, and how kubeconfig files are used. The main authorization mechanism in Kubernetes is Role-Based Access Control (RBAC) which uses roles and role bindings to control access to Kubernetes API resources and operations.







![Role Based Access Control (RBAC) - Roles
Role
“Applicable to a given namespace
only.”
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: cloudyuga
name: deployment-manager
rules:
- apiGroups: ["", "apps"]
resources: ["deployments", "replicasets", "pods"]
verbs: ["get", "list", "watch", "create", "update"]
ClusterRole
“Applicable Cluster Wide.”
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: deployment-manager-cluster
rules:
- apiGroups: ["", "apps"]
resources: ["deployments", "replicasets", "pods"]
verbs: ["get", "list", "watch", "create", "update"]](https://image.slidesharecdn.com/userauthenticationandauthorizarionink8s-181109095335/75/User-authentication-and-authorizarion-in-Kubernetes-17-2048.jpg)