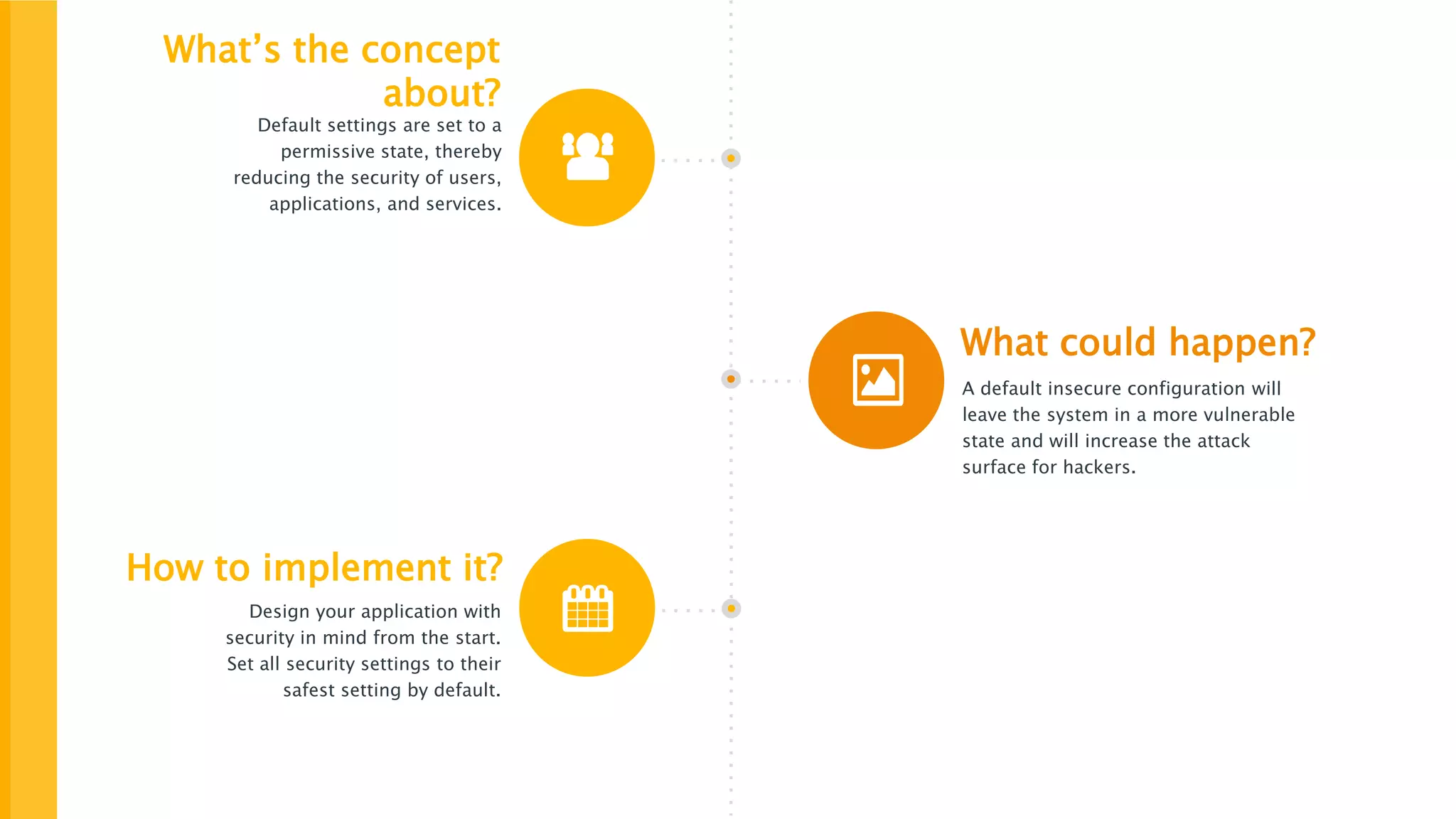
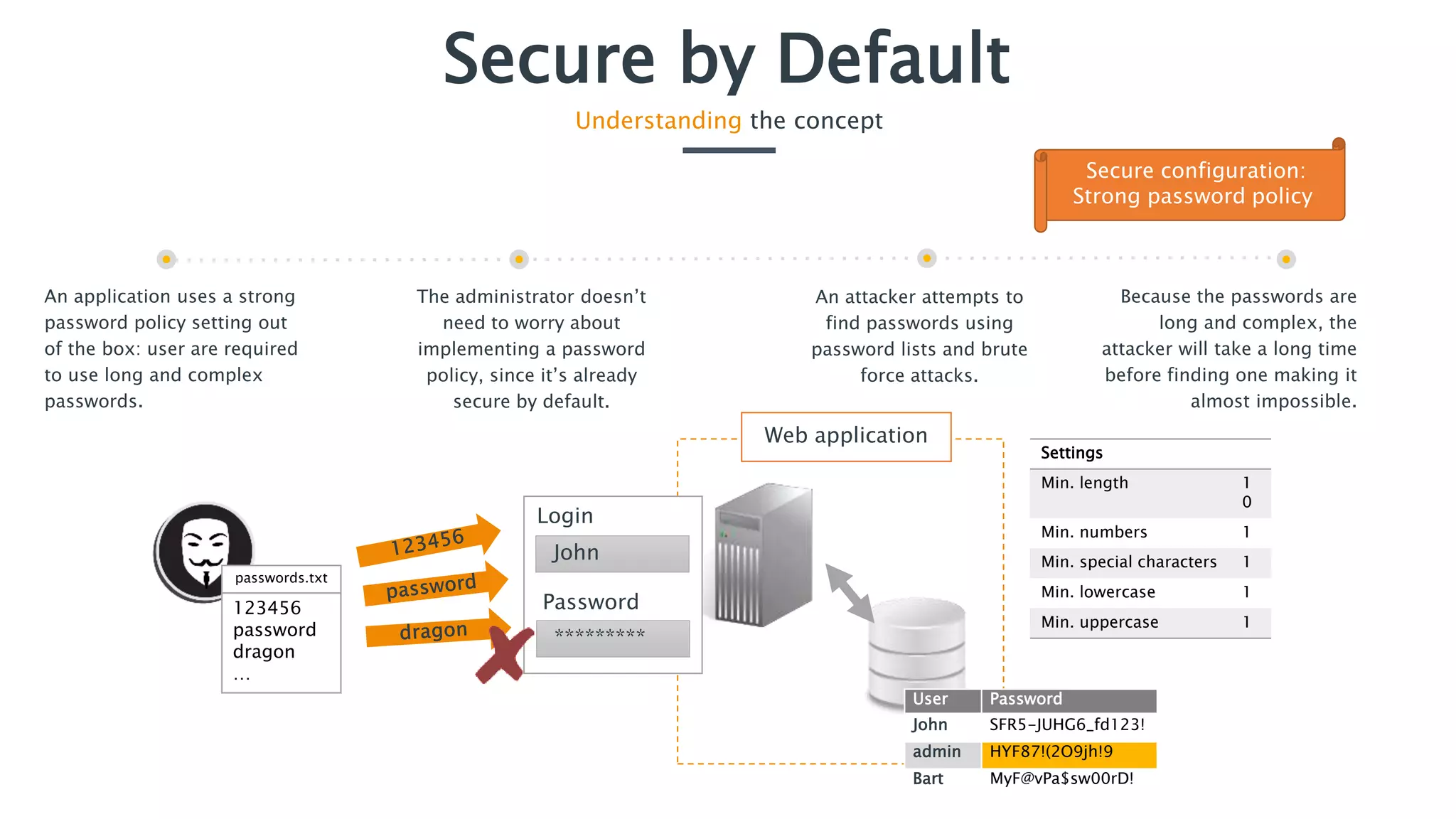
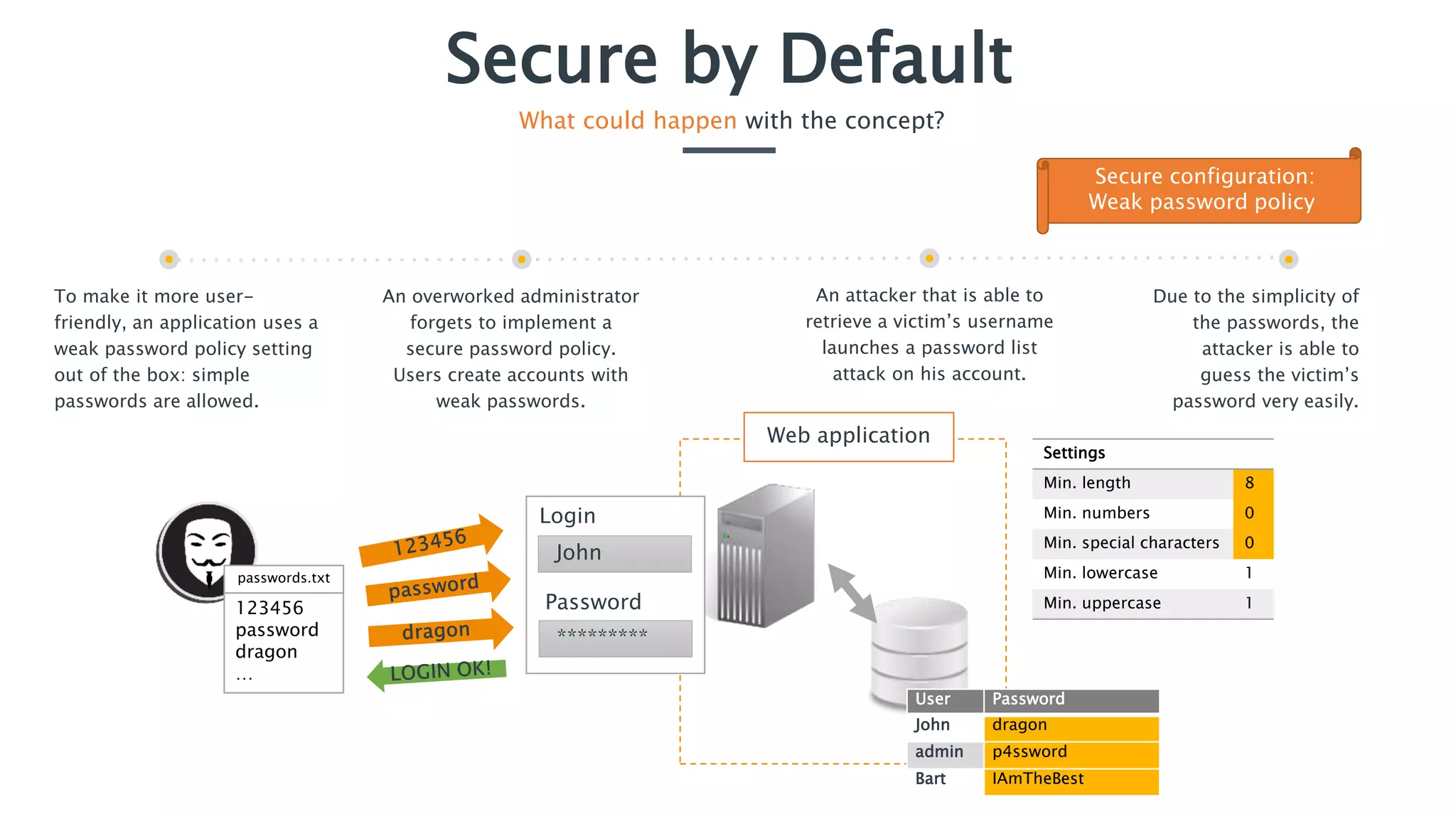
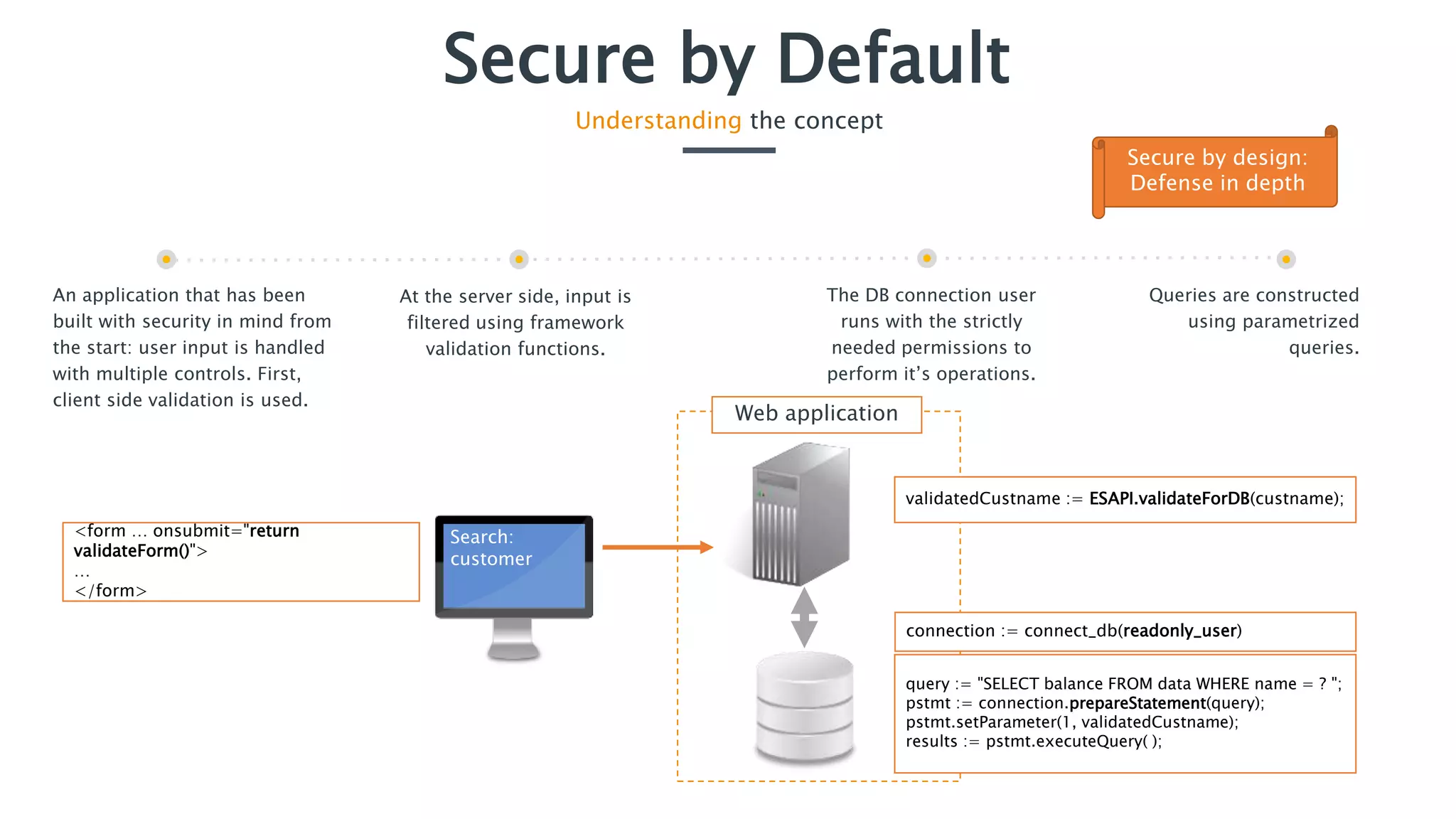
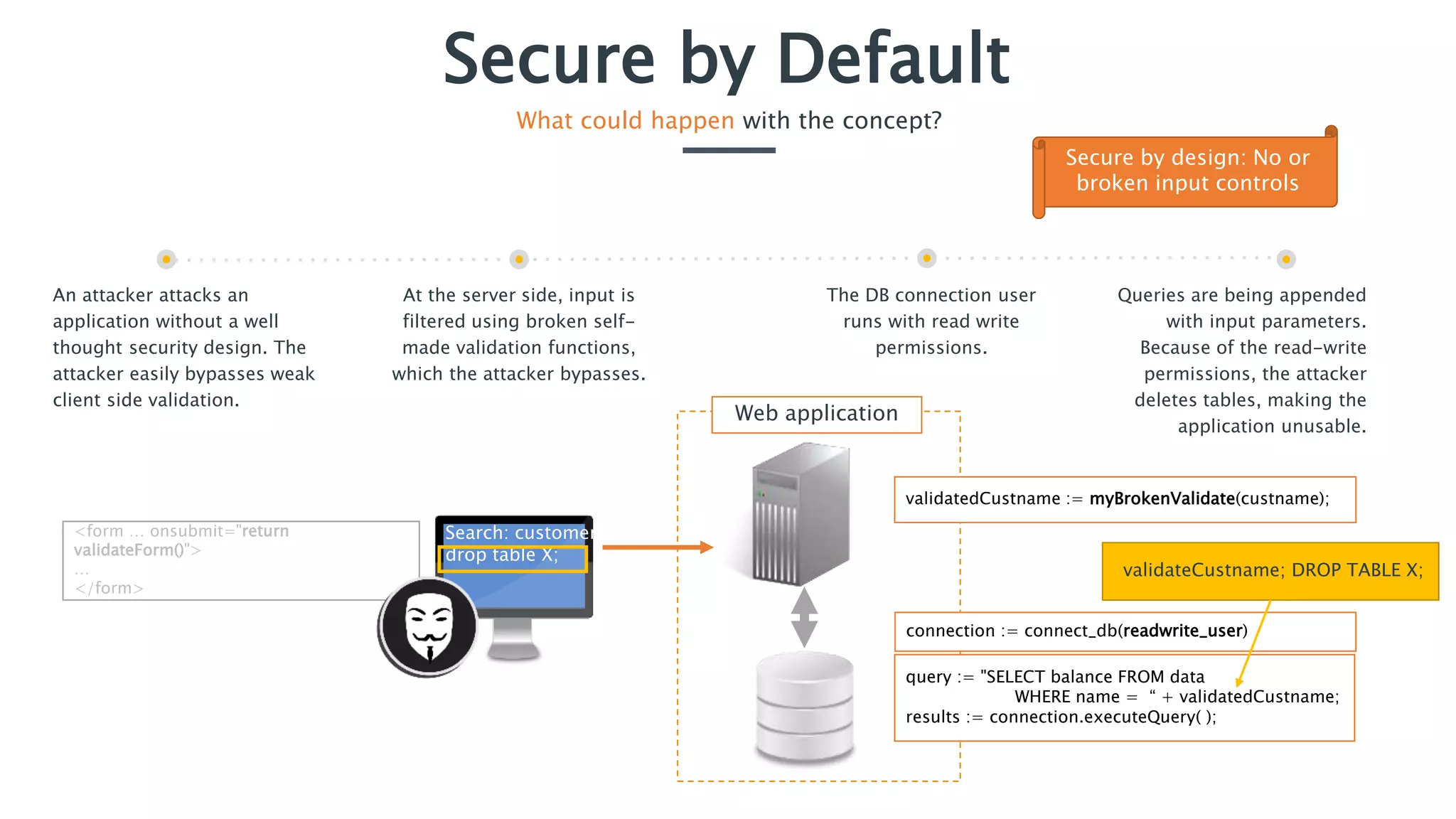
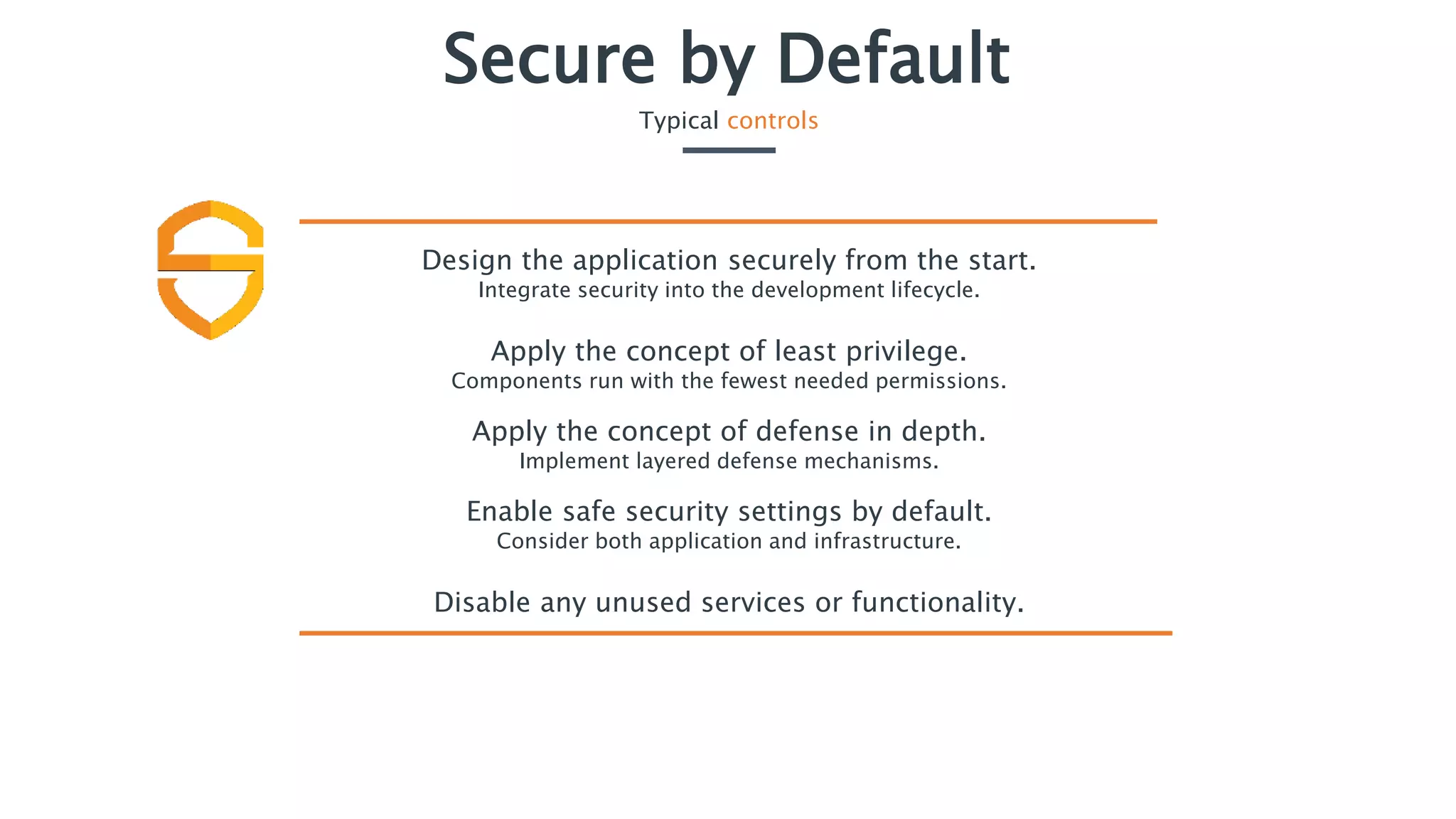
The document discusses the importance of implementing secure by default application security practices to prevent vulnerabilities and reduce the attack surface. It emphasizes designing applications with security in mind from the outset, implementing strong password policies, and integrating security throughout the development lifecycle. Key concepts include the need for strong input controls and the principle of least privilege for components to operate with minimal permissions.