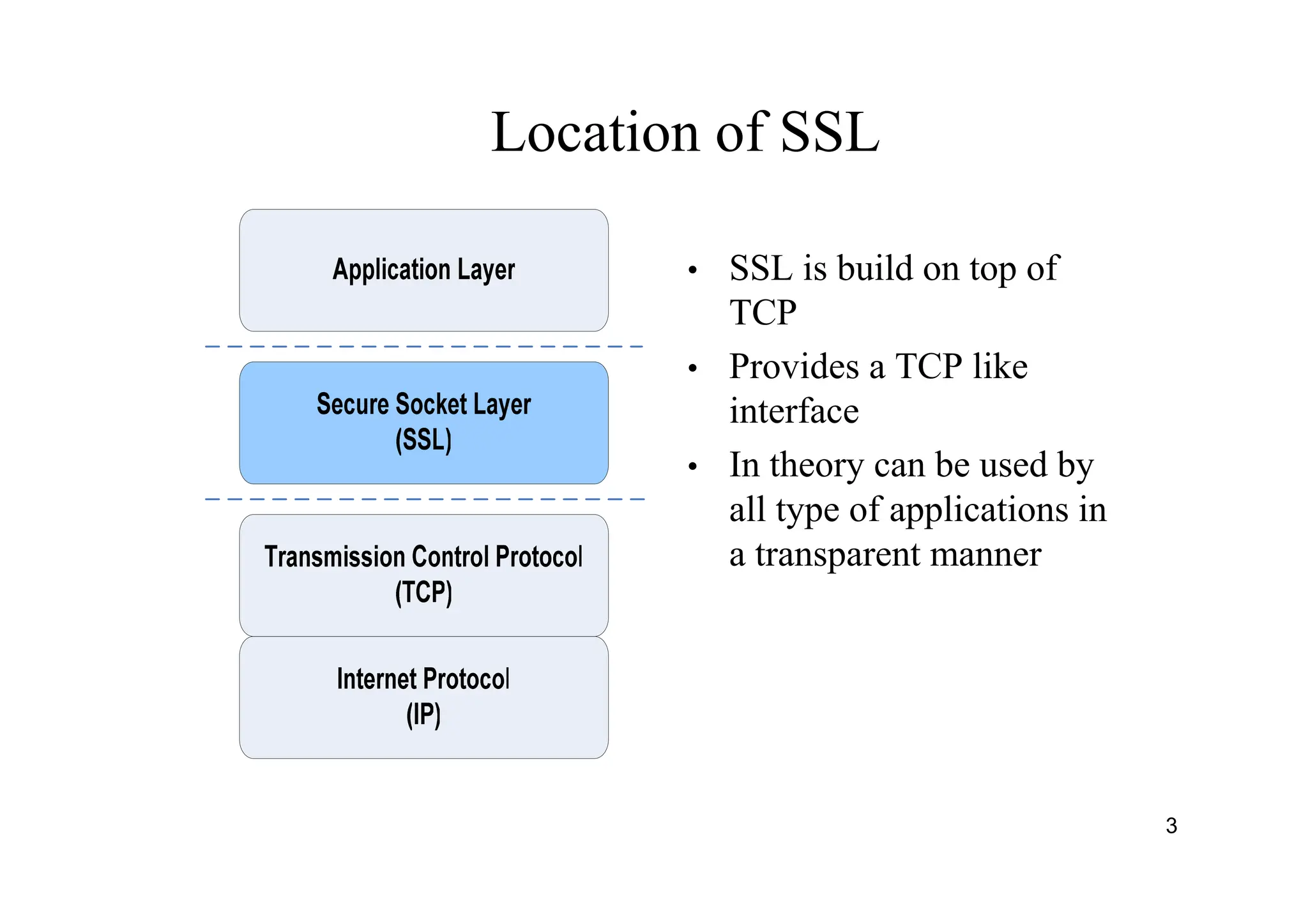
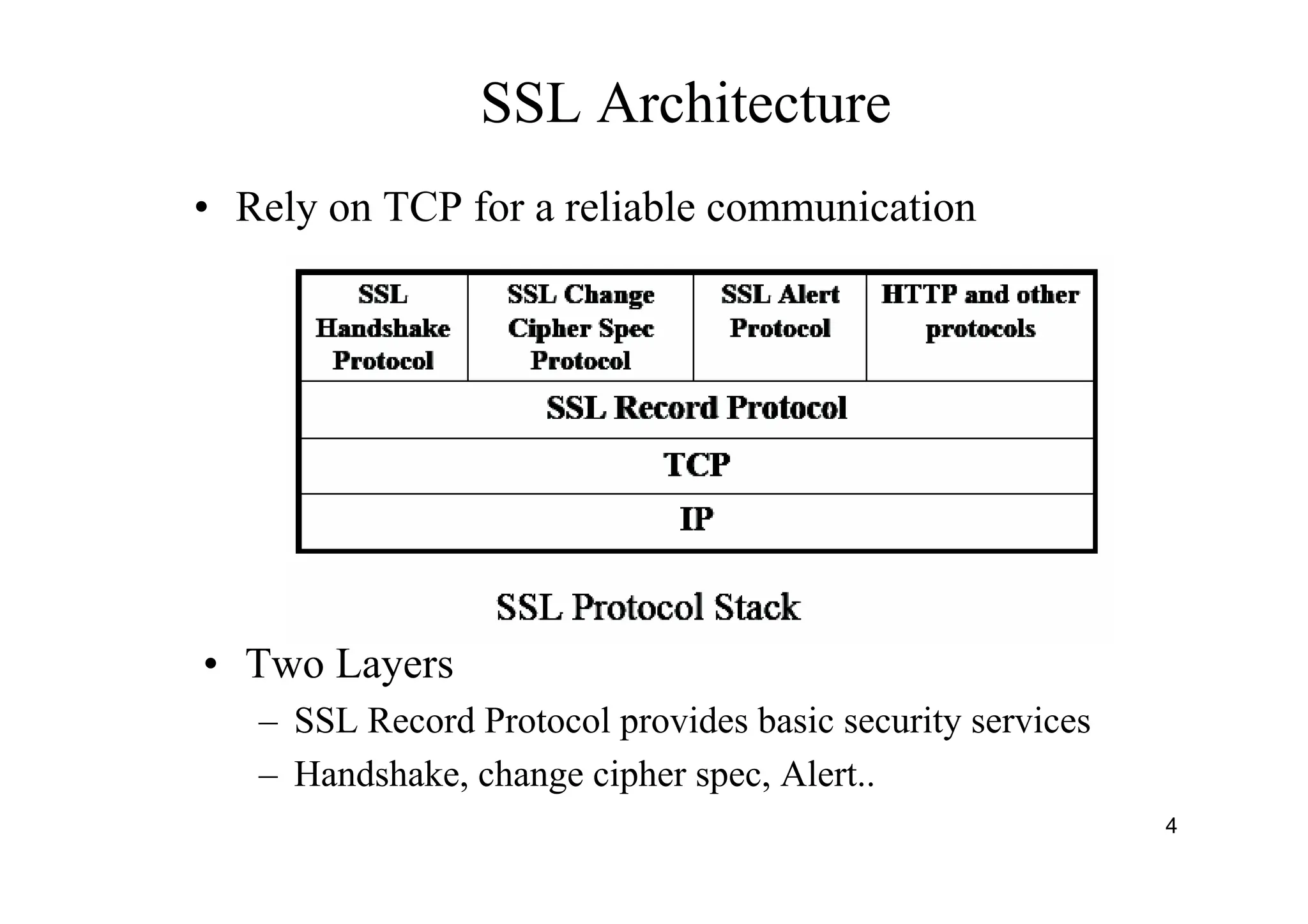
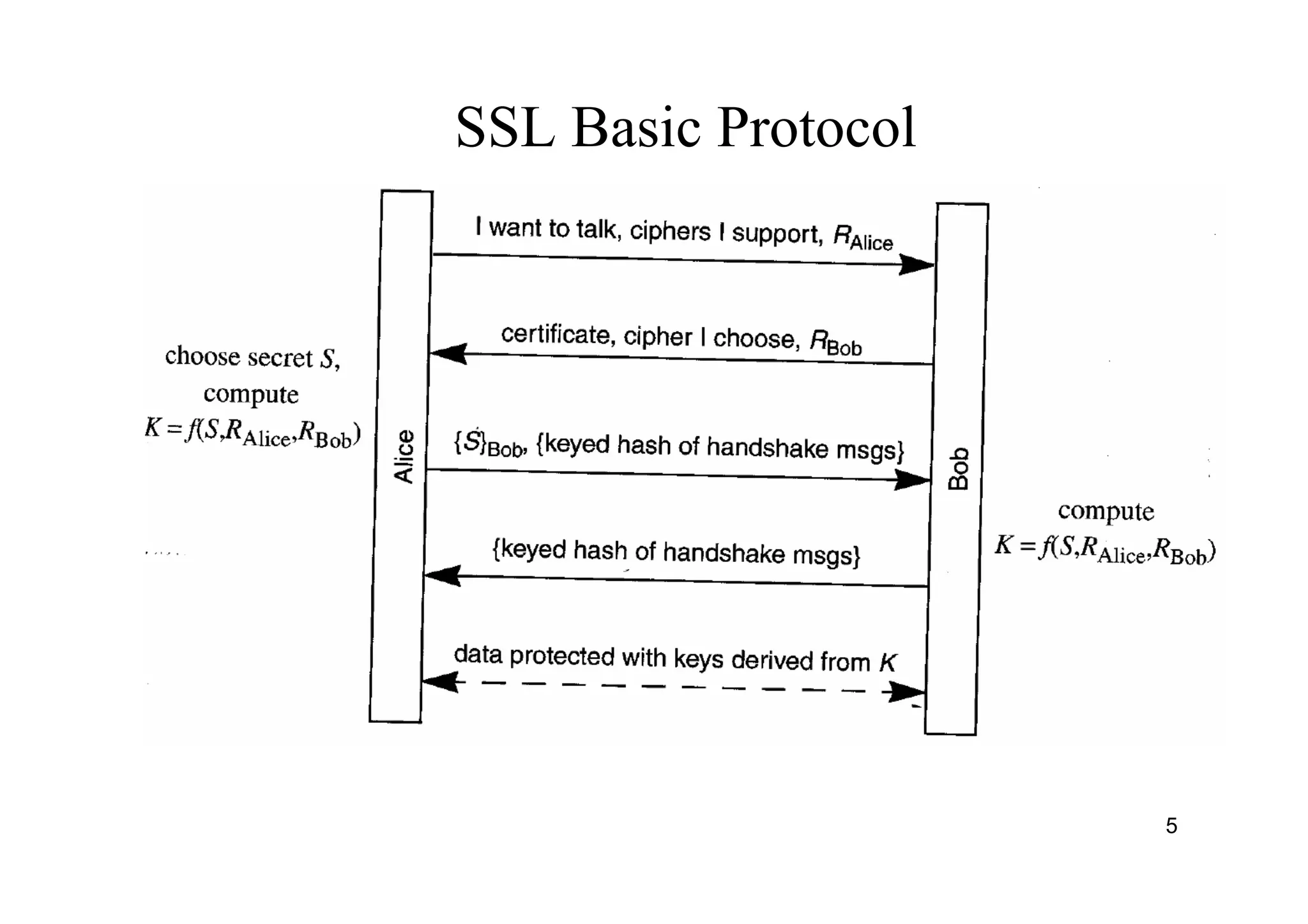
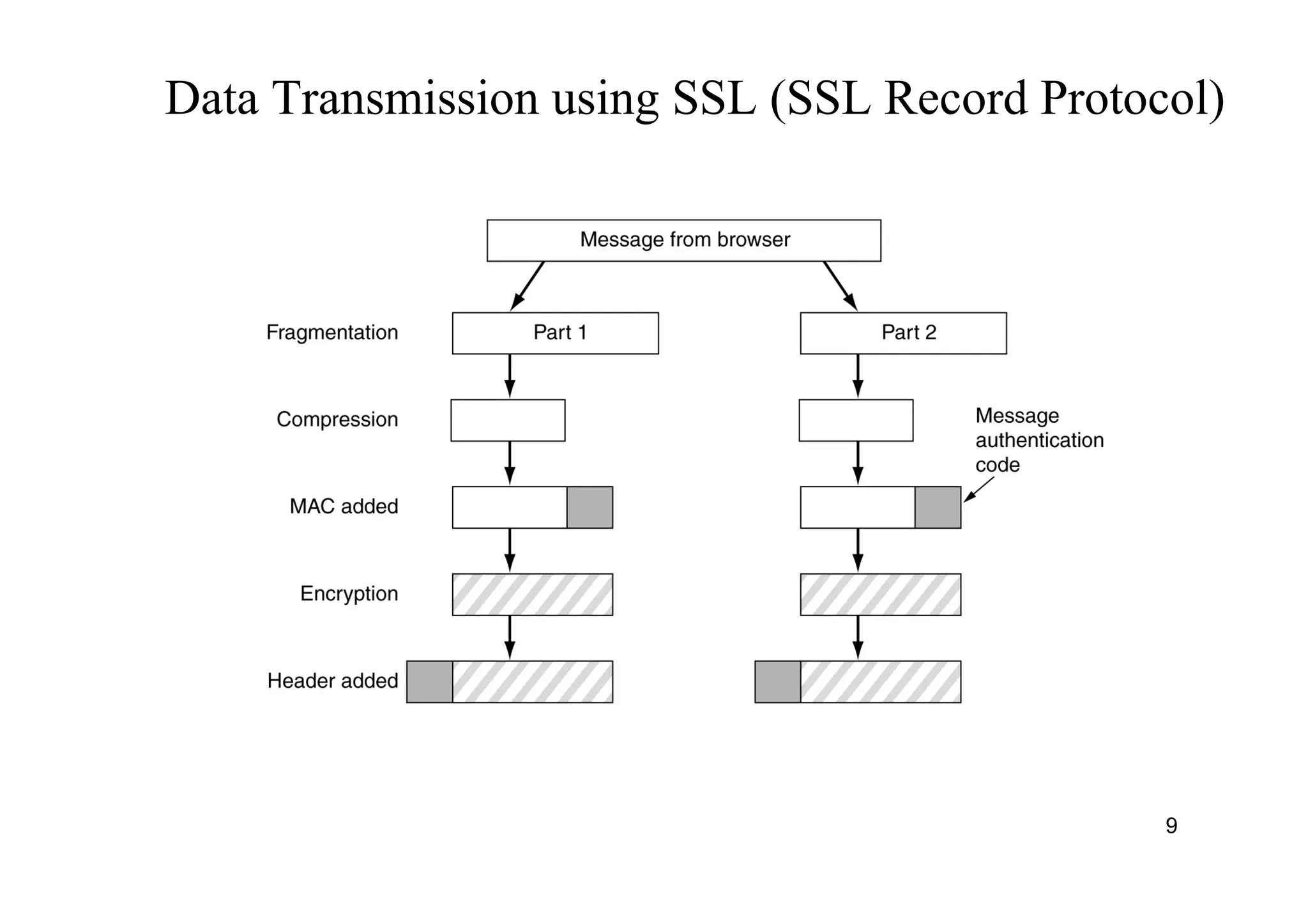
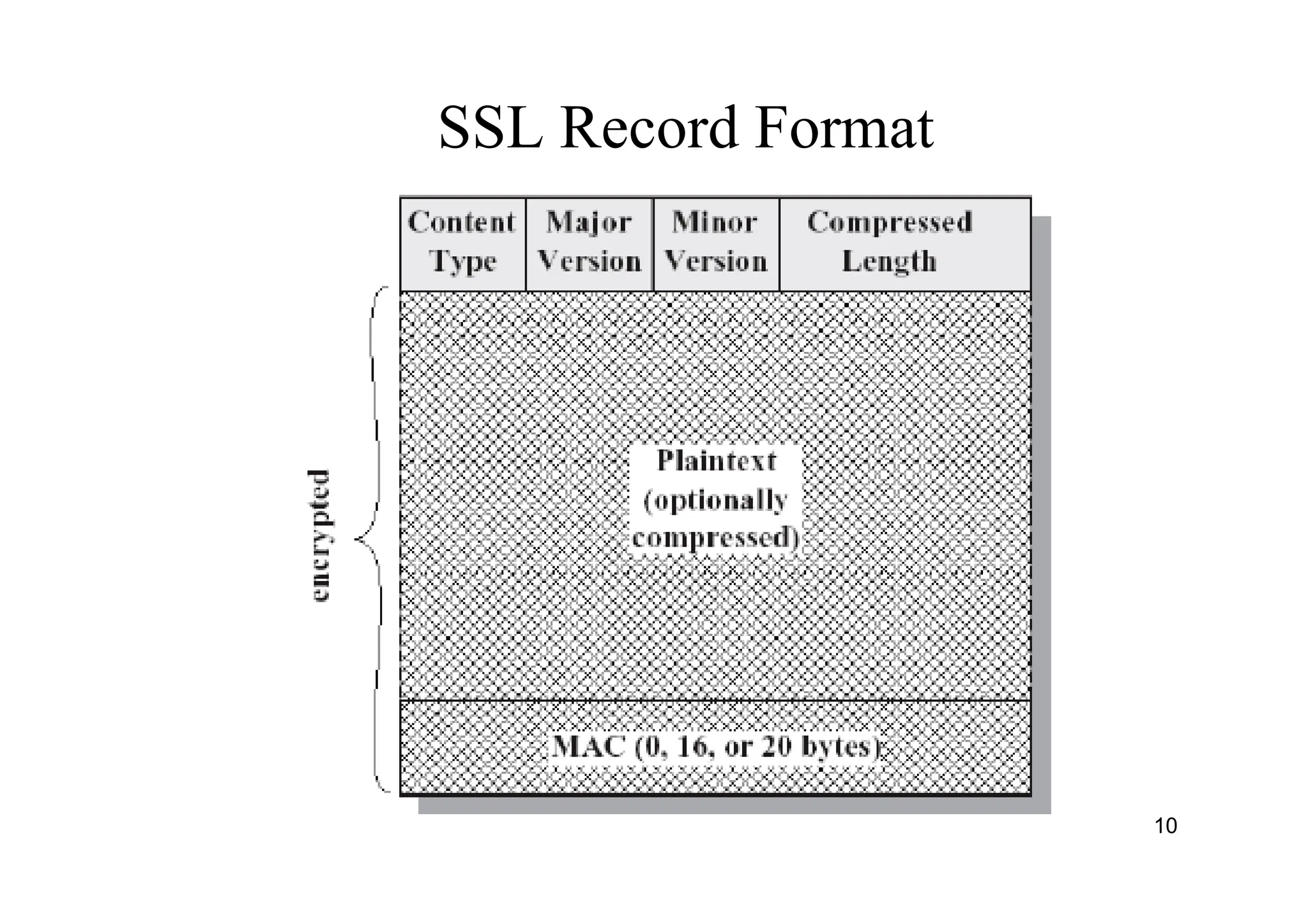
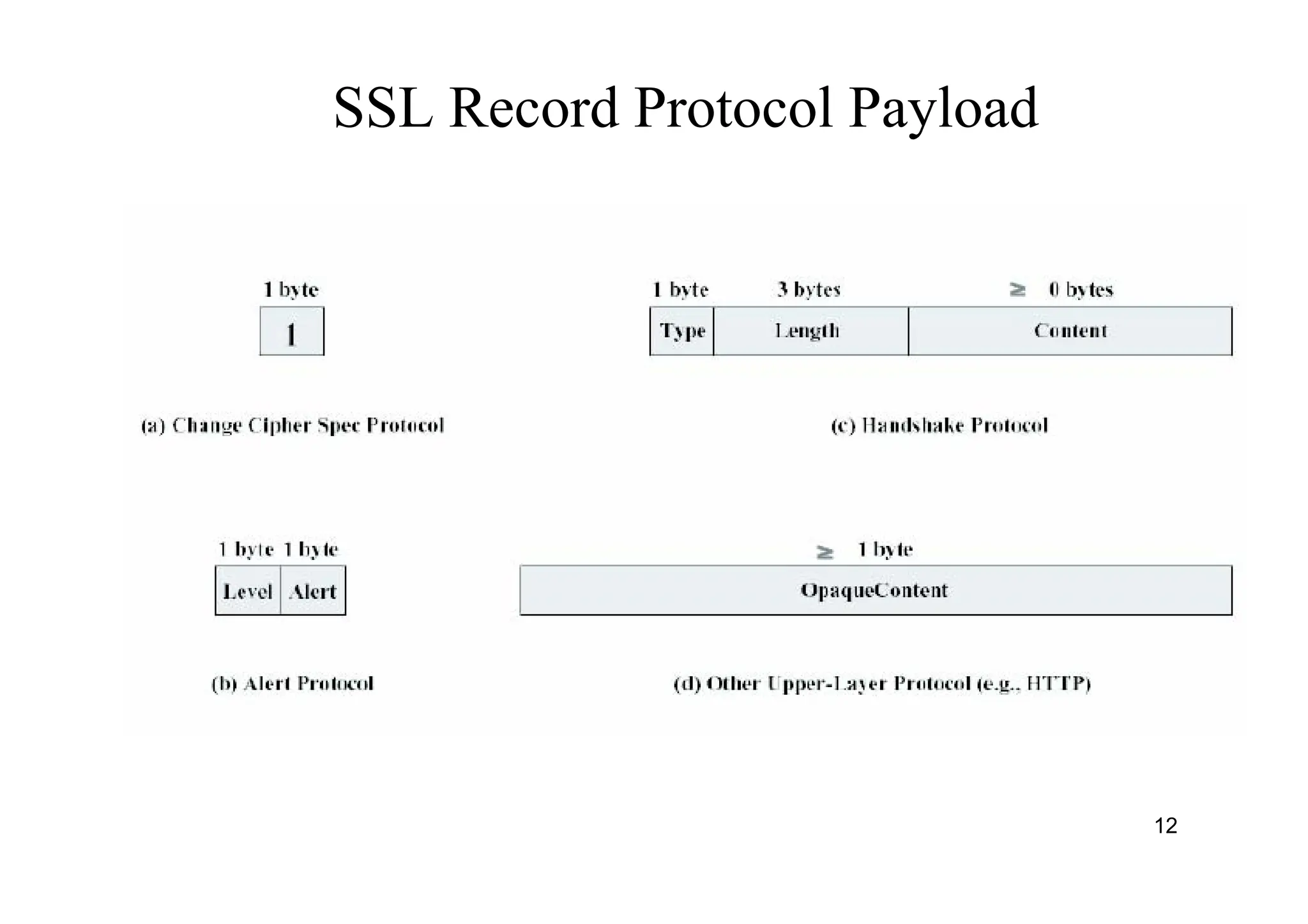
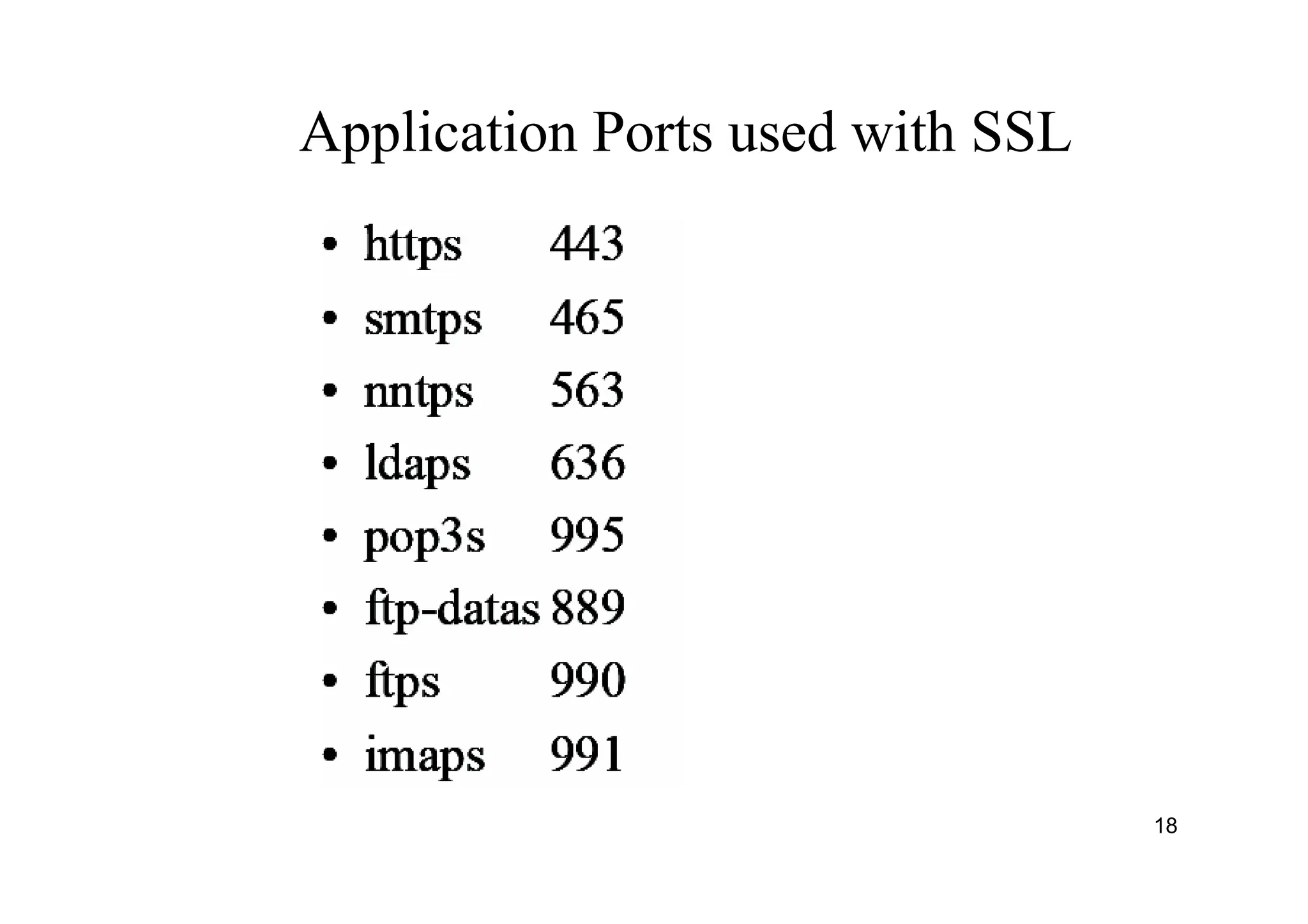
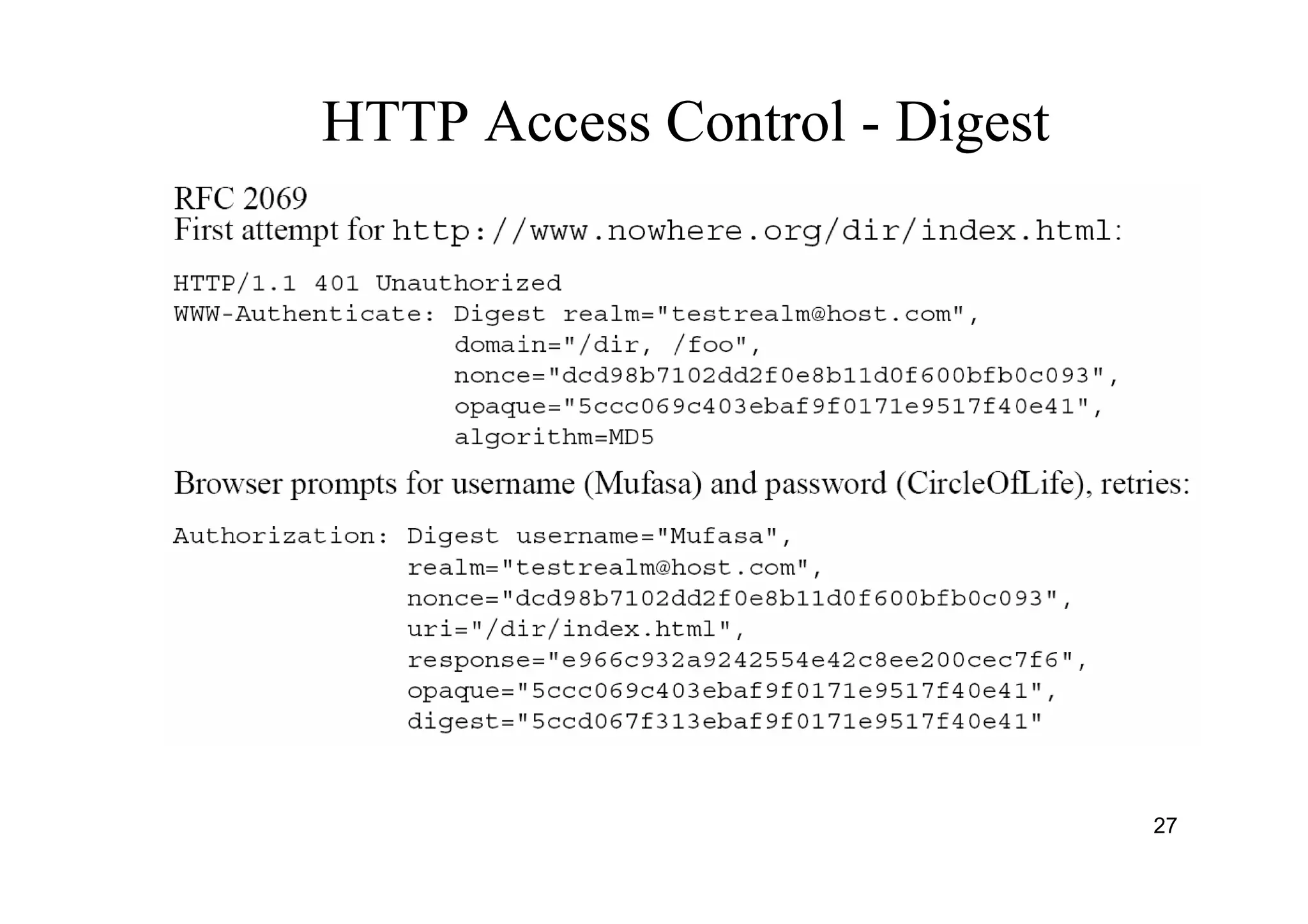
The document provides an overview of SSL/TLS protocols, detailing their architecture, components, and functionality aimed at securing internet communications. It explains the structure of SSL sessions and connections, emphasizing the handshake protocol and record protocol for confidentiality and message integrity. Additionally, it covers web security issues and authentication methods, including basic and digest authentication.