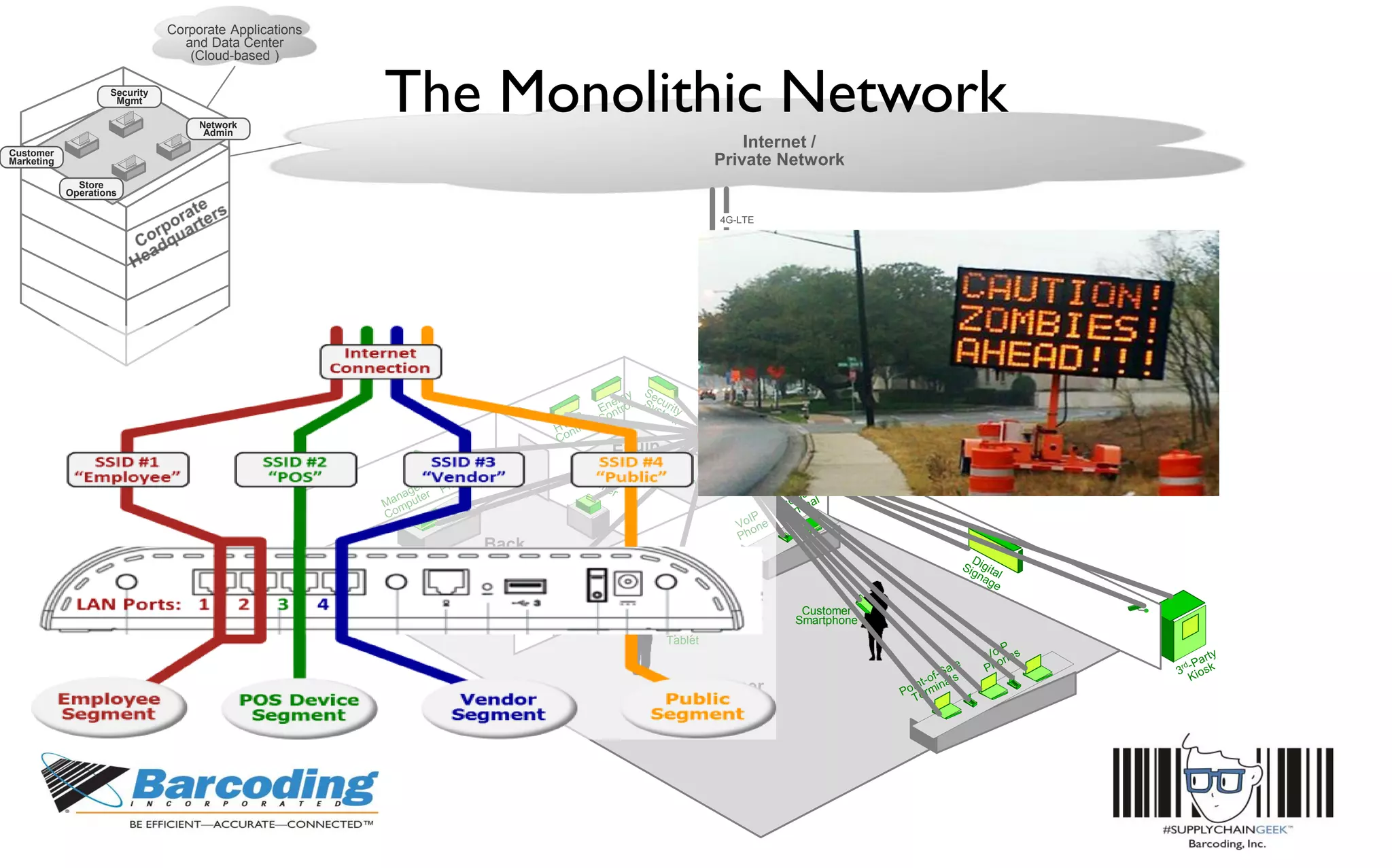
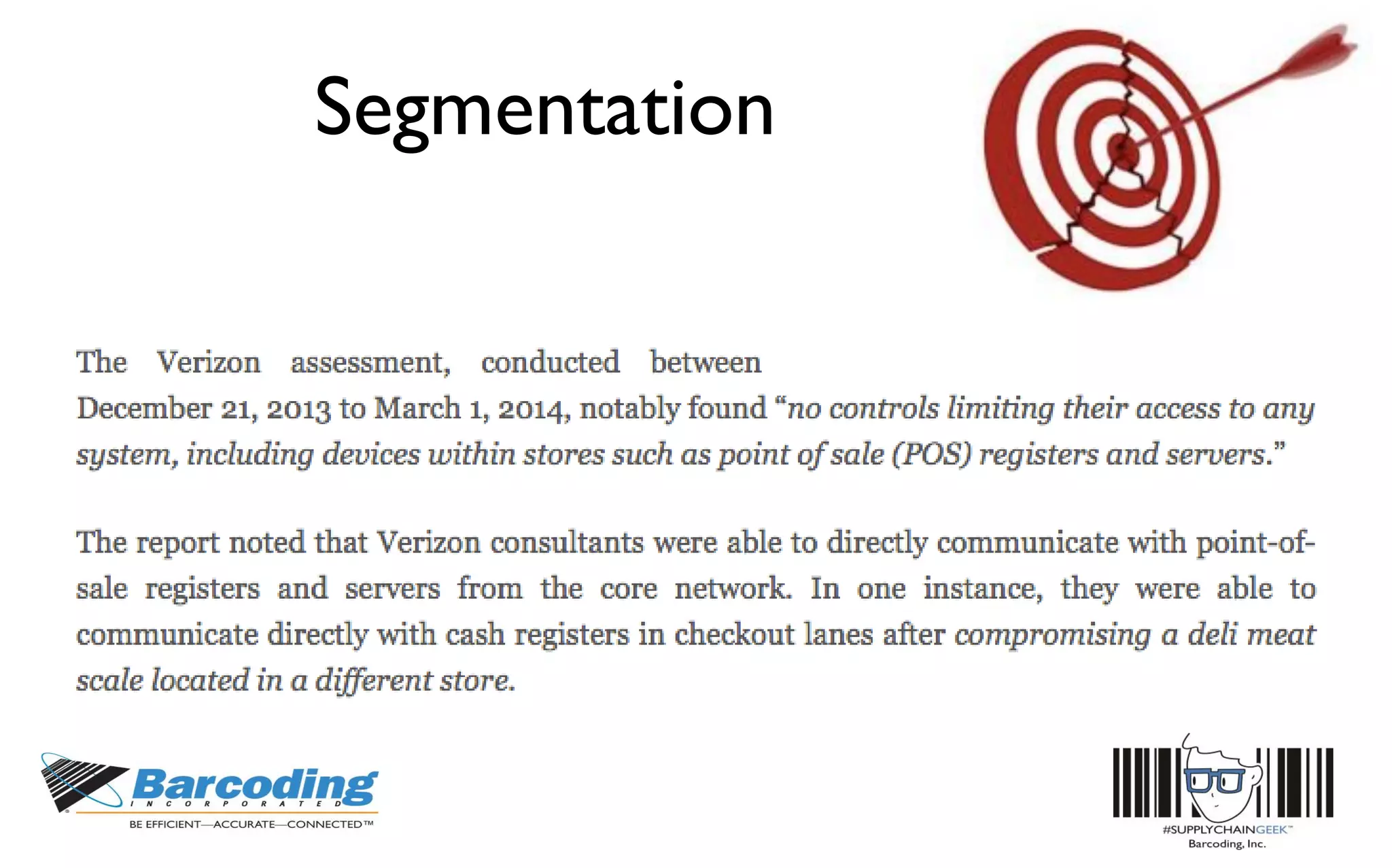
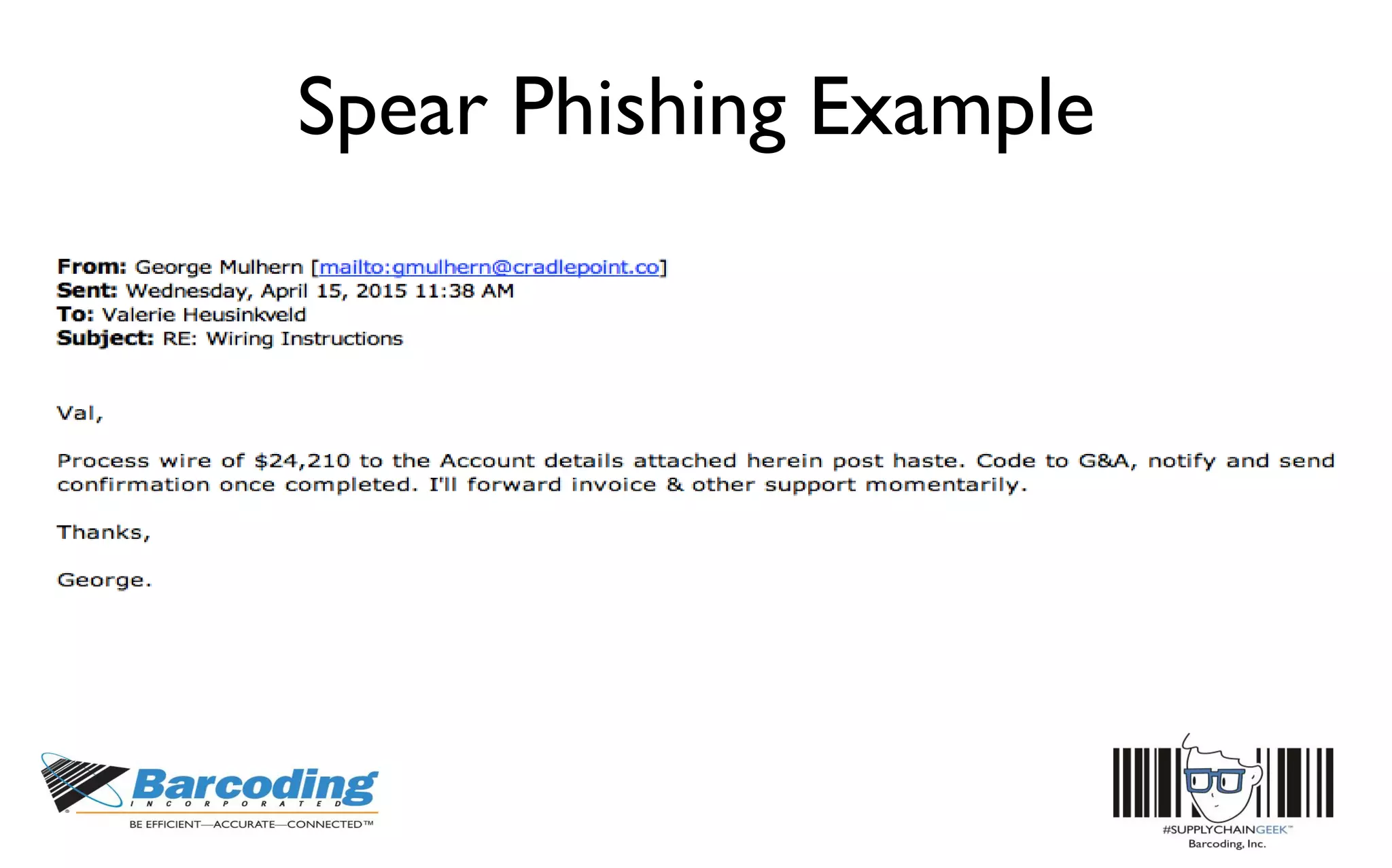
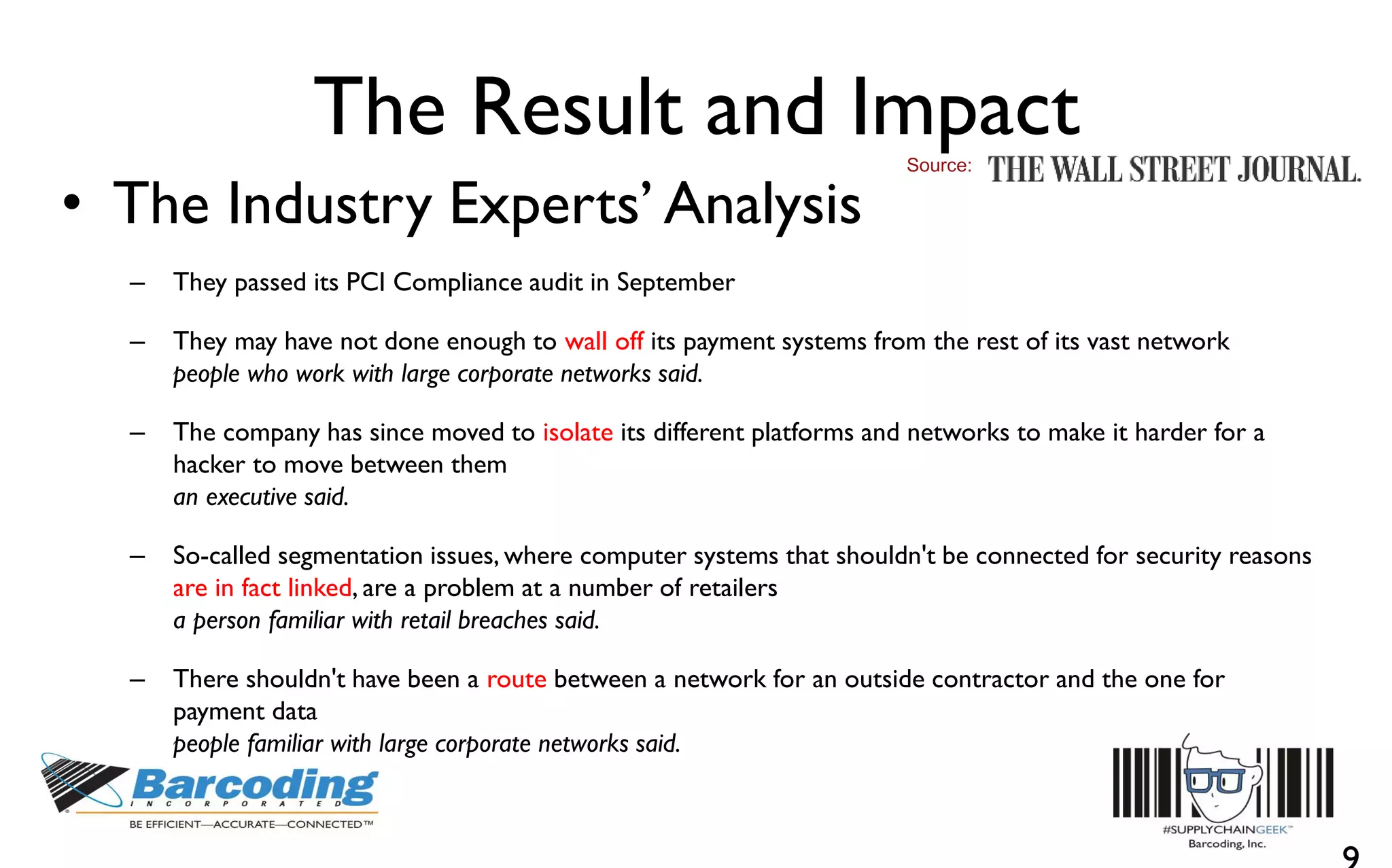
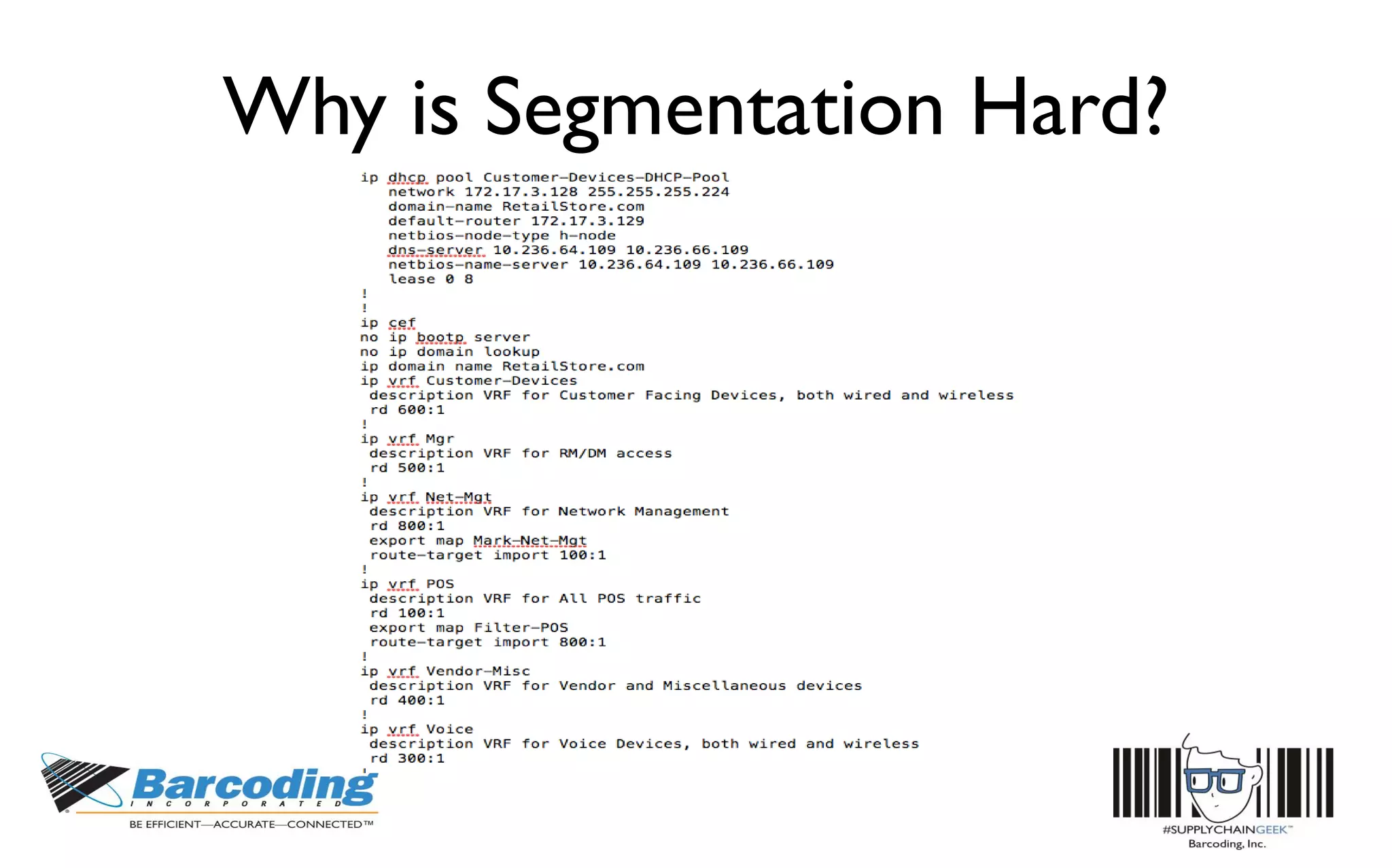
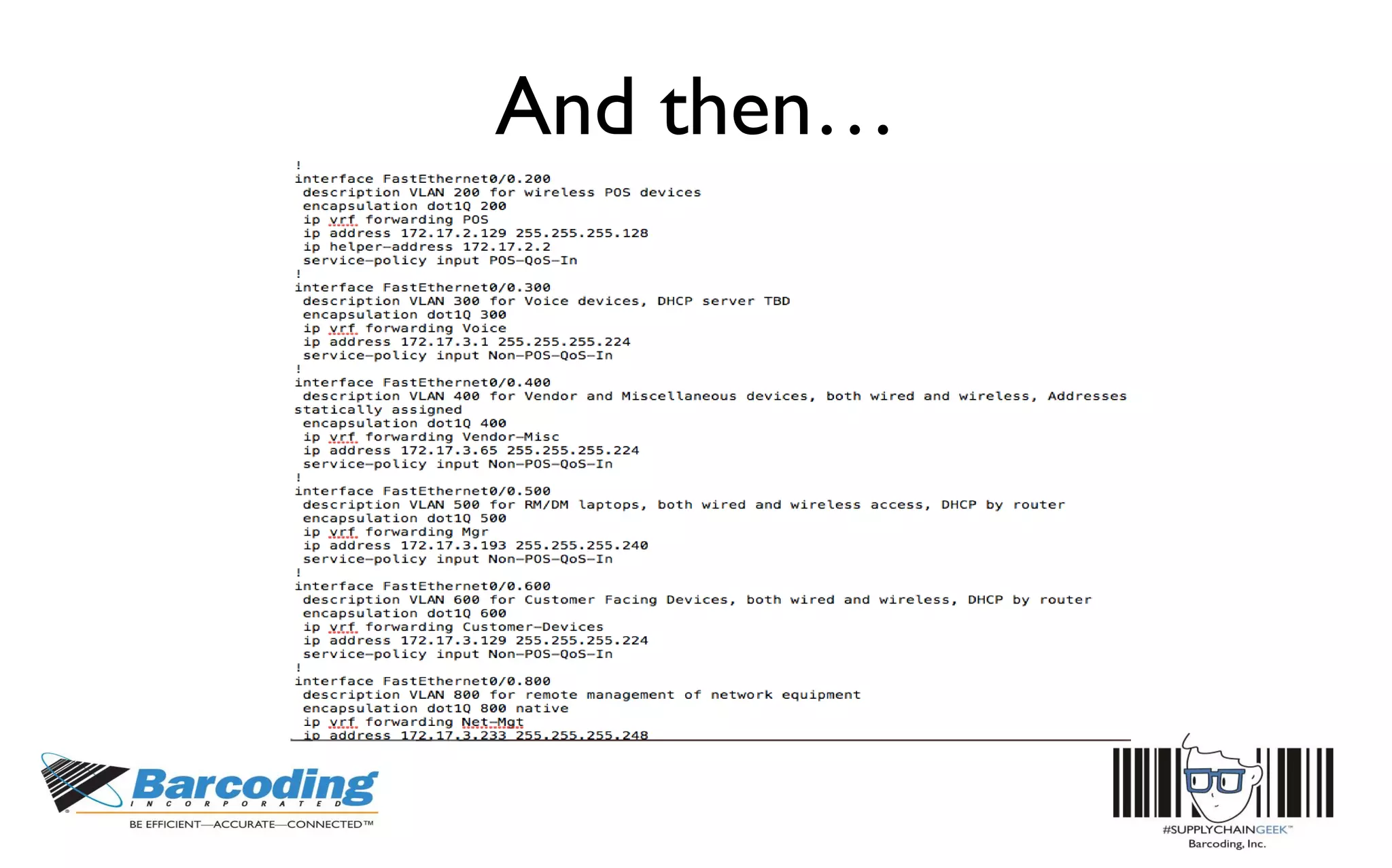
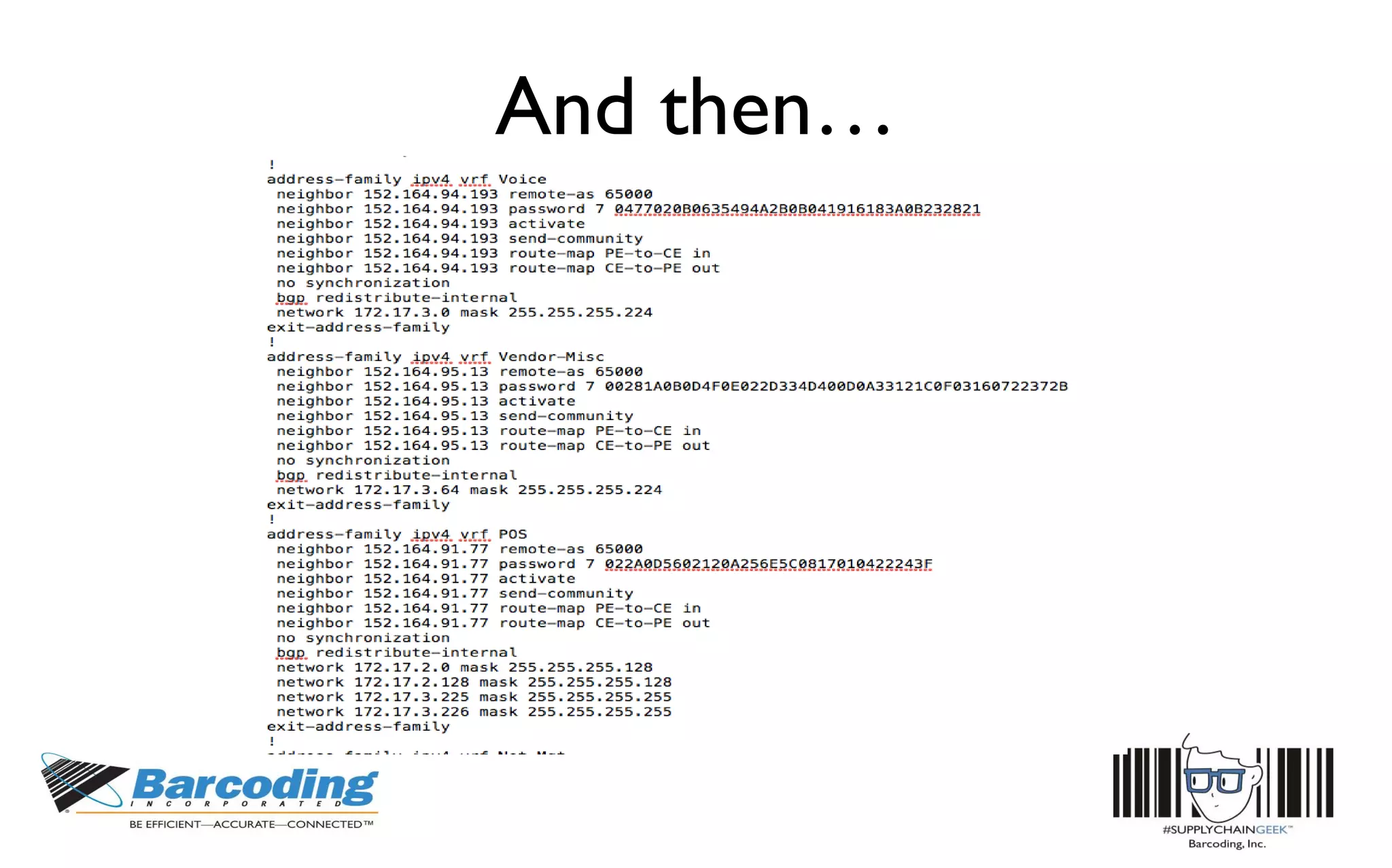
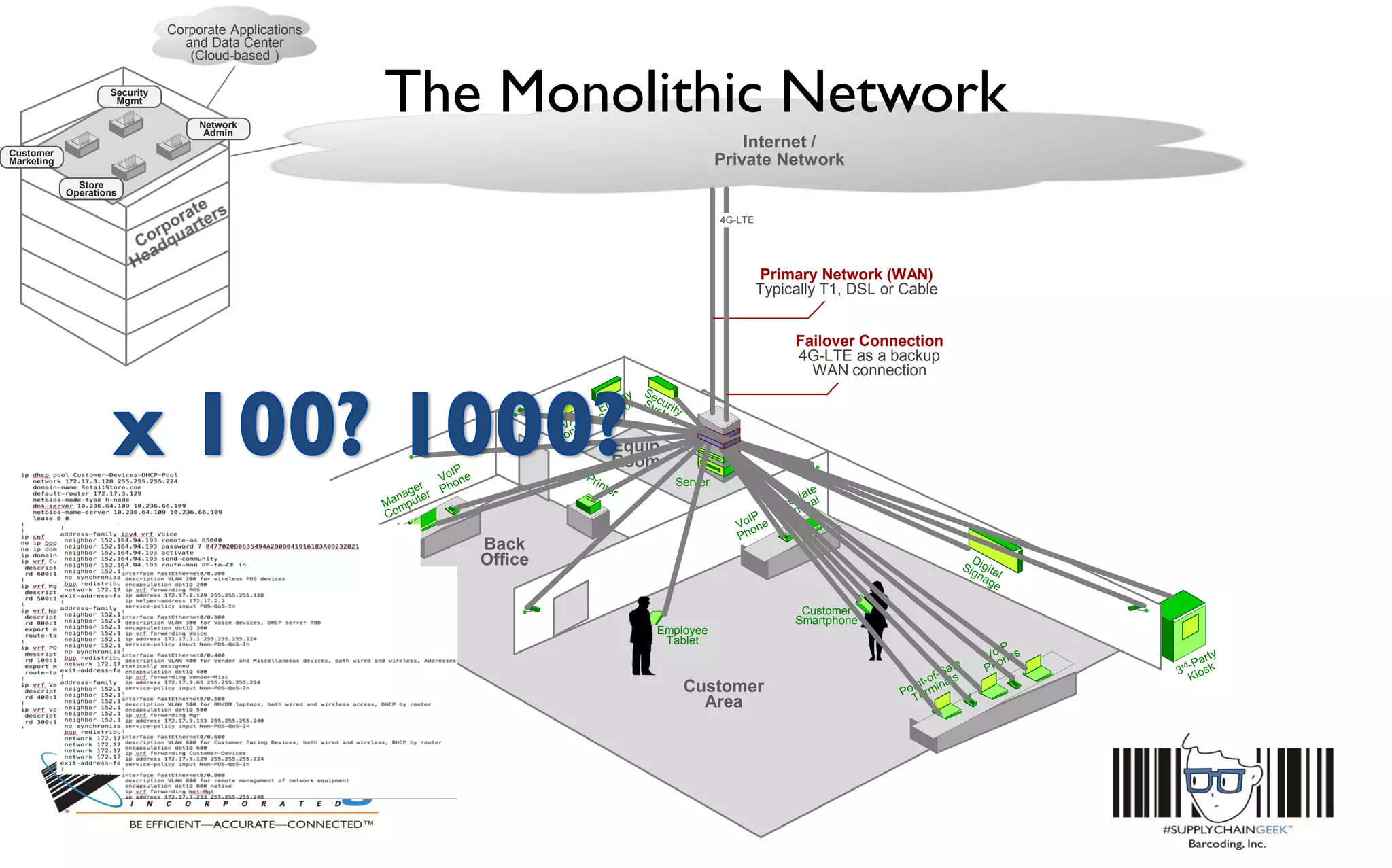
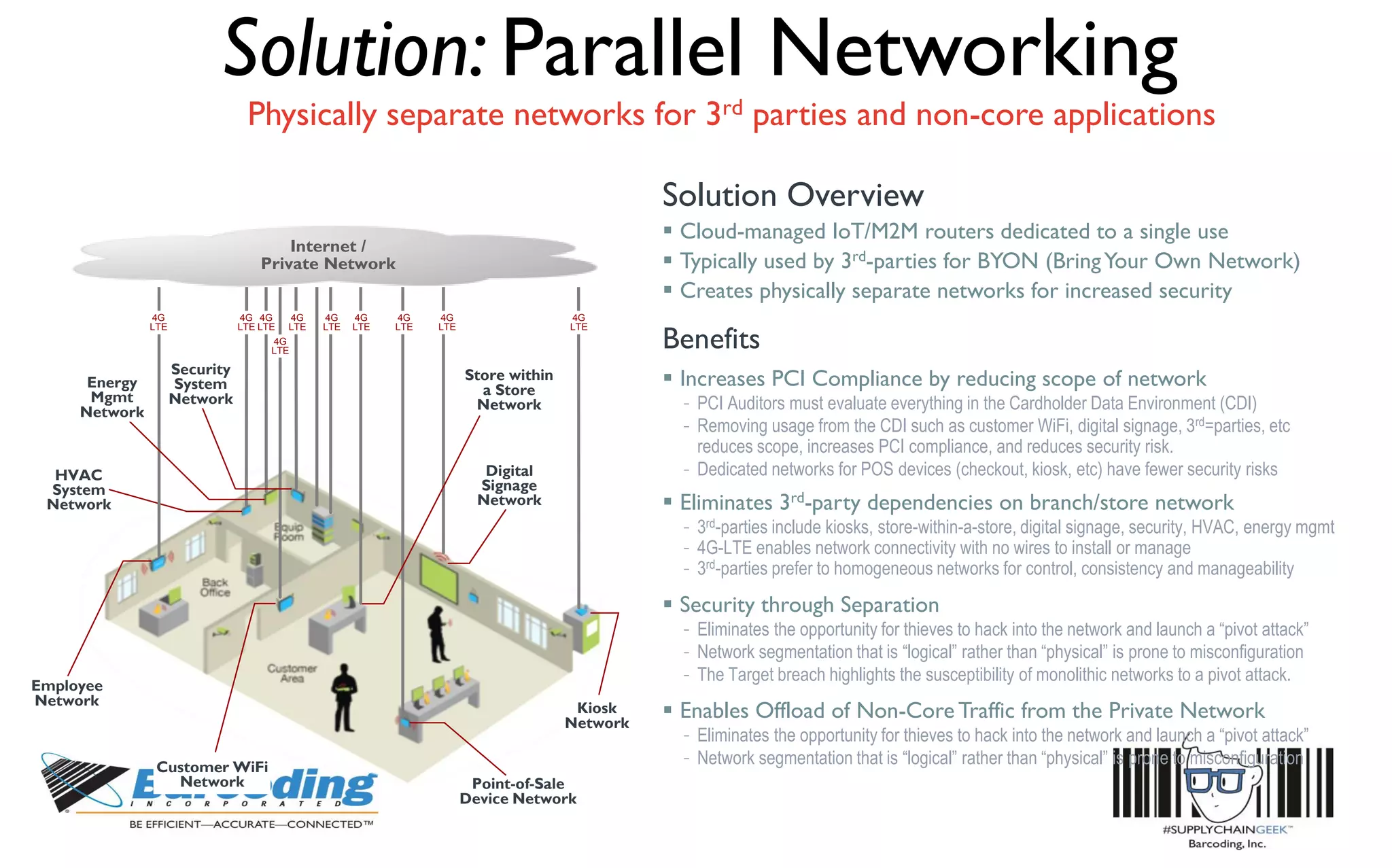
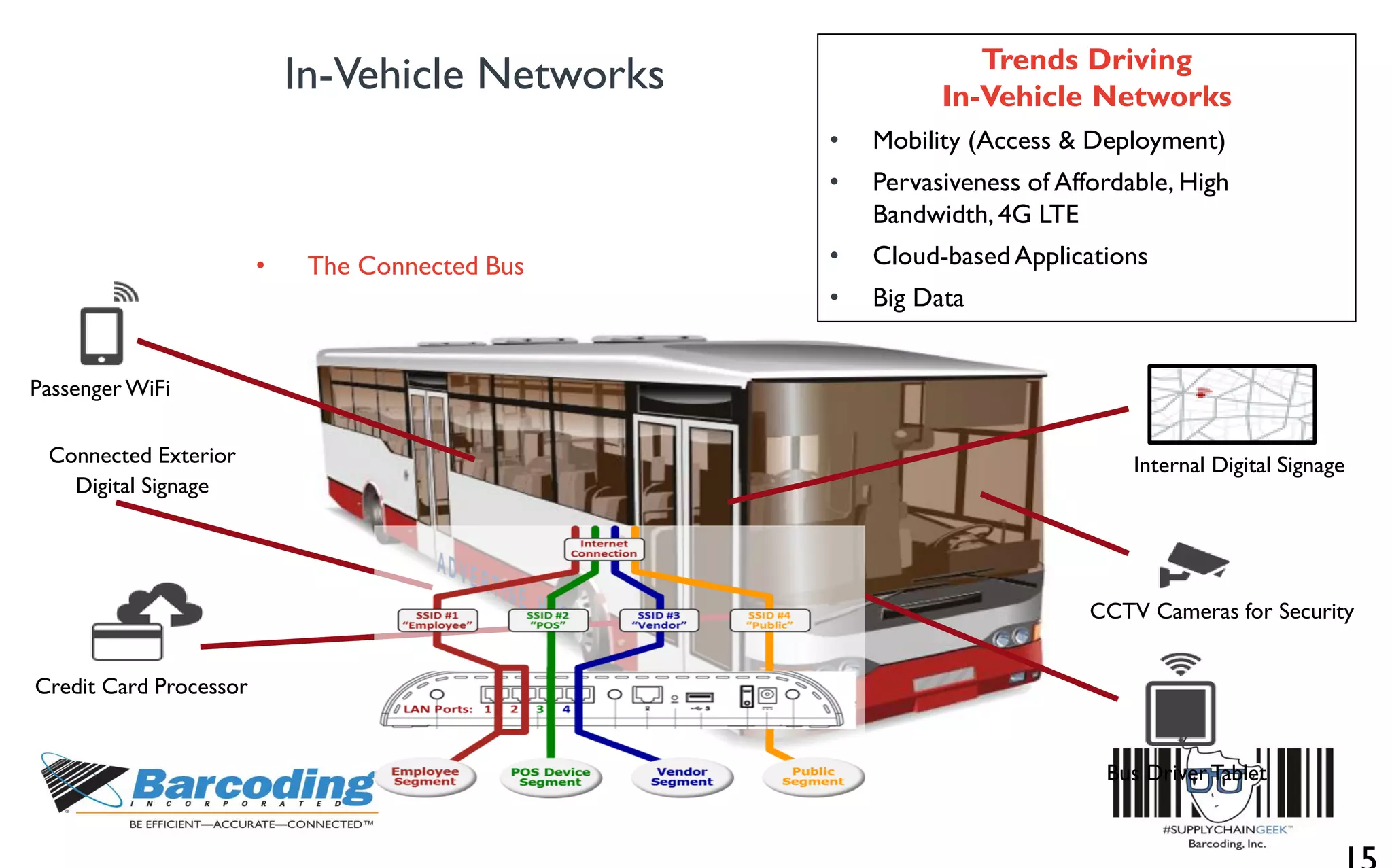
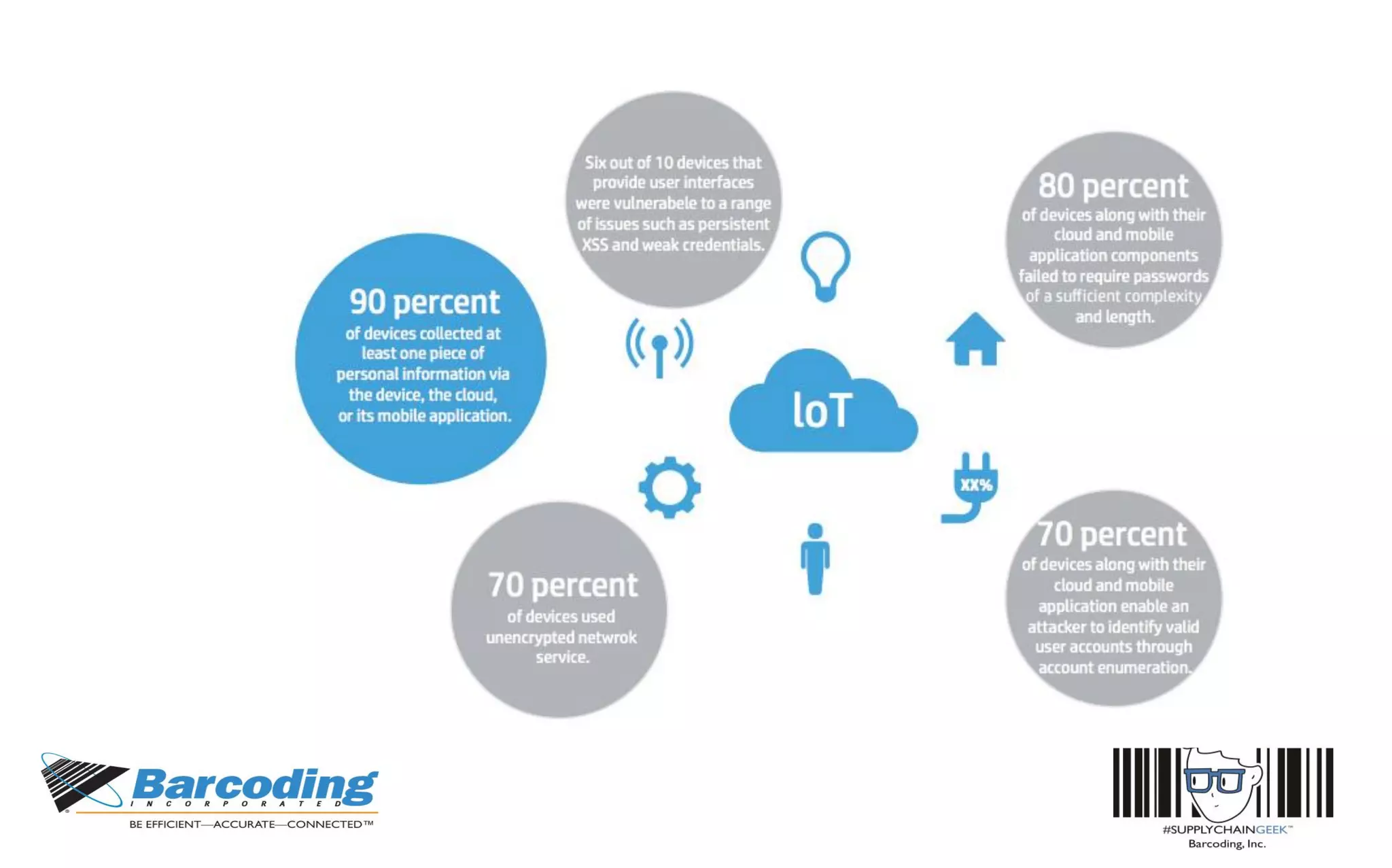
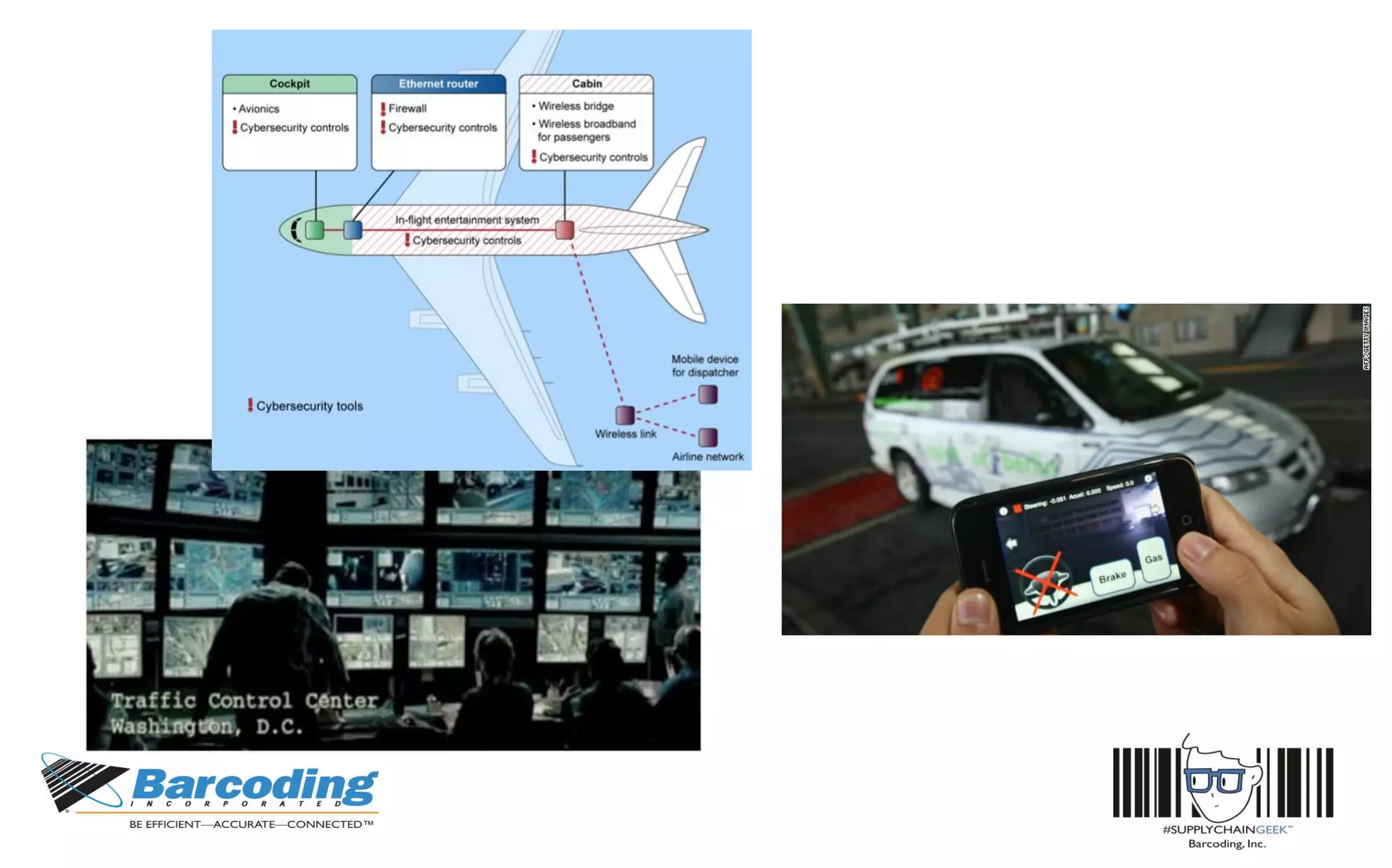
This document discusses the benefits of parallel networking and network segmentation for IoT devices. It describes how traditionally networks are monolithic with everything connected, but this poses security risks. The solution proposed is to use separate, dedicated networks for different systems like POS, customer WiFi, digital signage, HVAC etc. This physically segments the networks for increased security. The benefits are improved PCI compliance by reducing the scope of networks auditors need to assess, and eliminating opportunities for hackers to pivot from one network to another. It gives an example of how network segmentation could have prevented the Target data breach.