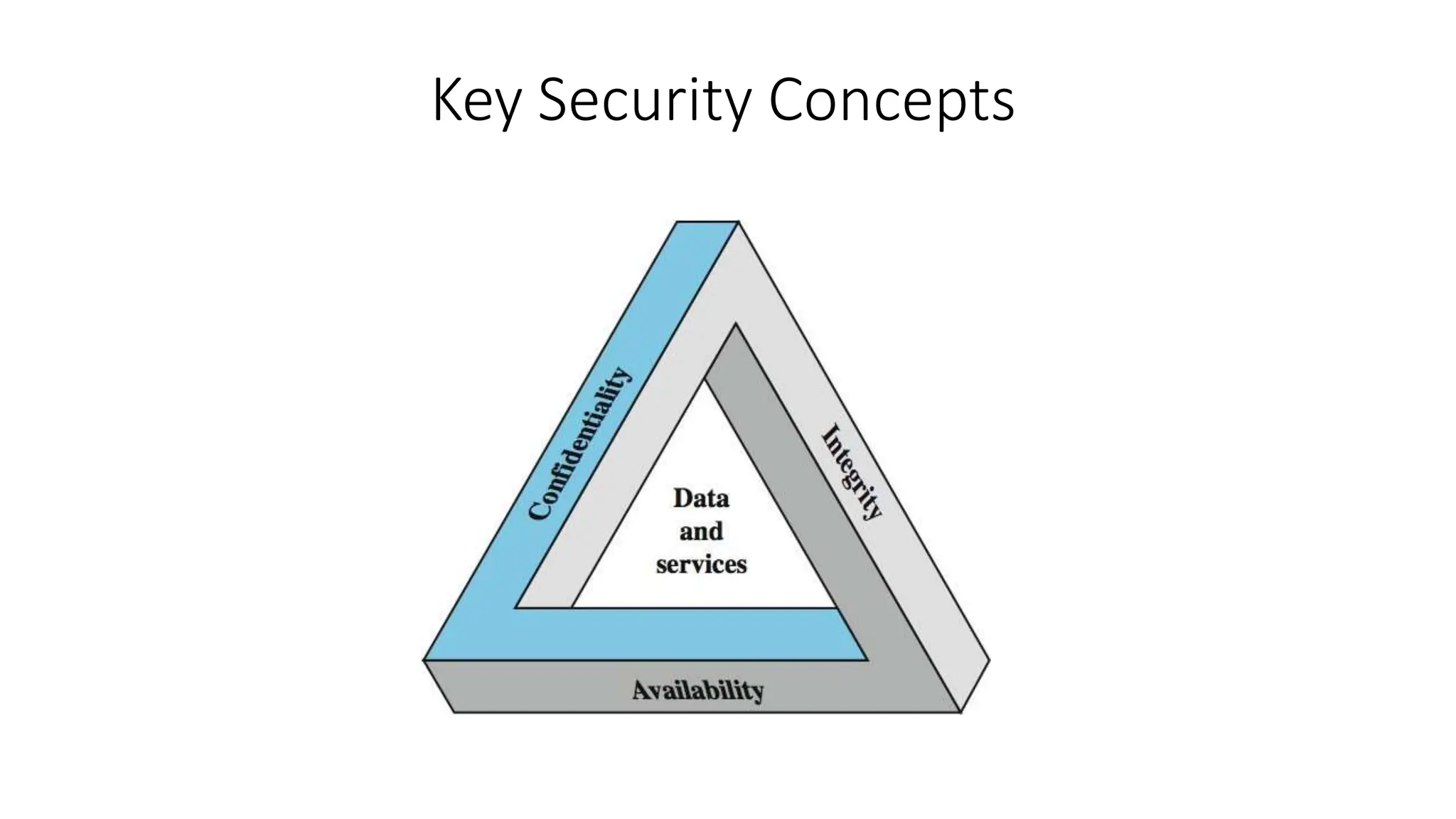
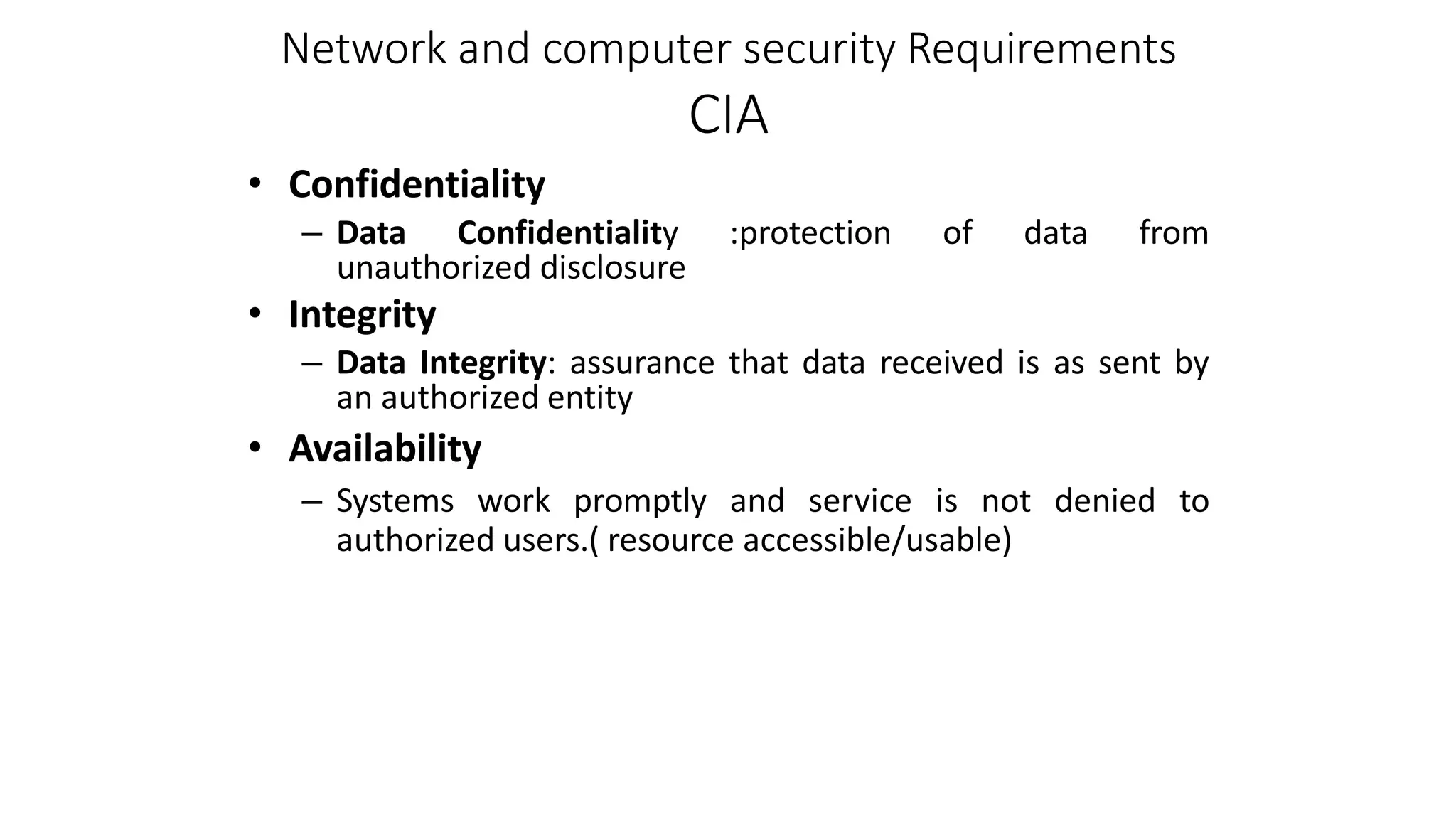
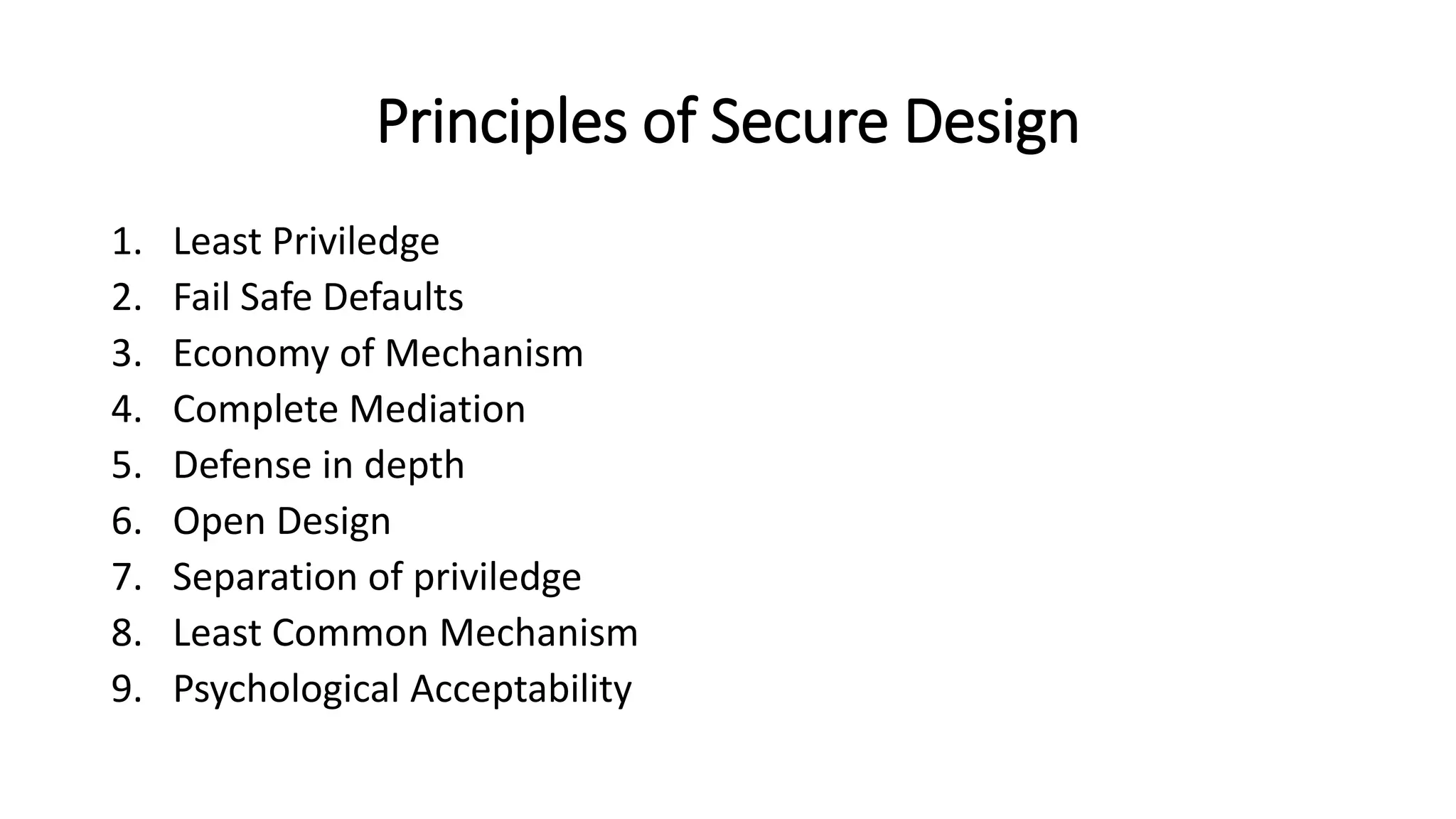
This document provides an introduction to computer security concepts. It discusses how computer security aims to protect hardware, software, data, users and information from unauthorized access and use. The key concepts of confidentiality, integrity and availability (CIA) are explained. Principles of secure design are outlined, including least privilege, fail-safe defaults, defense in depth, and separation of privilege. Computer security challenges like ensuring systems are not simple to attack and require regular monitoring are also covered.