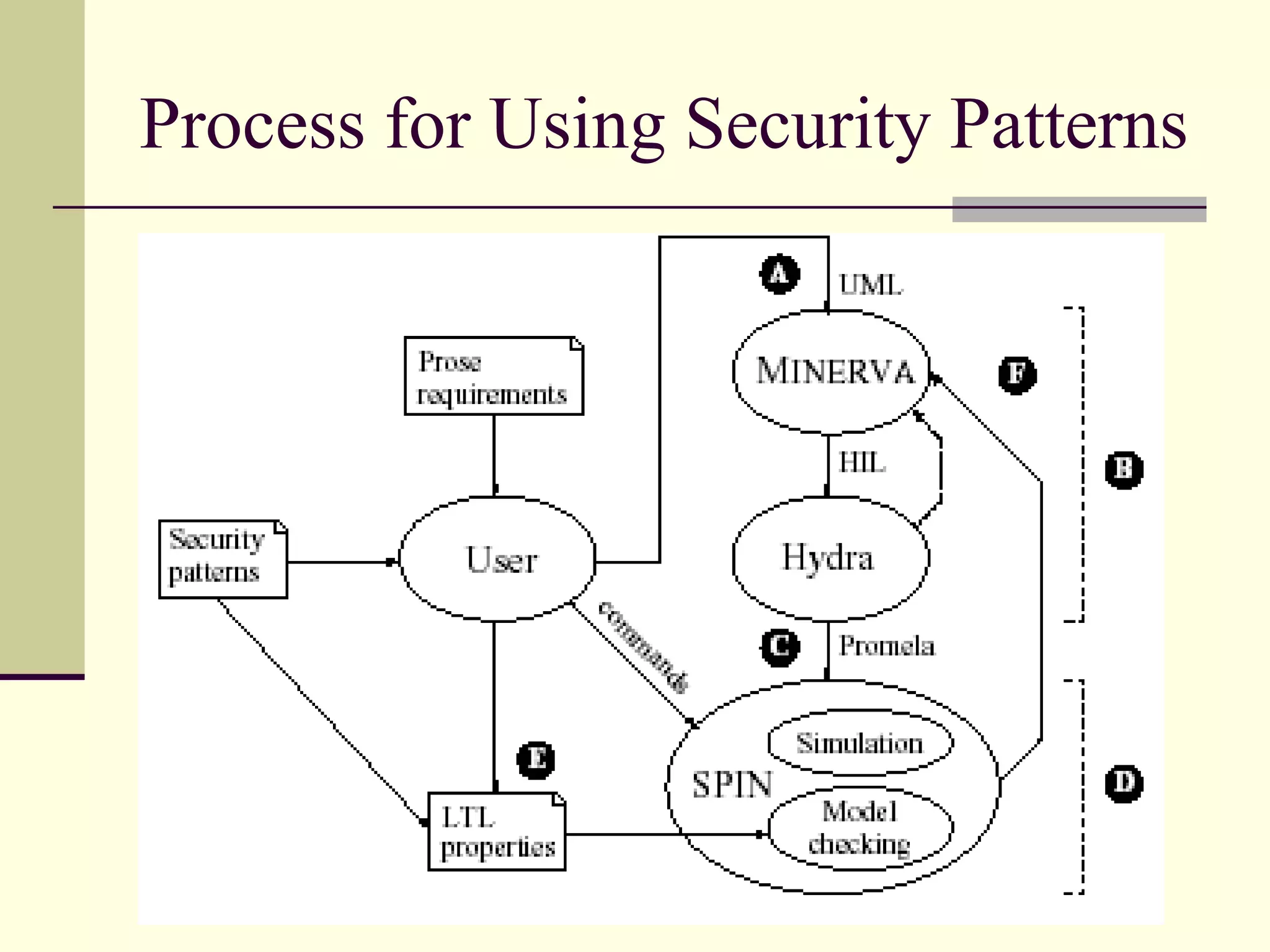
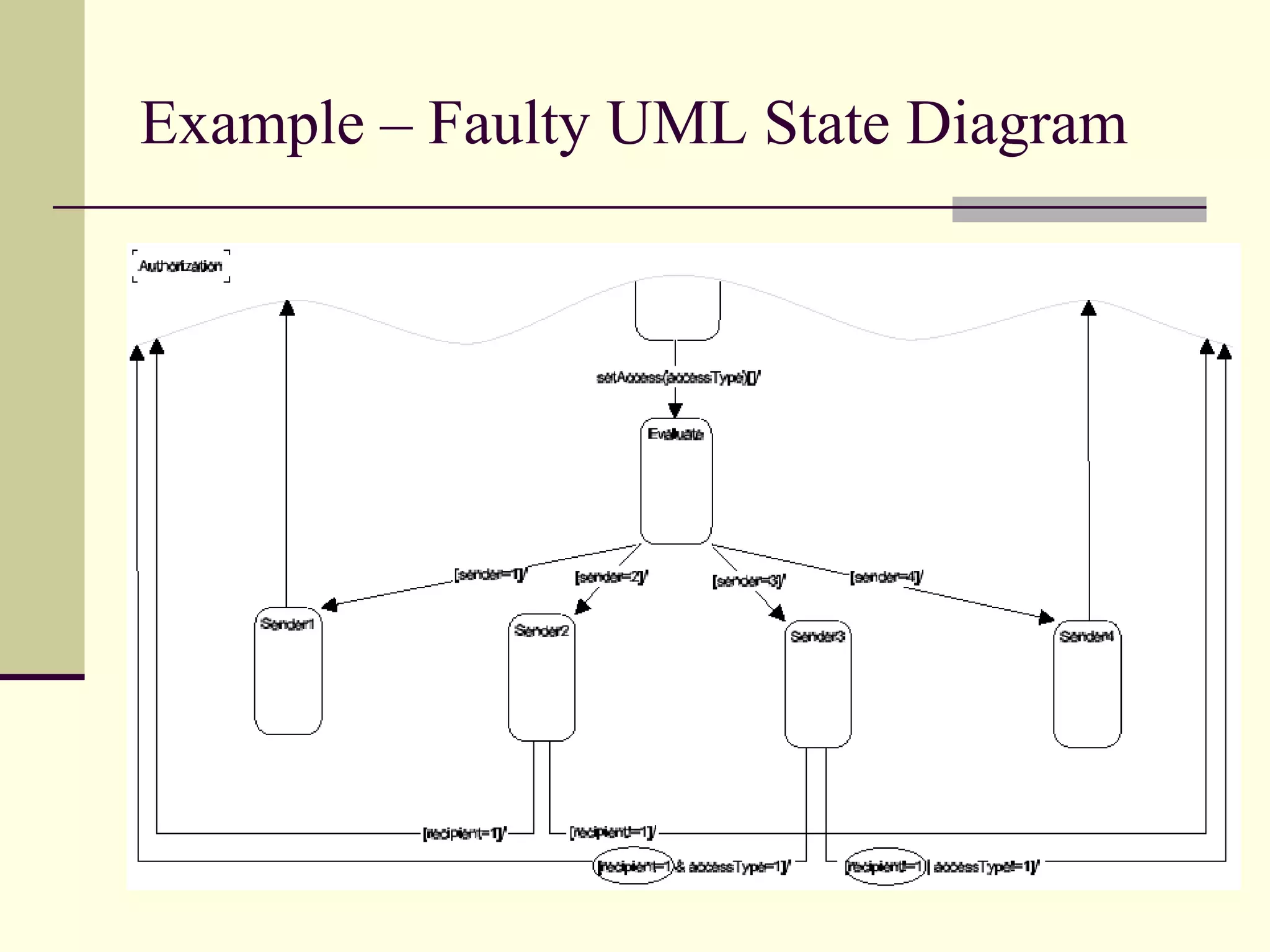
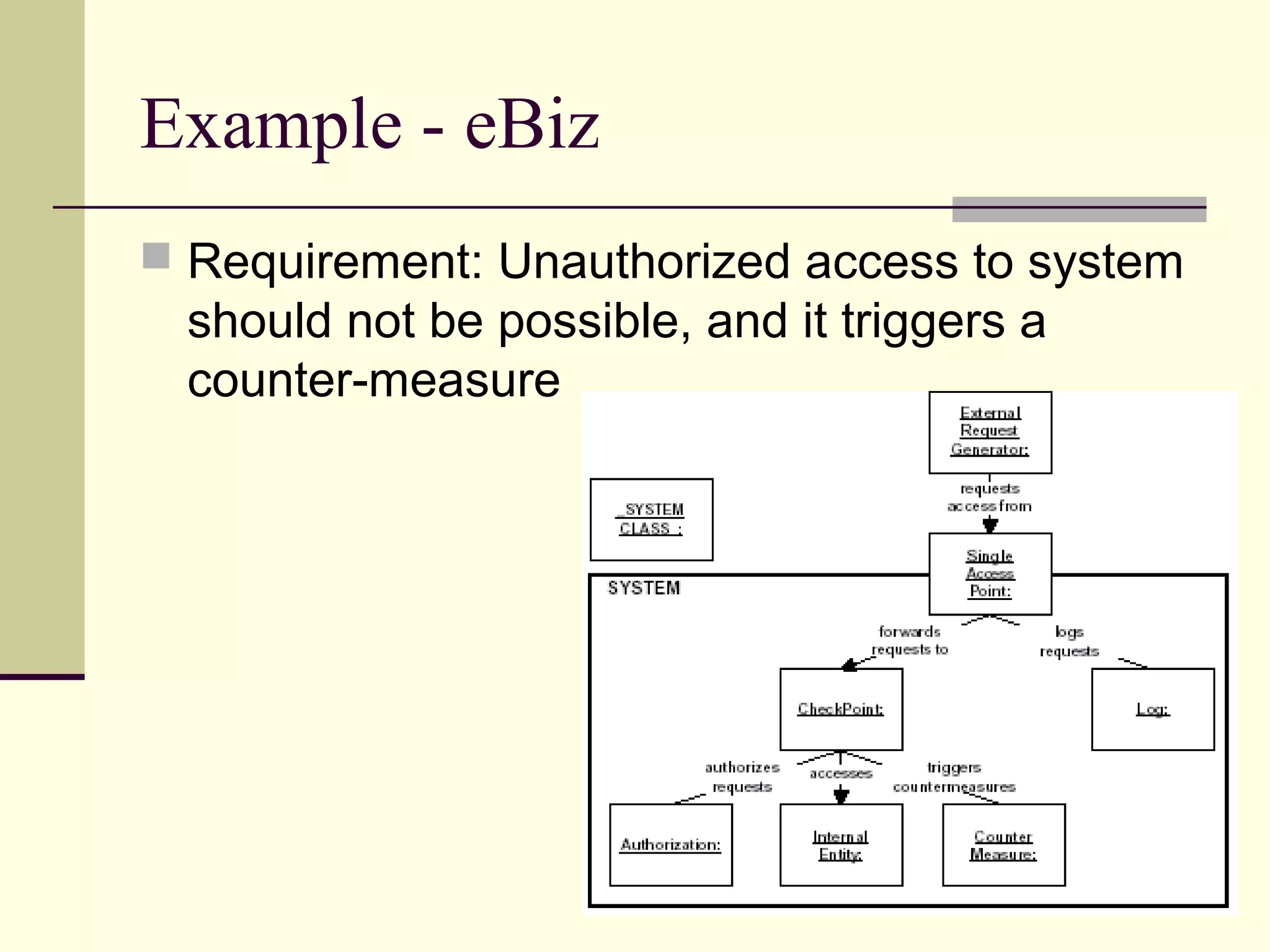
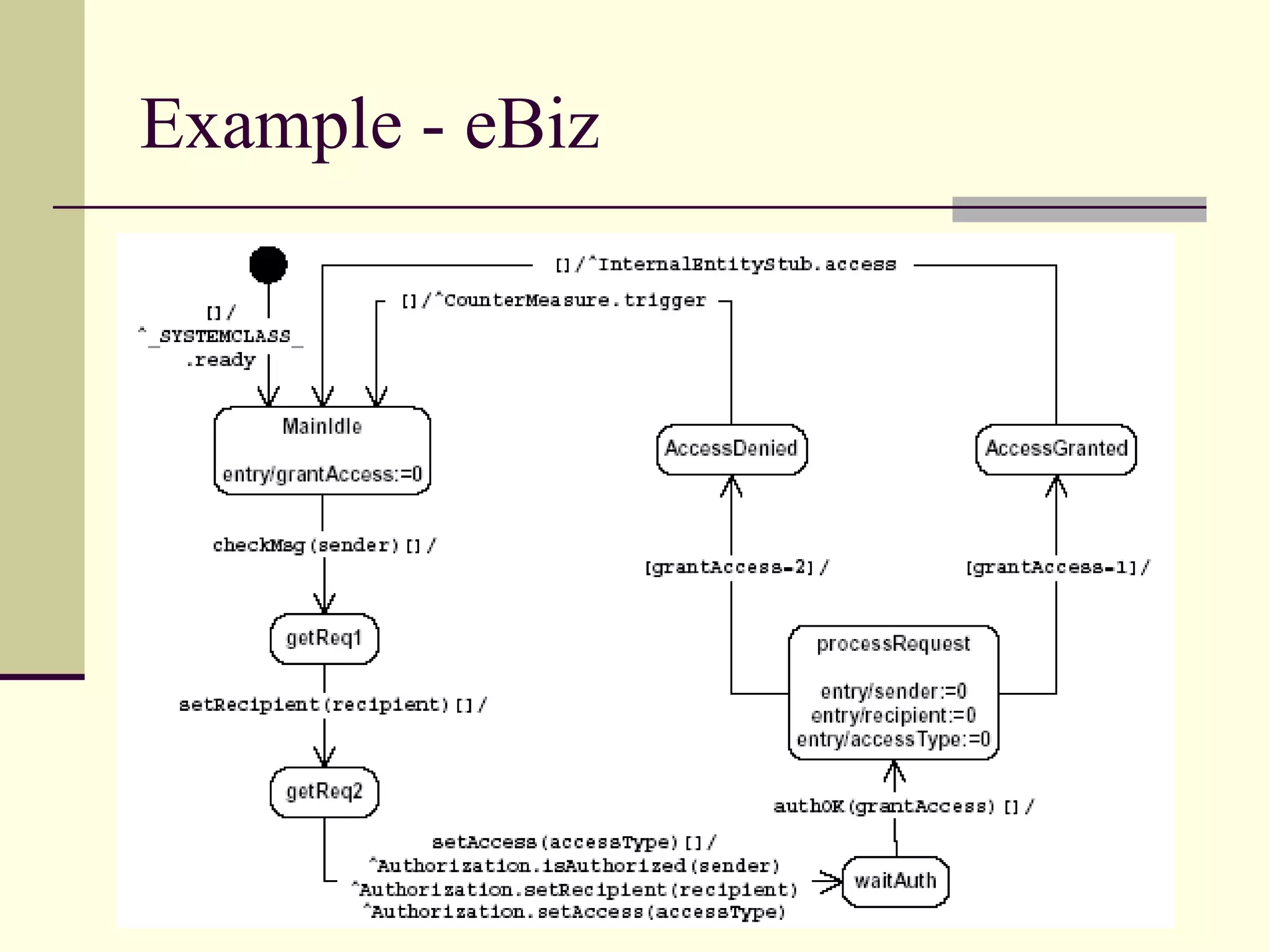
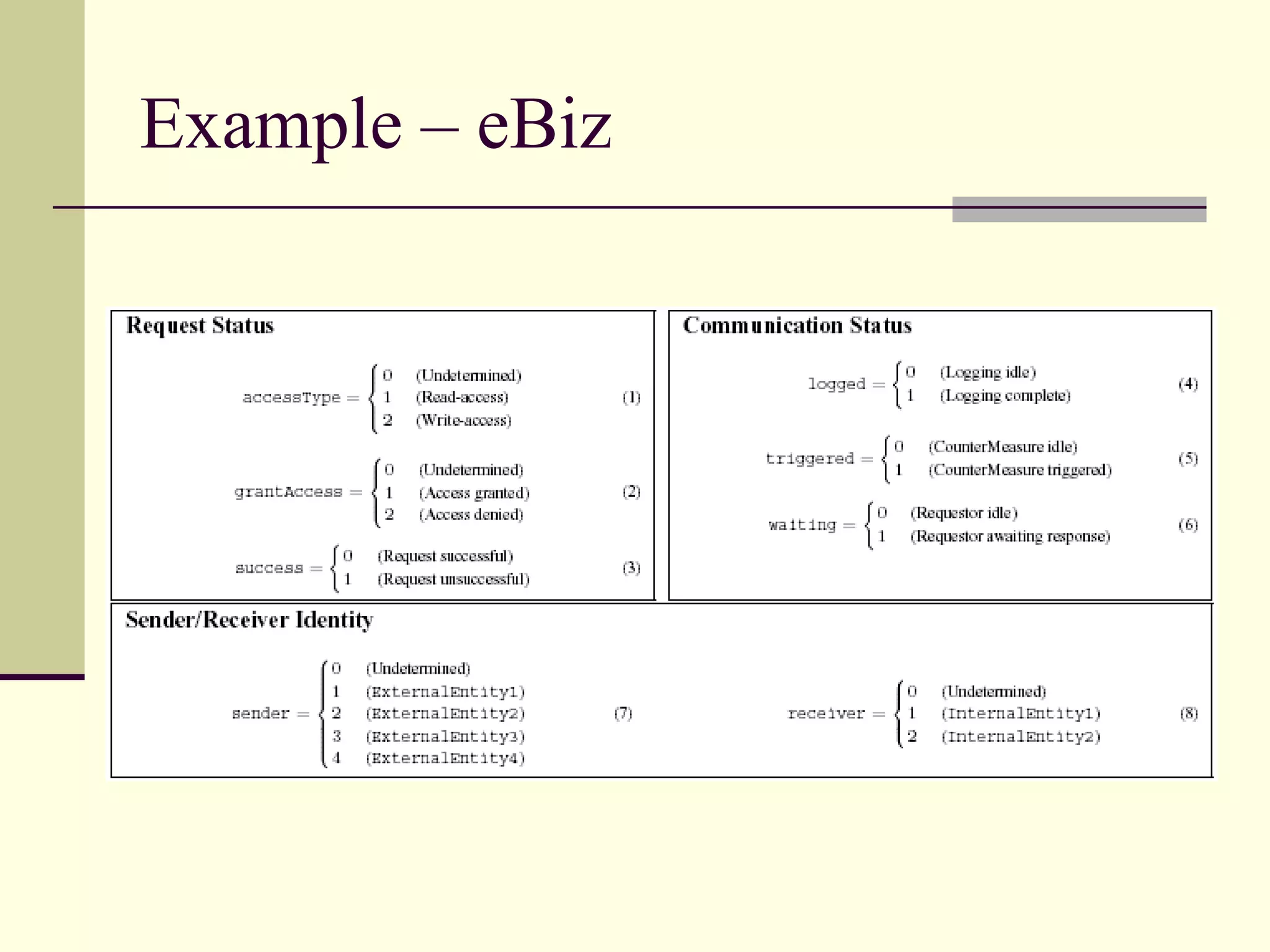
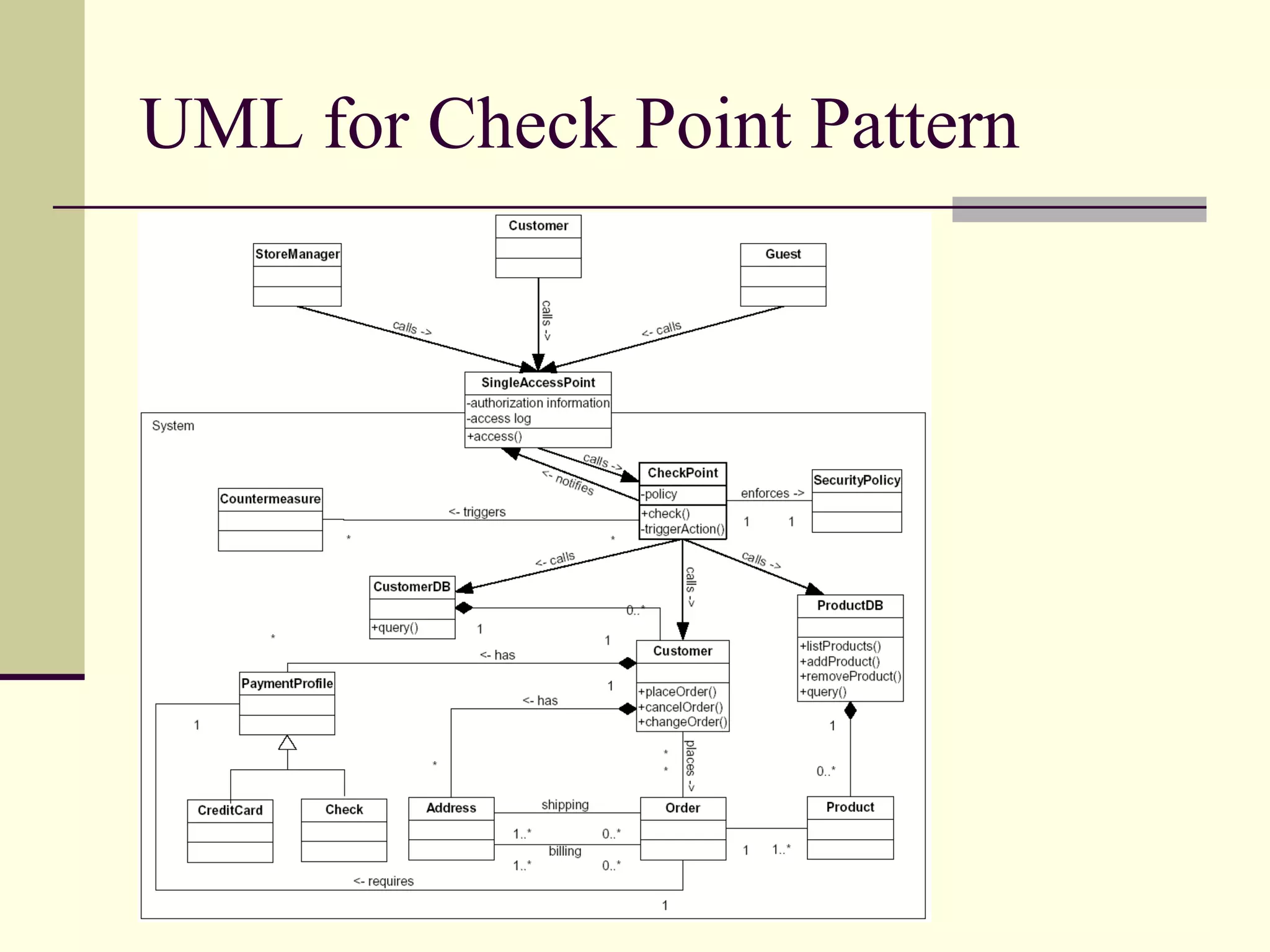
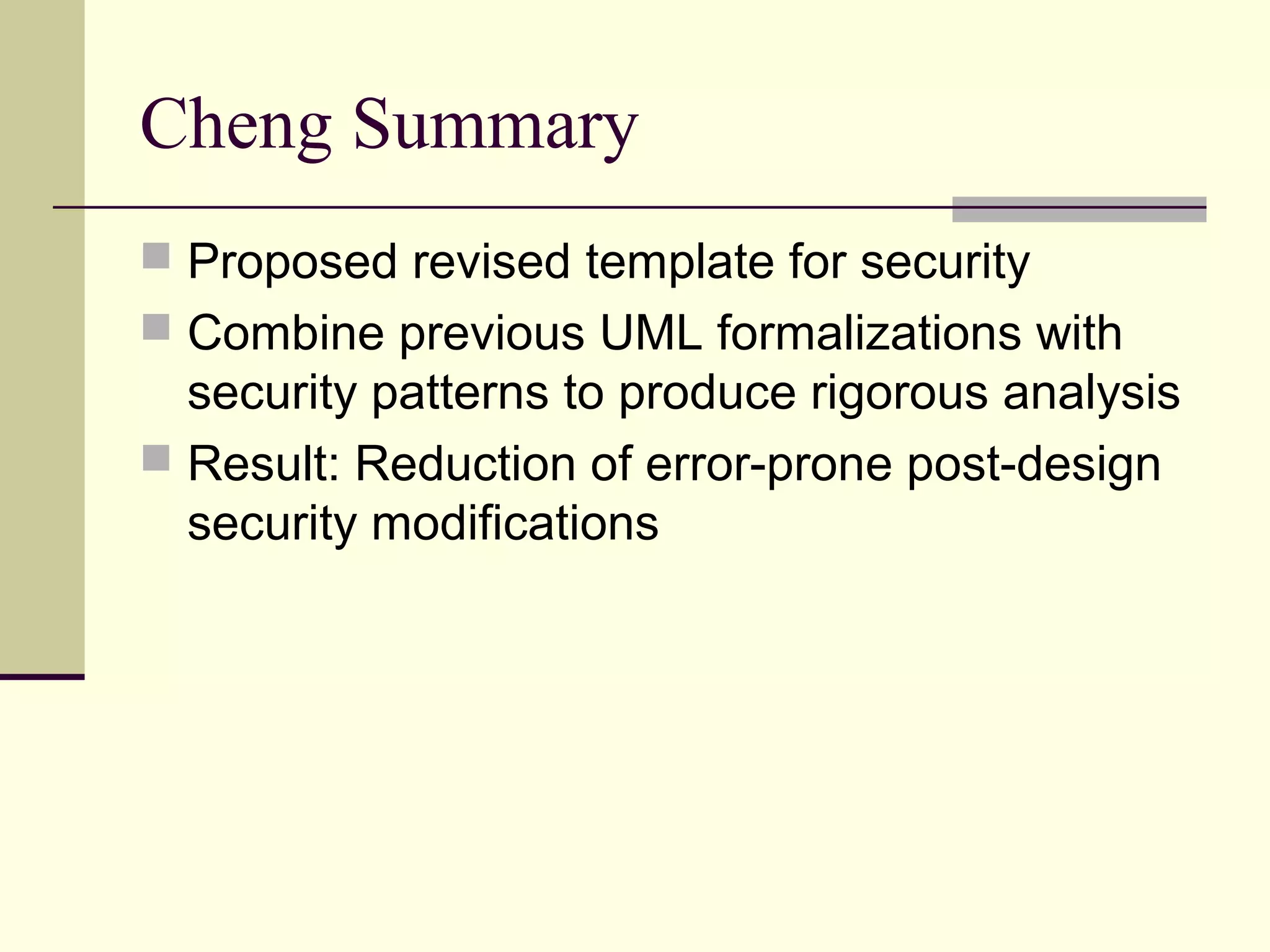
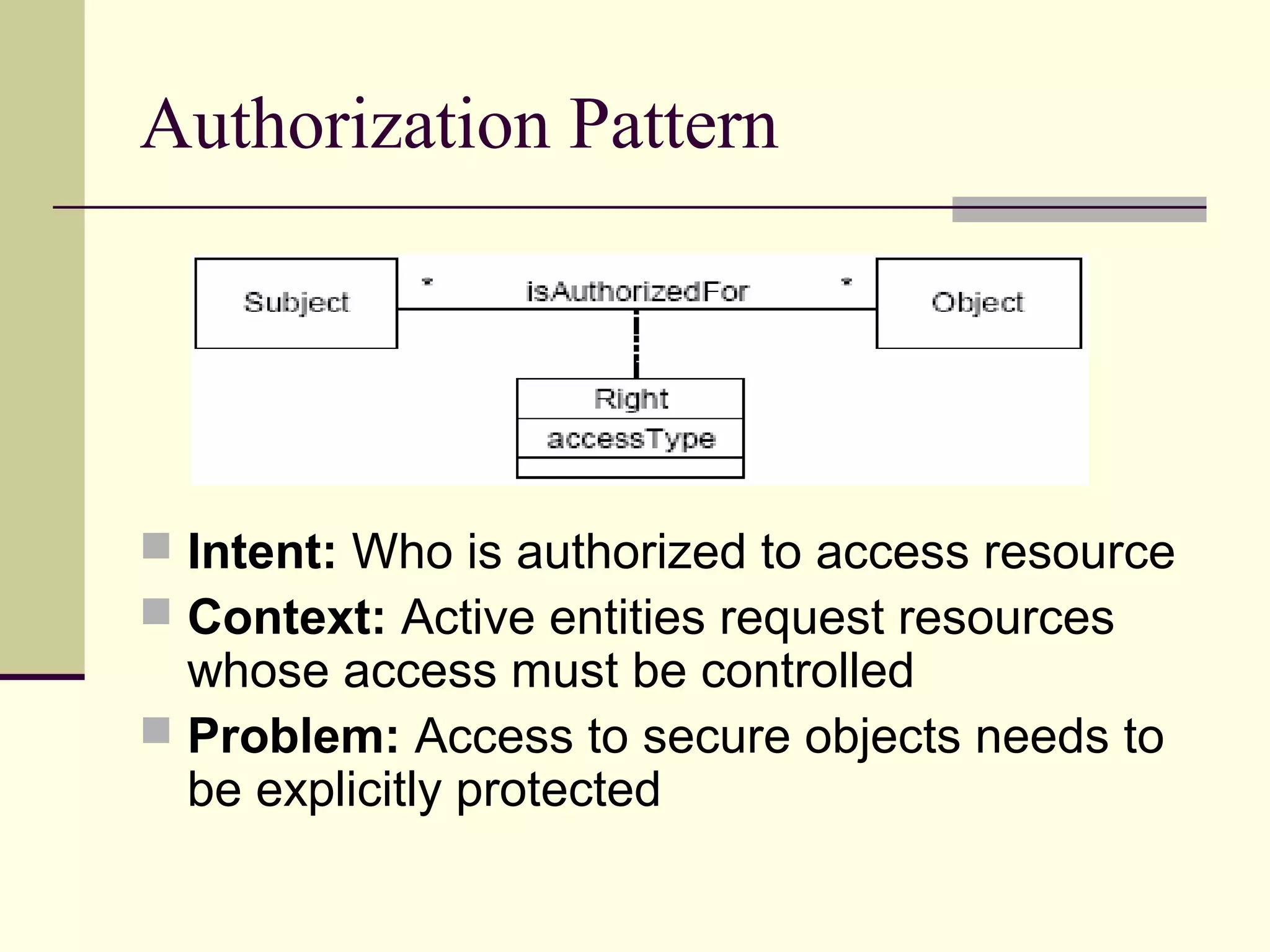
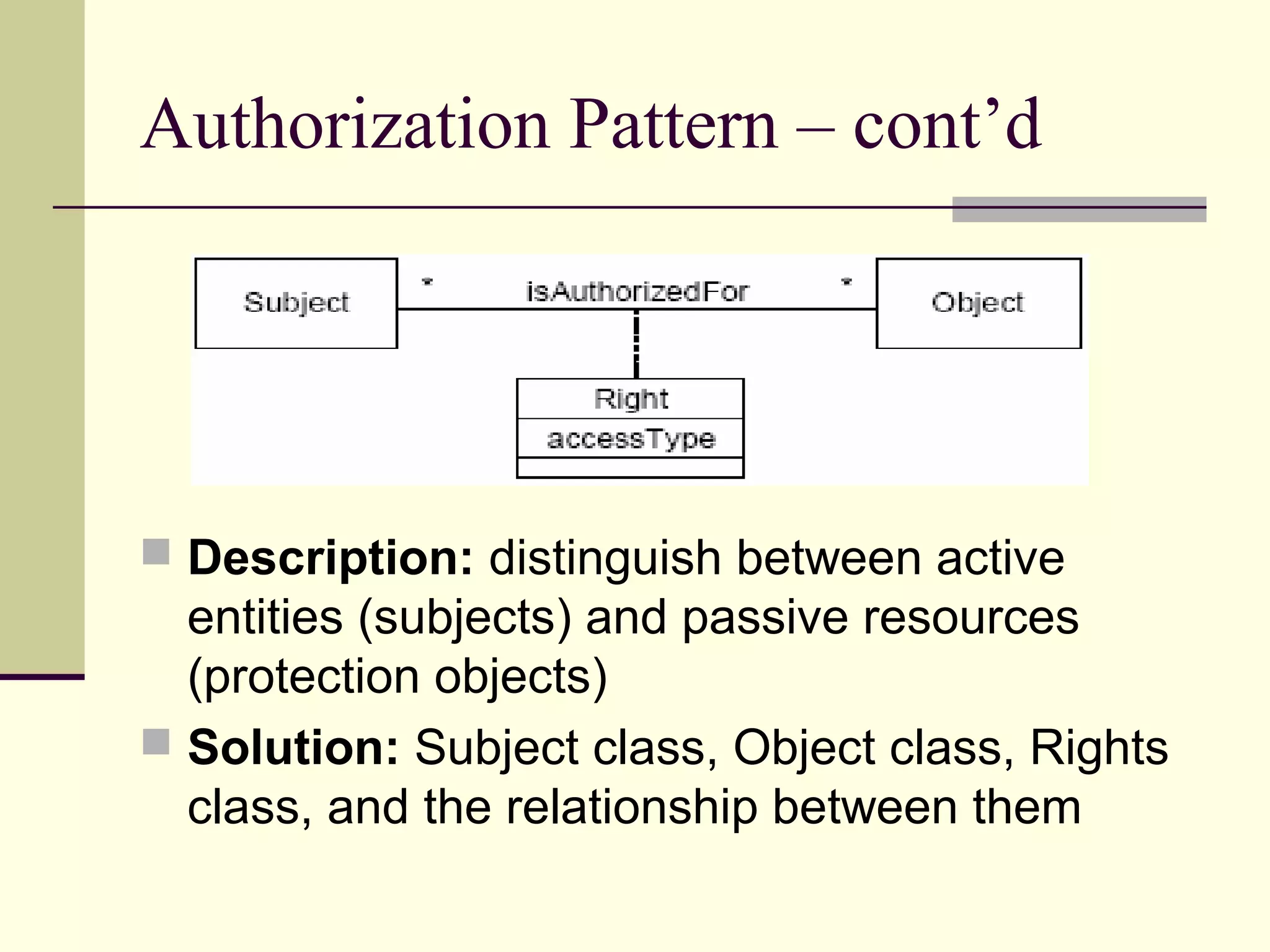
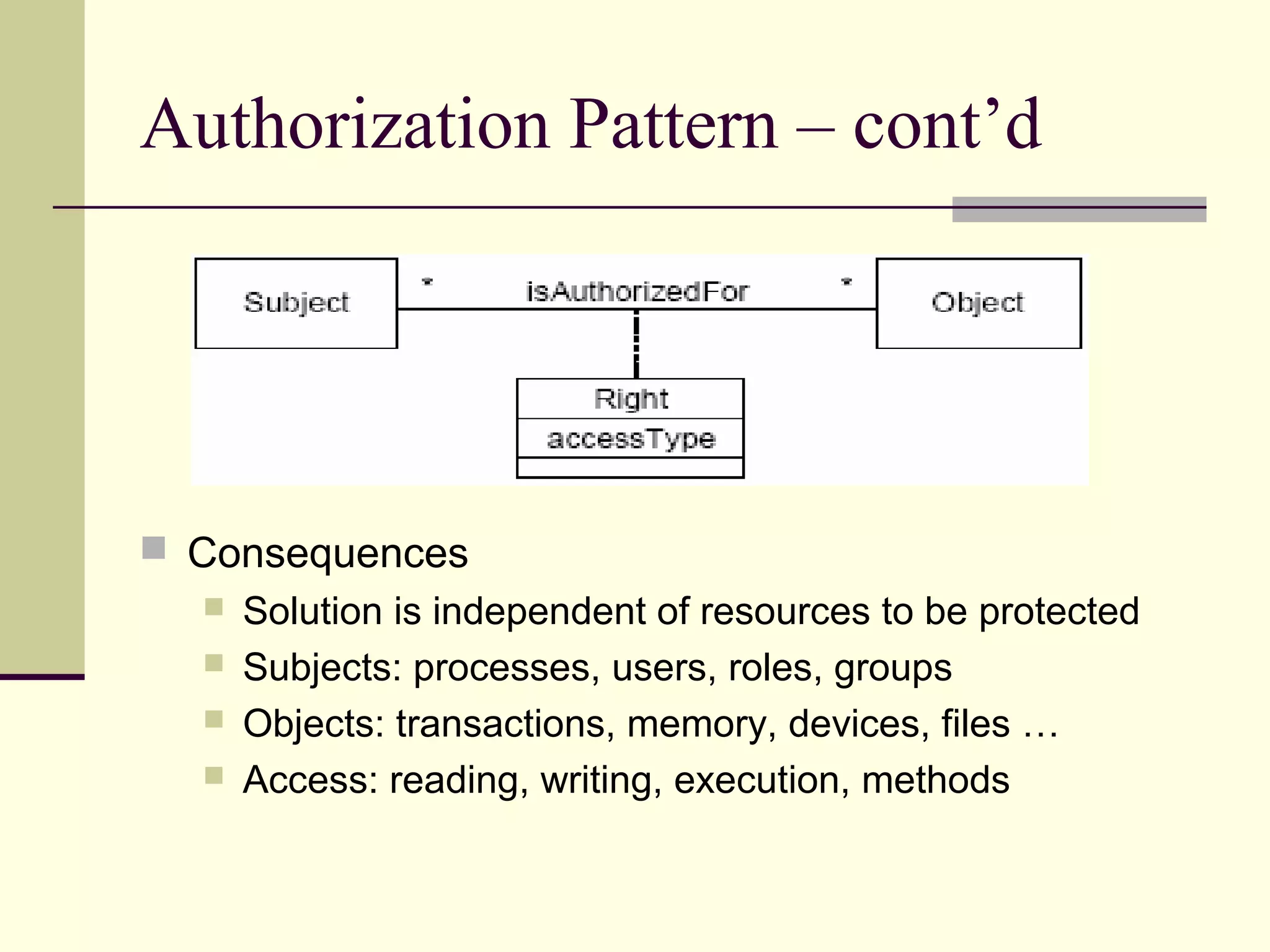
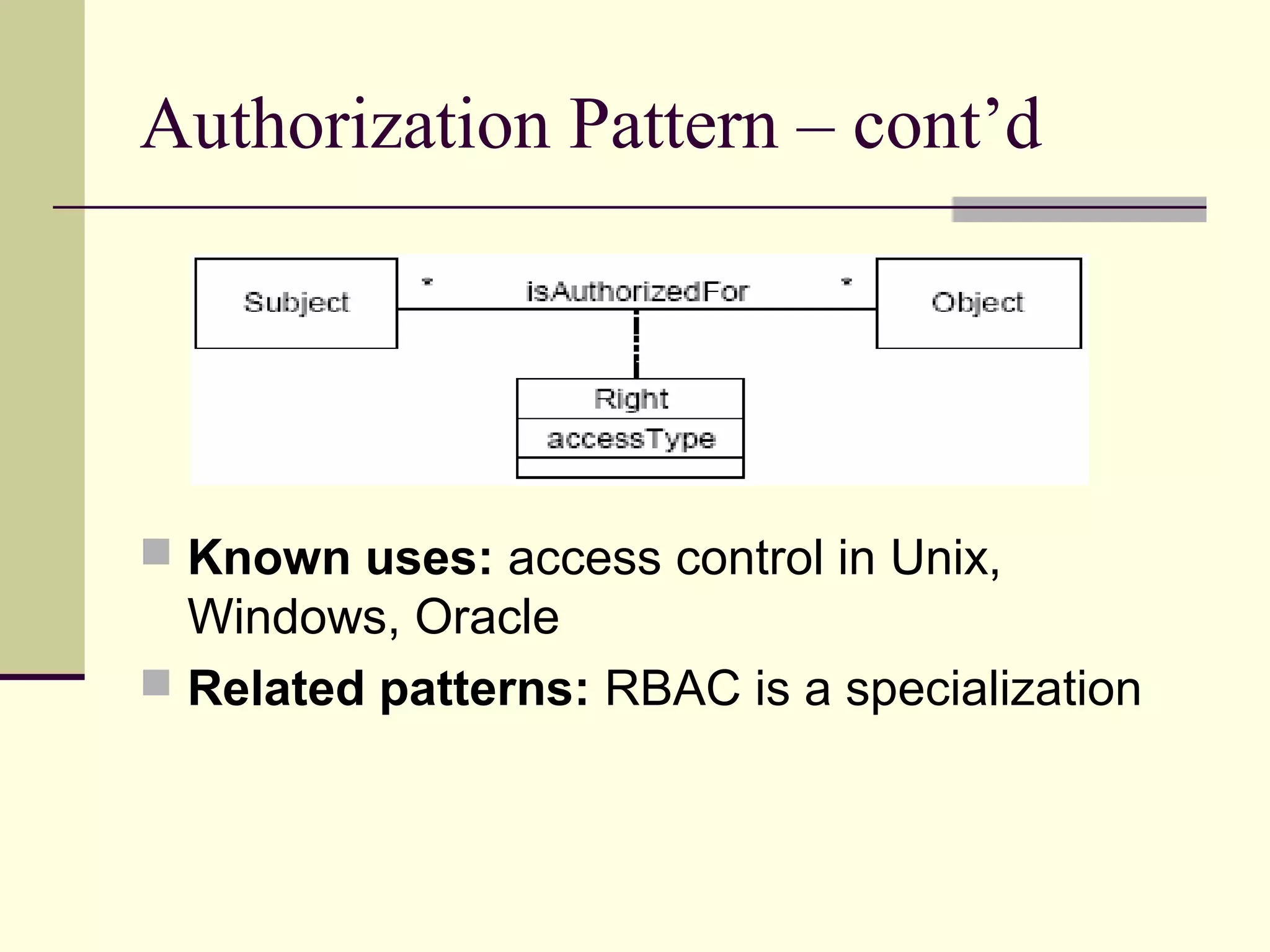
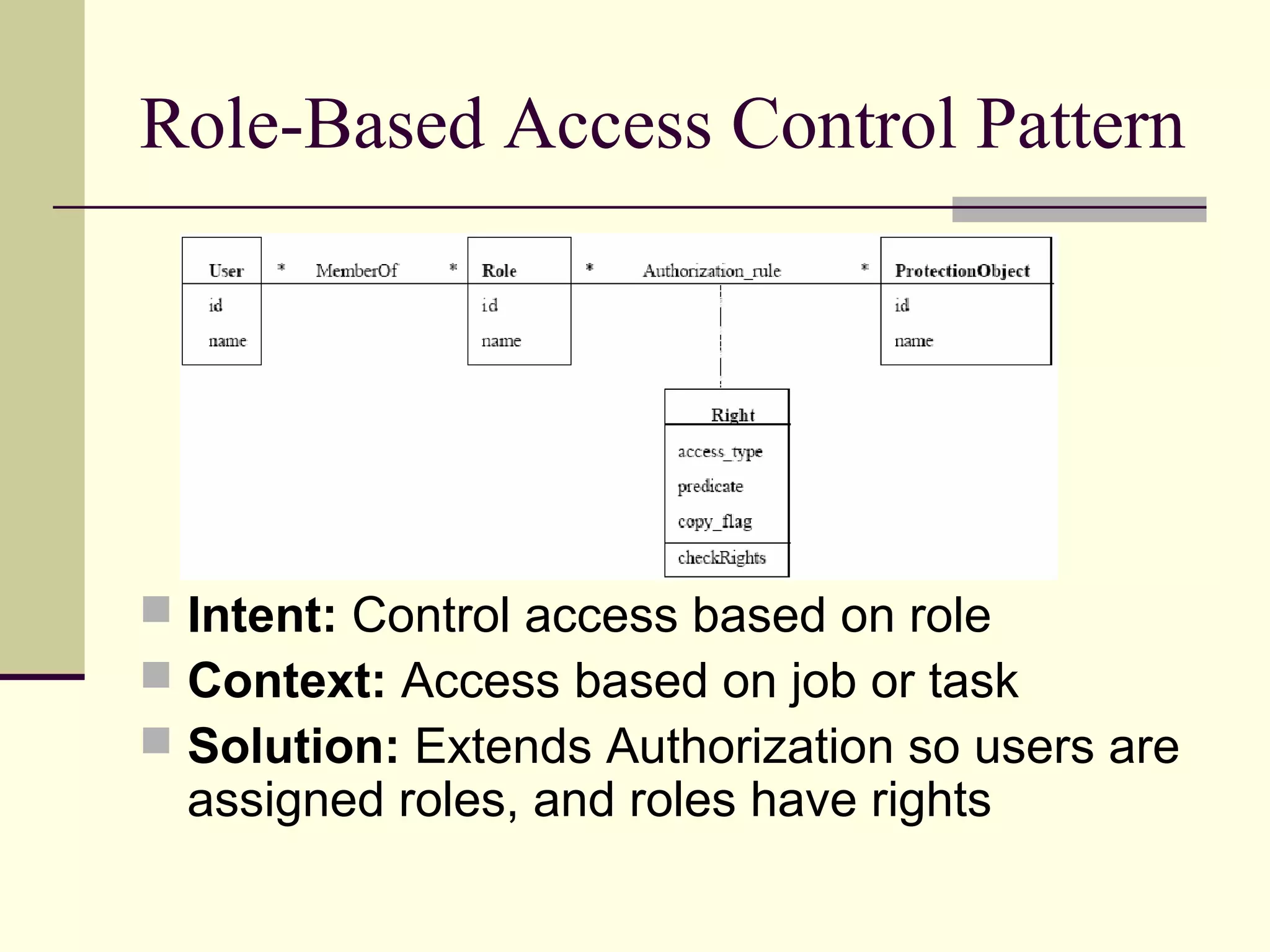
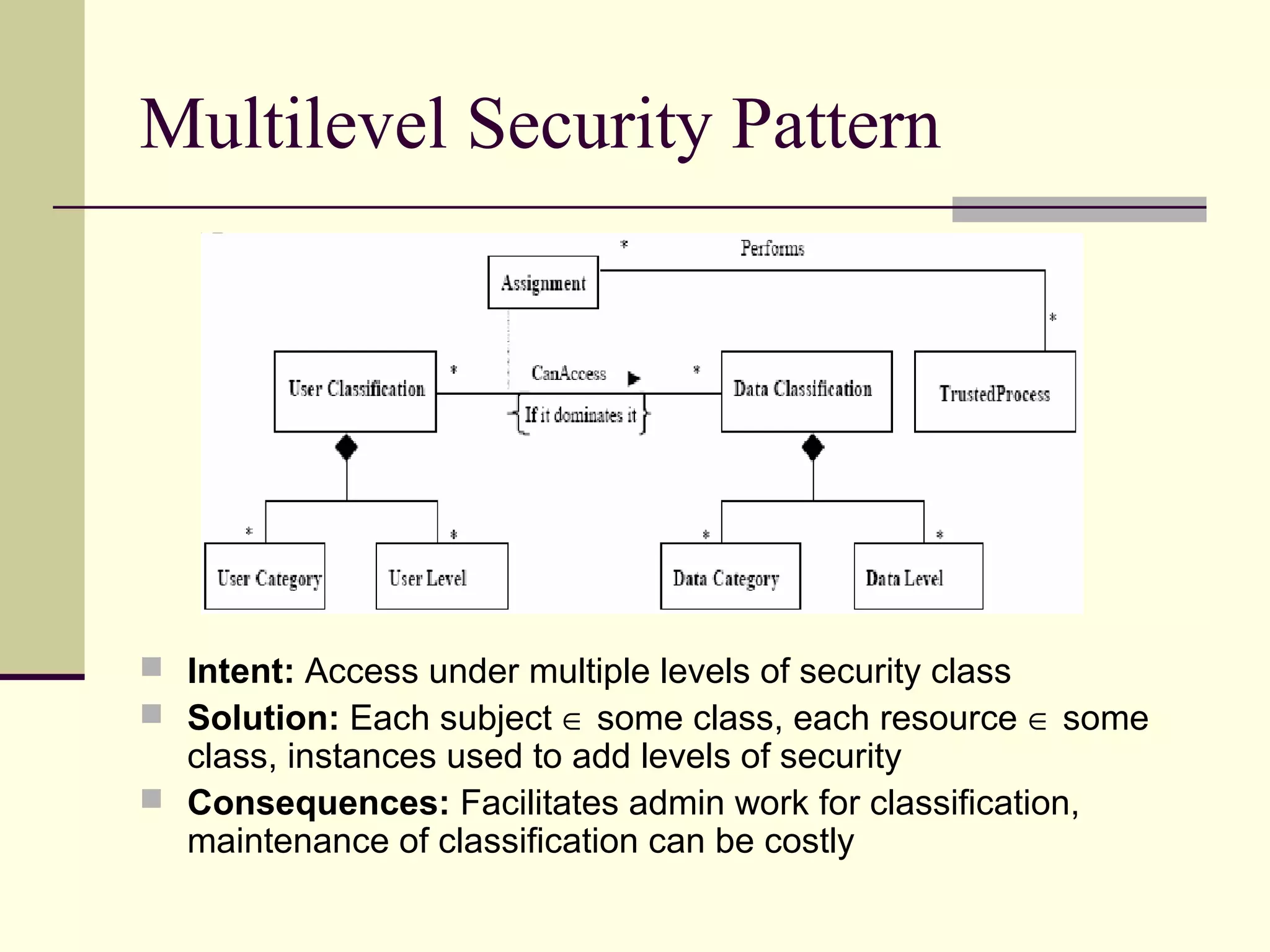
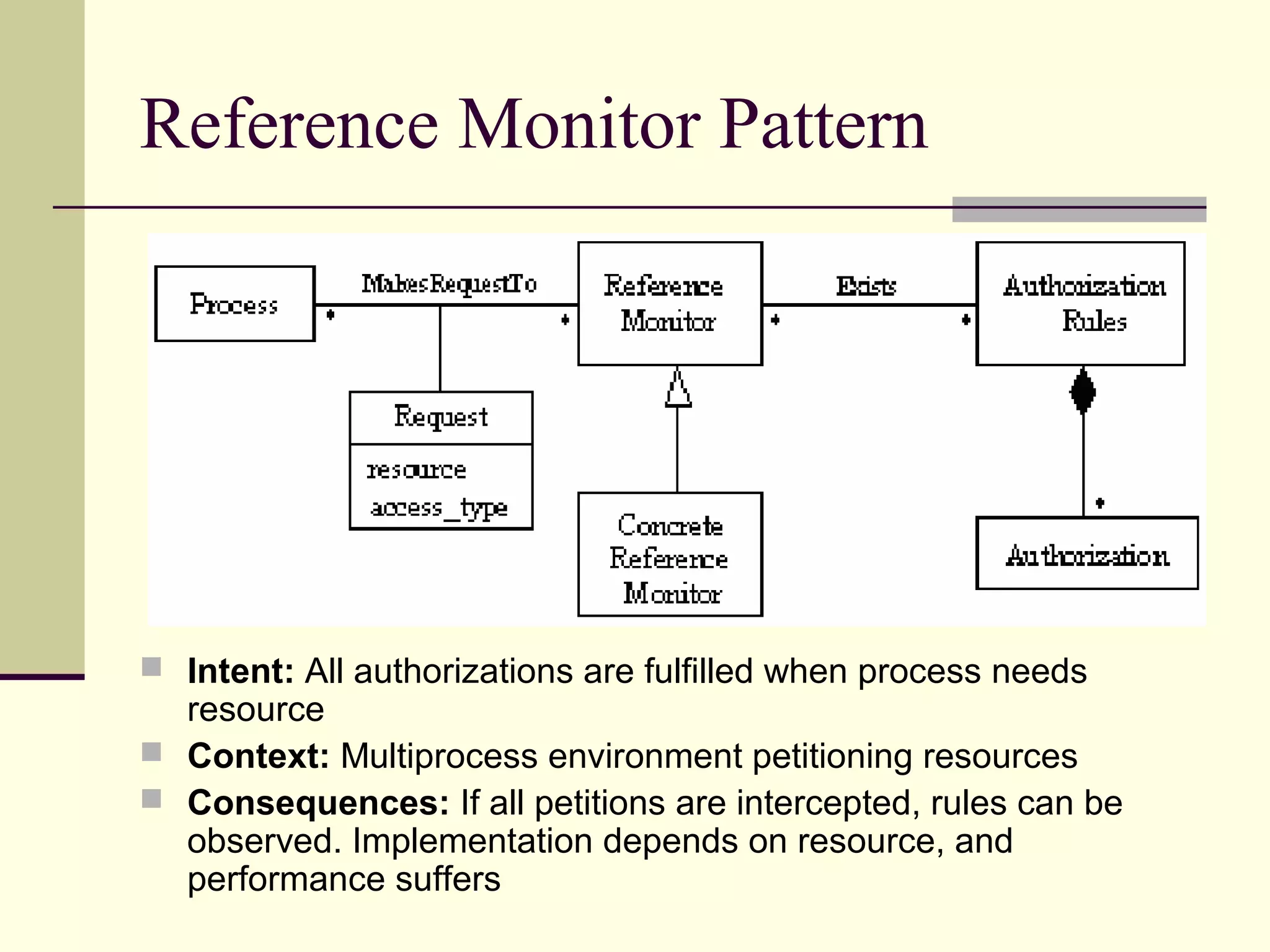
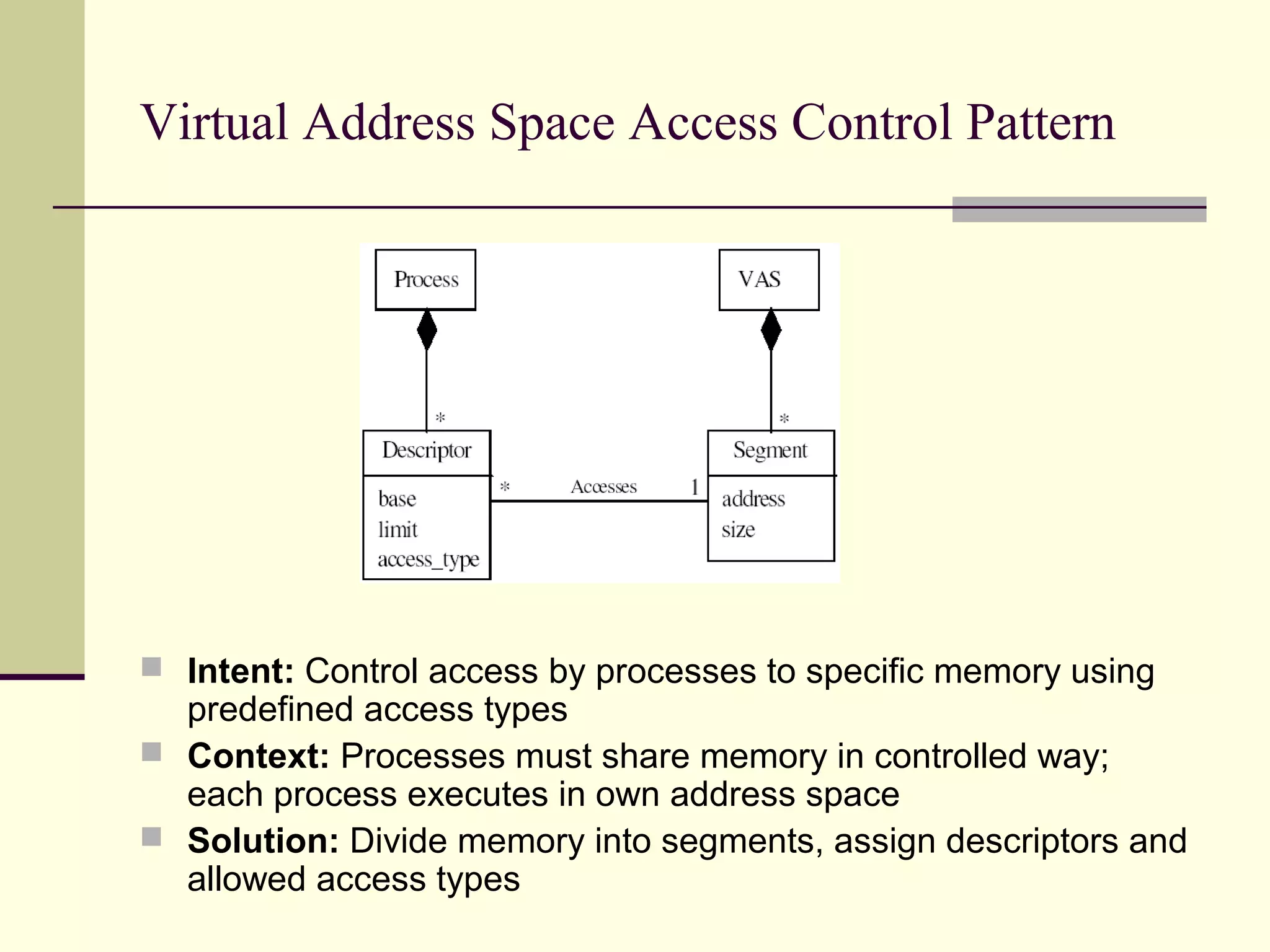
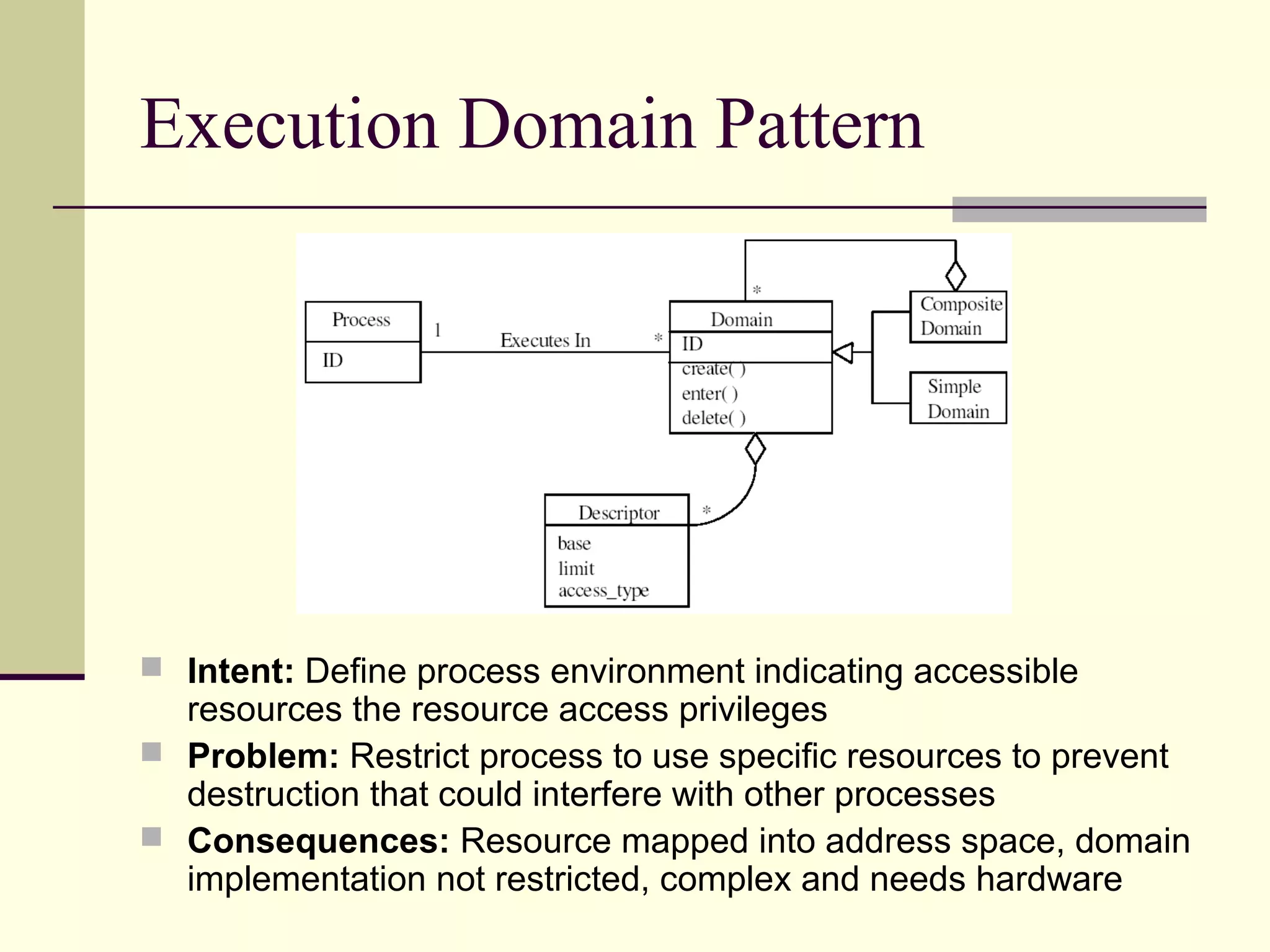
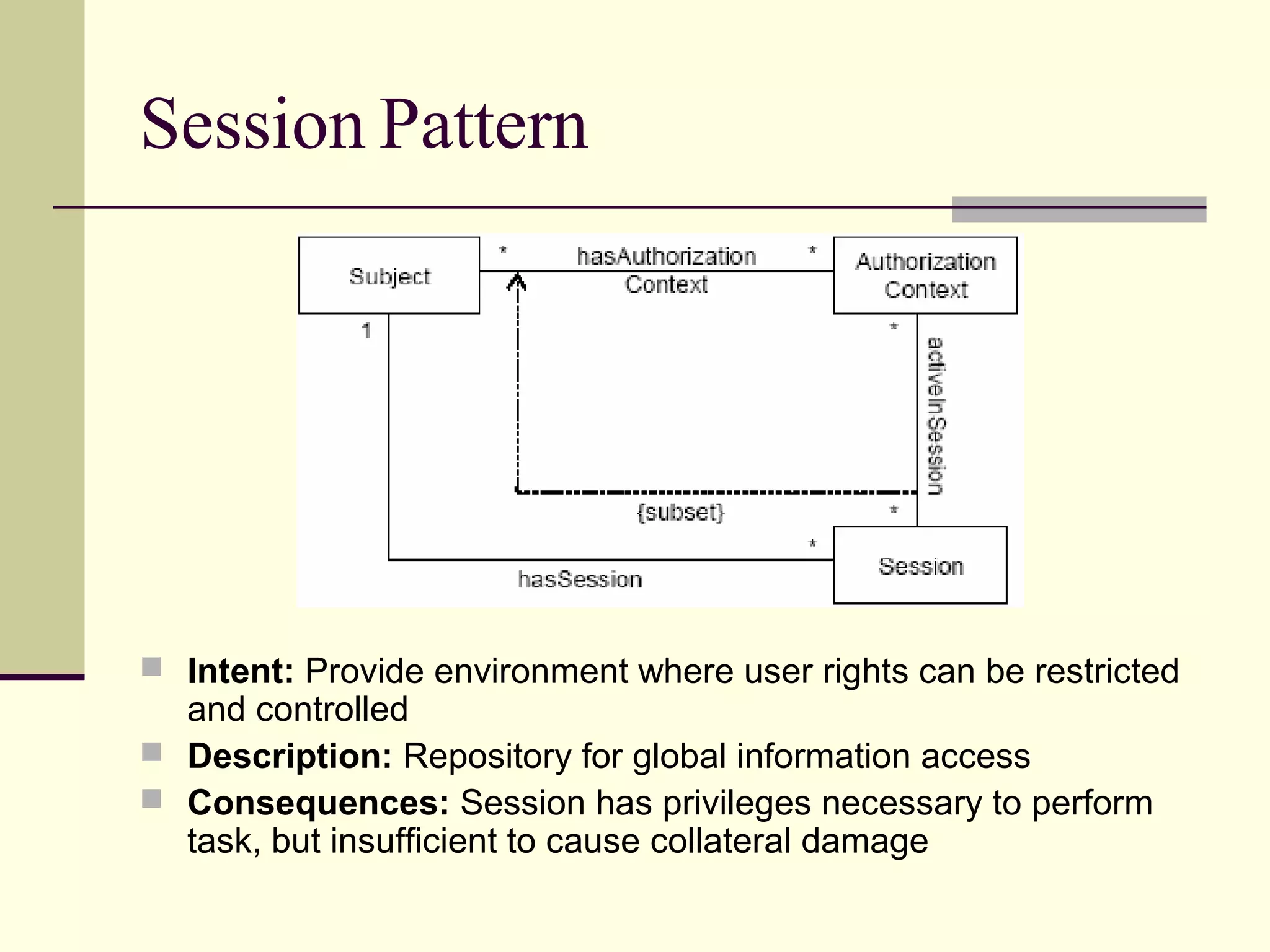
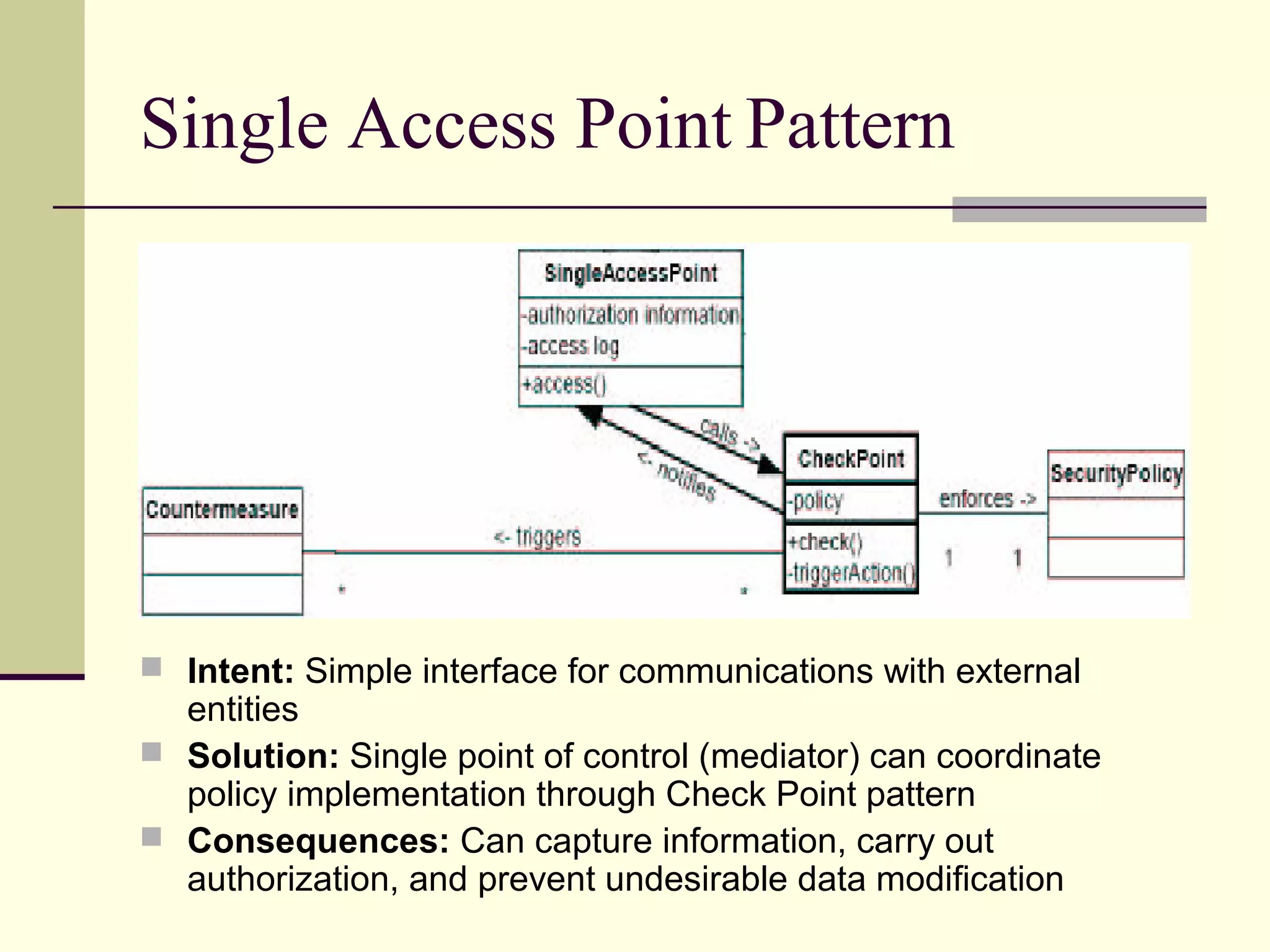
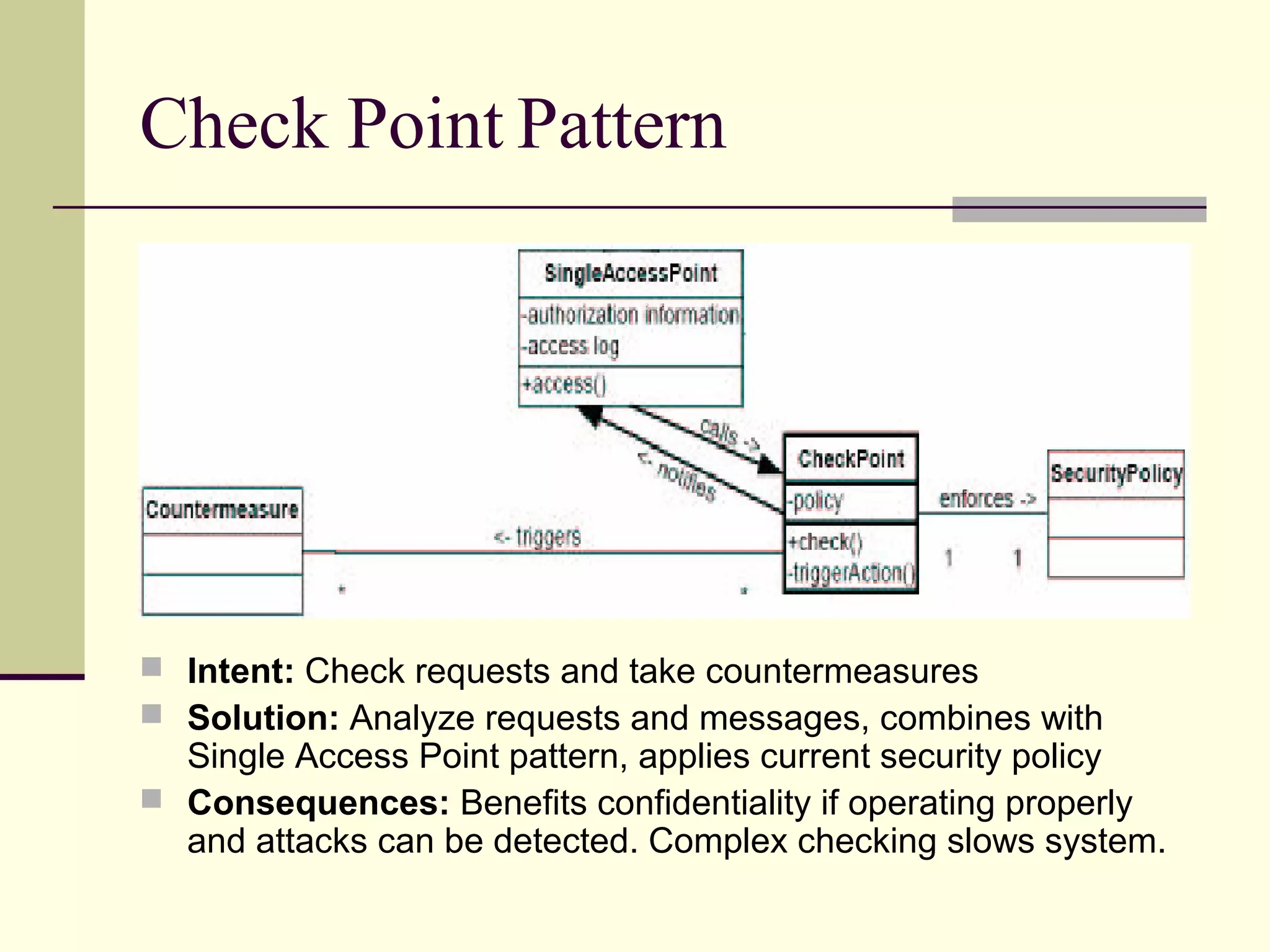
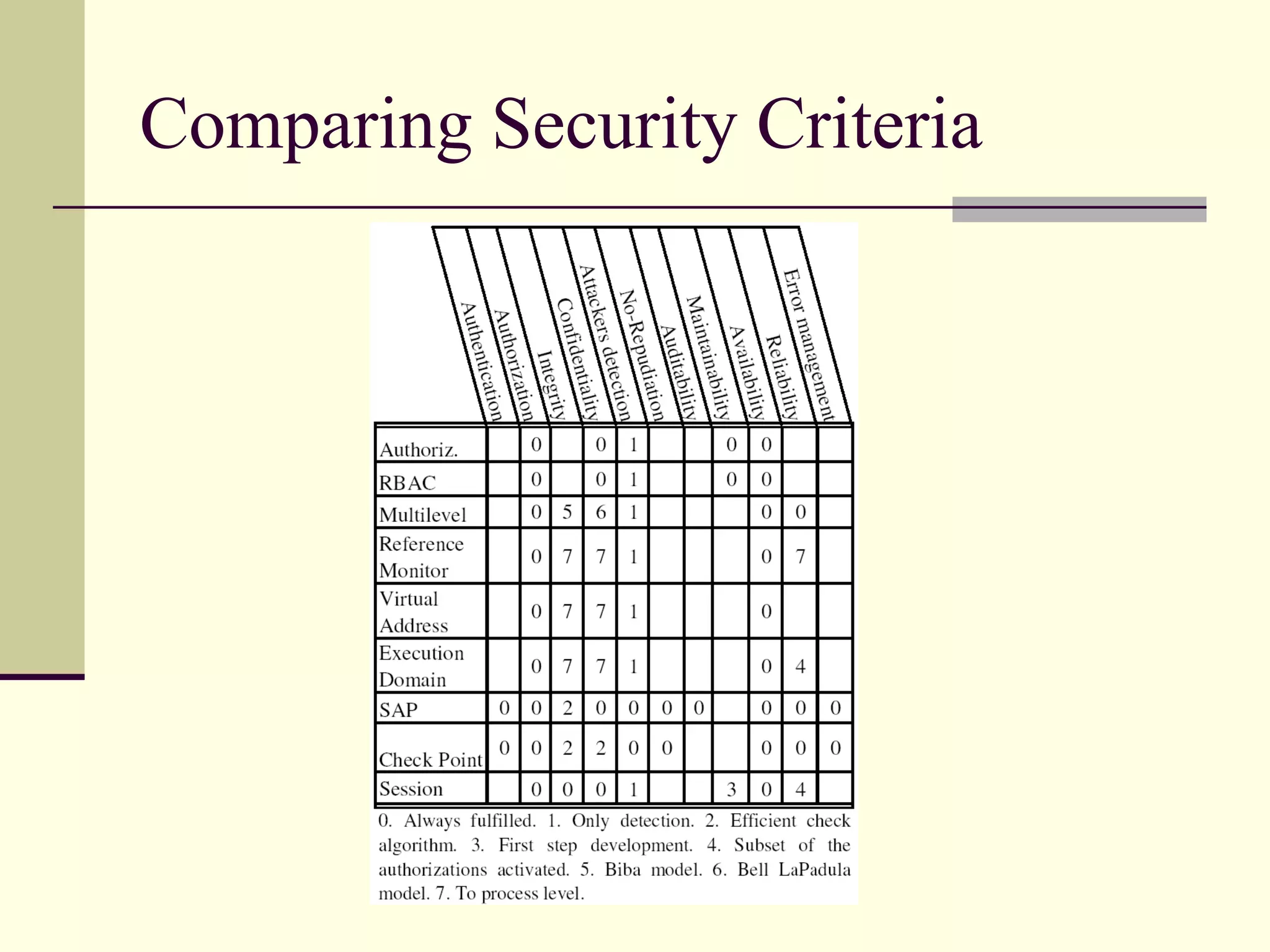
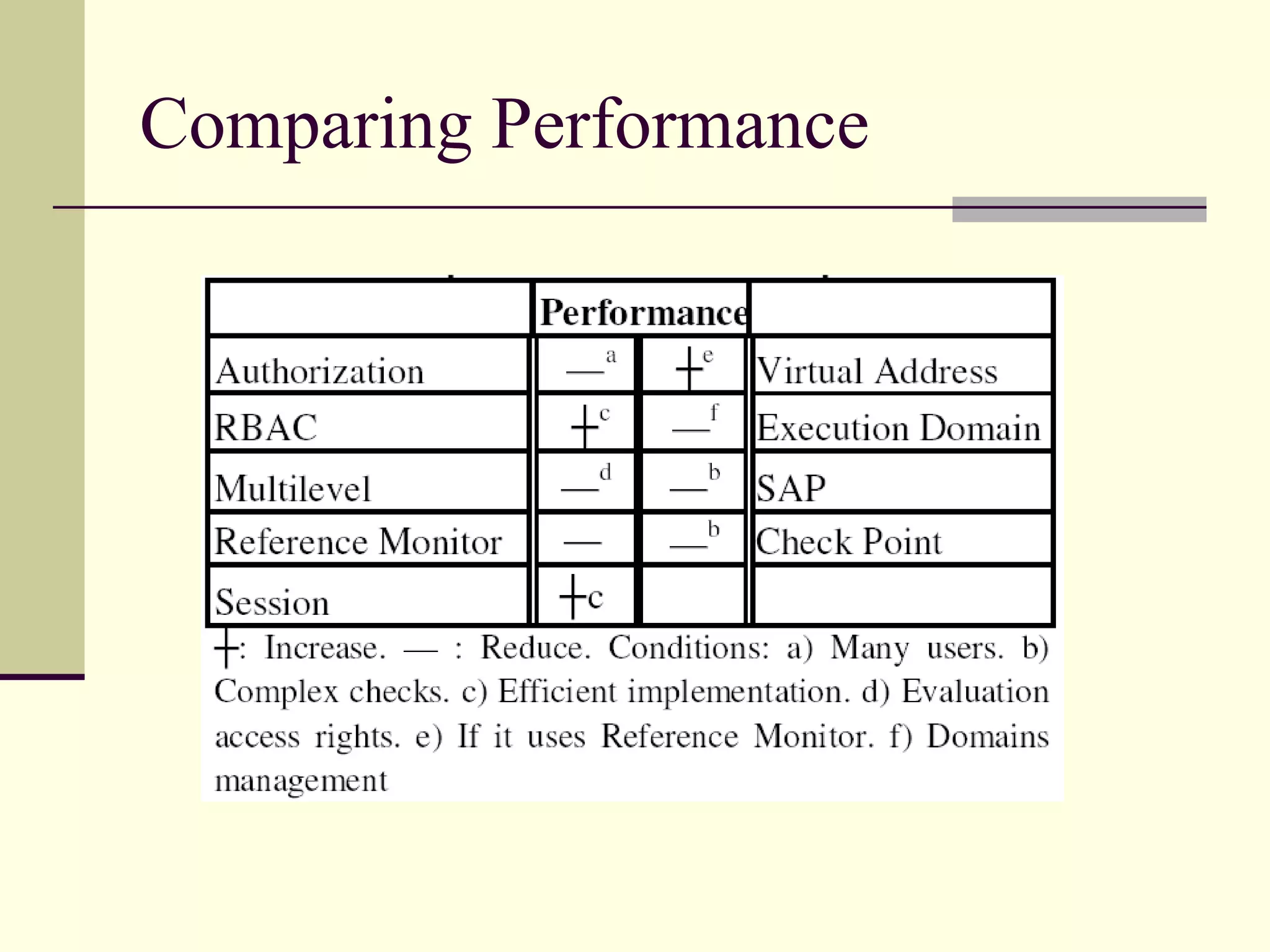
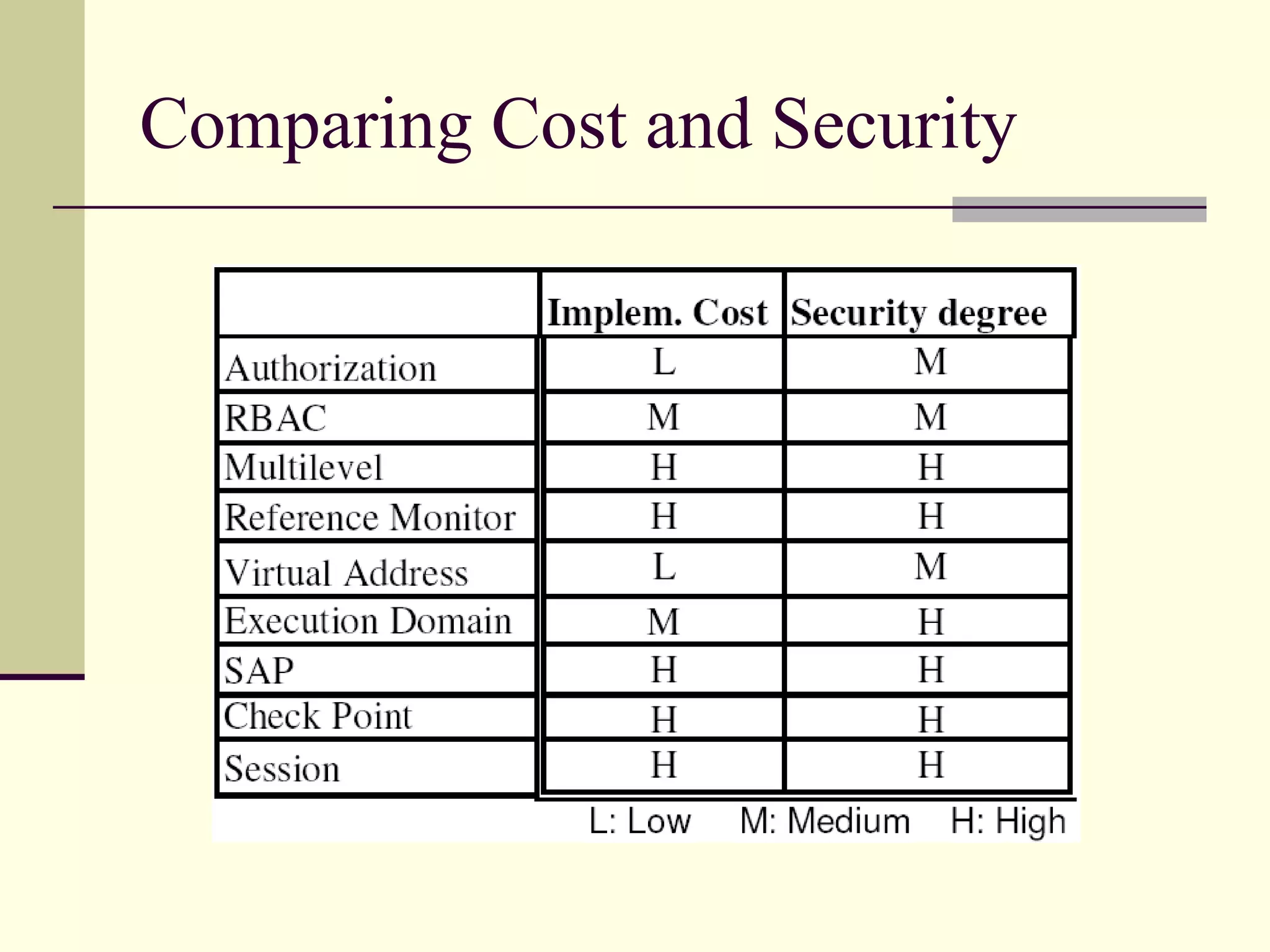
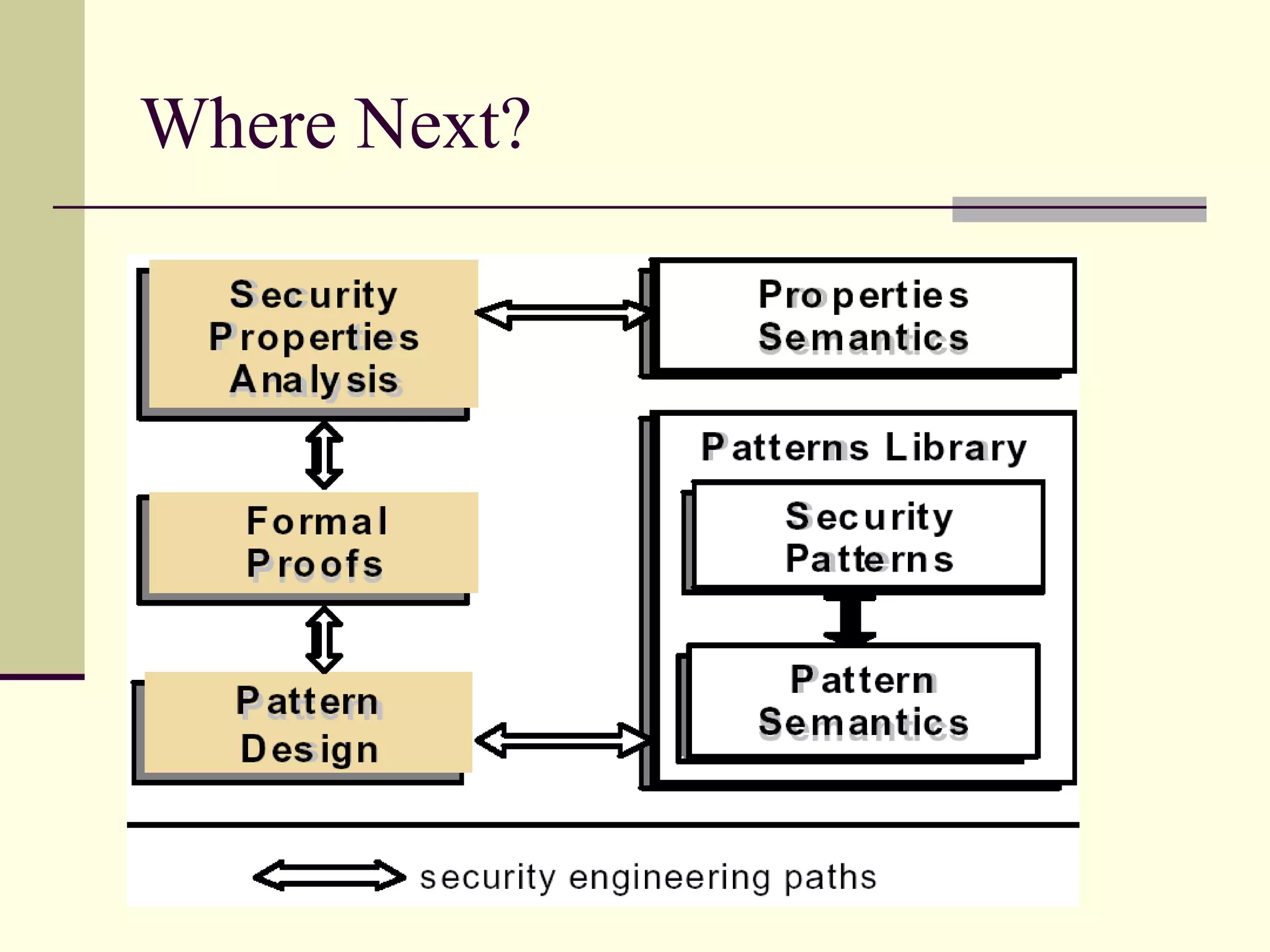
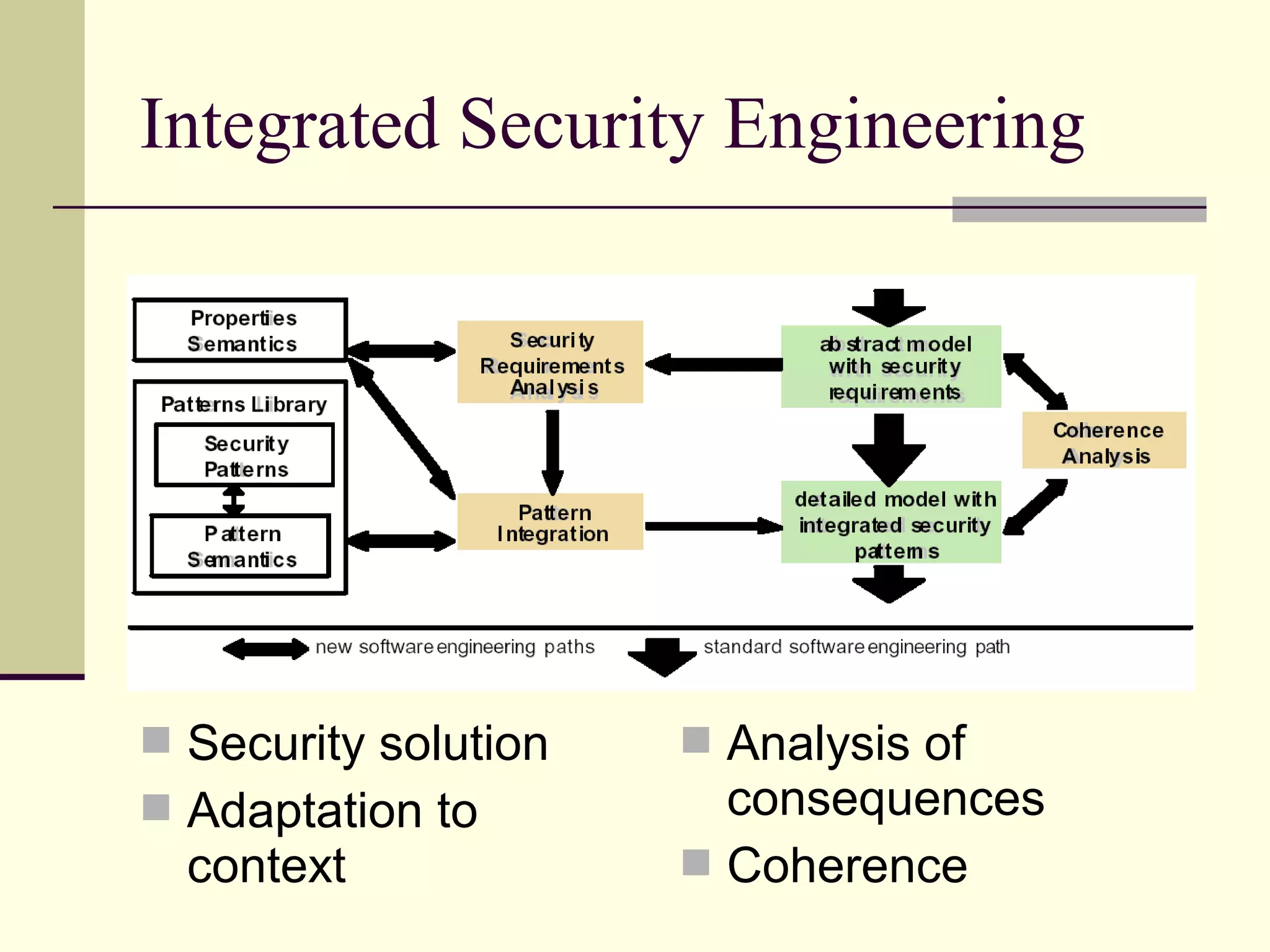
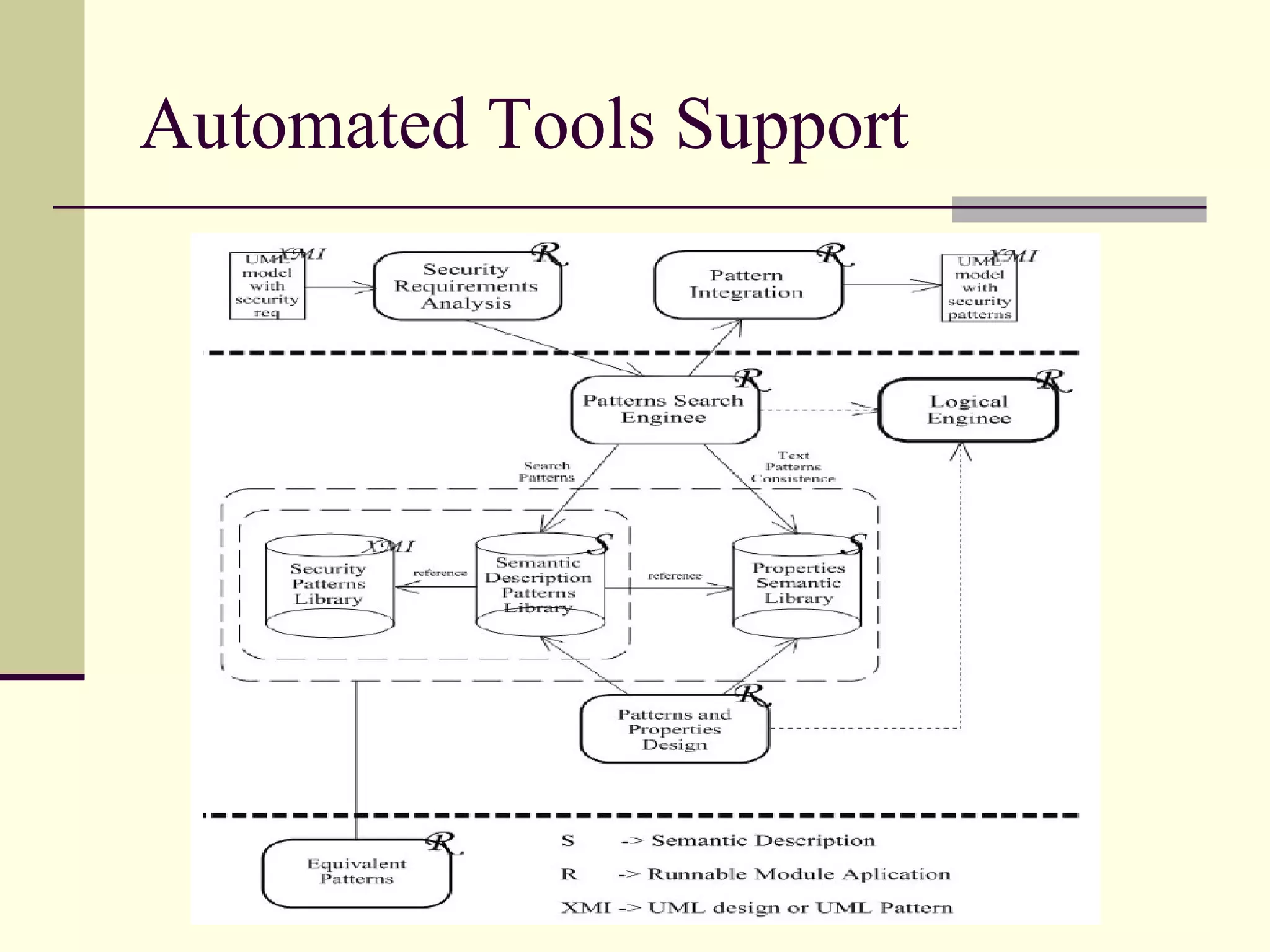
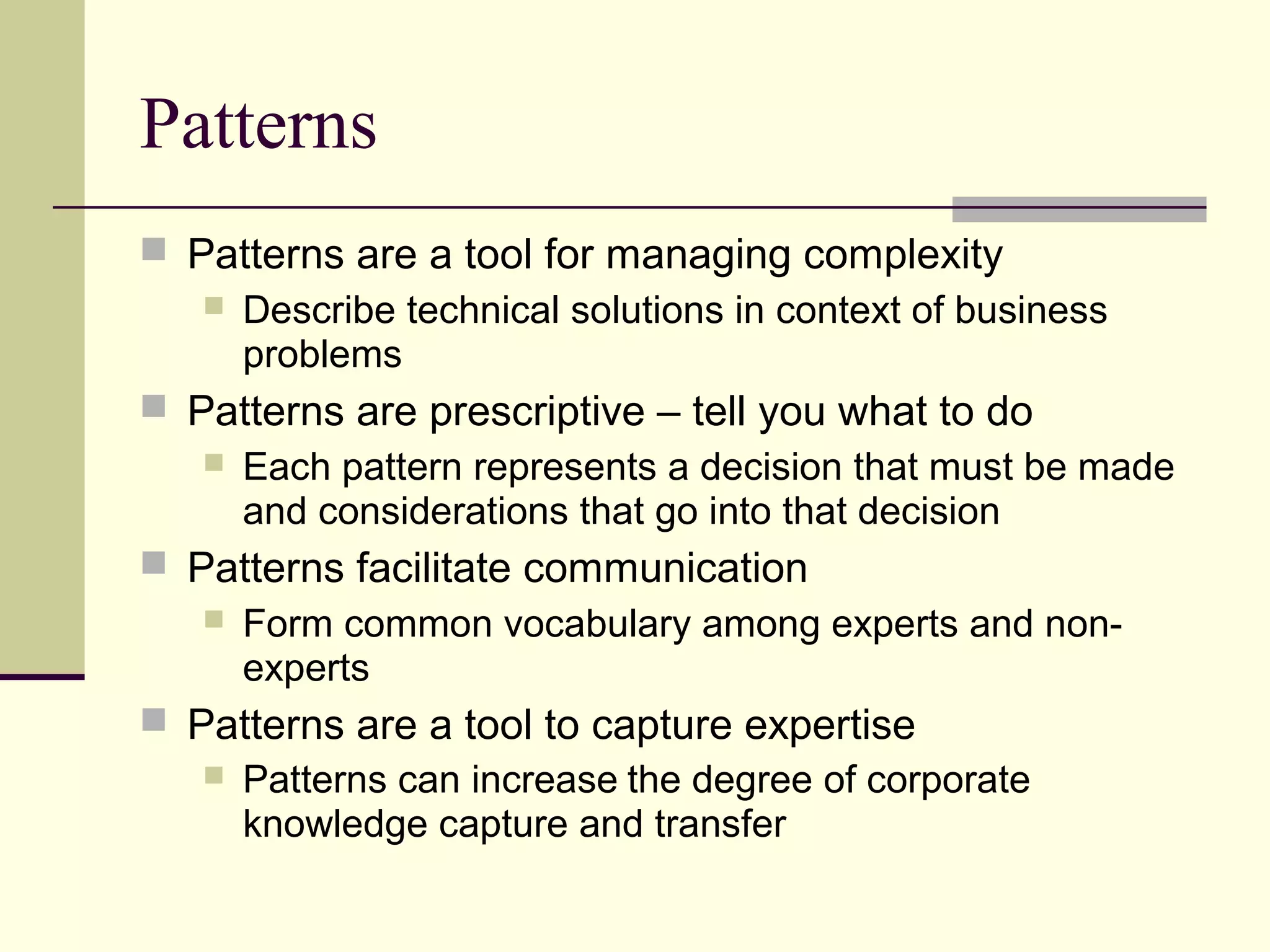
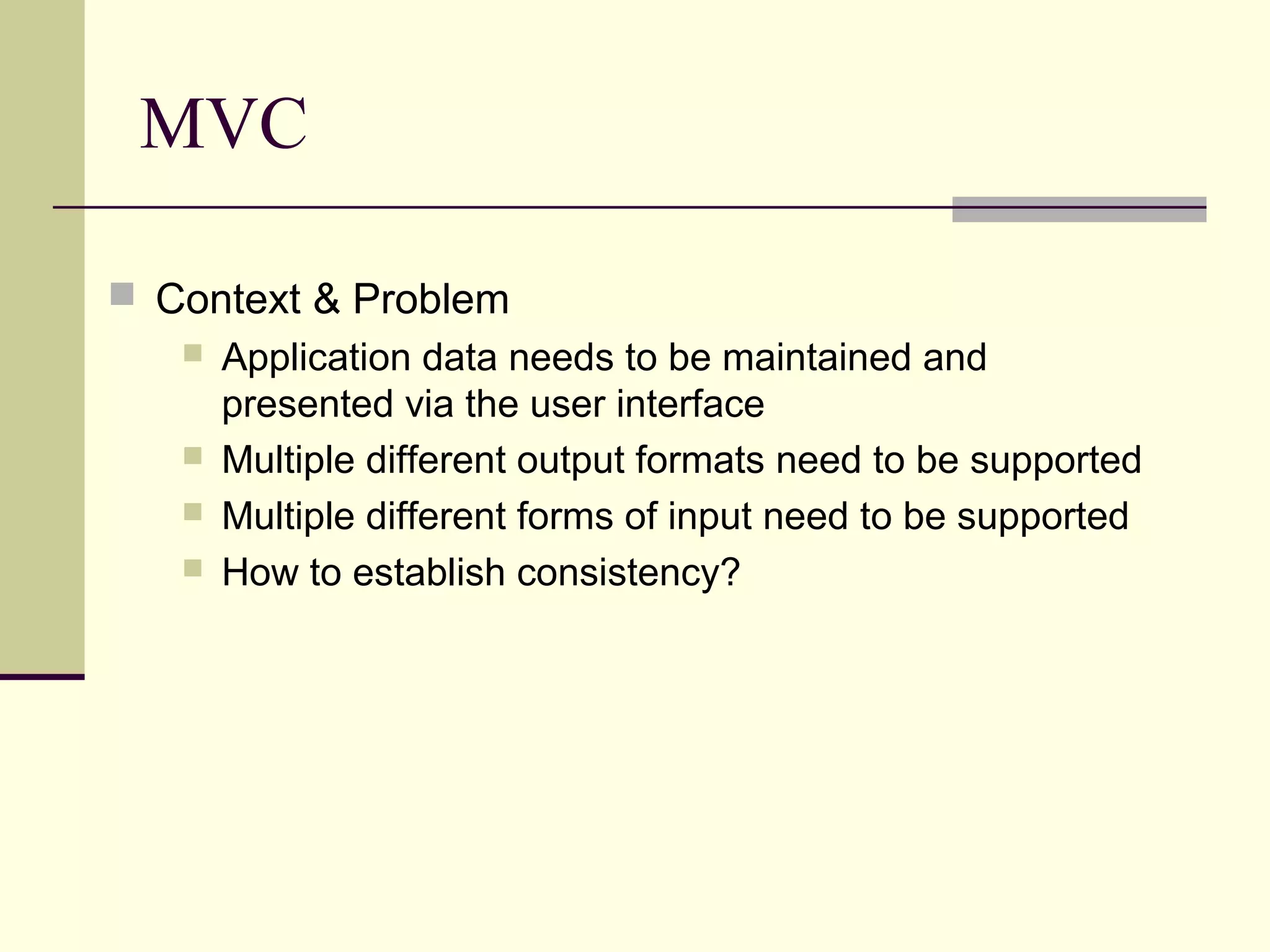
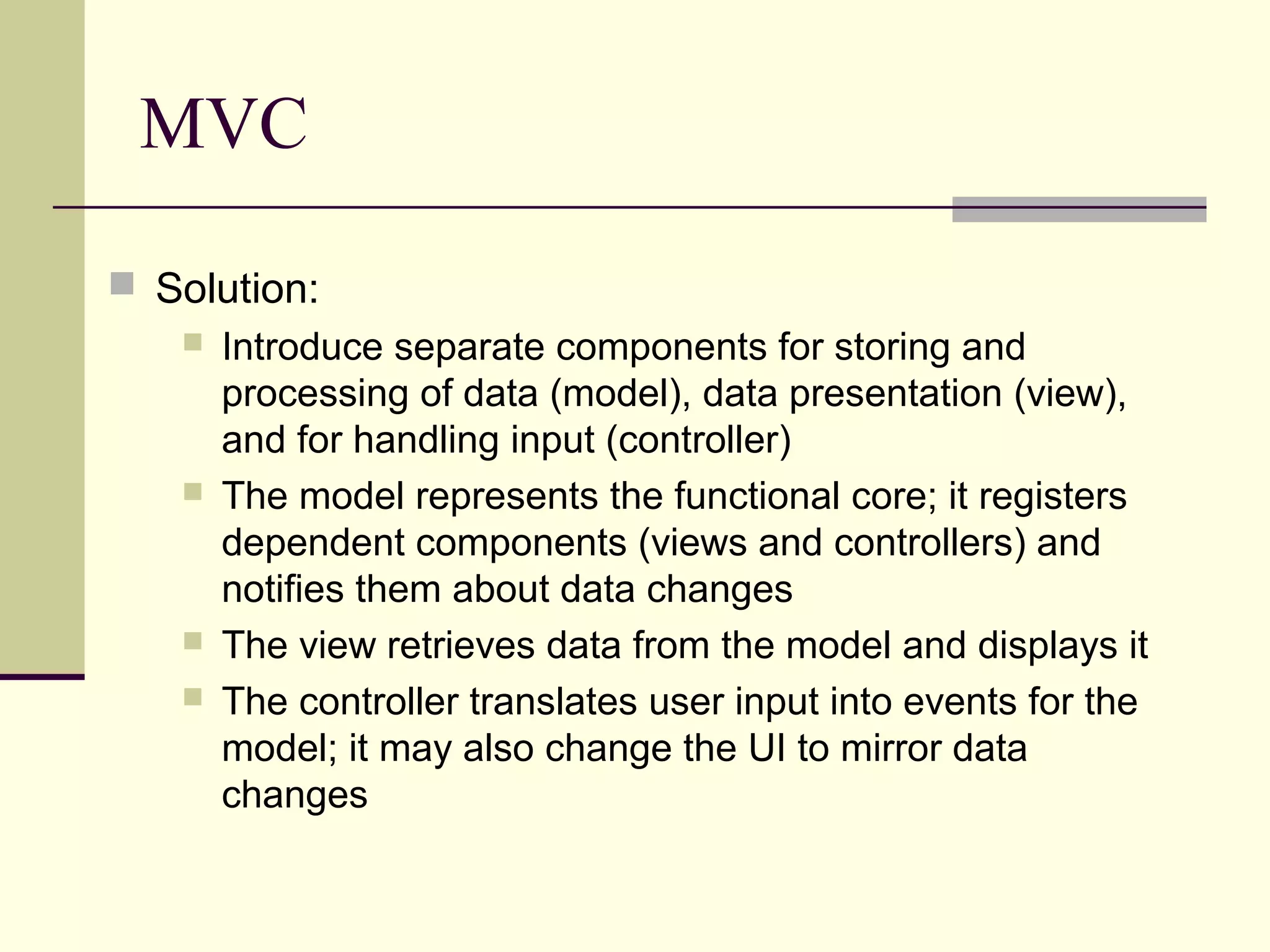
This document provides an overview of security patterns and model driven architecture. It summarizes three papers on using security patterns to model security requirements. The document discusses how security patterns can be used to address the common problem of irregular and haphazard application of security measures leading to insecure systems. It describes Cheng's approach of revising the security pattern template to allow formal verification of requirements. Rosado's approach is also summarized, which presents a standardized security pattern template and evaluates several common security patterns. The document provides context on how security patterns can help capture expertise to facilitate secure systems design.


![Papers to Review
Using Security Patterns to Model and Analyze
Security Requirements (Betty Cheng et al, Michigan
State University) [~2000]
A Study of Security Architecture Patterns
(Rosado et al, University of Castilla-La Mancha) [2006]
Integration of Security Patterns in Software
Models based on Semantic Descriptions (Diego
Ray, University of Malaga) [2003]](https://image.slidesharecdn.com/securitypatternsandmodeldrivenarchitecture-151112004237-lva1-app6891/75/Security-patterns-and-model-driven-architecture-4-2048.jpg)


![What is a Pattern?
A pattern for software architecture describes a
particular recurring design problem that arises
in specific design contexts, and presents a
well-proven generic scheme for its solution.
The solution scheme is specified by
describing its constituent components, their
responsibilities and relationships, and the
ways in which they collaborate.
[POSA96]](https://image.slidesharecdn.com/securitypatternsandmodeldrivenarchitecture-151112004237-lva1-app6891/75/Security-patterns-and-model-driven-architecture-10-2048.jpg)
![MVC: Example
0
20
40
60
80
100
120
140
160
180
200
a b c
Series1
a
b
c
a b c
60 30 10
50 30 20
80 10 10
a = 63%
b = 23%
c = 14%
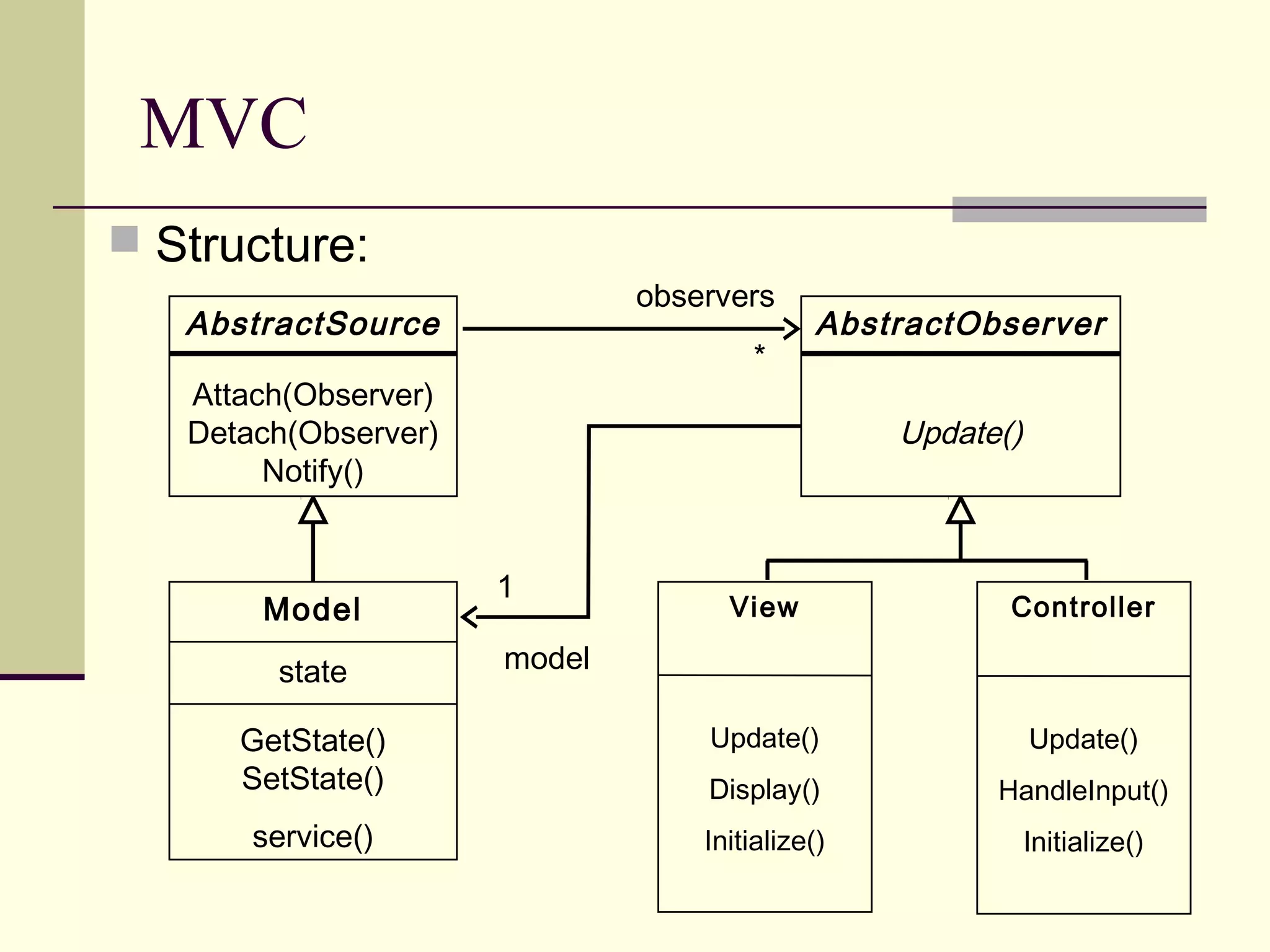
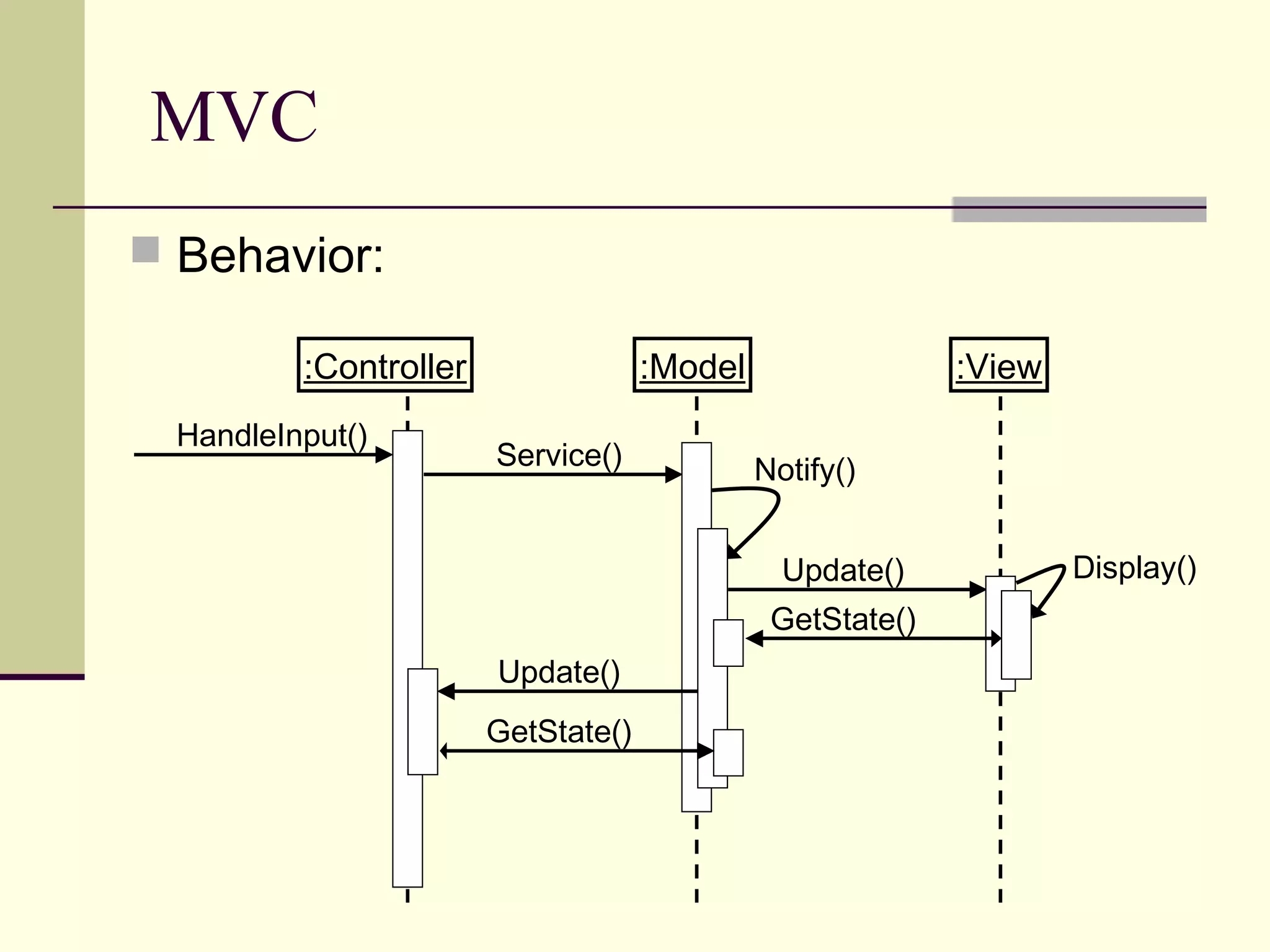
Model
View
Controller
adapted from [M05]](https://image.slidesharecdn.com/securitypatternsandmodeldrivenarchitecture-151112004237-lva1-app6891/75/Security-patterns-and-model-driven-architecture-13-2048.jpg)
![Pattern Information
Analysis patterns [Fowler: Analysis Patterns]
Design patterns [Gamma et al: Design
Patterns]
Specification patterns [Dwyer et al: 2nd
Workshop on Formal Methods in Software
Engineering (1998)]](https://image.slidesharecdn.com/securitypatternsandmodeldrivenarchitecture-151112004237-lva1-app6891/75/Security-patterns-and-model-driven-architecture-17-2048.jpg)