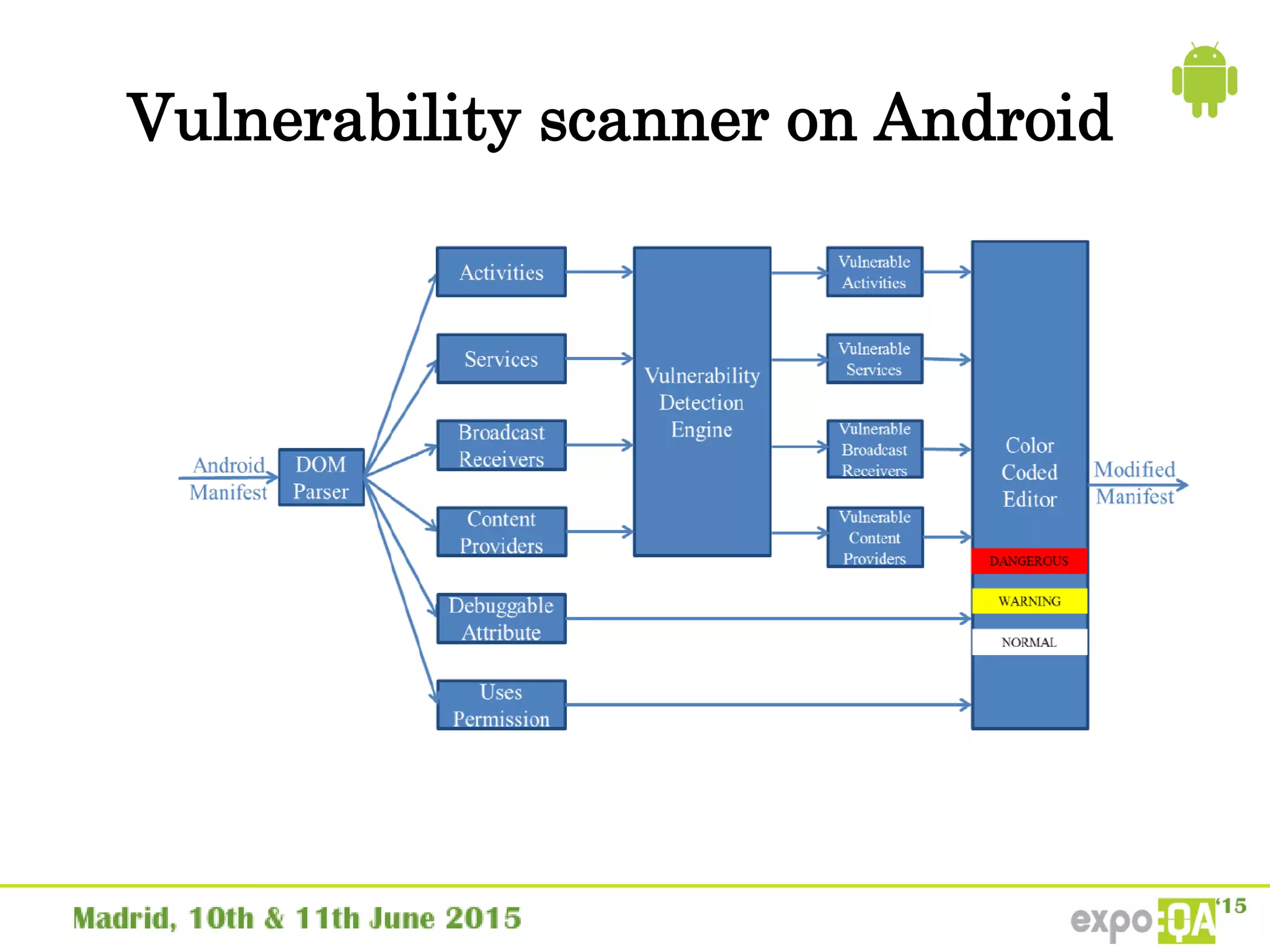
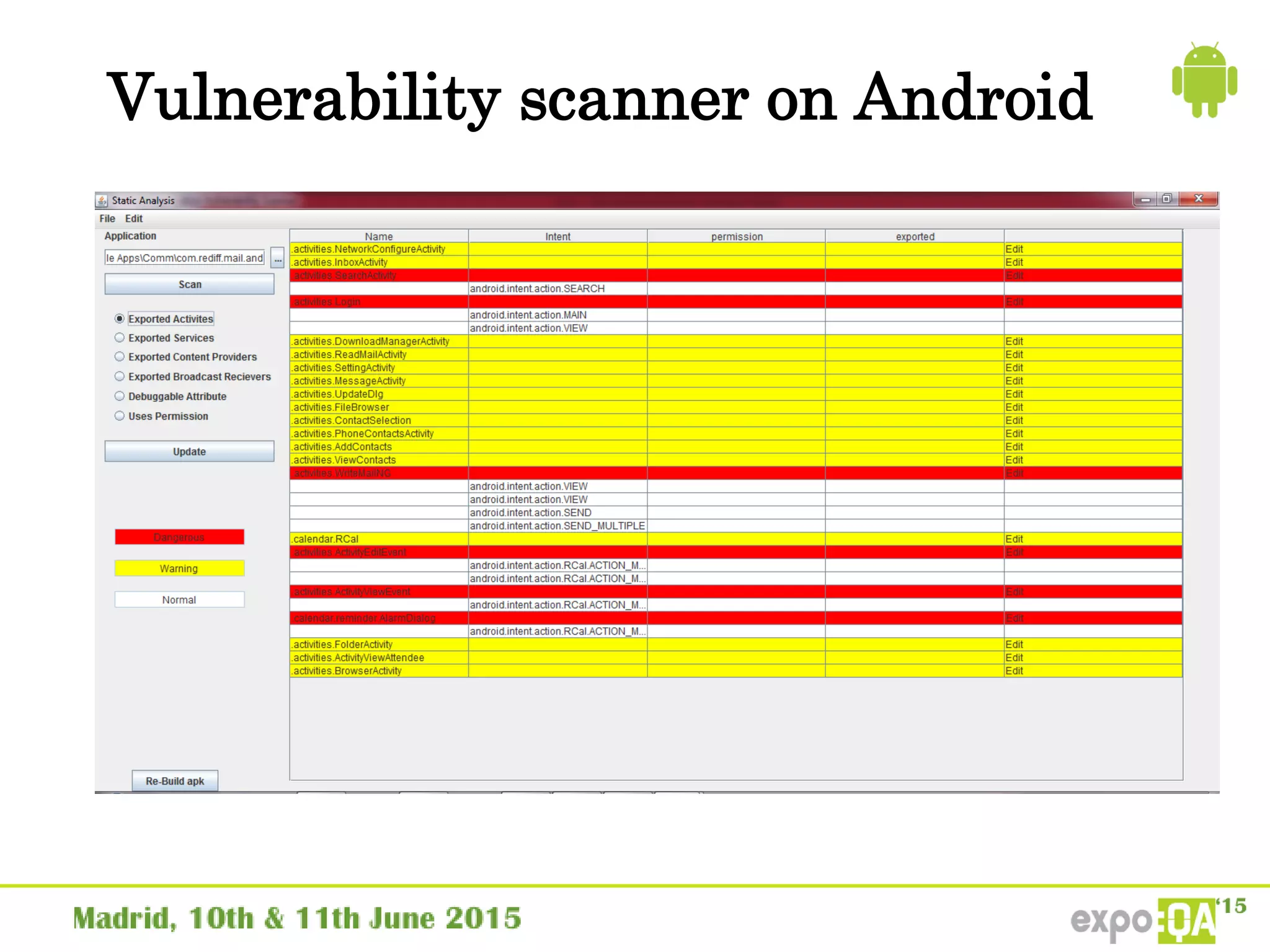
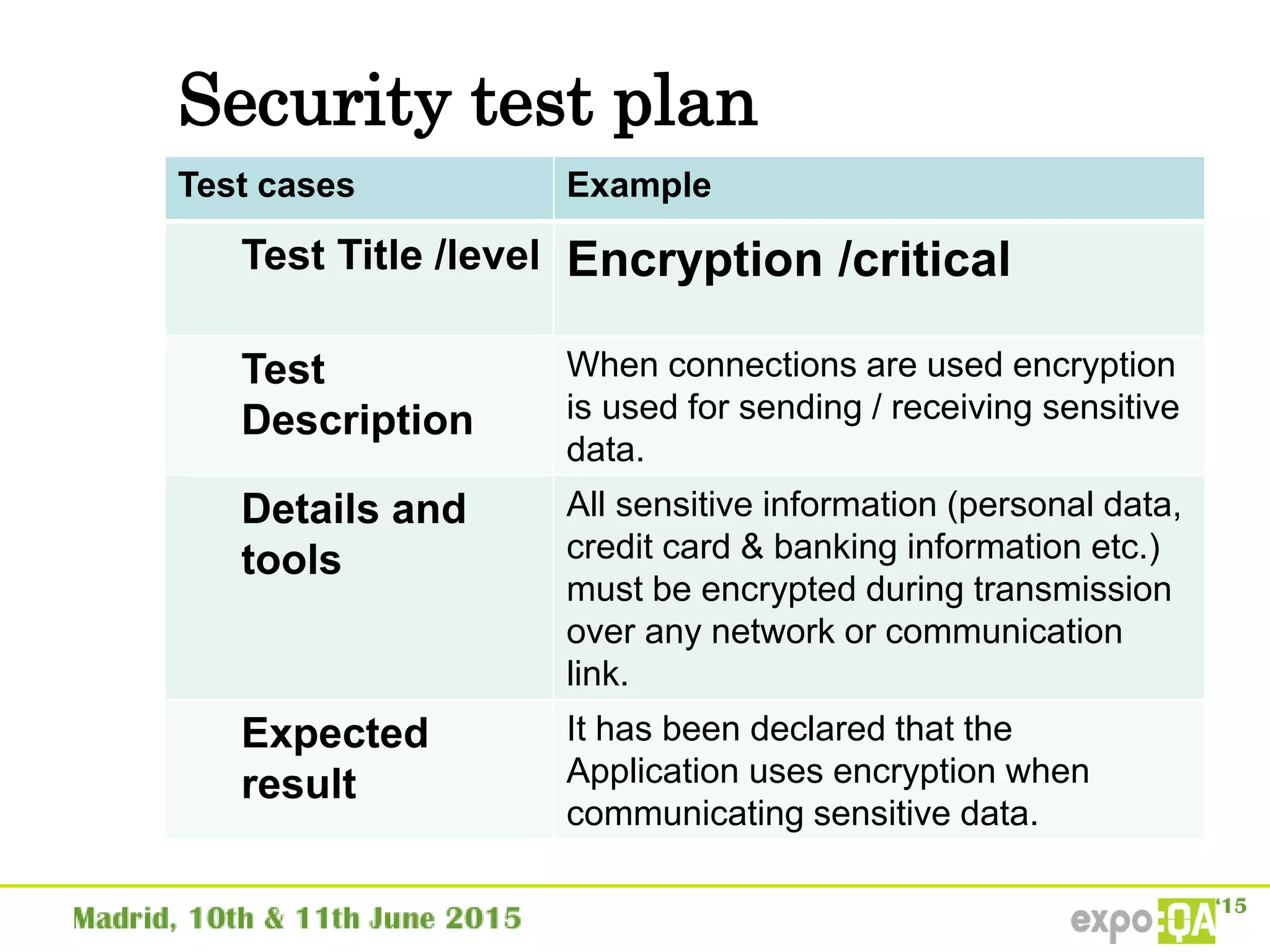
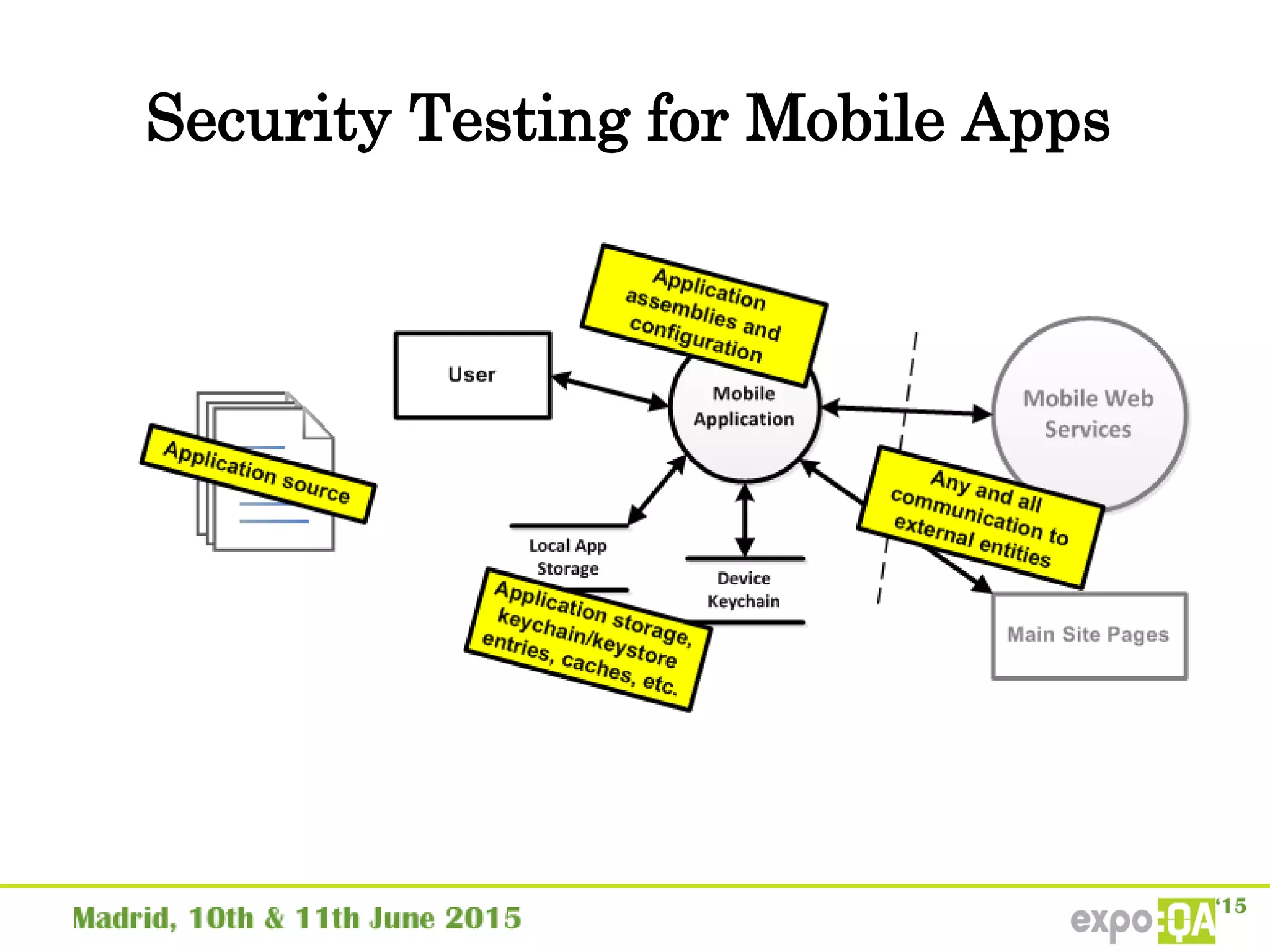
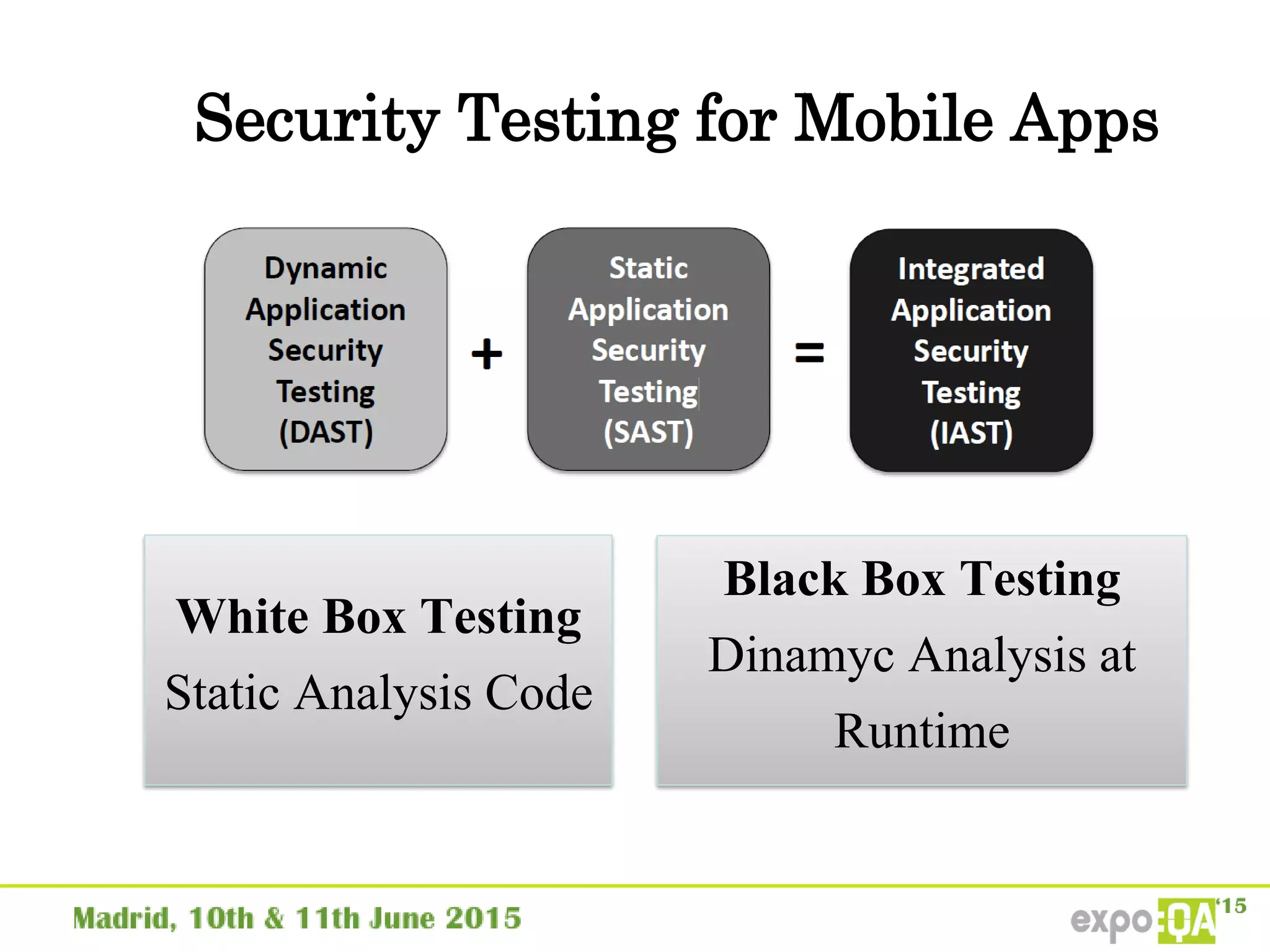
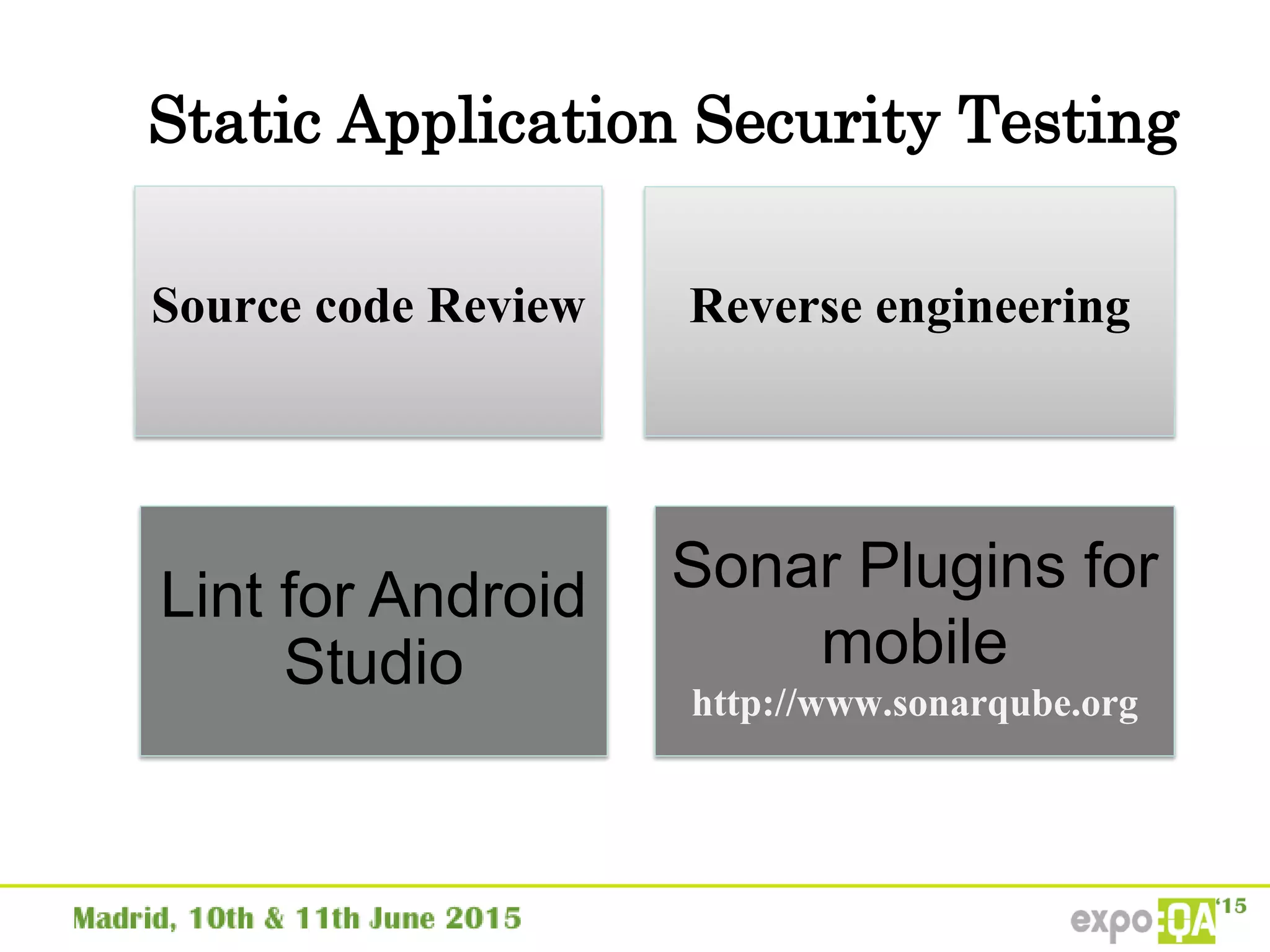
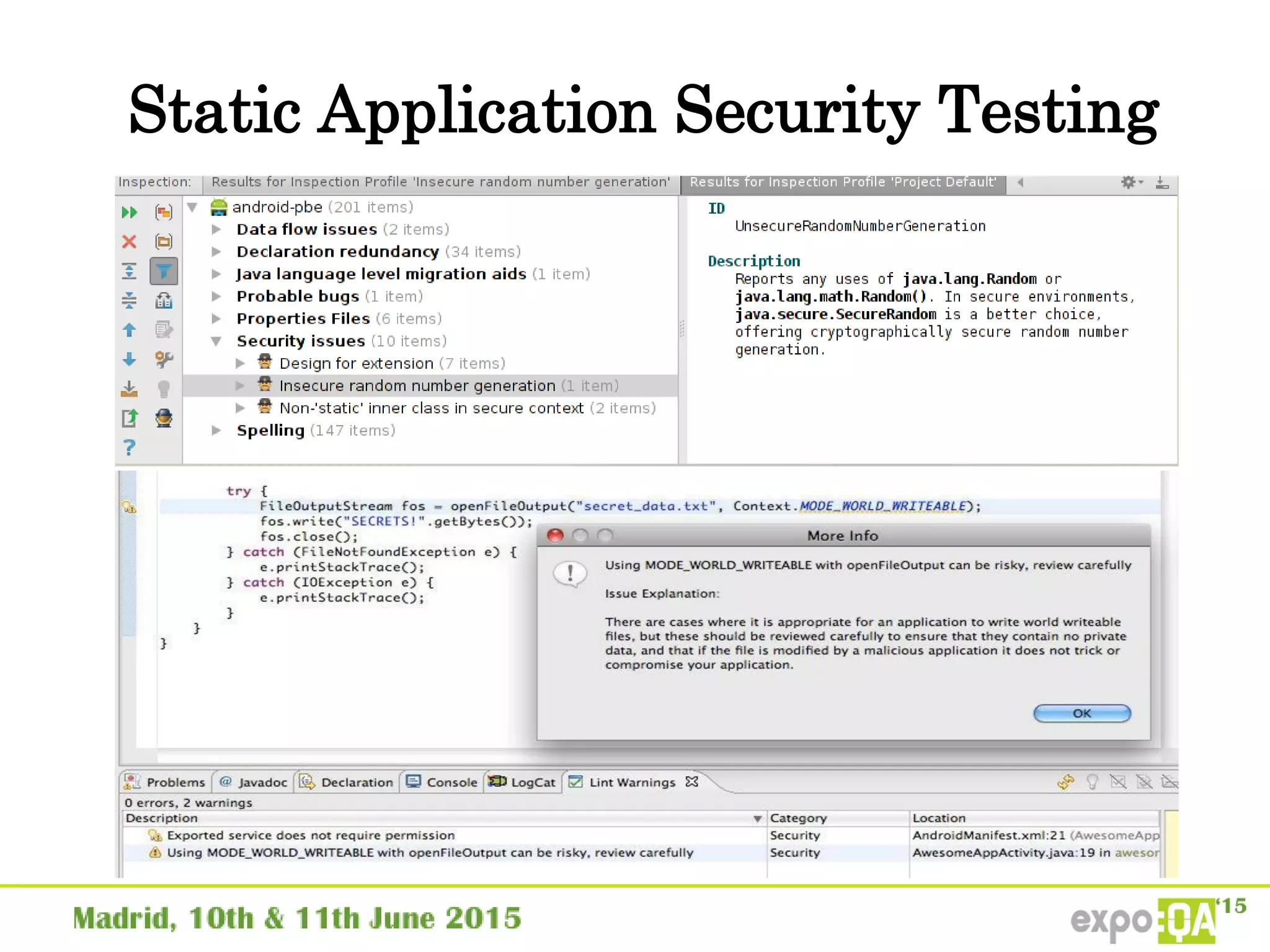
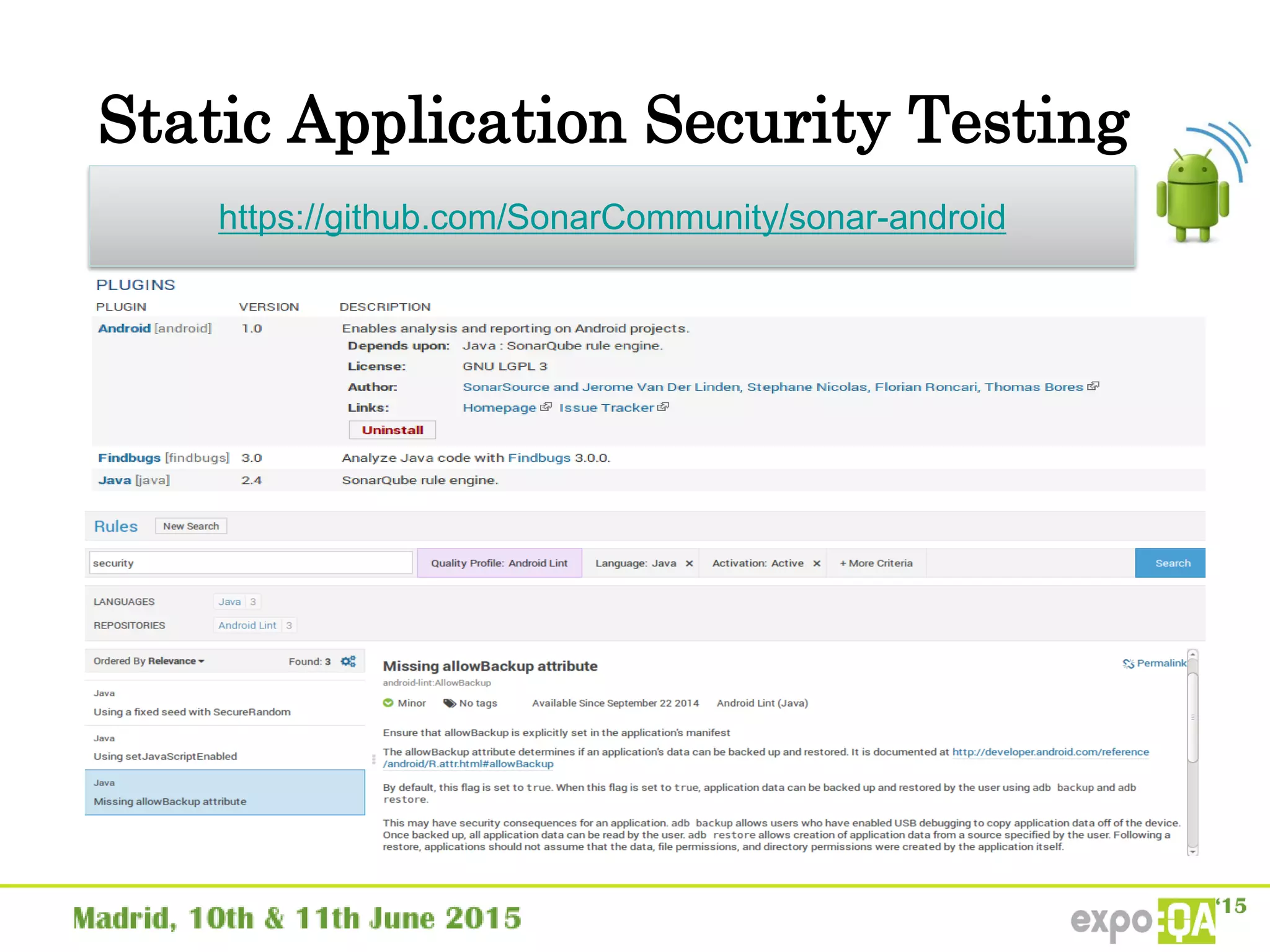
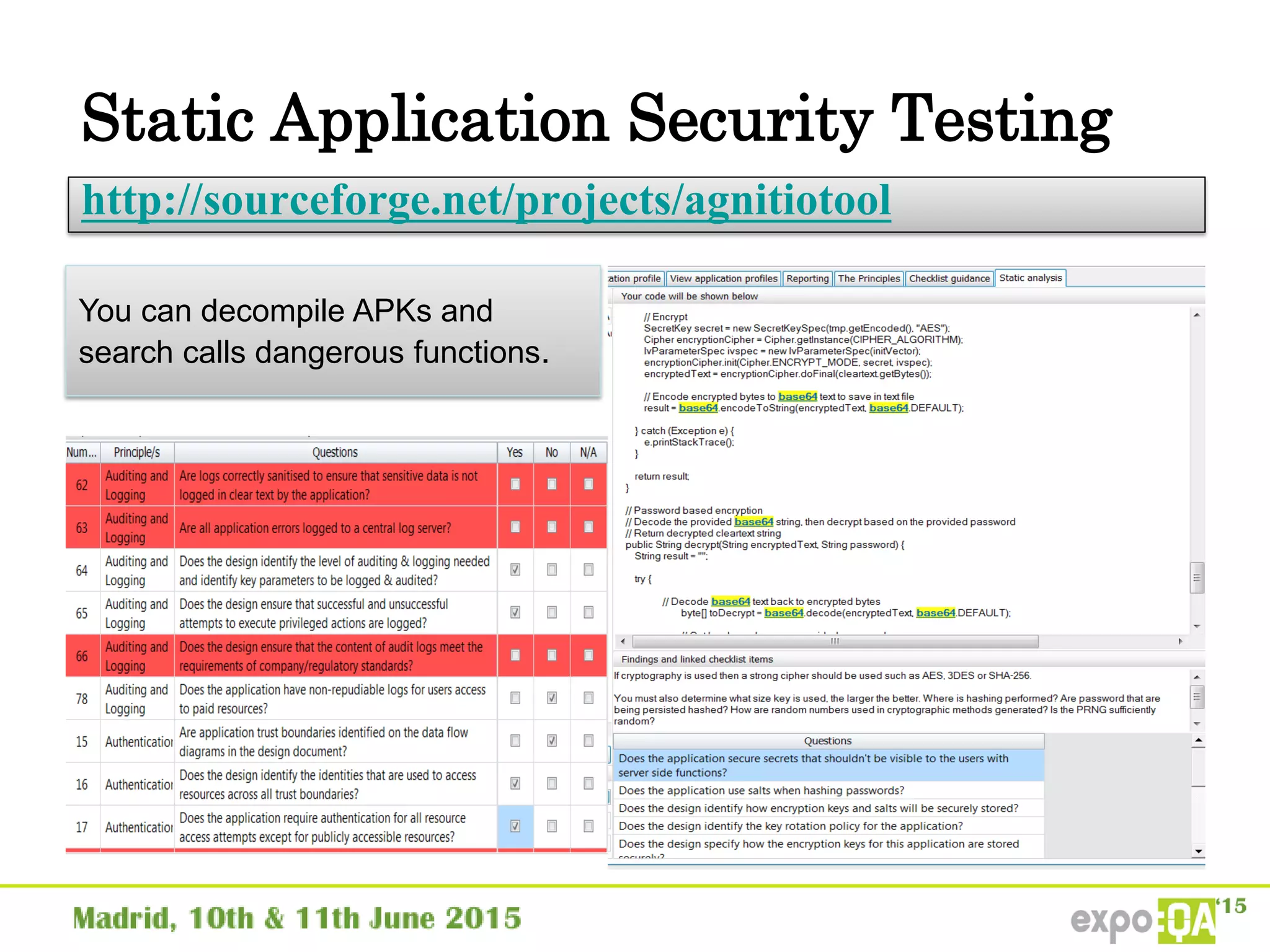
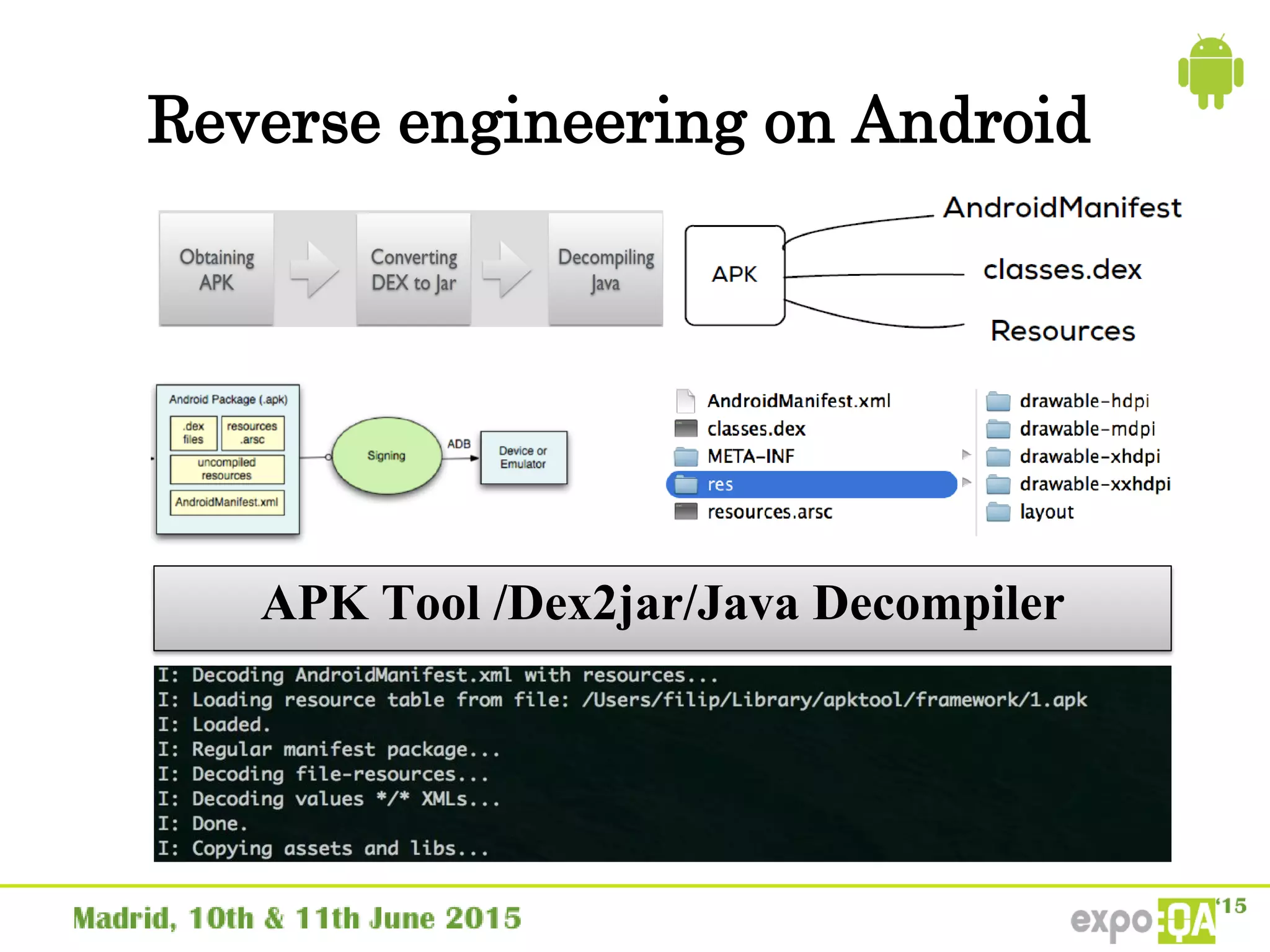
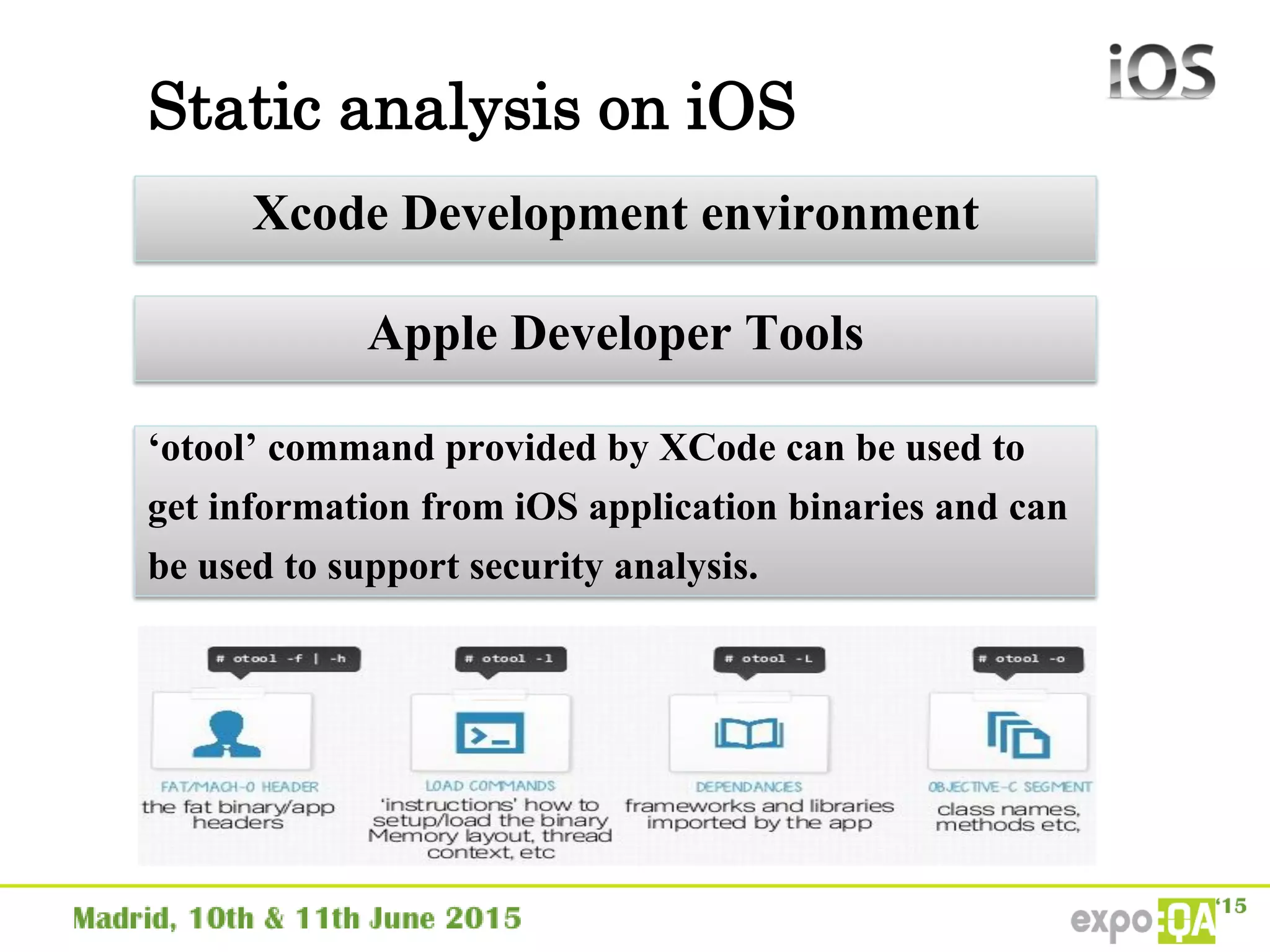
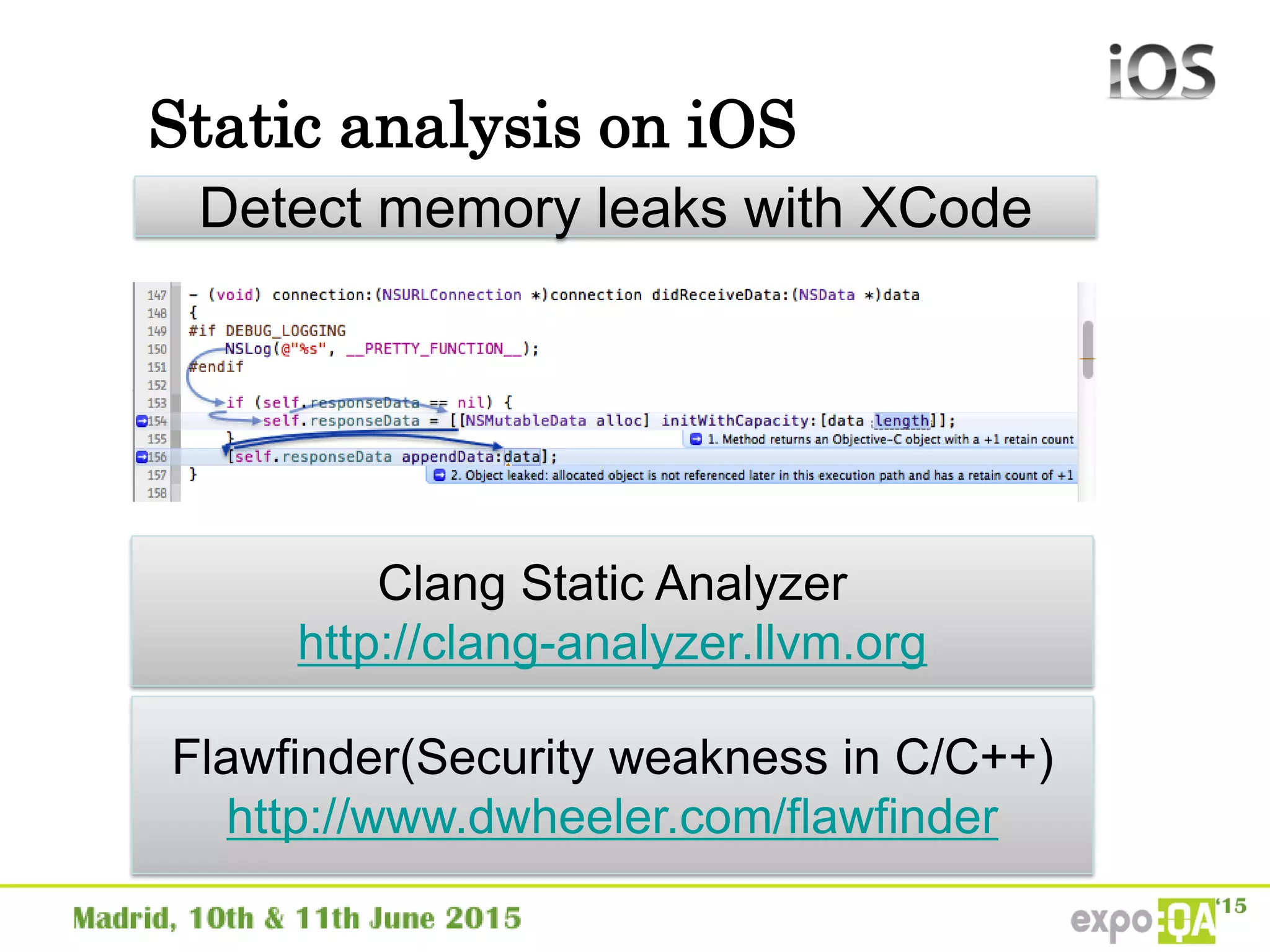
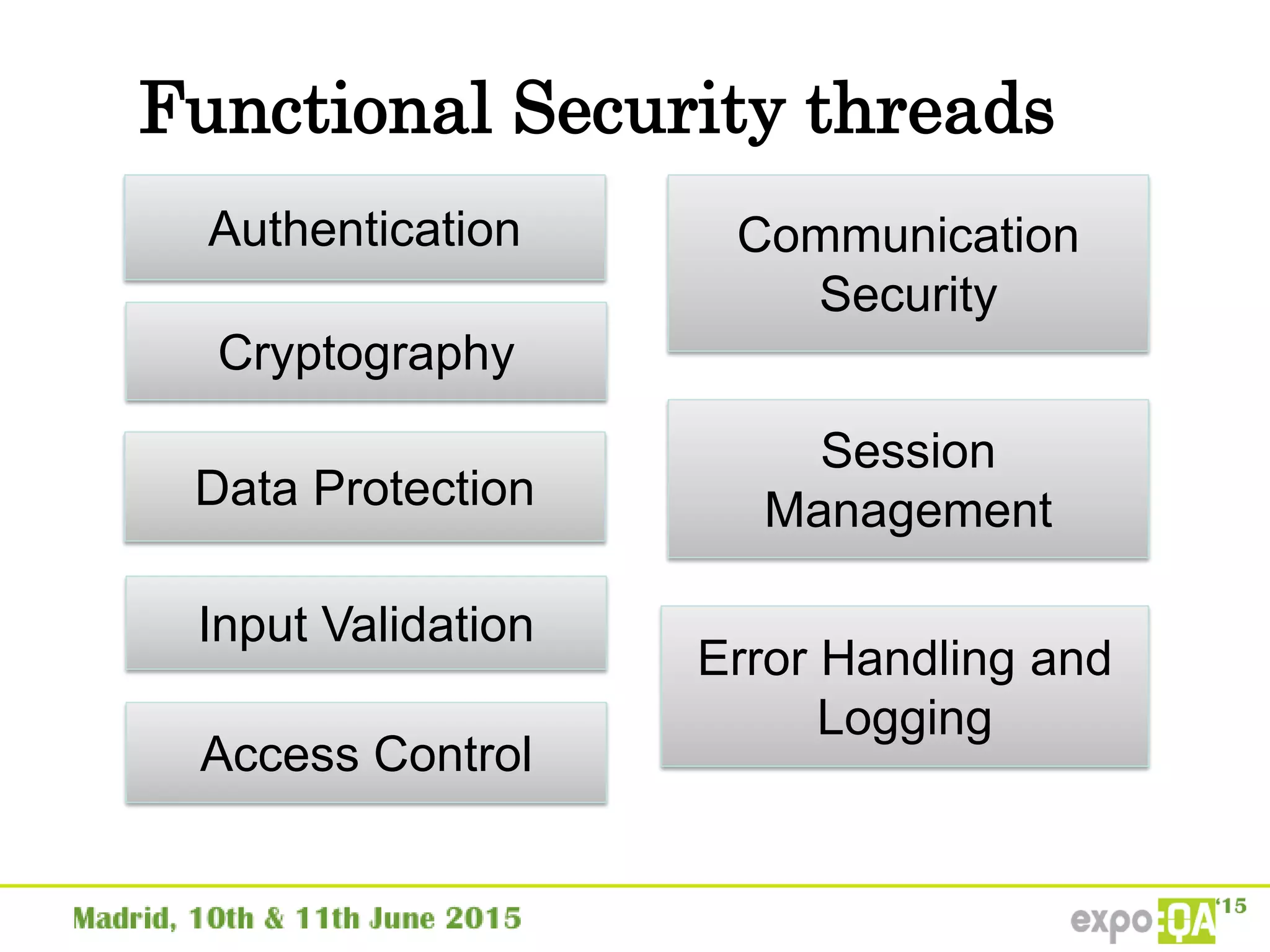
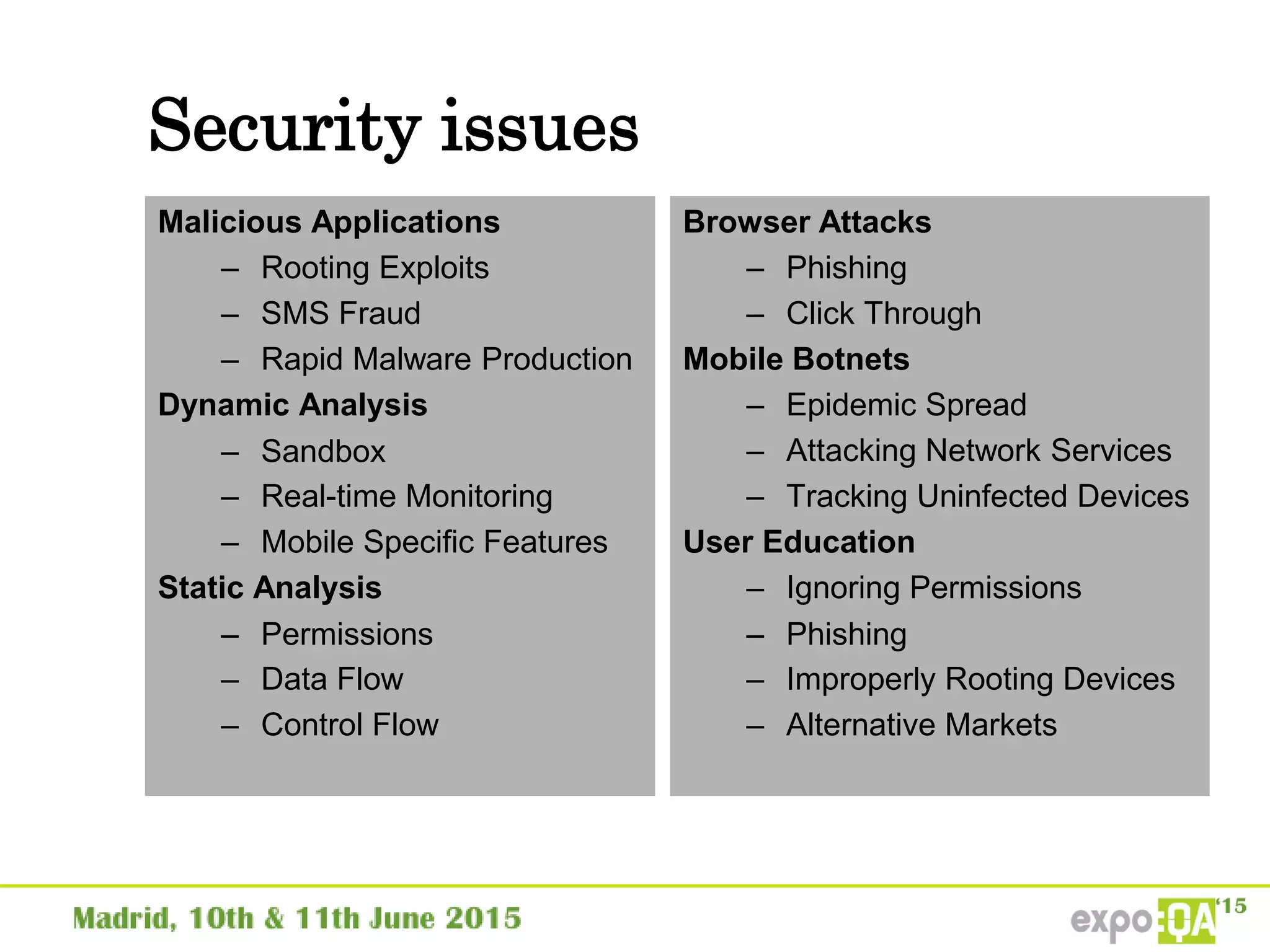
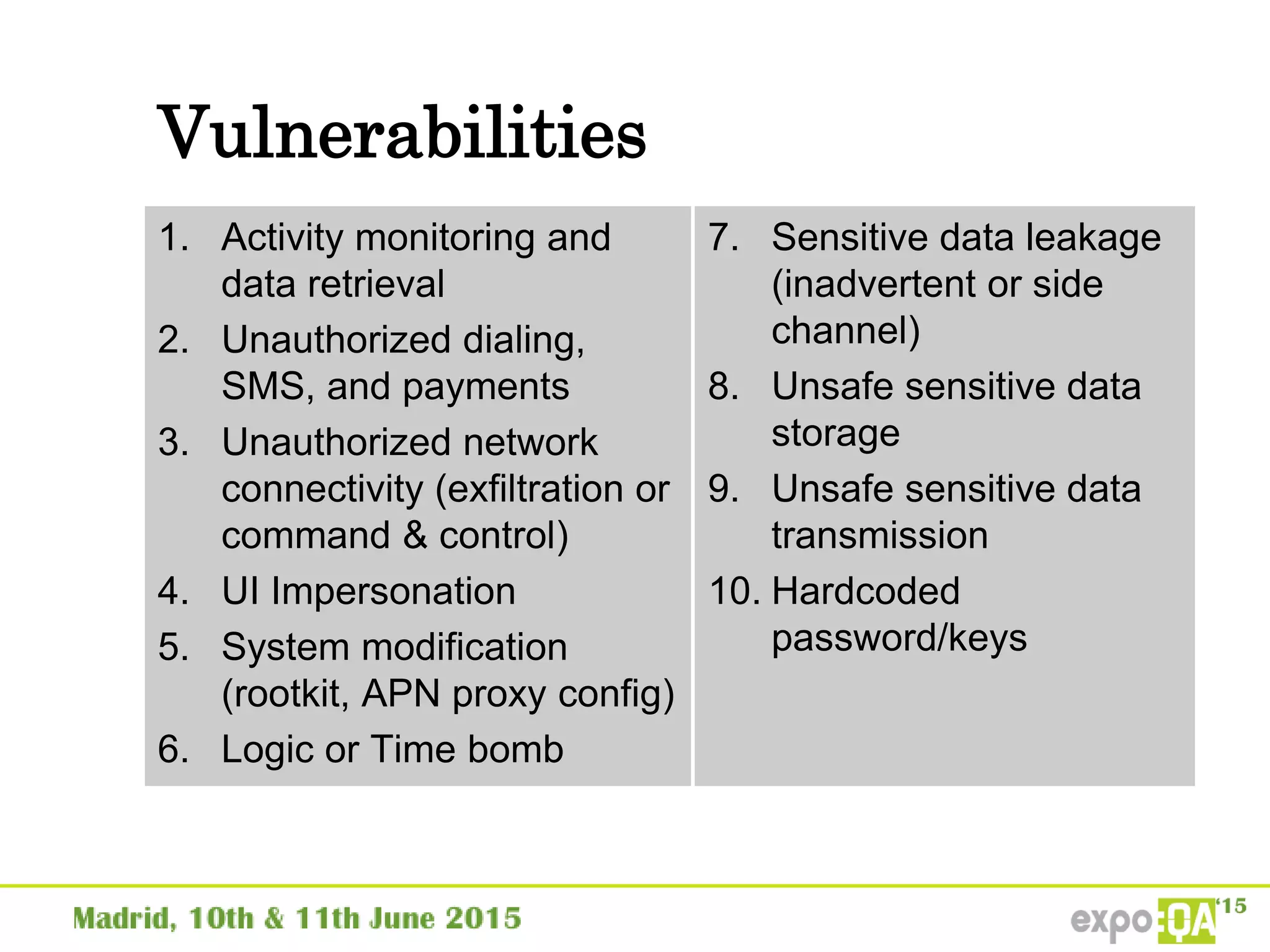
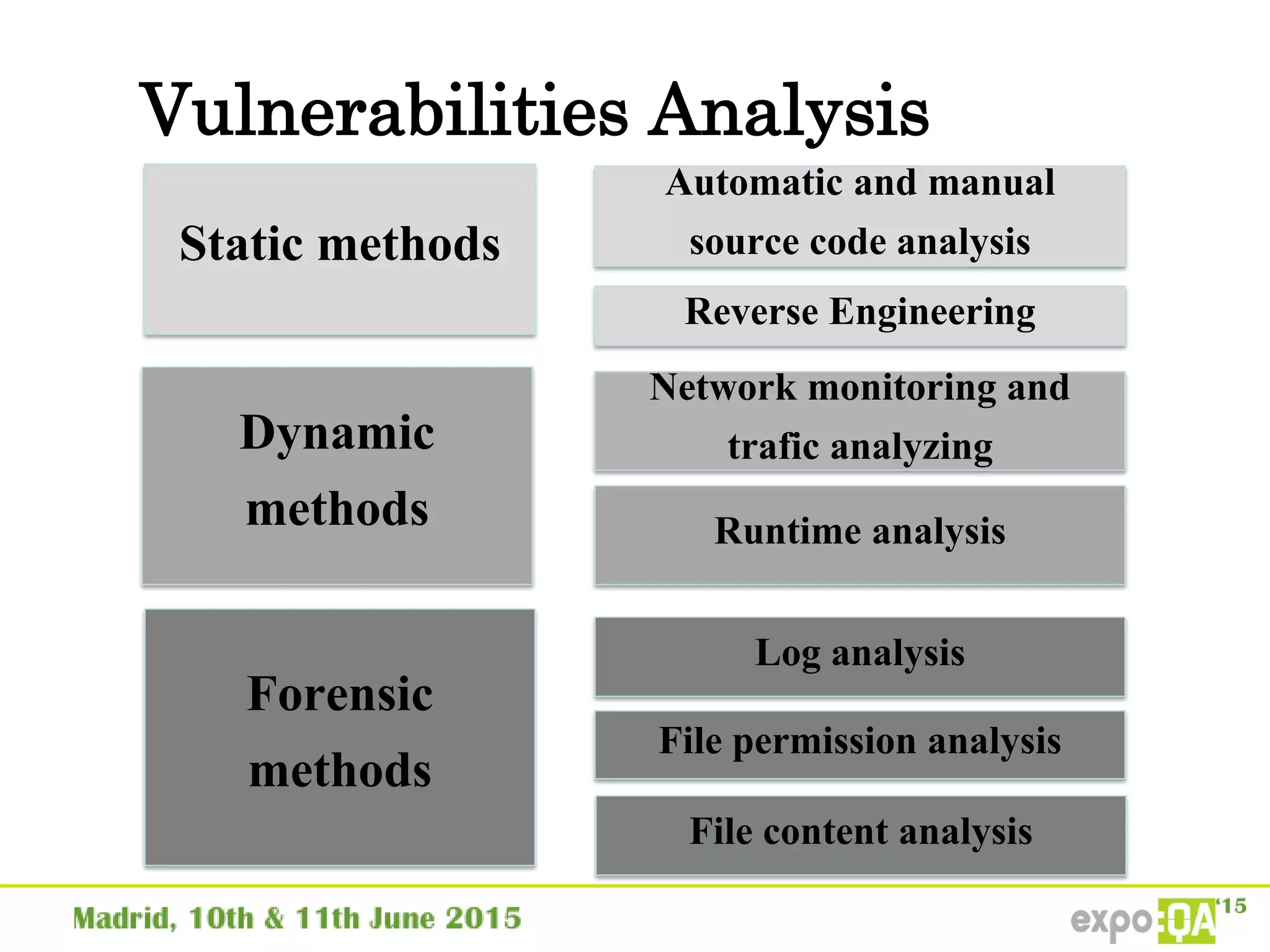
José Manuel Ortega Candel presented on security testing in mobile applications. The presentation covered static and dynamic application security testing, vulnerabilities, security risks, and best practices for mobile security testing. It discussed analyzing application source code, network traffic, and runtime behavior to identify issues. The document also provided examples of common mobile vulnerabilities and tools that can be used to conduct security testing on both Android and iOS applications.



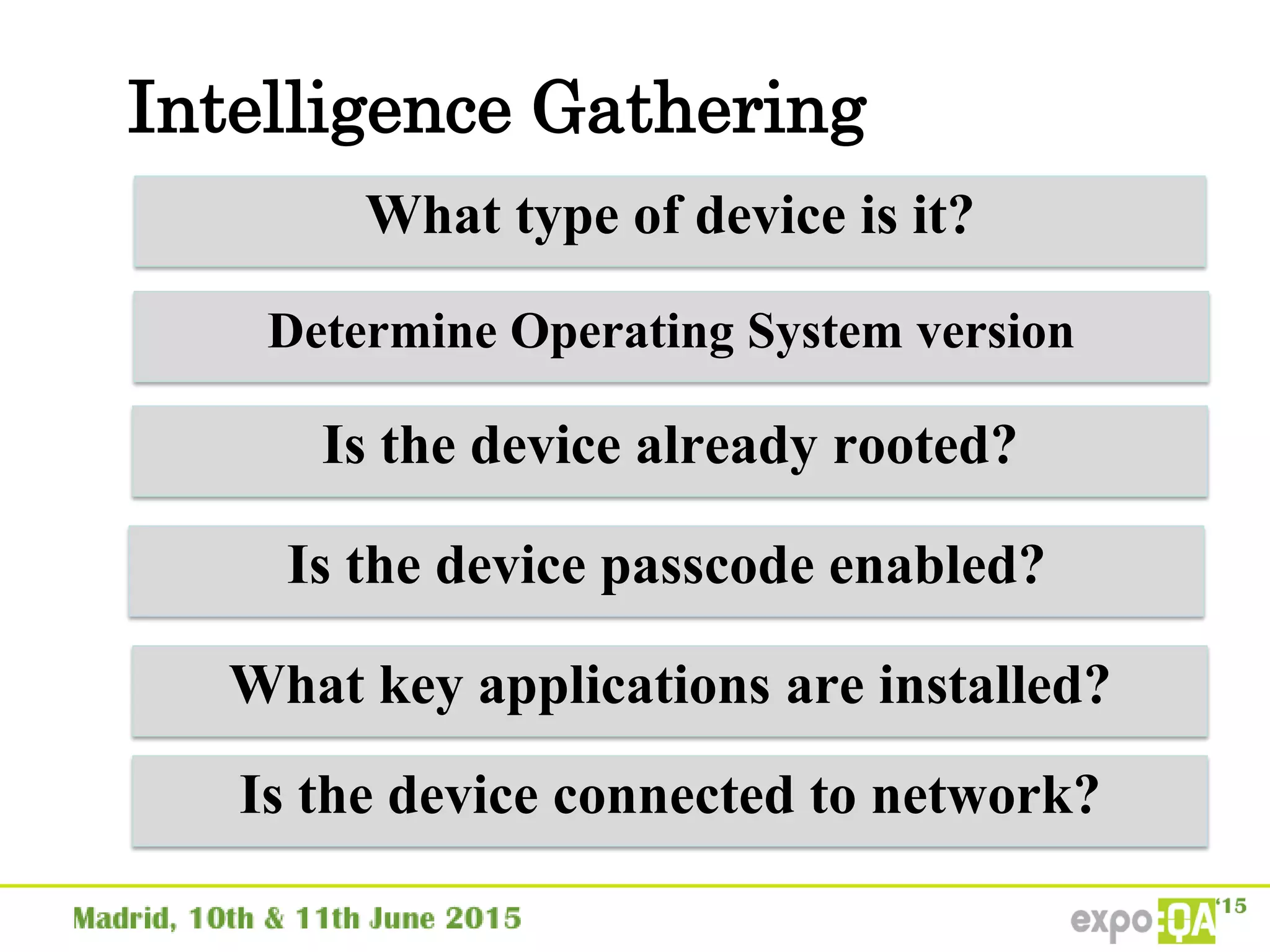
![Intelligence Gathering
Environmental
Analysis
Architectural
Analysis
Analyze internal
processes and structures
App [network interfaces, used
data, communication with other
resources, session management]
Runtime environment [MDM,
jailbreak/rooting, OS version]
Backend services [application
server, databases]](https://image.slidesharecdn.com/securitytestinginmobileapplications-150611164204-lva1-app6891/75/Security-testing-in-mobile-applications-19-2048.jpg)
![Vulnerabilities
Third party
libraries
Components
WebView
[JavaScript+Cache]
SQLite DataBase
Multiplaftorm
libraries for hybrid apps
Shared Preferences](https://image.slidesharecdn.com/securitytestinginmobileapplications-150611164204-lva1-app6891/75/Security-testing-in-mobile-applications-24-2048.jpg)
![OWASP Mobile Security Risks
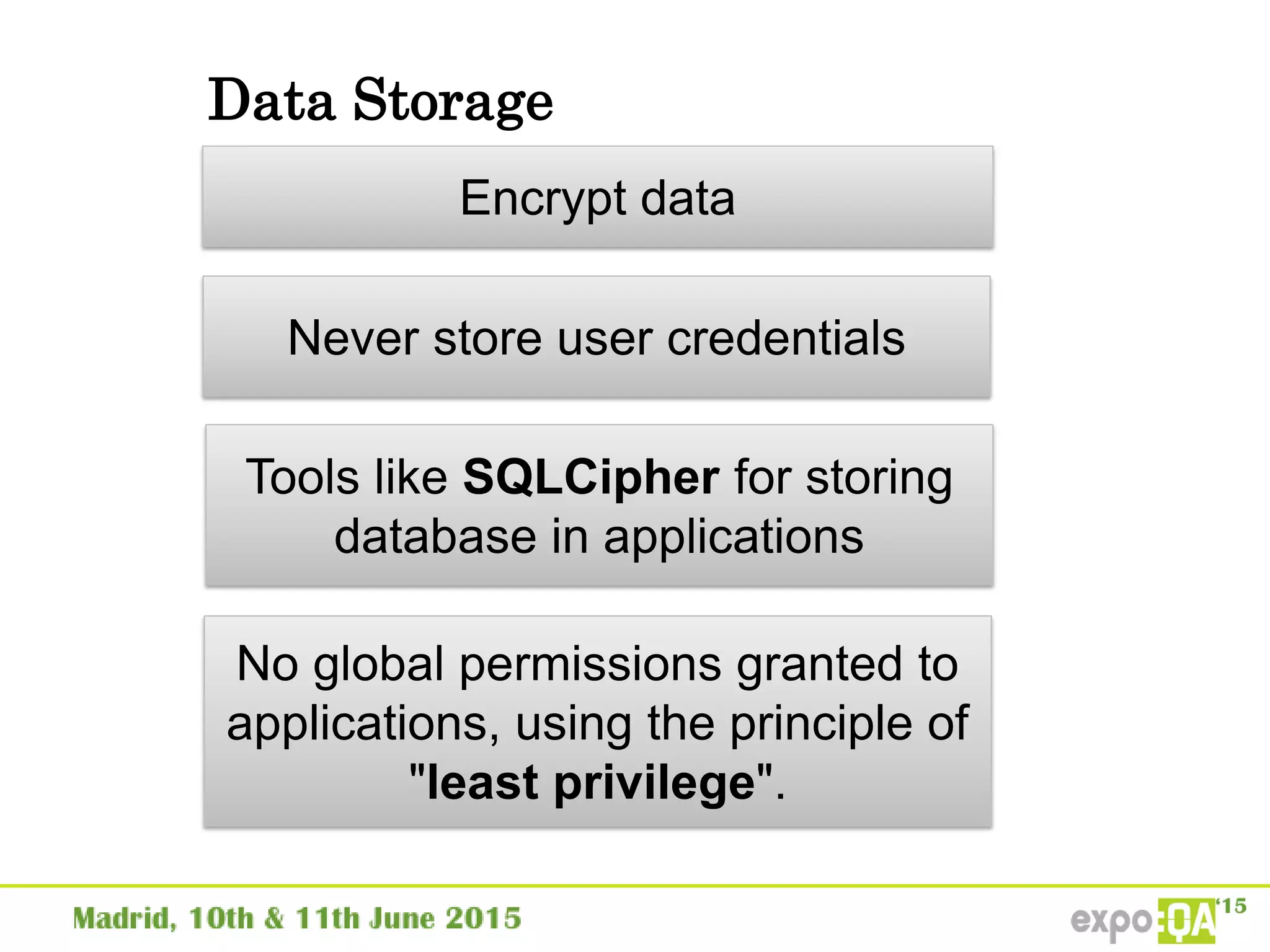
Insecure Data
Storage
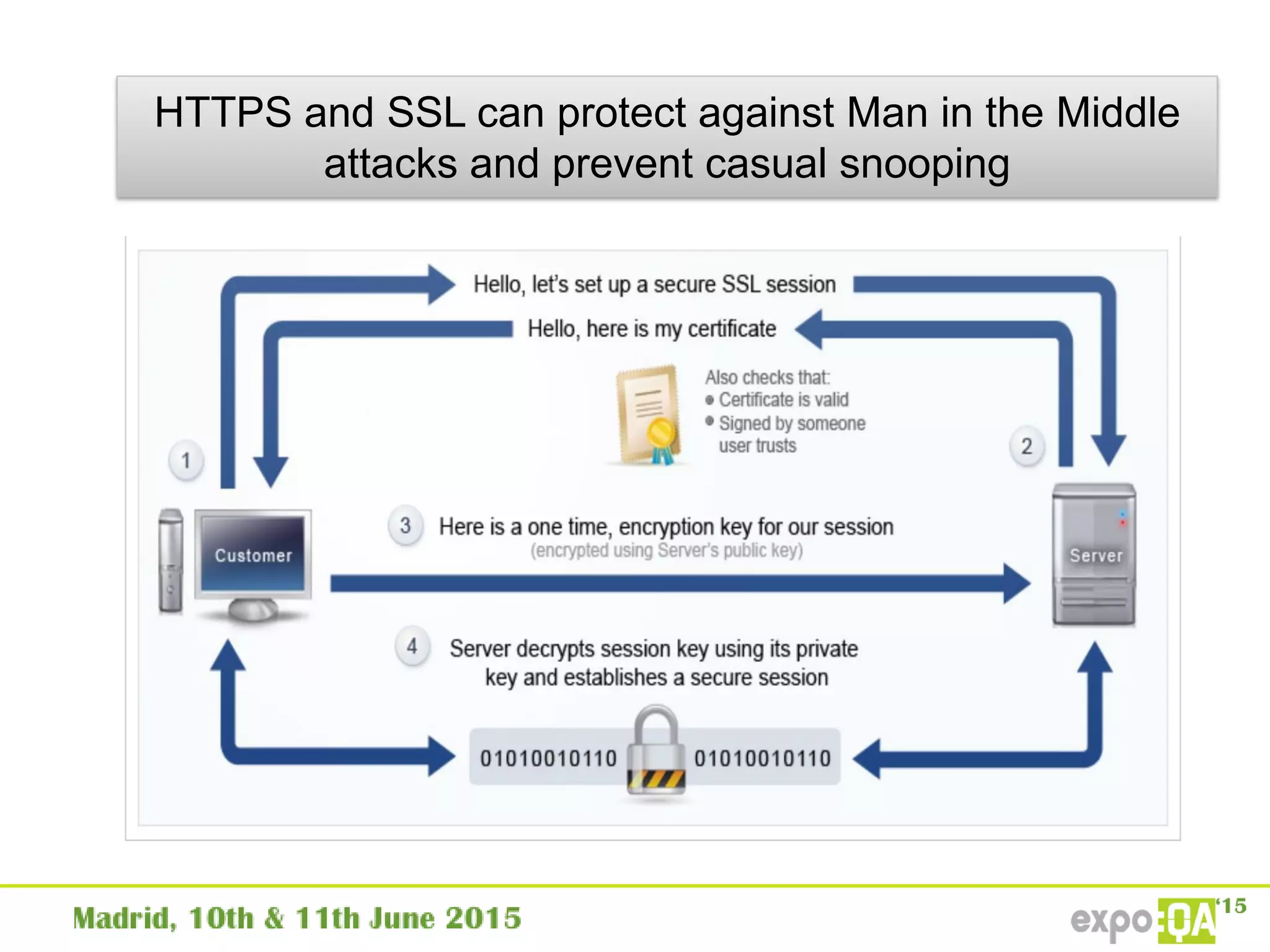
Transport Layer
Protection,
HTTP/SSL
Authorization and
Authentication
Cryptography /
Encrypting data
Session handling
Weak Server Side
Controls in backend
services
Sensitive information
[passwords,API
keys,code ofuscation]
Data Leakage [cache,
logging, temp
directories]](https://image.slidesharecdn.com/securitytestinginmobileapplications-150611164204-lva1-app6891/75/Security-testing-in-mobile-applications-29-2048.jpg)
![Testing components security
Content Providers Data Storage
WebViewServices
NetWork Connections
[HTTP / SSL]
Certificates
Data Encryption
SQLite
Shared Preferences
File storage](https://image.slidesharecdn.com/securitytestinginmobileapplications-150611164204-lva1-app6891/75/Security-testing-in-mobile-applications-30-2048.jpg)
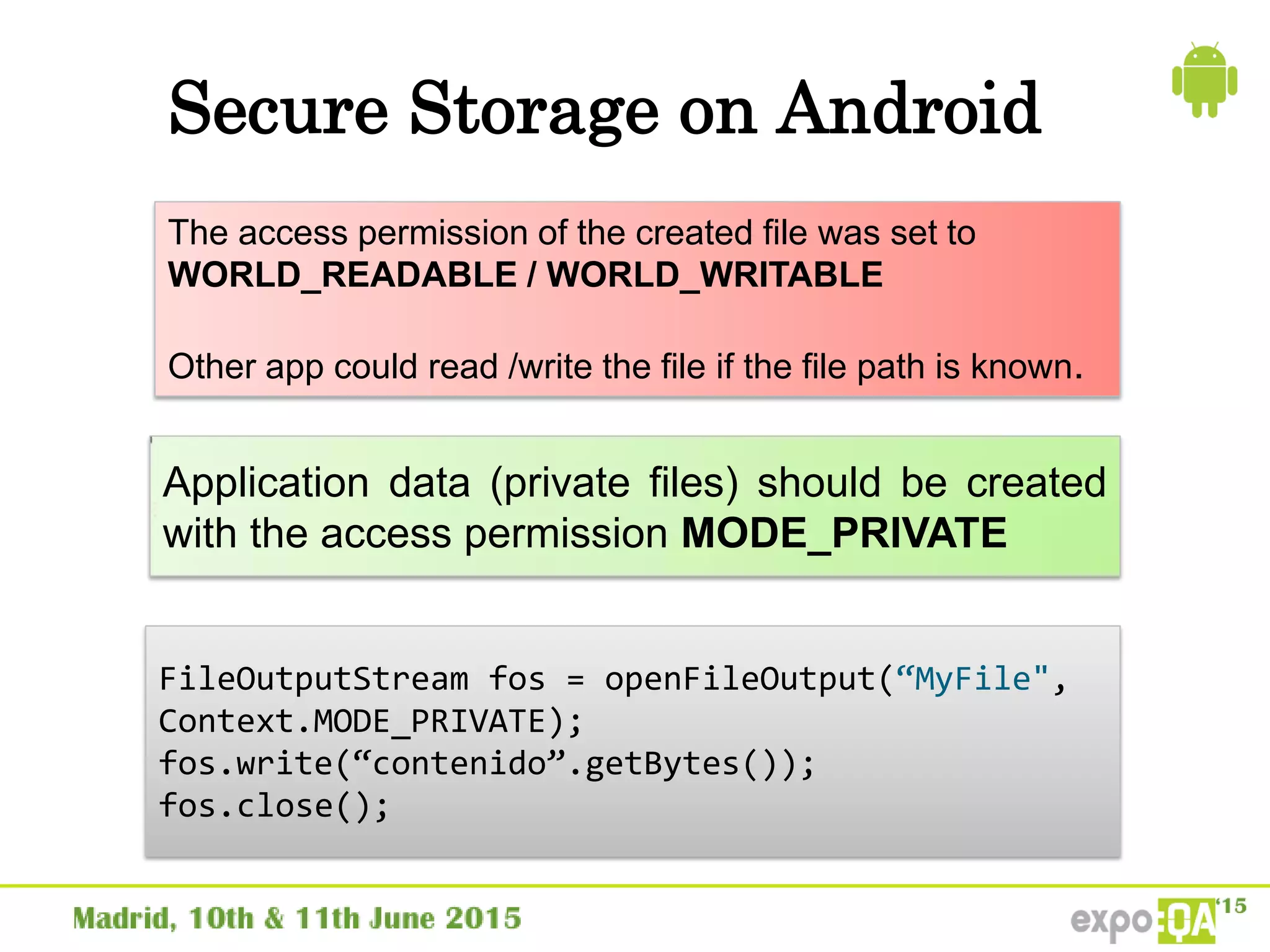
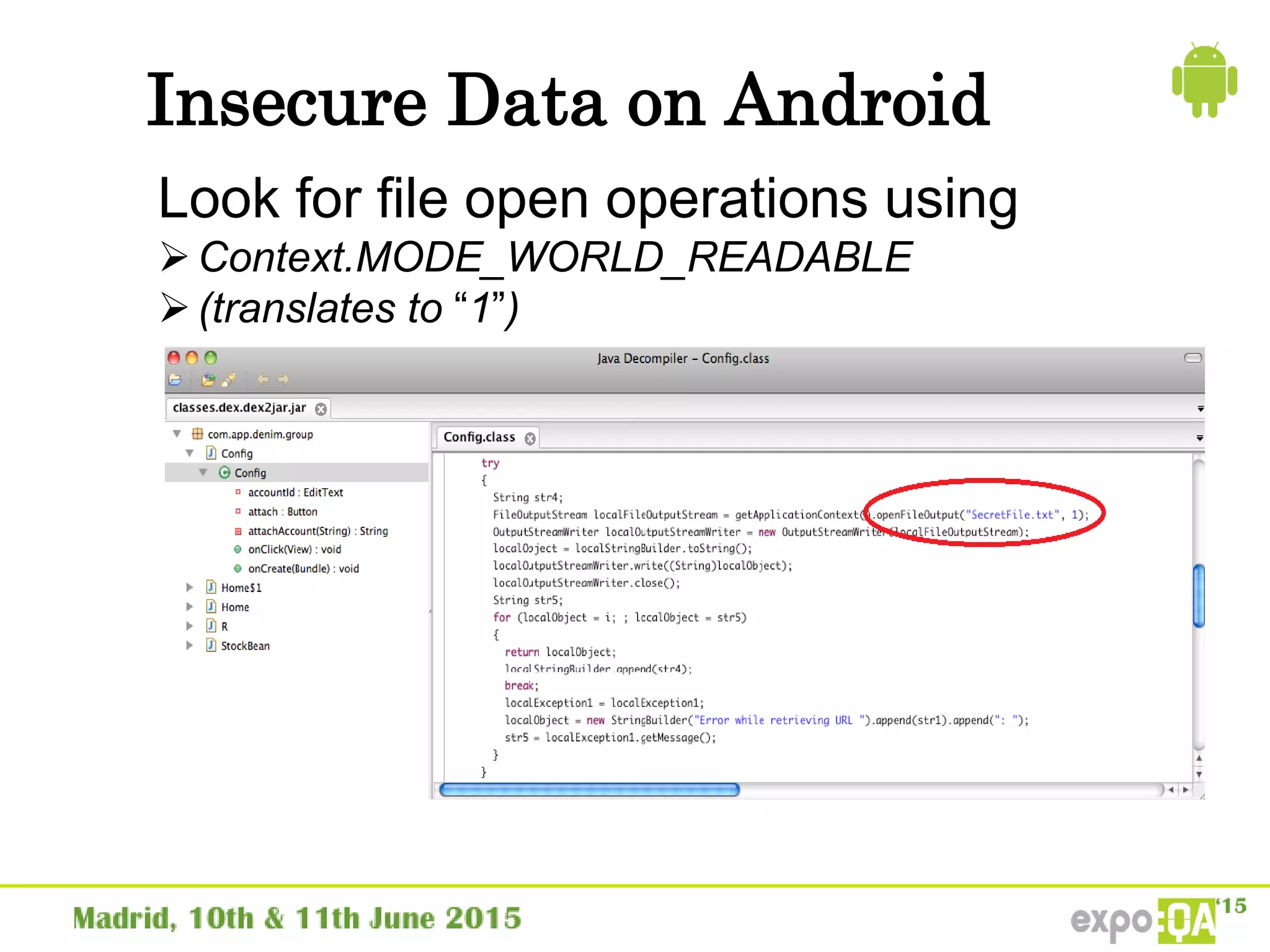
![Secure Storage on iOS
NSFileManager class
NSFileProtectionKey attribute
NSFileProtectionNone – Always accessible
NSFileProtectionComplete – Encrypted on disk
when device is locked or booting
[[NSFileManager defaultManager] createFileAtPath:[self
filePath]
contents:[@"super secret file contents“
dataUsingEncoding:NSUTF8StringEncoding]
attributes:[NSDictionary
dictionaryWithObject:NSFileProtectionComplete
forKey:NSFileProtectionKey]];](https://image.slidesharecdn.com/securitytestinginmobileapplications-150611164204-lva1-app6891/75/Security-testing-in-mobile-applications-35-2048.jpg)