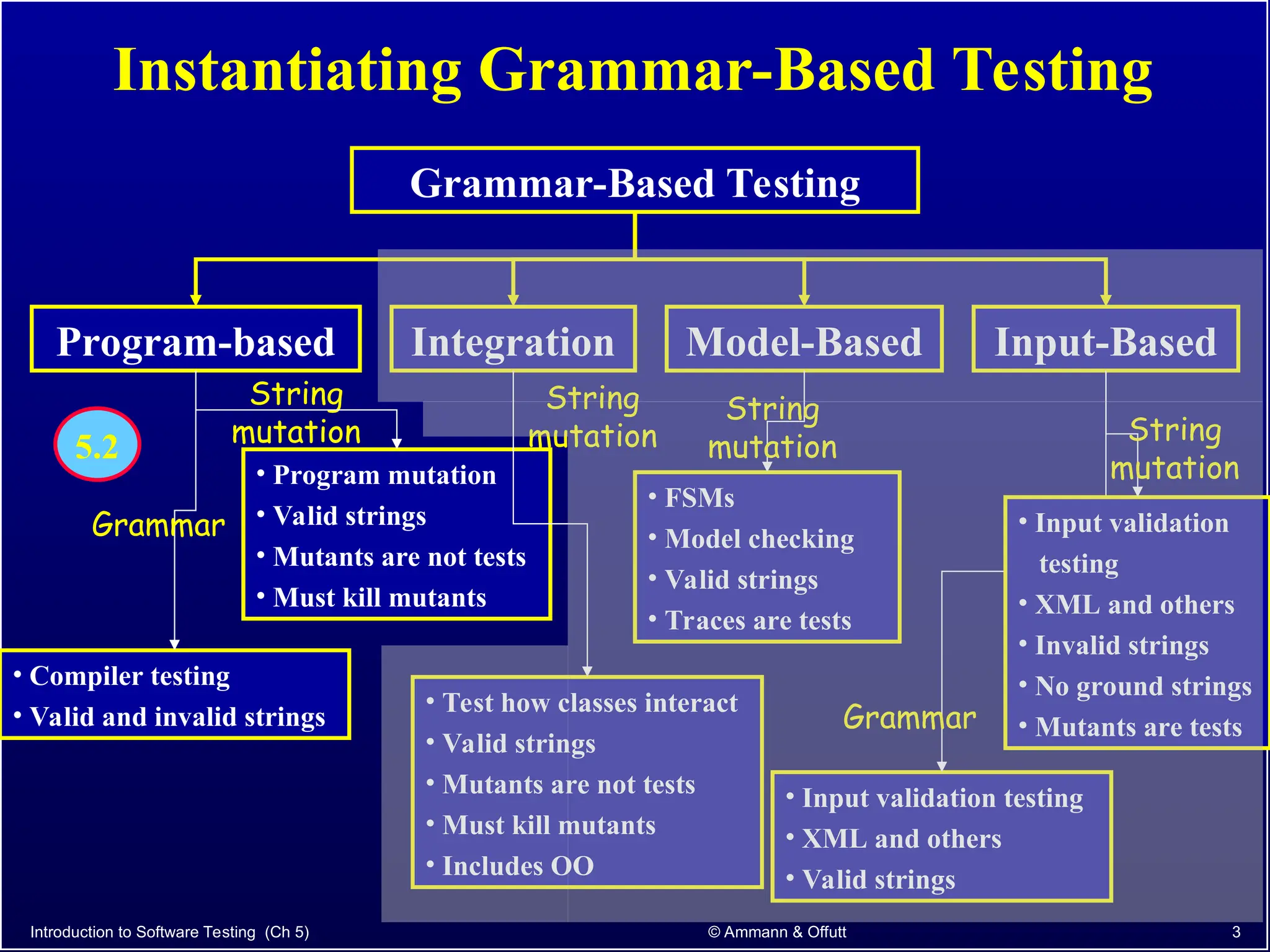
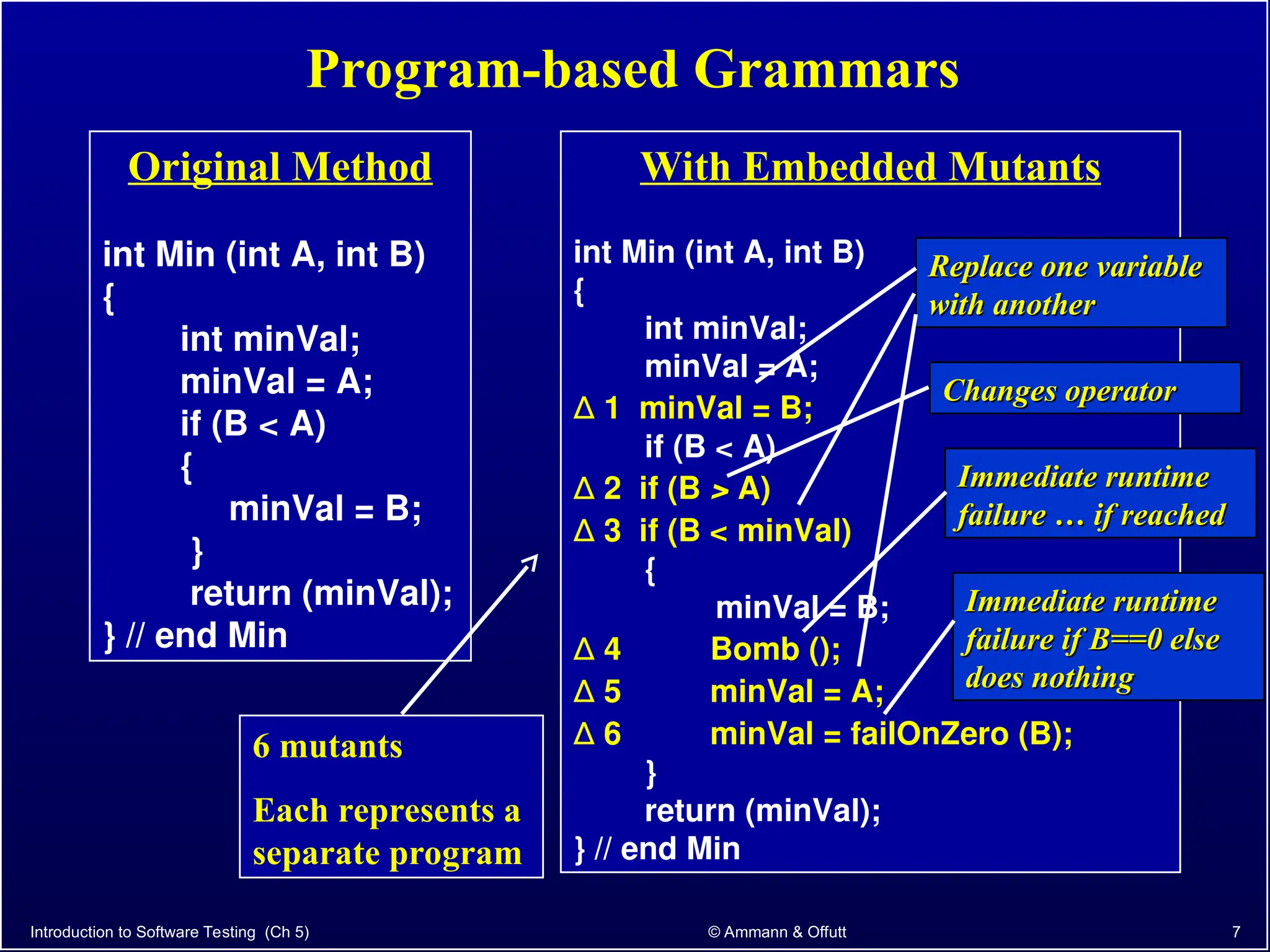
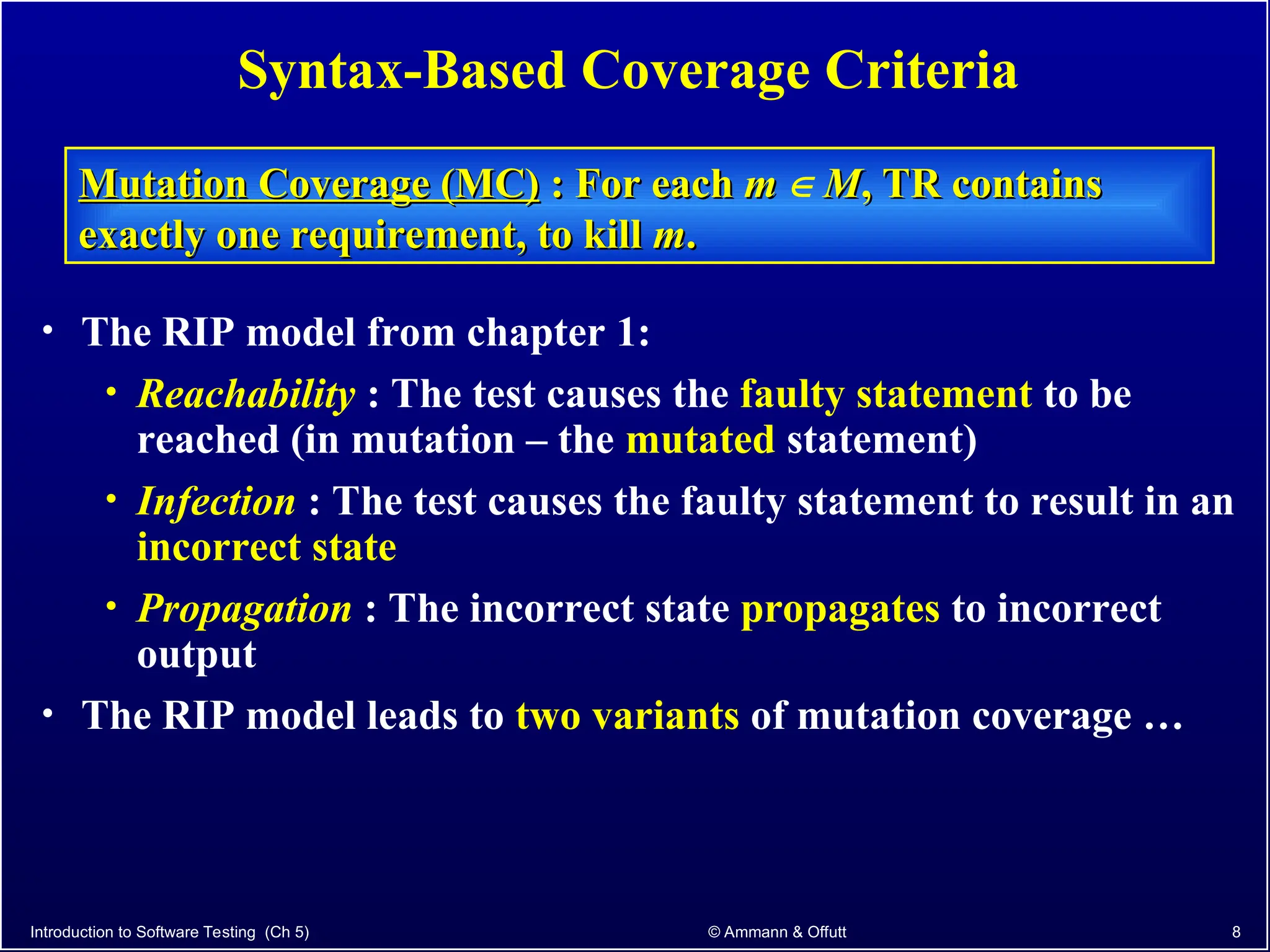
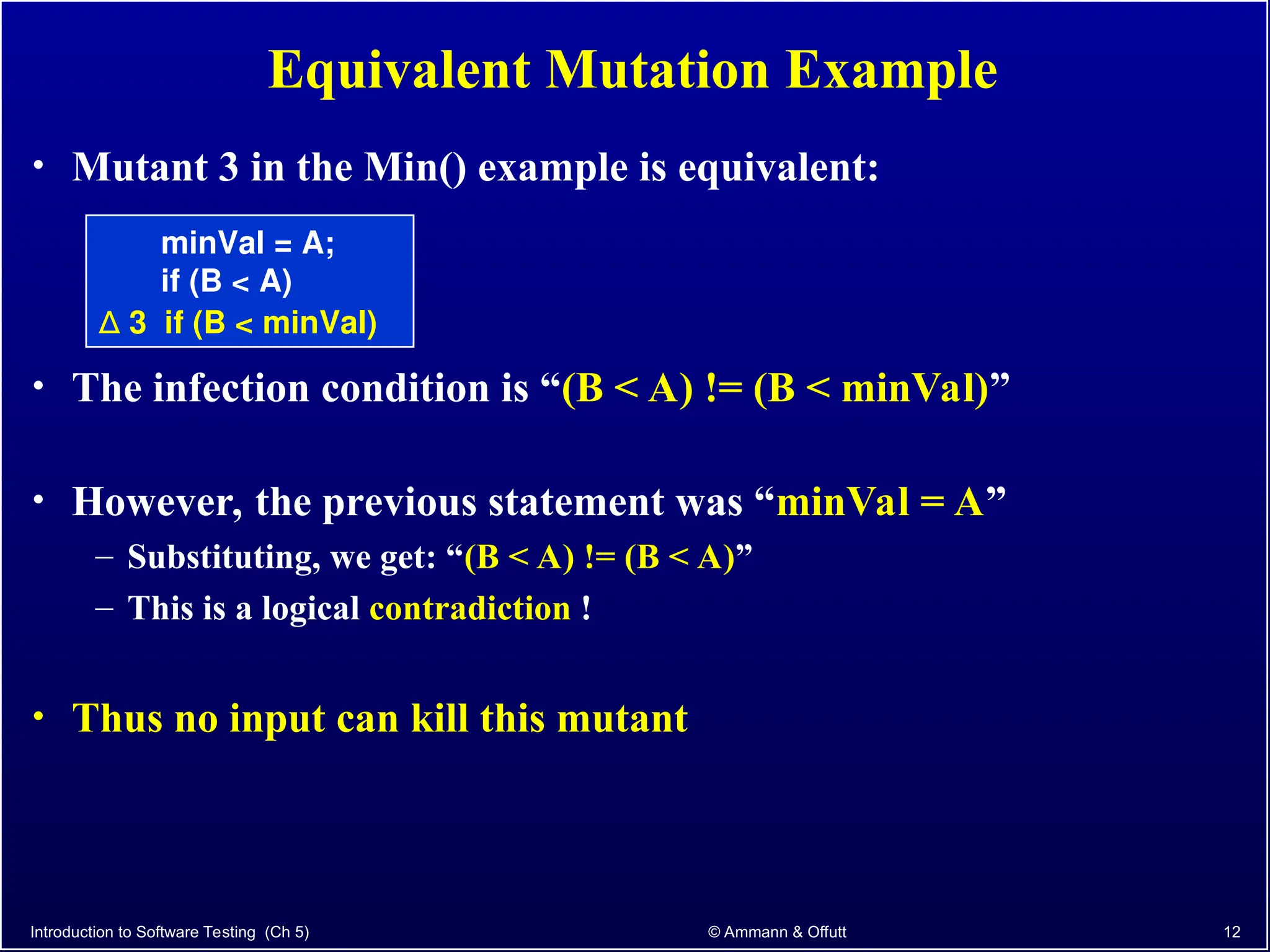
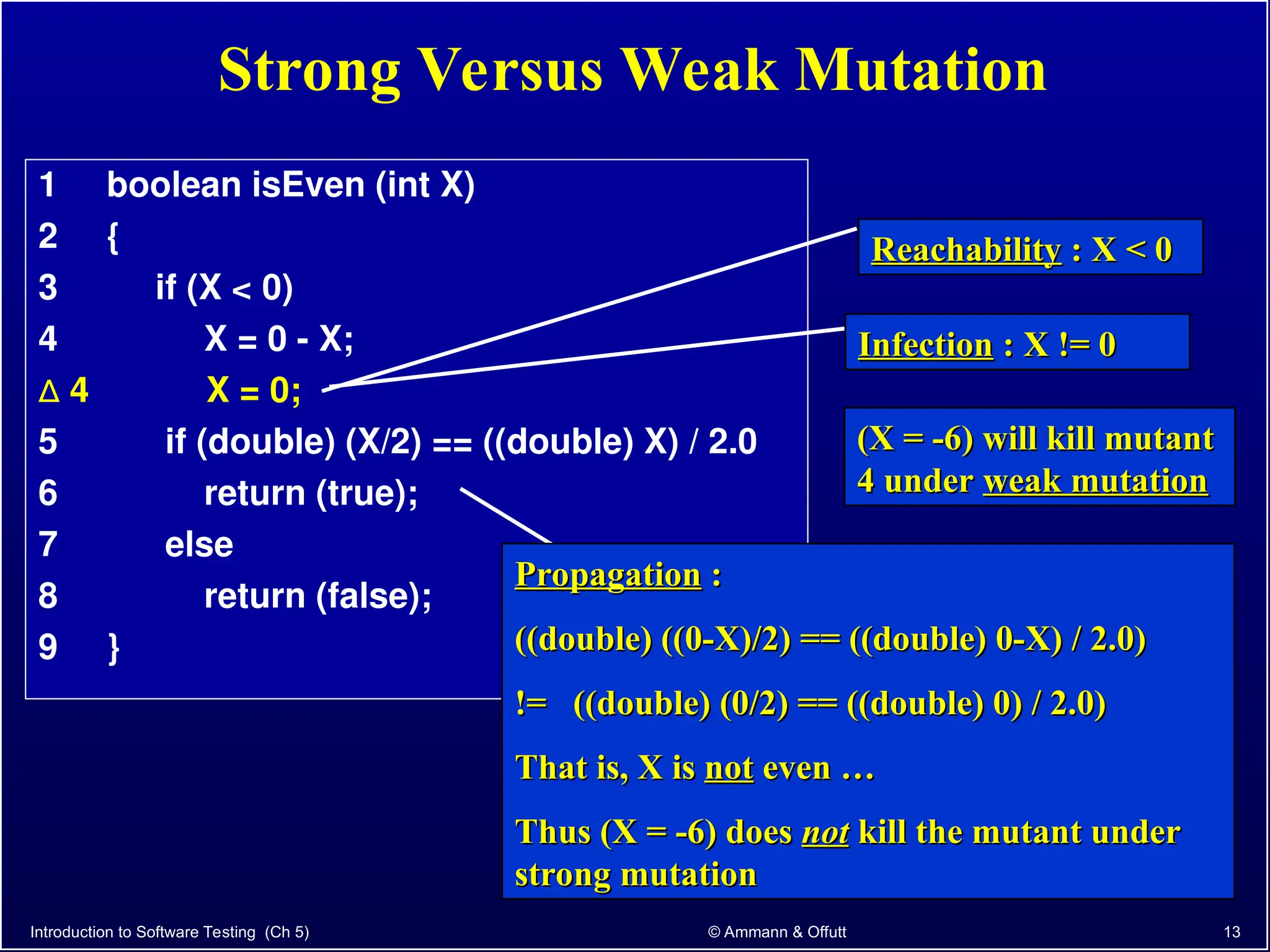
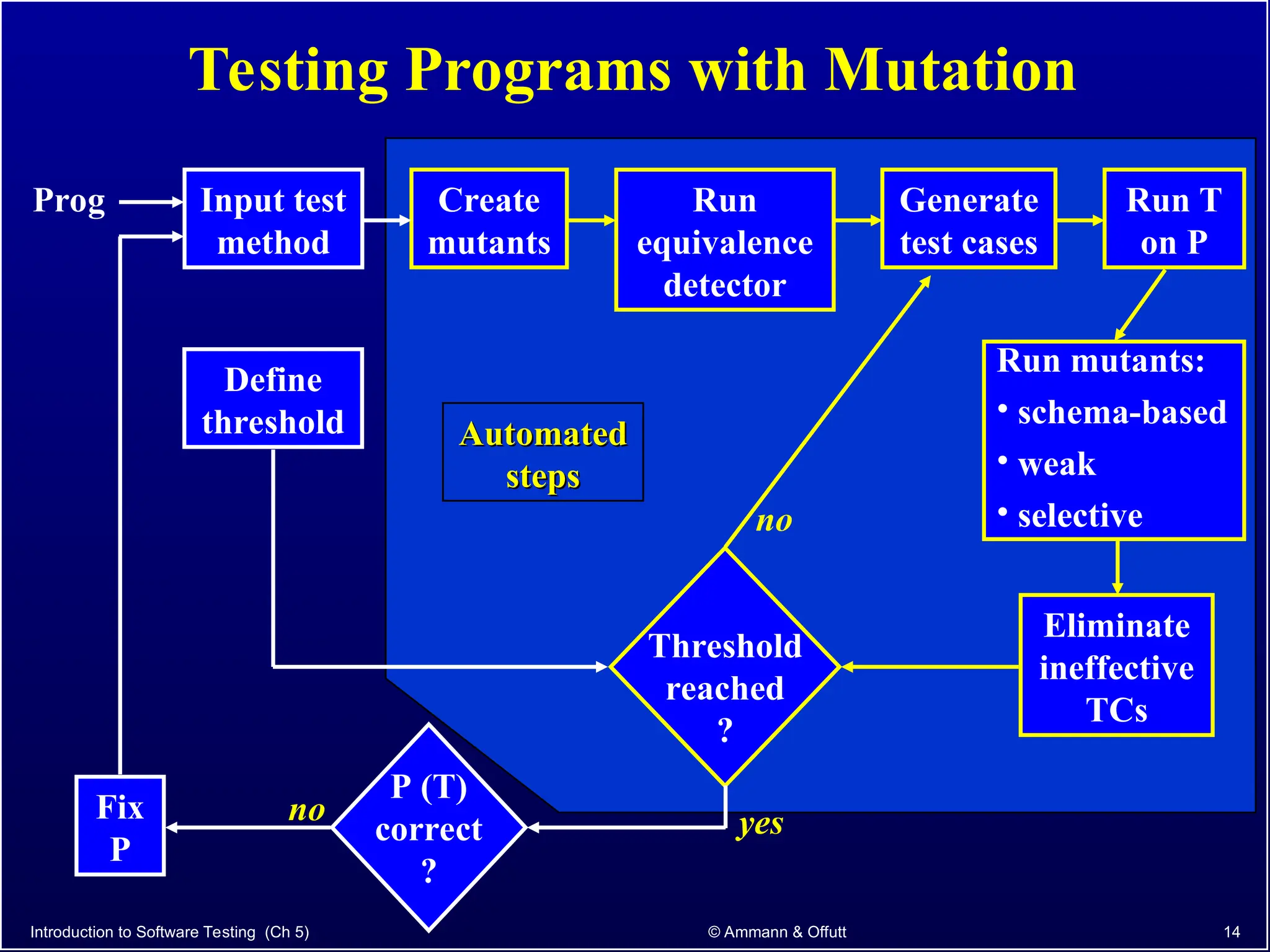
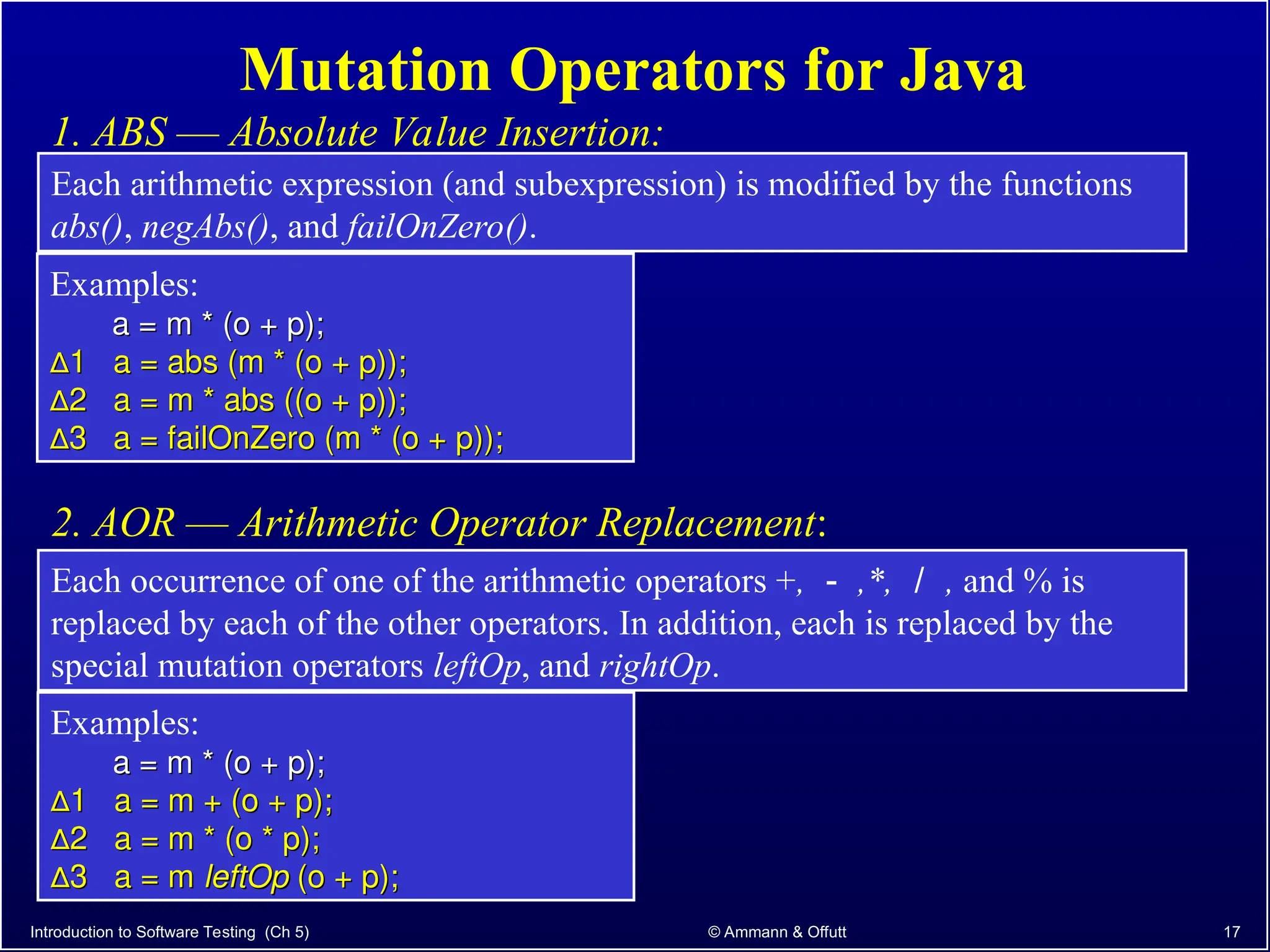
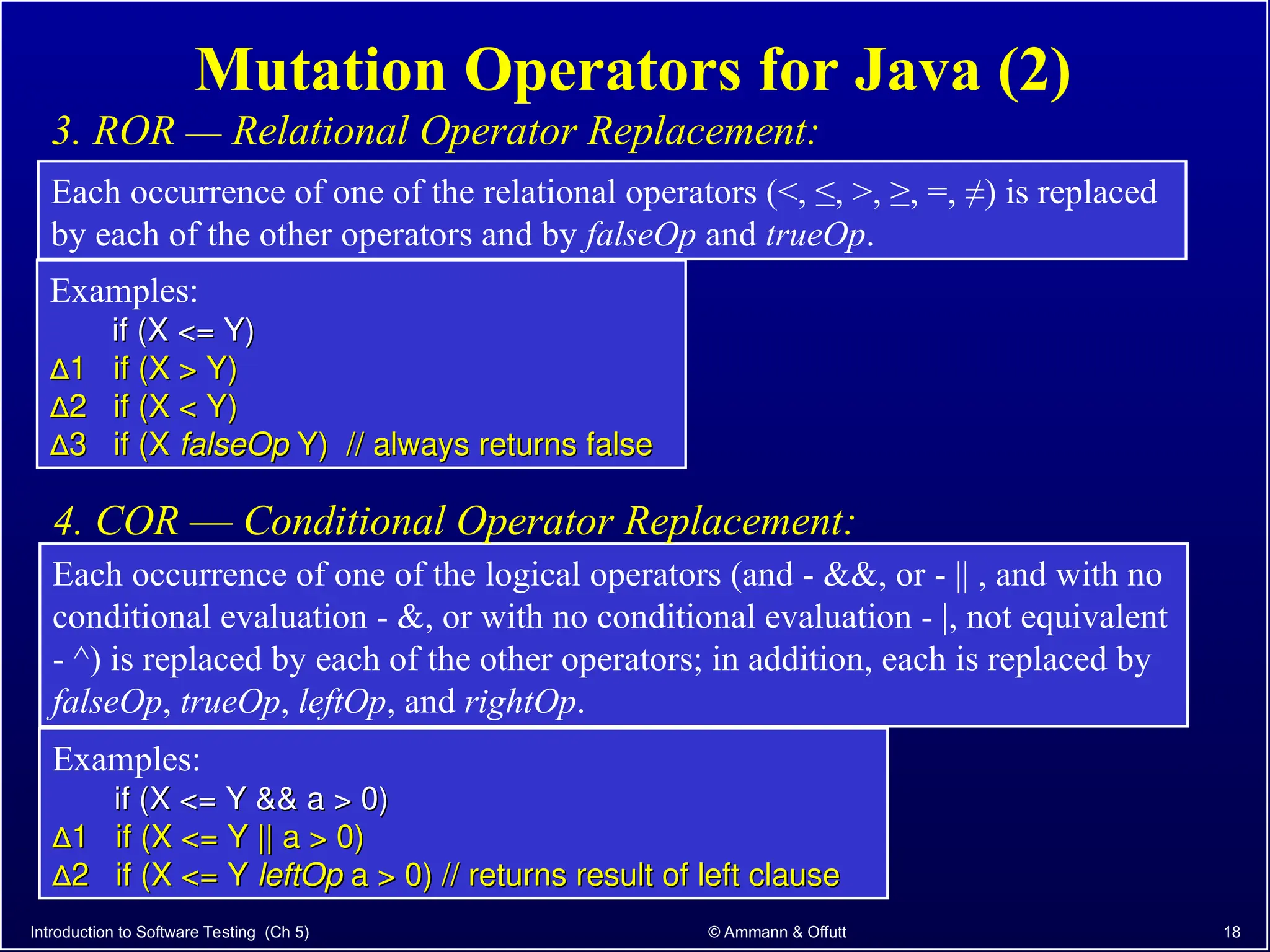
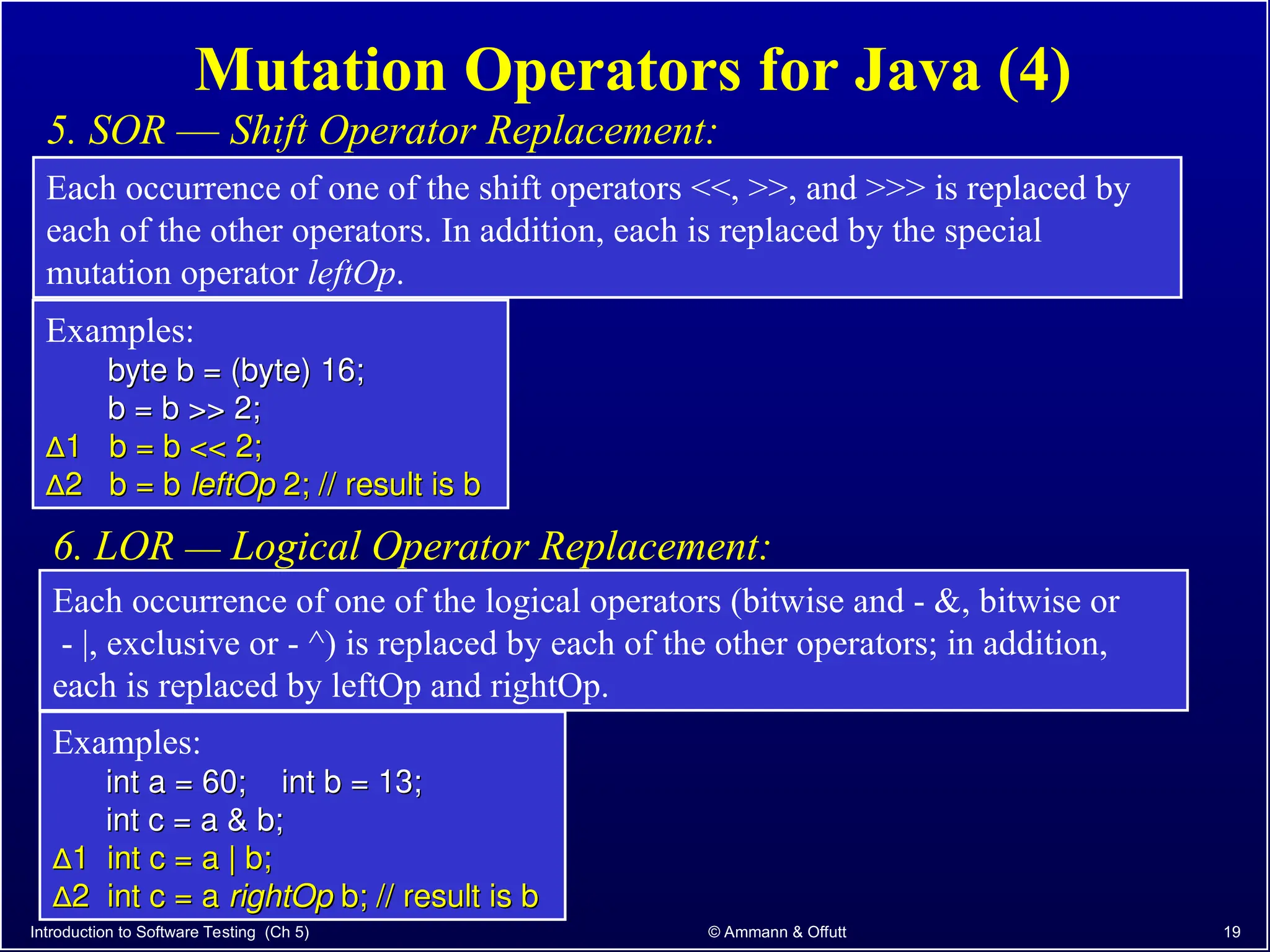
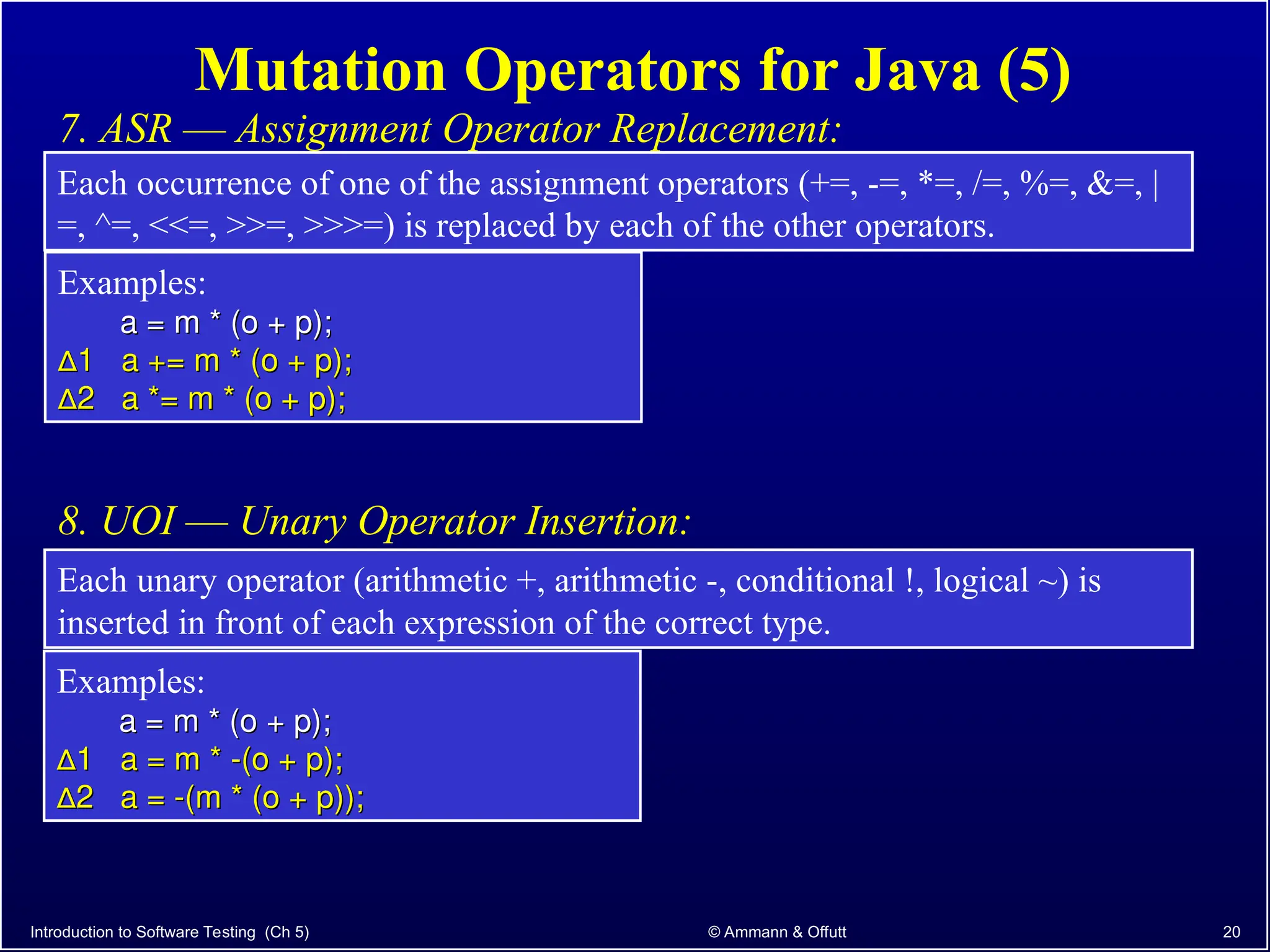
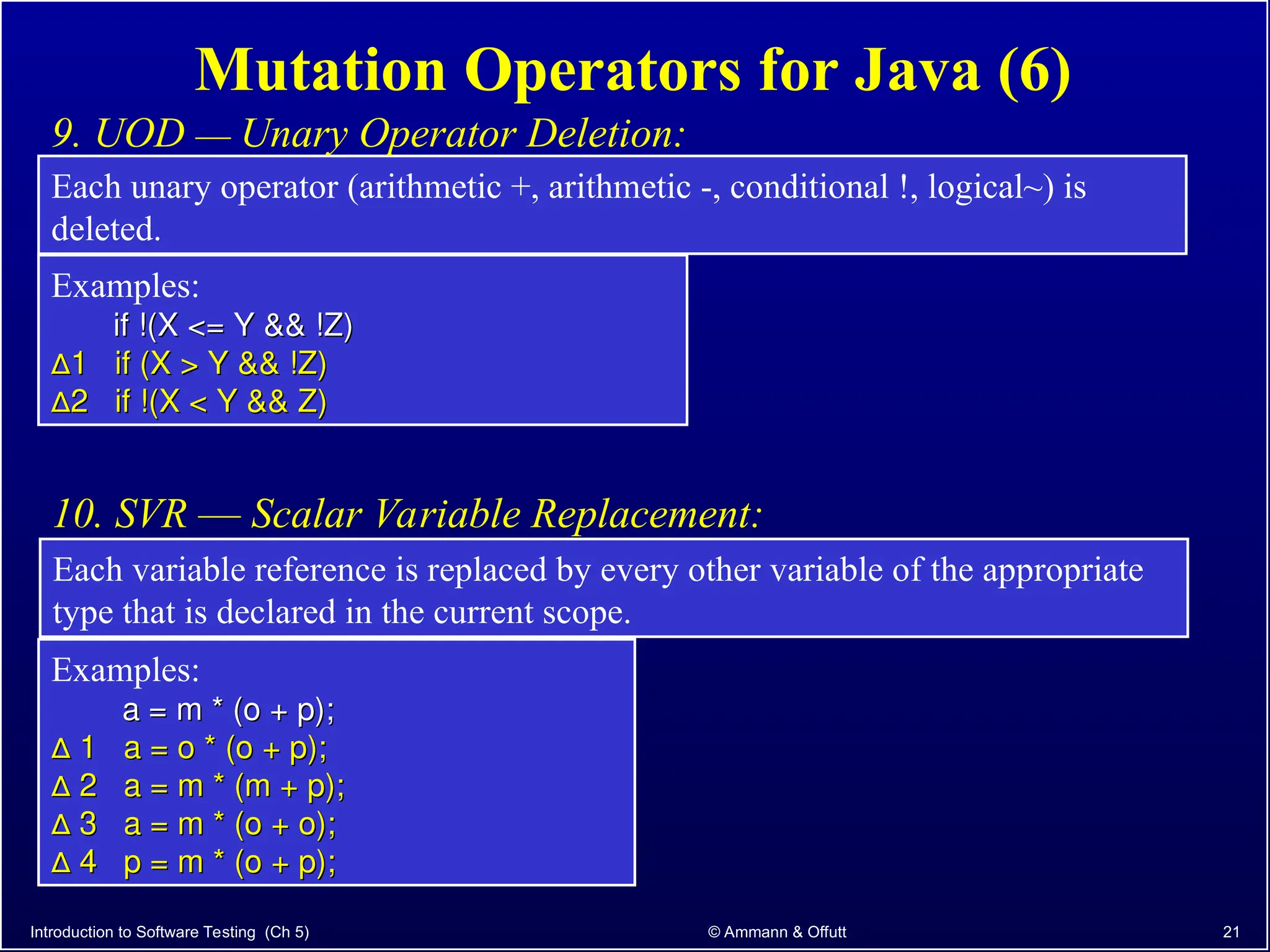
Chapter 5.2 of 'Introduction to Software Testing' discusses syntax-based testing, focusing on grammar-based testing and its application to programs, particularly through mutation testing. It details how mutant programs, derived from the original code, must be tested to identify errors by killing 'mutants' with specific test cases, thus ensuring software correctness. The chapter also explains mutation operators for Java, which introduce changes to the code to assess the effectiveness of tests in detecting faults.