The document discusses information security threats focusing on SQL injection and clickjacking attacks. SQL injection vulnerabilities are highlighted as critical risks for web applications, detailing how they allow attackers to access databases and suggesting best practices for prevention, such as using stored procedures and dynamic SQL with caution. Additionally, clickjacking attacks are explained, outlining their mechanics and defenses like frame busting to protect users from malicious interactions.



![Important concepts
SQL: is Structured Query Language, which is a computer language for storing, manipulating
and retrieving data stored in relational database.
Reference: [1] SQL TUTORIAL-Simply Easy Learning by tutorialspoint.com](https://image.slidesharecdn.com/sqlandclickjackingattacks-170421212706/75/SQL-Injection-and-Clickjacking-Attack-in-Web-security-5-2048.jpg)
![What is SQL injection?
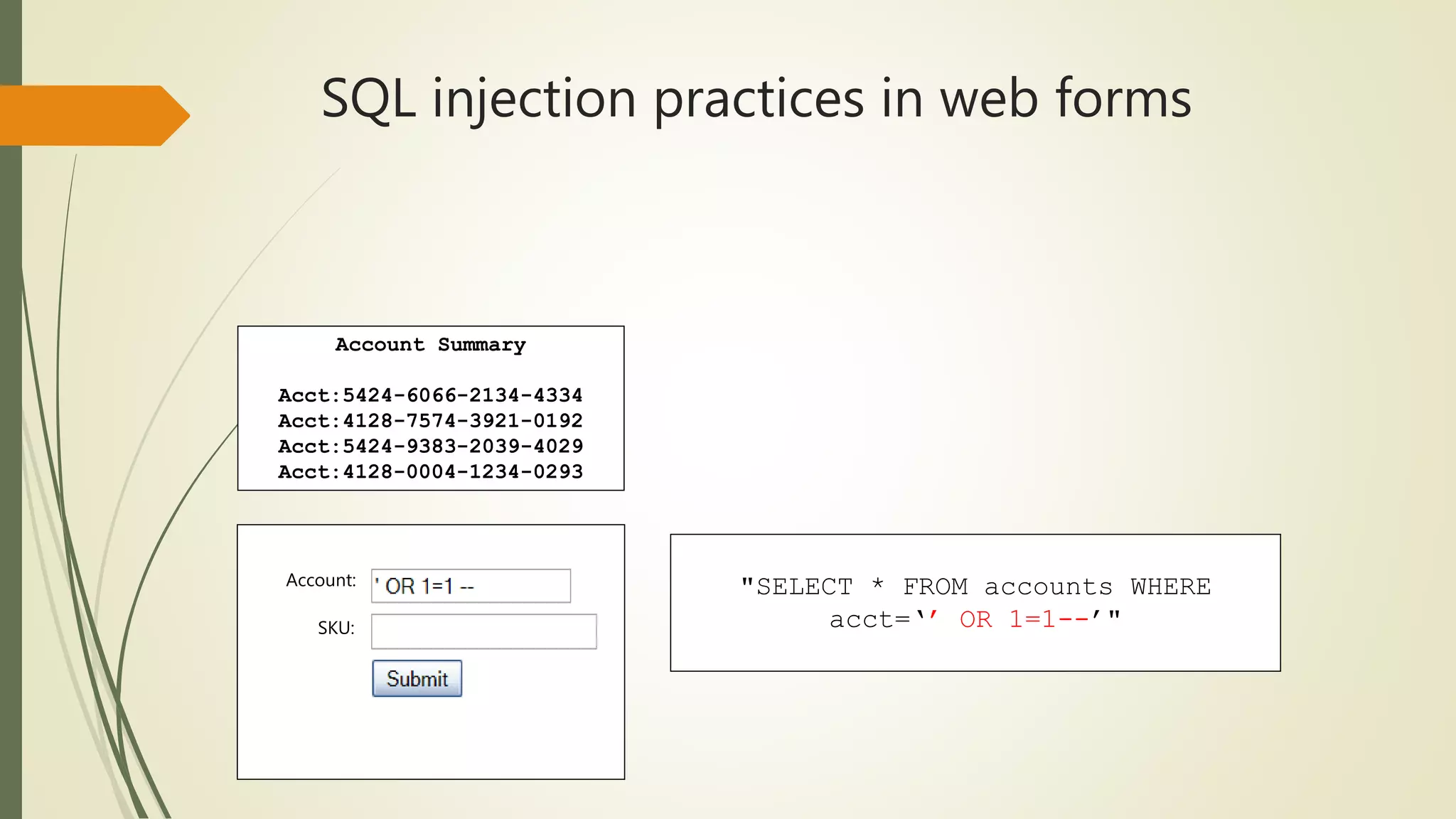
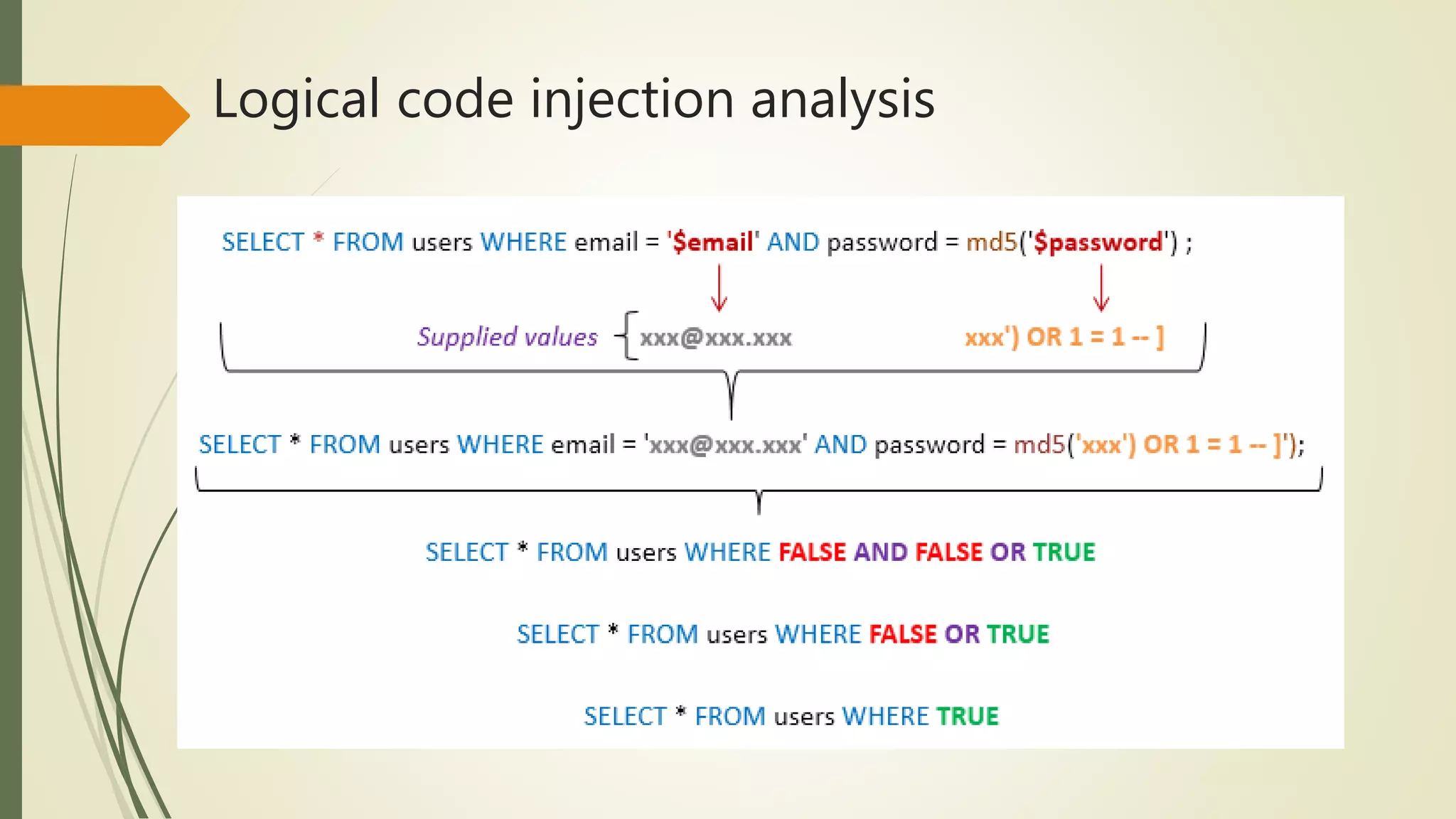
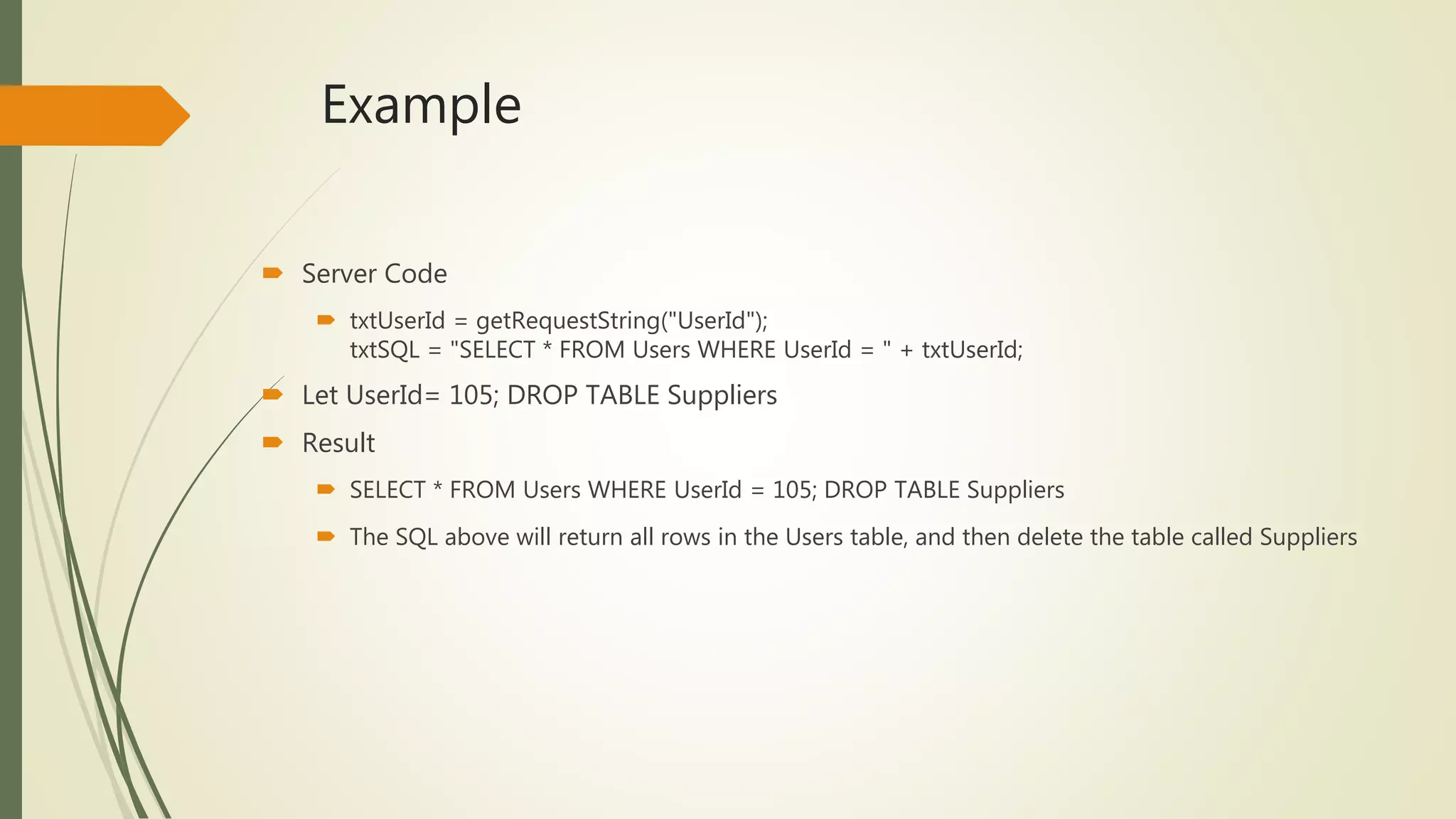
SQL injection vulnerabilities have been described as one of the most serious threats for Web
applications [2, 3]. Web applications that are vulnerable to SQL injection may allow an attacker
to gain complete access to their underlying databases.
Reference:
[2] D. Aucsmith. Creating and Maintaining Software that Resists Malicious Attack. http://www.gtisc.gatech.edu/bio
aucsmith.html, September 2004. Distinguished Lecture Series.
[3] T. O. Foundation. Top Ten Most Critical Web Application Vulnerabilities, 2005. http:
//www.owasp.org/documentation/topten.html](https://image.slidesharecdn.com/sqlandclickjackingattacks-170421212706/75/SQL-Injection-and-Clickjacking-Attack-in-Web-security-6-2048.jpg)
![SQL injection architecture
Reference: [4] System Architecture for SQL Injection and Insider Misuse Detection System for DBMS , Aziah Asmawi Faculty of Computer
Science and Information System Universiti Teknologi Malaysia aziah@fsktm.upm.edu.my , © 2008 IEEE](https://image.slidesharecdn.com/sqlandclickjackingattacks-170421212706/75/SQL-Injection-and-Clickjacking-Attack-in-Web-security-7-2048.jpg)


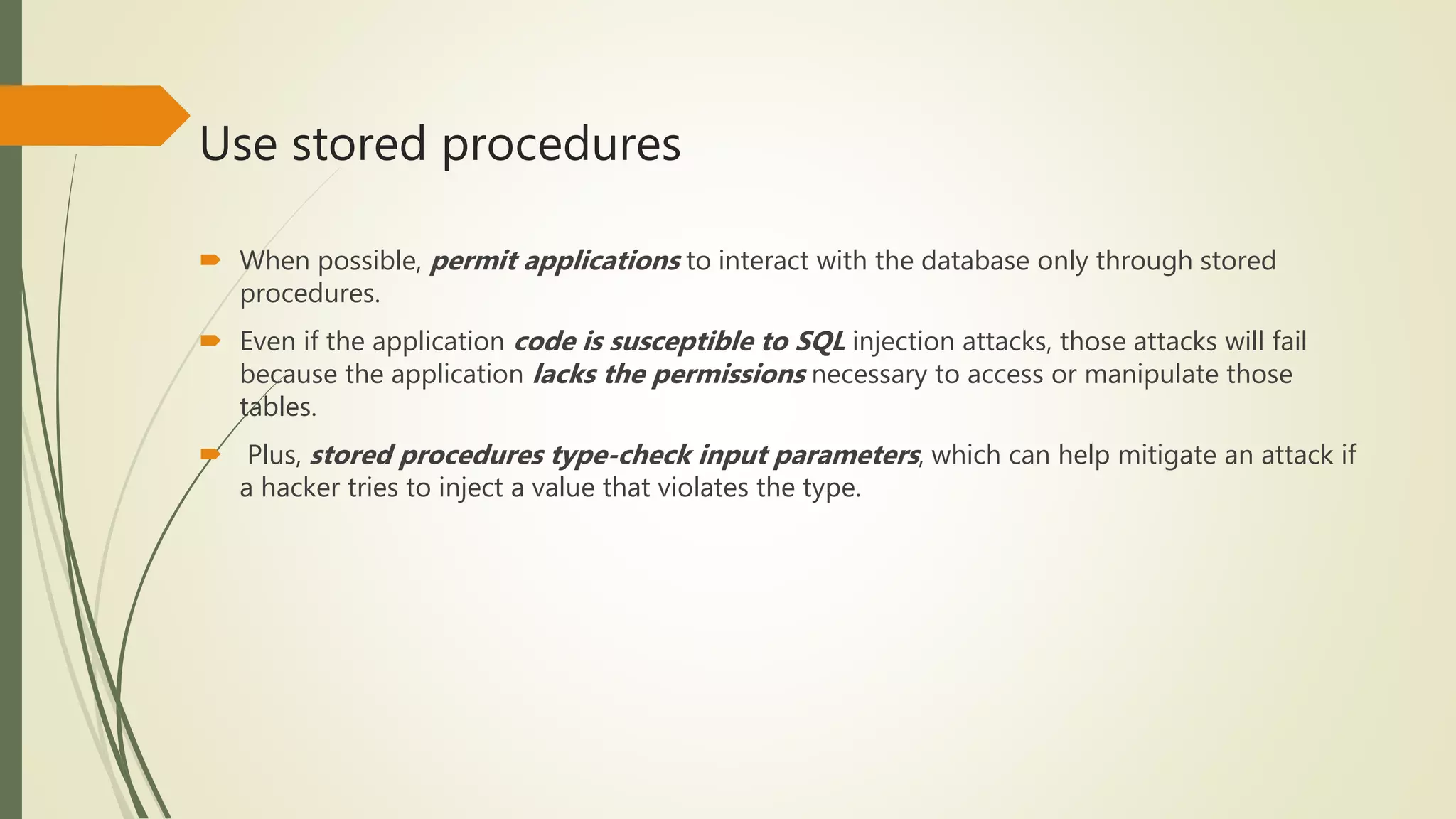
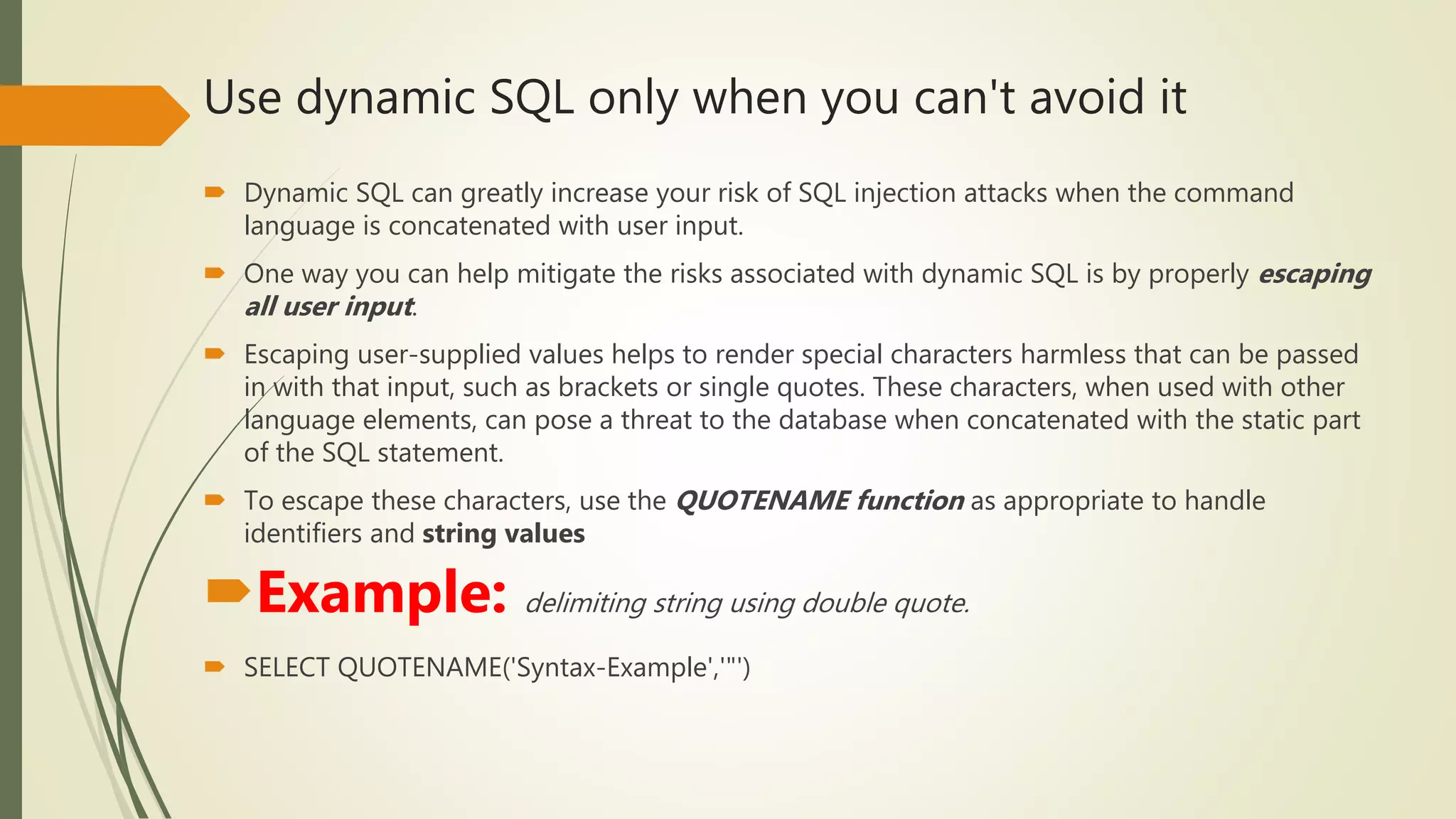
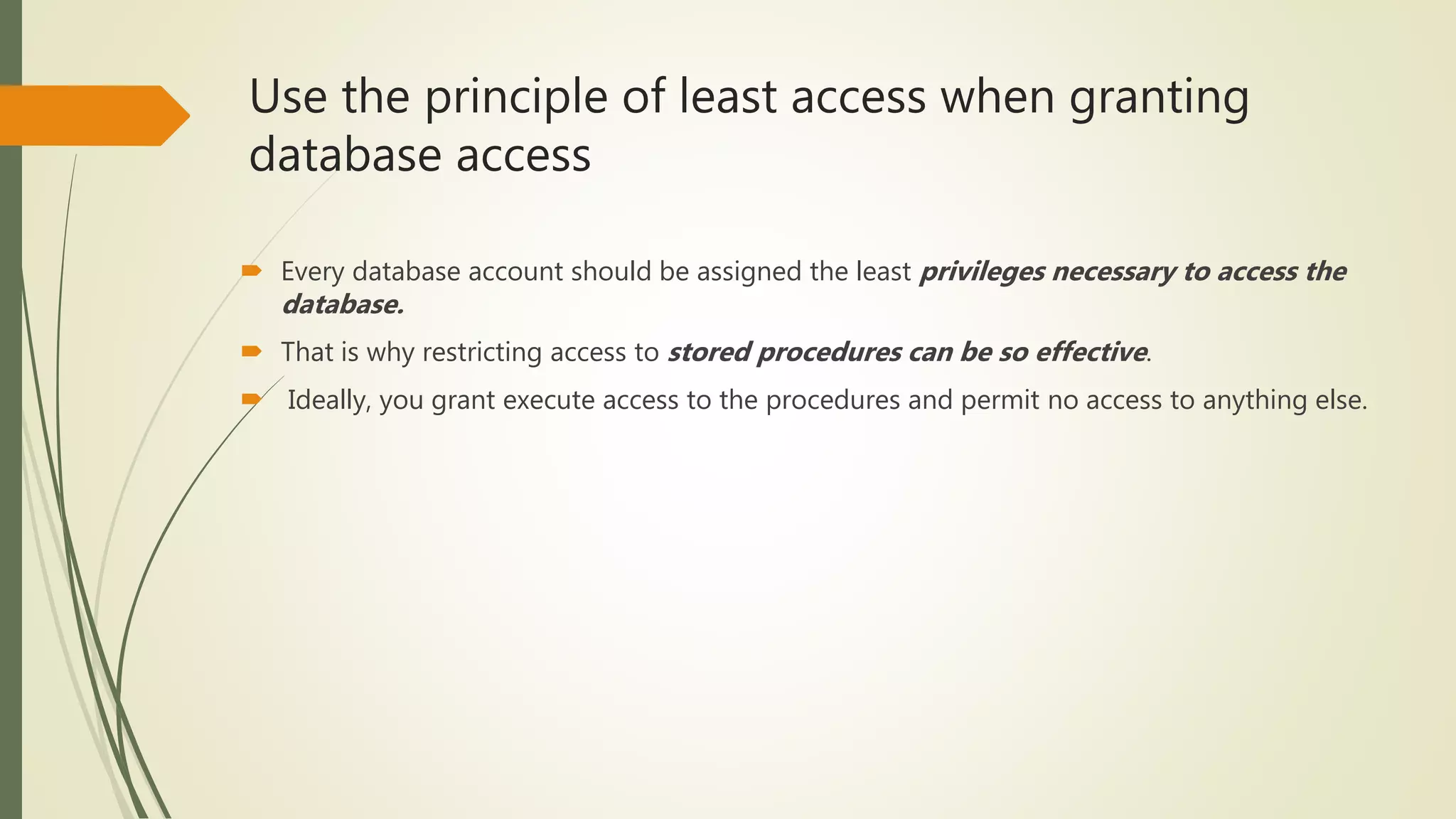
![Best practices for preventing SQL injection attacks
Use stored procedures
Use dynamic SQL only when you can't avoid it
Use the principle of least access when granting database access
Use testing and monitoring to guard against SQL injection
[5] http://searchsqlserver.techtarget.com/tip/Best-practices-for-preventing-a-SQL-
injection-attack](https://image.slidesharecdn.com/sqlandclickjackingattacks-170421212706/75/SQL-Injection-and-Clickjacking-Attack-in-Web-security-13-2048.jpg)

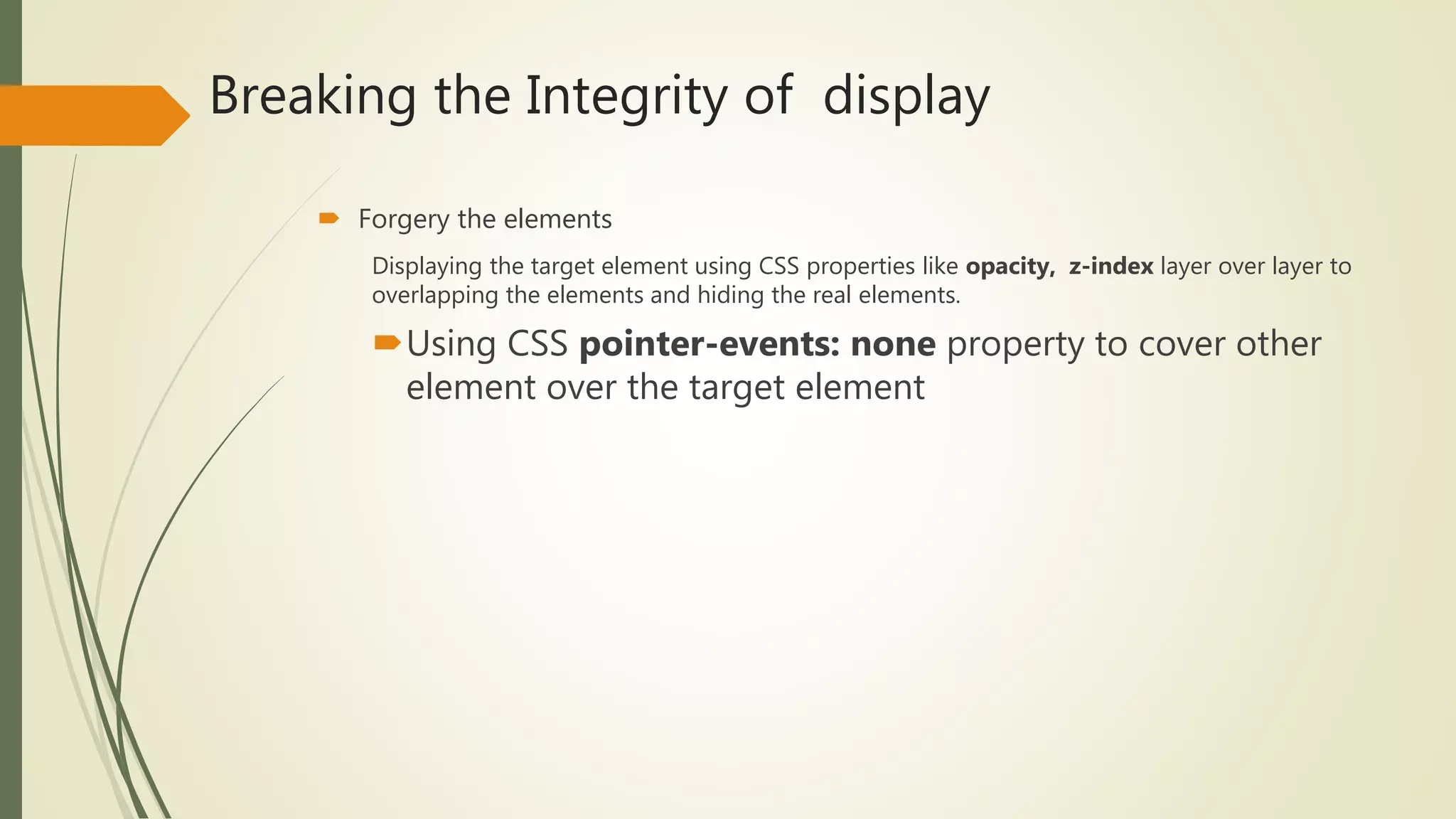
![Frame busting and Clickjacking attacks
Clickjacking attacks:is a malicious technique of tricking a Web user into
clicking on something different from what the user perceives they are
clicking on
Frame busting: is considered the most common defence to the Web
framing attacks to clickjacking by prevents a site from functioning when
loaded inside a Frame.
References:
[6] Busting Frame Busting: a Study of Clickjacking Vulnerabilities on Popular Sites, June 7, 2010.
2013 11th International Conference on Frontiers of Information Technology, On Detection and Prevention of
Clickjacking Attack for OSNs, © 2013 IEEE.
[7] https://www.microsoft.com/en-us/research/publication/clickjacking-attacks-and-defenses/](https://image.slidesharecdn.com/sqlandclickjackingattacks-170421212706/75/SQL-Injection-and-Clickjacking-Attack-in-Web-security-20-2048.jpg)
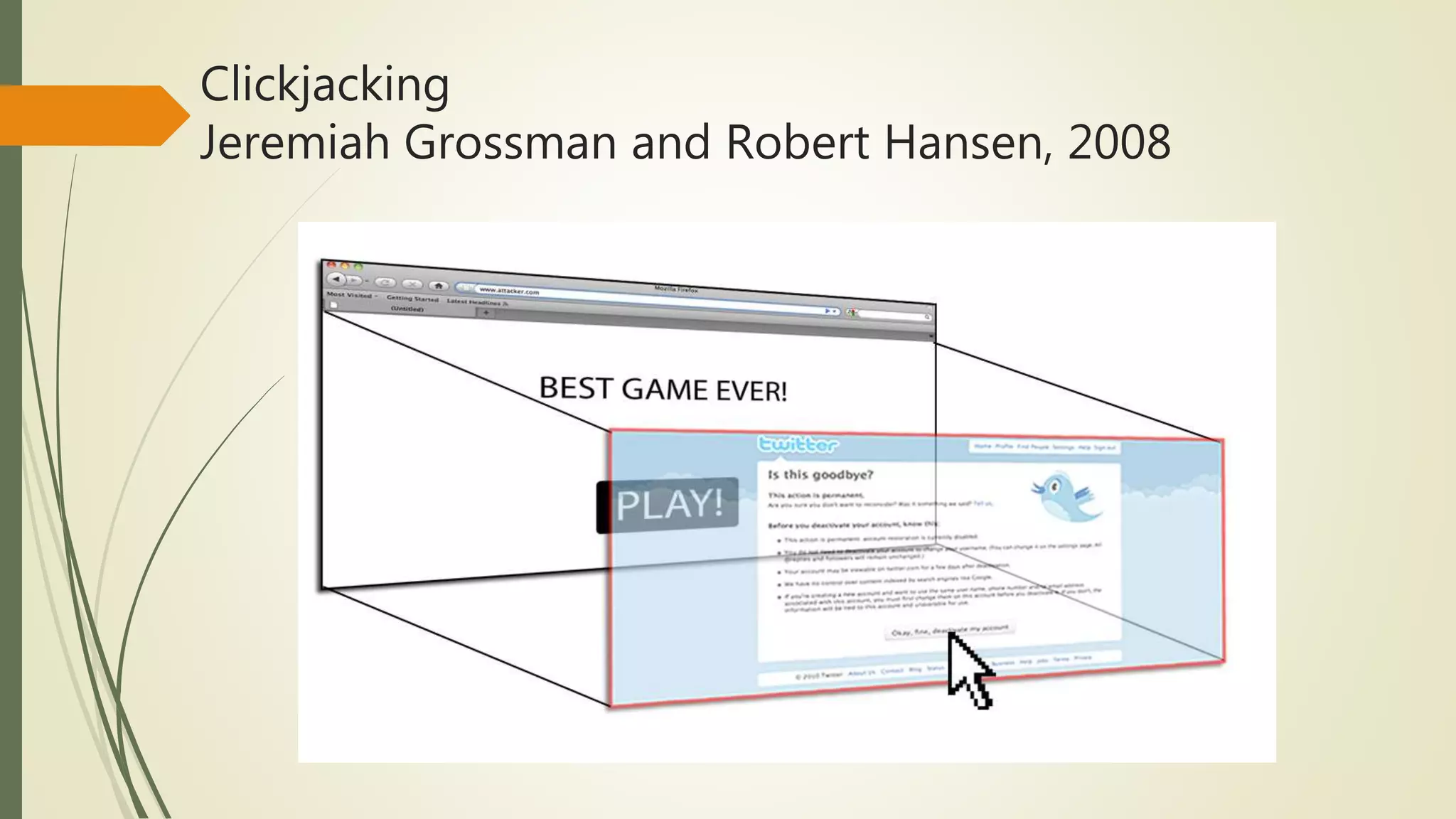
![An attacker builds a CJ attack in three steps:
The attacker creates a Web page (called a displayed page, or DP) including parts
that look like the usual clickable objects, such as text hyperlinks or buttons.
The attacker then creates a malicious page (called a hidden page, or HP) including
clickable objects whose position on the page fits perfectly with the previous ones.
The attacker then displays the DPs on top of the HPs so that visitors to the page
might decide to click on the DP’s fake hyperlink, thus clicking on a real HP
hyperlink, which could be the starting point of an attack on the system.
Reference: [8] Attack Trends Editors: Marcus Sachs, marcus.sachs@verizon.com David Ahmad,drma@mac.com](https://image.slidesharecdn.com/sqlandclickjackingattacks-170421212706/75/SQL-Injection-and-Clickjacking-Attack-in-Web-security-23-2048.jpg)
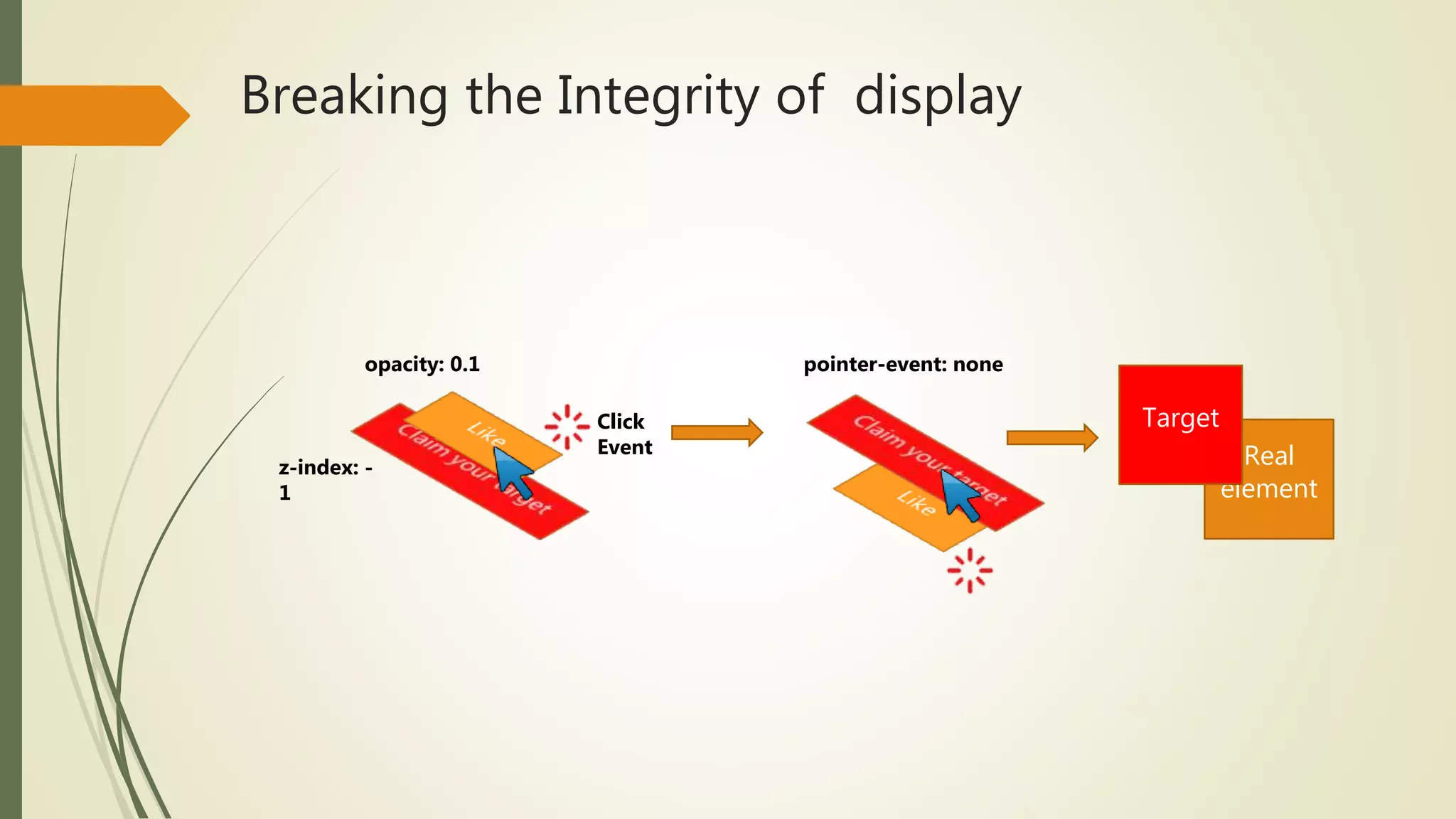
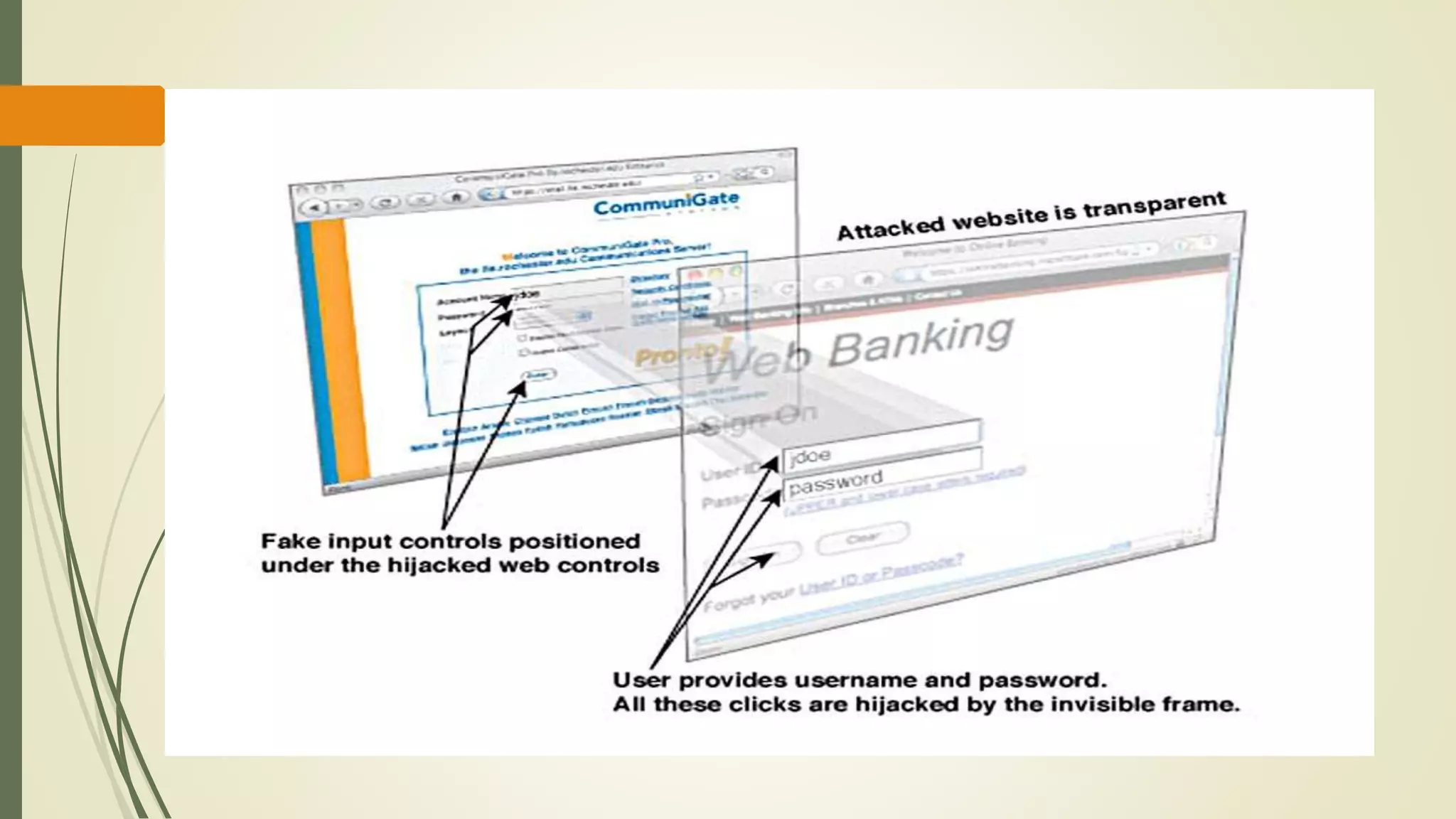
![Visualization of a clickjacking attack
The victim site is framed in a transparent iframe that is put on top of what
appears to be a normal page.
When users interact with the normal page, they are unwittingly interacting
with the victim site.
Reference: [9] Busting Frame Busting: a Study of Clickjacking Vulnerabilities on Popular Sites, June 7,](https://image.slidesharecdn.com/sqlandclickjackingattacks-170421212706/75/SQL-Injection-and-Clickjacking-Attack-in-Web-security-24-2048.jpg)
![Framebuster
A framebuster is a piece of JavaScript code that prevents a web page from being
rendered within a frame. There are many variations of framebusters in use in
different web sites. As recommended by the OWASP community, the most
reliable framebuster is:
o <head>
o <style> body { display : none;} </style>
o </head>
o <body> <
o script> if (self == top)
o { var theBody = document.getElementsByTagName('body')[0]; theBody.style.display = "block";
}
o else { top.location = self.location; }
o </script>](https://image.slidesharecdn.com/sqlandclickjackingattacks-170421212706/75/SQL-Injection-and-Clickjacking-Attack-in-Web-security-25-2048.jpg)