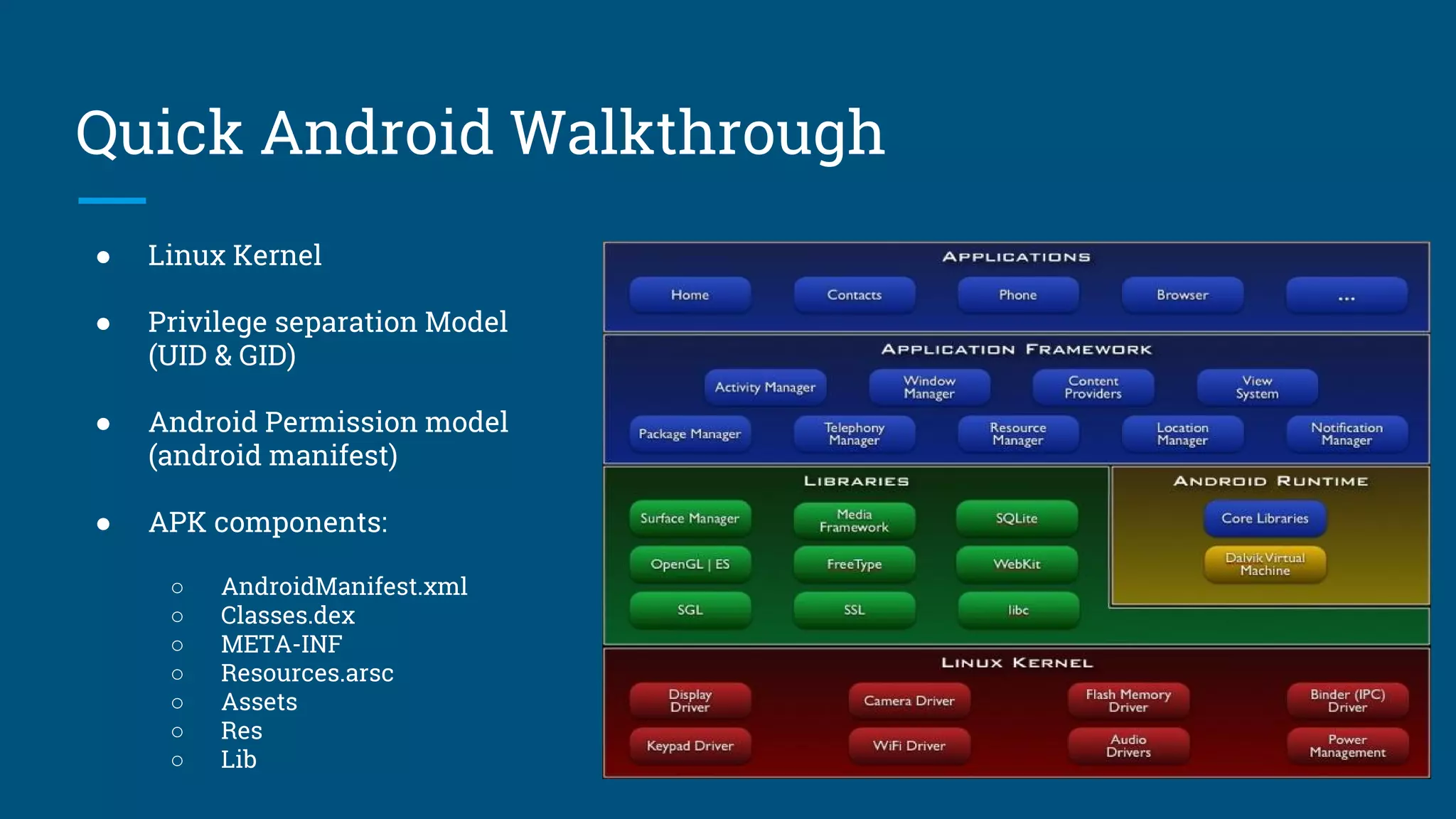
This document discusses Android application security and provides an overview of assessing Android applications for vulnerabilities. It covers Android architecture, application structure, tools for analysis including emulators and Drozer, and demonstrates reversing an APK file. The document also lists examples of vulnerabilities the presenter has found in Android apps with associated bounty amounts, and how to detect each one. It proposes using a virtual machine called Droider for Android application assessments.