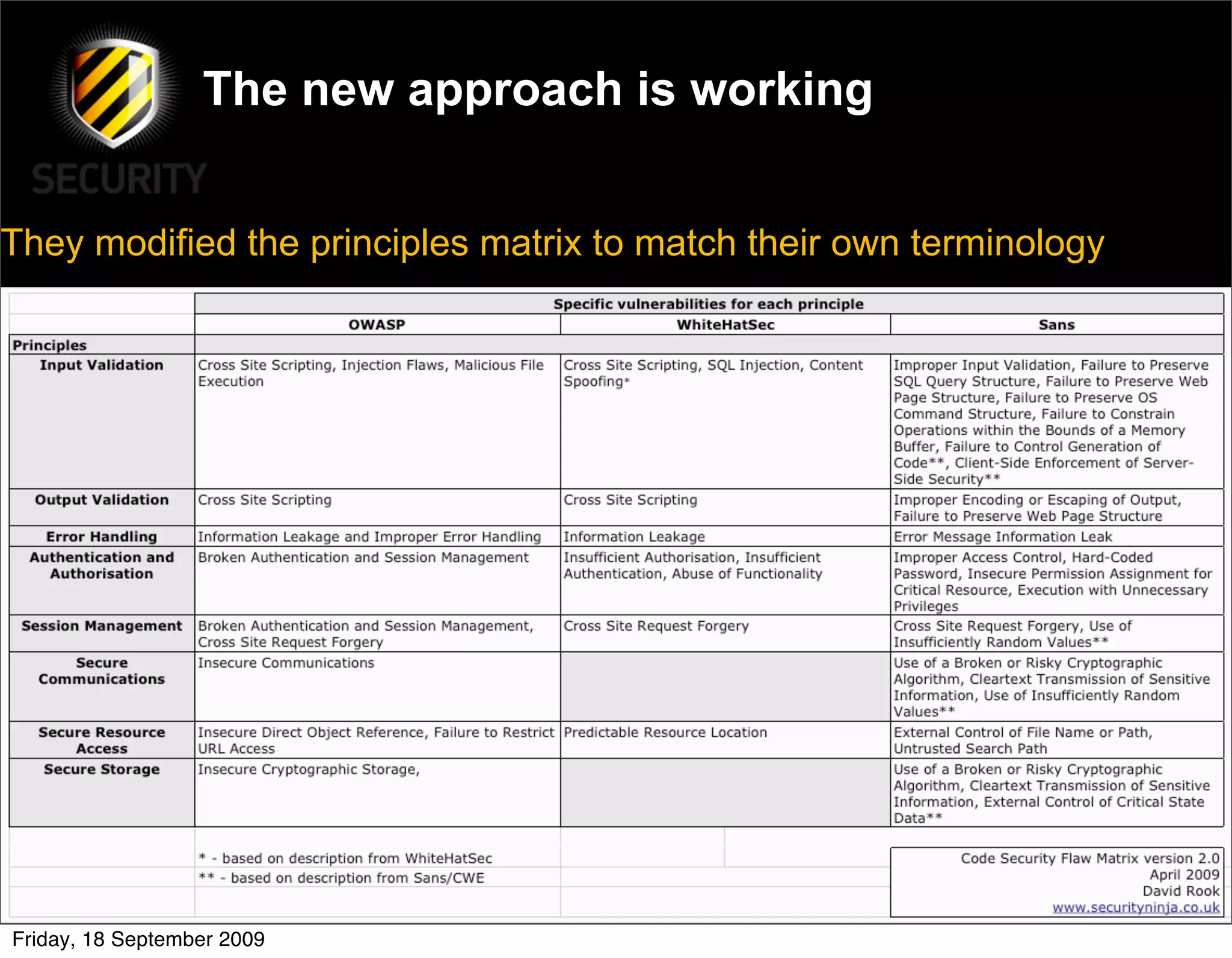
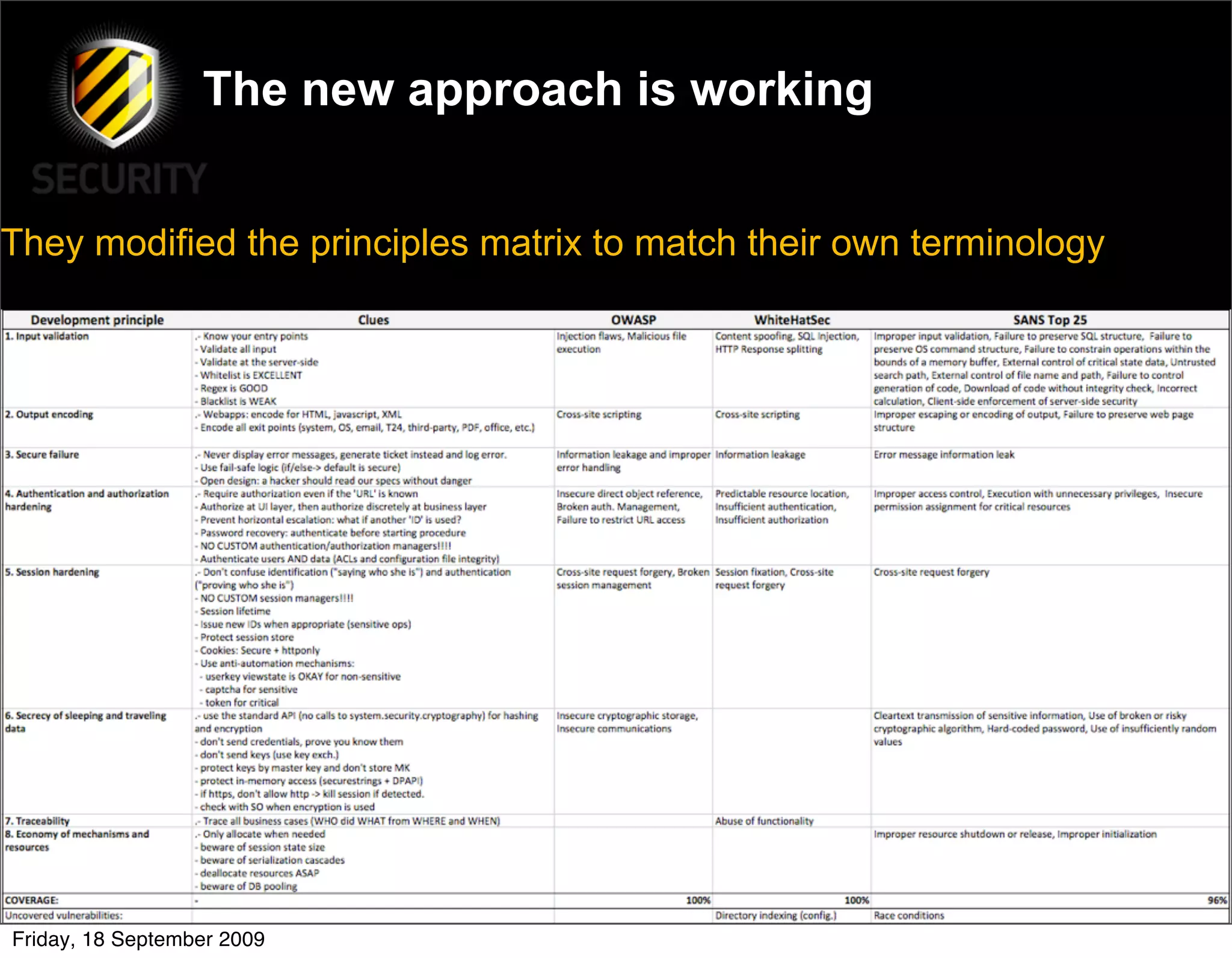
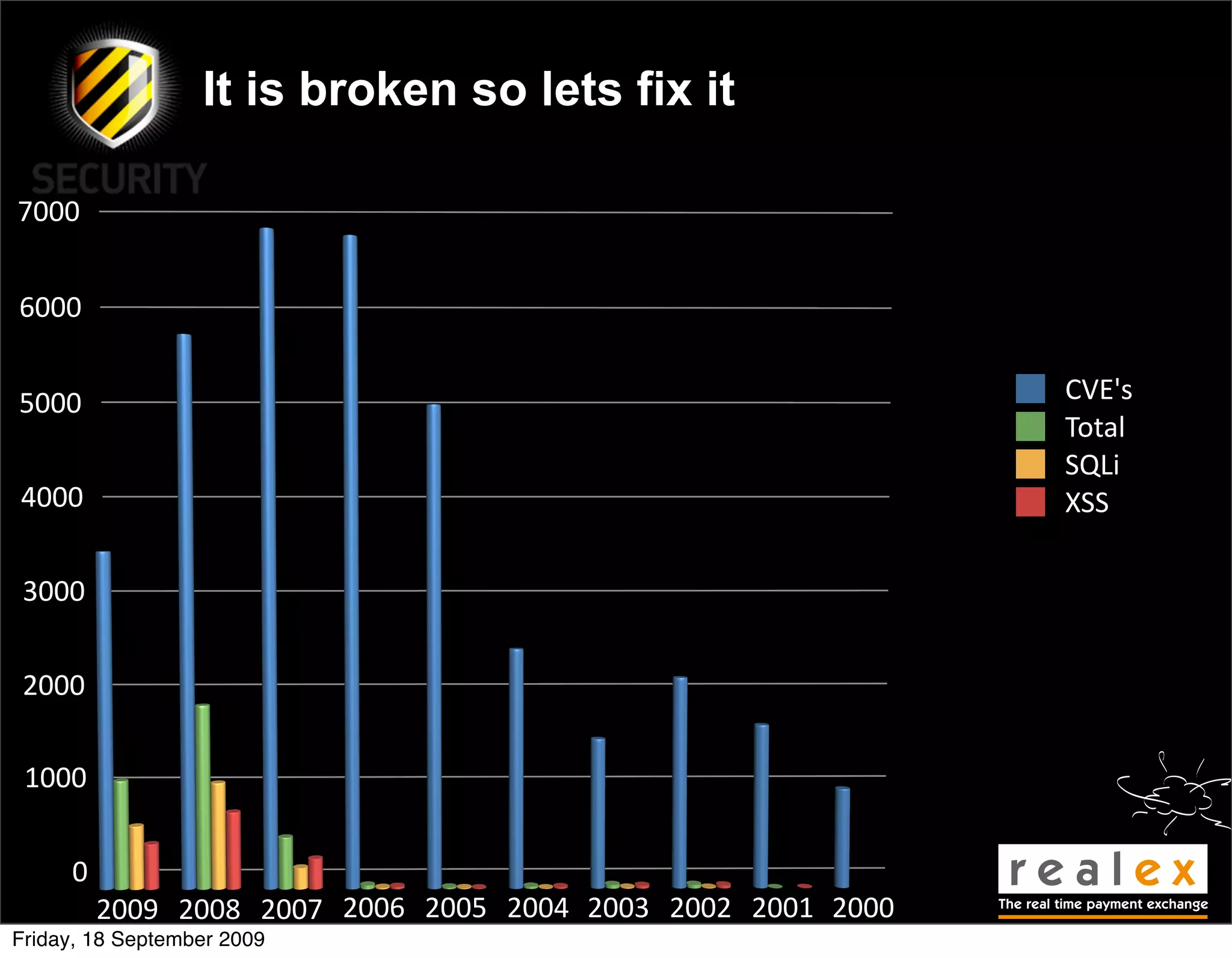
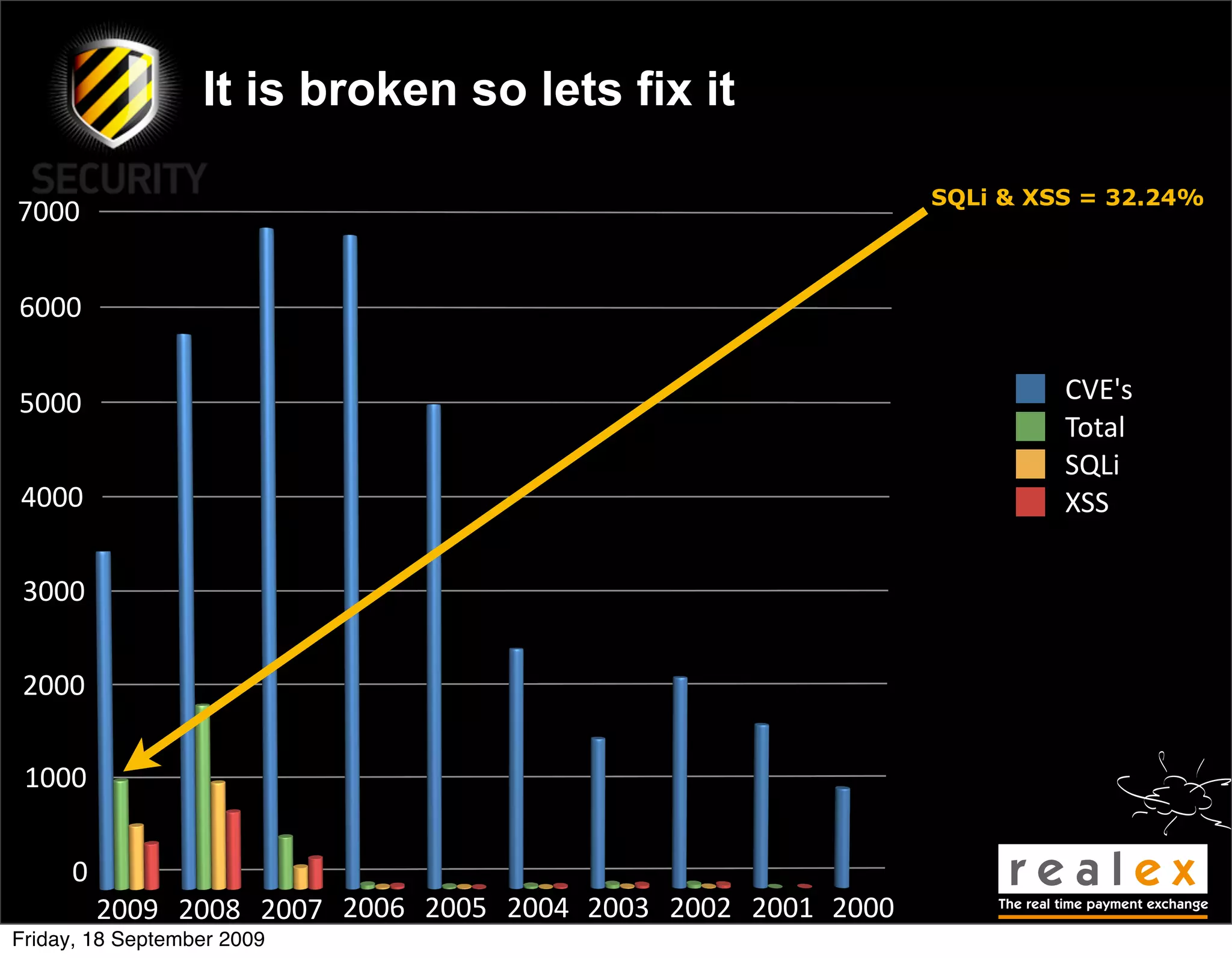
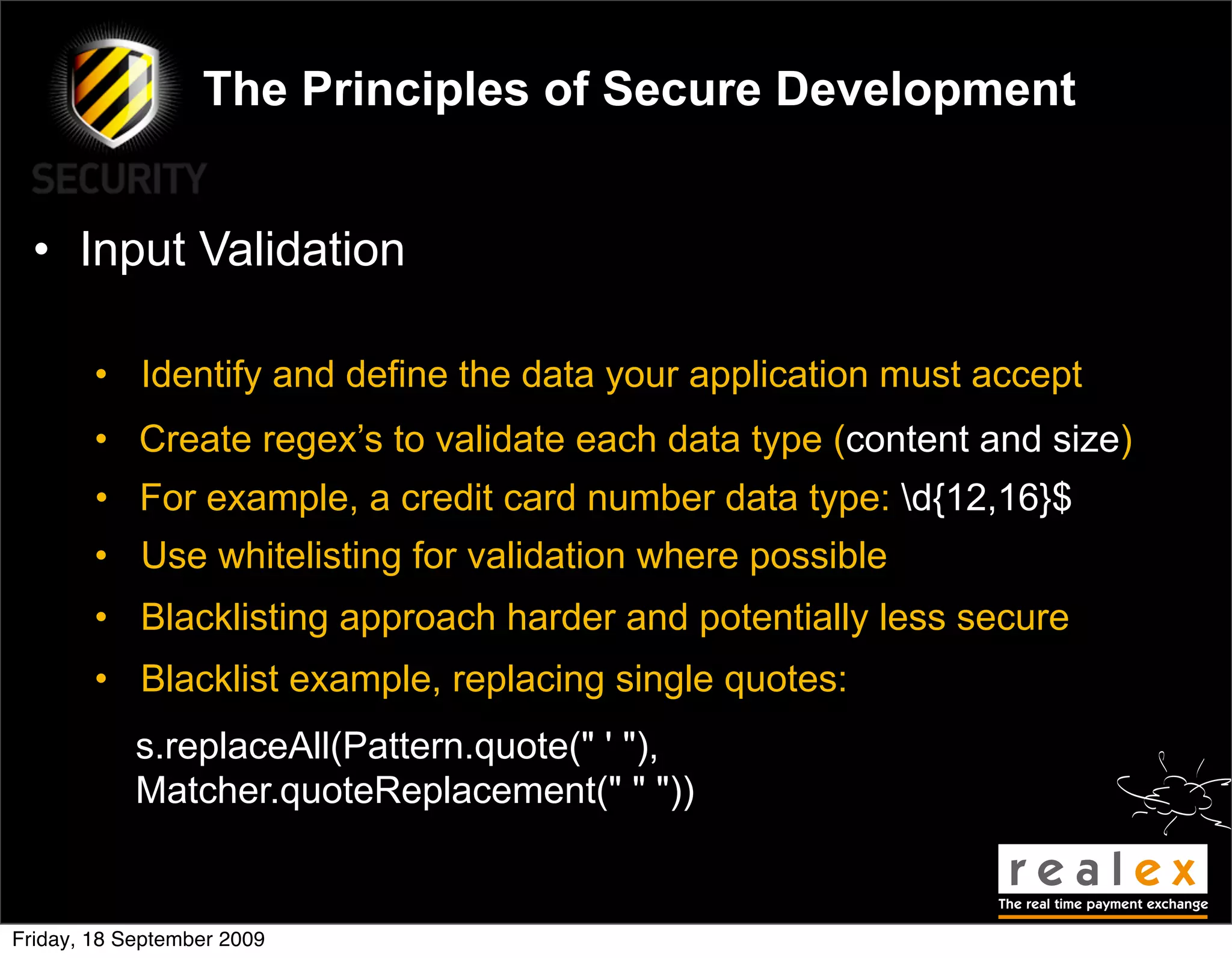
David Rook presented on The Principles of Secure Development at the OWASP Ireland Conference in Dublin. He outlined 8 principles of secure development: input validation, output validation, error handling, authentication and authorization, session management, secure communications, secure storage, and secure resource access. The principles are meant to teach developers how to build security into their code from the start rather than focusing on specific vulnerabilities. Rook argued this approach could help reduce common vulnerabilities like SQL injection and cross-site scripting.














![The Principles of Secure Development
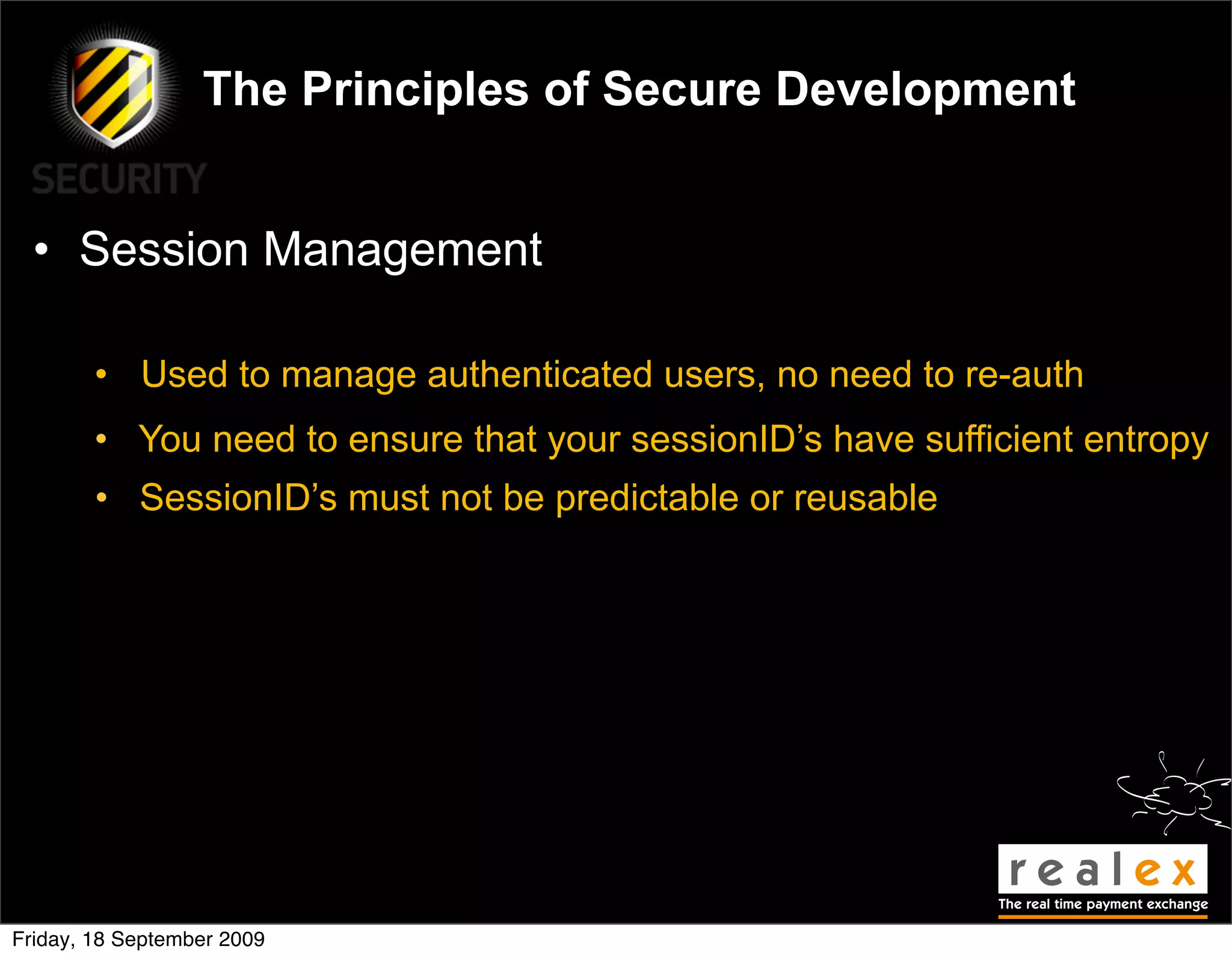
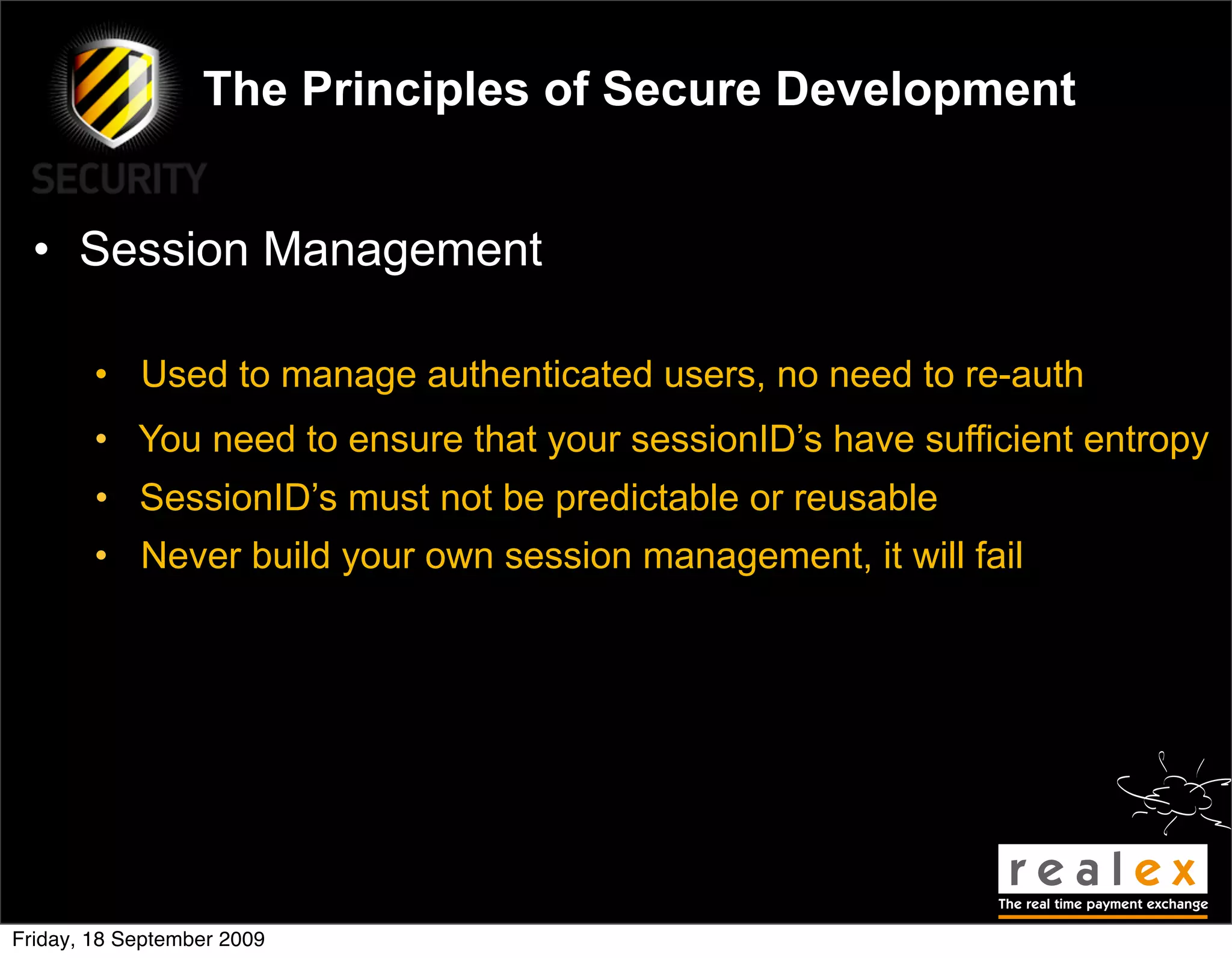
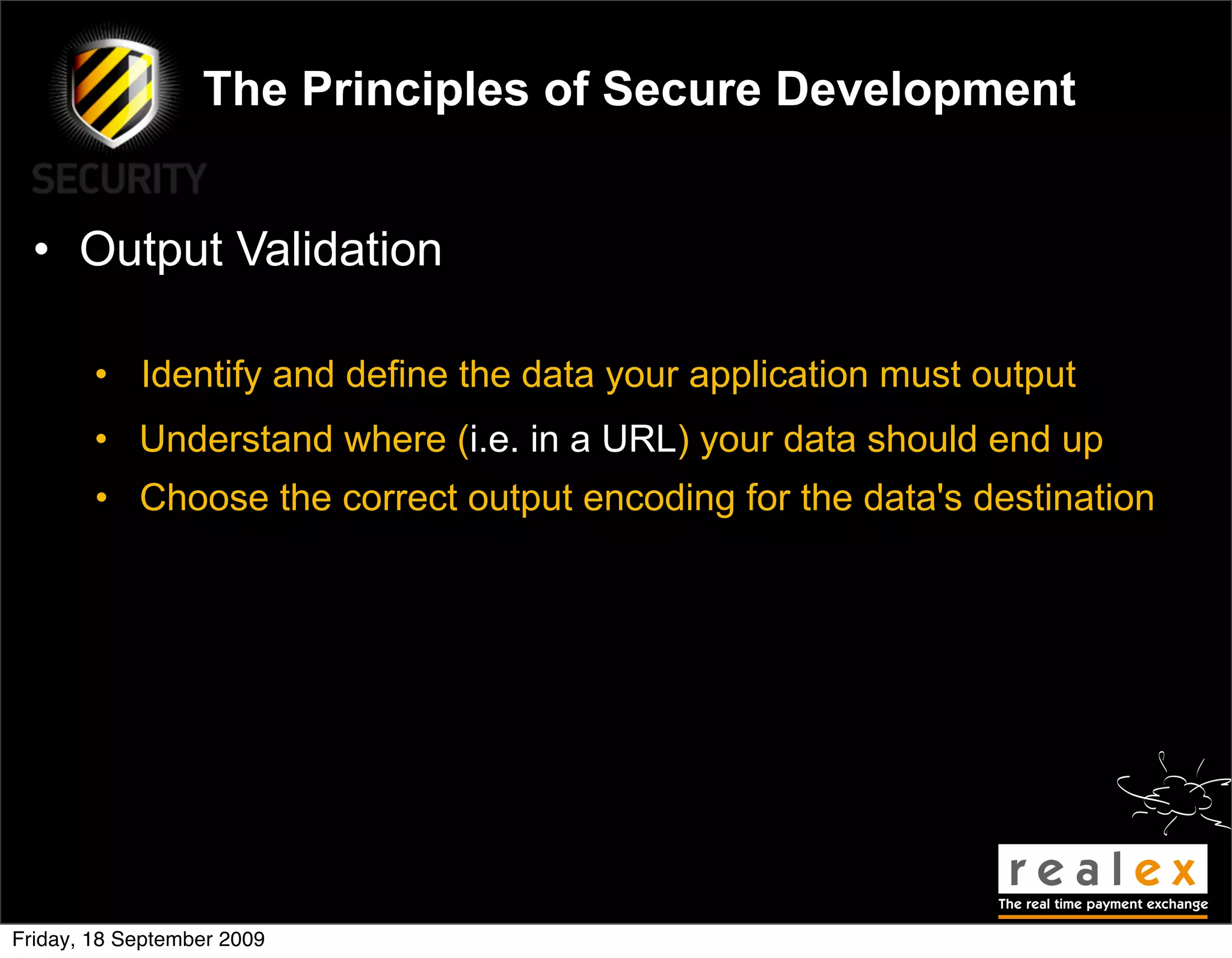
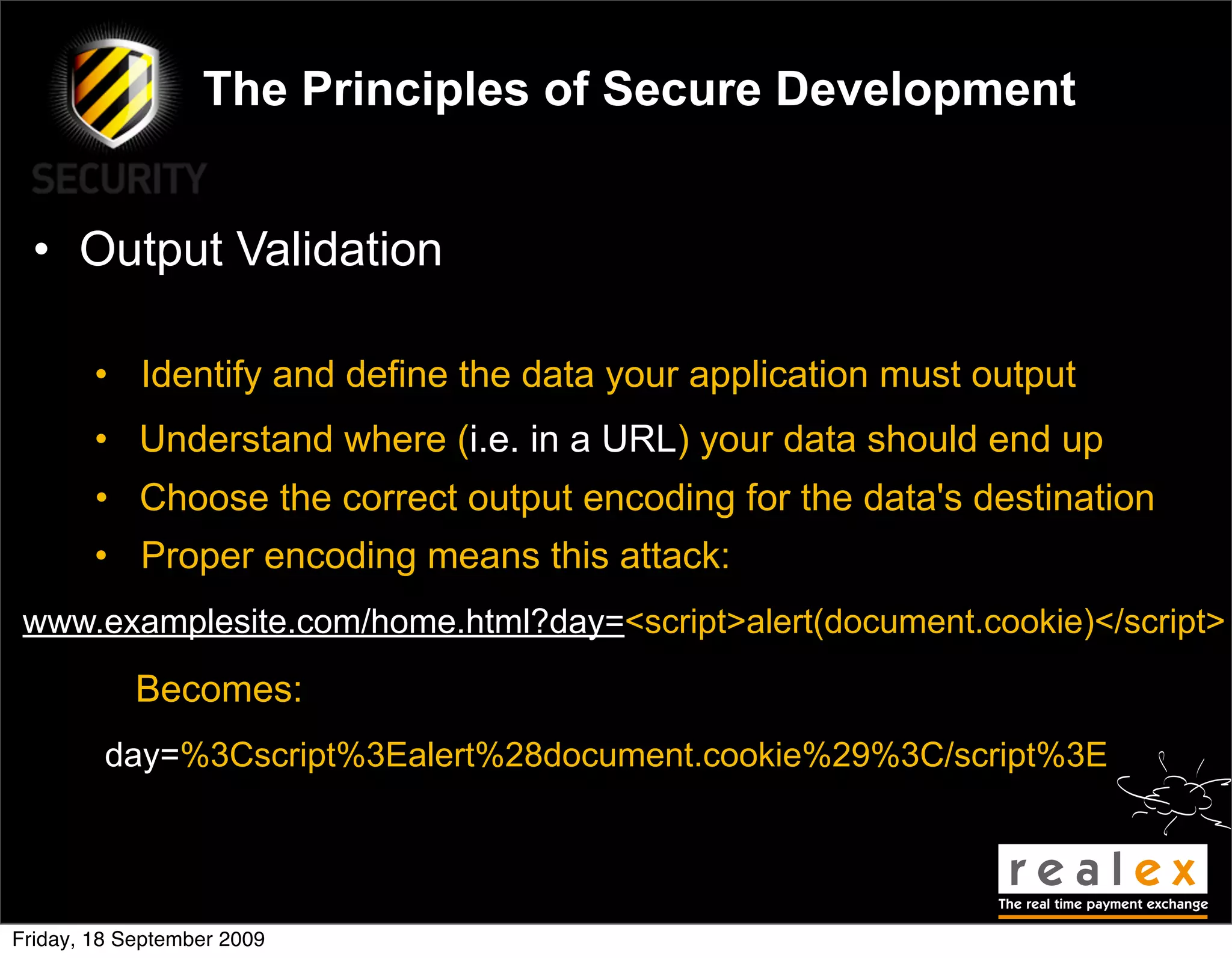
• Error Handling
• Even the best apps will crash at some point, be prepared!
• Crashes/errors can help an attacker if you don’t handle them
• Handle error conditions securely, sanitise the message sent
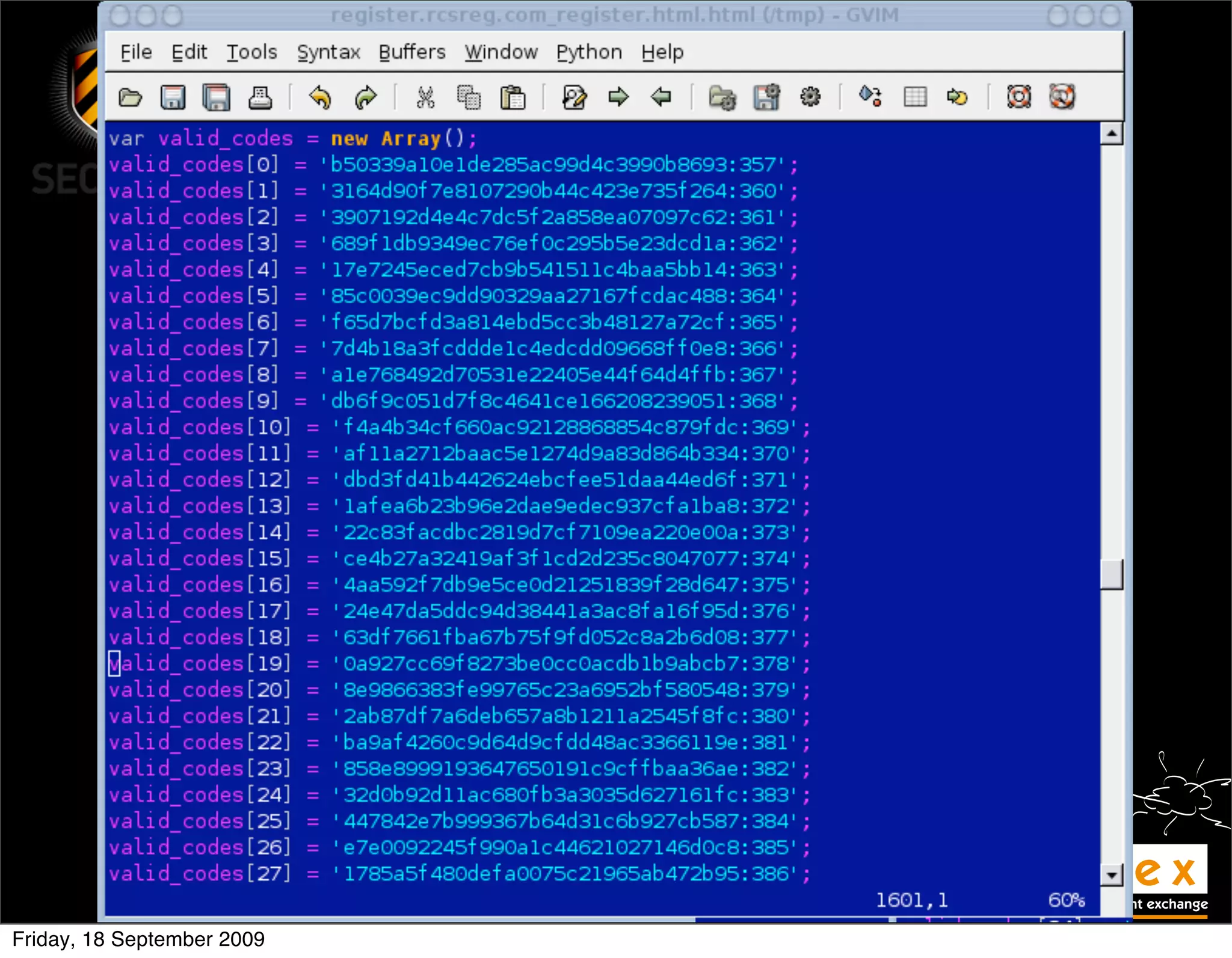
• No error handling = information leakage
Microsoft OLE DB Provider for ODBC
Drivers(0x80040E14)
[Microsoft][ODBC SQL Server Driver]
[SQL Server]Invalid column name
/examplesite/login.asp, line 10
Friday, 18 September 2009](https://image.slidesharecdn.com/owasp-securedevprinciples-david-rook-110322061054-phpapp01/75/The-Principles-of-Secure-Development-27-2048.jpg)