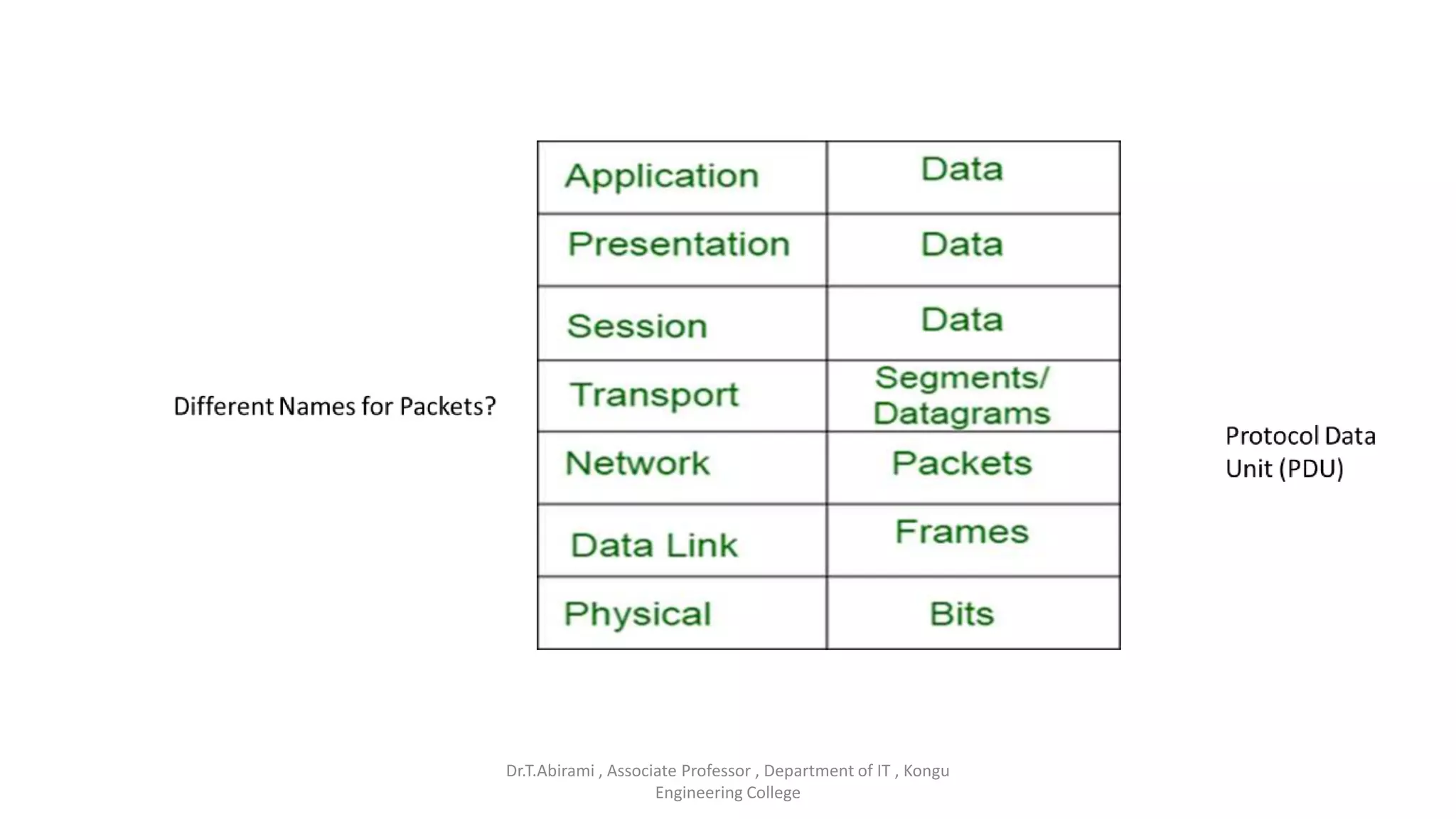
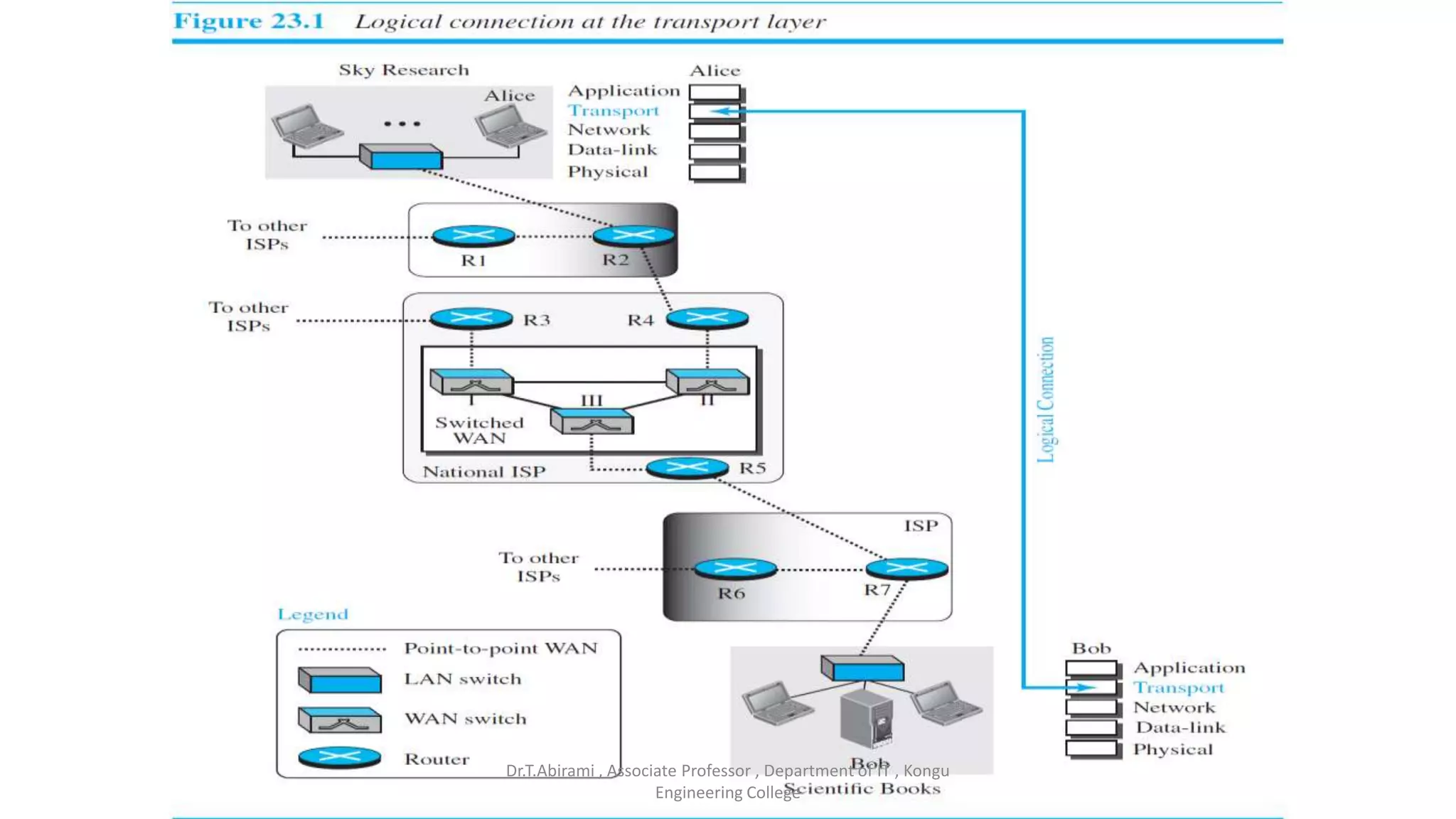
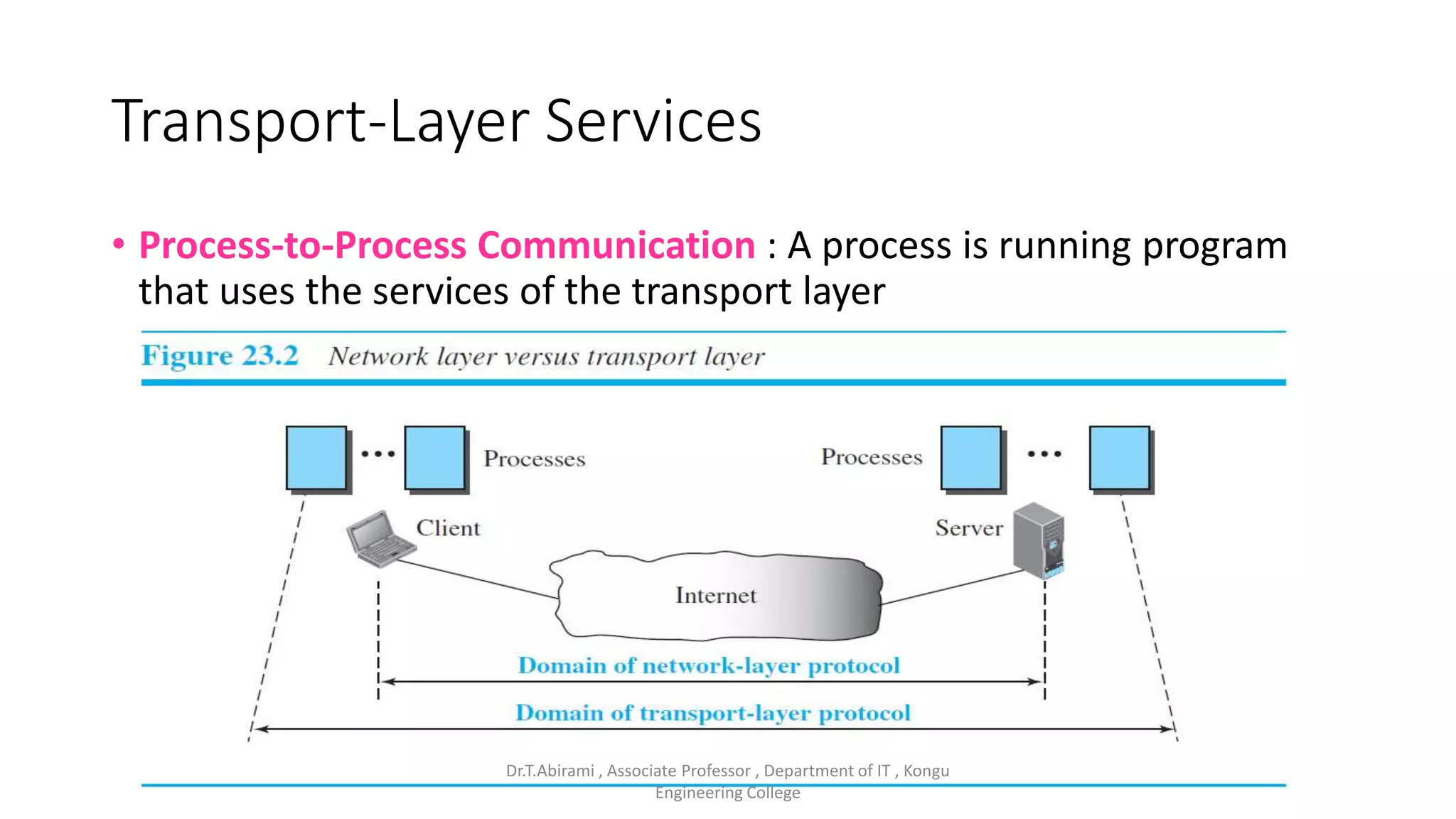
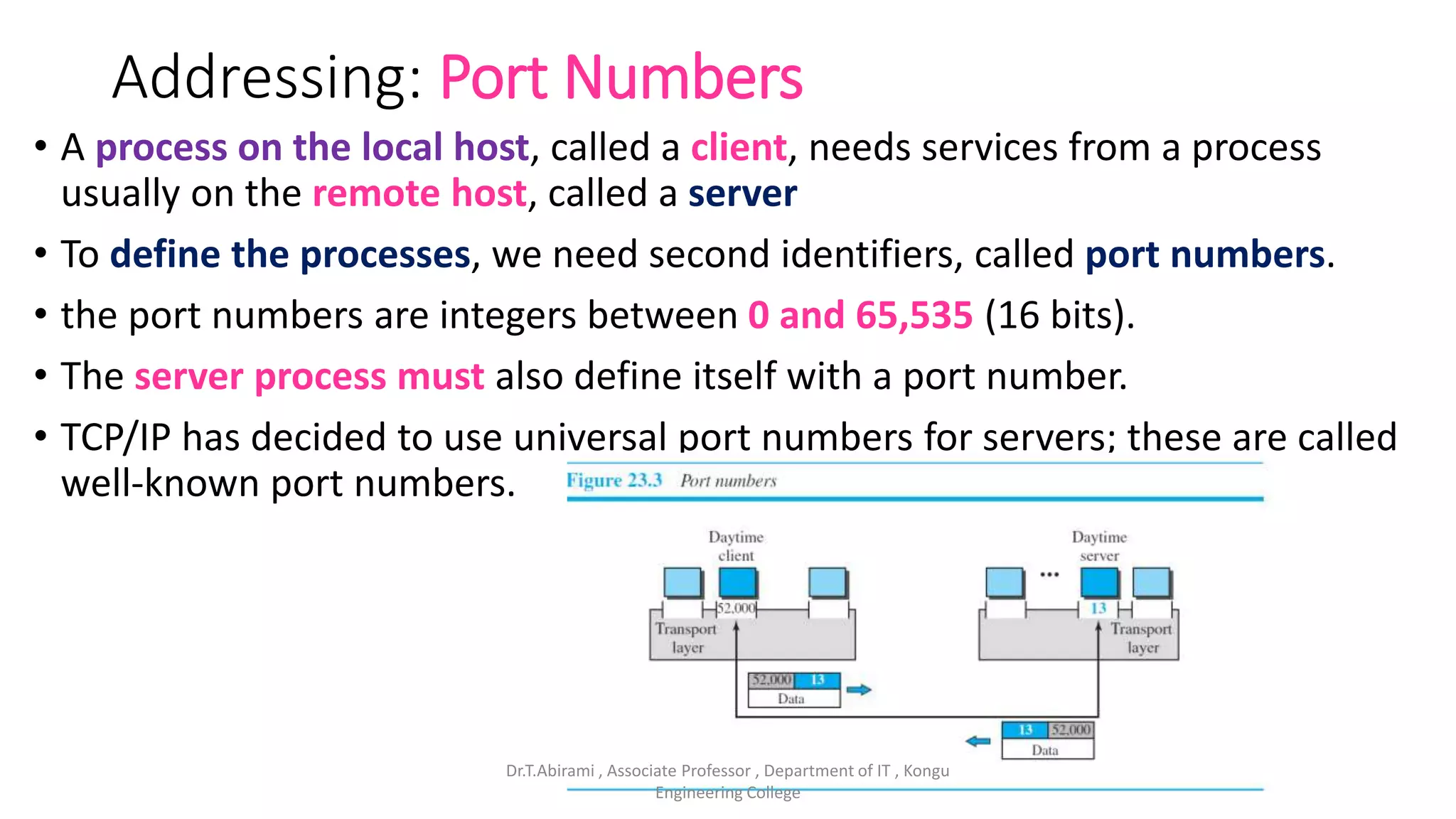
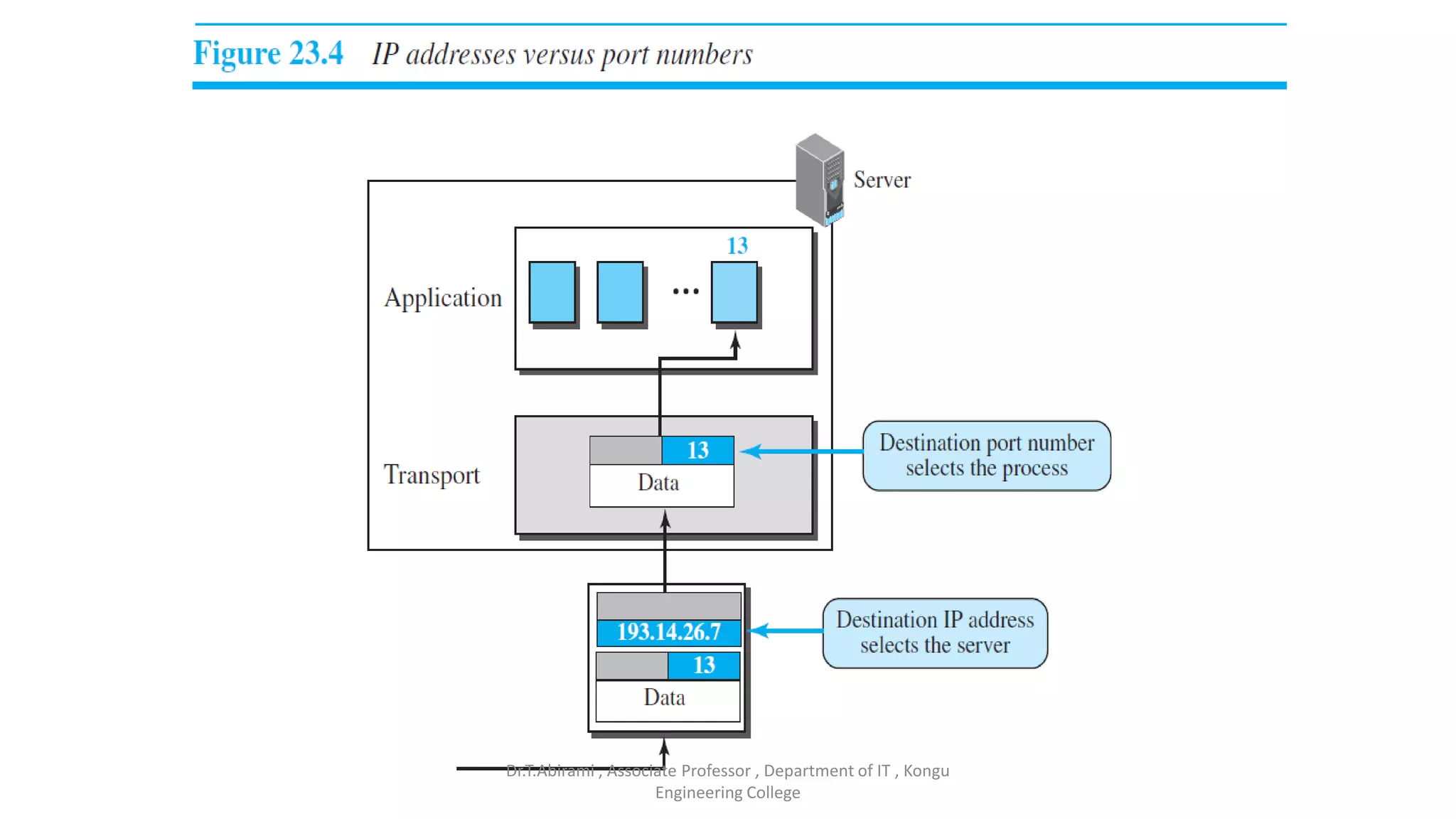
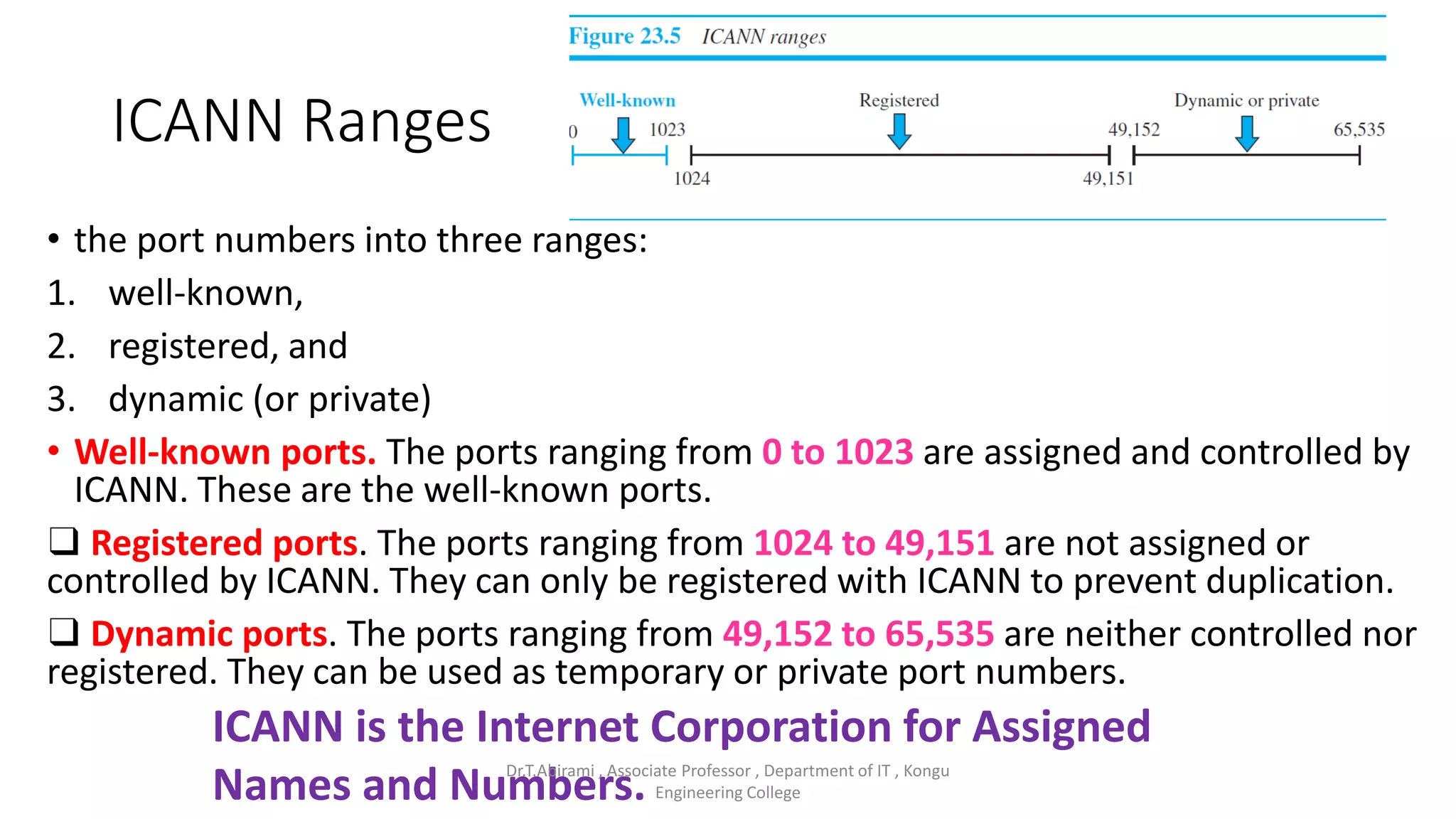
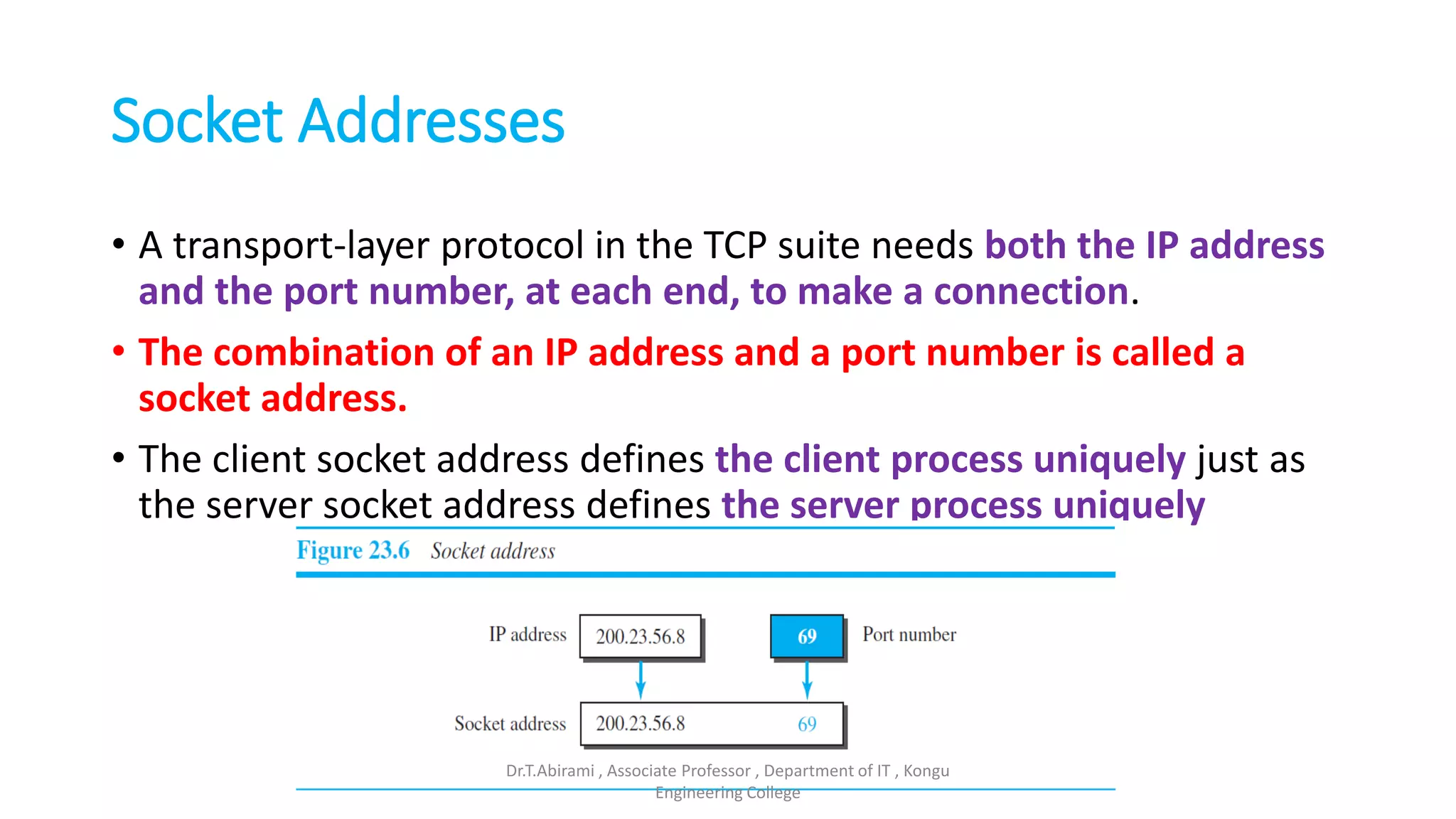
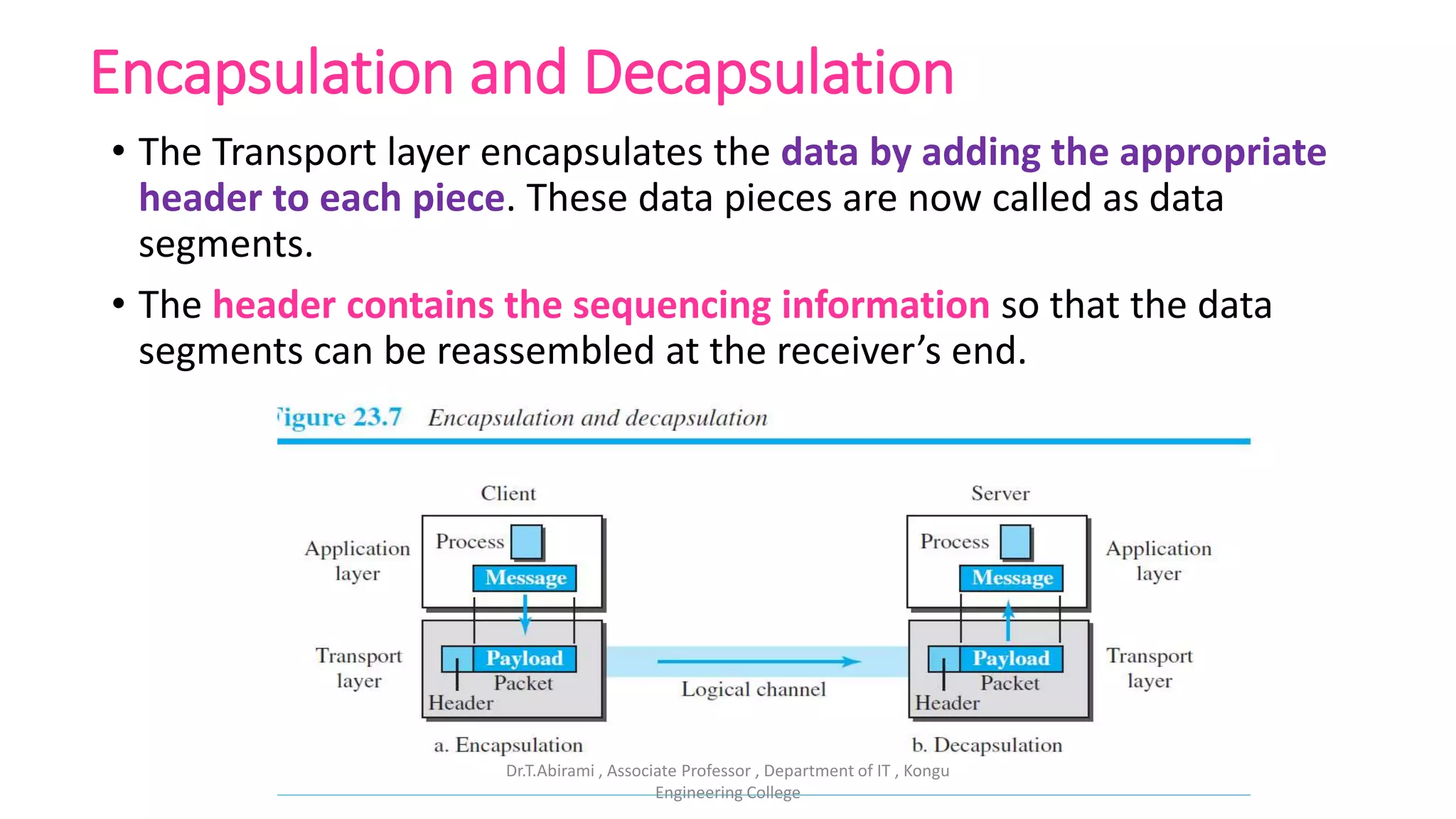
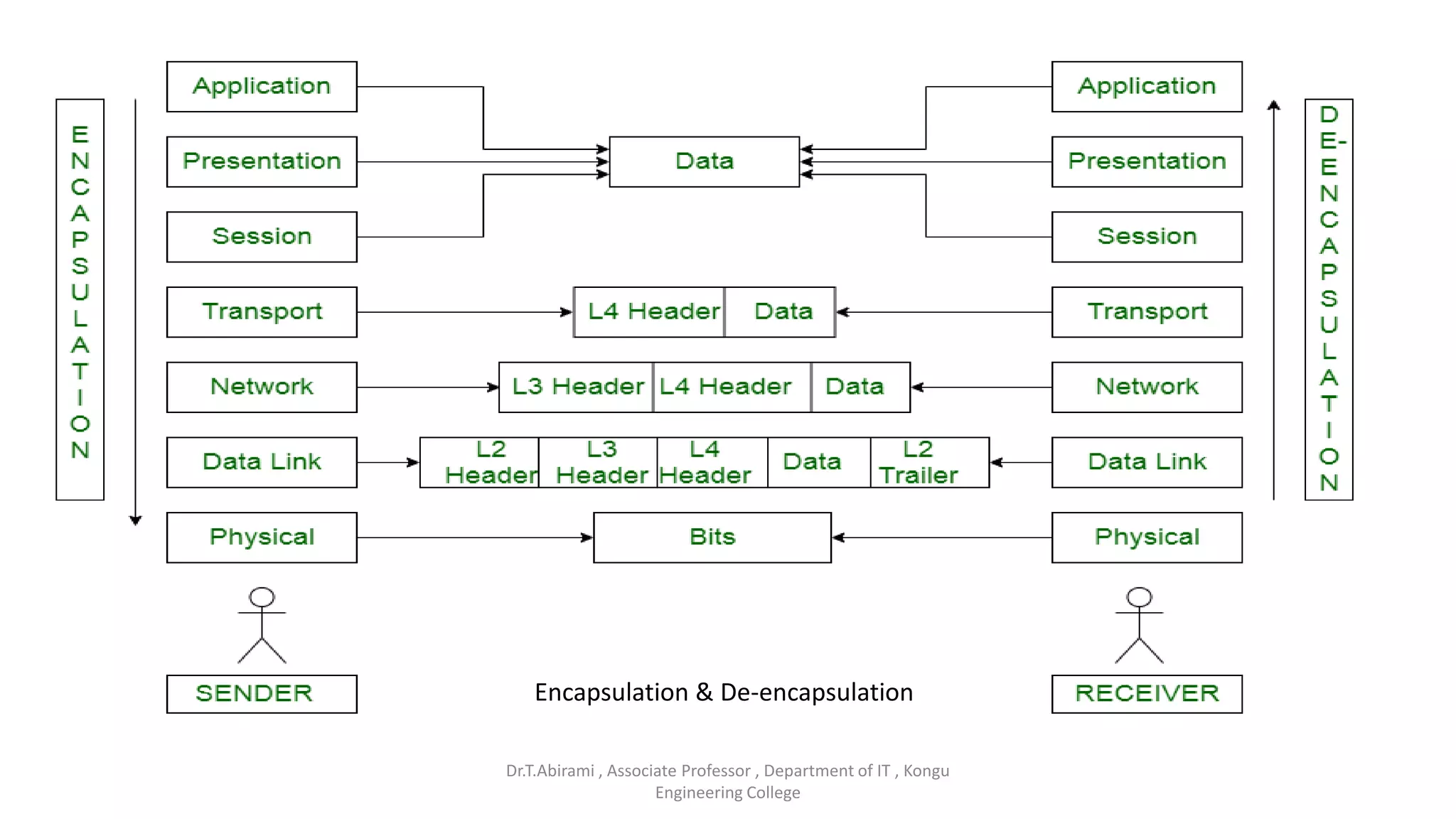
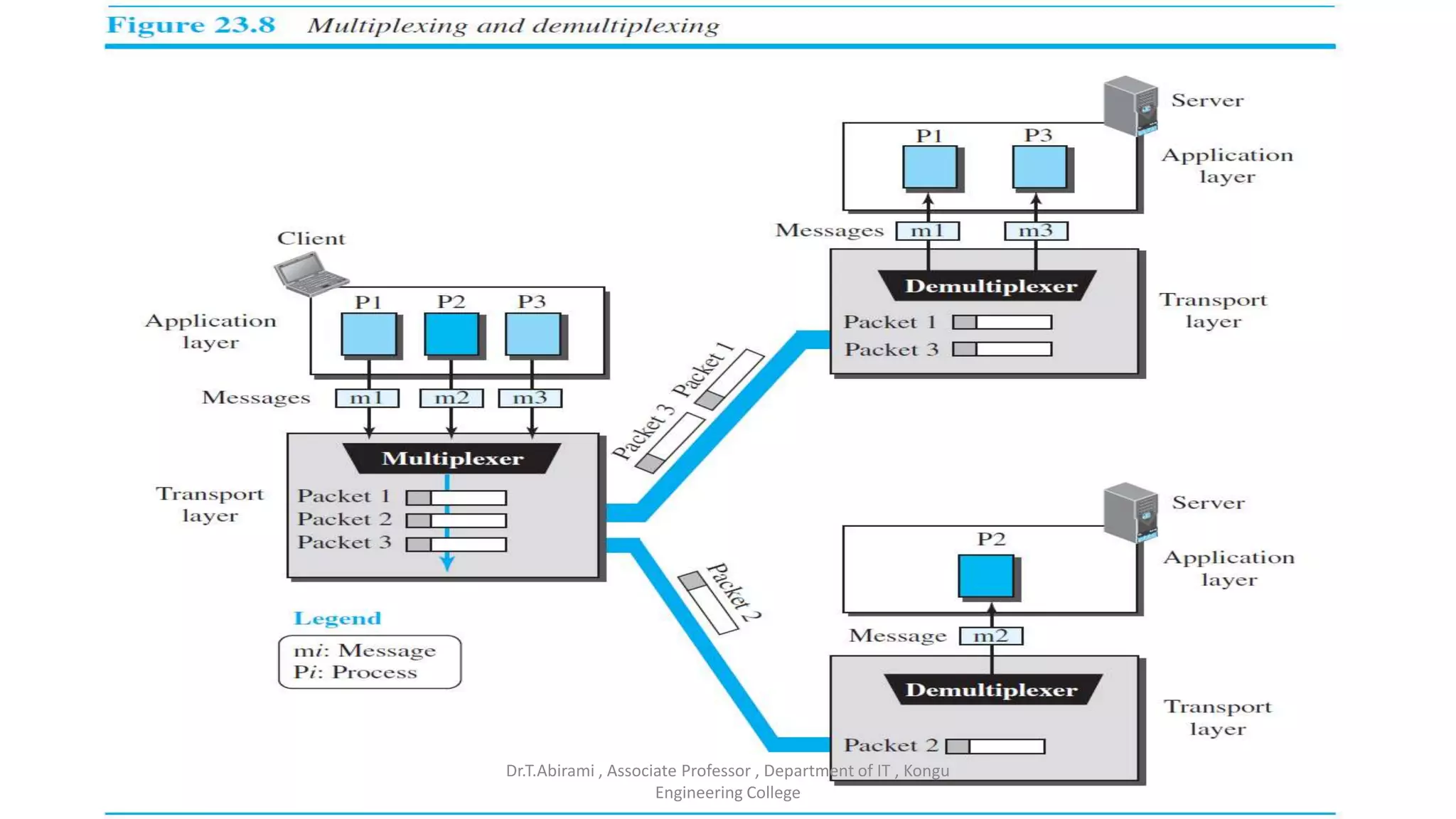
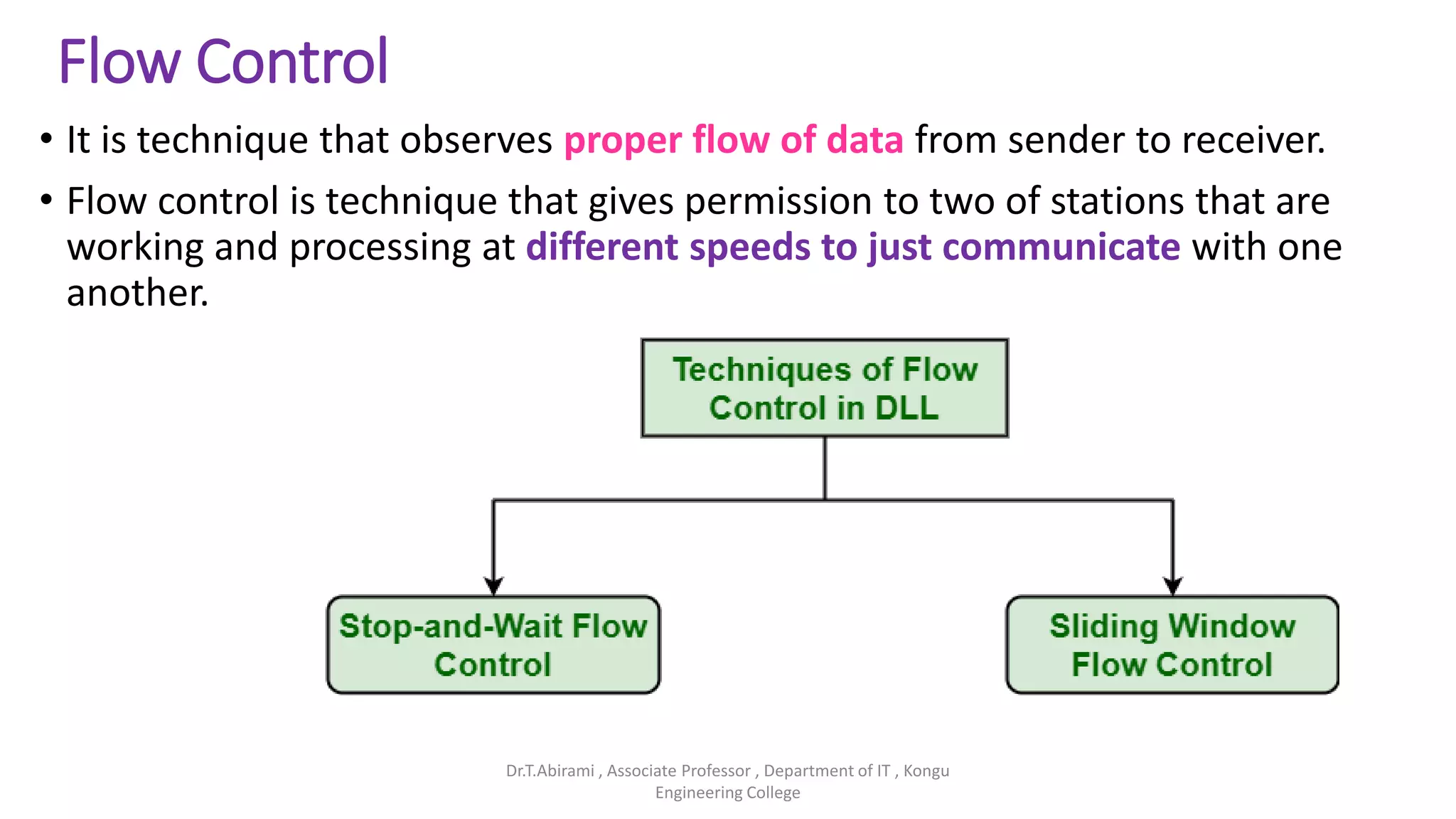
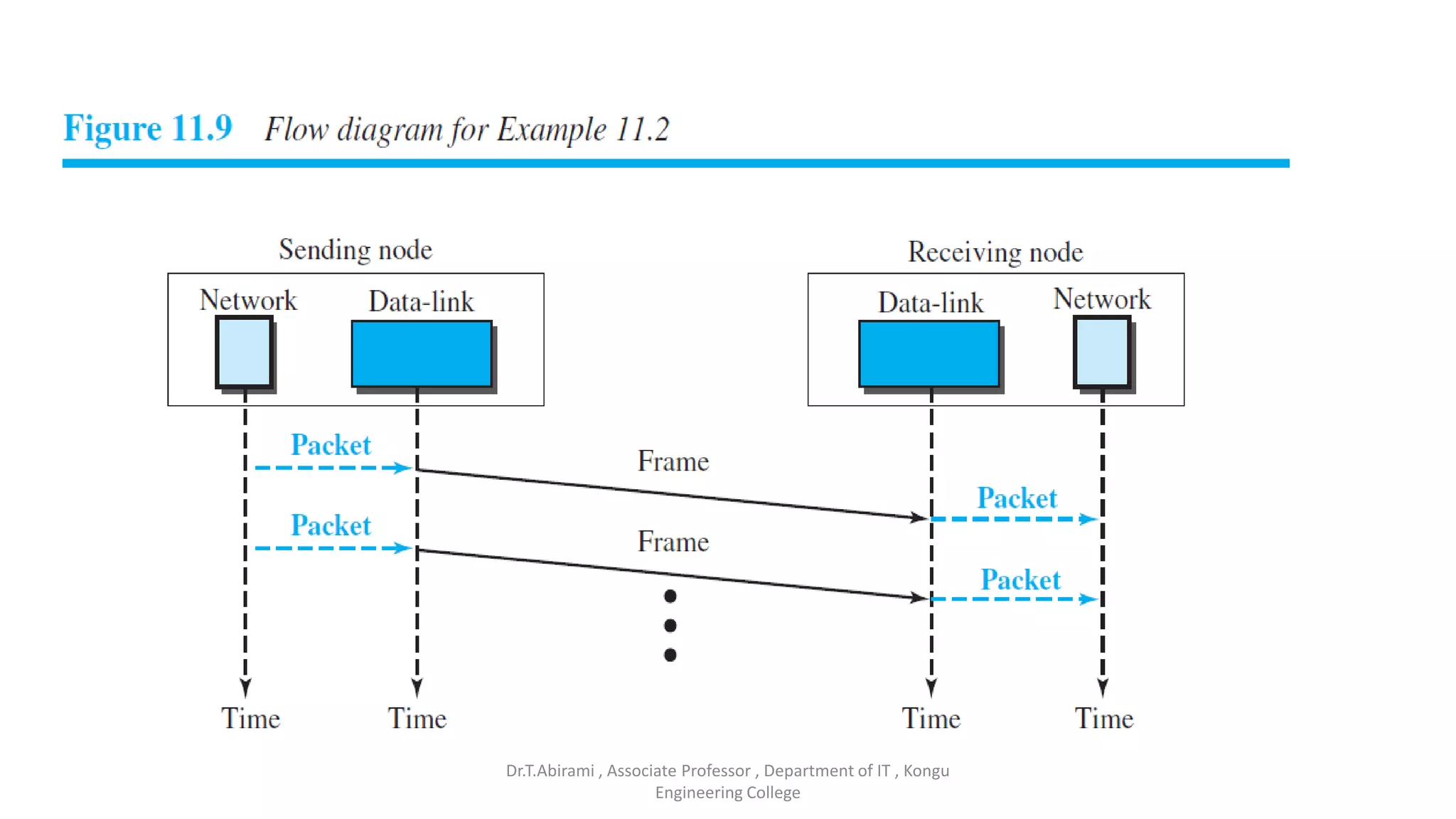
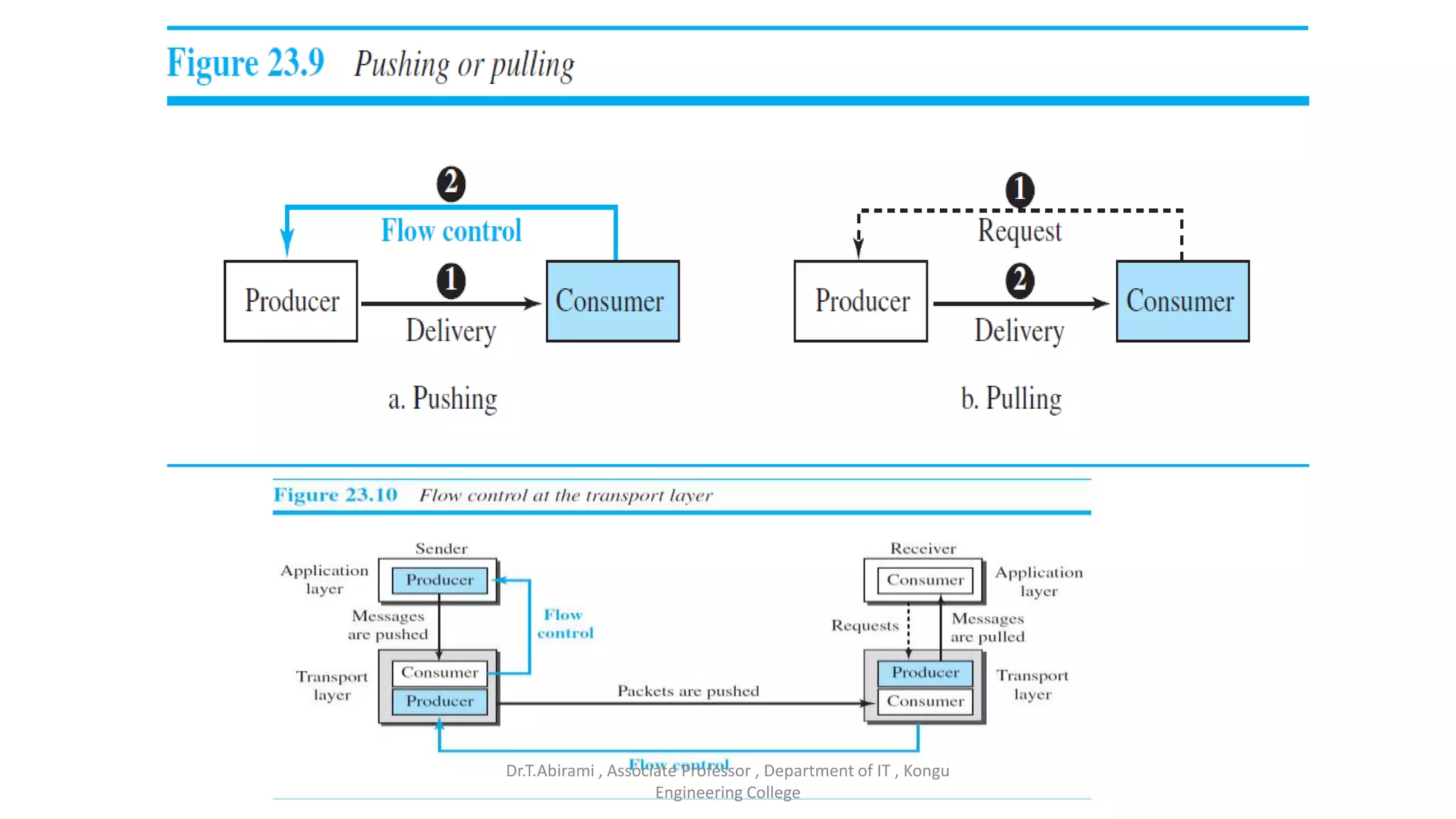
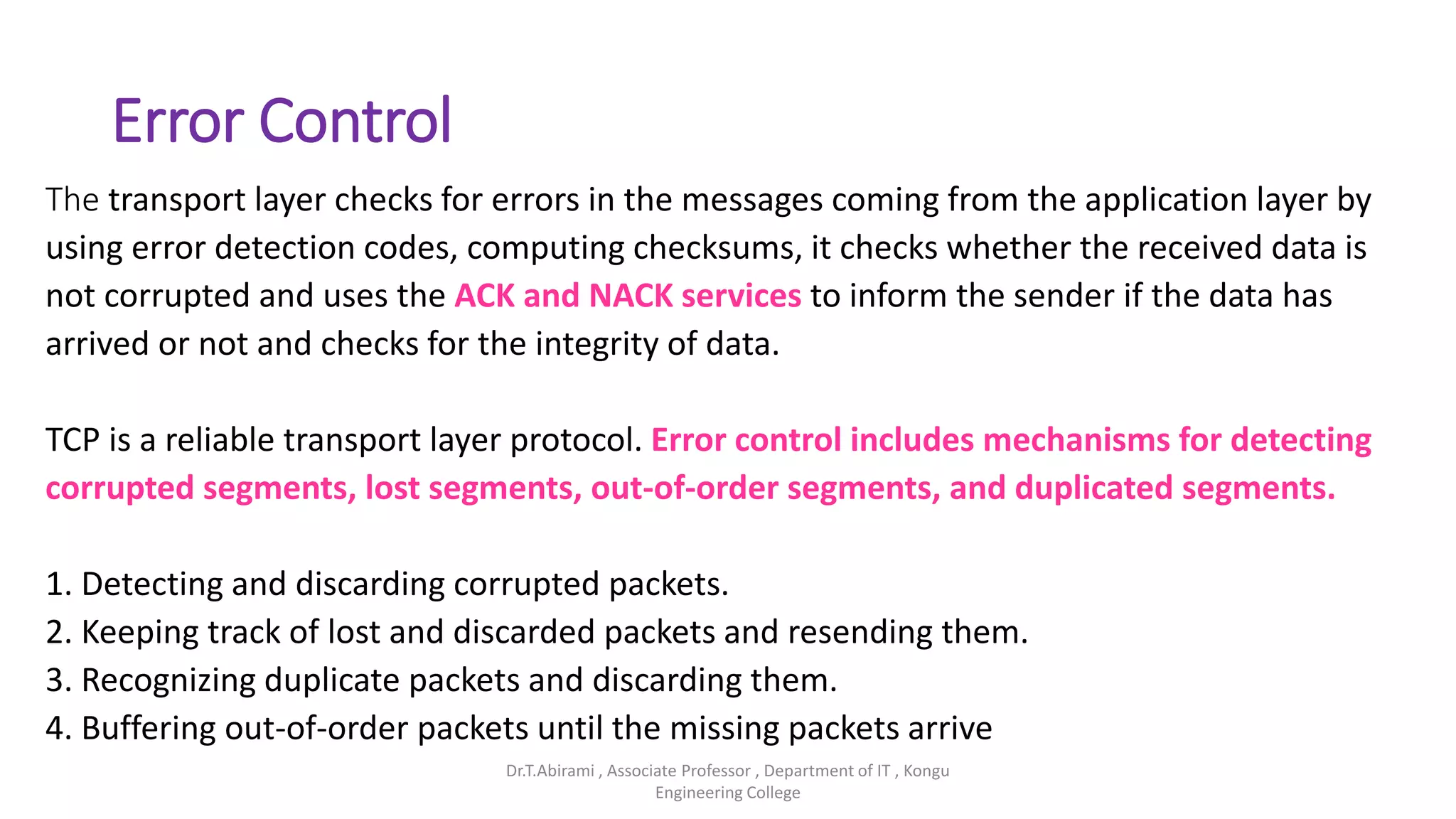
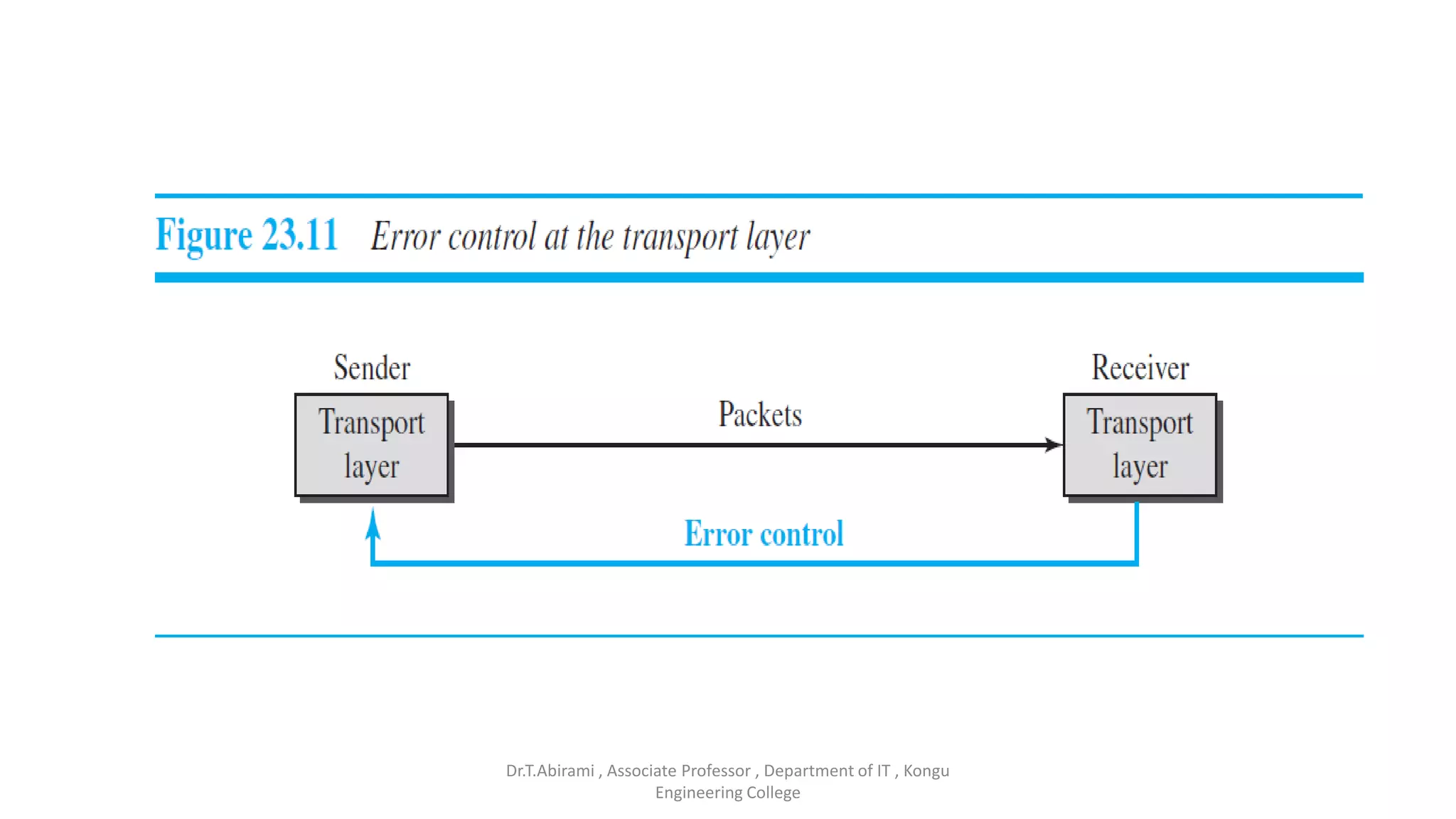
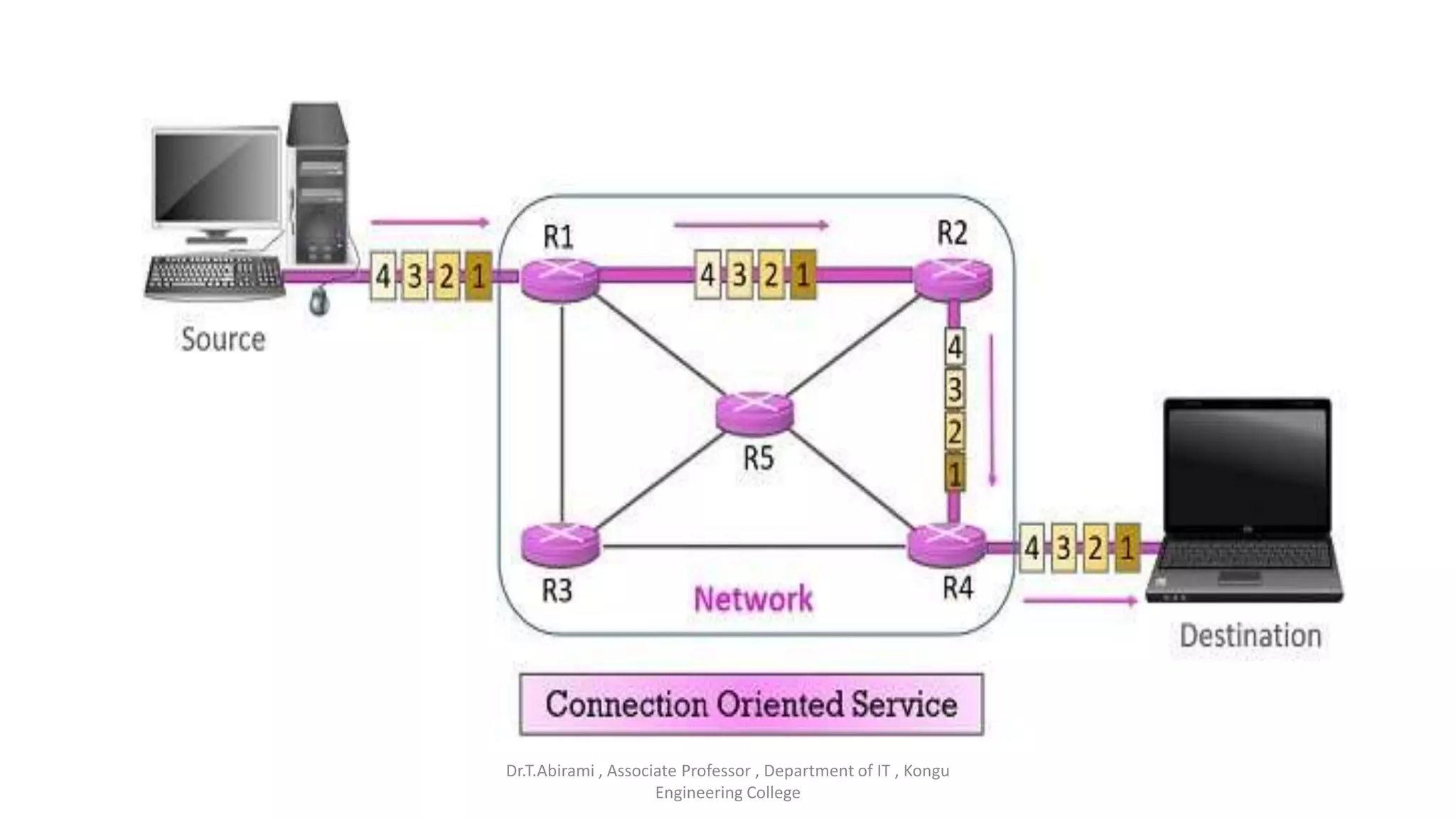
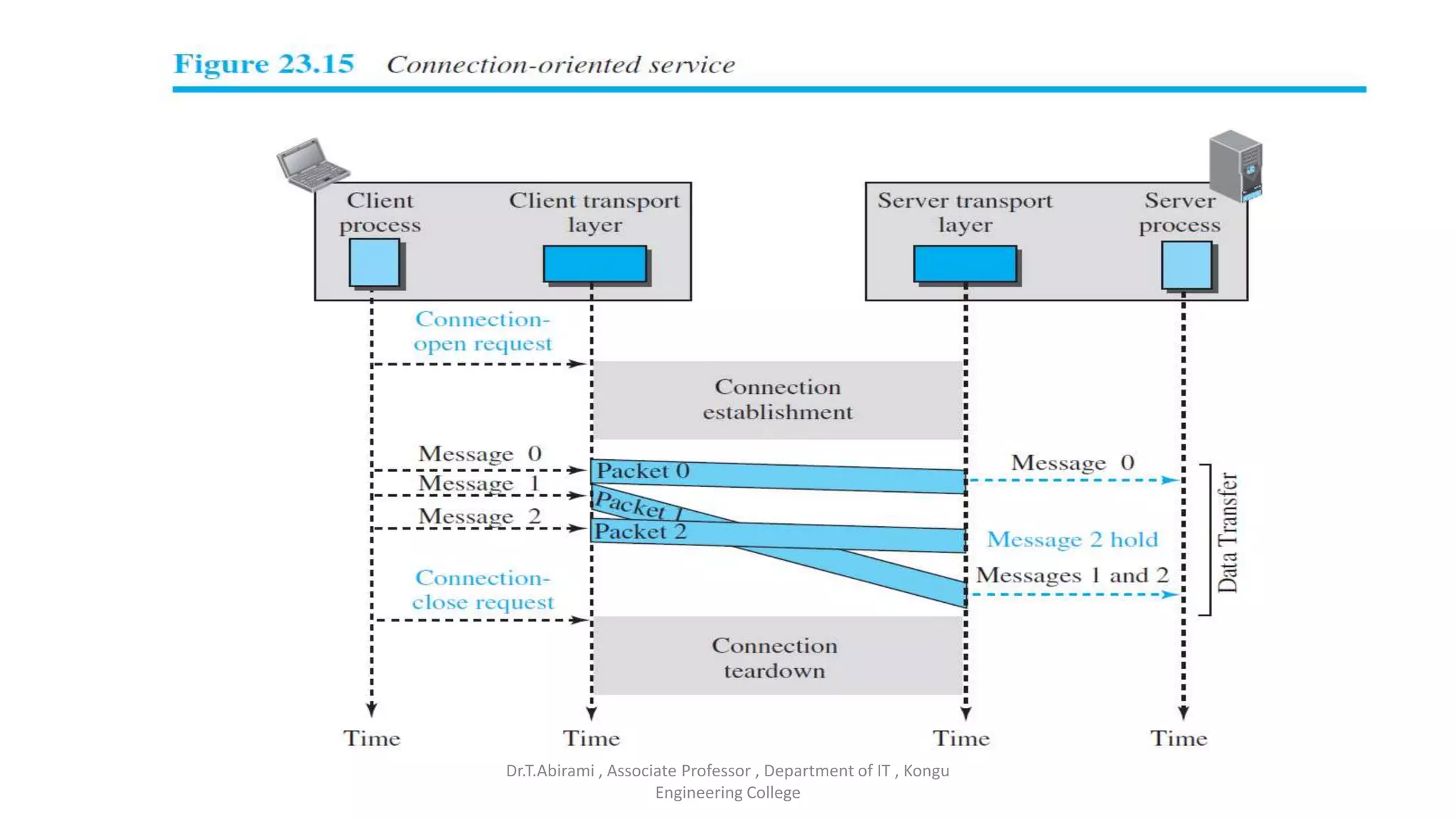
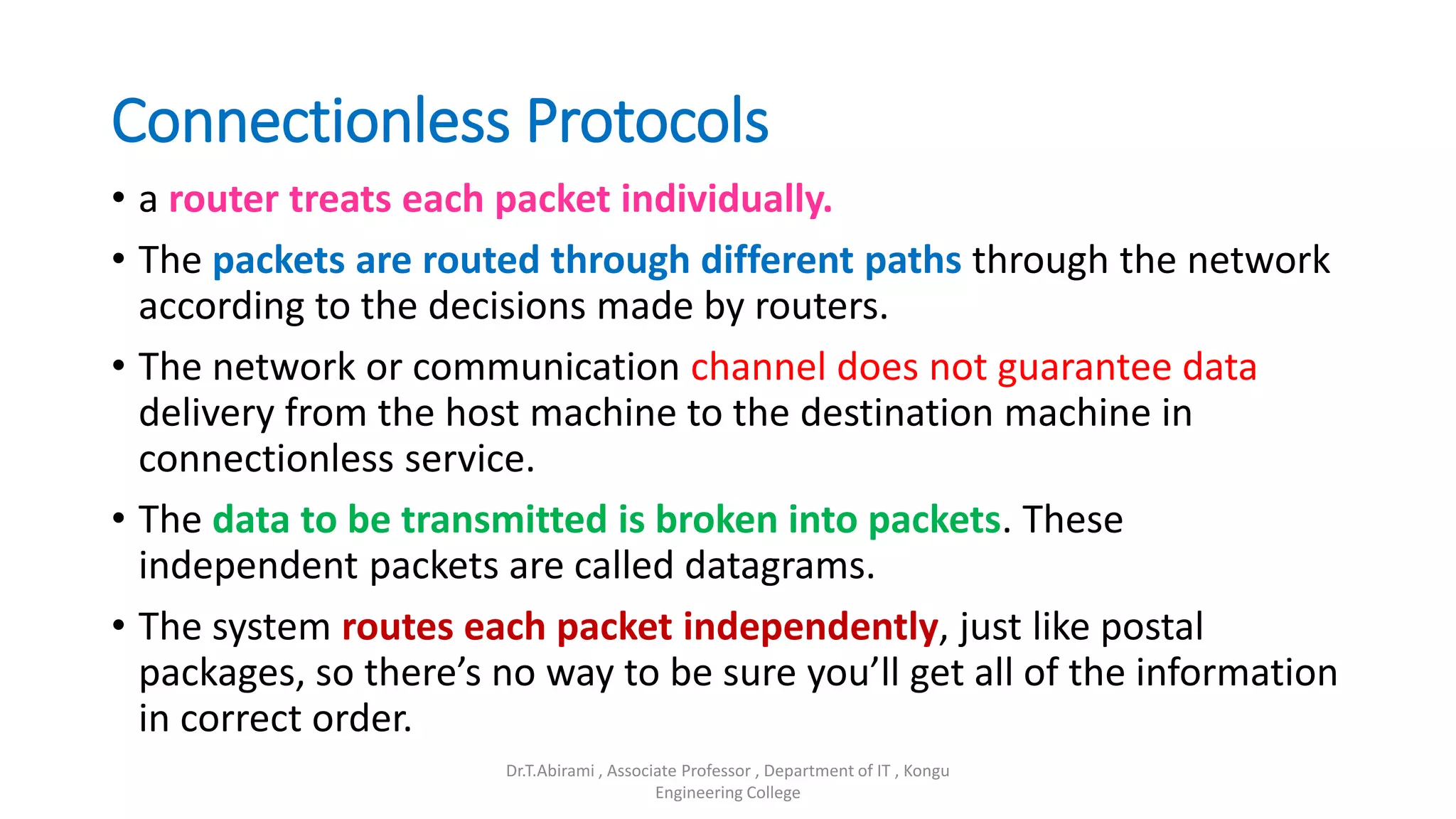
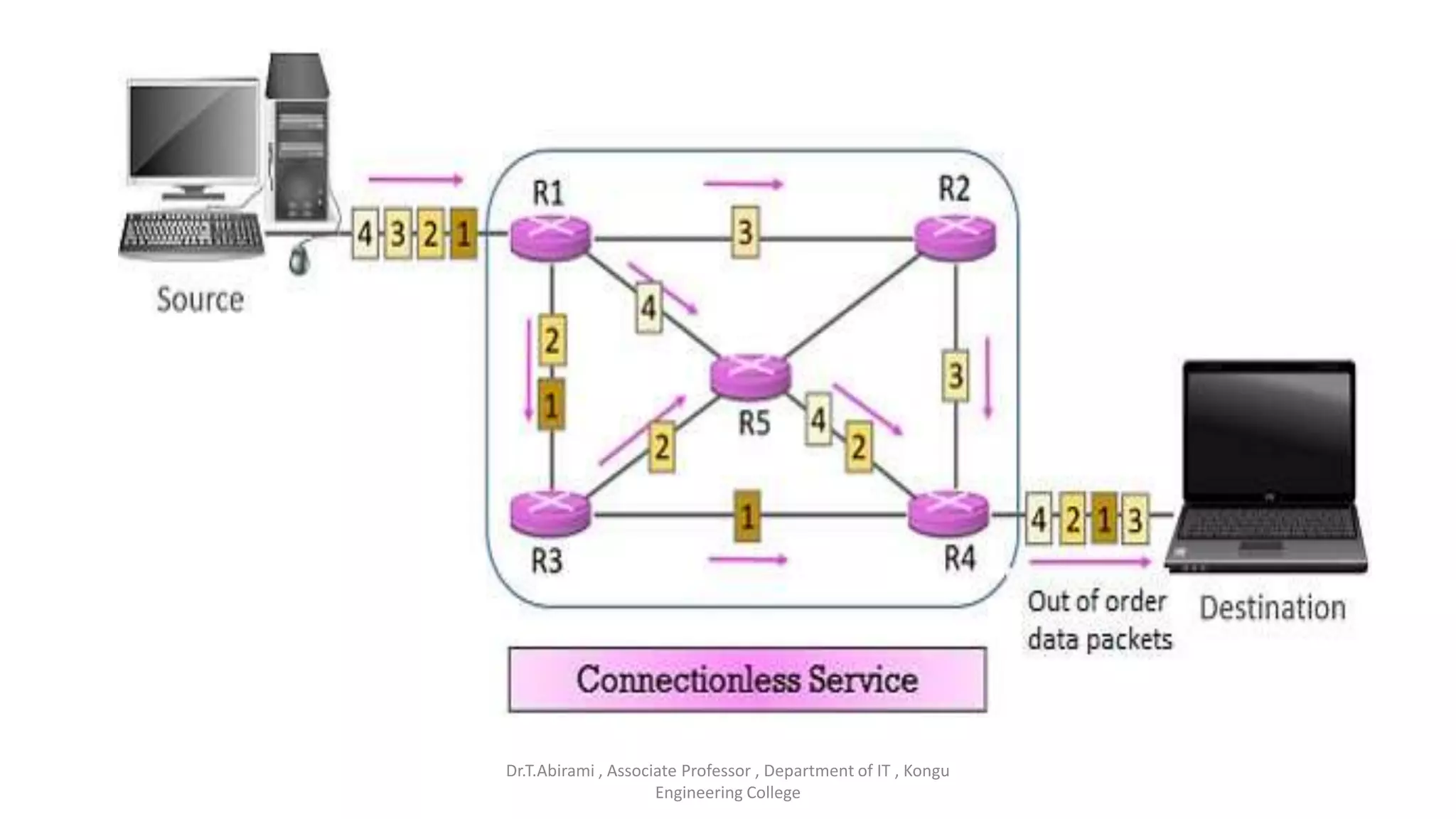
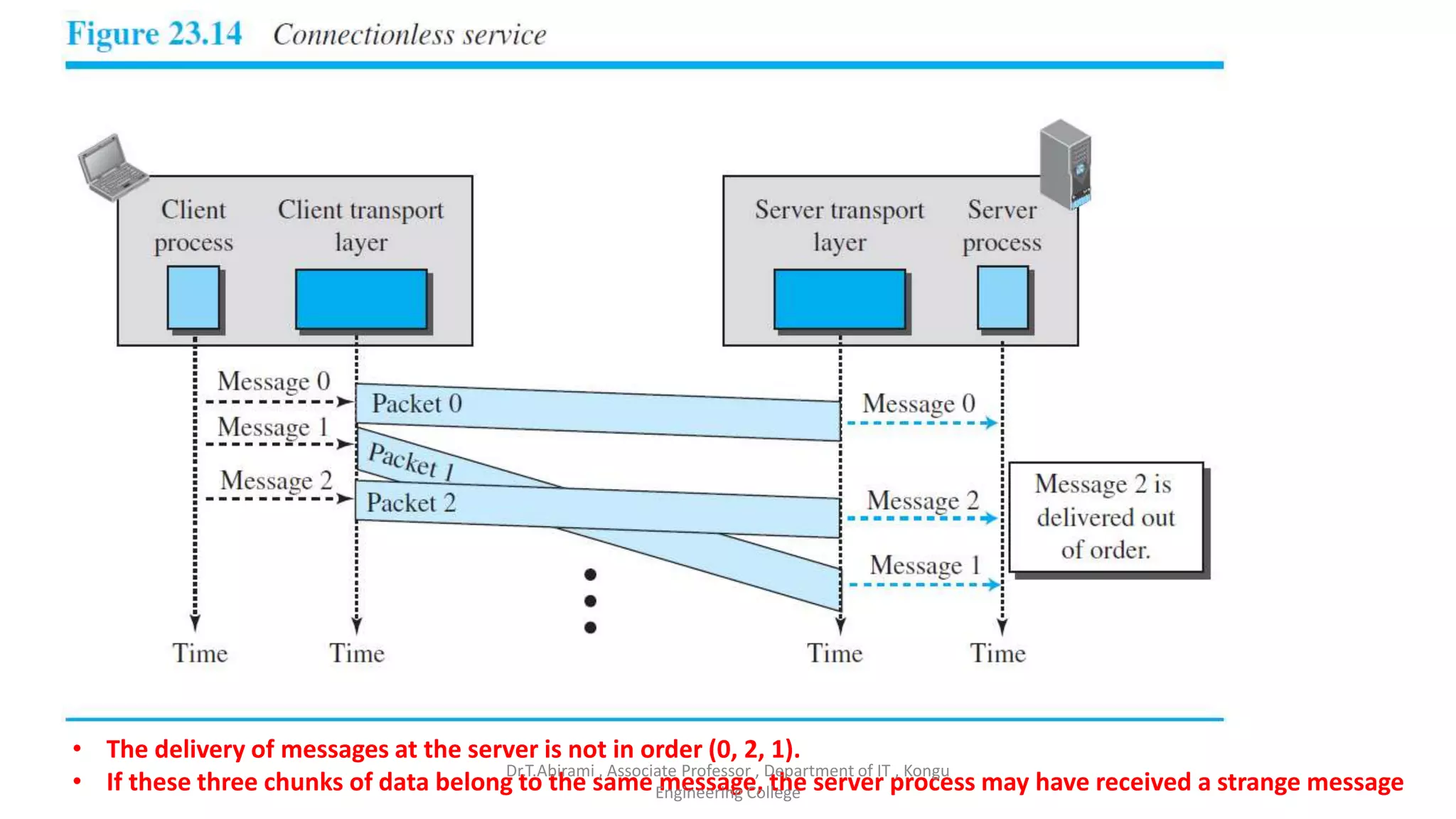
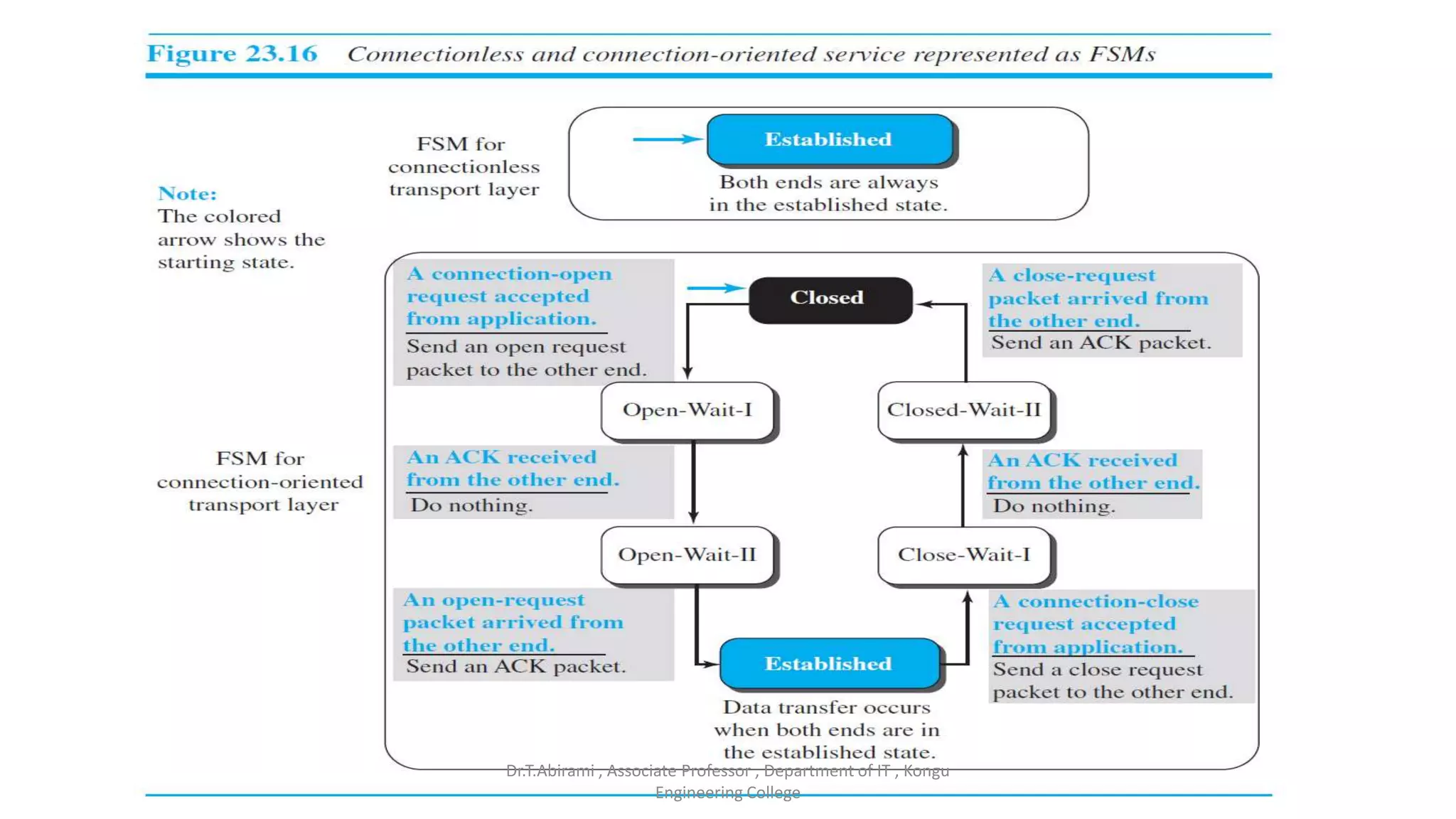
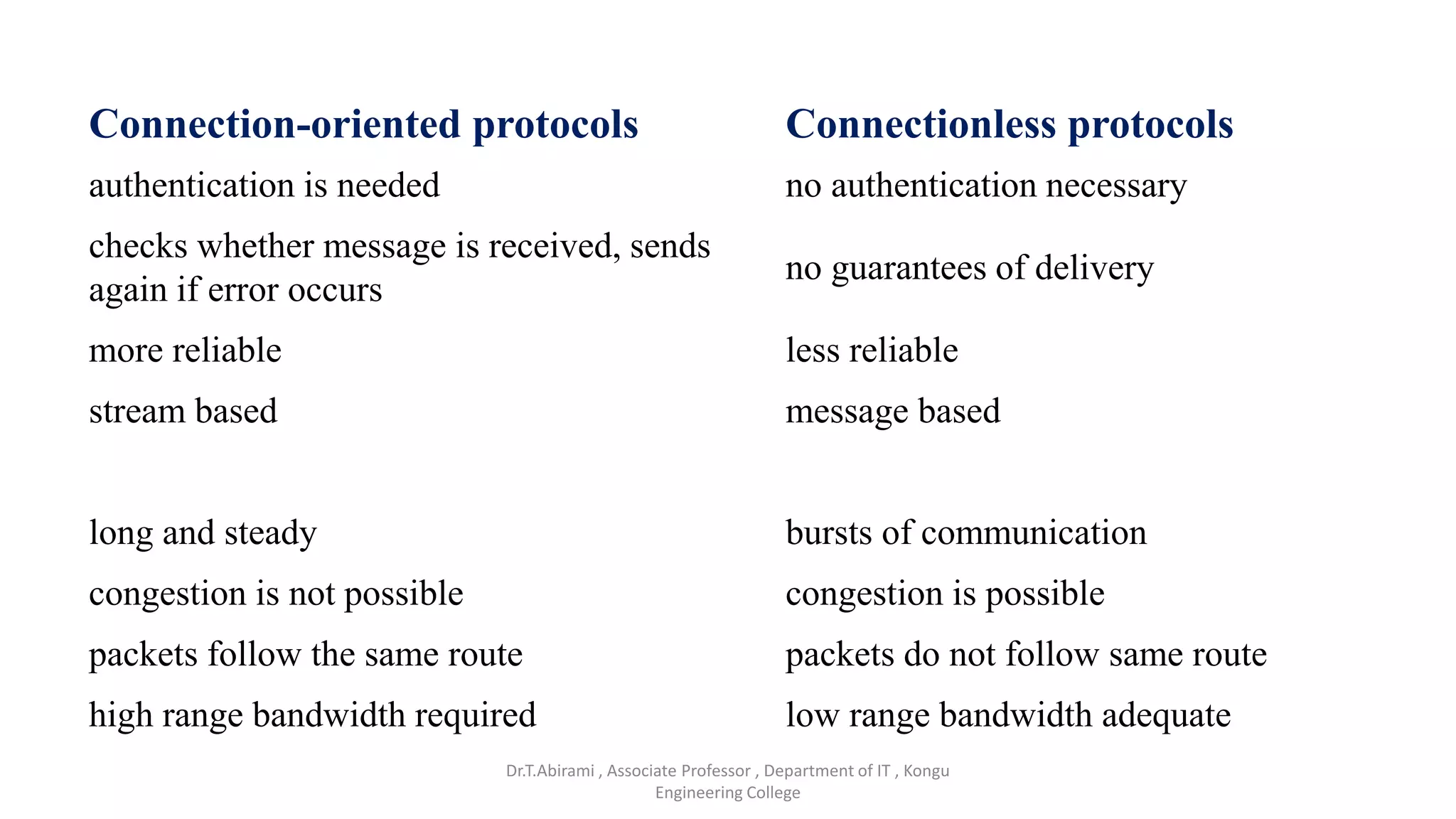
The document discusses the key functions and protocols of the transport layer. It describes how the transport layer establishes end-to-end connections between hosts, delivers data through encapsulation and multiplexing, and provides services like flow control, error control, and congestion control. The major transport layer protocols are TCP and UDP, with TCP providing connection-oriented and reliable data transfer, and UDP being connectionless.