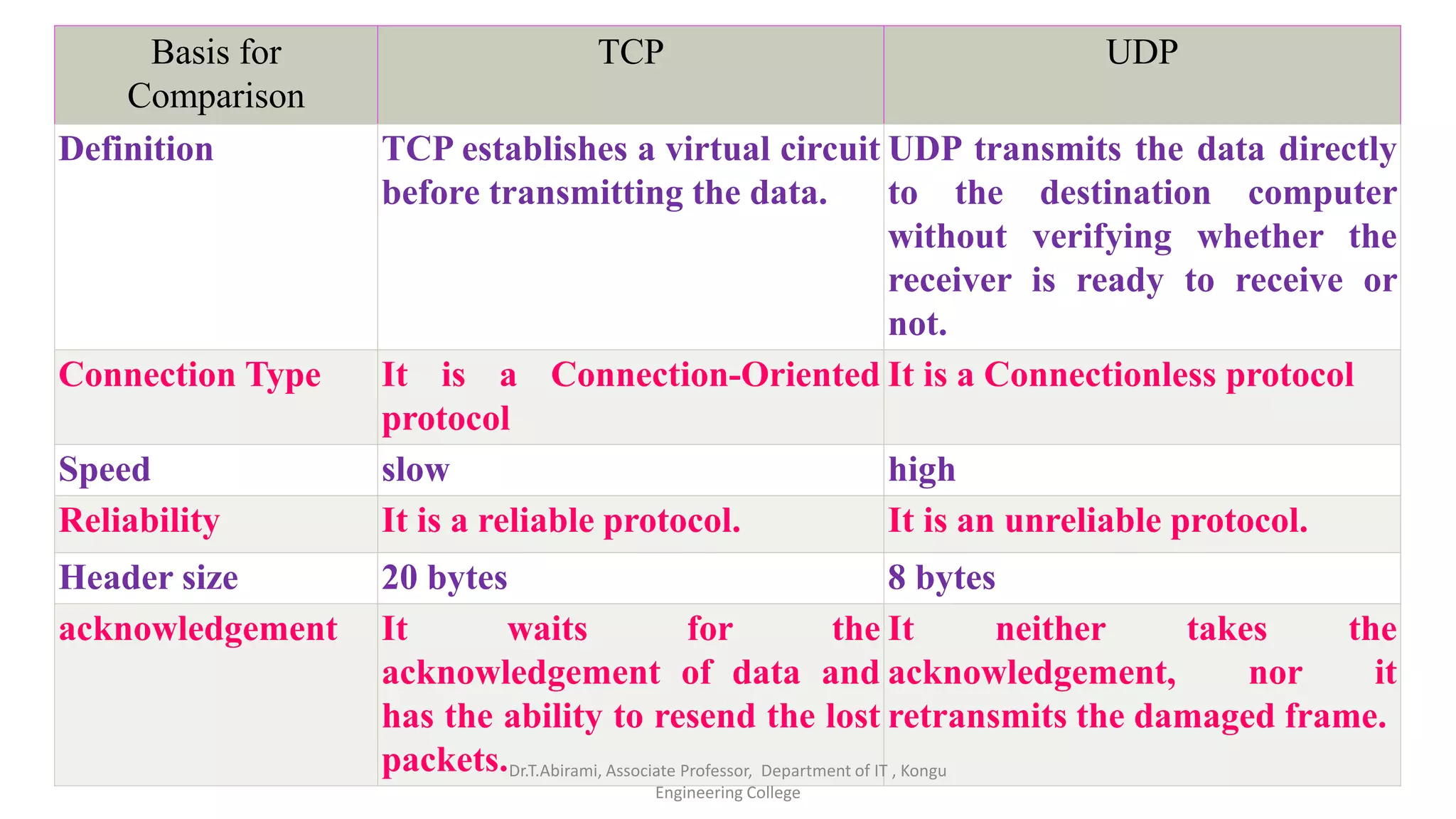
1. The document discusses the Transport Layer protocols TCP and UDP. TCP provides connection-oriented and reliable transmission, while UDP provides connectionless and unreliable transmission.
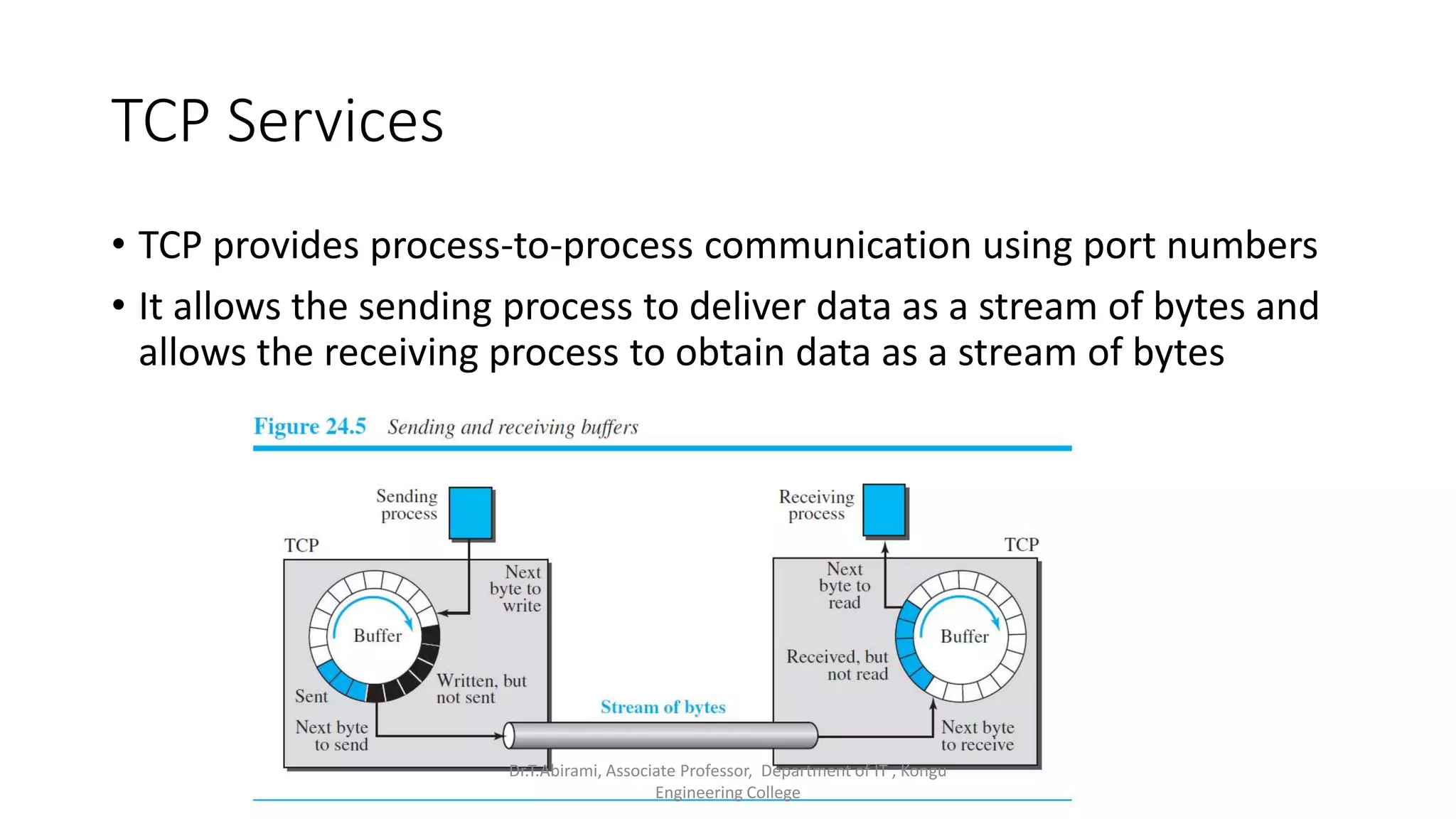
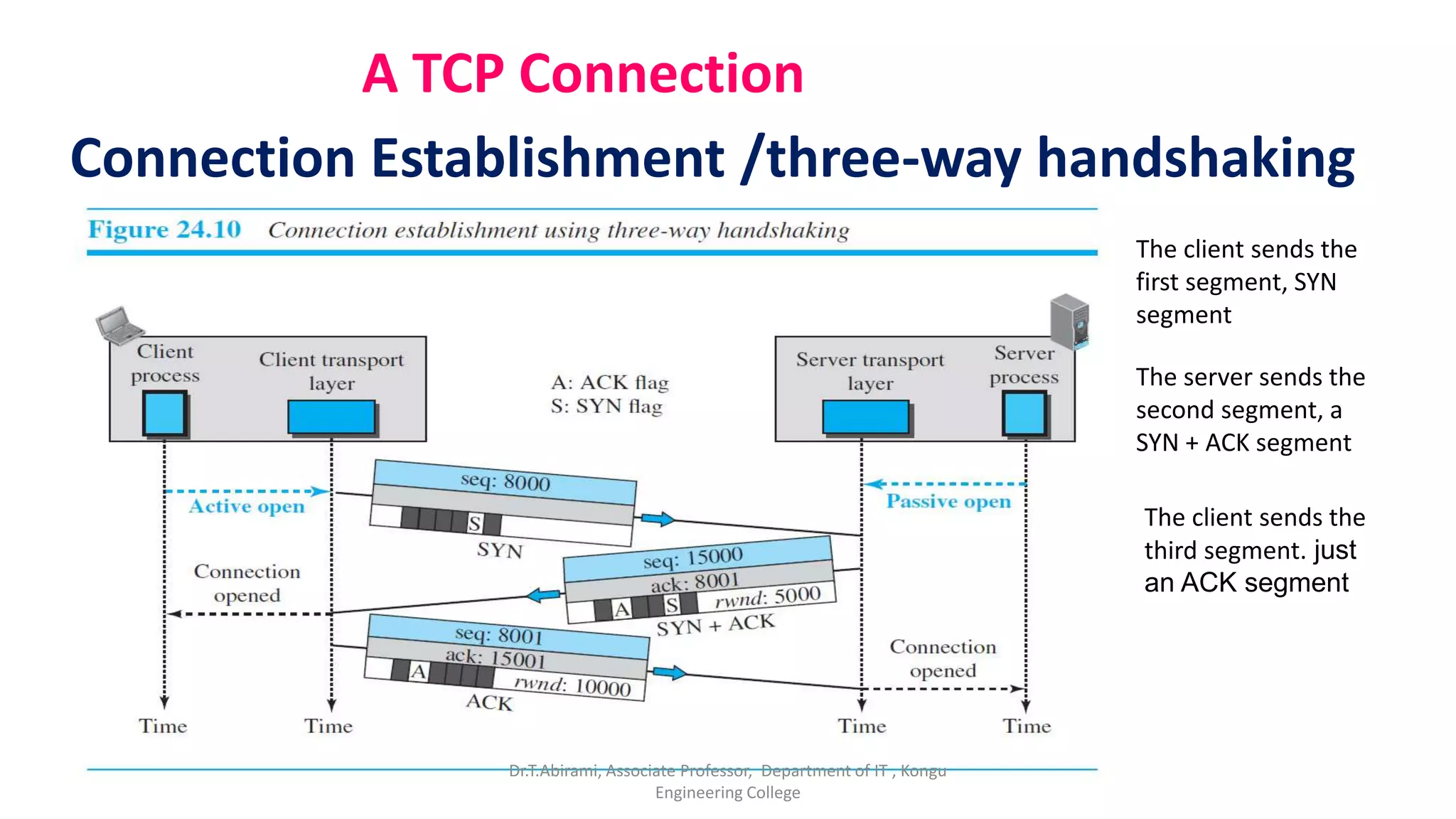
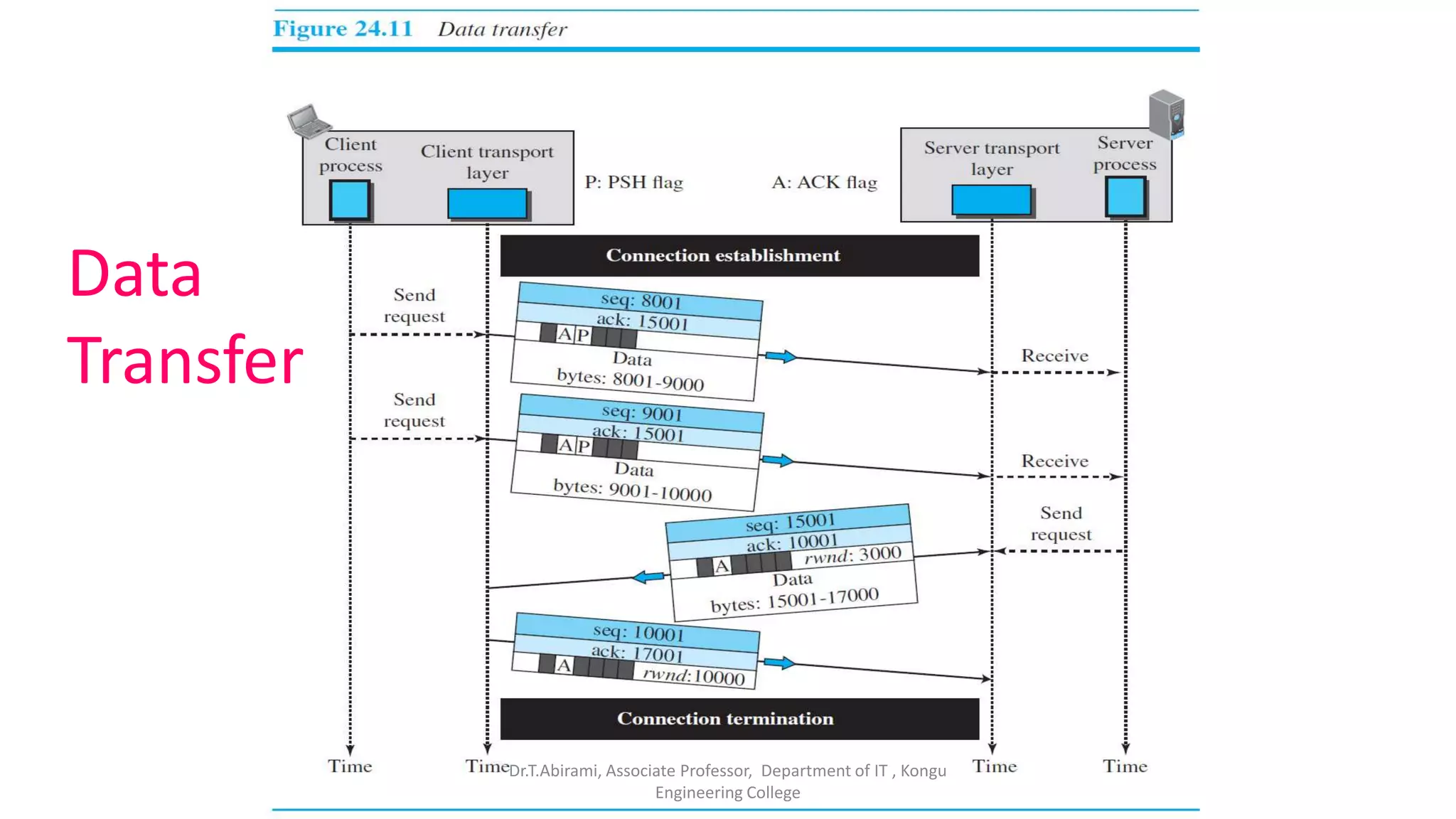
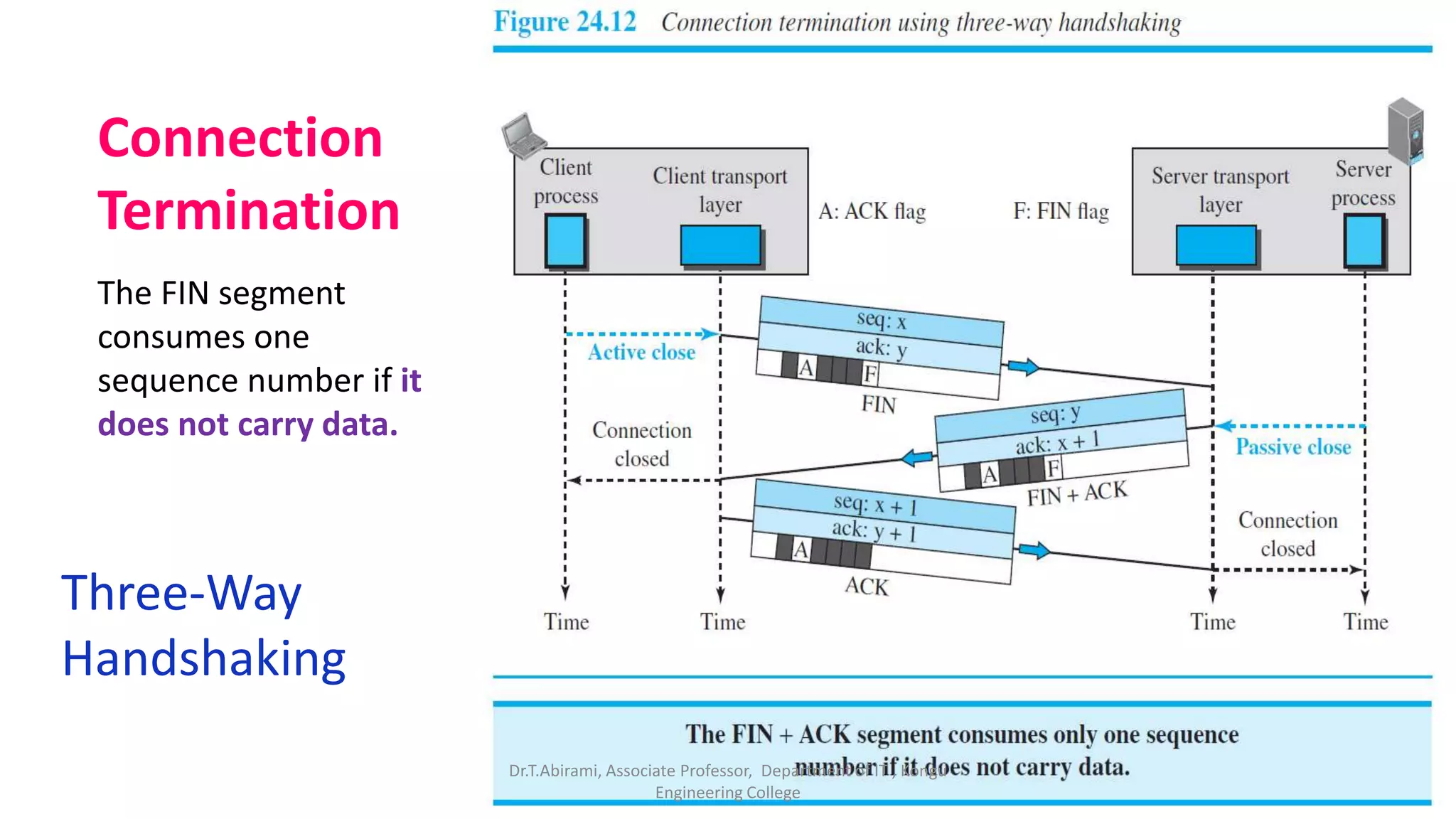
2. TCP establishes connections between processes using three-way handshaking and provides flow control, error checking, and retransmission of lost packets to ensure reliable delivery.
3. UDP is a simpler protocol that does not establish connections or ensure delivery. It is used for applications that require low-latency transmission and can tolerate some data loss.