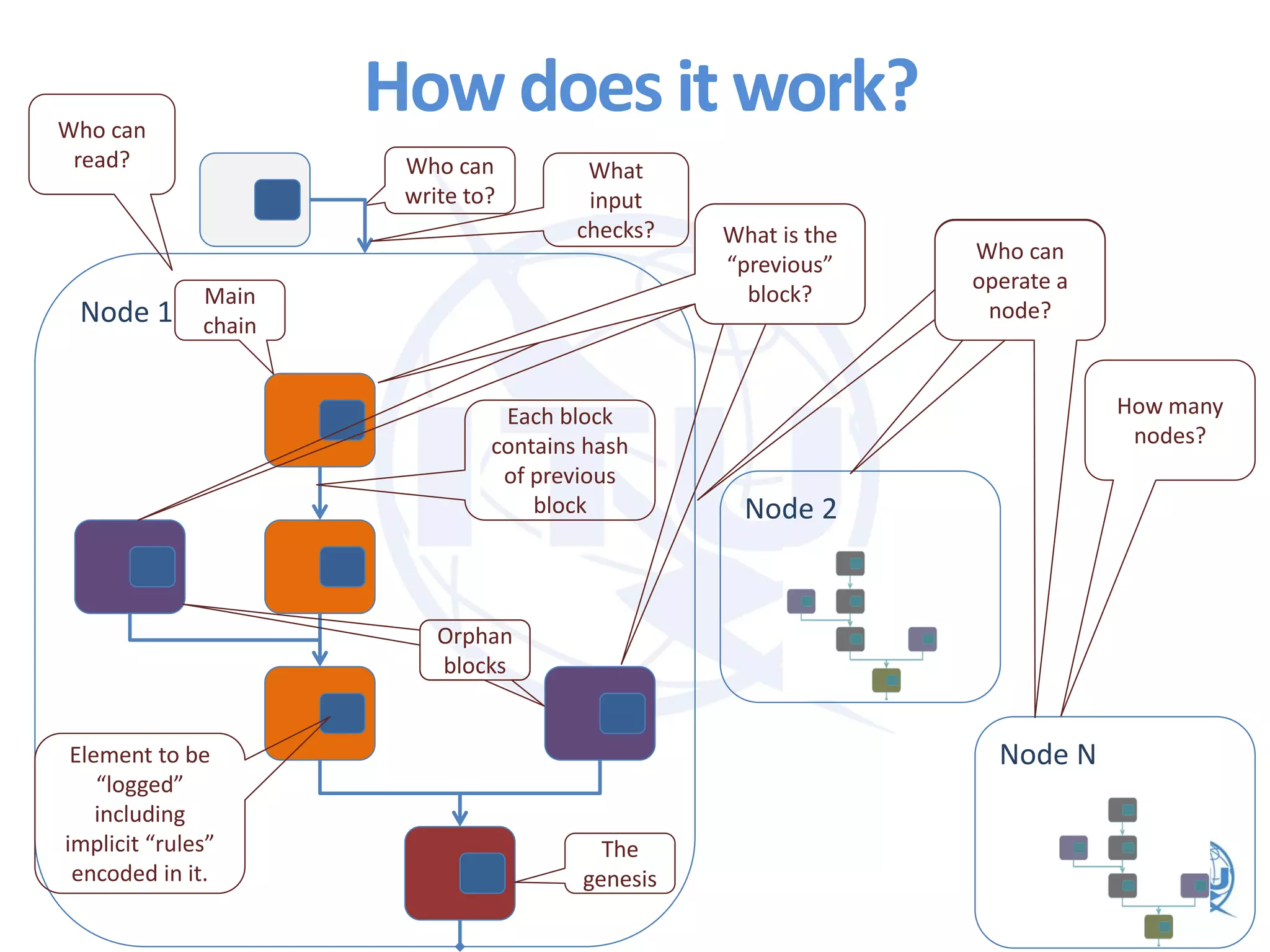
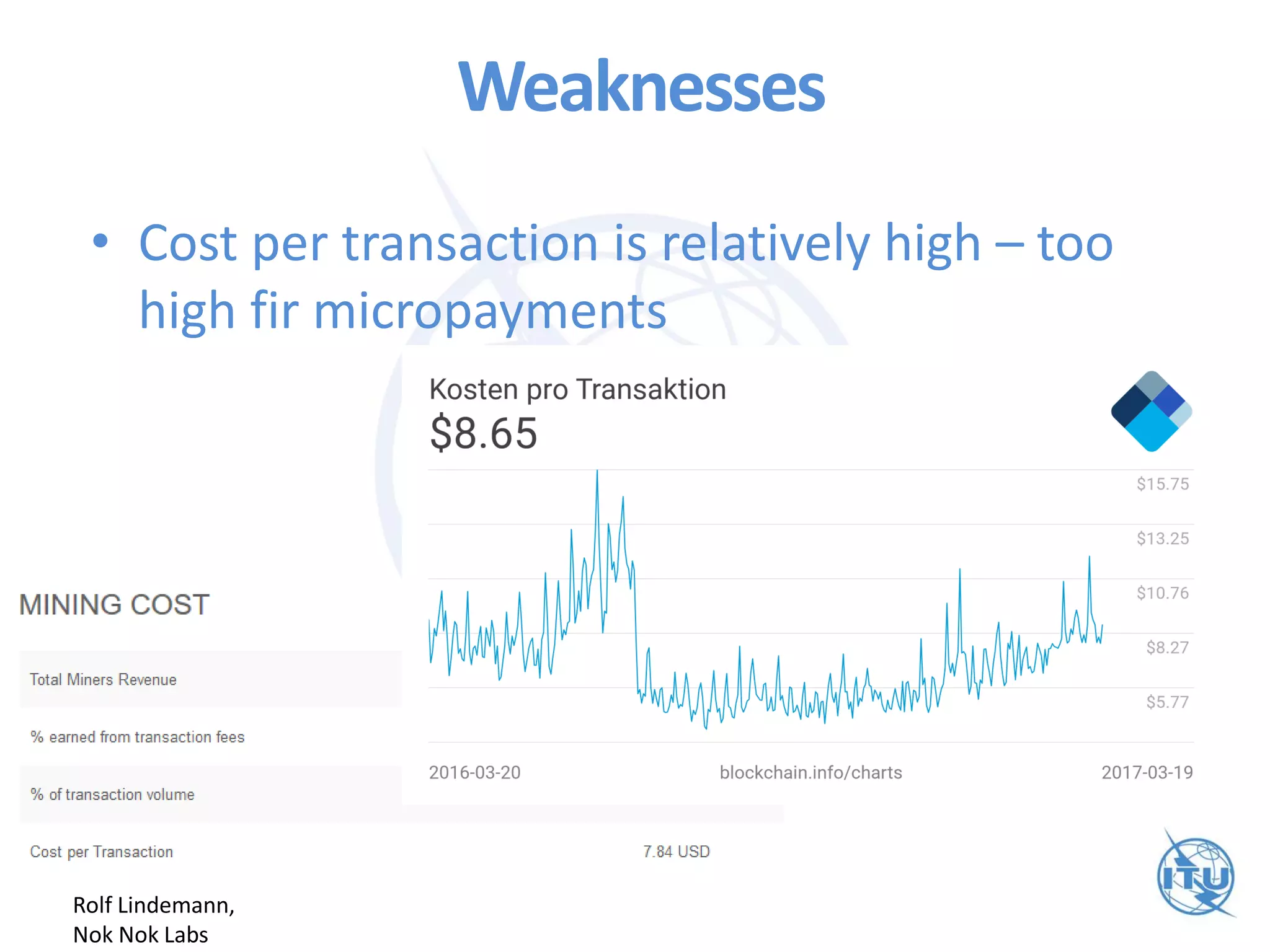
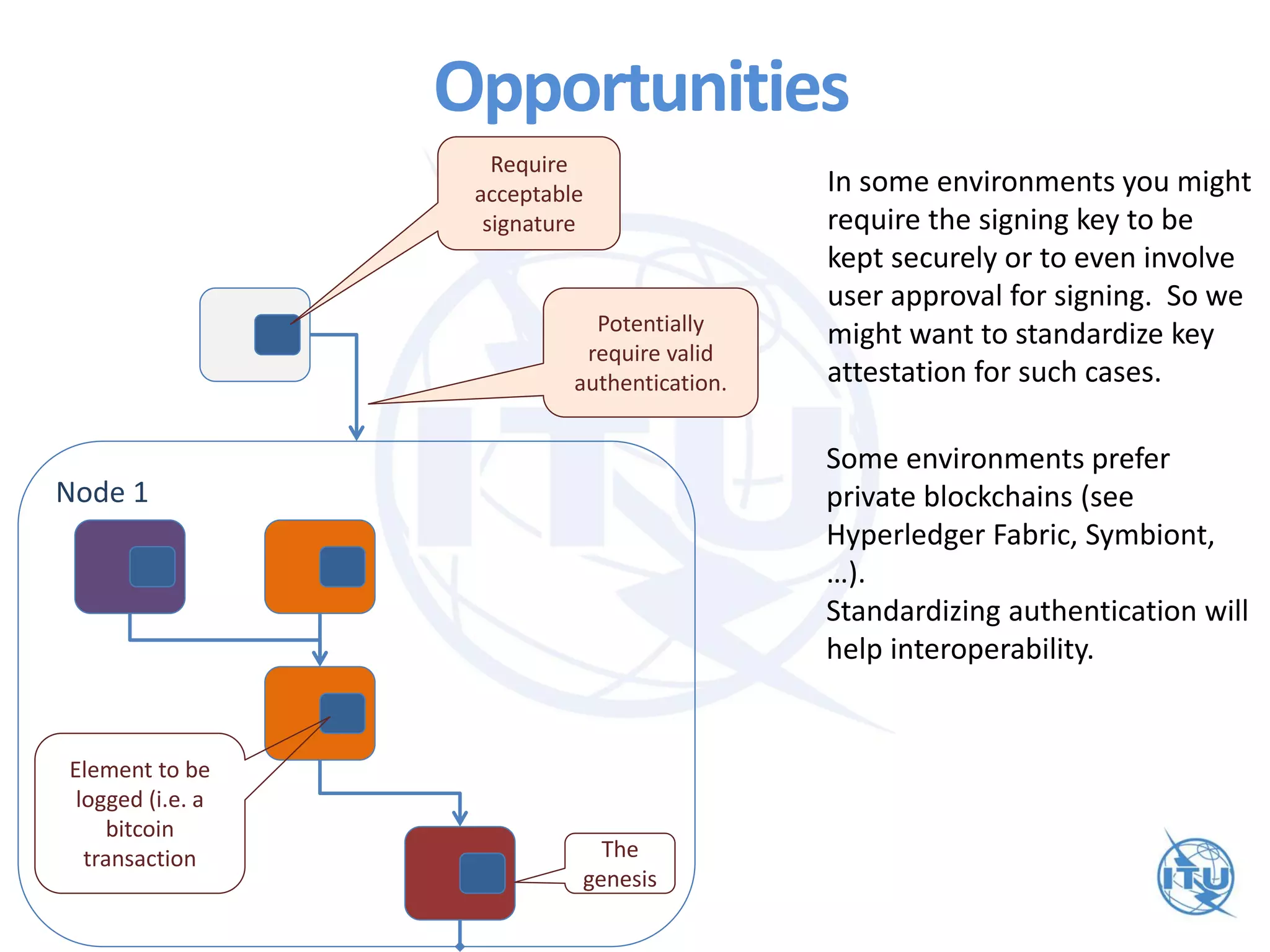
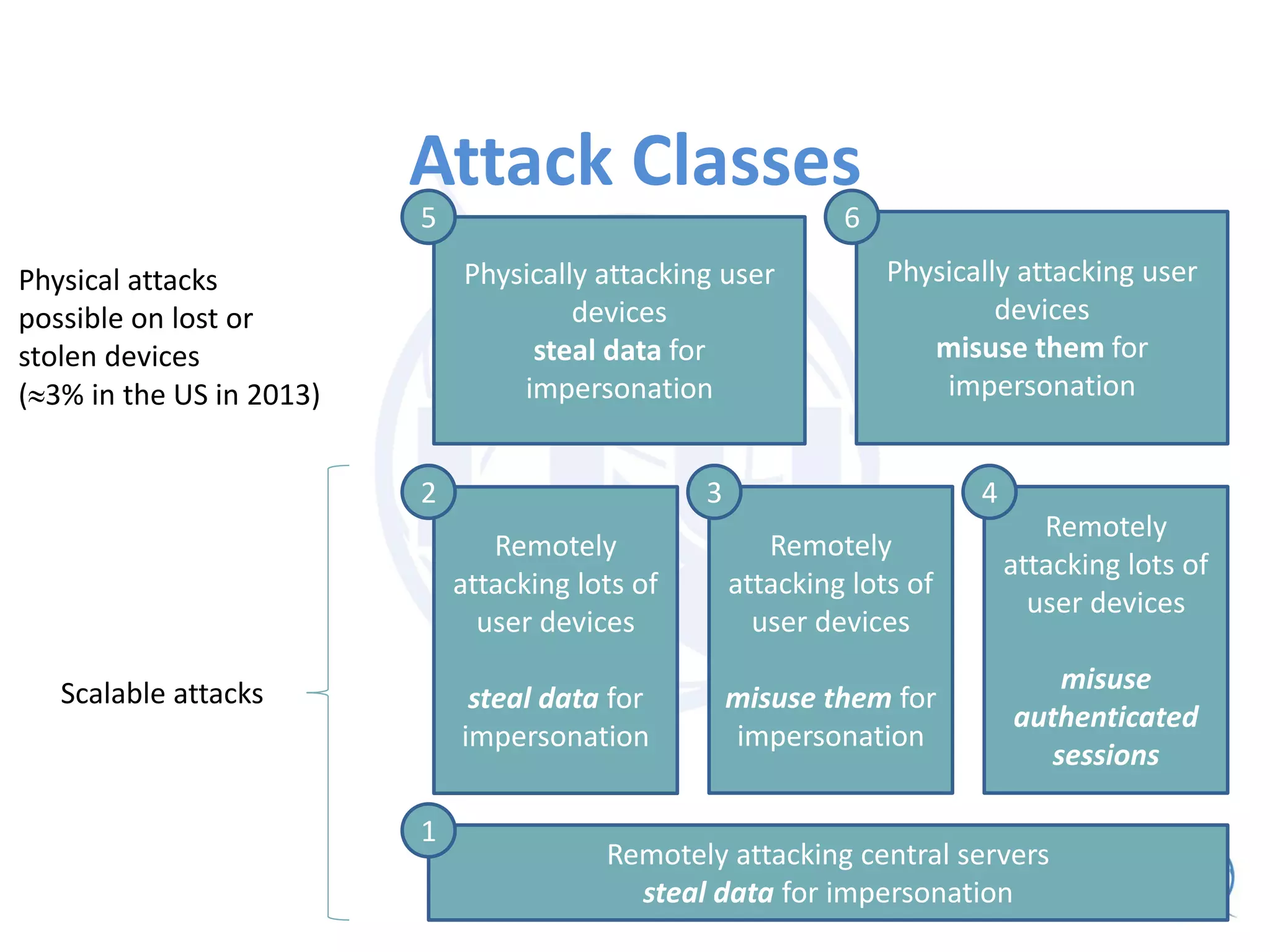
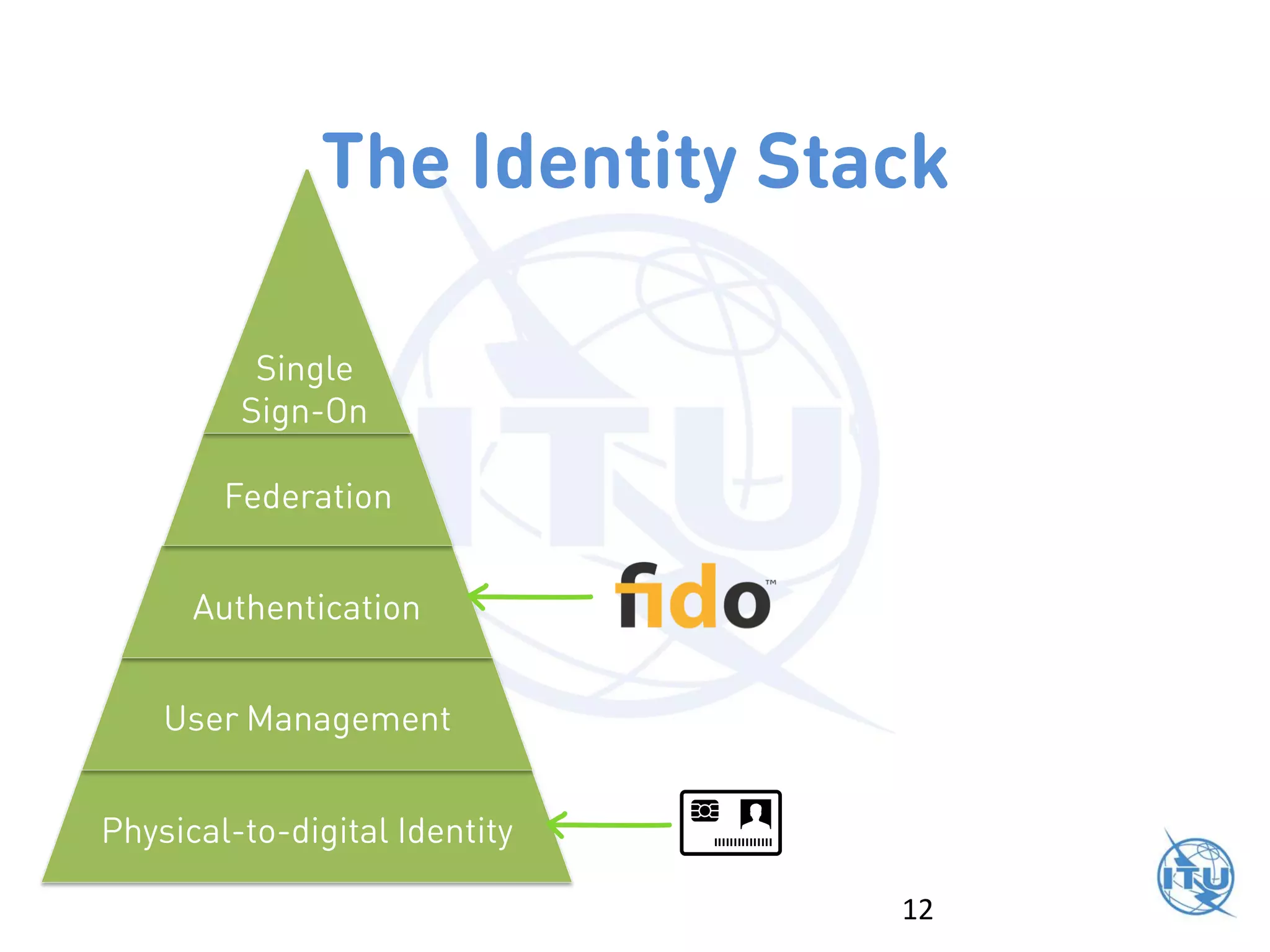
The ITU workshop on blockchain security highlighted that the term 'blockchain' lacks a clear definition and cautioned against putting sensitive data into public blockchains due to potential long-term vulnerabilities. It proposed exploring standardization of deprecated cryptographic algorithms and authentication measures for interoperability, while also addressing weaknesses such as the irreversible nature of transactions and high costs for micropayments. Opportunities for improvement include initiatives focused on smart contracts and enhancing key attestation to reflect varying levels of assurance in blockchain transactions.