Distributed Files: Introduction, File System Architecture, Sun
Network File System and HDFS.
Distributed Multimedia Systems: Characteristics of Multimedia Data,
Quality of Service Management, Resource Management.
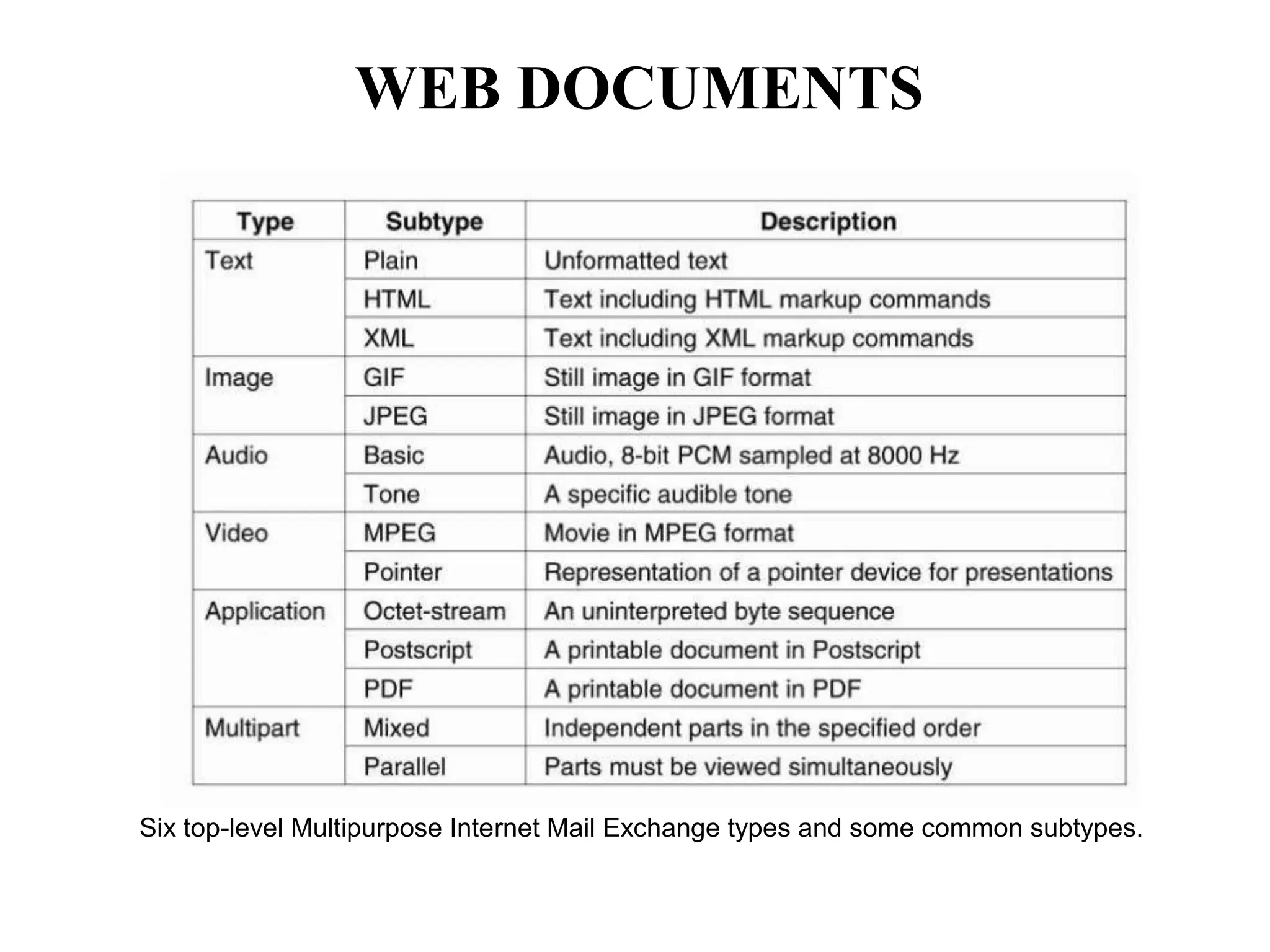
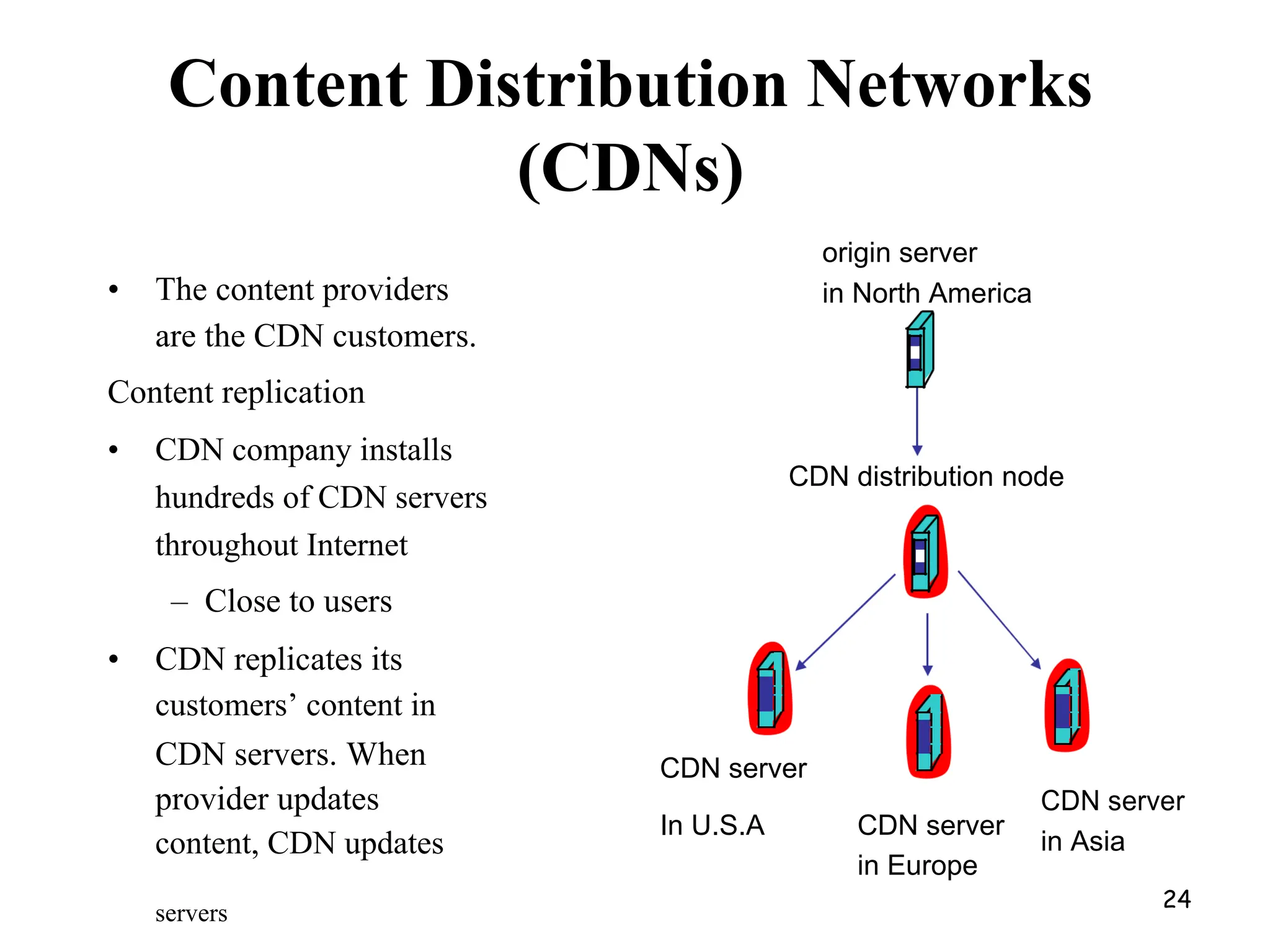
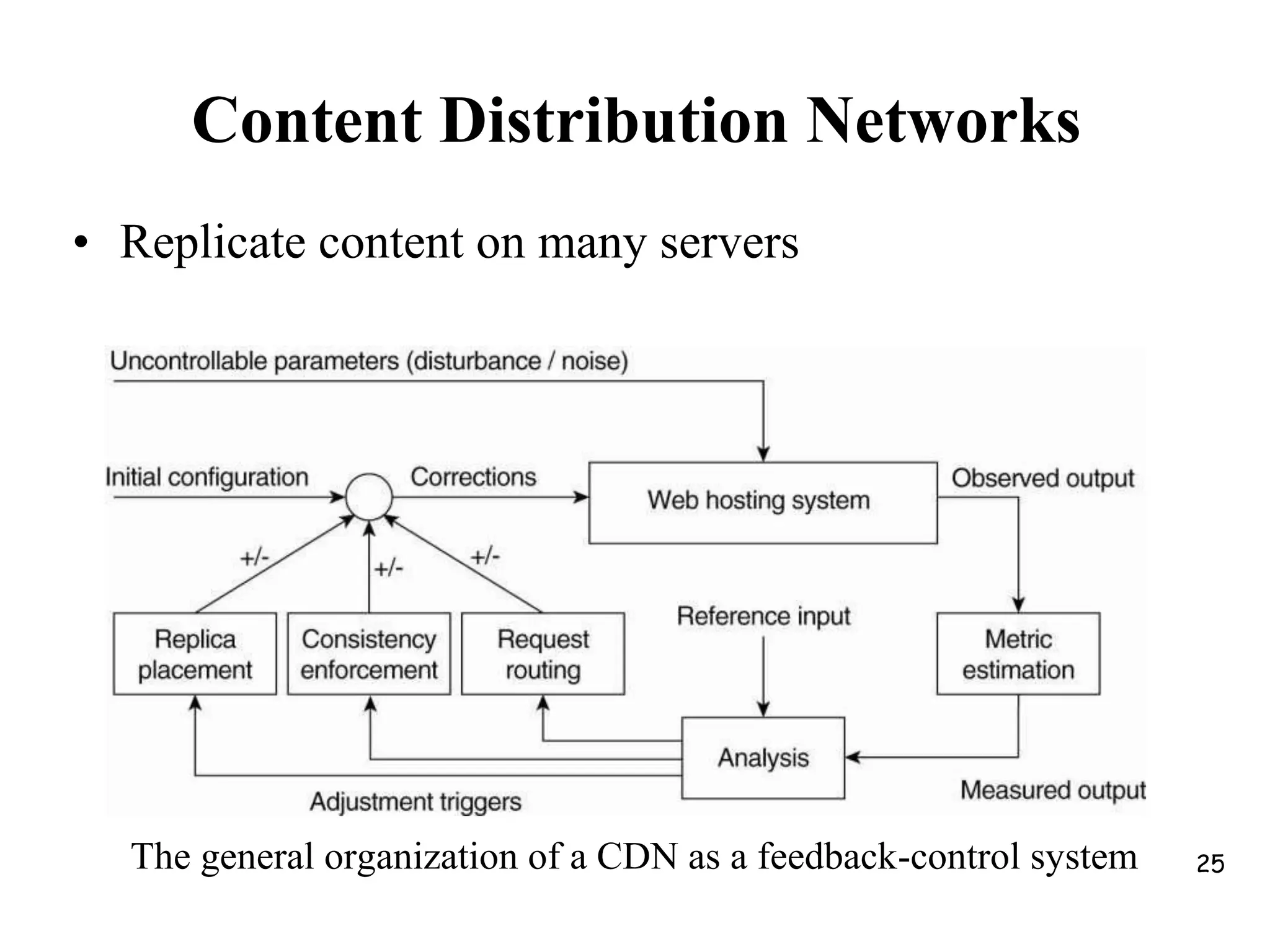
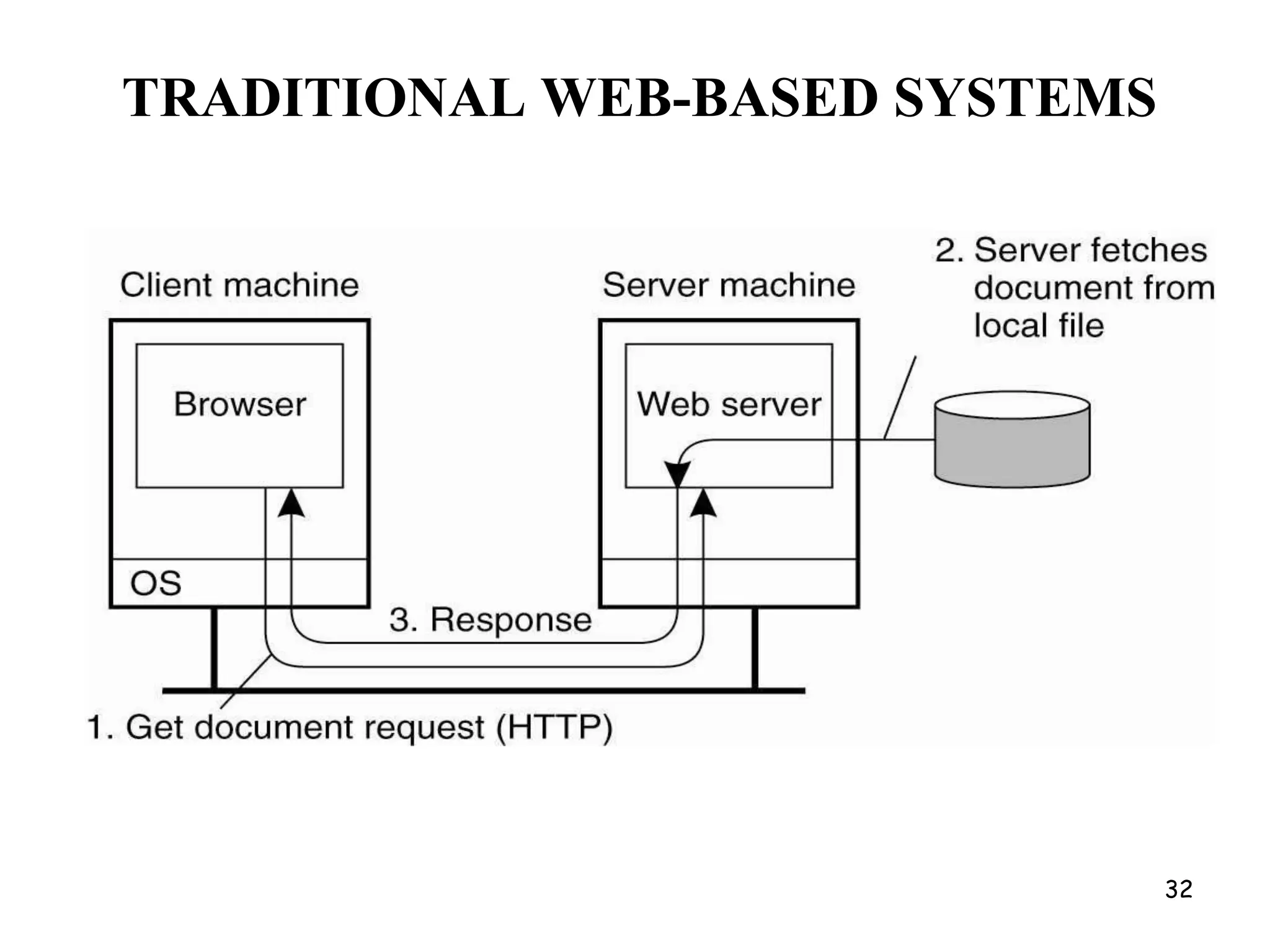
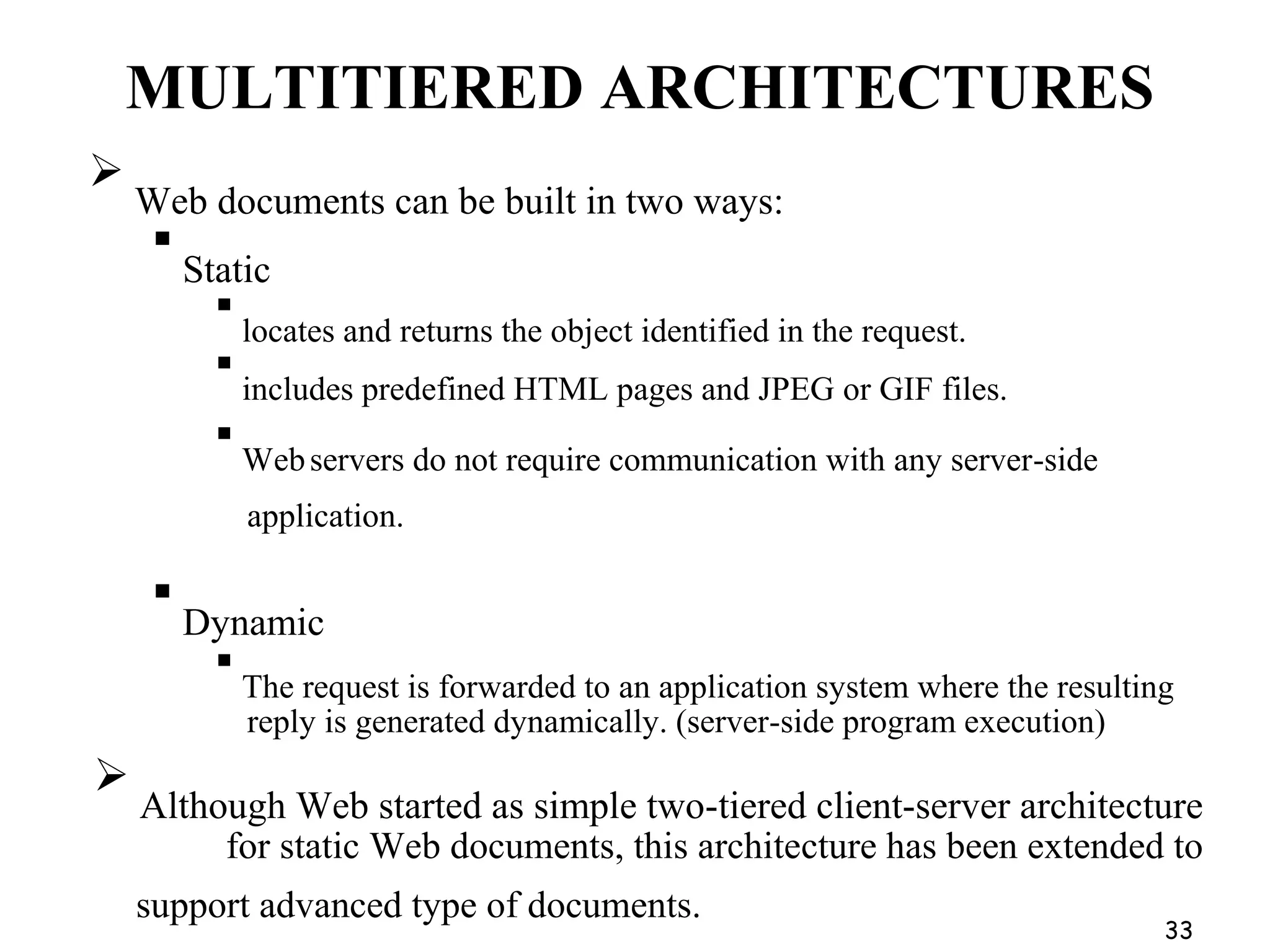
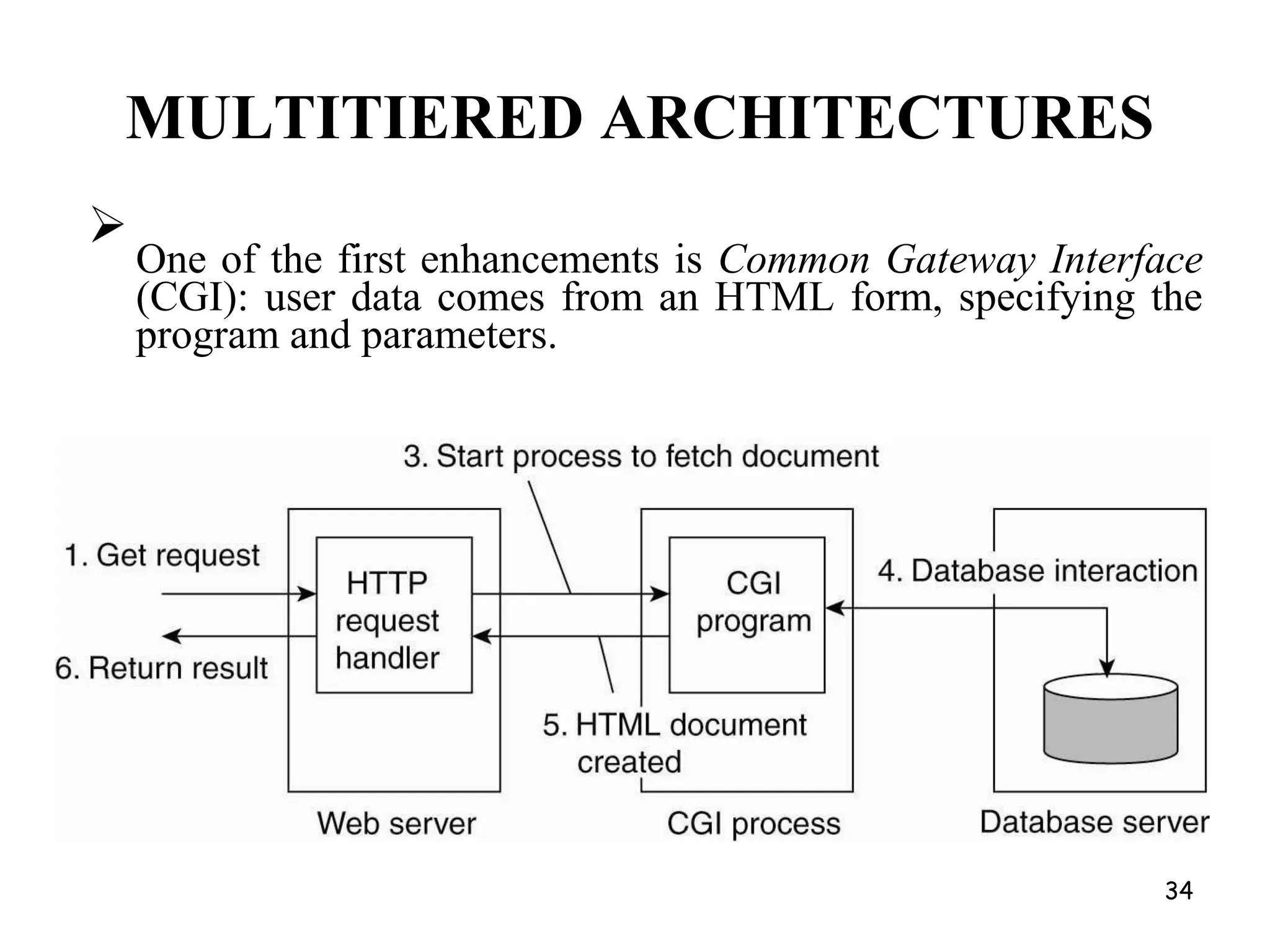
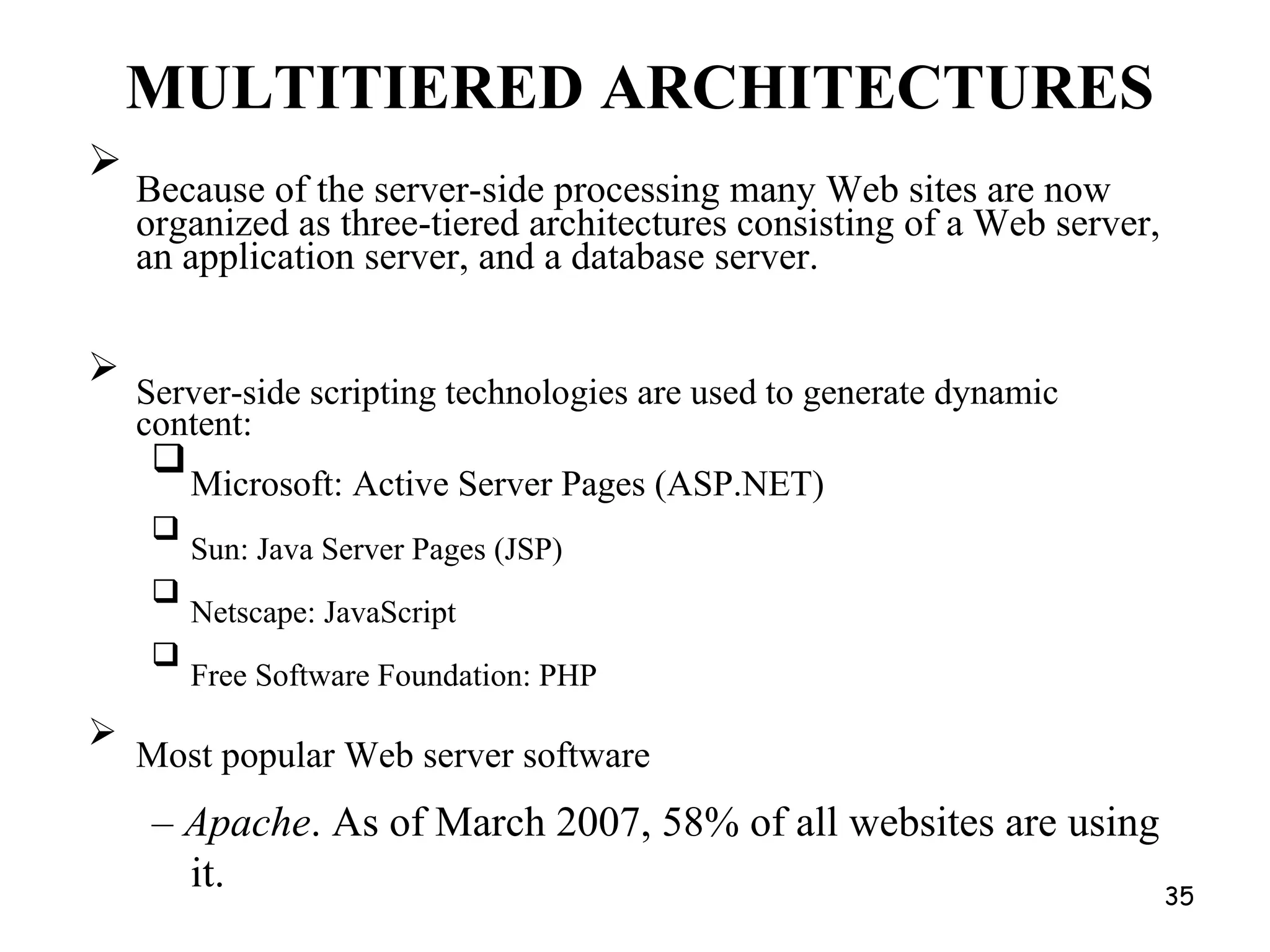
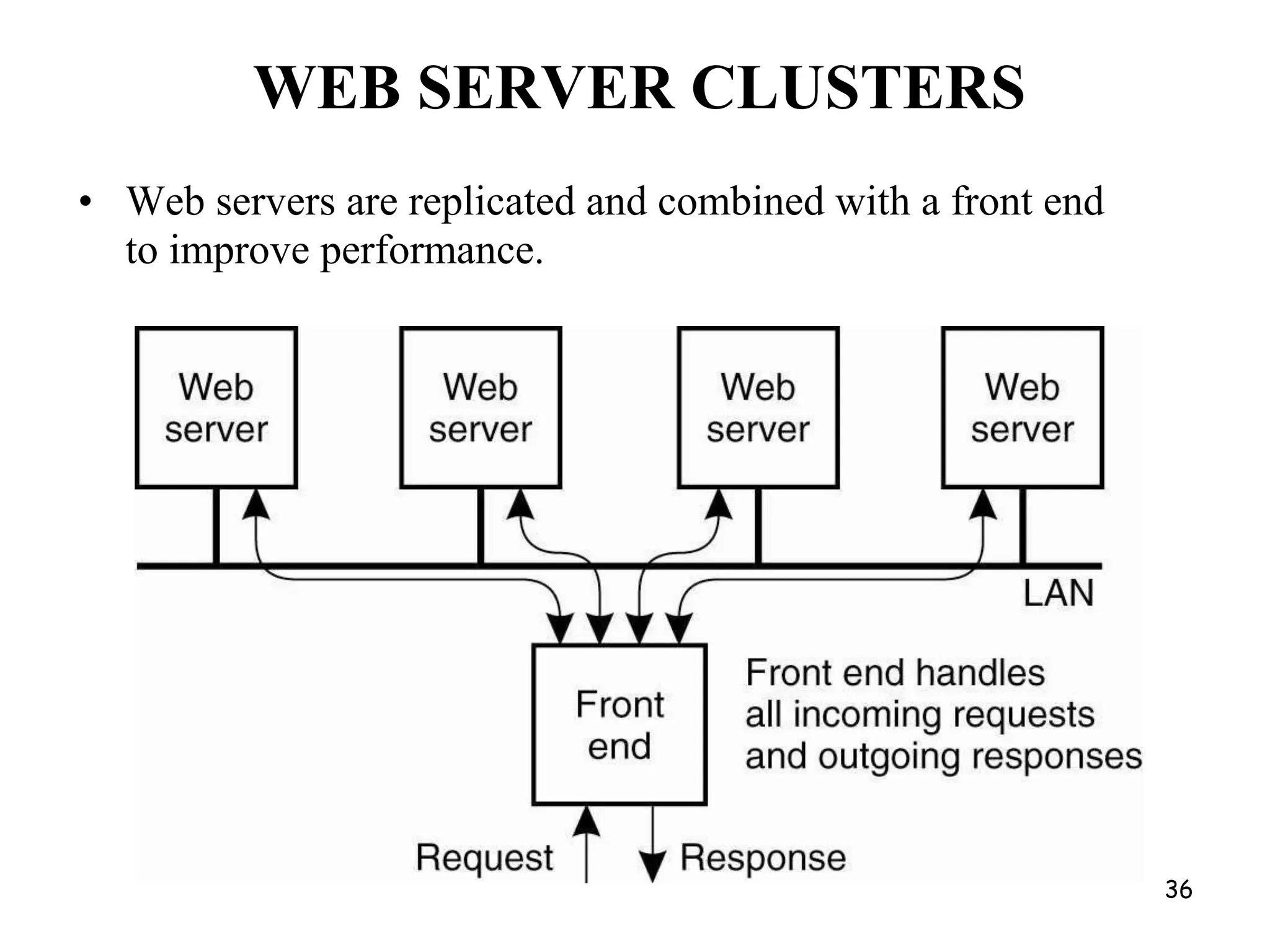
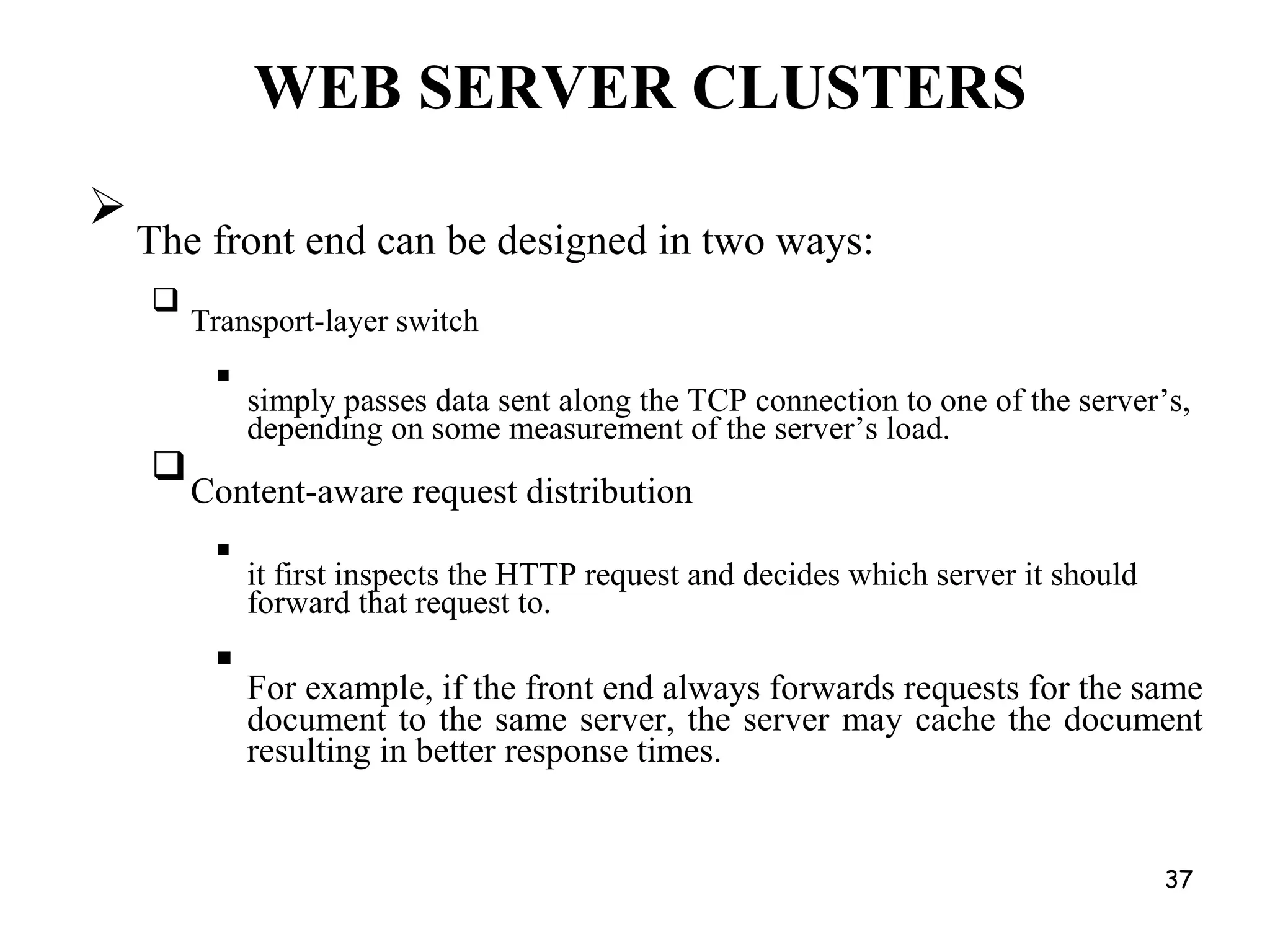
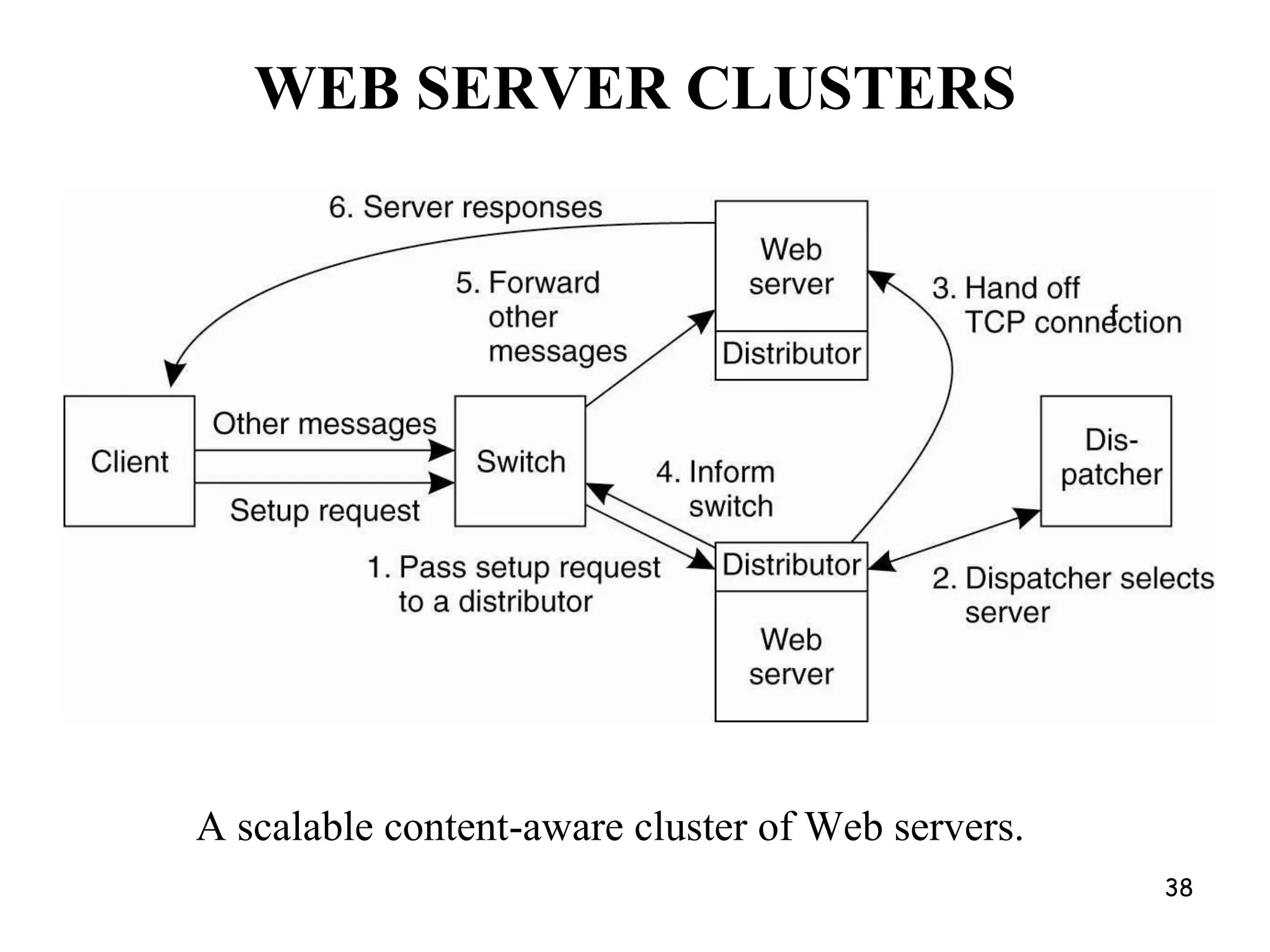
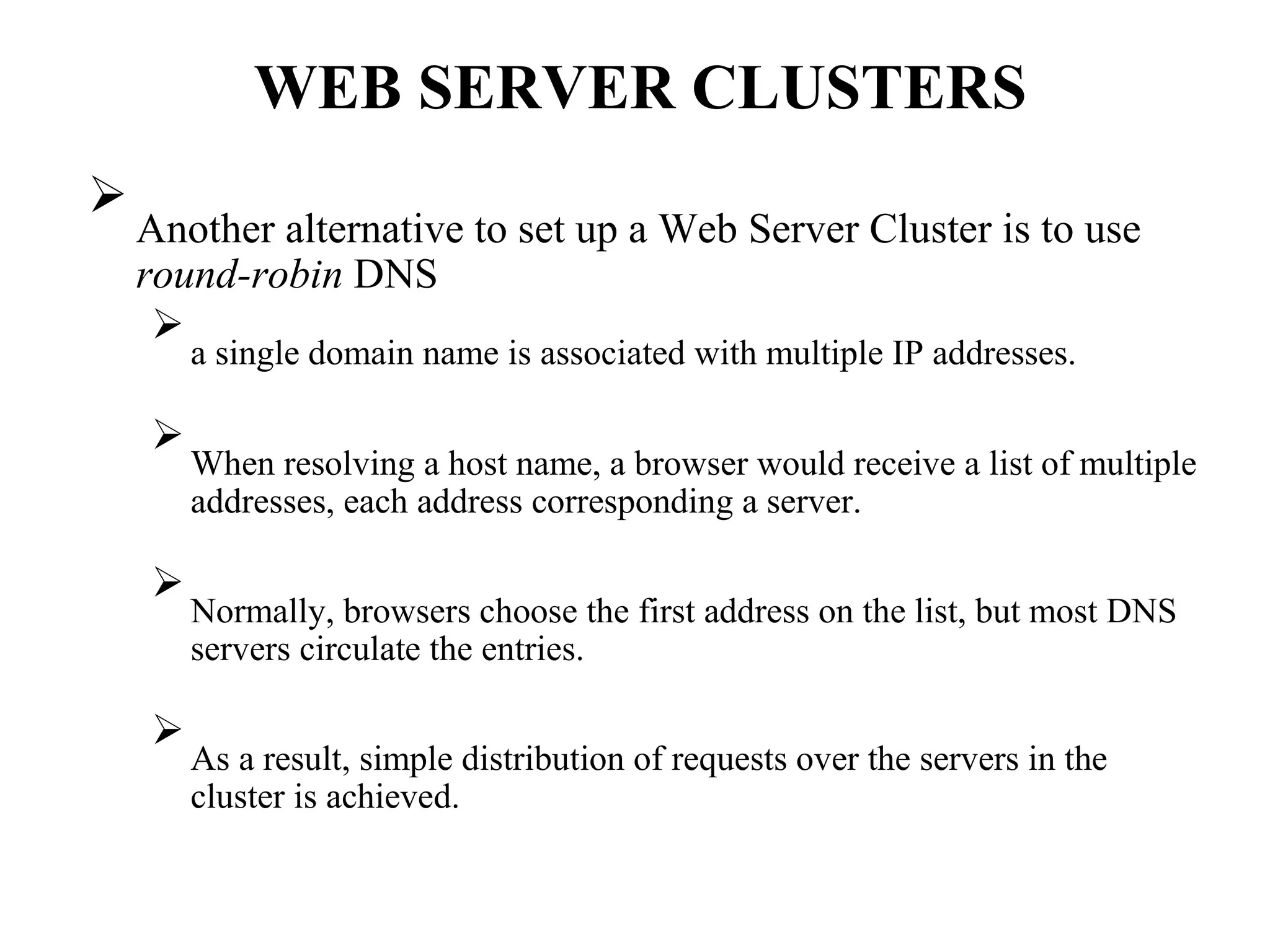
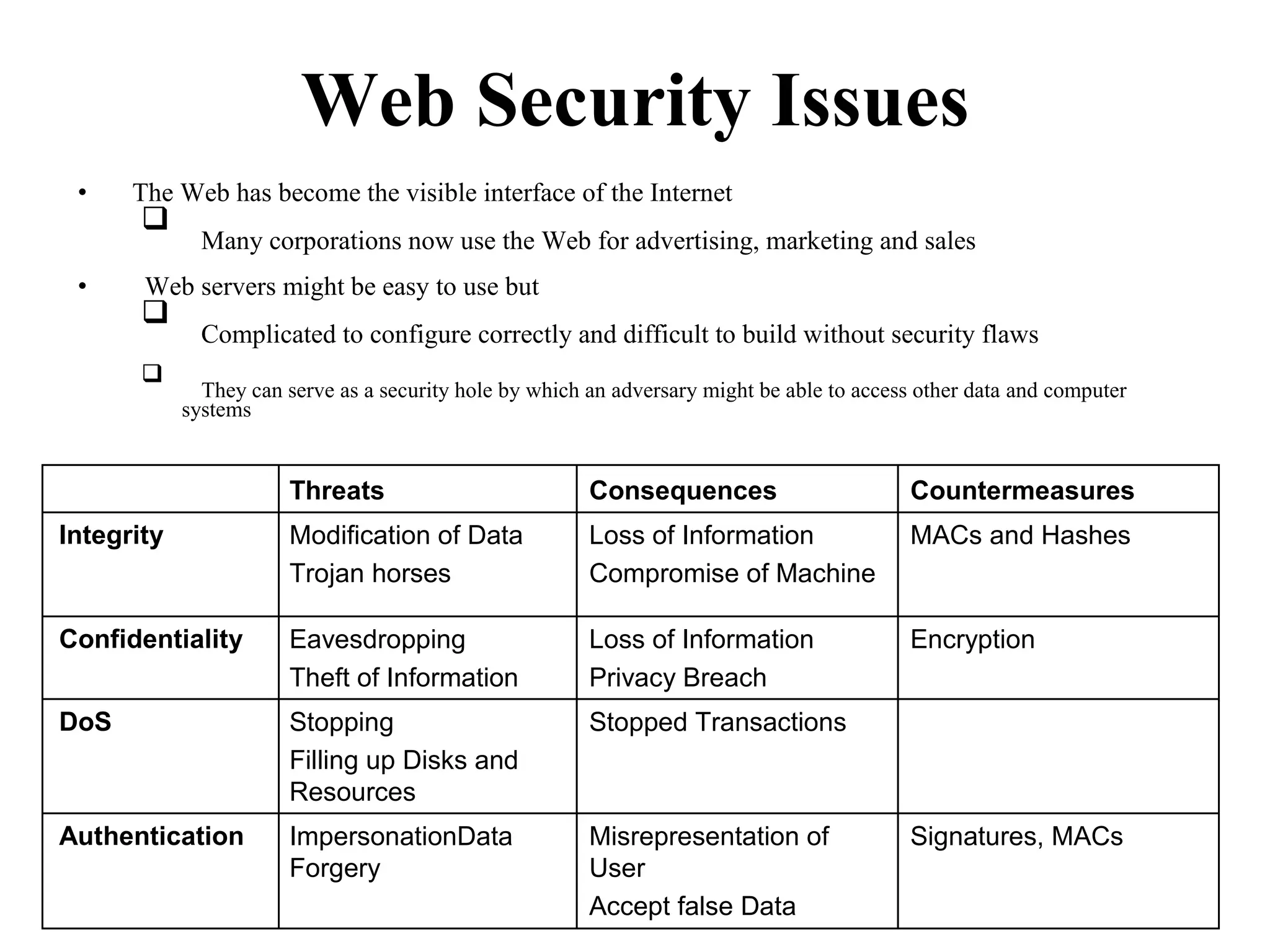
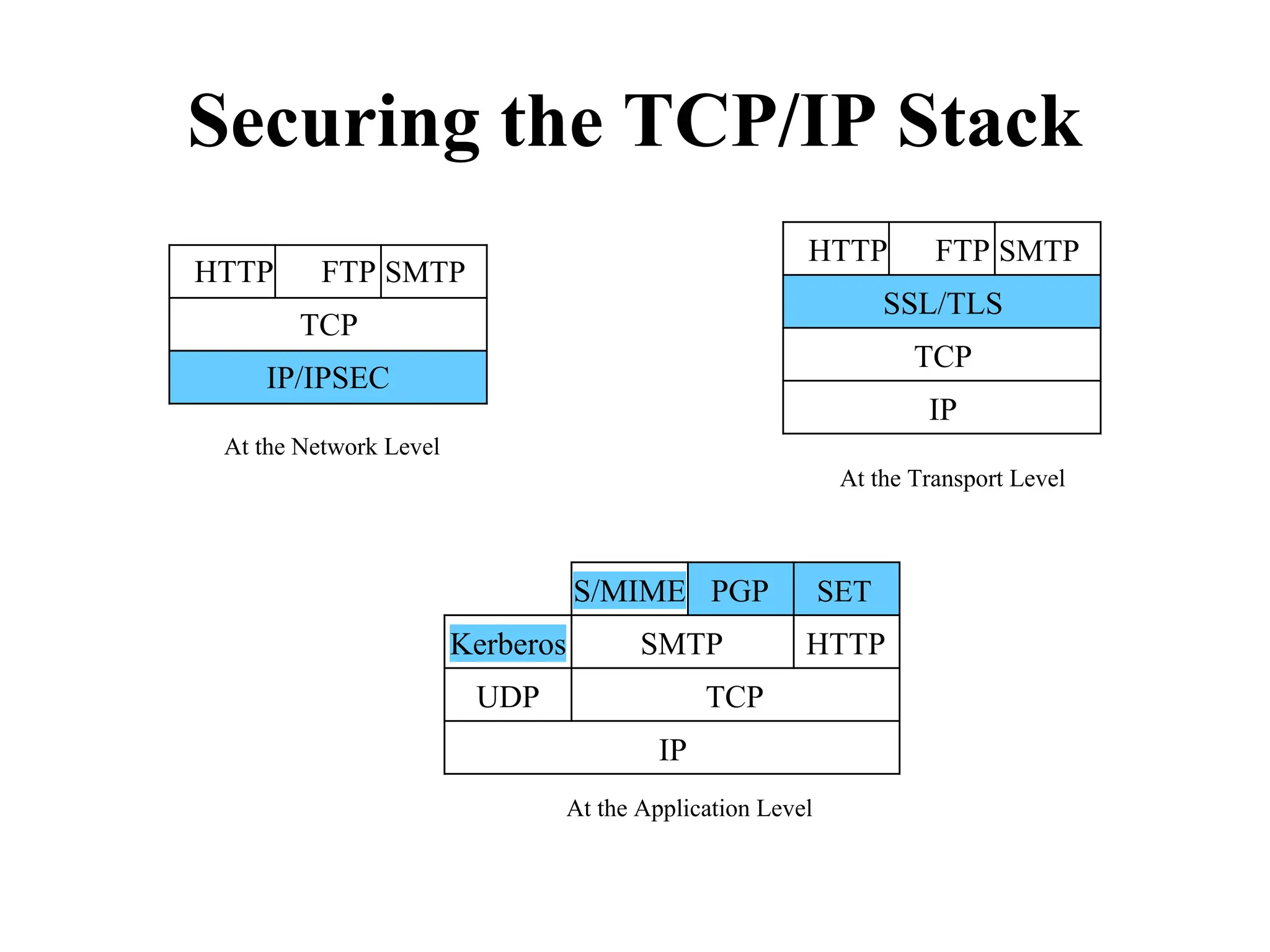
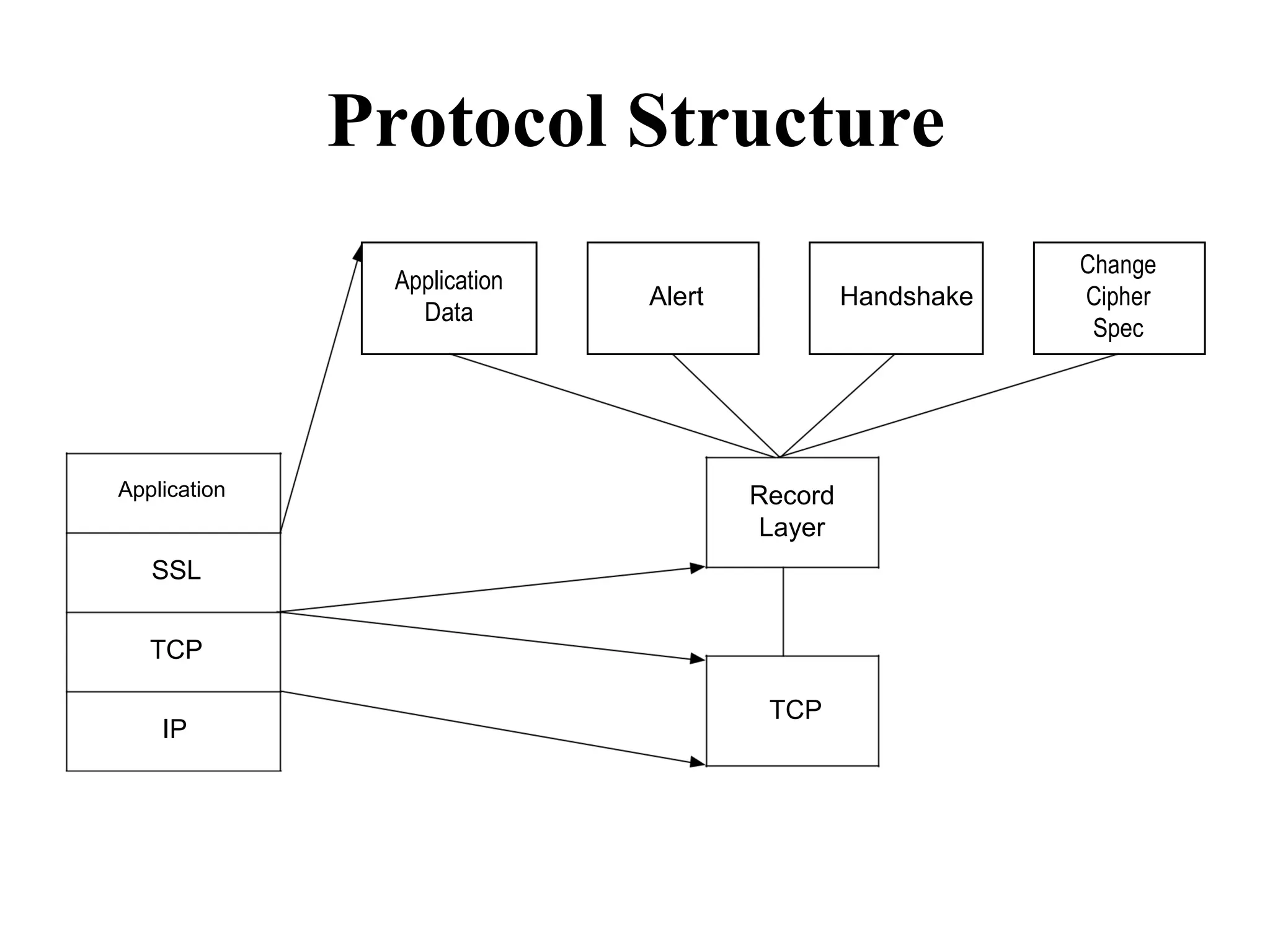
Distributed Web Based Systems: Architecture of Traditional Web-
Based Systems, Apache Web Server, Web Server Clusters,
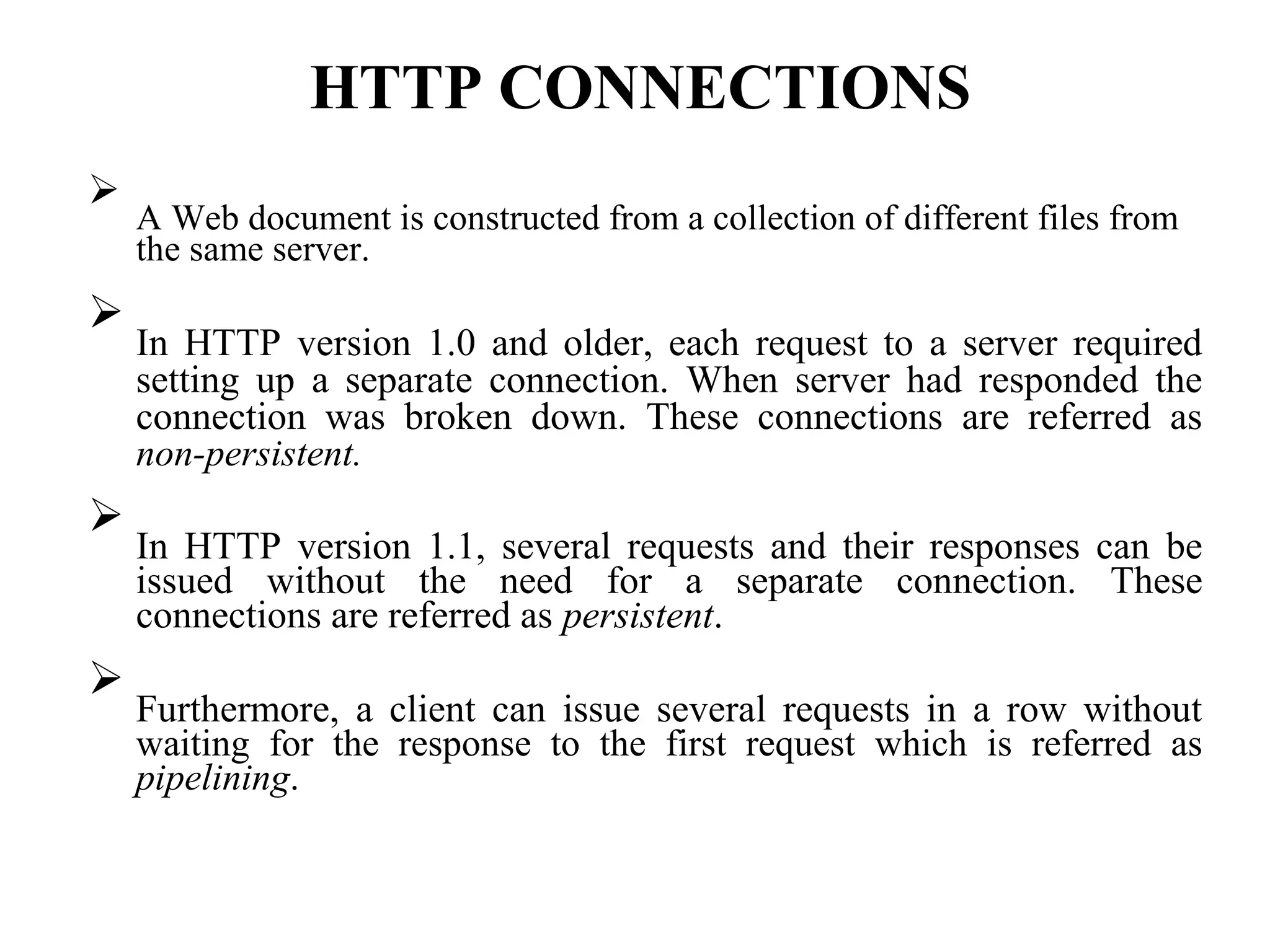
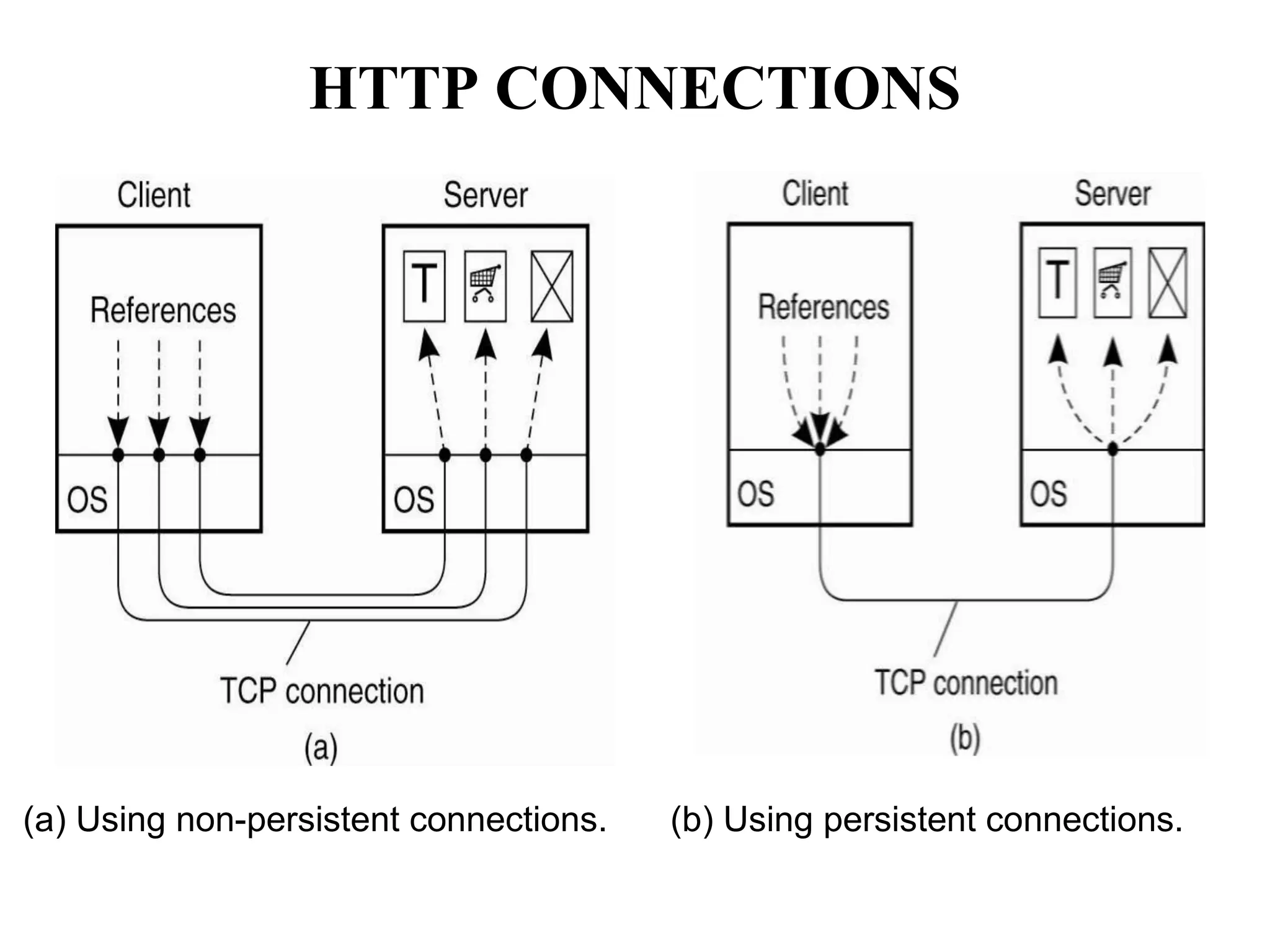
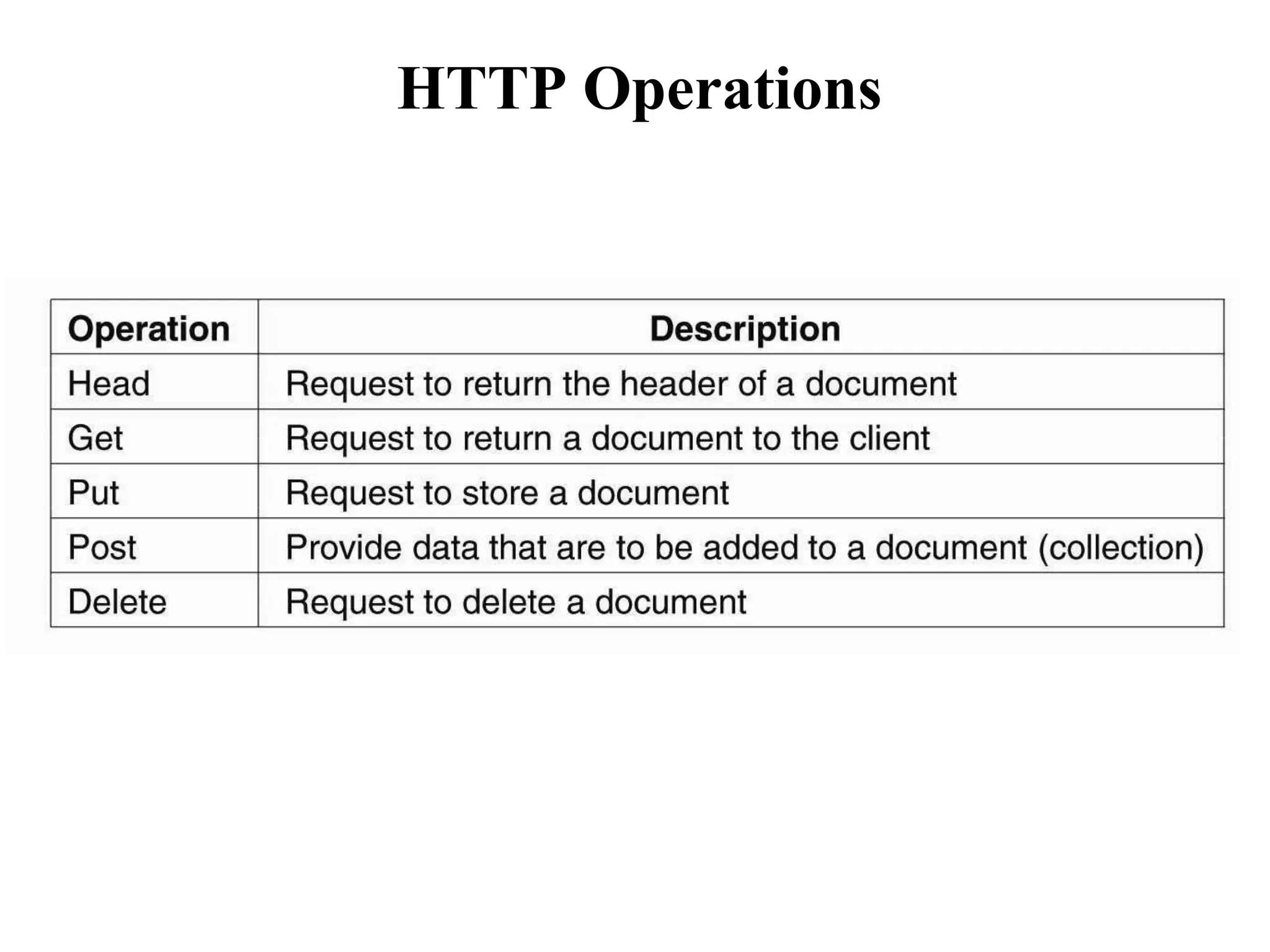
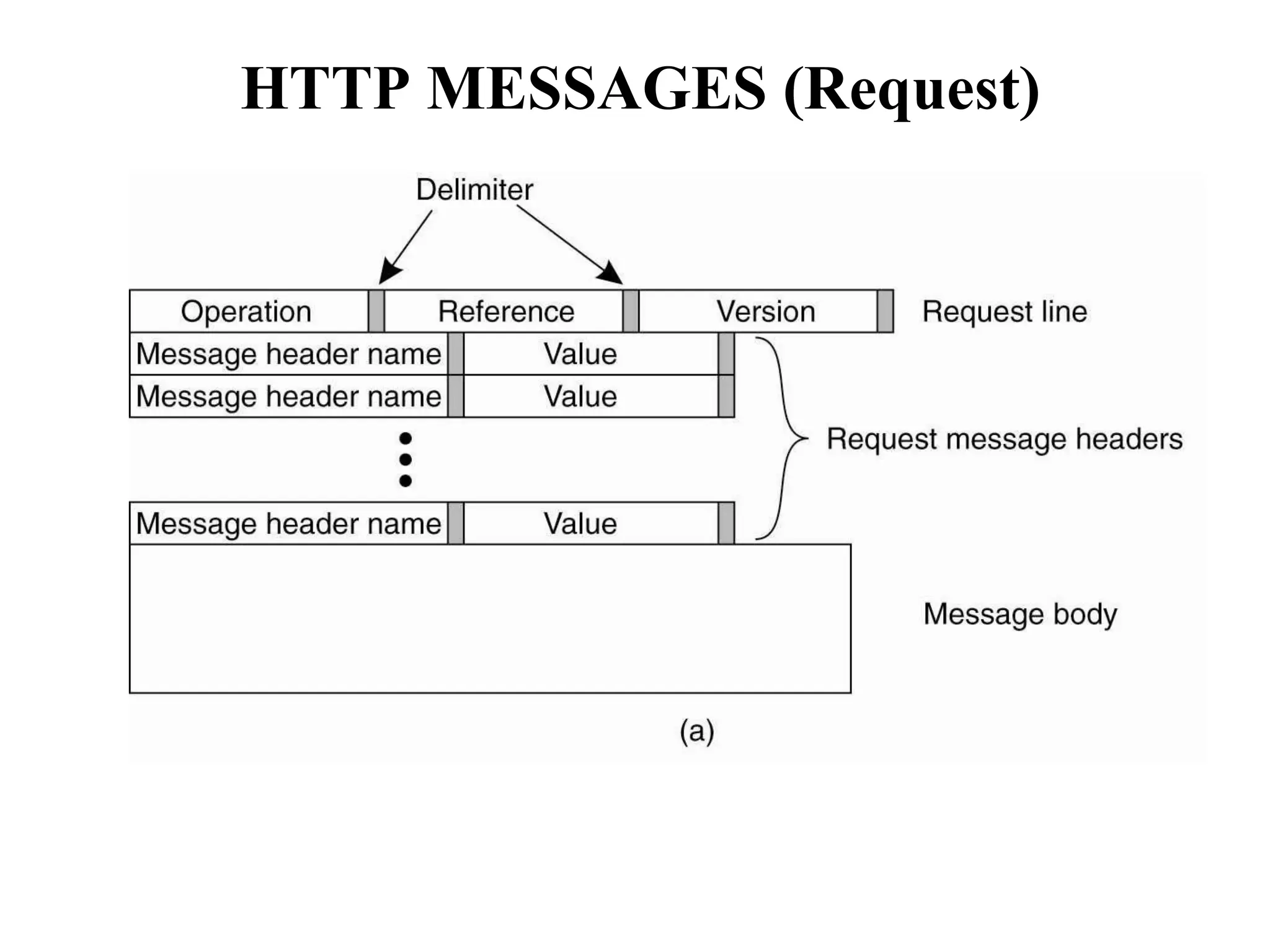
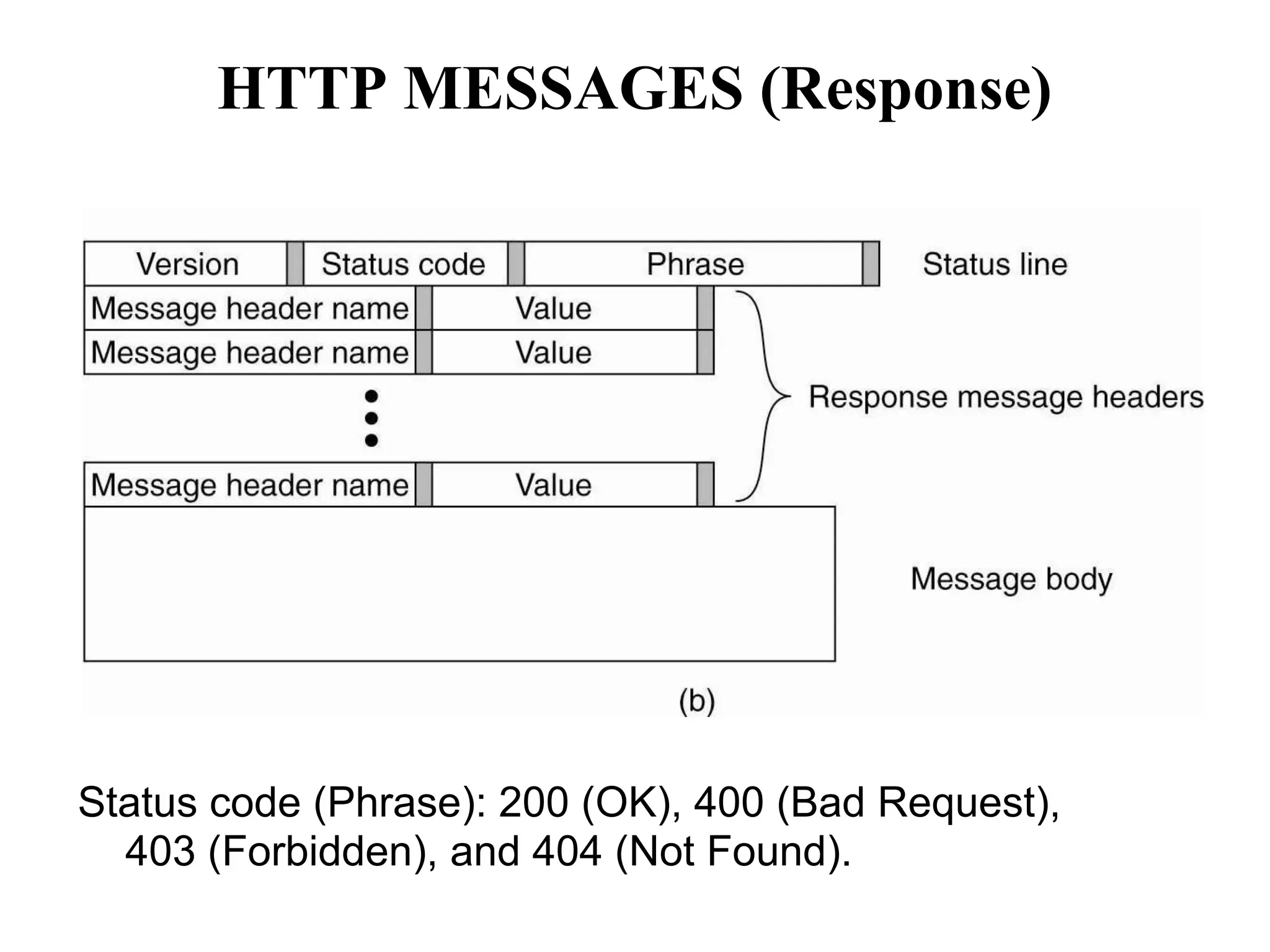
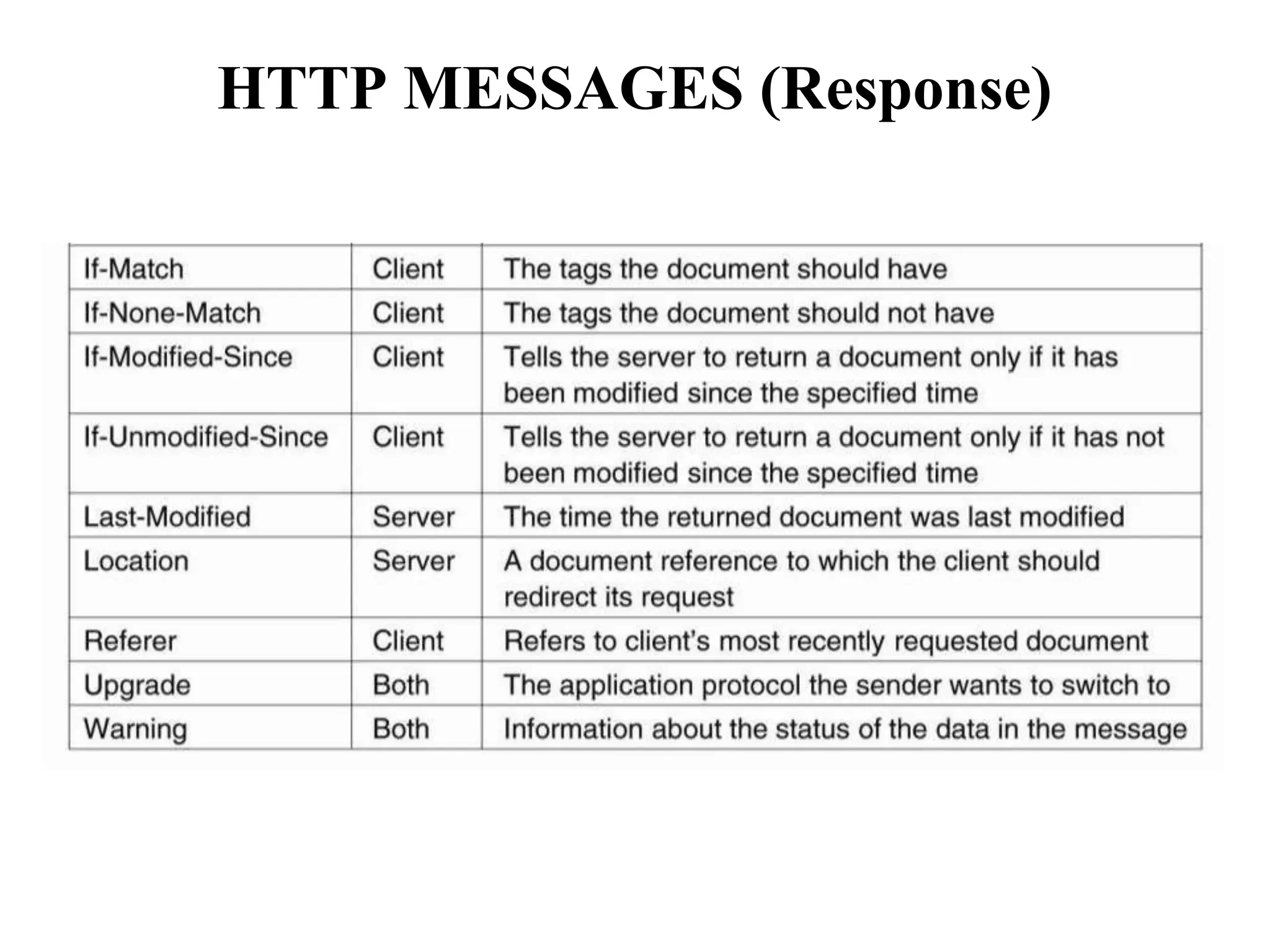
Communication by Hypertext Transfer Protocol, Synchronization,
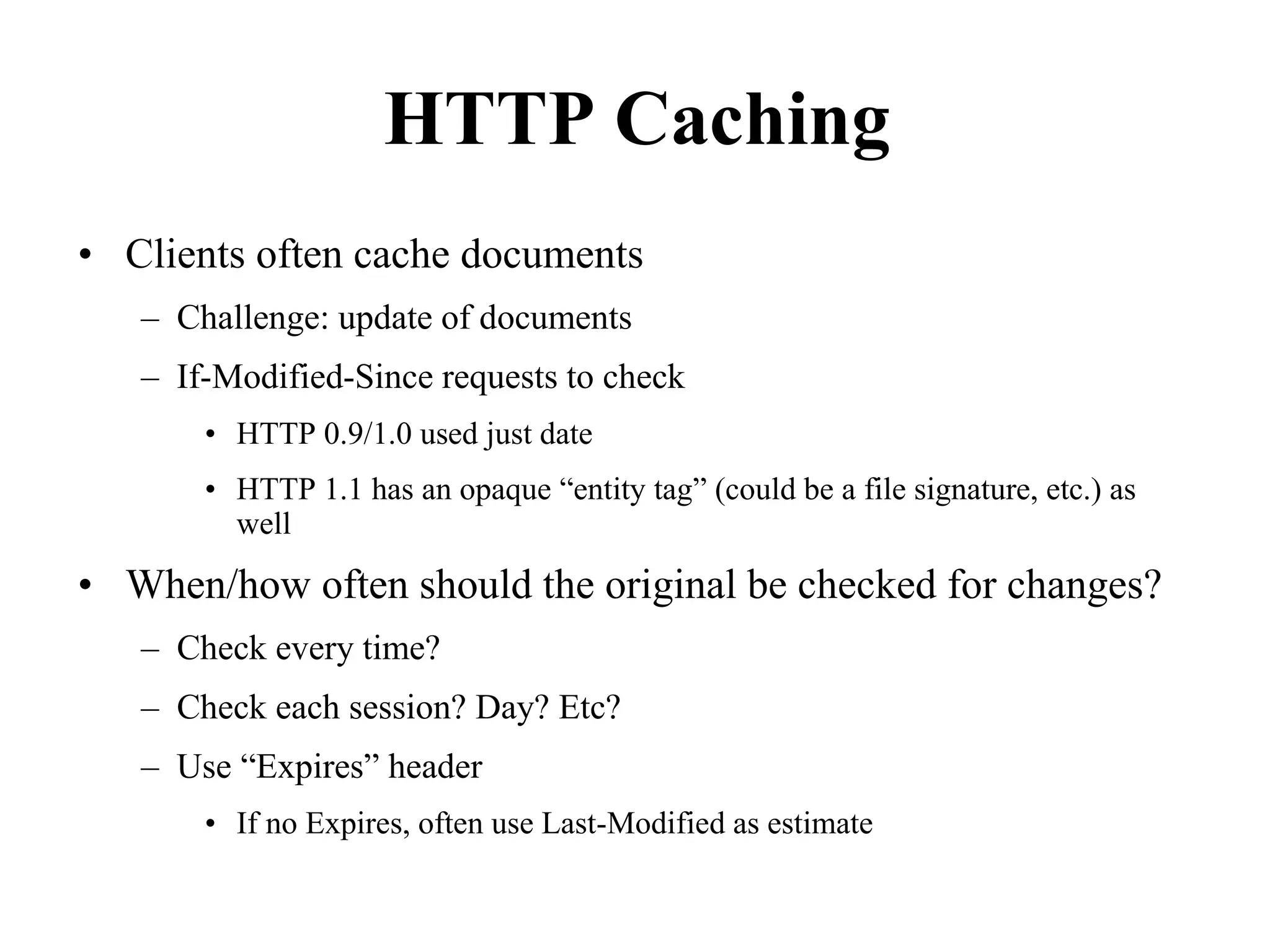
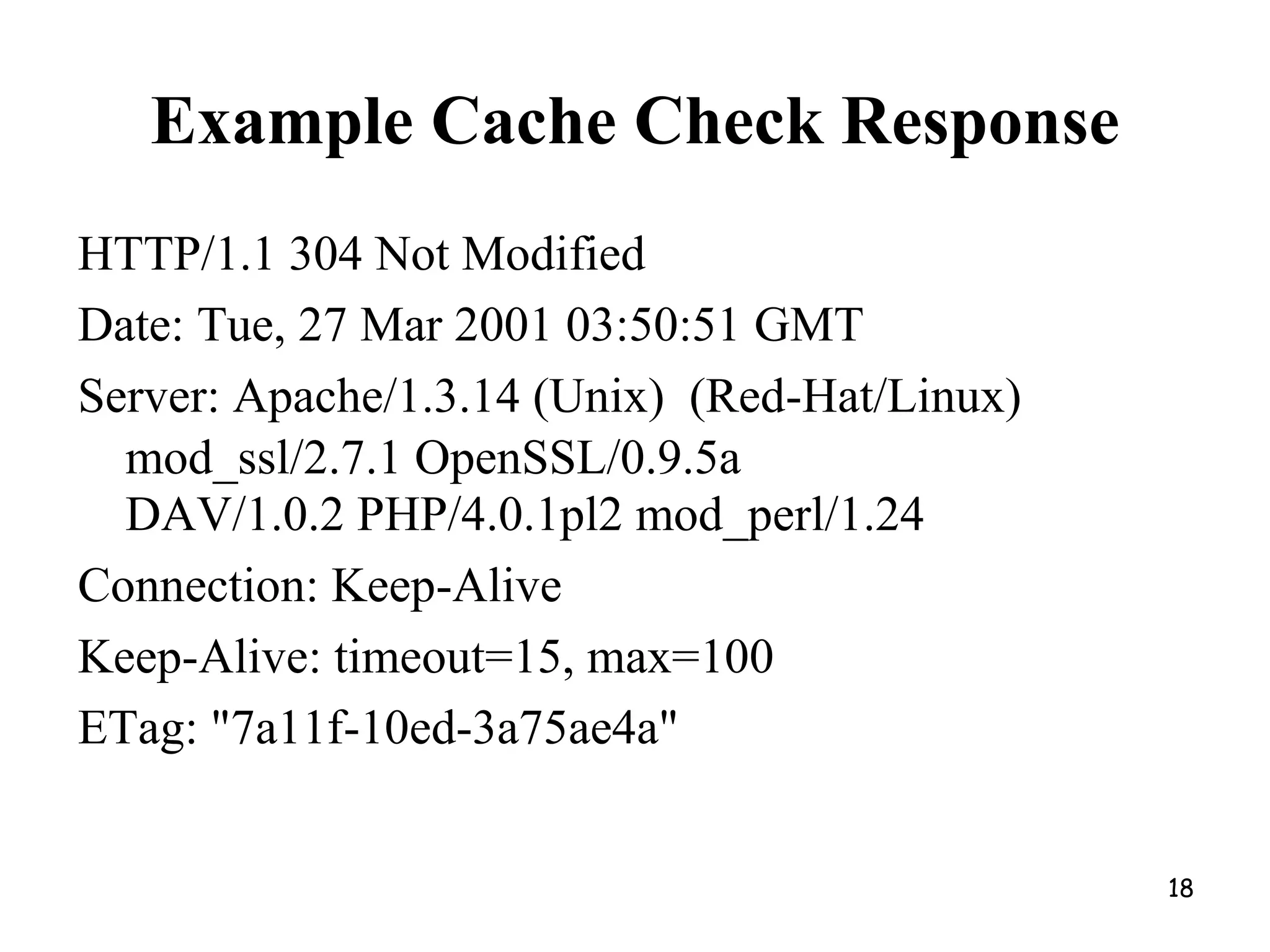
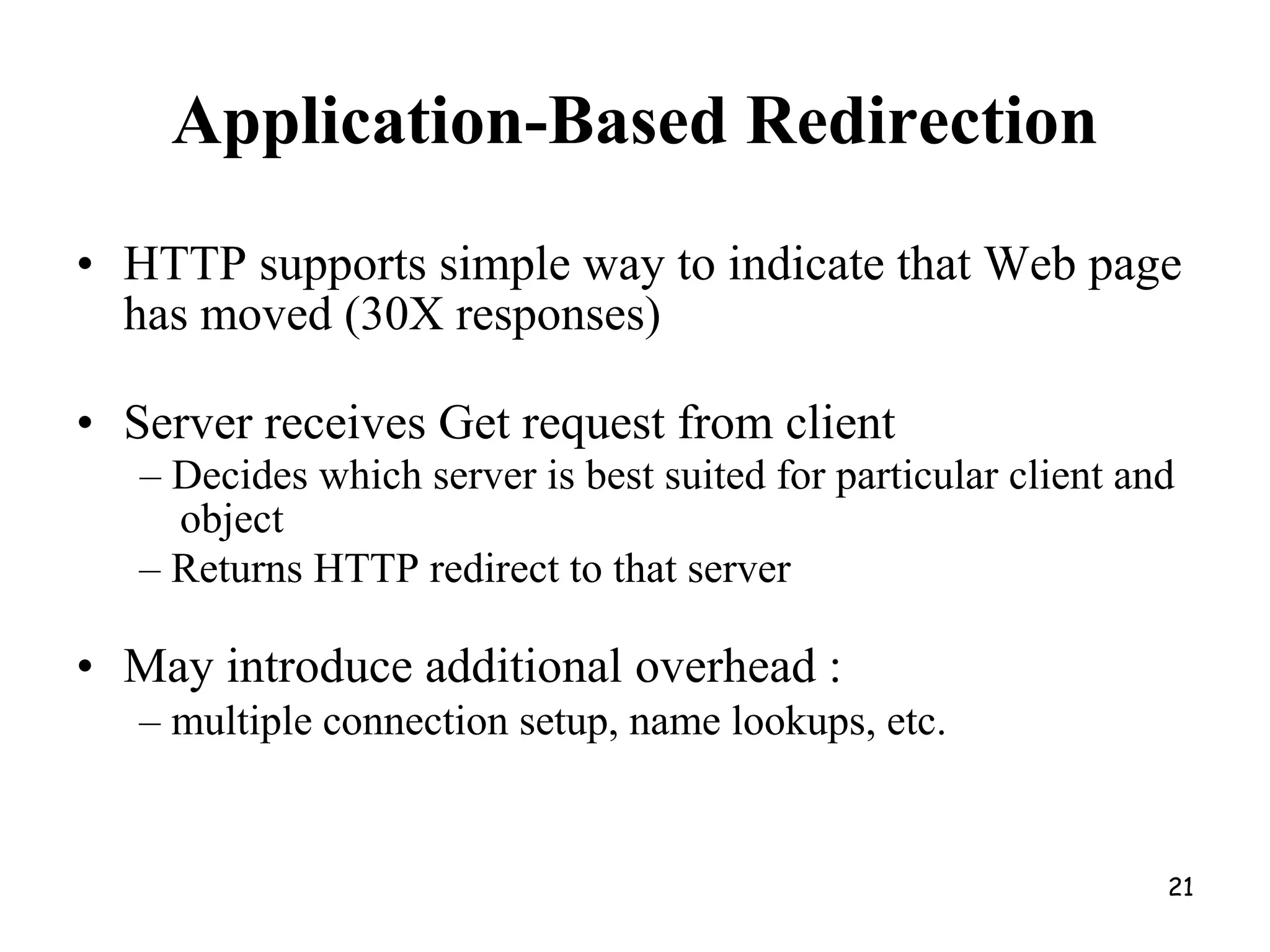
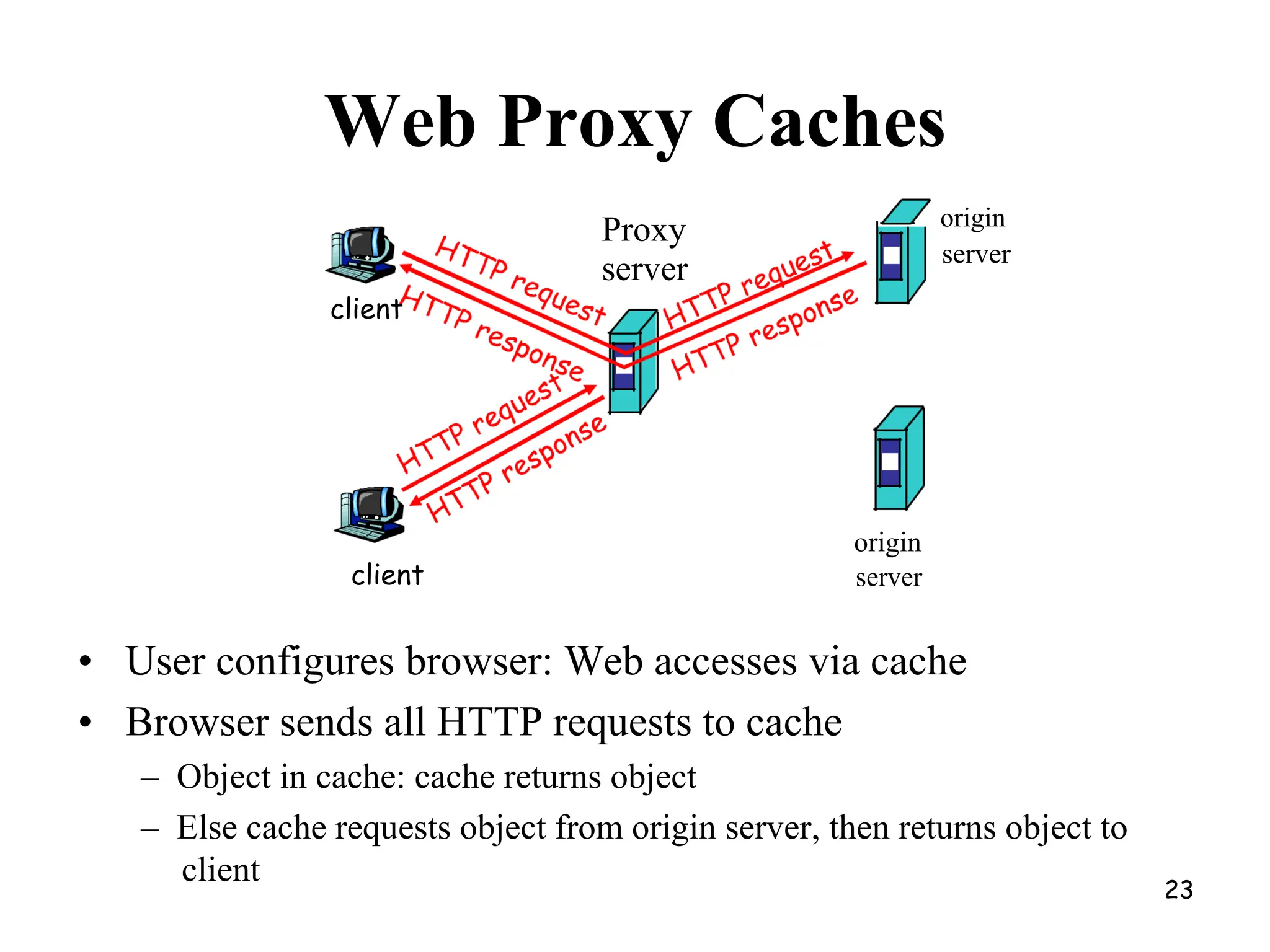
Web Proxy Caching.
Case Study: The Global Name Service, The X.500 Directory Service,
Bit Torrent.