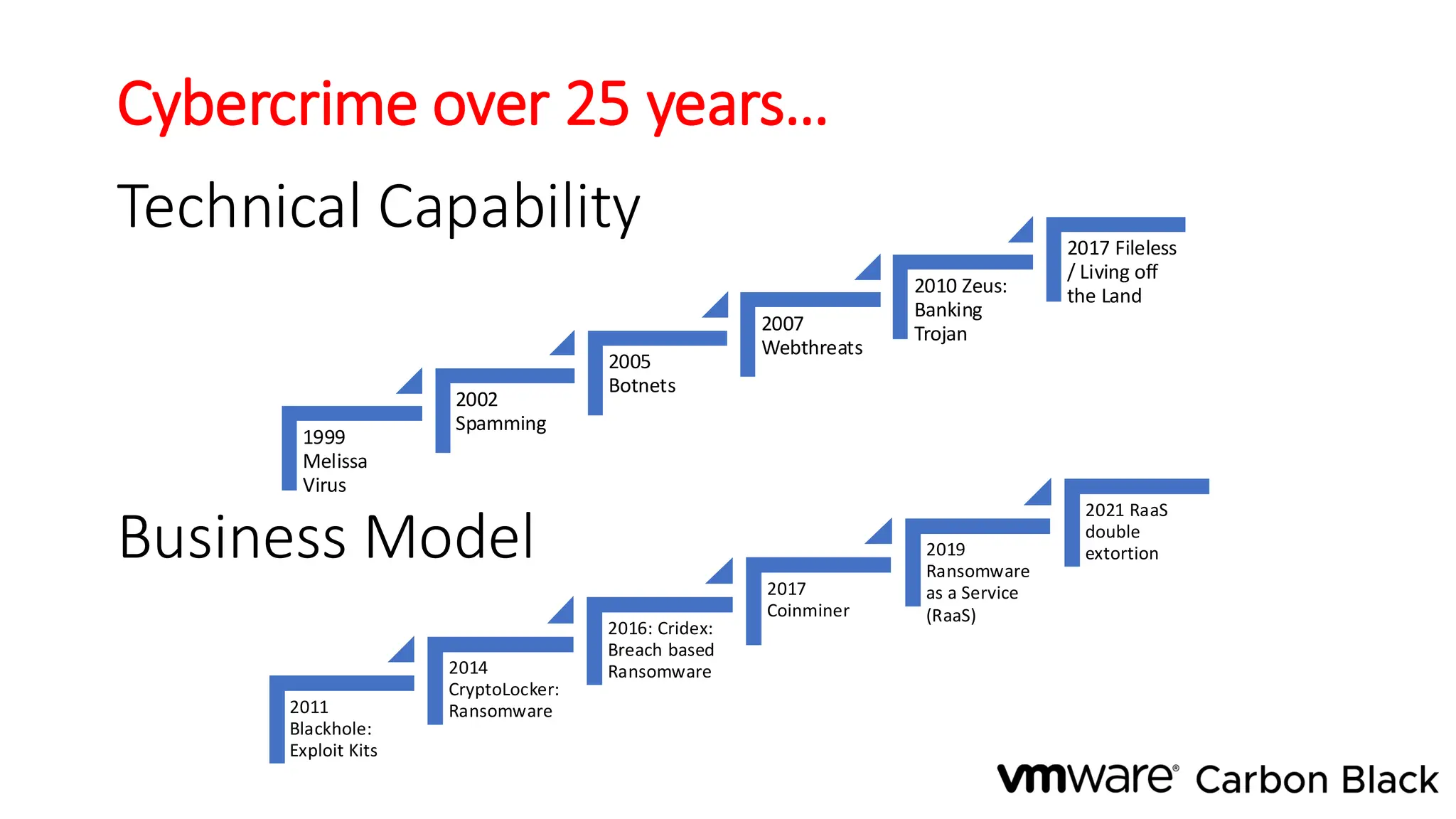
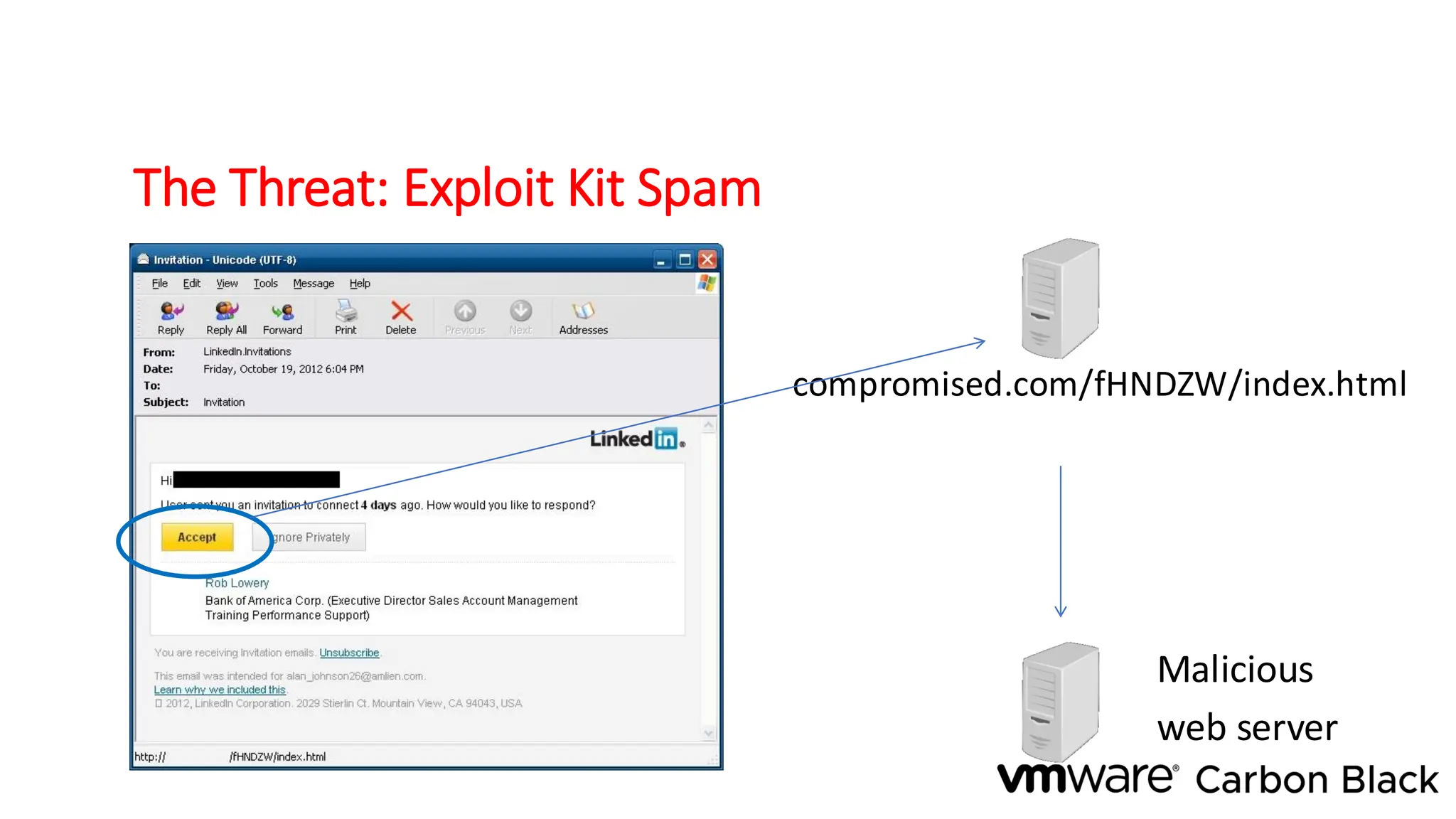
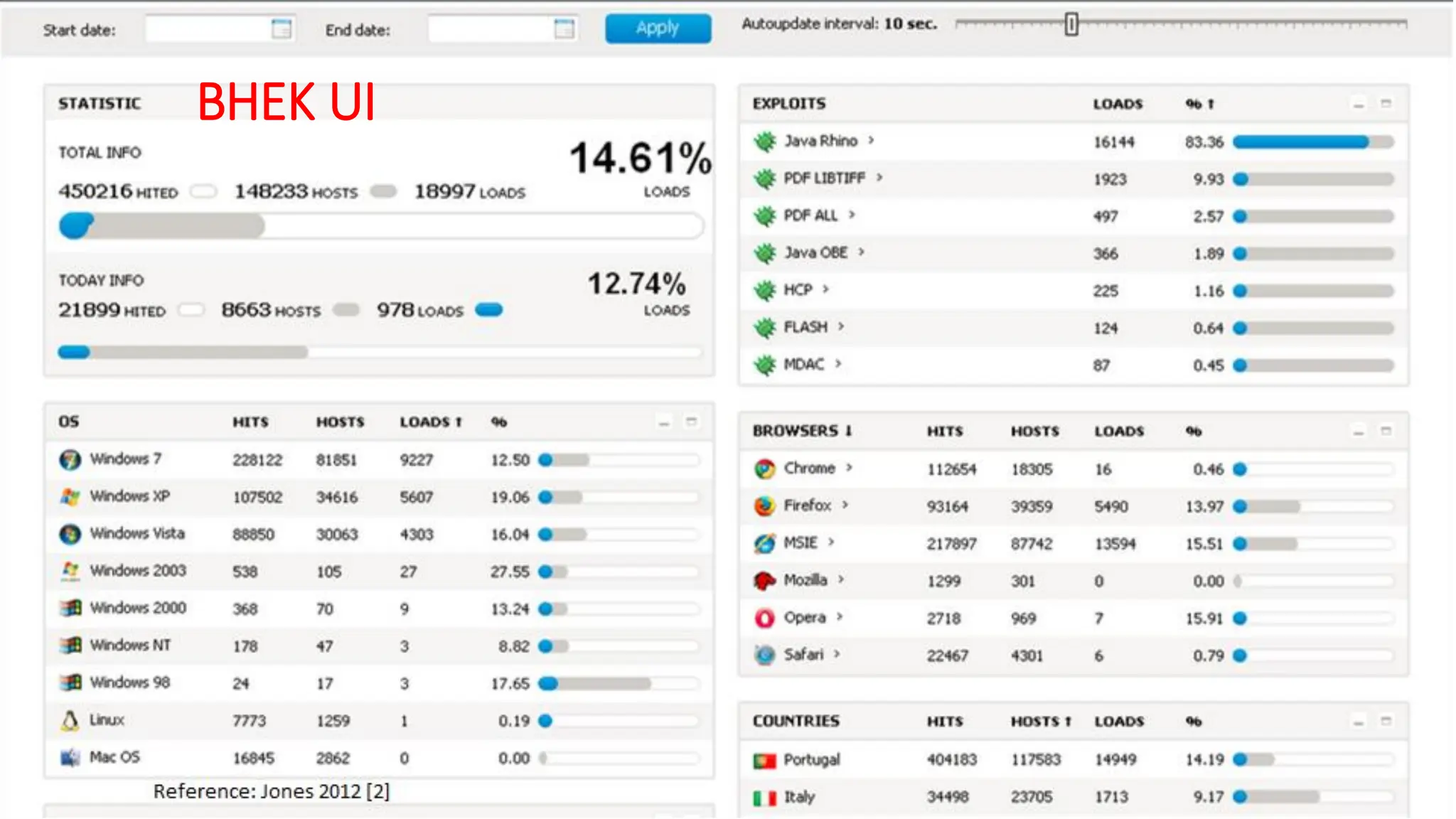
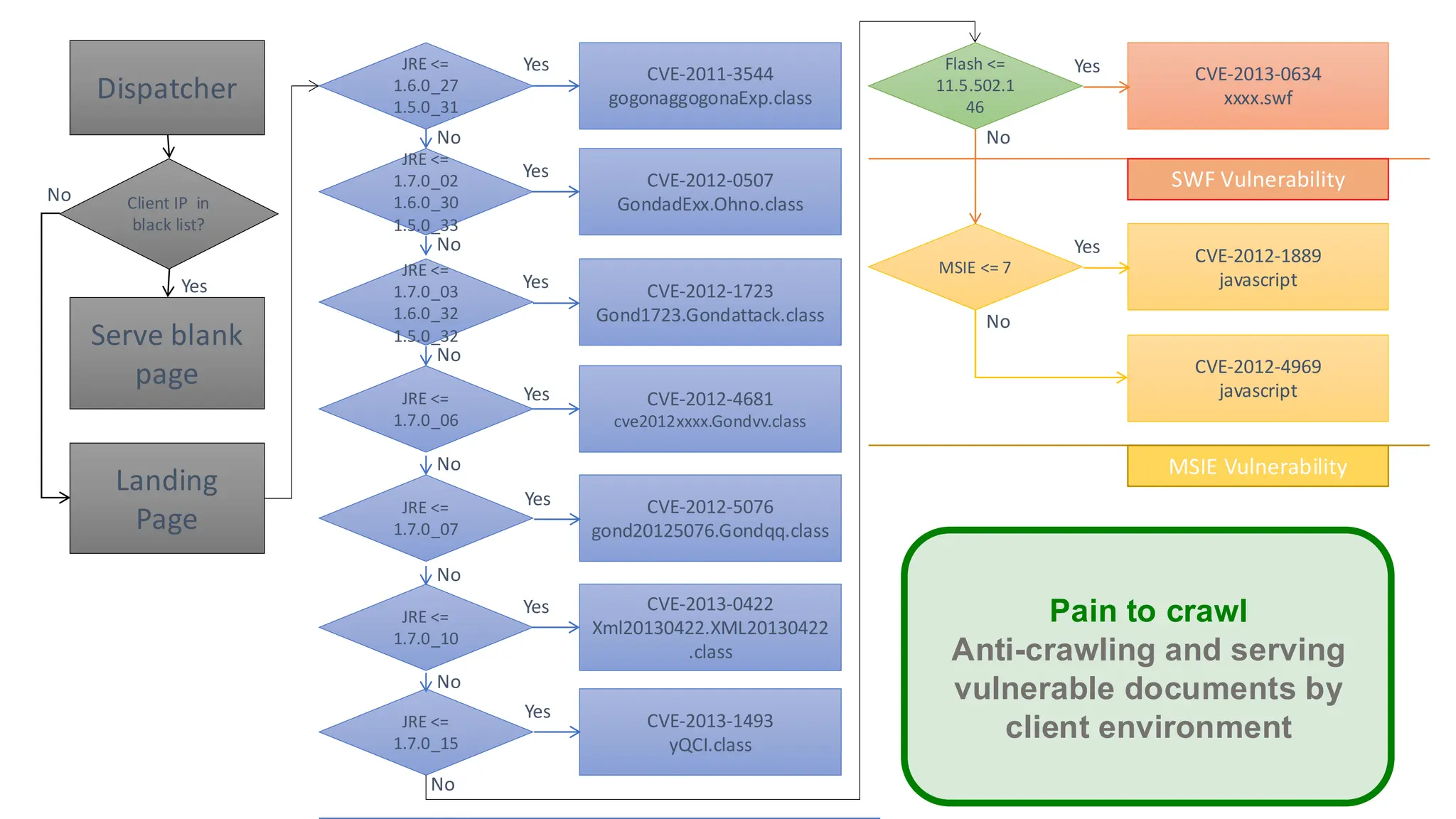
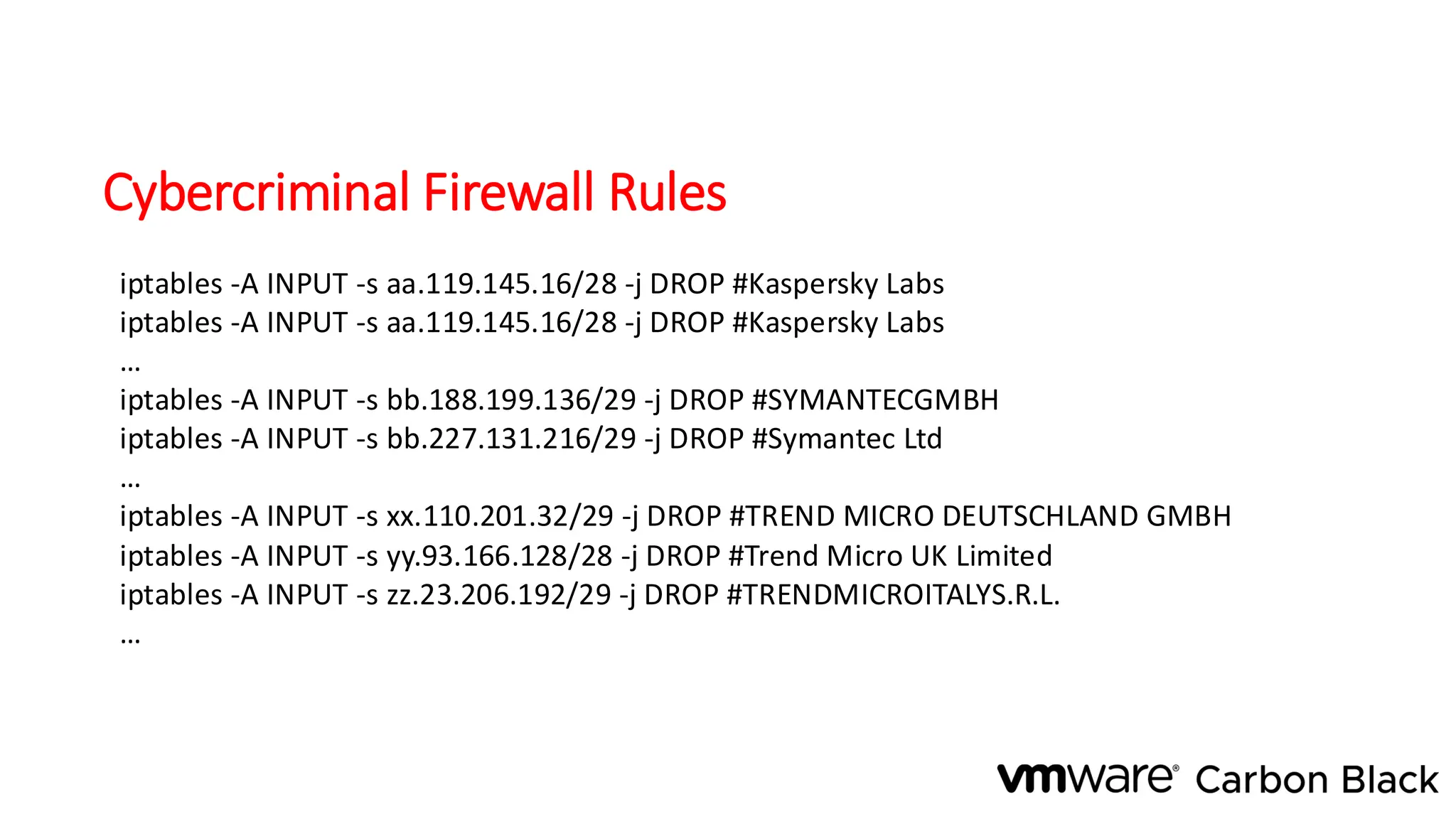
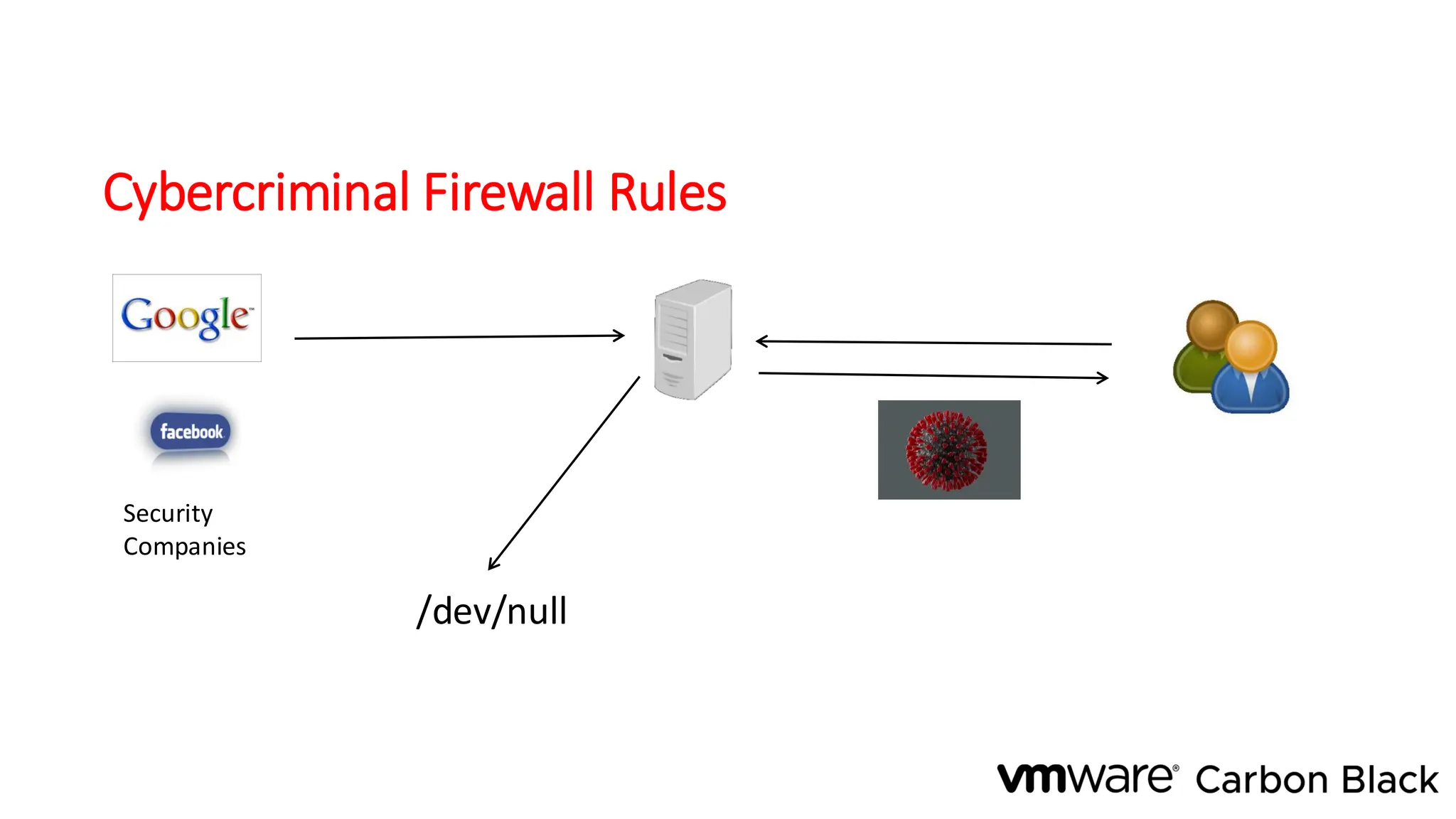
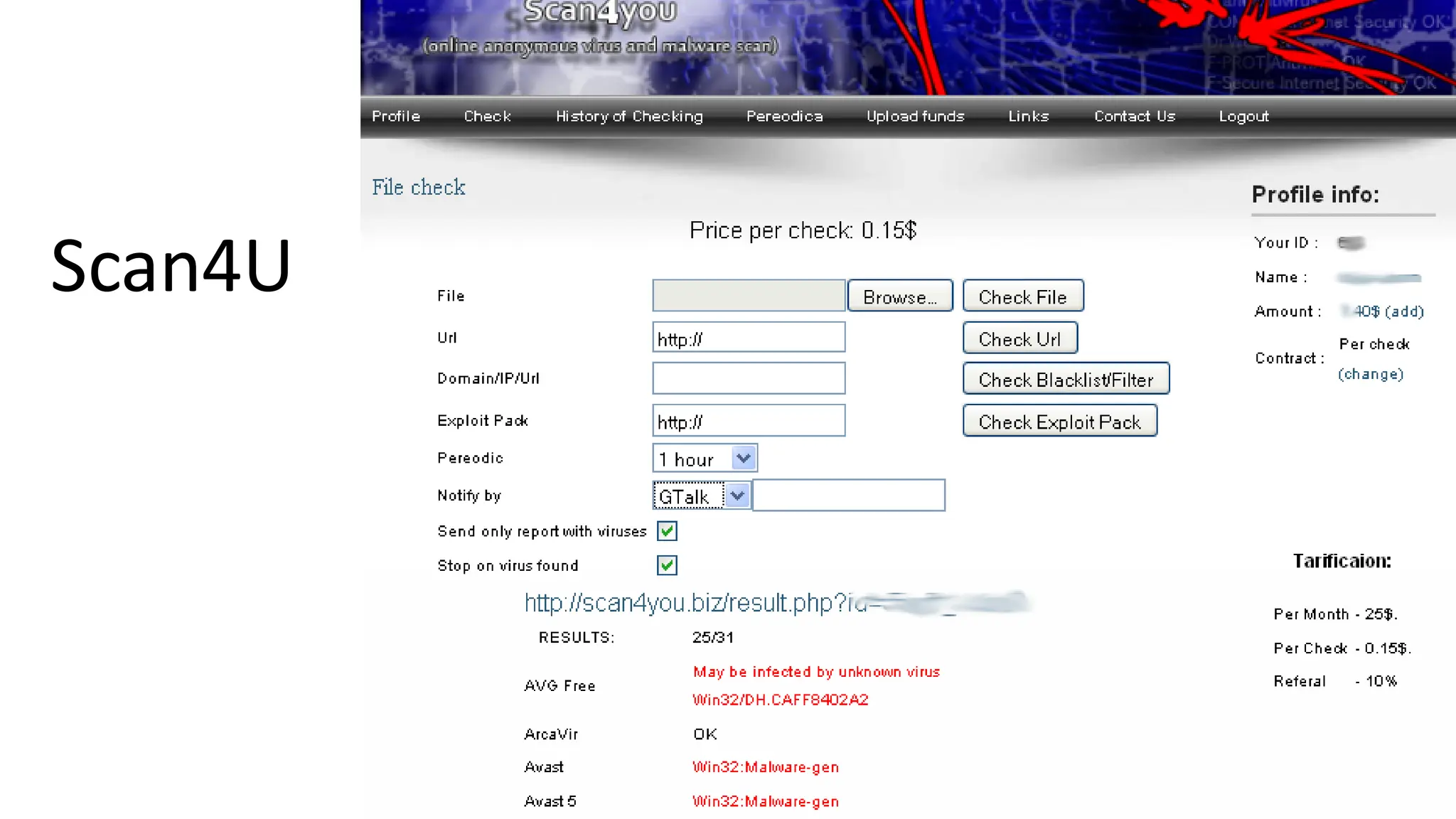
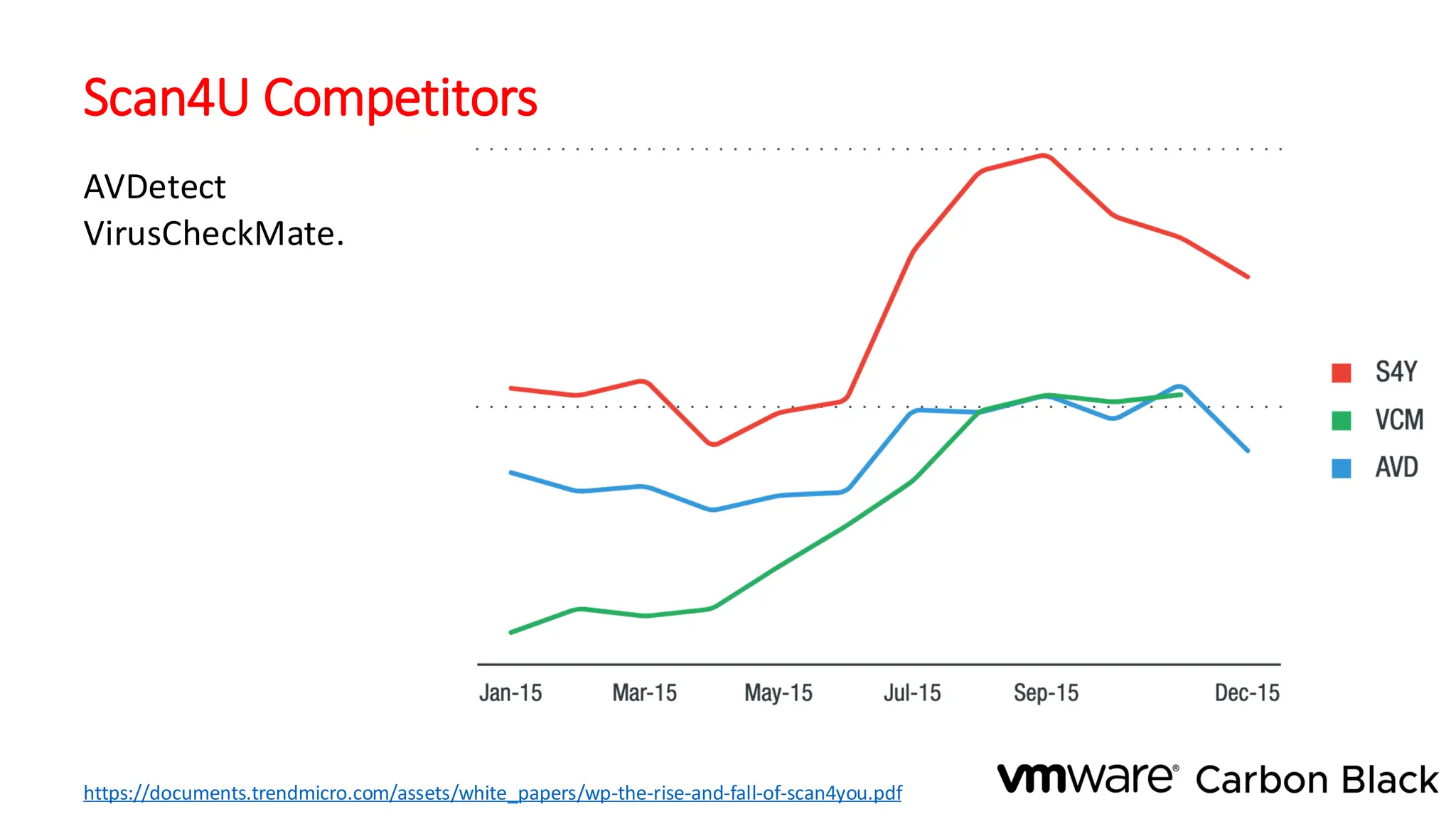
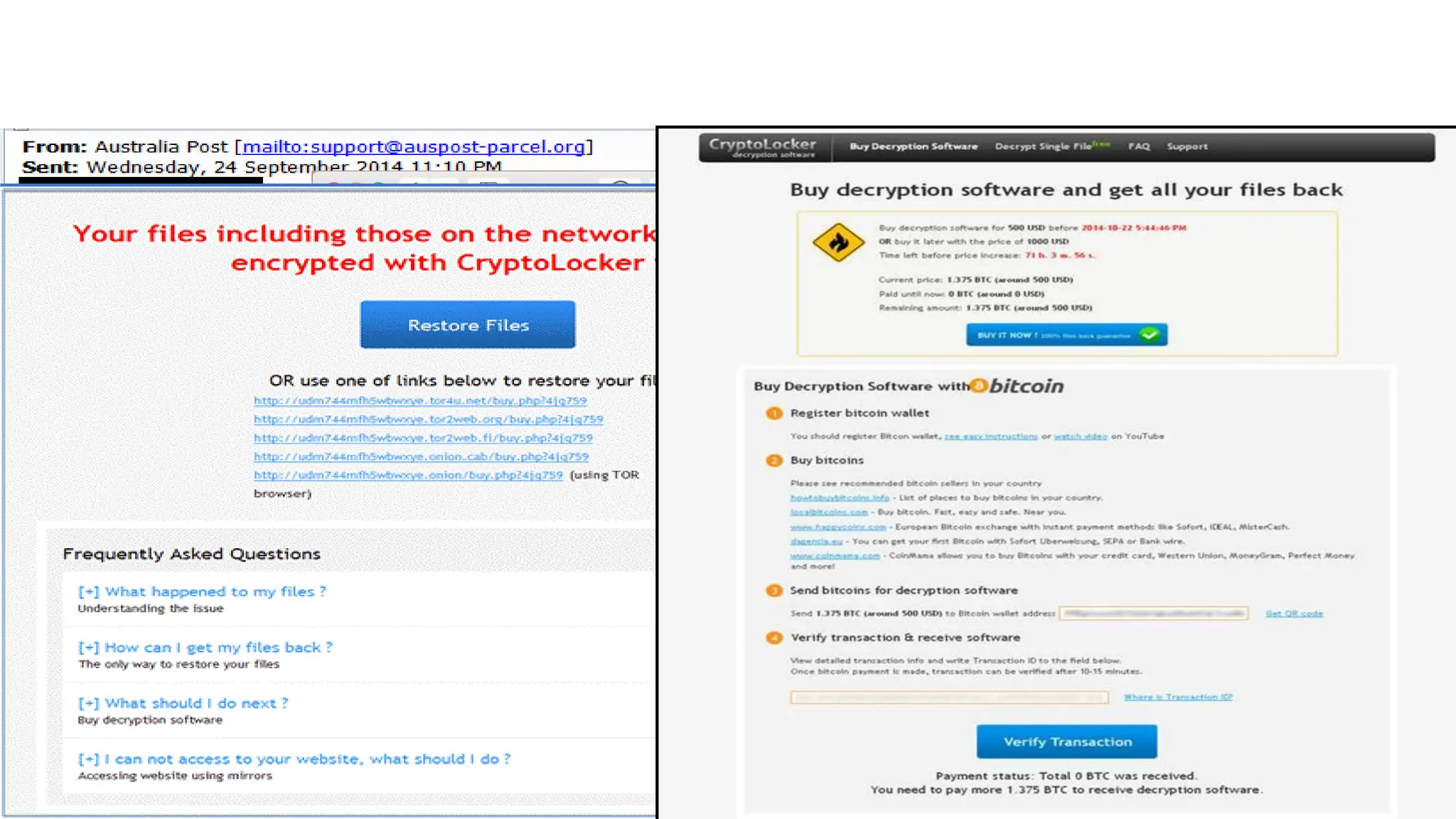
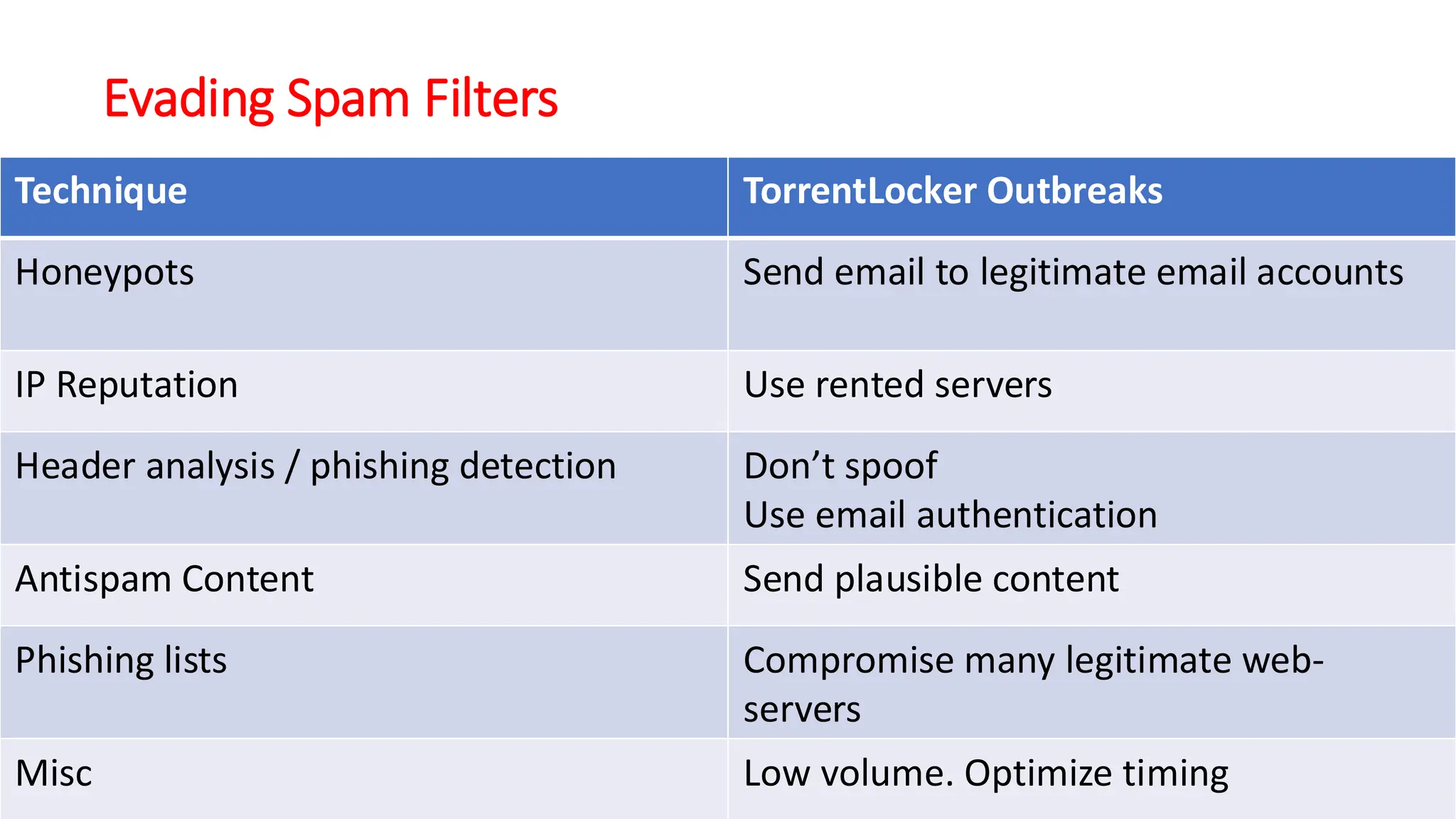
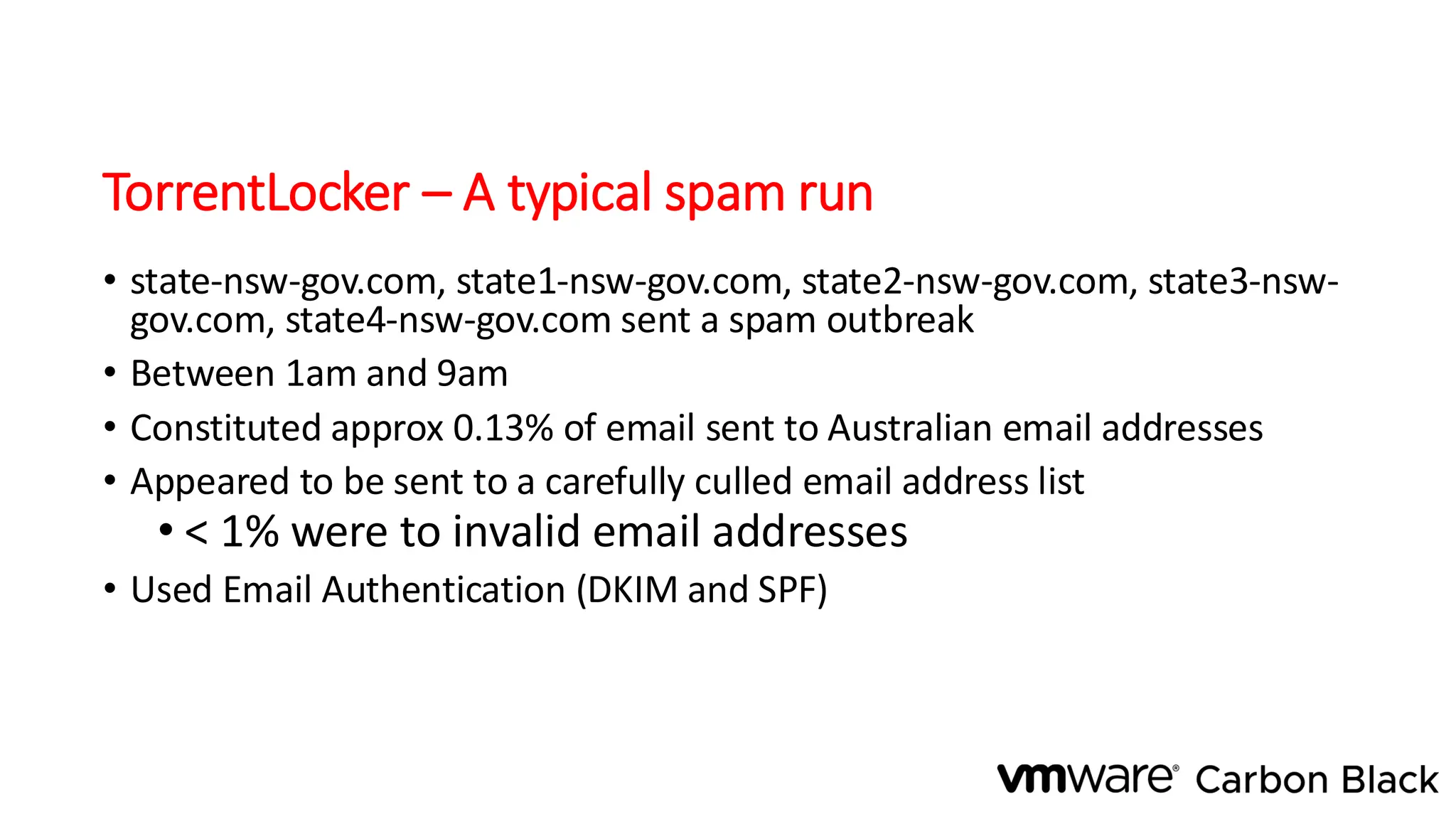
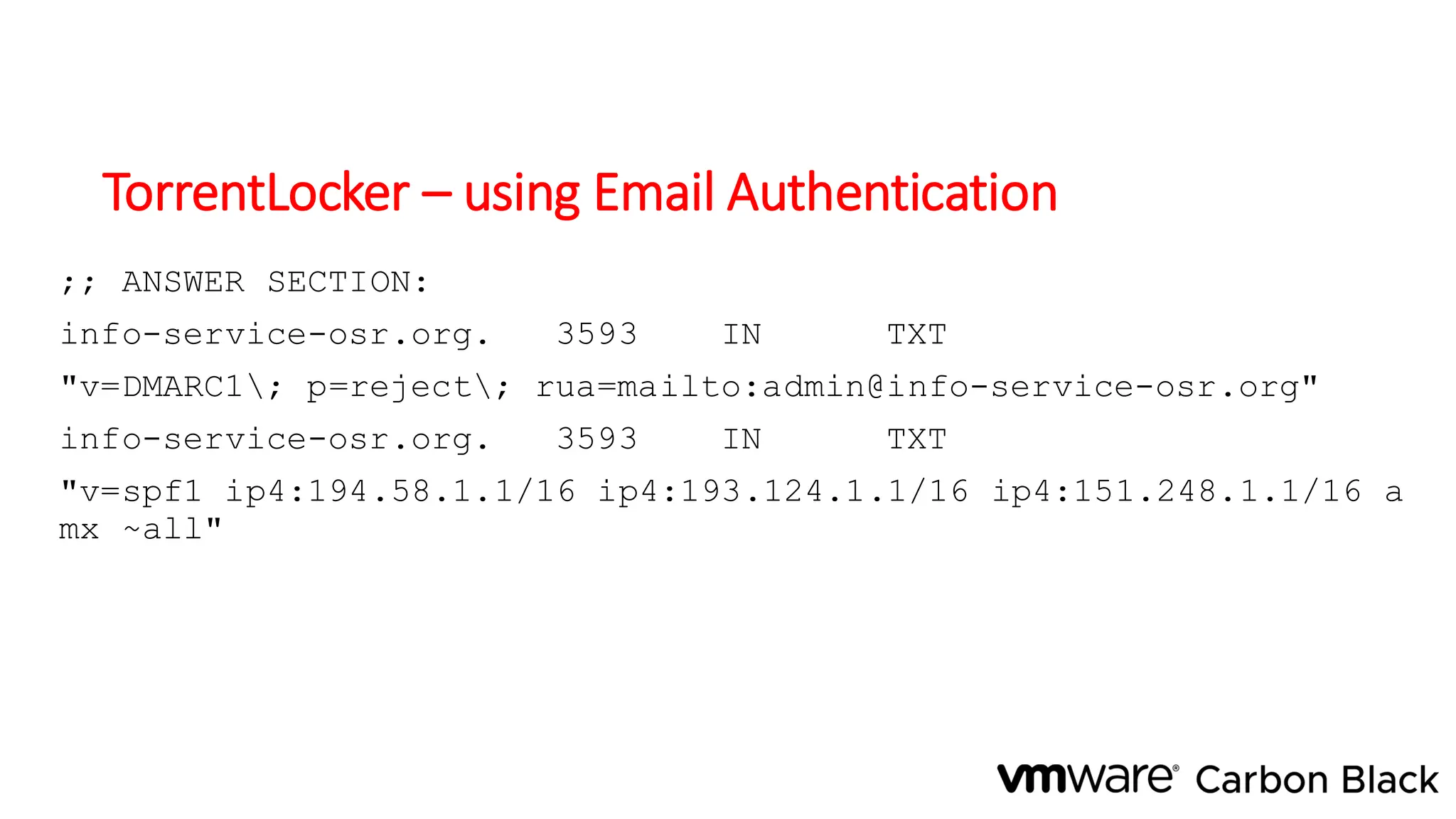
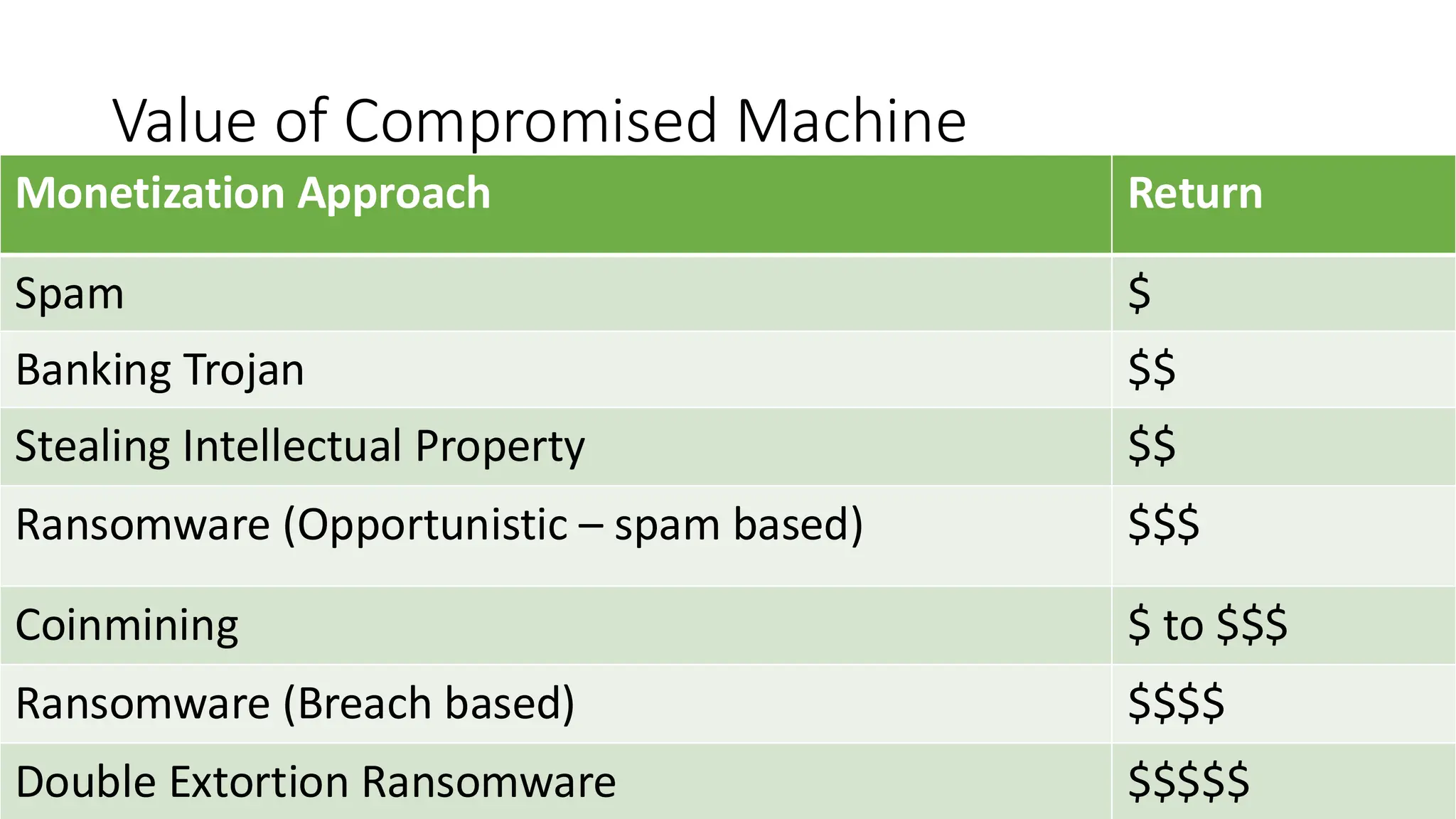
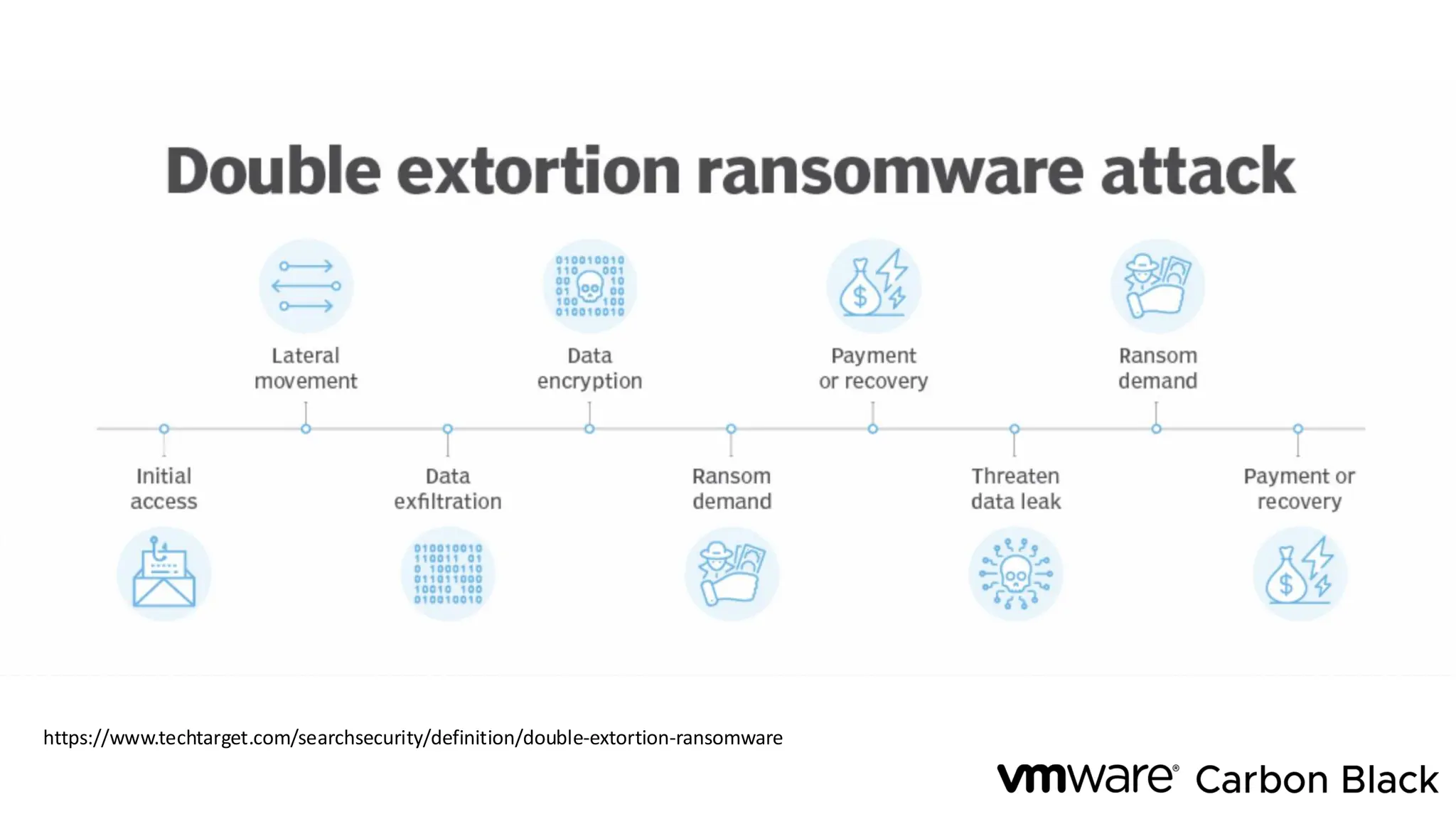
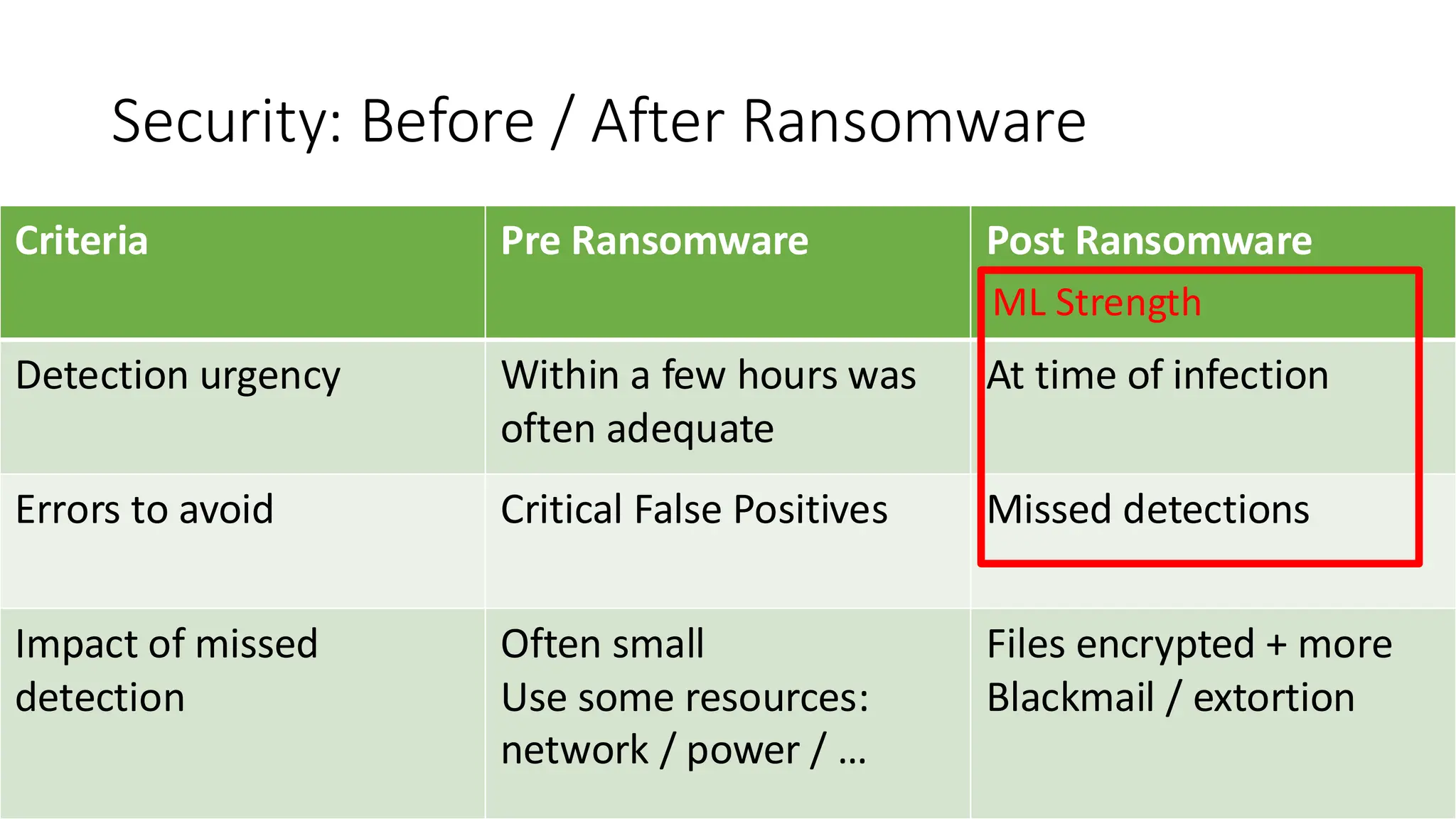
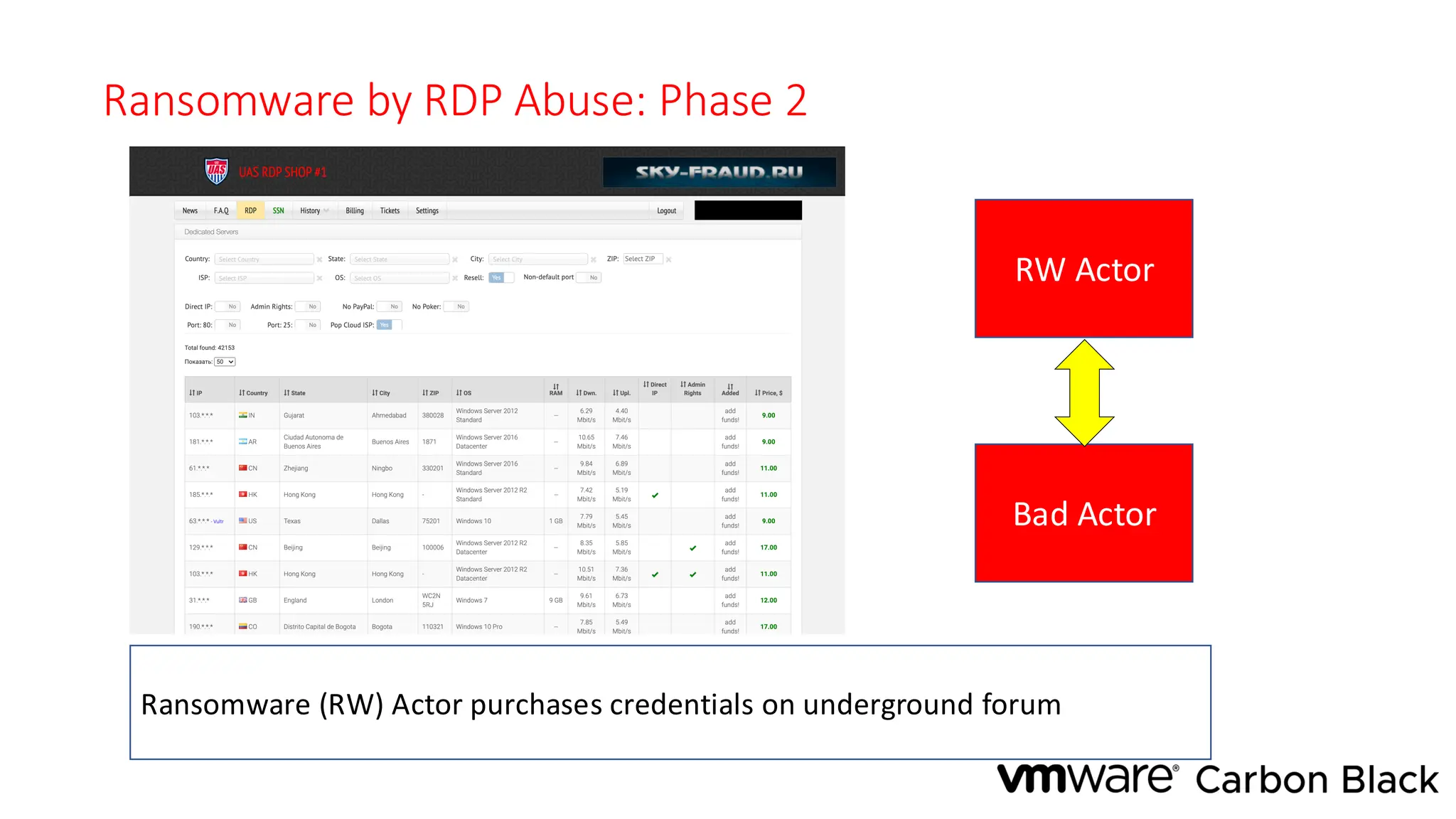
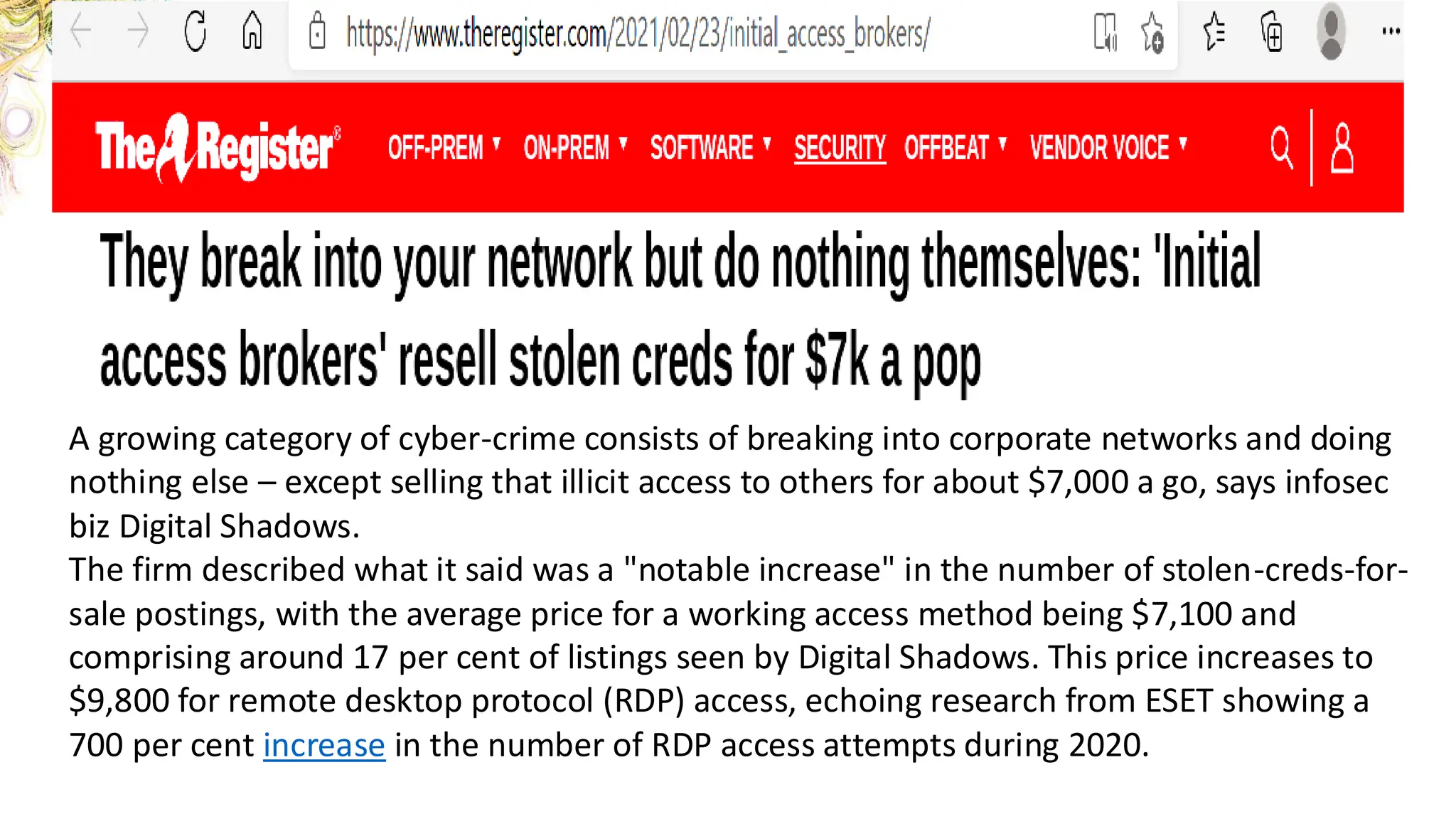
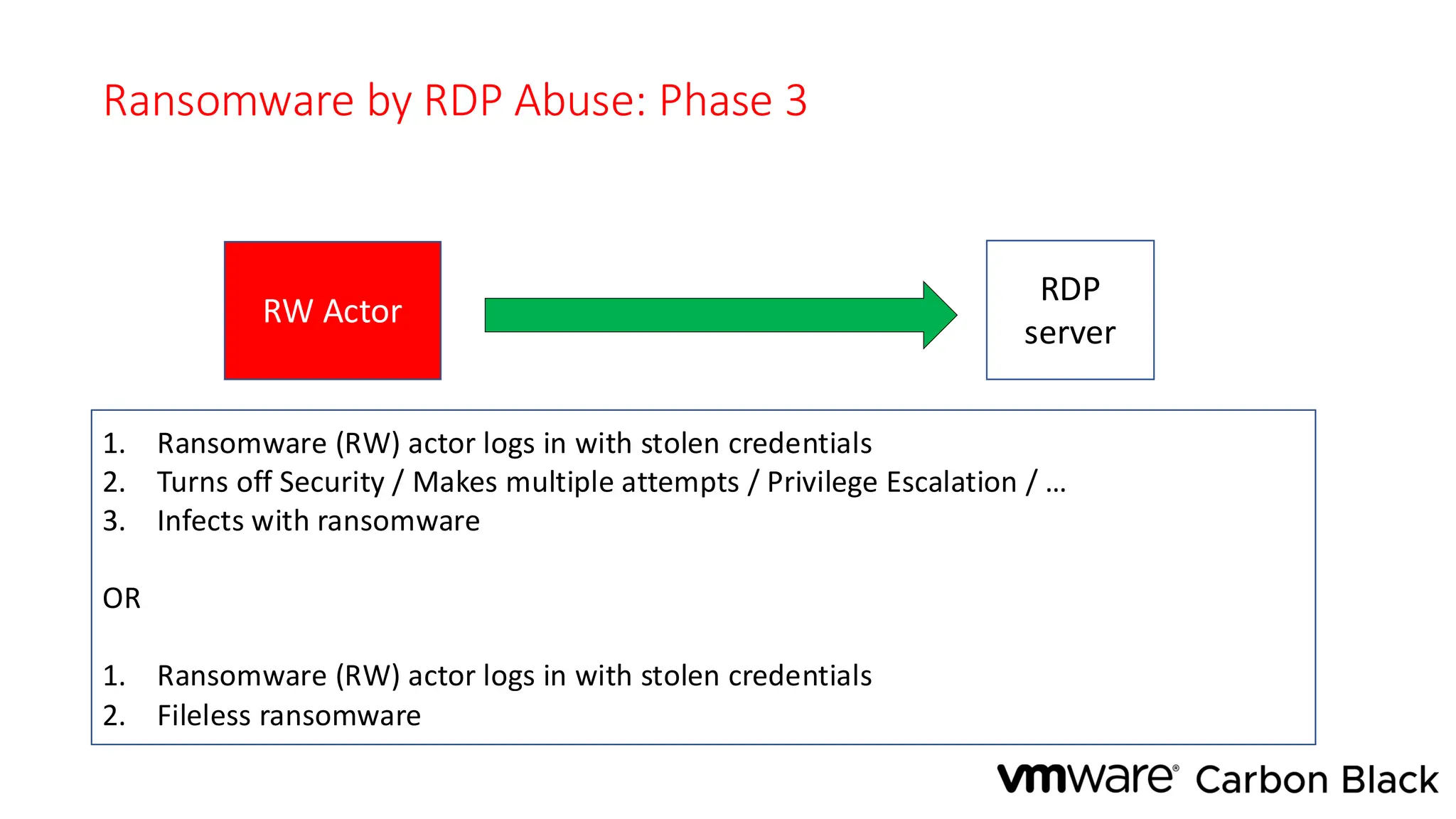
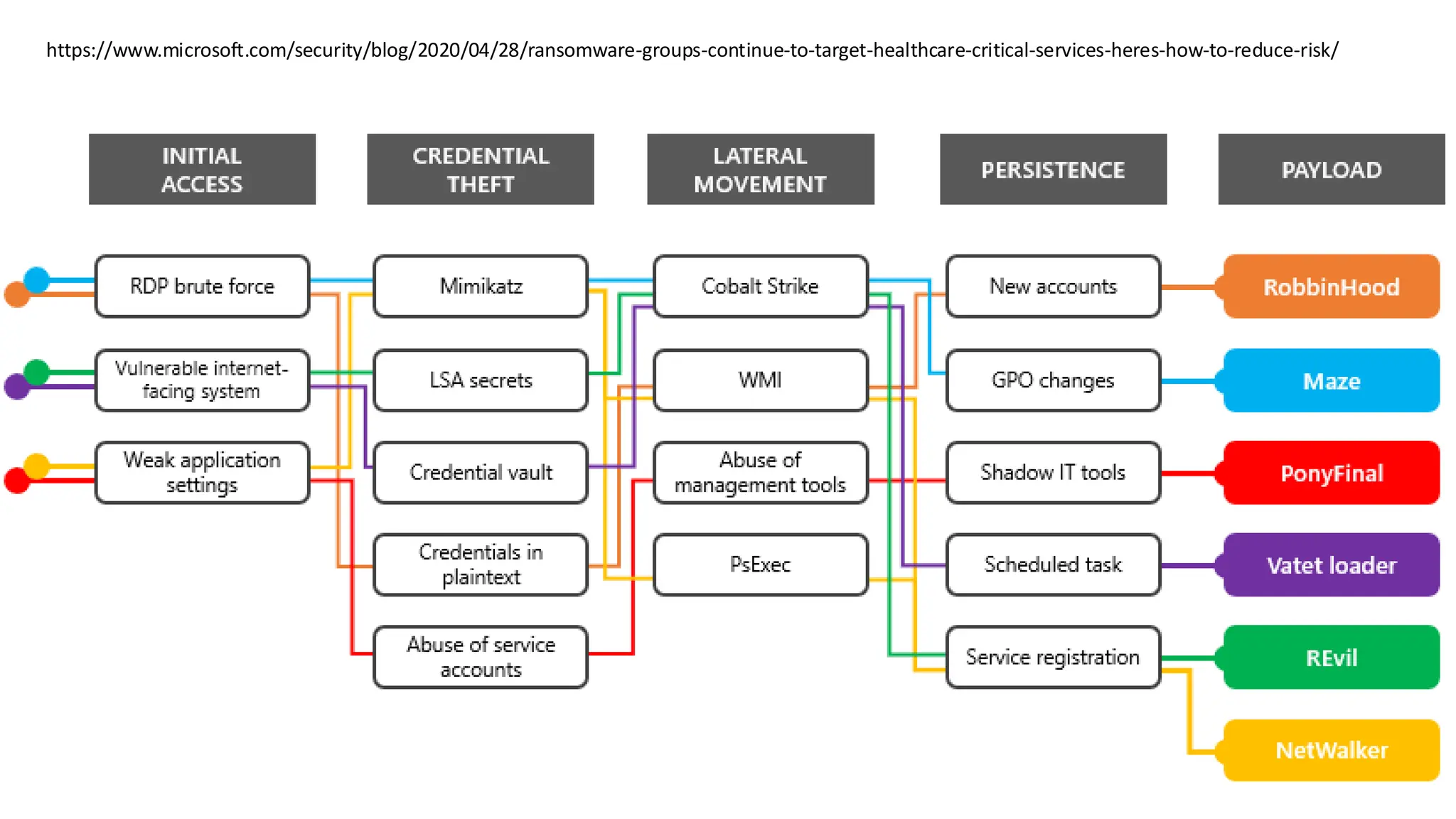
The document discusses the evolution and professionalism of cybercrime over the past 25 years, highlighting various malicious techniques and attack vectors used by cybercriminals. It emphasizes the strategic aspects of cyberattacks, such as optimizing processes and utilizing business models for better execution. Additionally, it covers the challenges faced in detecting and responding to ransomware, particularly in light of advancements in machine learning technologies.