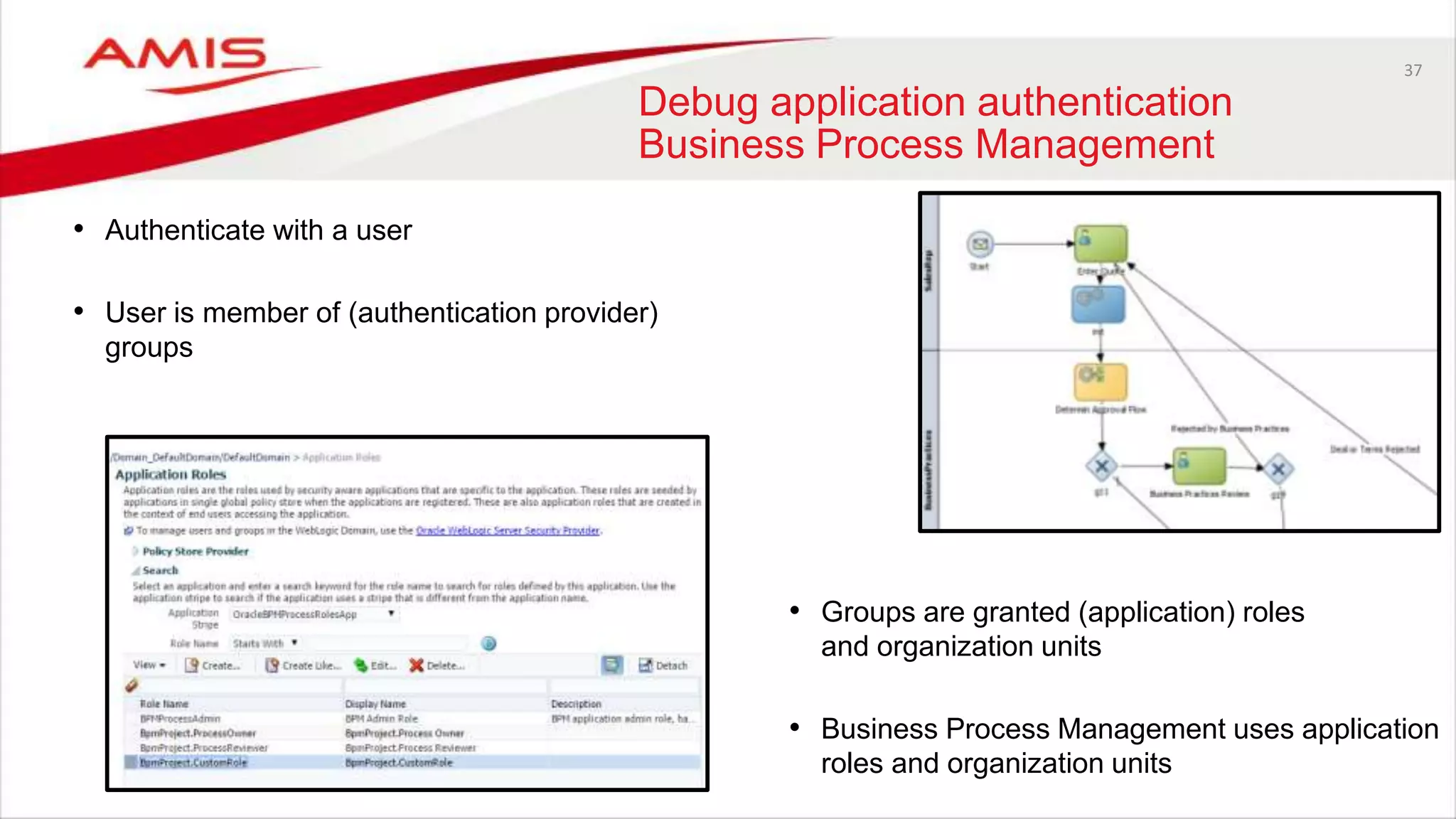
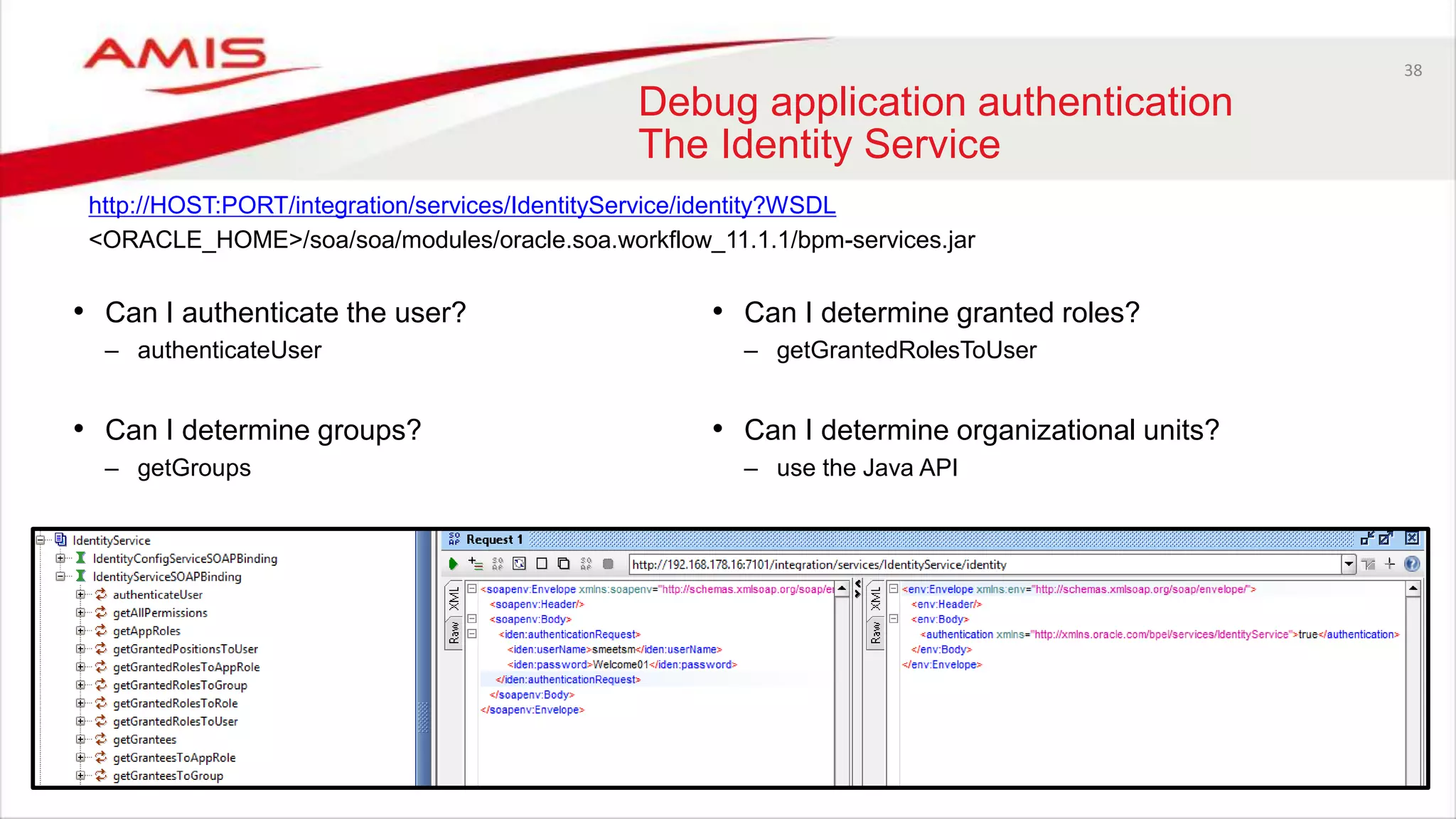
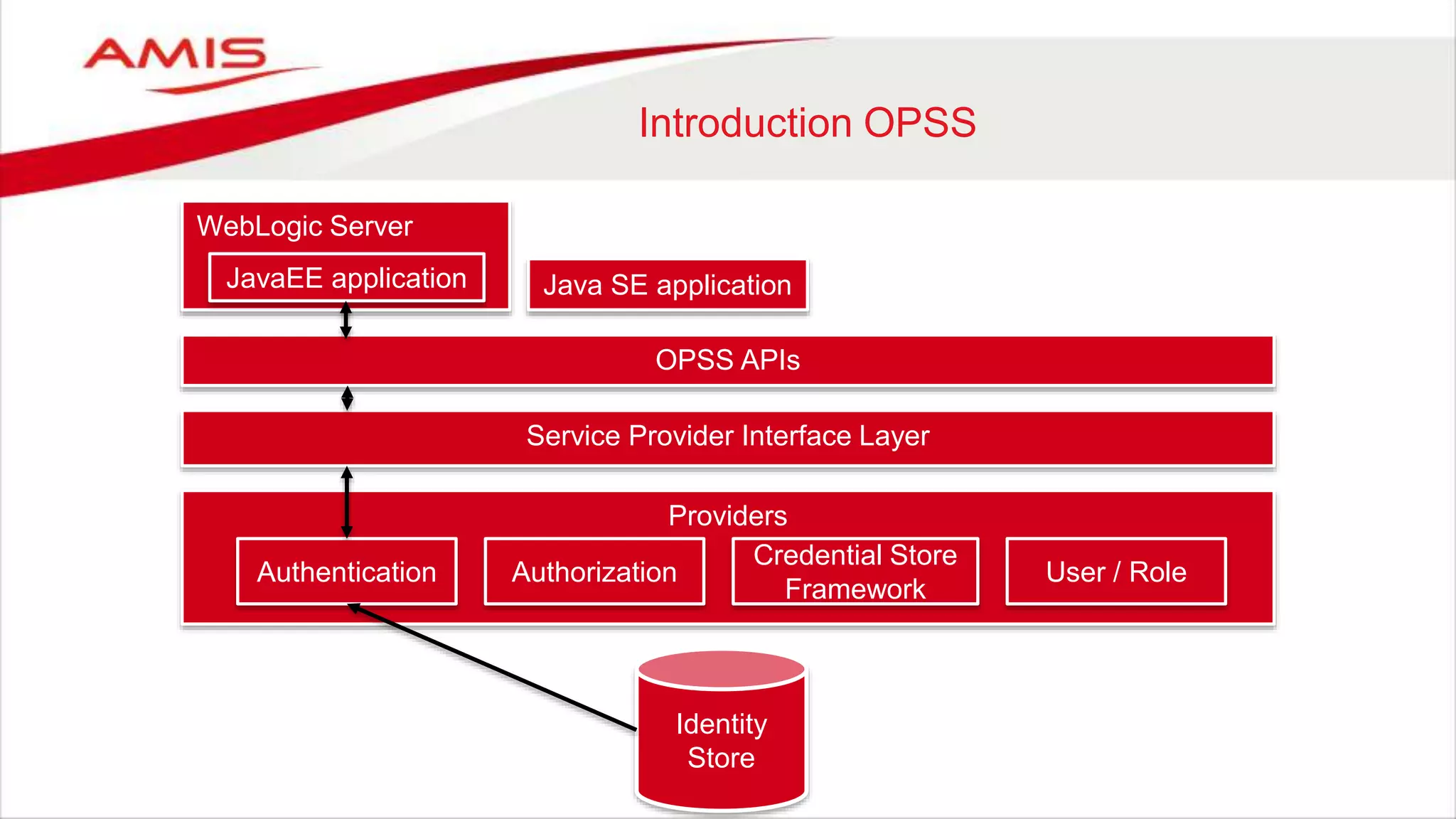
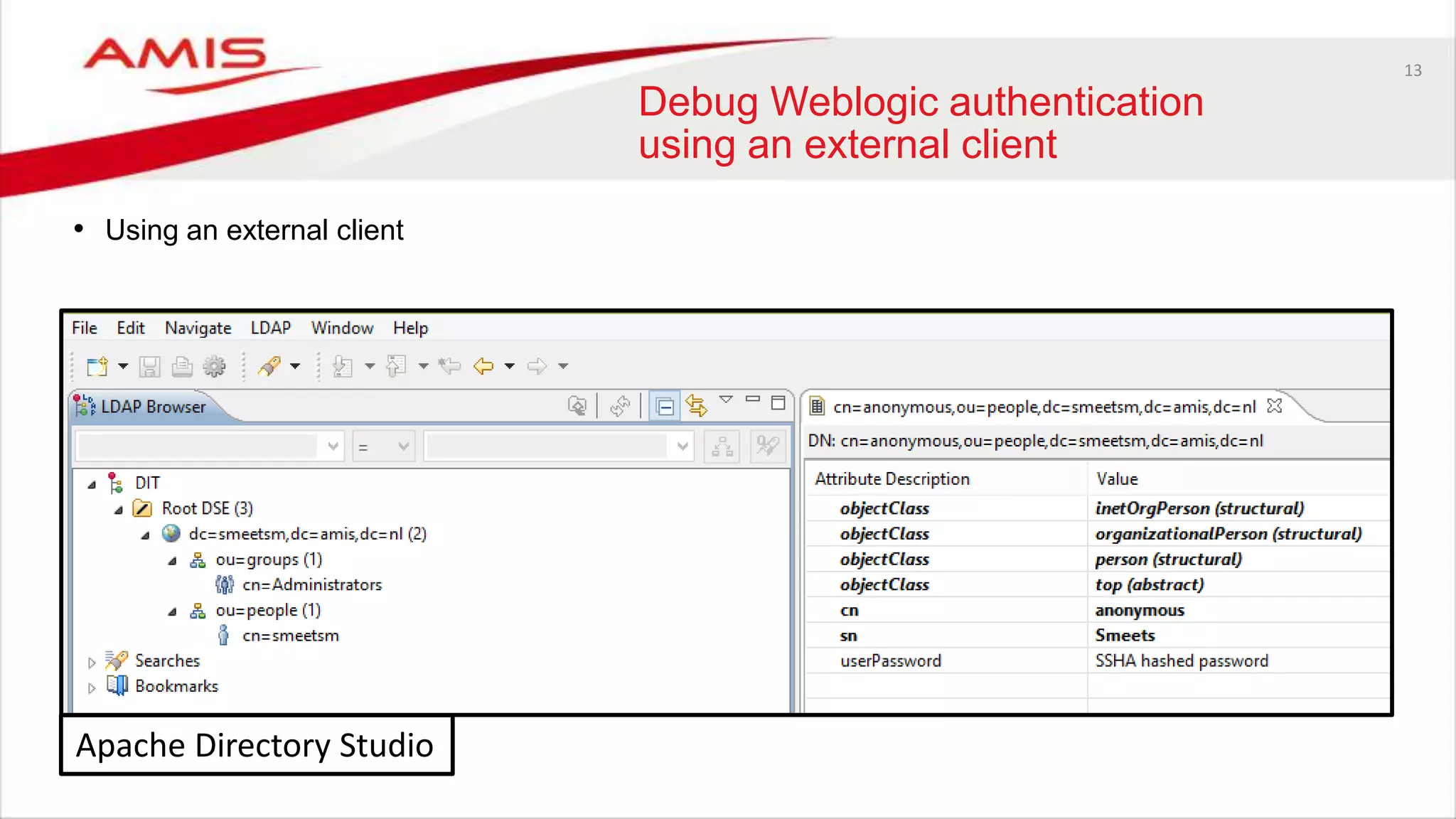
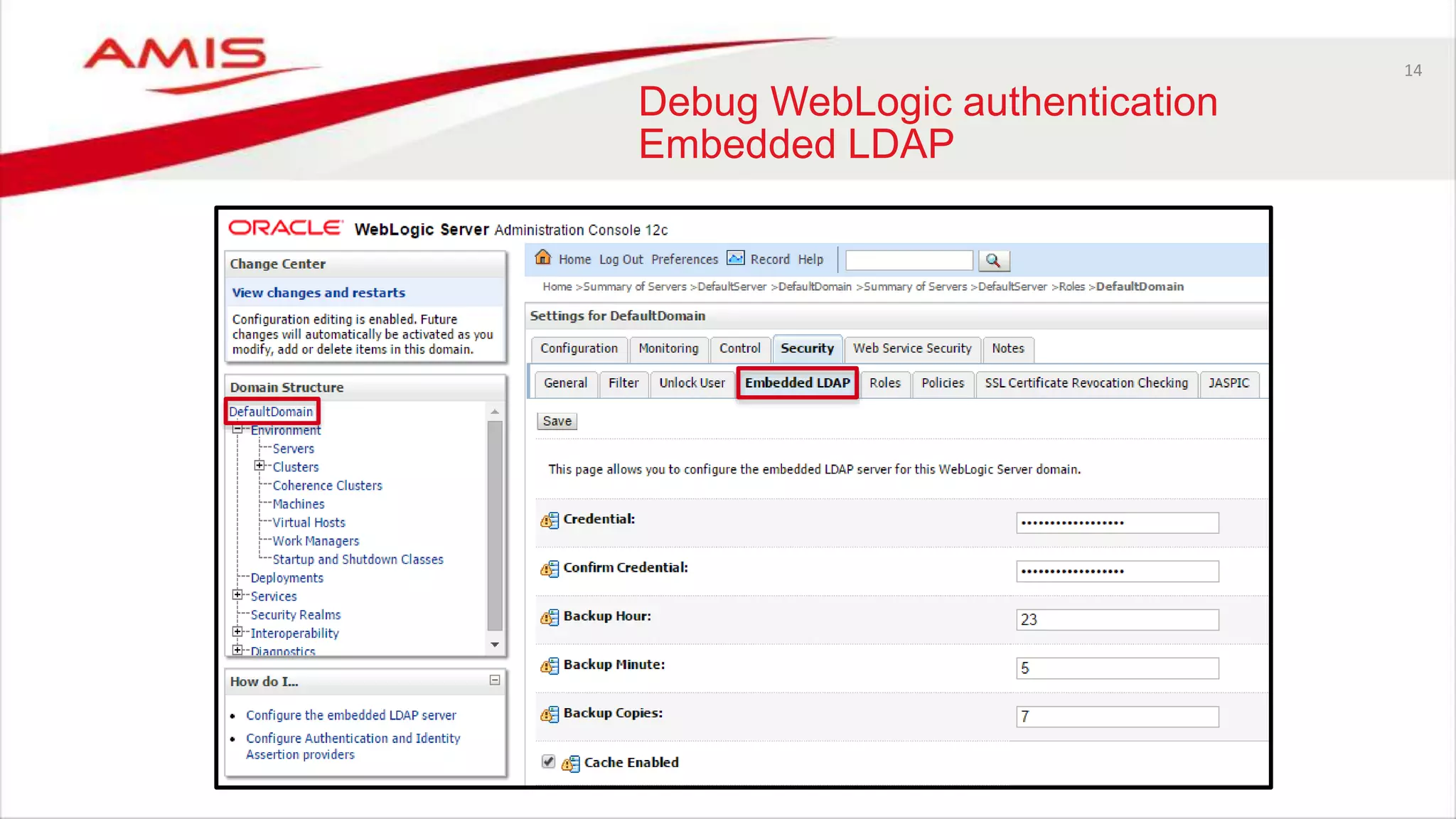
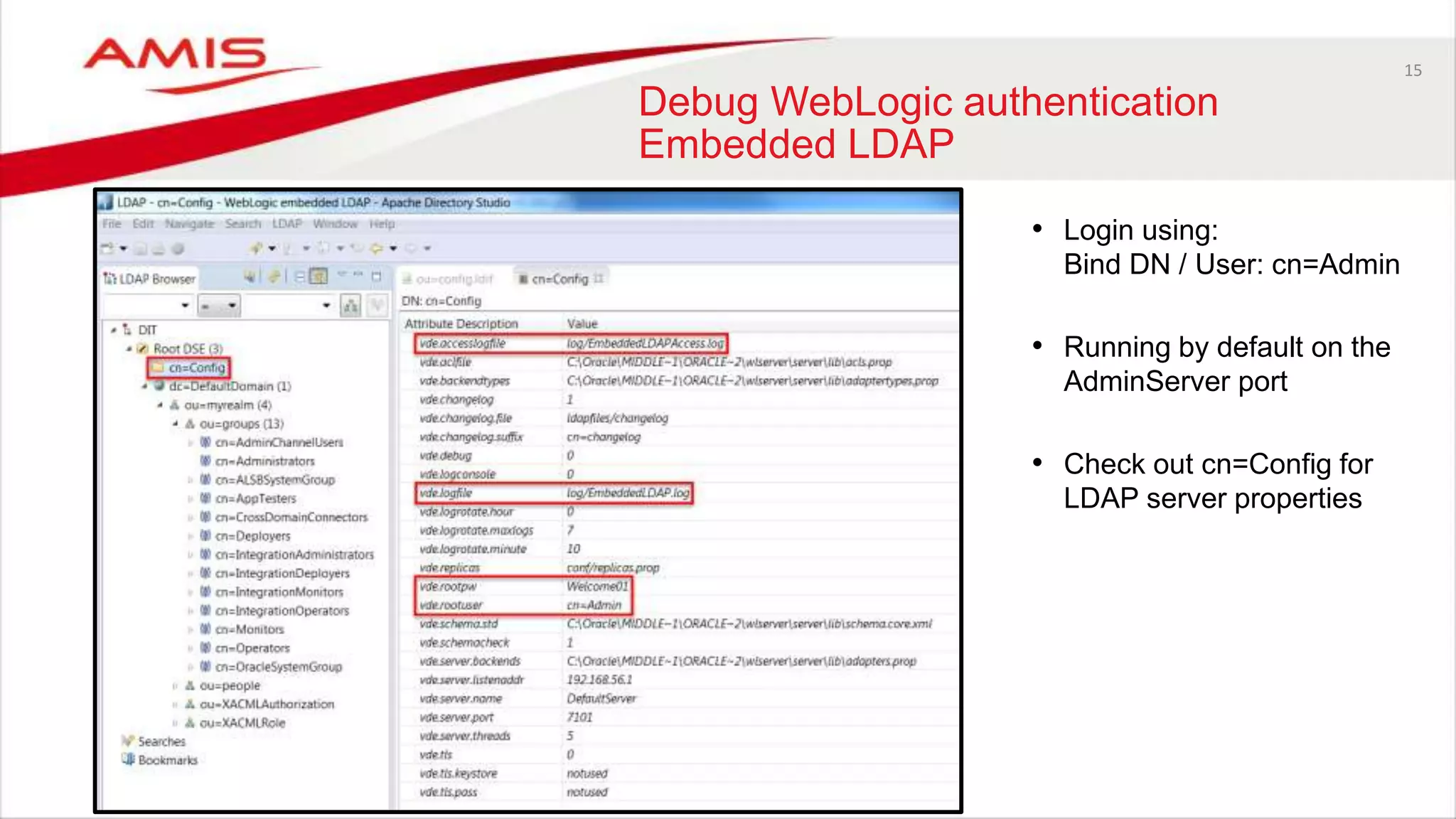
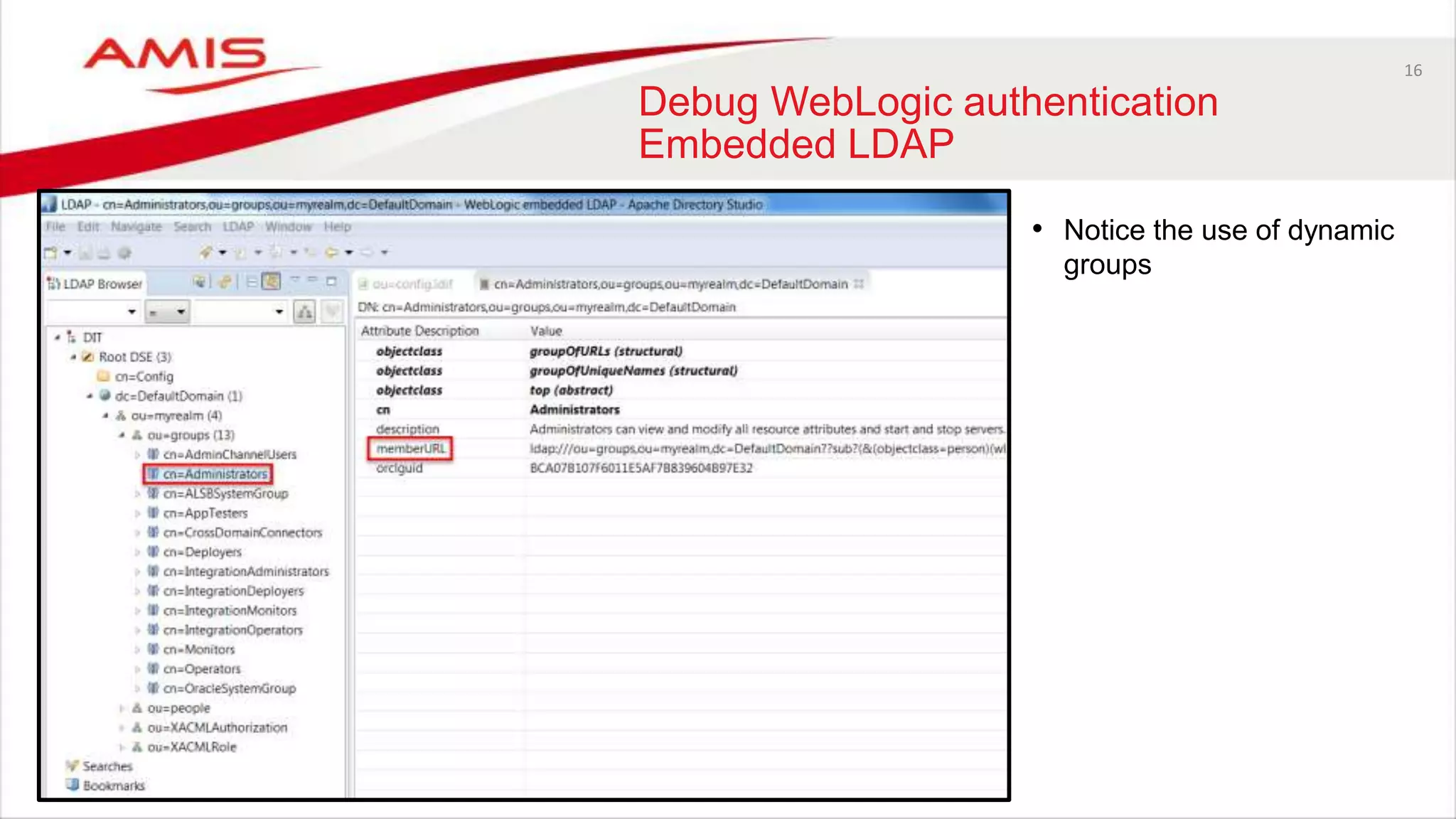
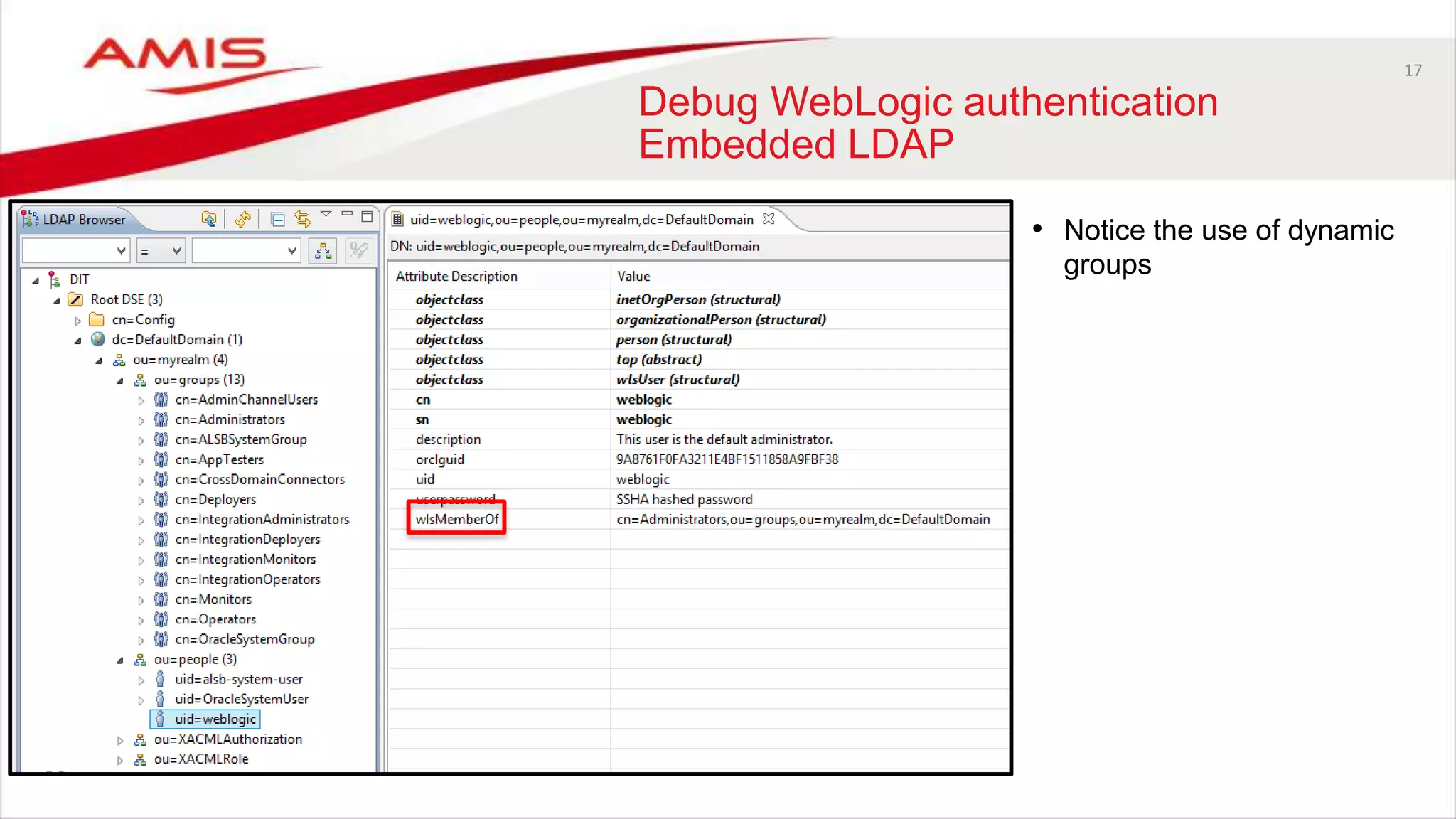
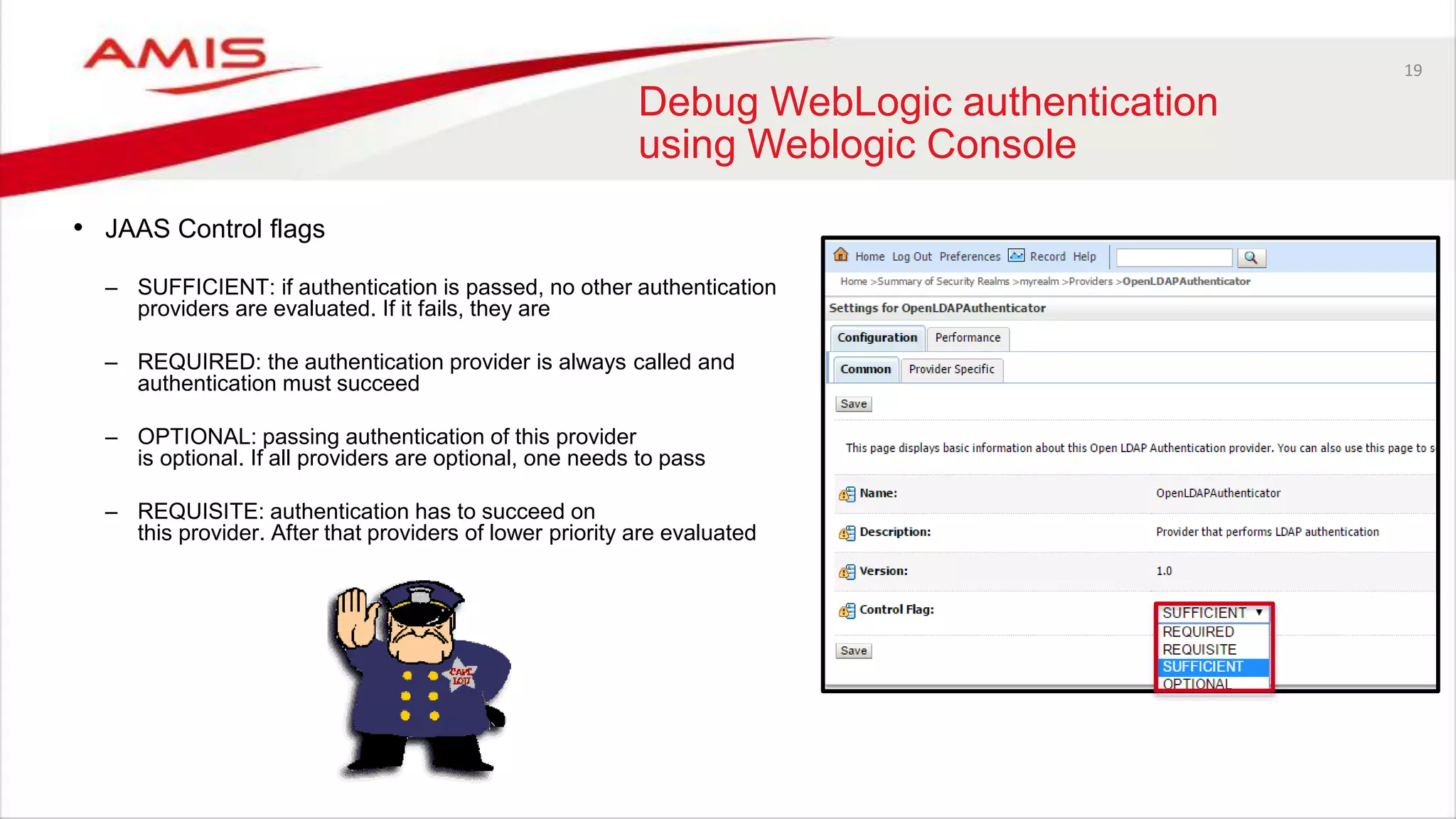
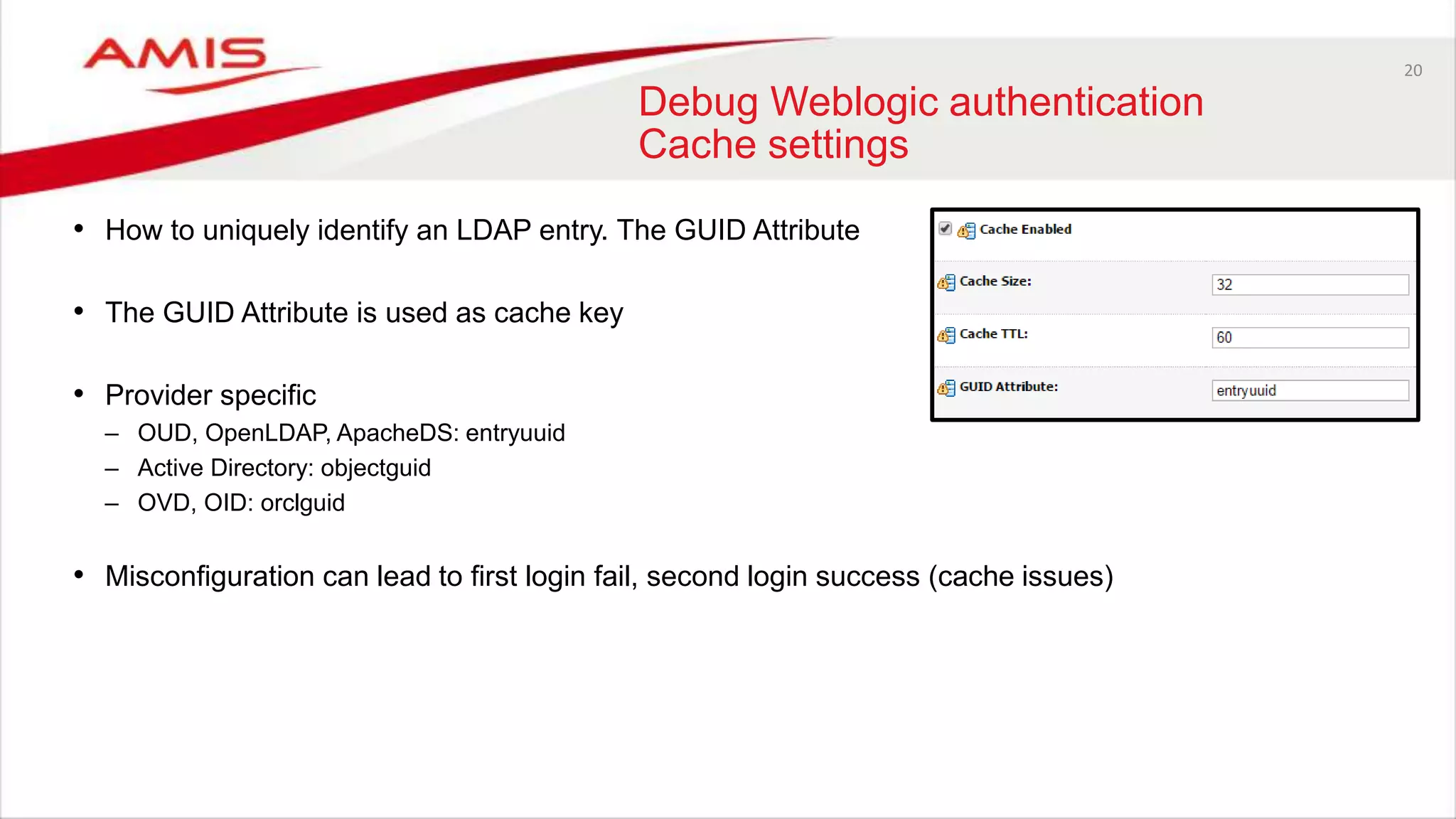
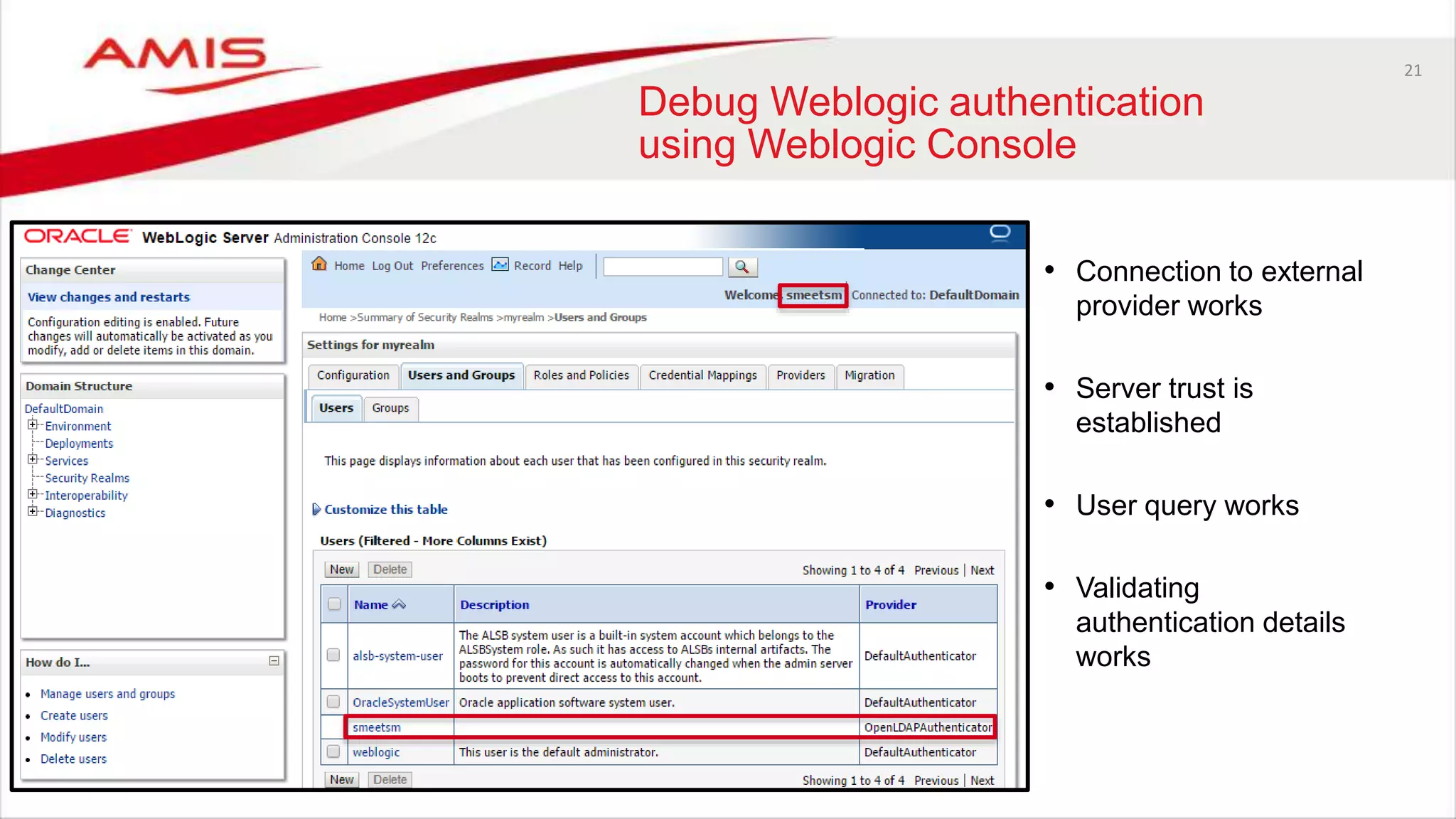
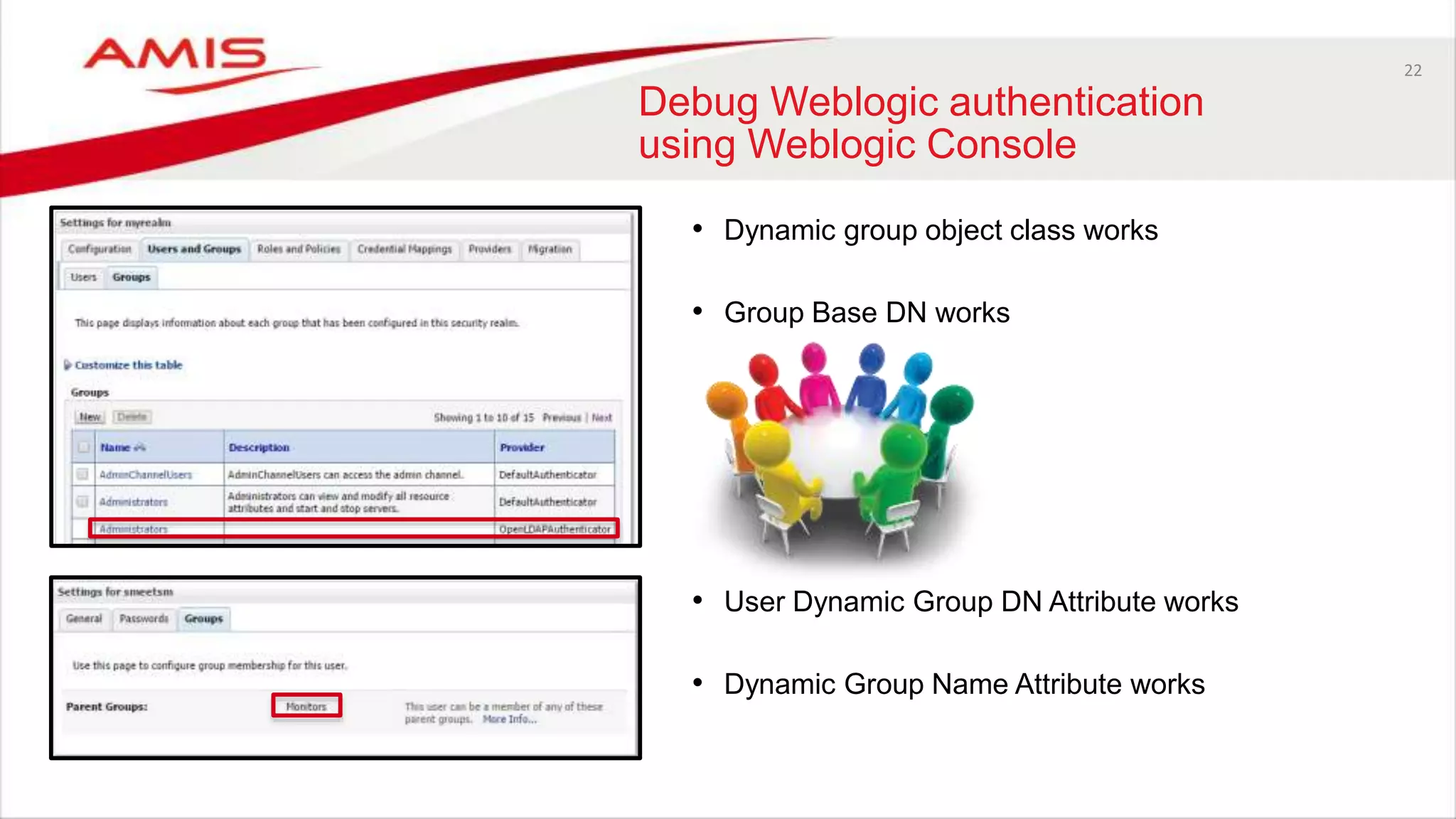
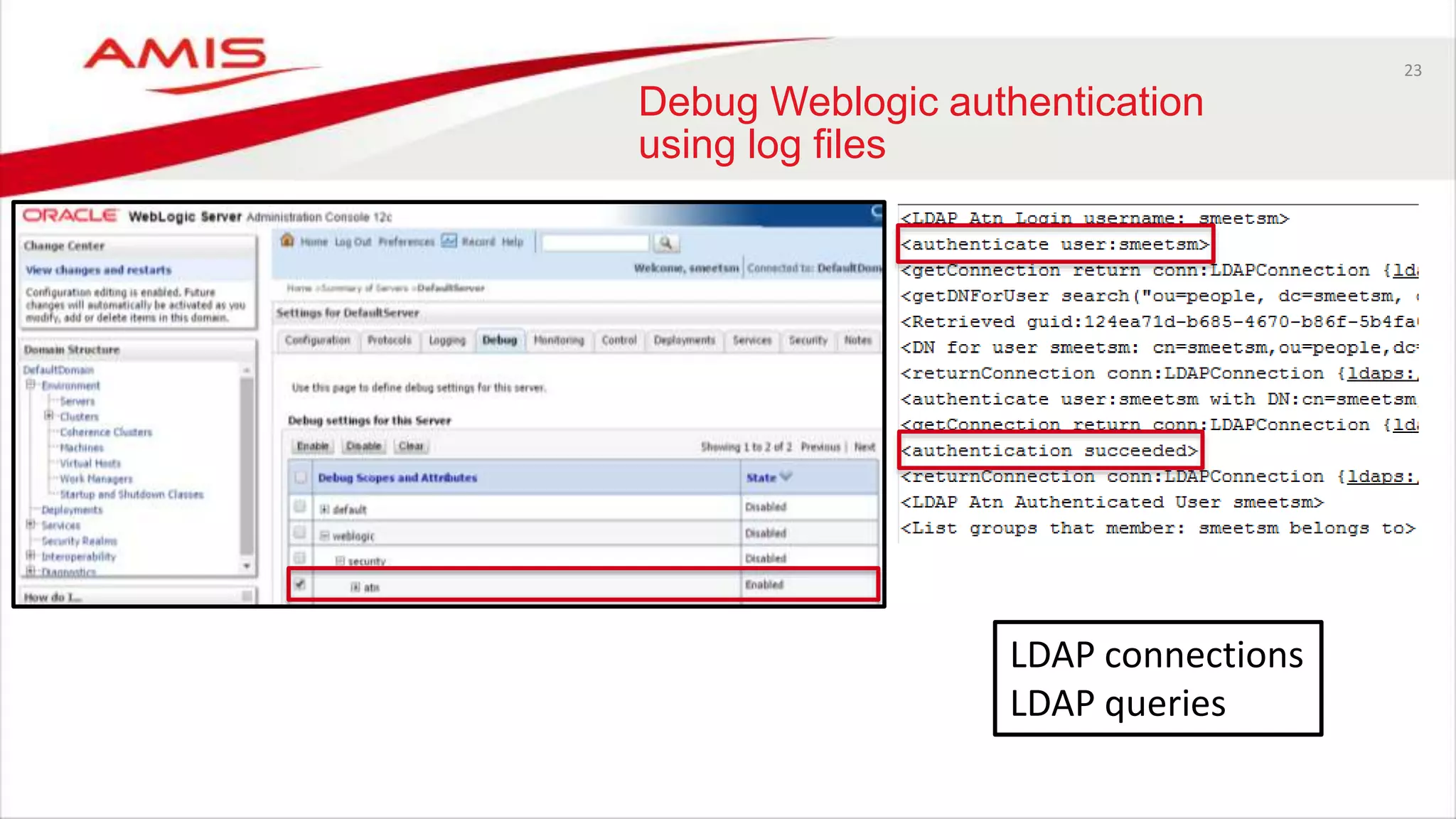
The document discusses debugging WebLogic authentication within Oracle Fusion Middleware, focusing on Oracle Identity Store solutions and Oracle Platform Security Services (OPSS). It covers various debugging techniques such as using external clients, the WebLogic console, and specific configuration files to troubleshoot application authentication issues. The conclusion emphasizes the importance of understanding the relationships between applications and authentication providers to effectively debug problems.









![34
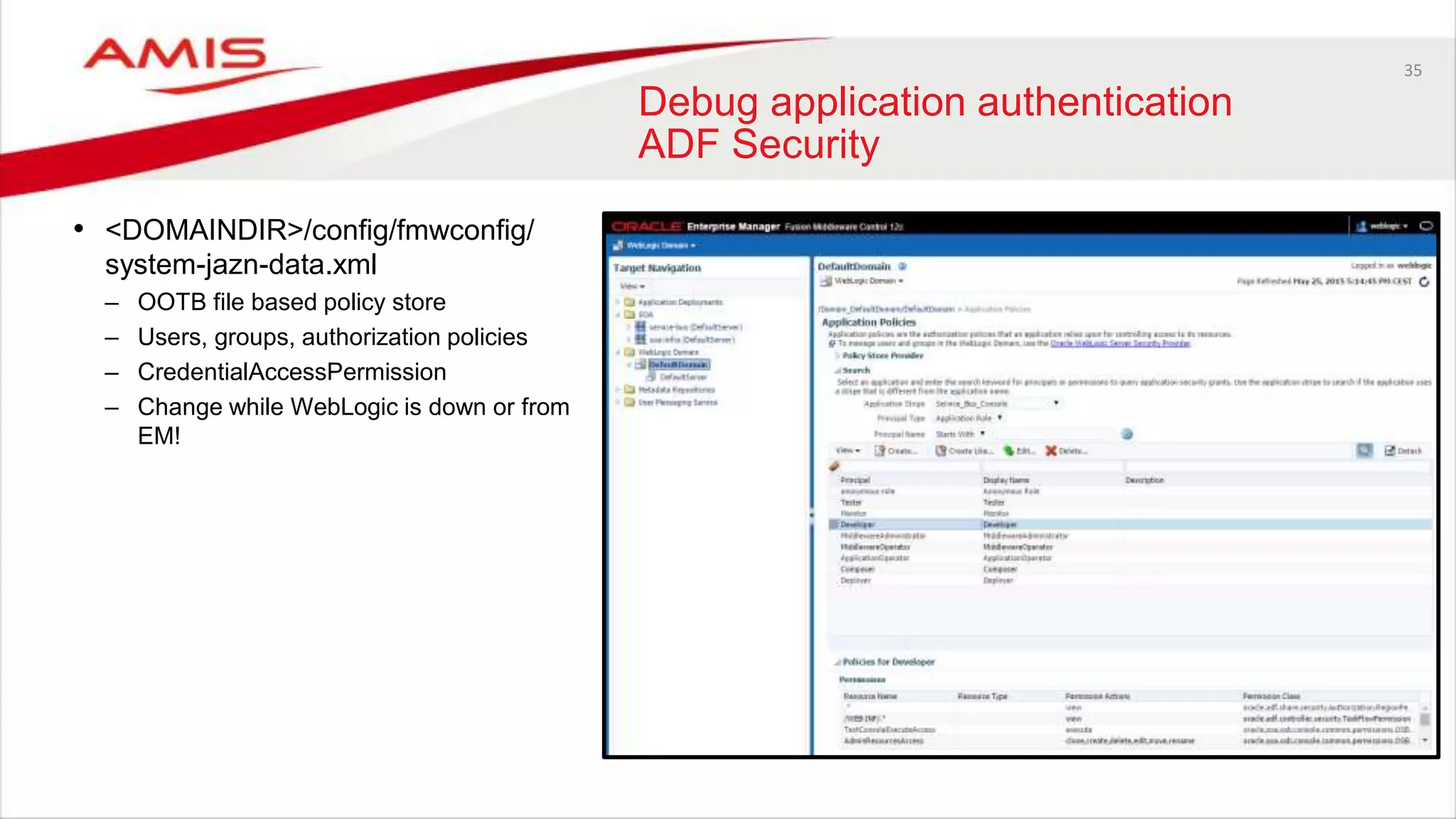
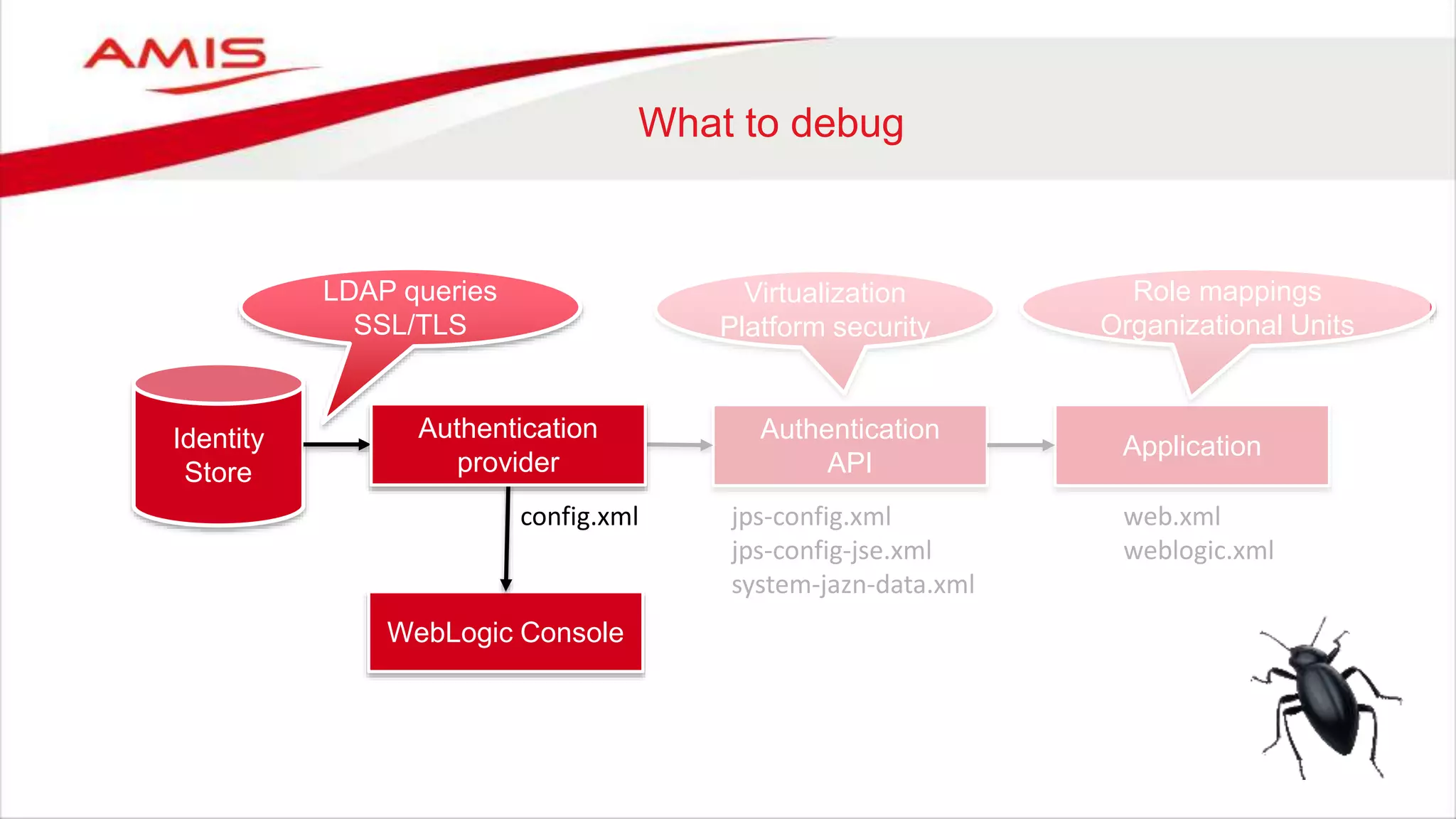
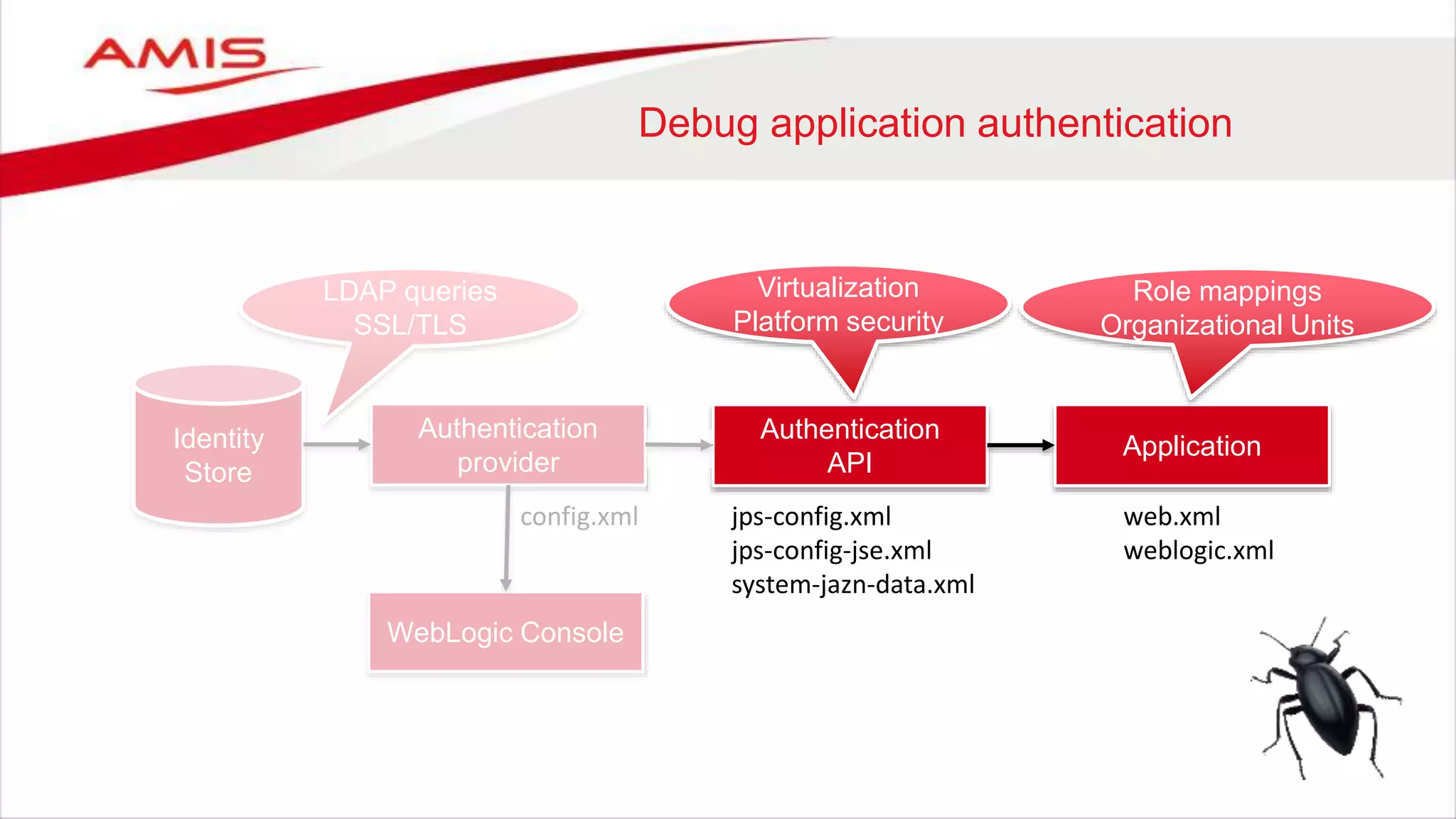
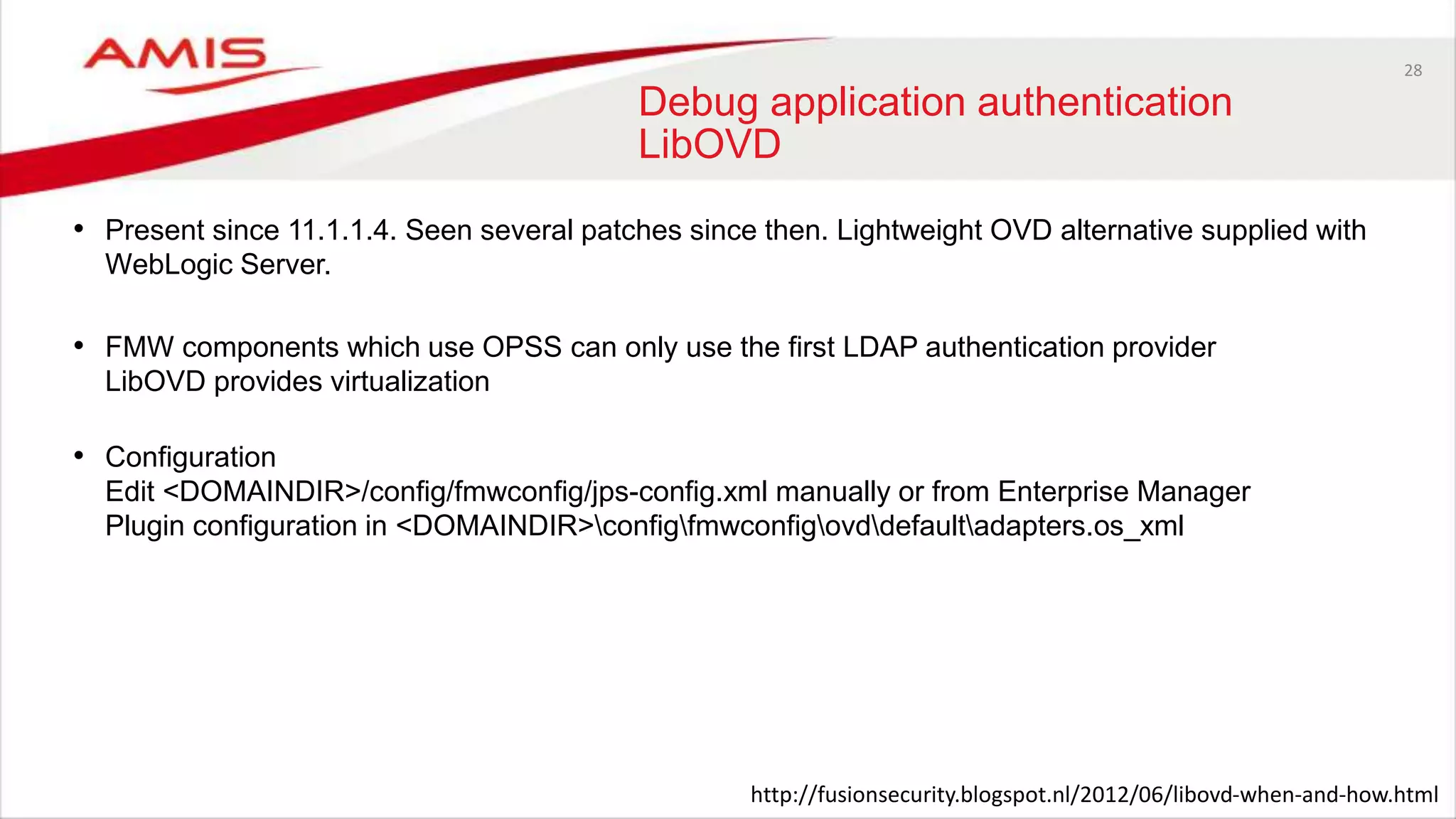
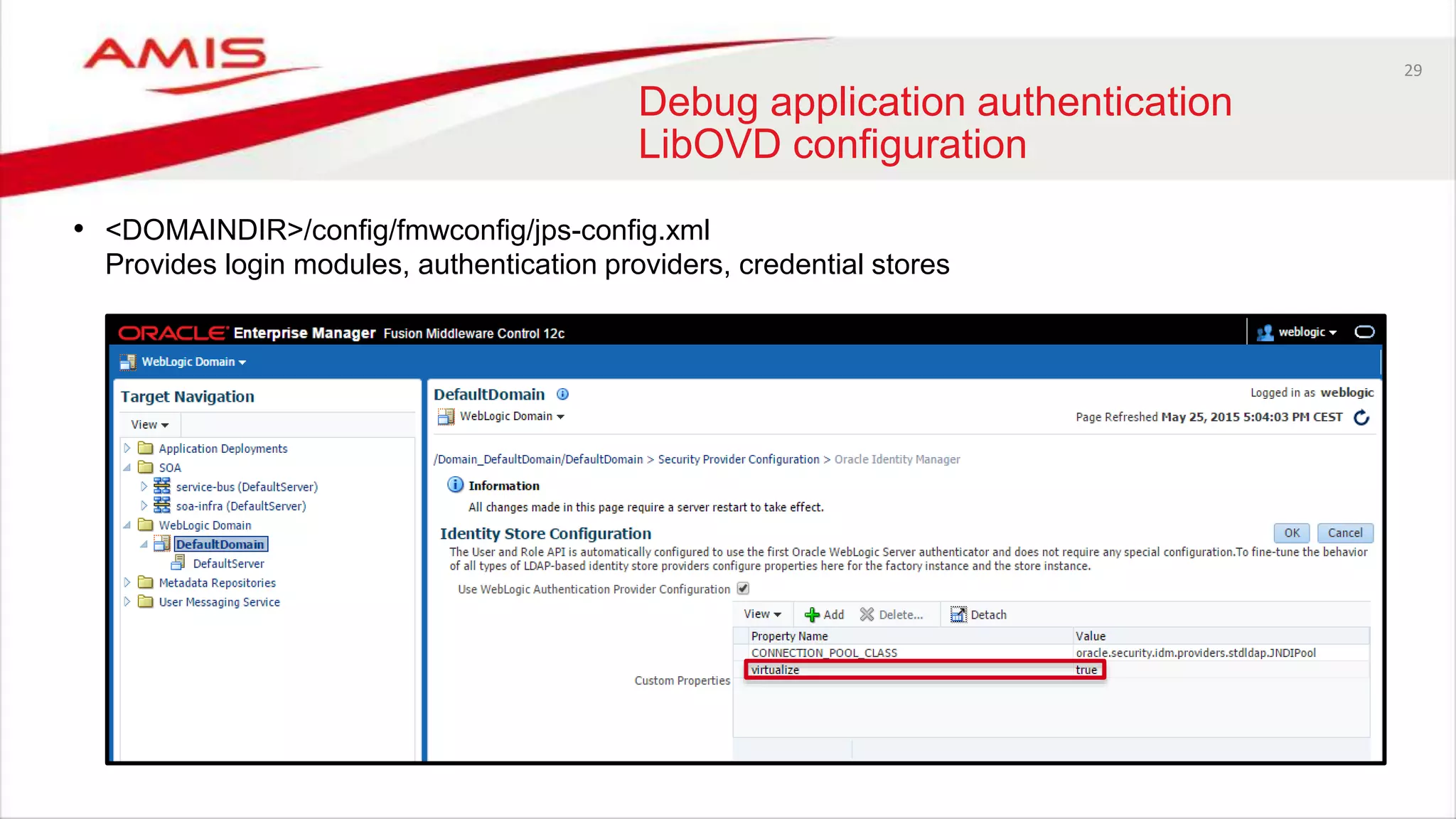
Debug application authentication
ADF Security
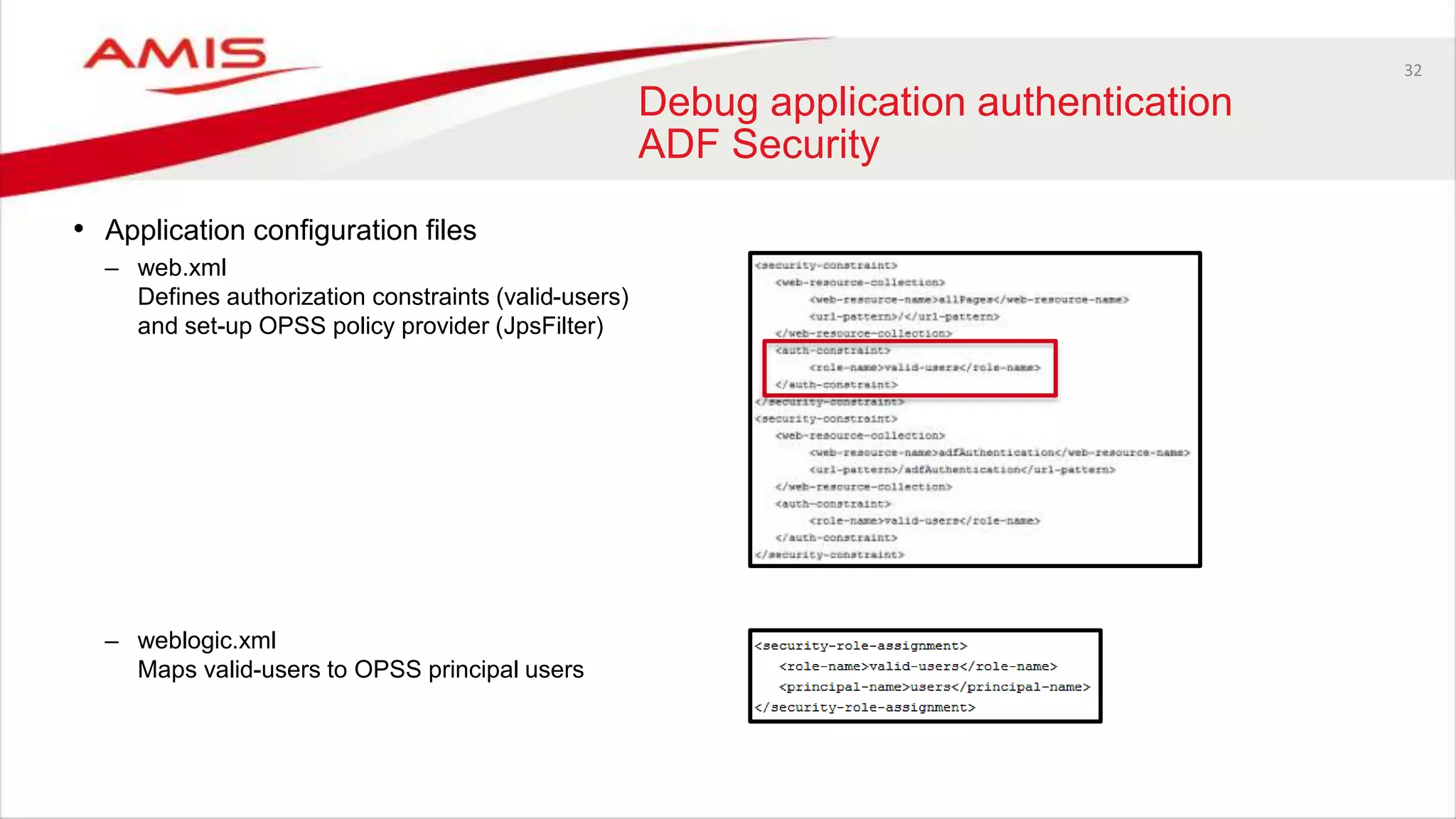
• Application configuration files
– jazn-data.xml
Contains development users / roles
Application roles are granted to enterprise roles / users (from the OPSS API which uses the authorization provider).
Resource permissions are granted to application roles or enterprise roles.
– Test with:
Java: ADFContext.getCurrent().getSecurityContext().isUserInRole(“role”)
EL: #{securityContext.userInRole[‘role']}
Users
Enterprise
roles
Application
roles
Permissions
Grants
weblogic.xml jazn-data.xml](https://image.slidesharecdn.com/weblogic-authentication-debugging-160217200351/75/WebLogic-authentication-debugging-34-2048.jpg)