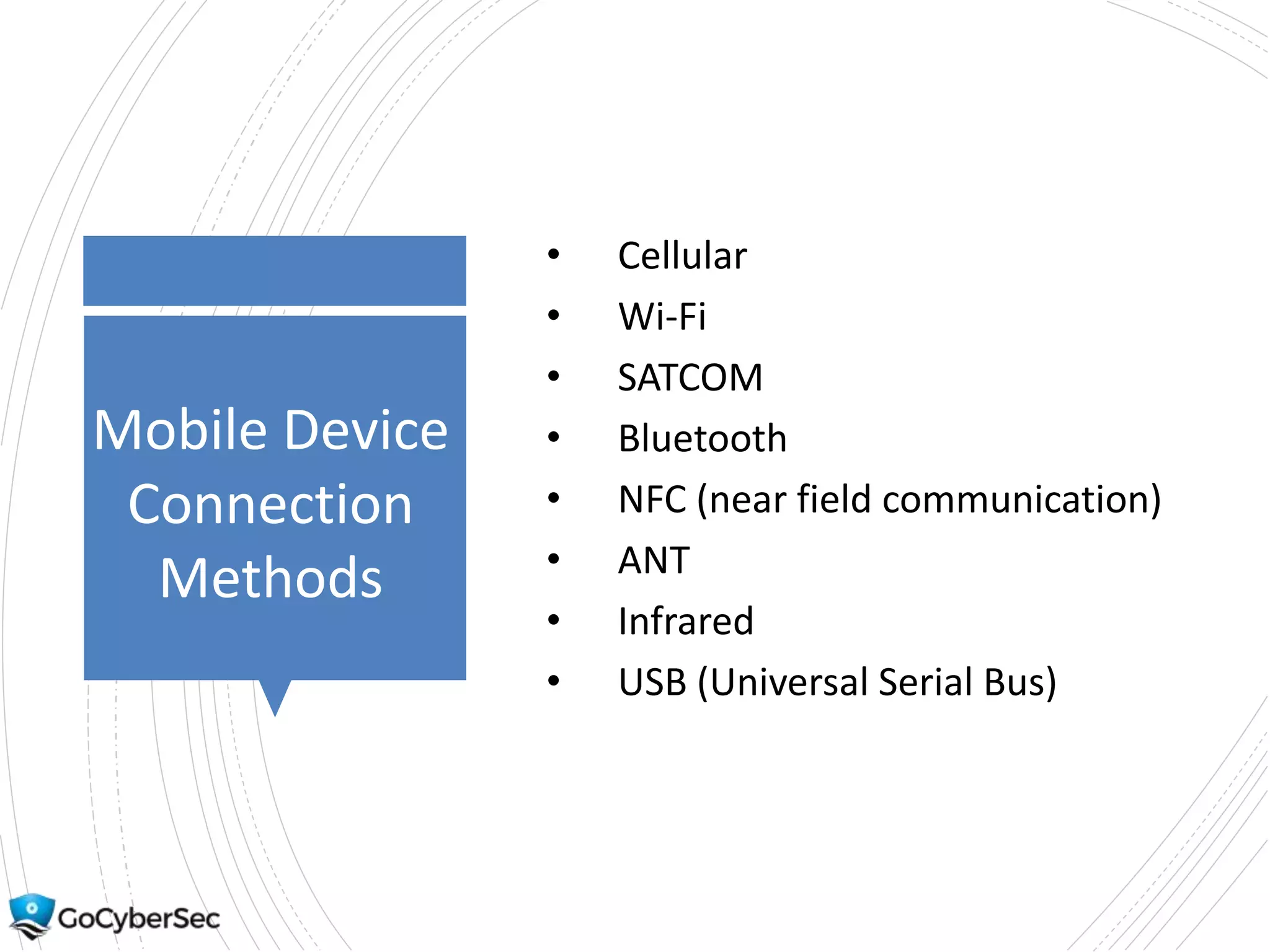
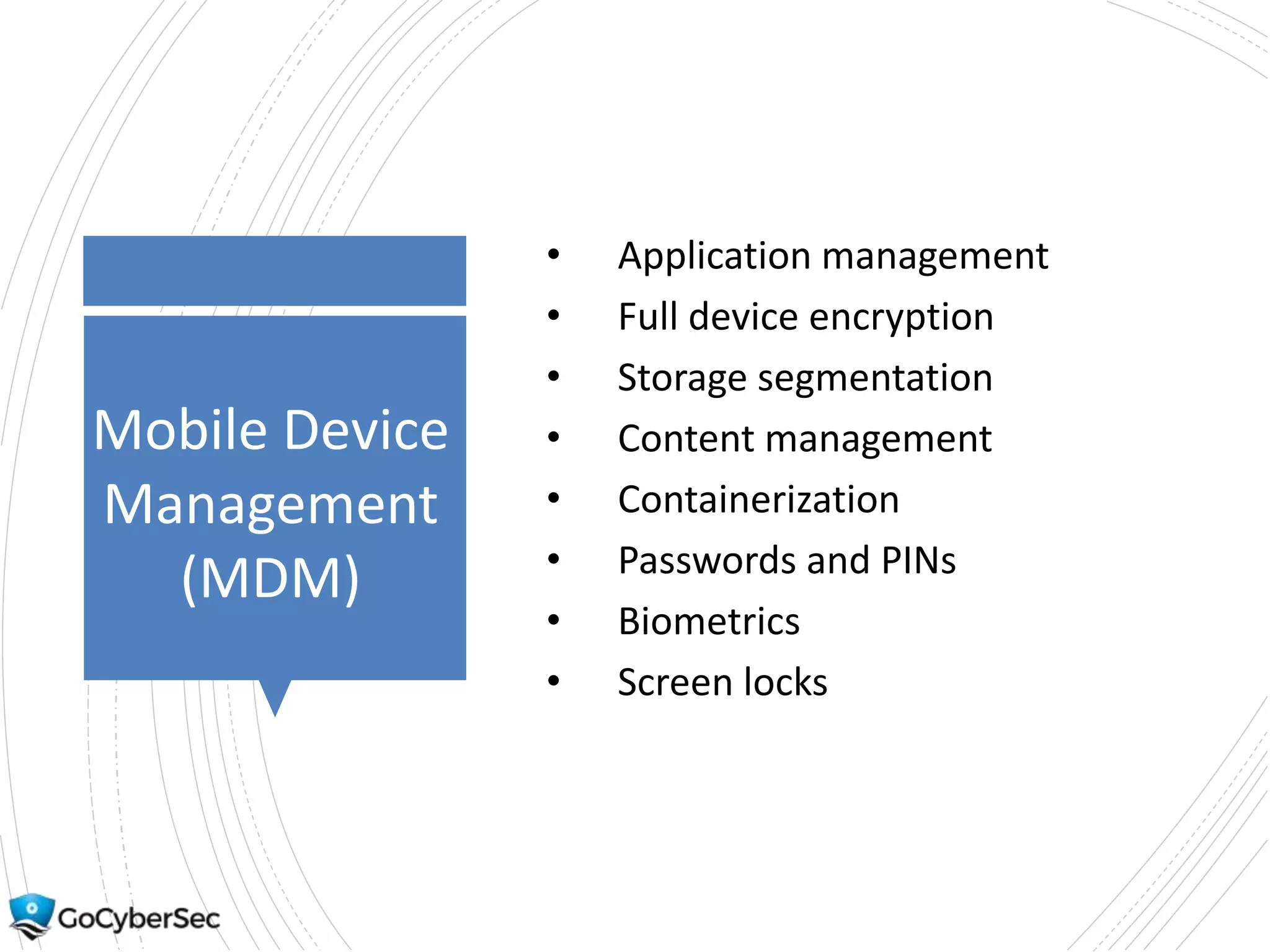
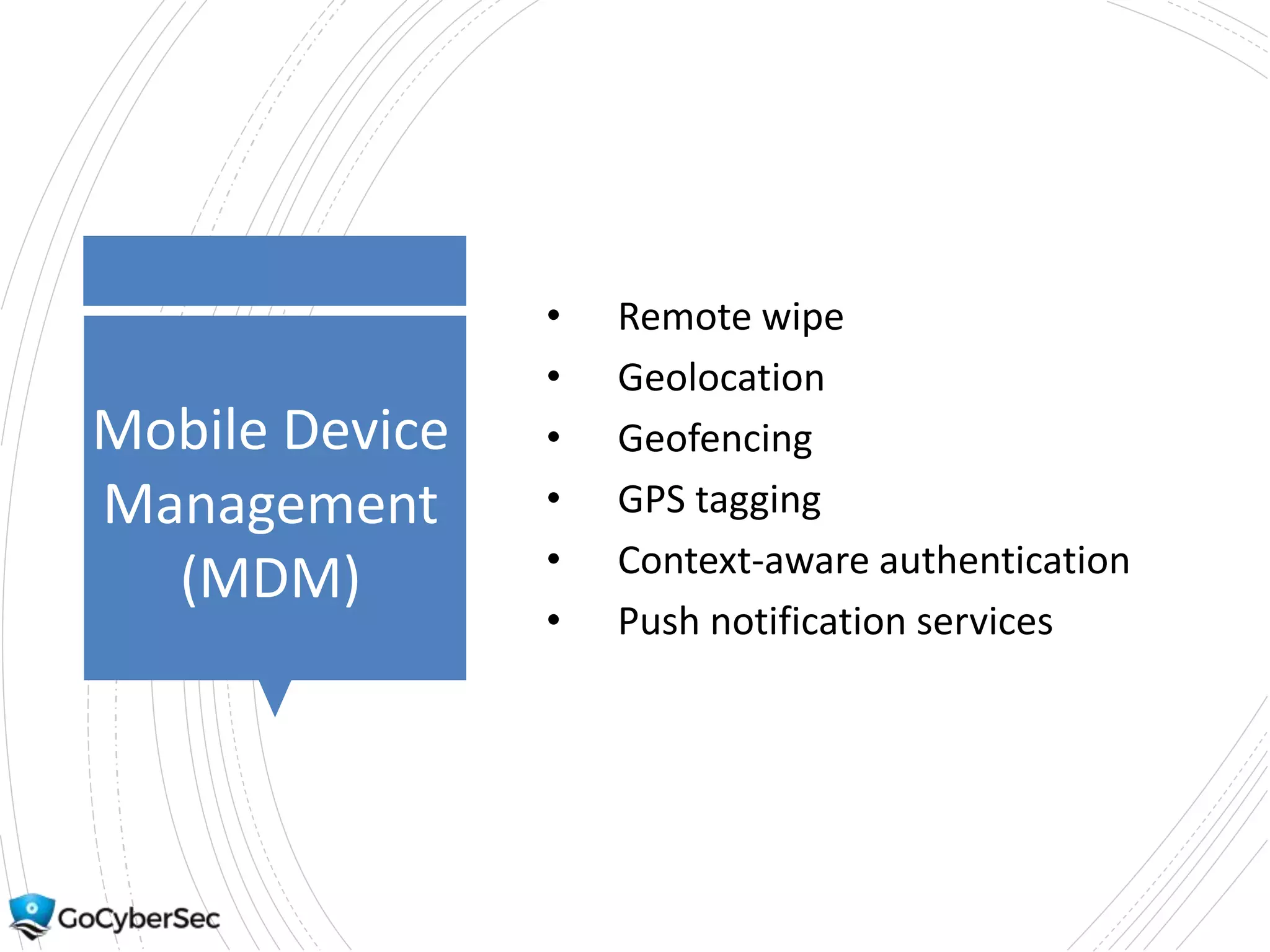
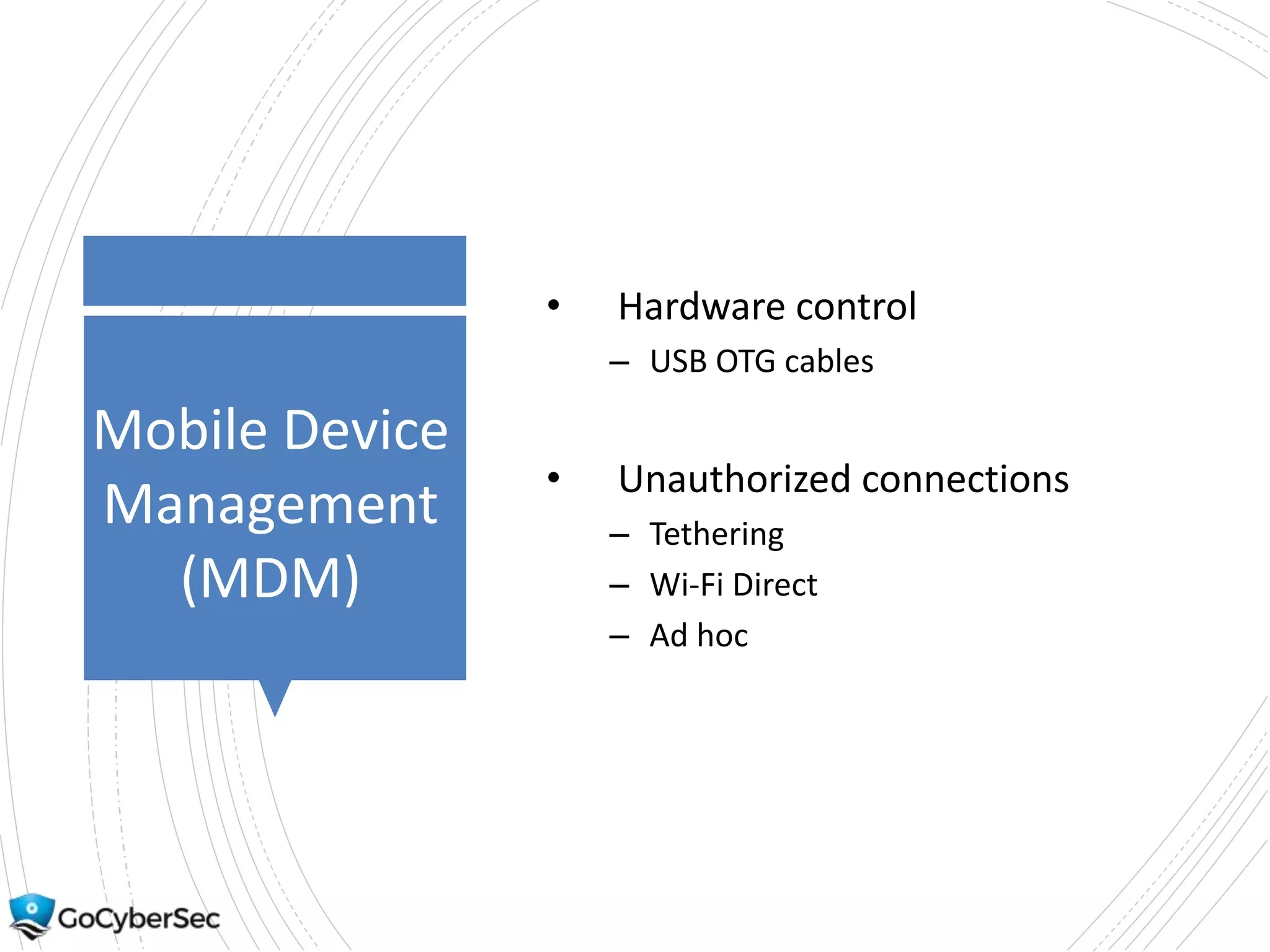
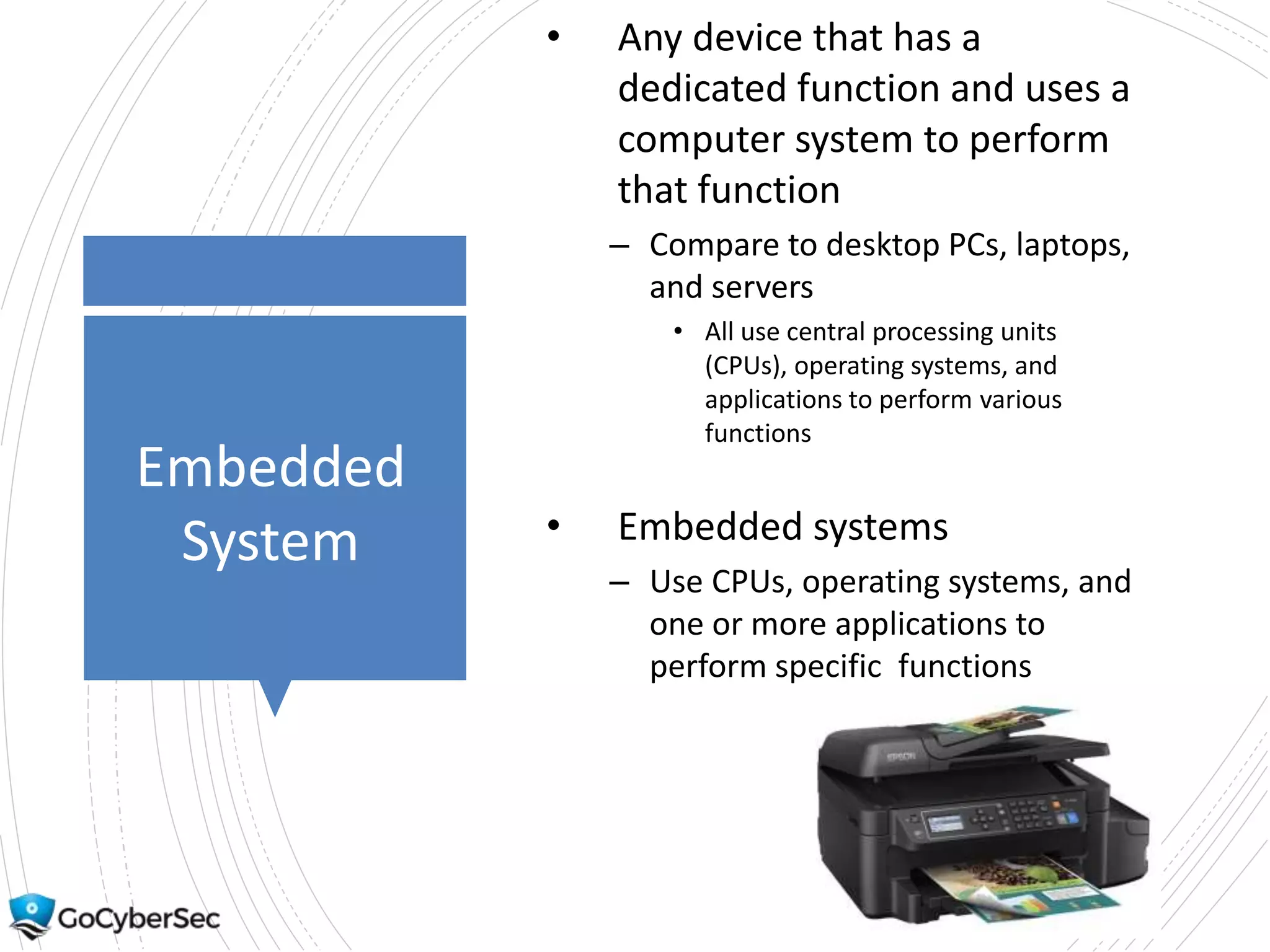
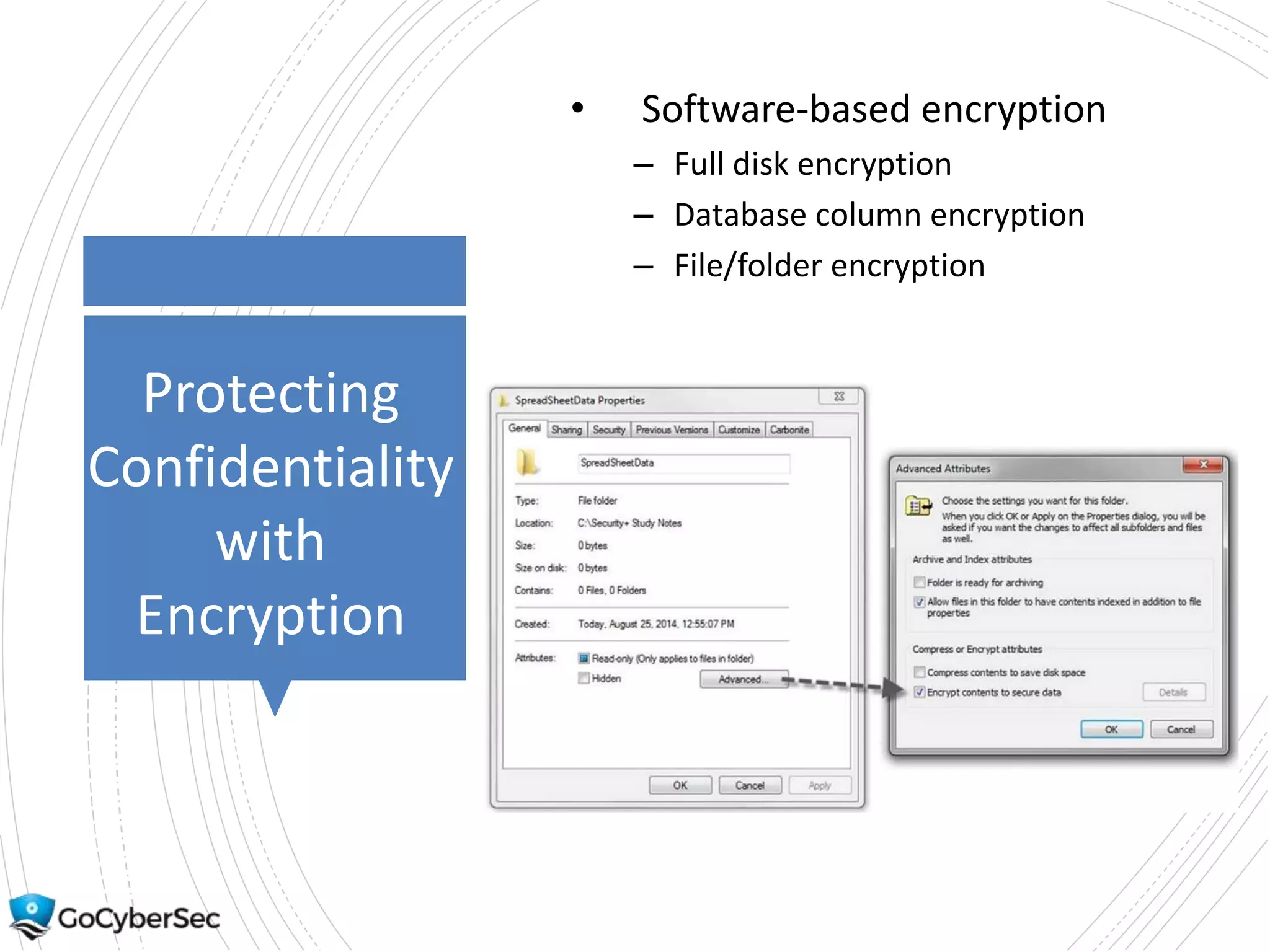
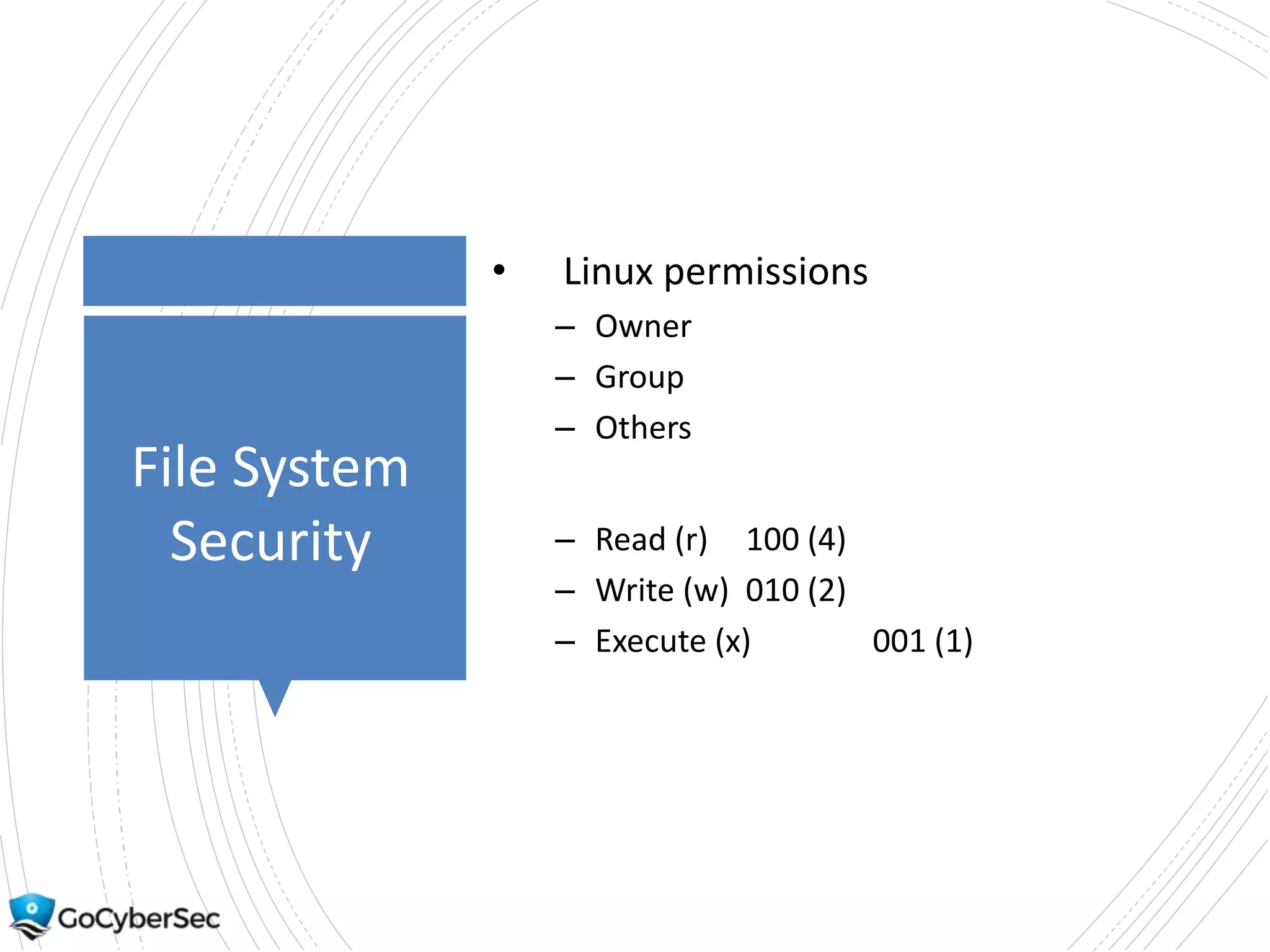
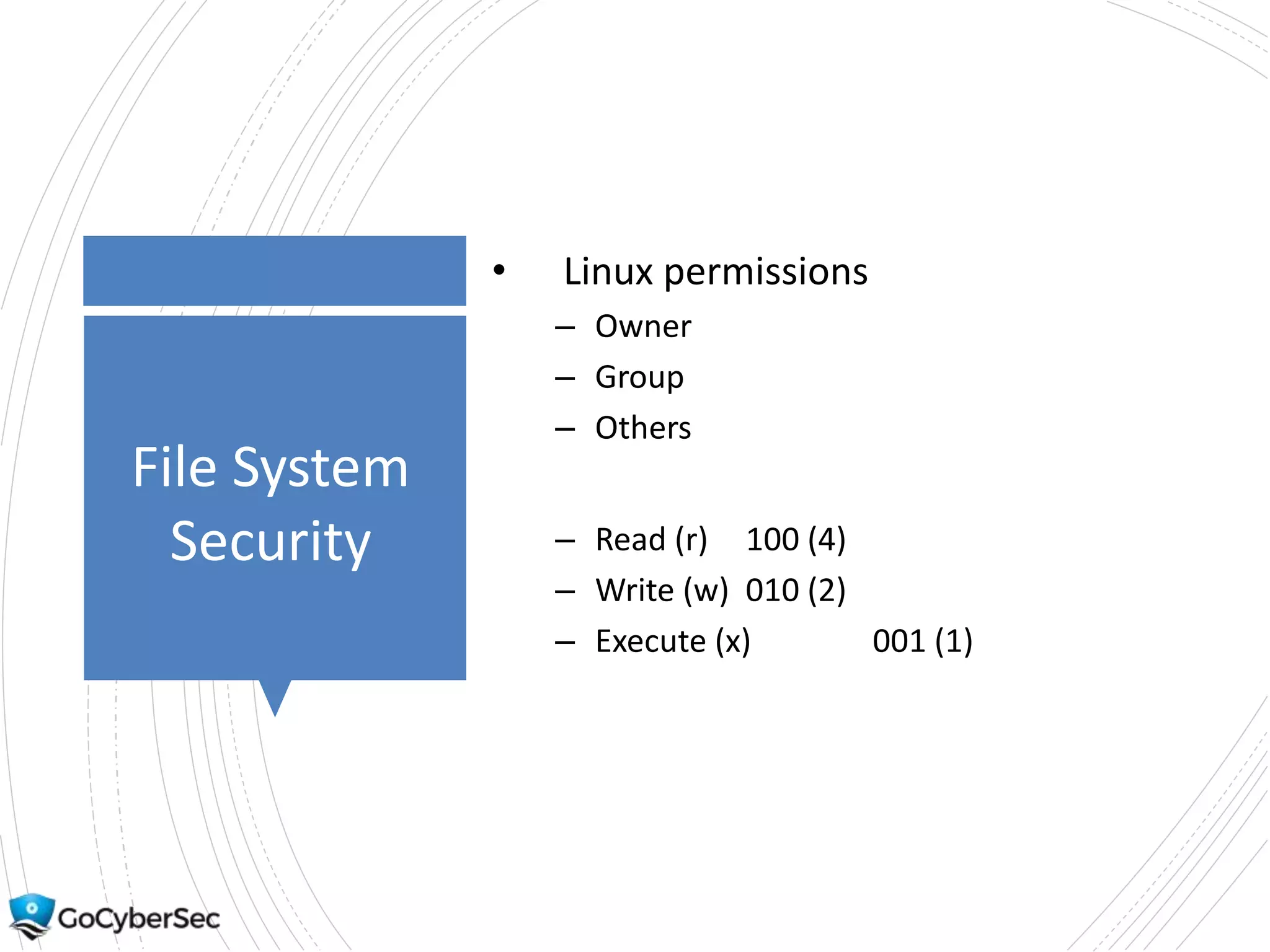
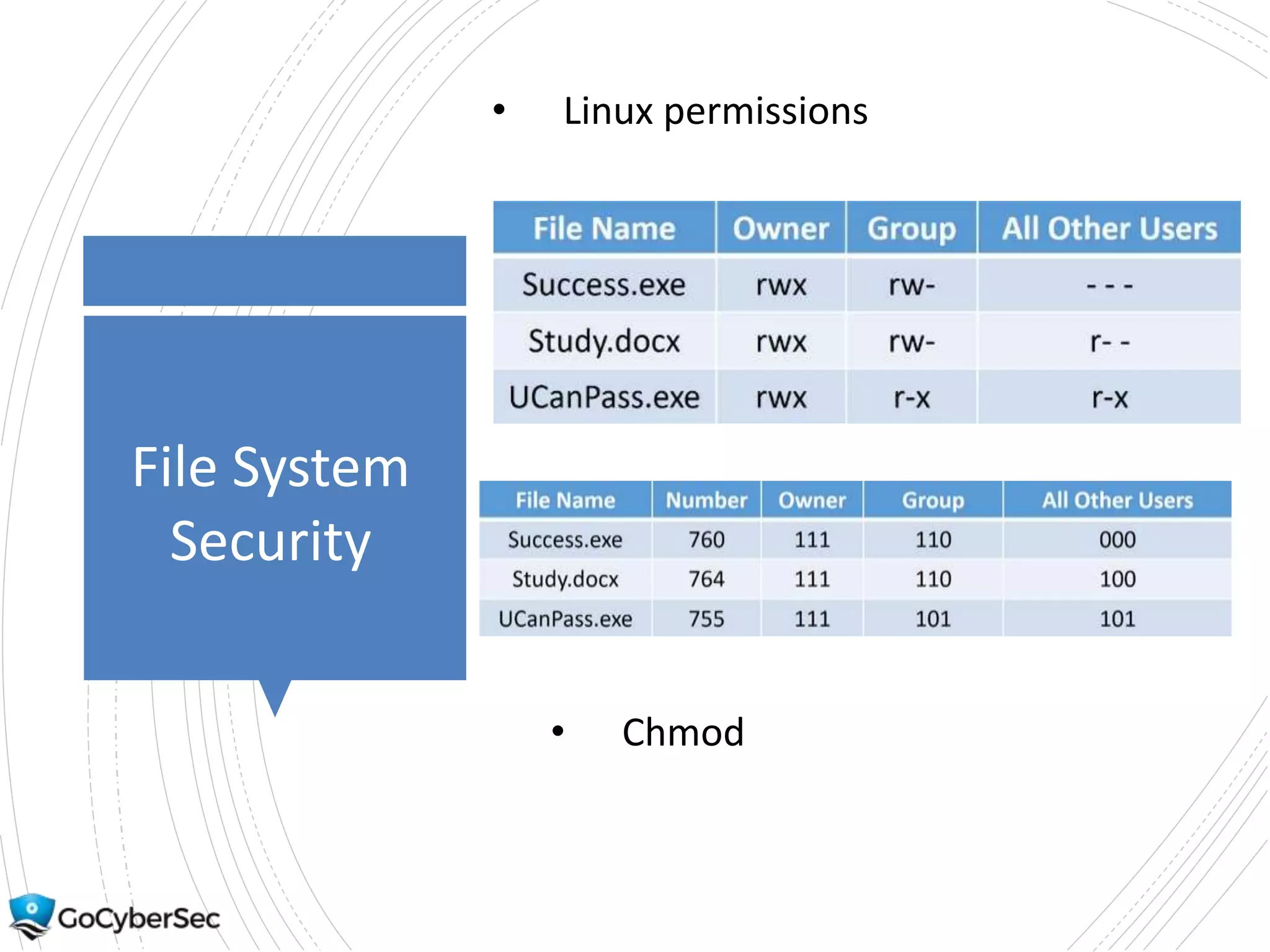
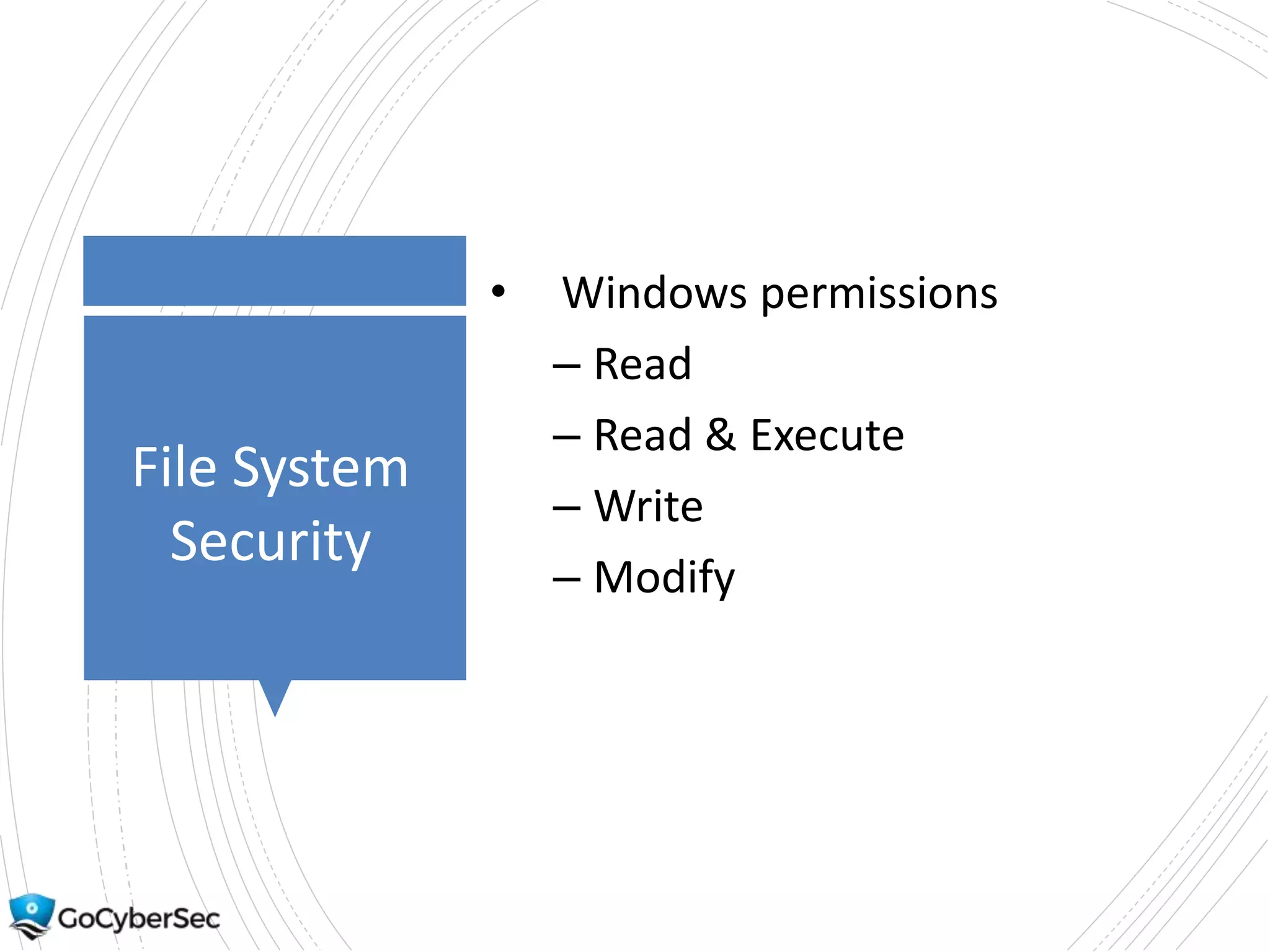
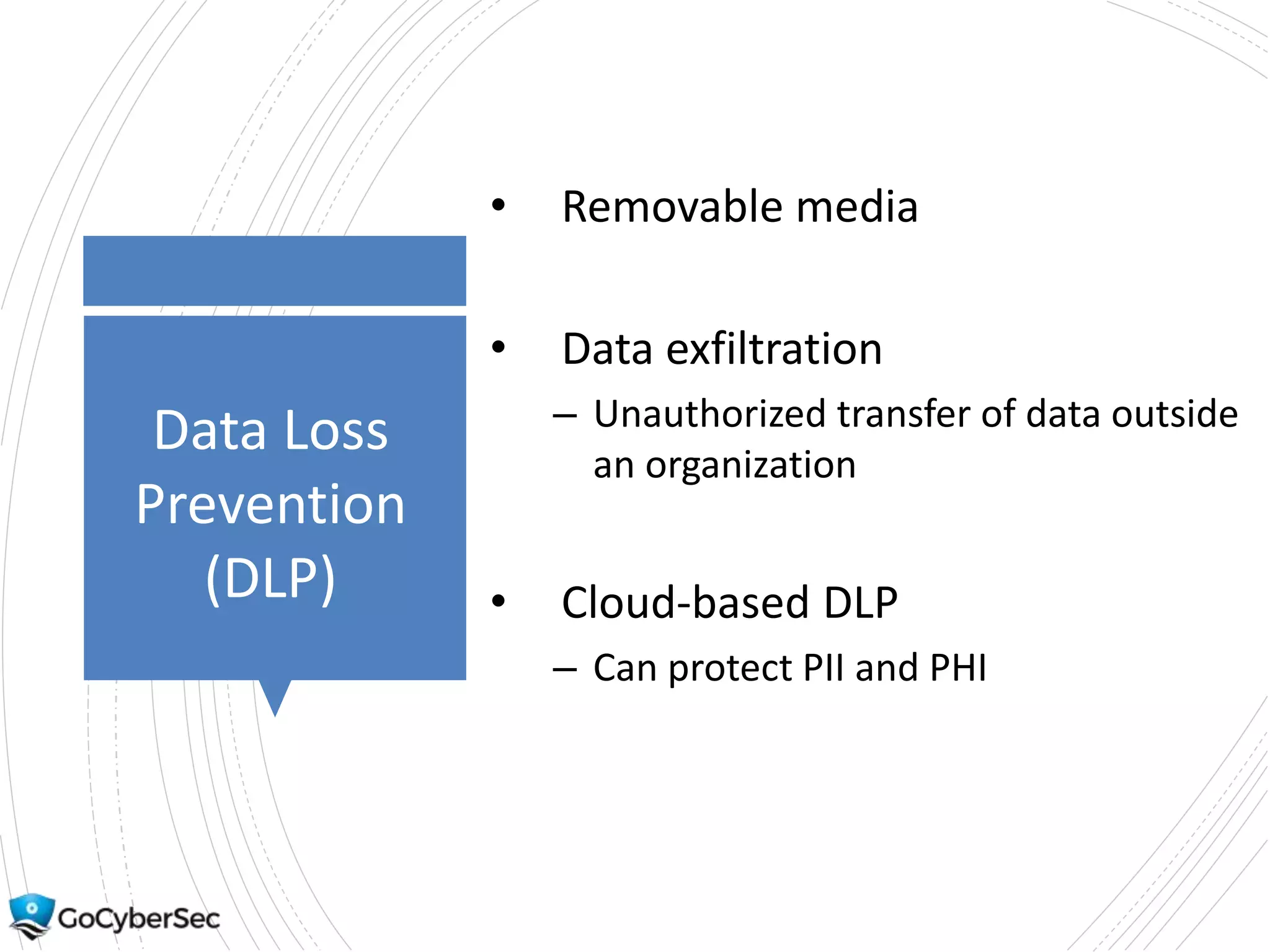
This chapter discusses securing operating systems, hosts, and data. It covers implementing least functionality and keeping systems updated to reduce attack surfaces. It also summarizes cloud computing models including IaaS, PaaS, and SaaS and mobile device deployment models. The chapter discusses securing data at rest and in transit through encryption techniques.