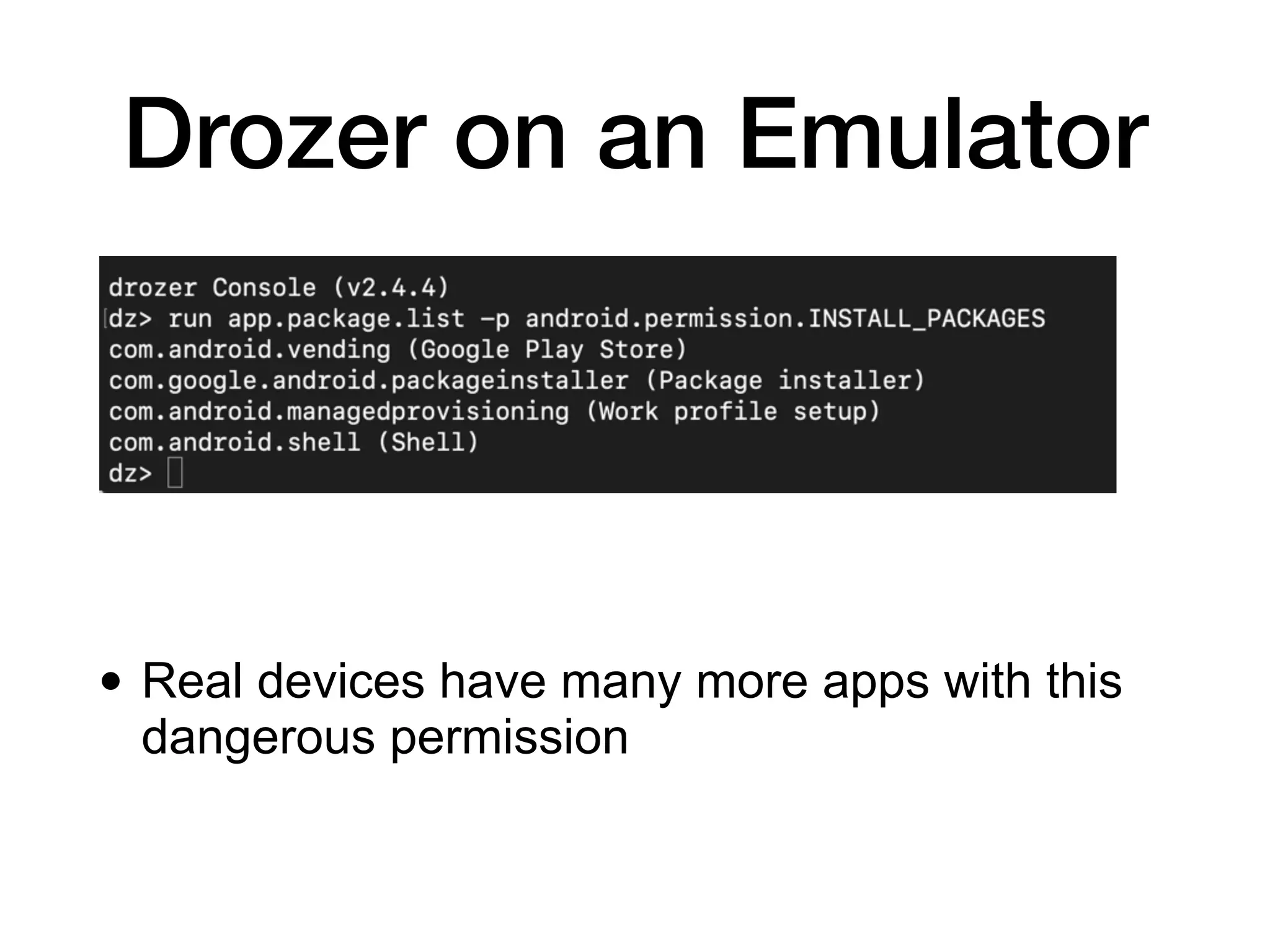
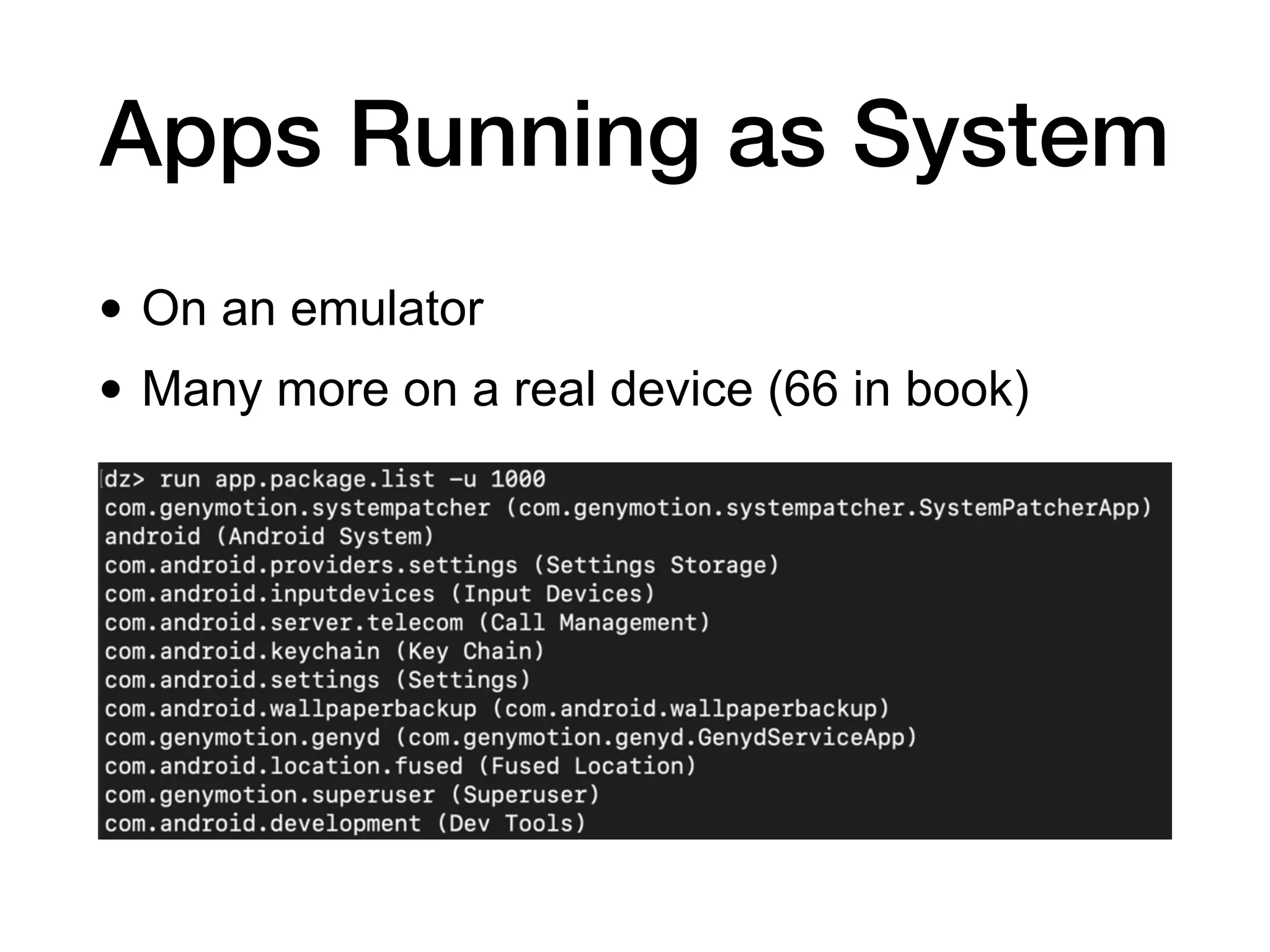
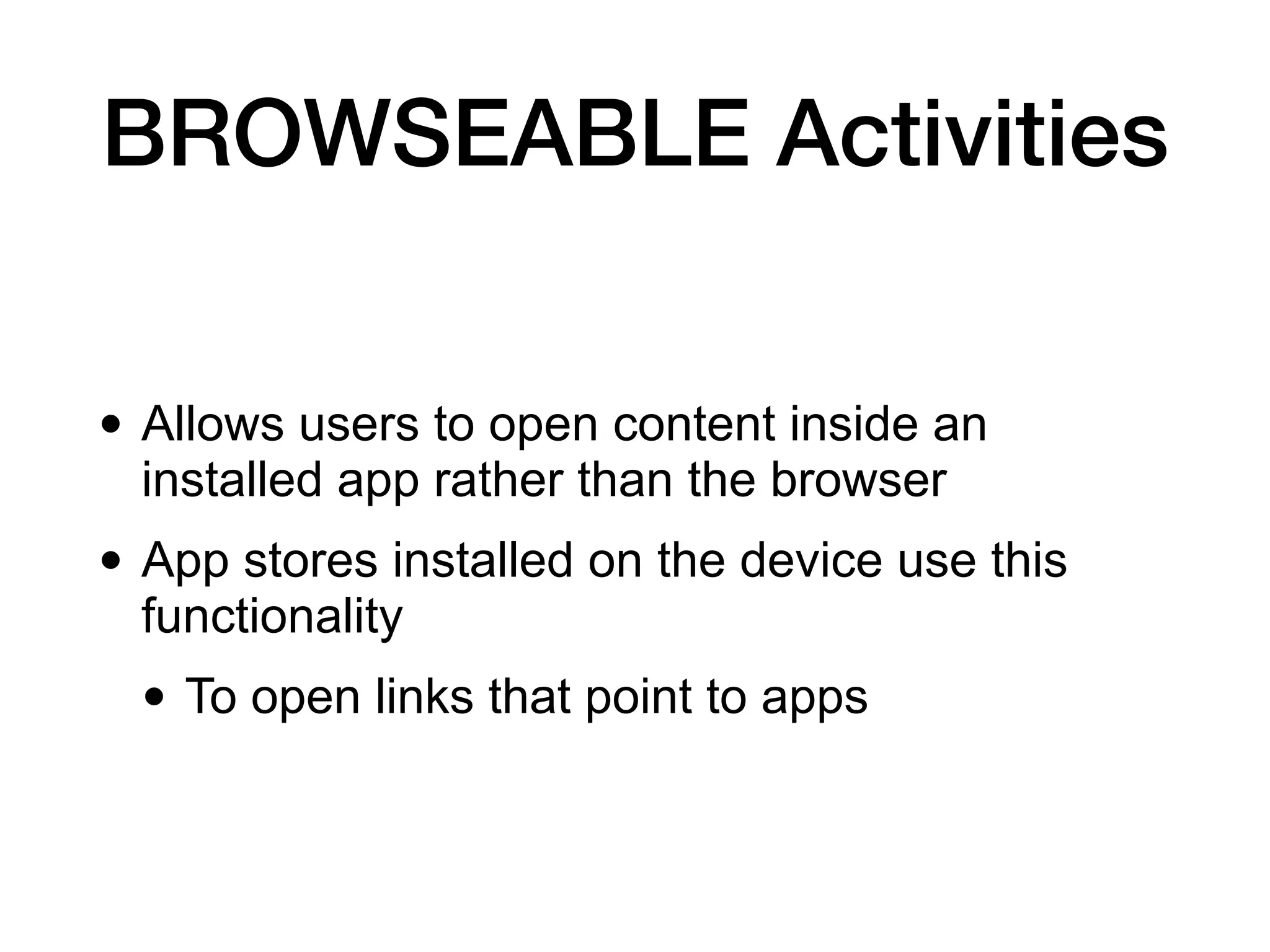
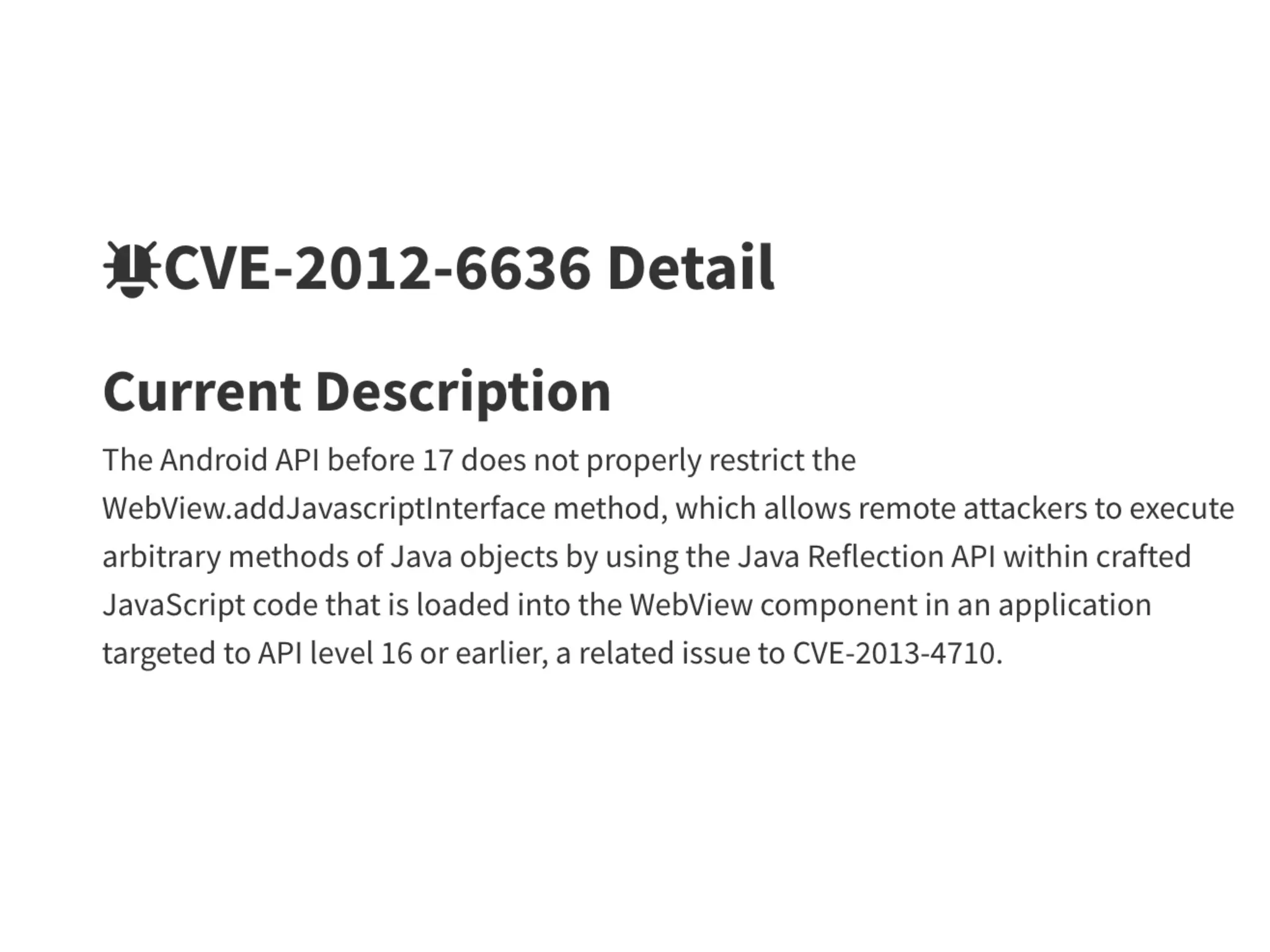
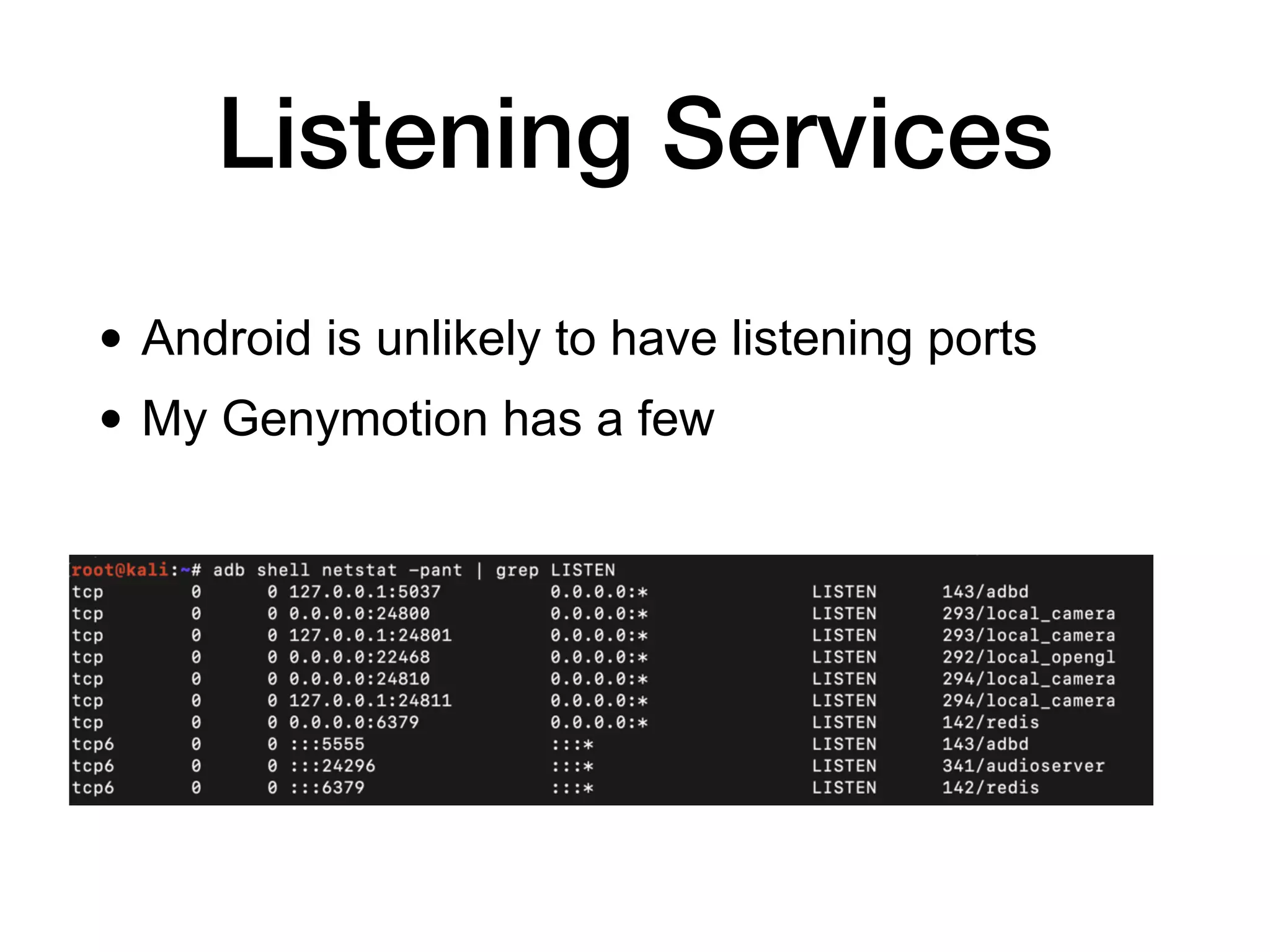
This document discusses exploiting vulnerabilities in Android devices. It covers identifying pre-installed apps that could provide access, techniques for remotely or locally exploiting devices, and the different privilege levels an attacker may obtain including non-system app access, installed package access, ADB shell access, system user access, and root user access. Specific exploitation techniques mentioned include exploiting update mechanisms, remote code loading, webviews, listening services, and messaging apps. Tools discussed include Drozer, Ettercap, and Burp.