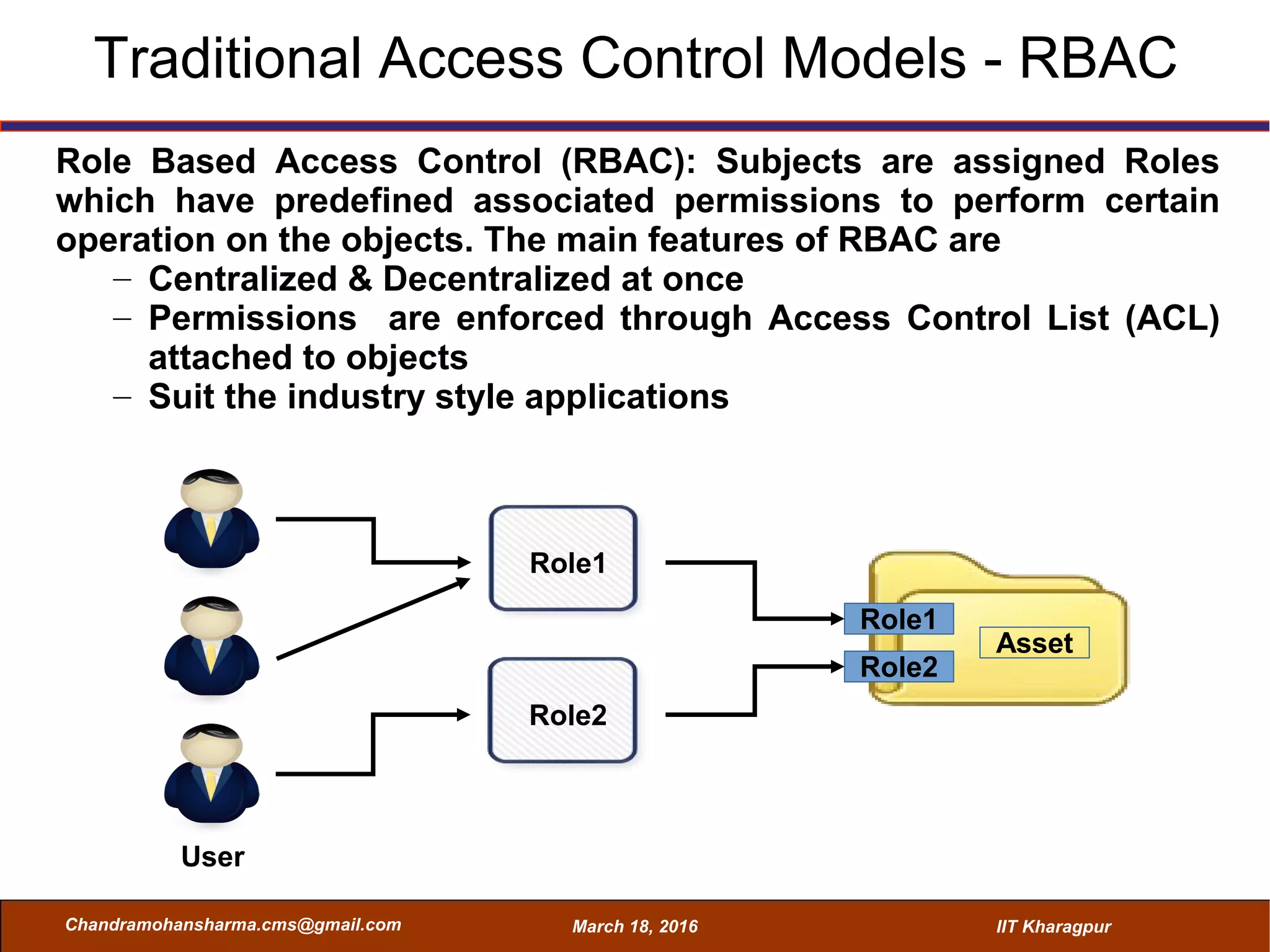
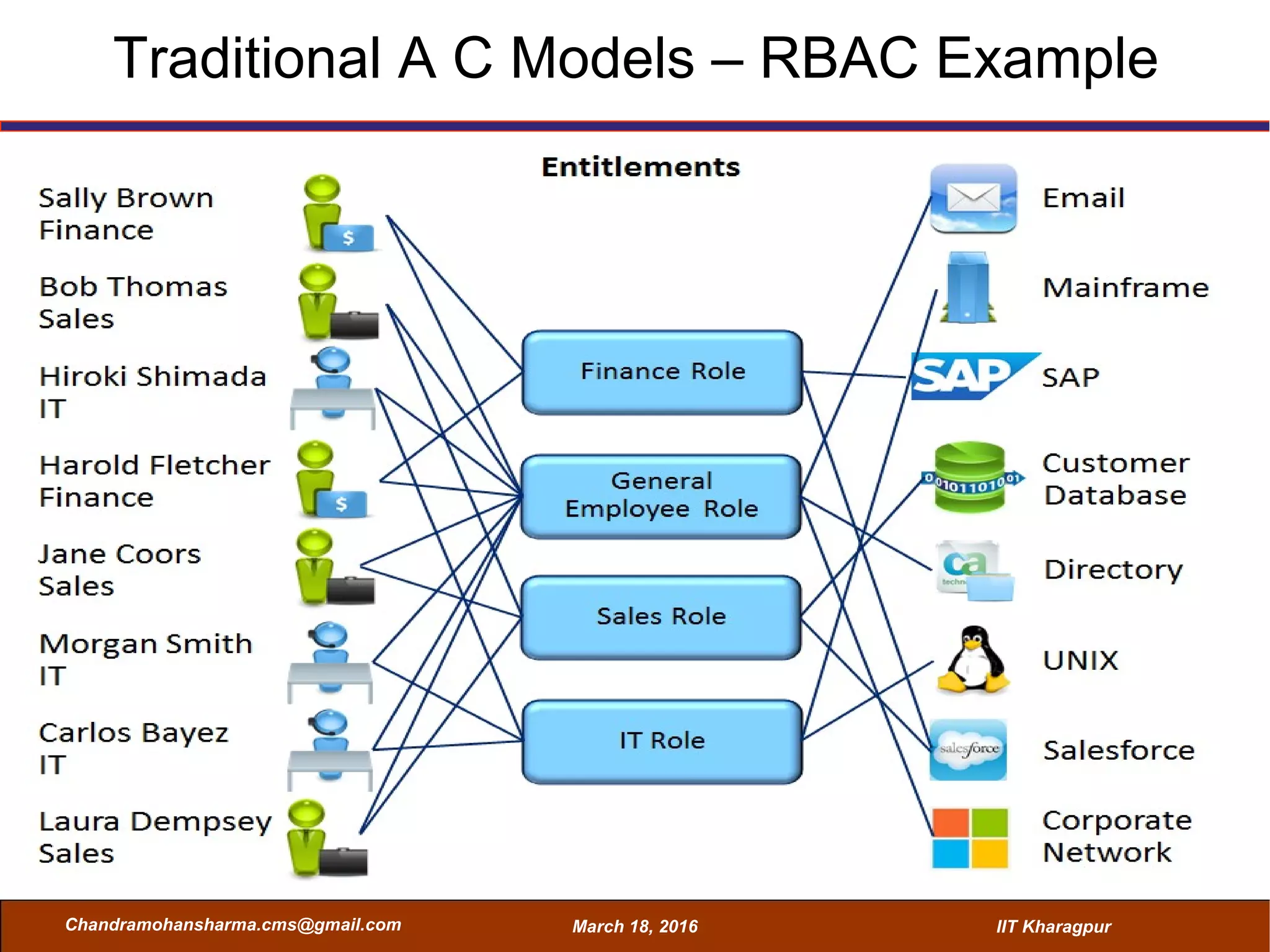
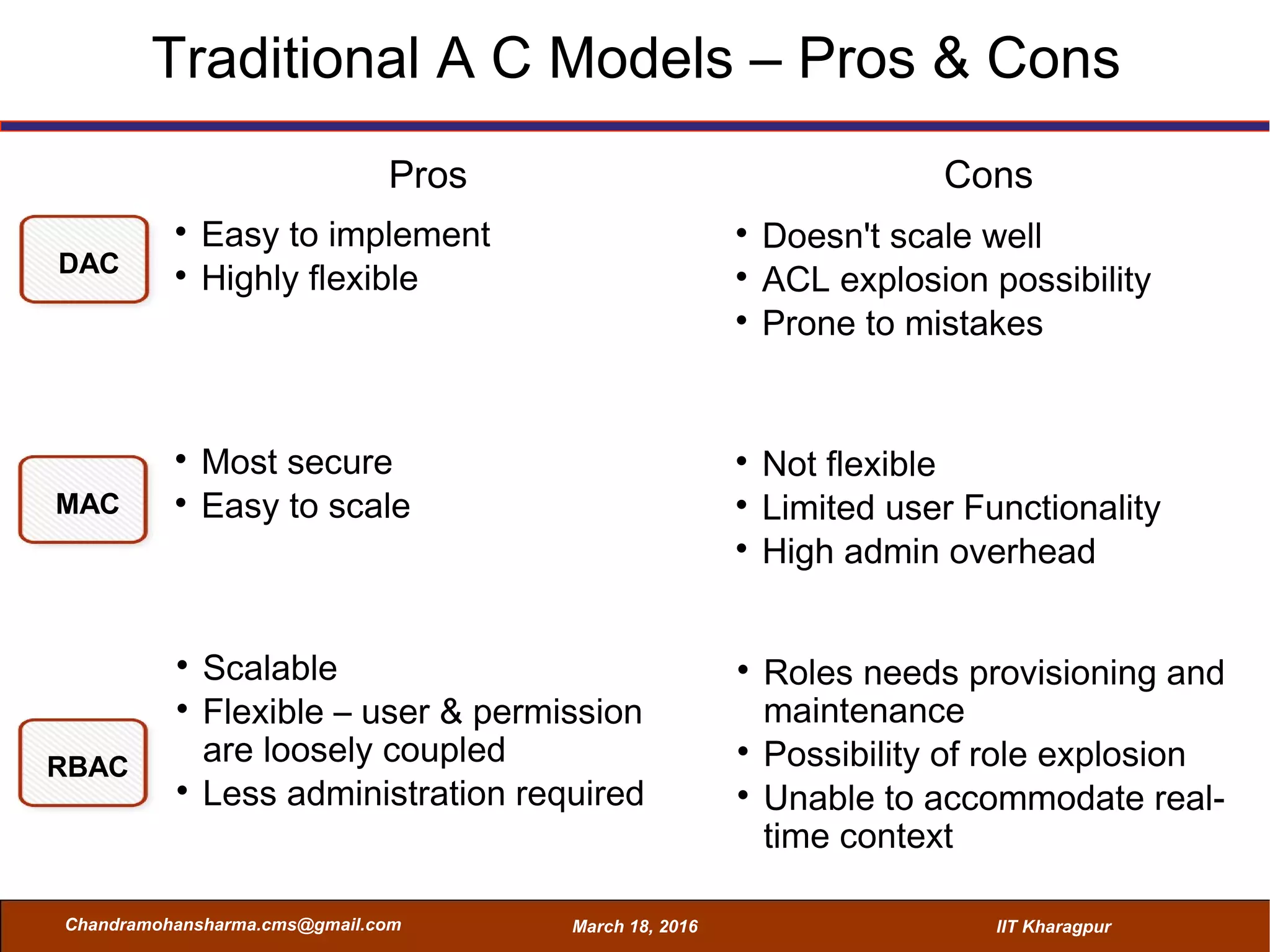
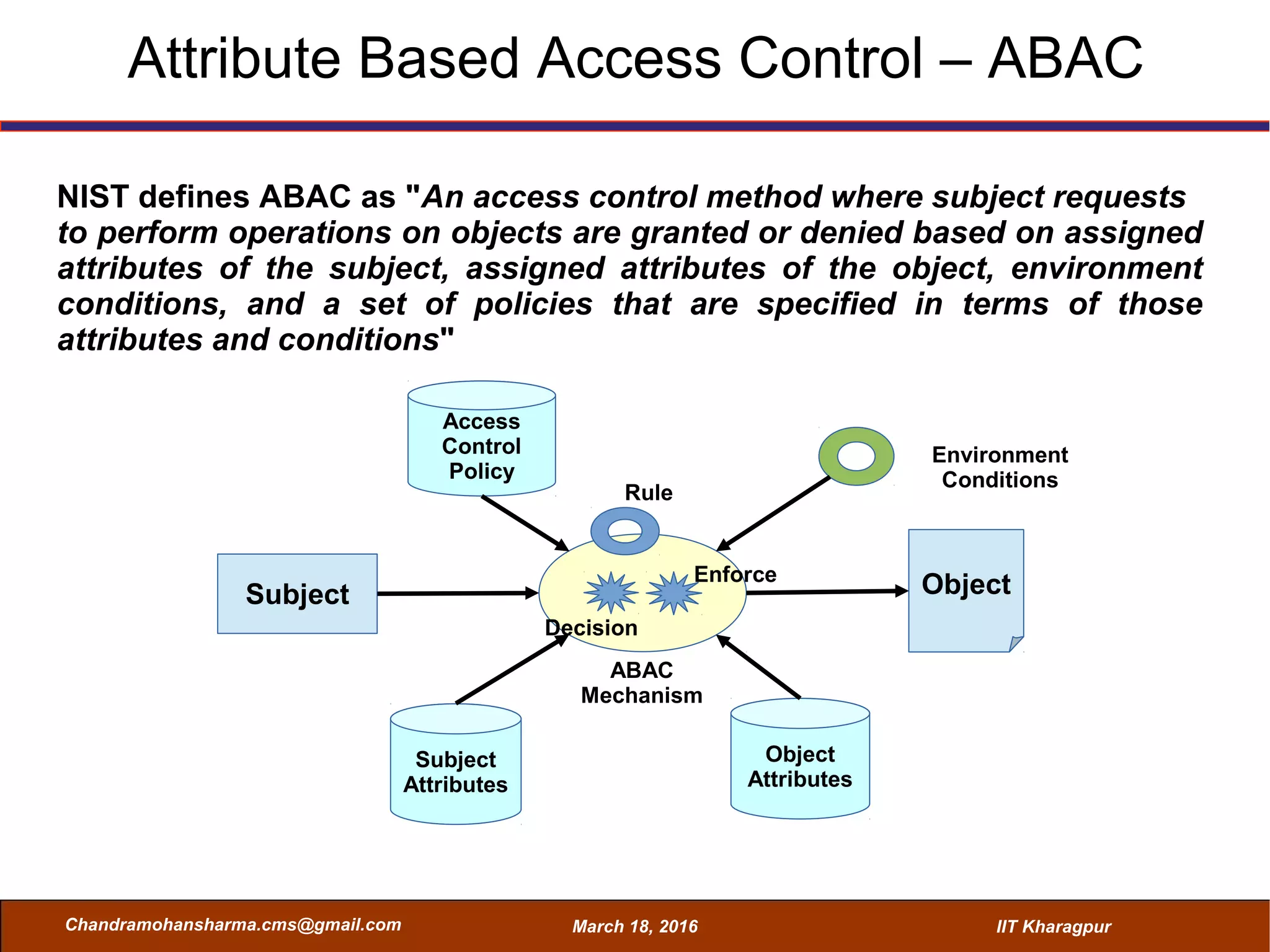
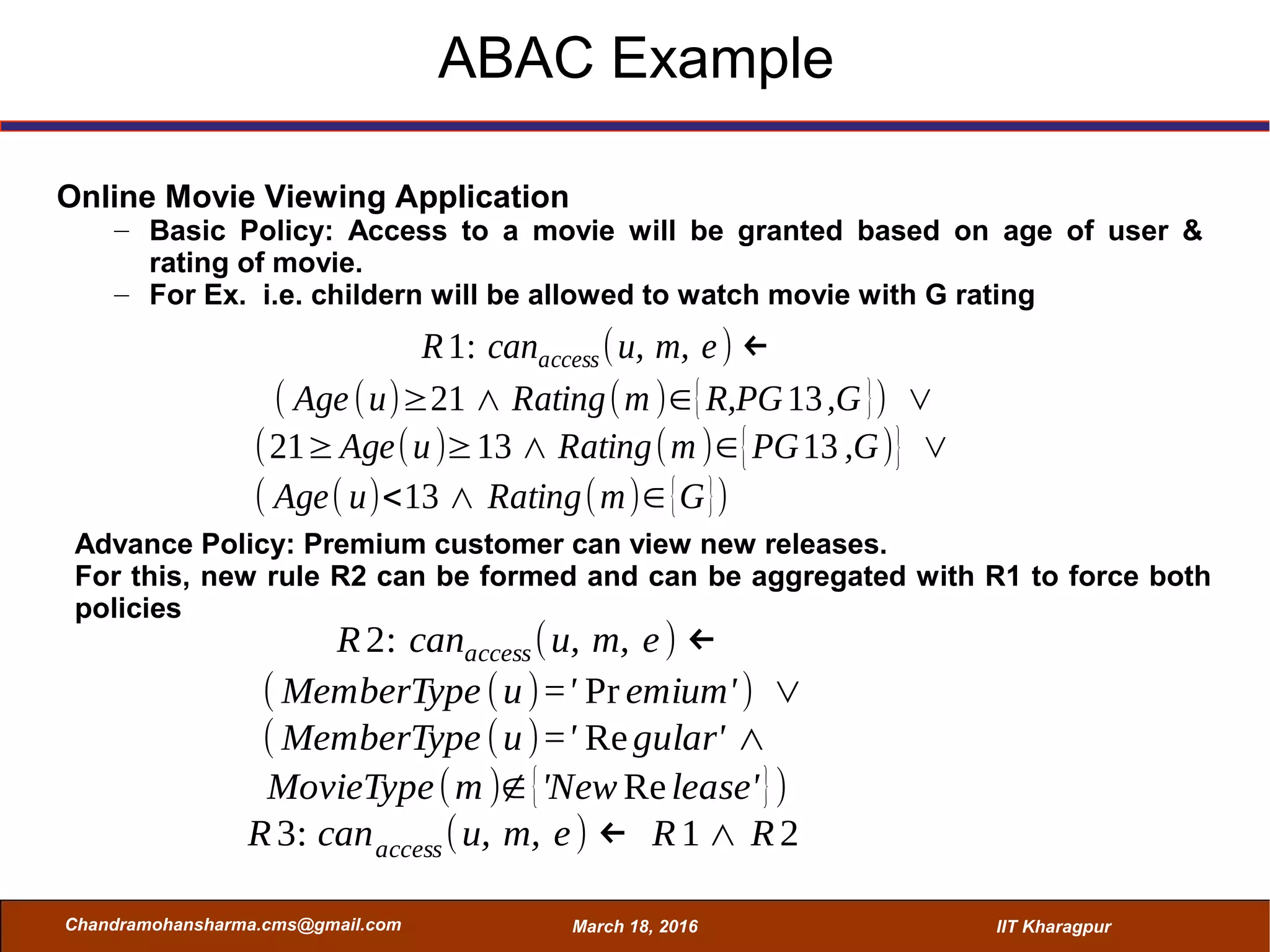
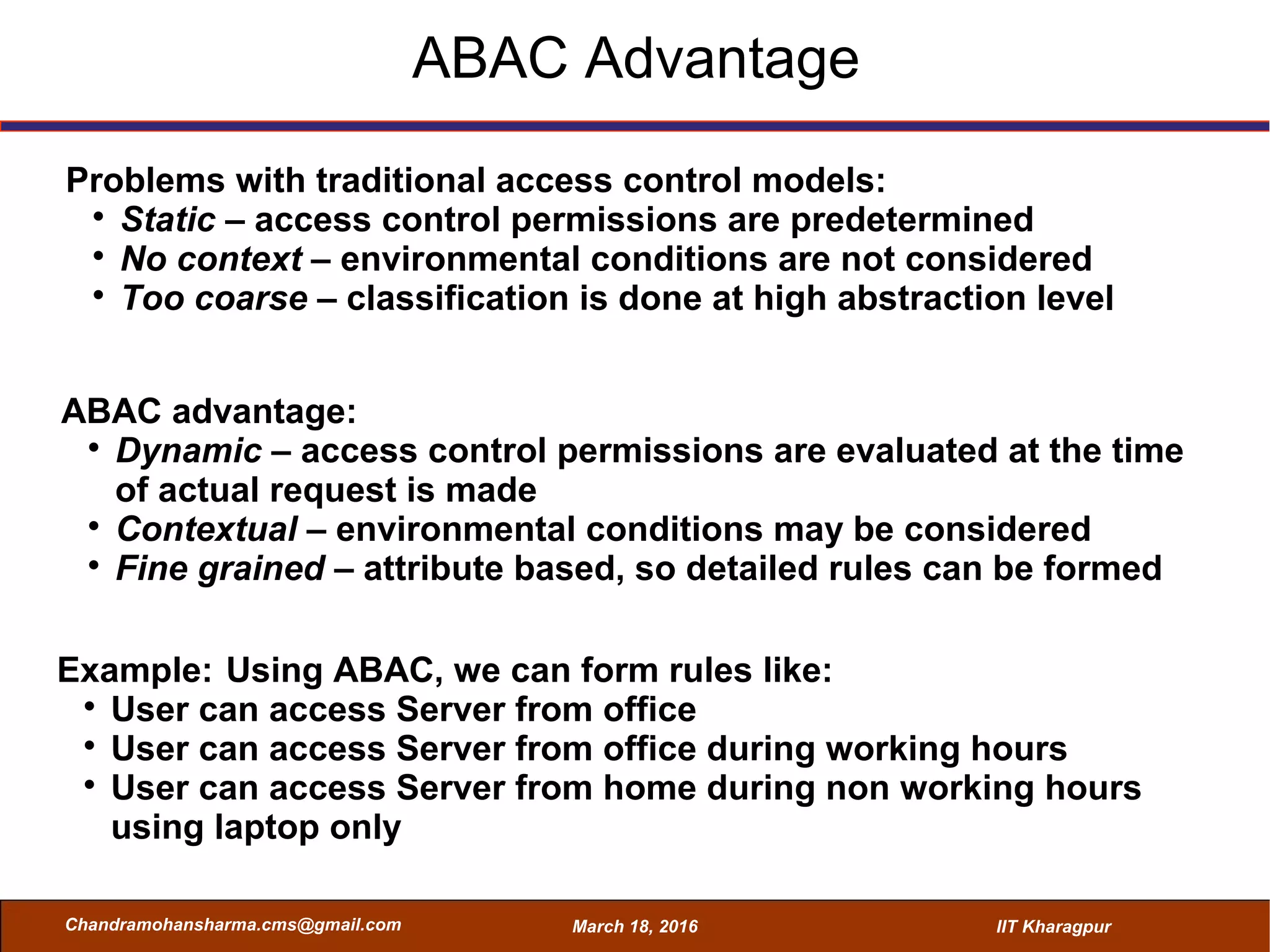
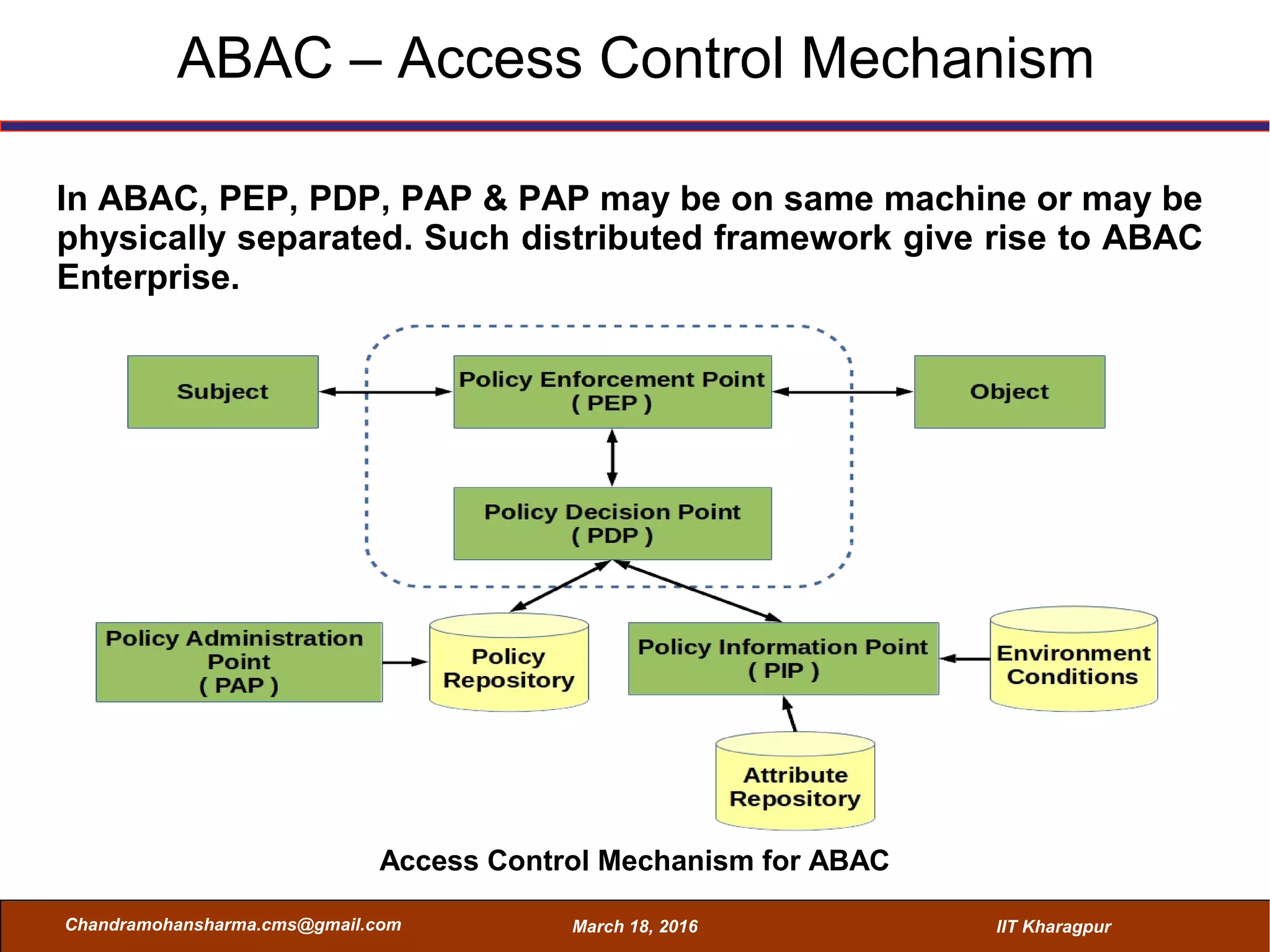
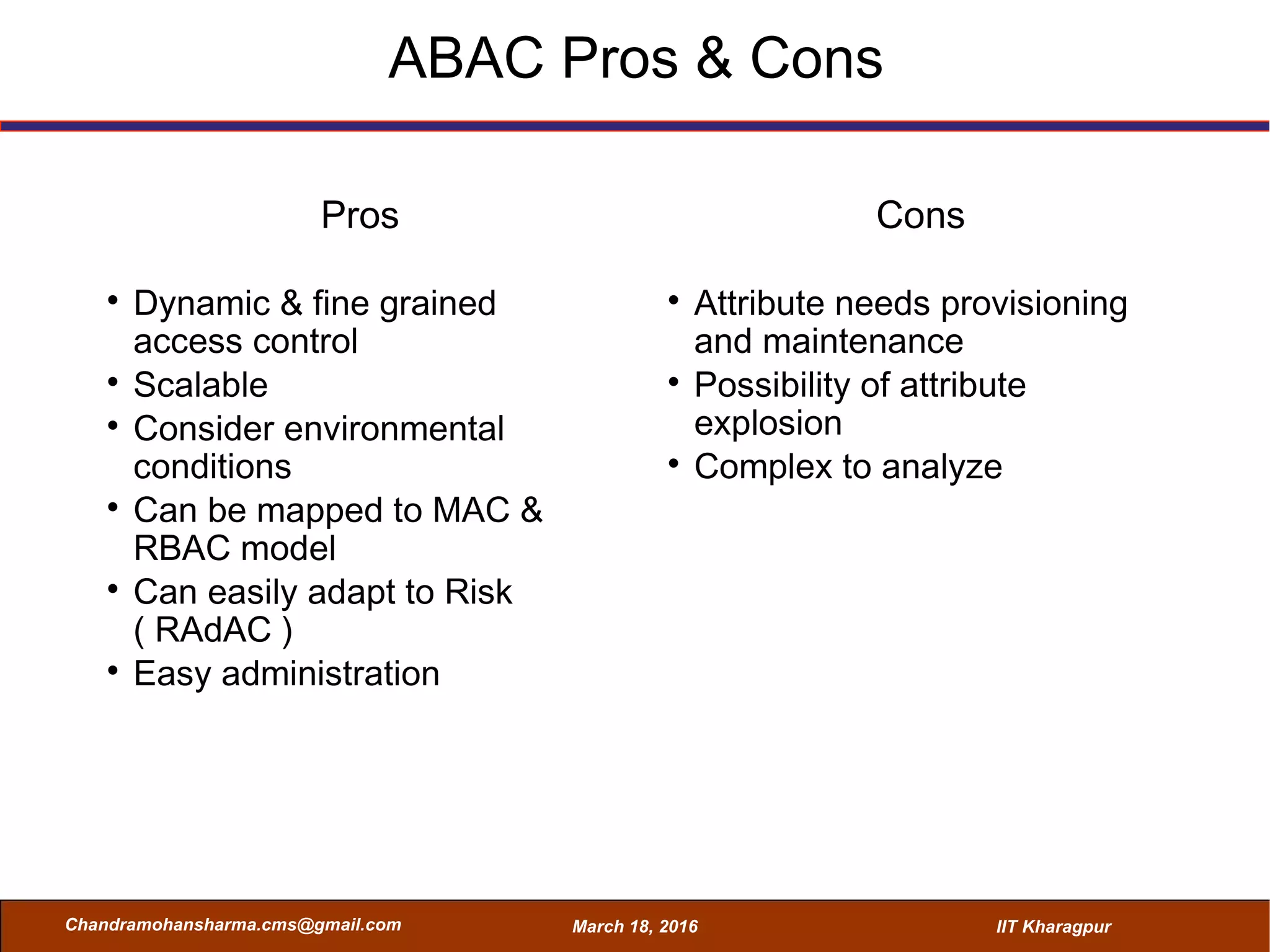
The seminar on Attribute-Based Access Control (ABAC) discussed various access control mechanisms including Discretionary Access Control (DAC), Mandatory Access Control (MAC), and Role-Based Access Control (RBAC), emphasizing their characteristics and limitations. ABAC, which allows dynamic, fine-grained access permissions based on attributes and environmental conditions, is gaining traction as a flexible and scalable model in comparison to traditional methods. Key advantages of ABAC include its ability to adapt to real-time contexts and its detailed rule formation, while challenges involve the need for attribute management and potential complexity.