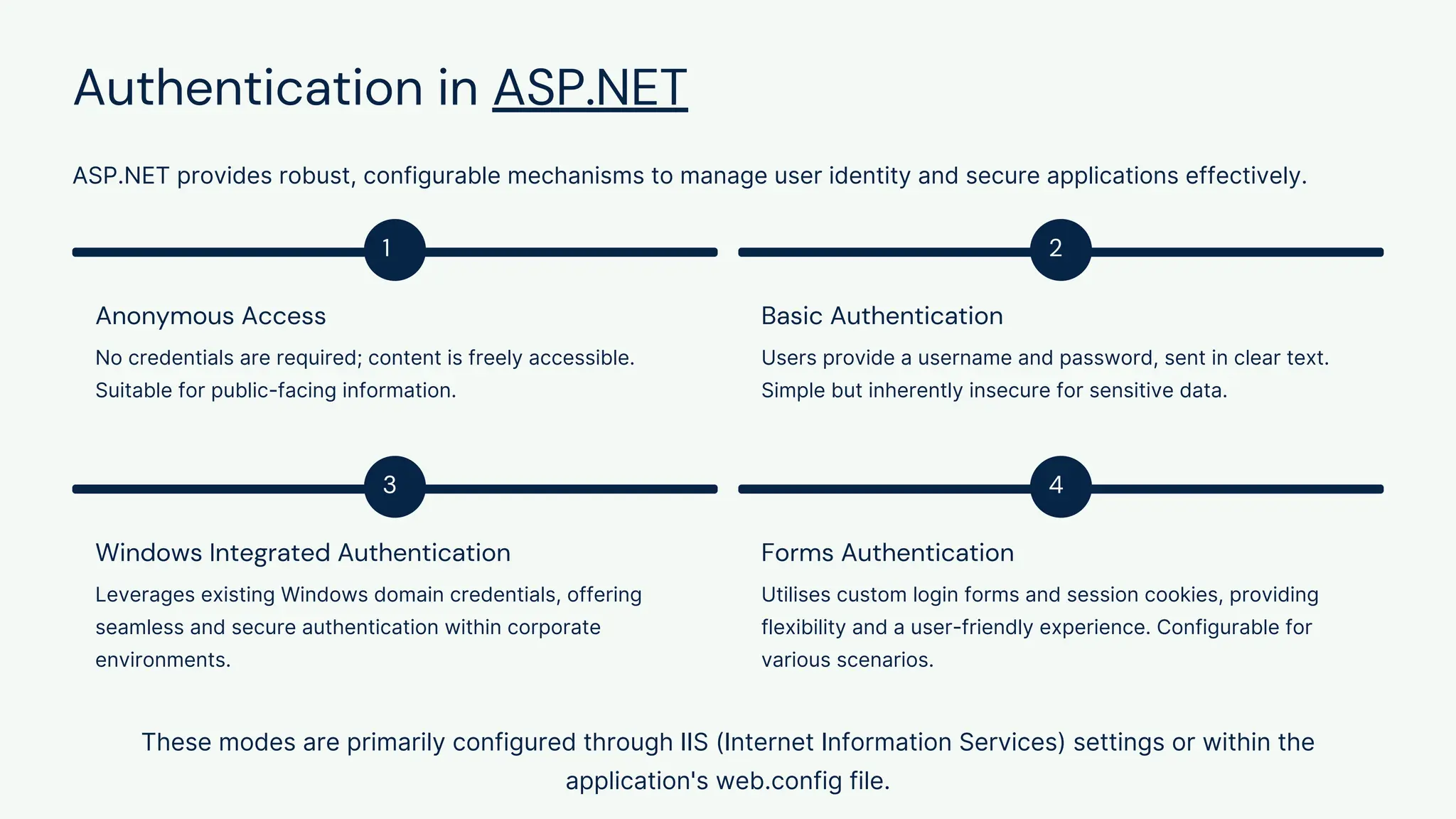
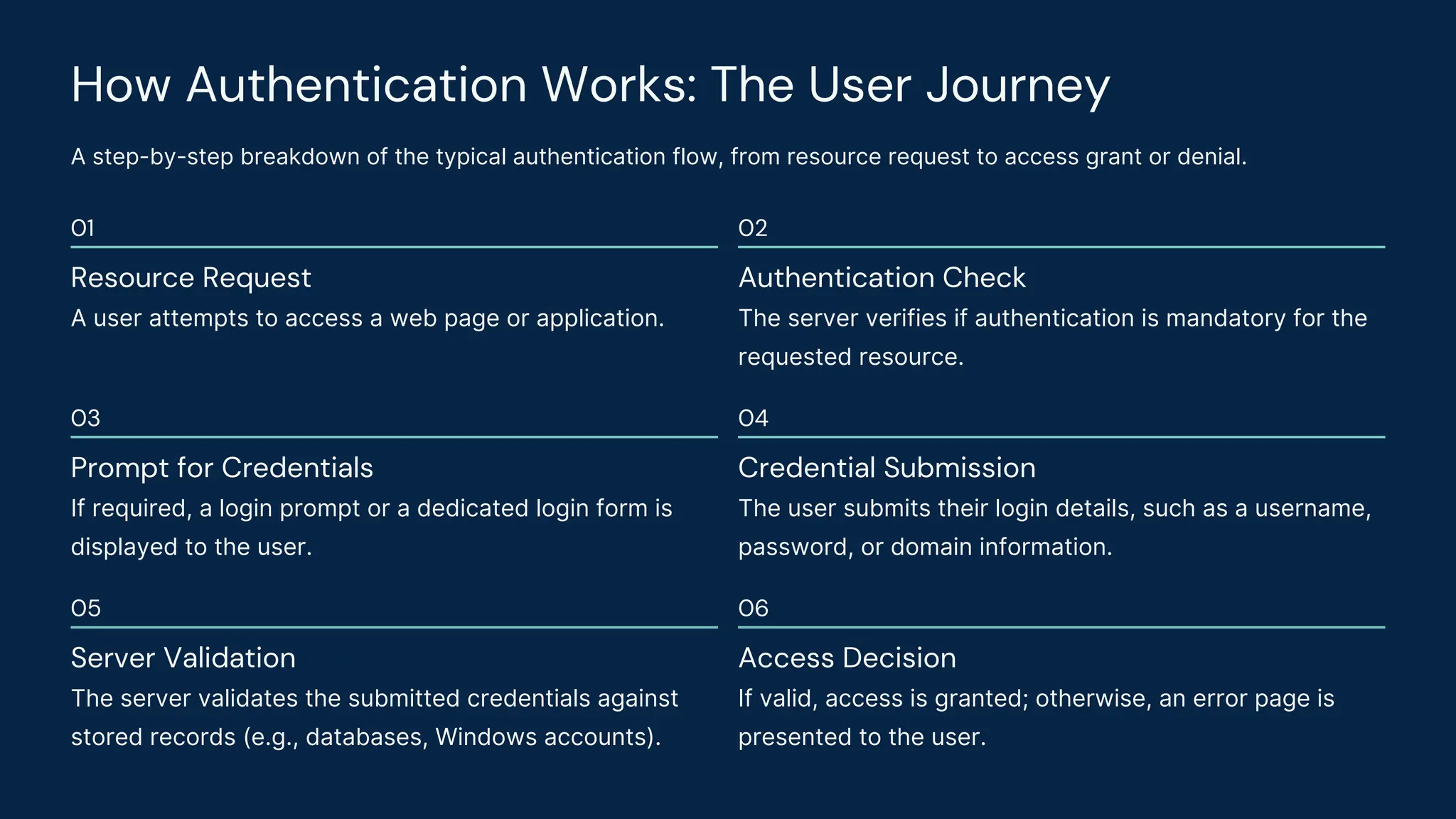
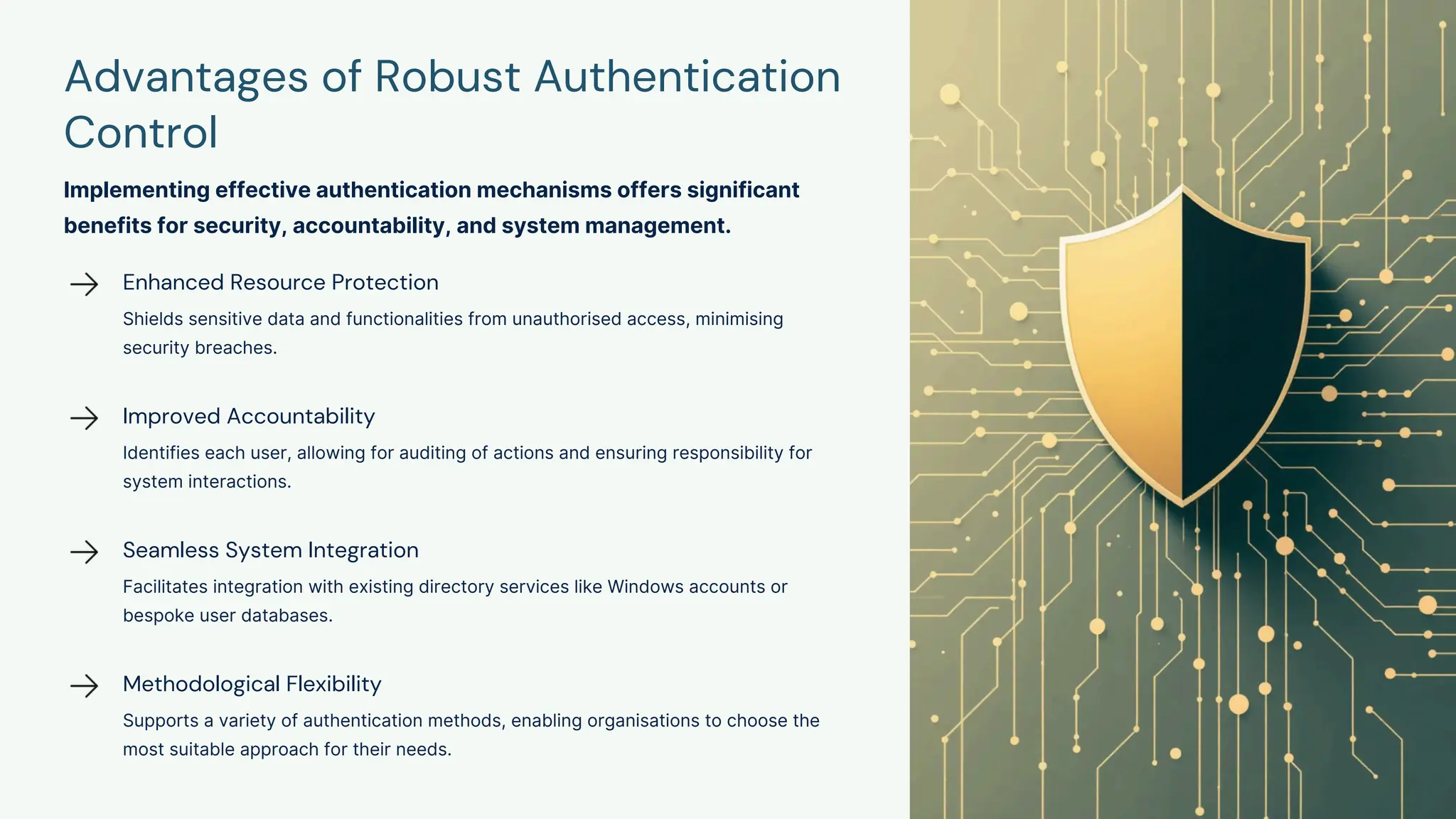
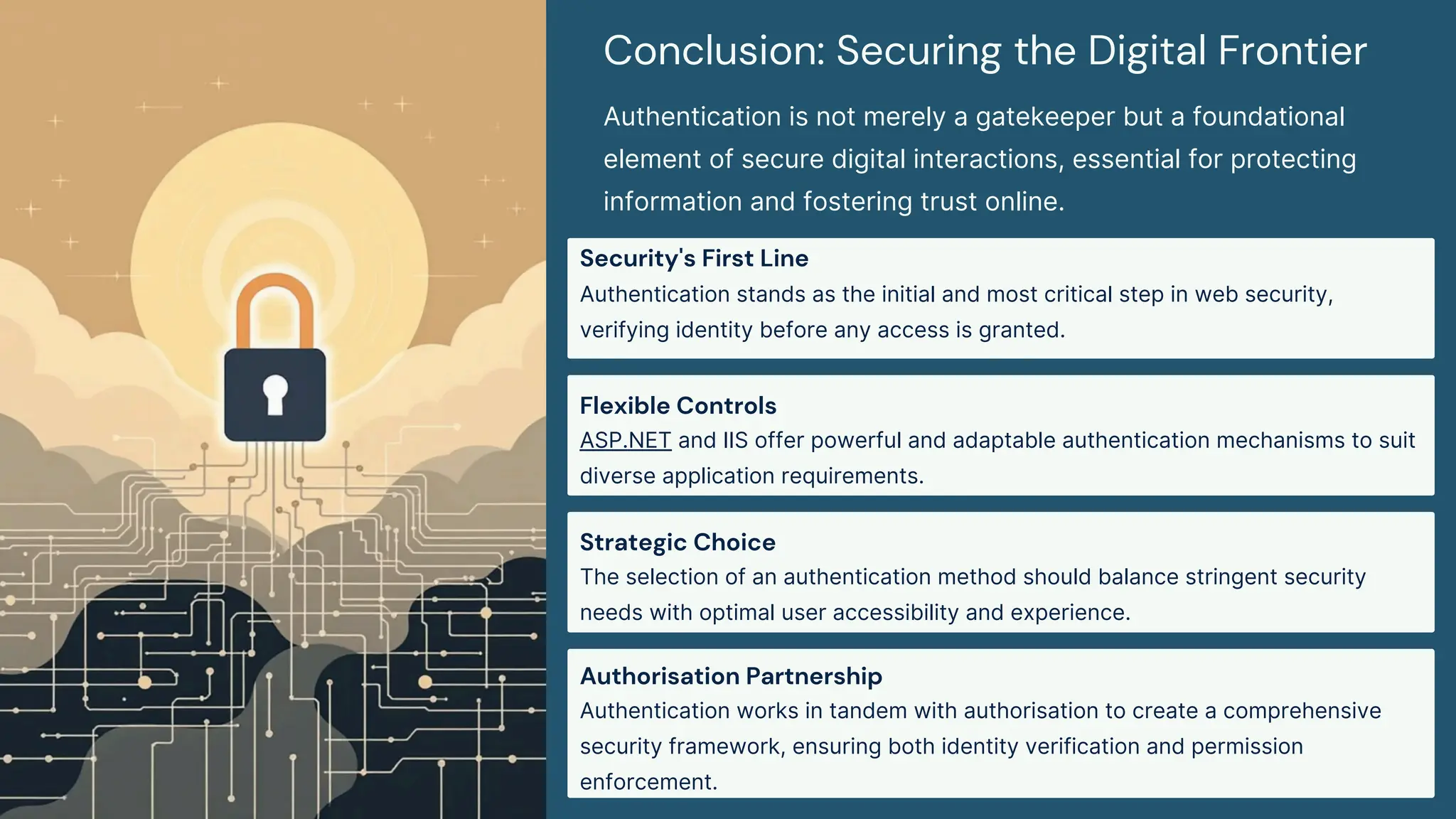
Authenticaiton Control Authenticaiton Control Authenticaiton Control Authenticaiton ControlAuthenticaiton Control Authenticaiton Control Authenticaiton Control Authenticaiton Control Authenticaiton ControlAuthenticaiton Control Authenticaiton Control Authenticaiton Control Authenticaiton Control Authenticaiton ControlAuthenticaiton Control Authenticaiton Control Authenticaiton Control Authenticaiton Control Authenticaiton ControlAuthenticaiton Control