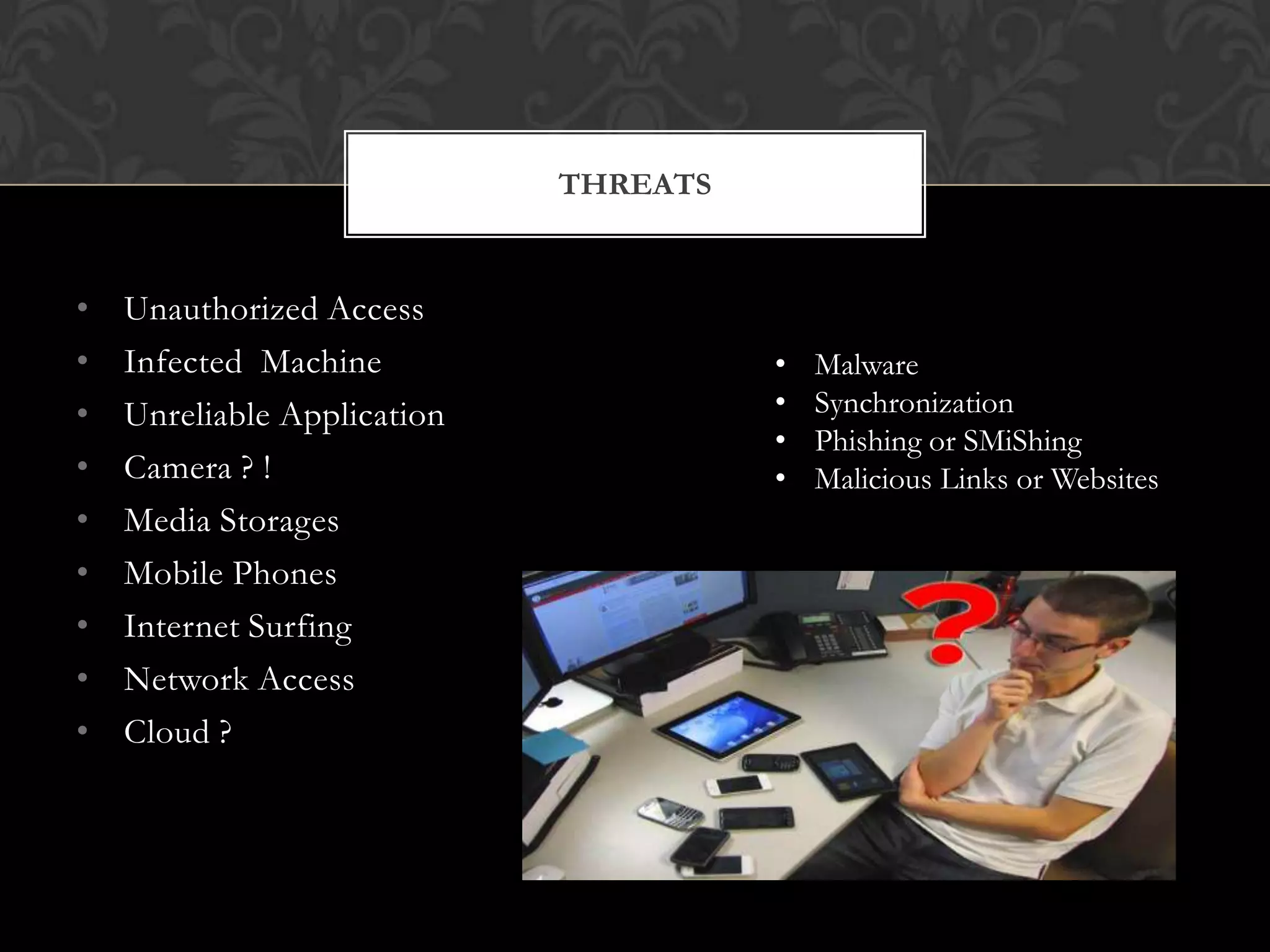
The document discusses BYOD (Bring Your Own Device) and its implications for mobile security, highlighting potential threats, benefits, and challenges associated with allowing employees to use personal devices for work. It outlines a four-step approach for designing a BYOD strategy that includes understanding business needs, creating protocols, defining legal rights, and addressing security concerns. The document also touches upon mobile hacking techniques and emphasizes the importance of data encryption and securing applications on personal devices.


















![MOBILE HACKING DEVICE HACKING
TECHNIQUES DEMO: ANDROID PHONE
• Network Spoofer / Dsicovery
[Need root access]
• Shark for root ( like Wireshark on PC) [Need root access]
•
•
•
•
•
•
•
TcpDump
Ettercap
dSploit
dDoS tool for Mobile Devices
Bluetooth Cloning
DroidShip
etc](https://image.slidesharecdn.com/byodandmobilesecurity-3-18am12022014version-140215015603-phpapp02/75/An-Introduction-on-Design-and-Implementation-on-BYOD-and-Mobile-Security-31-2048.jpg)