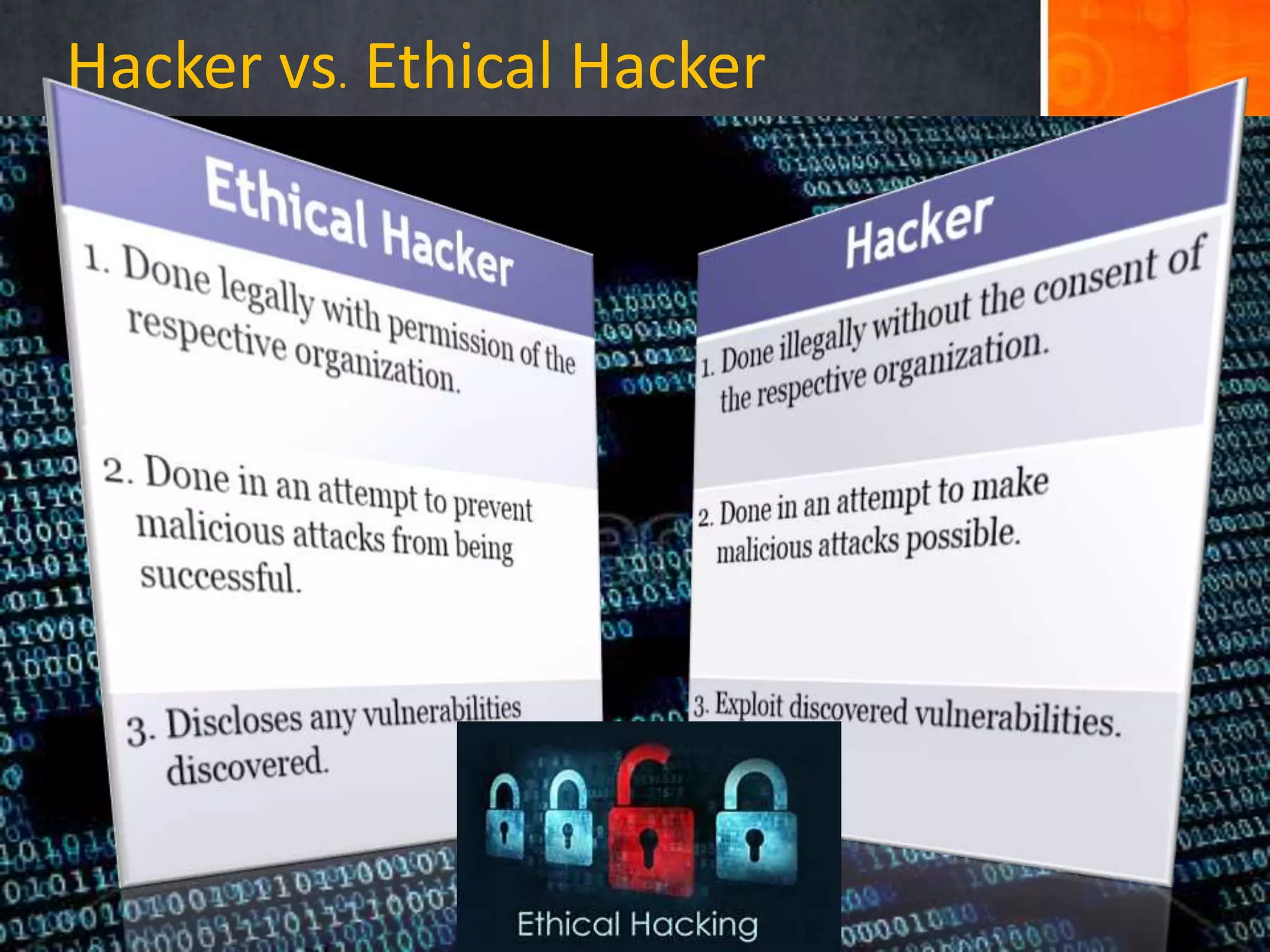
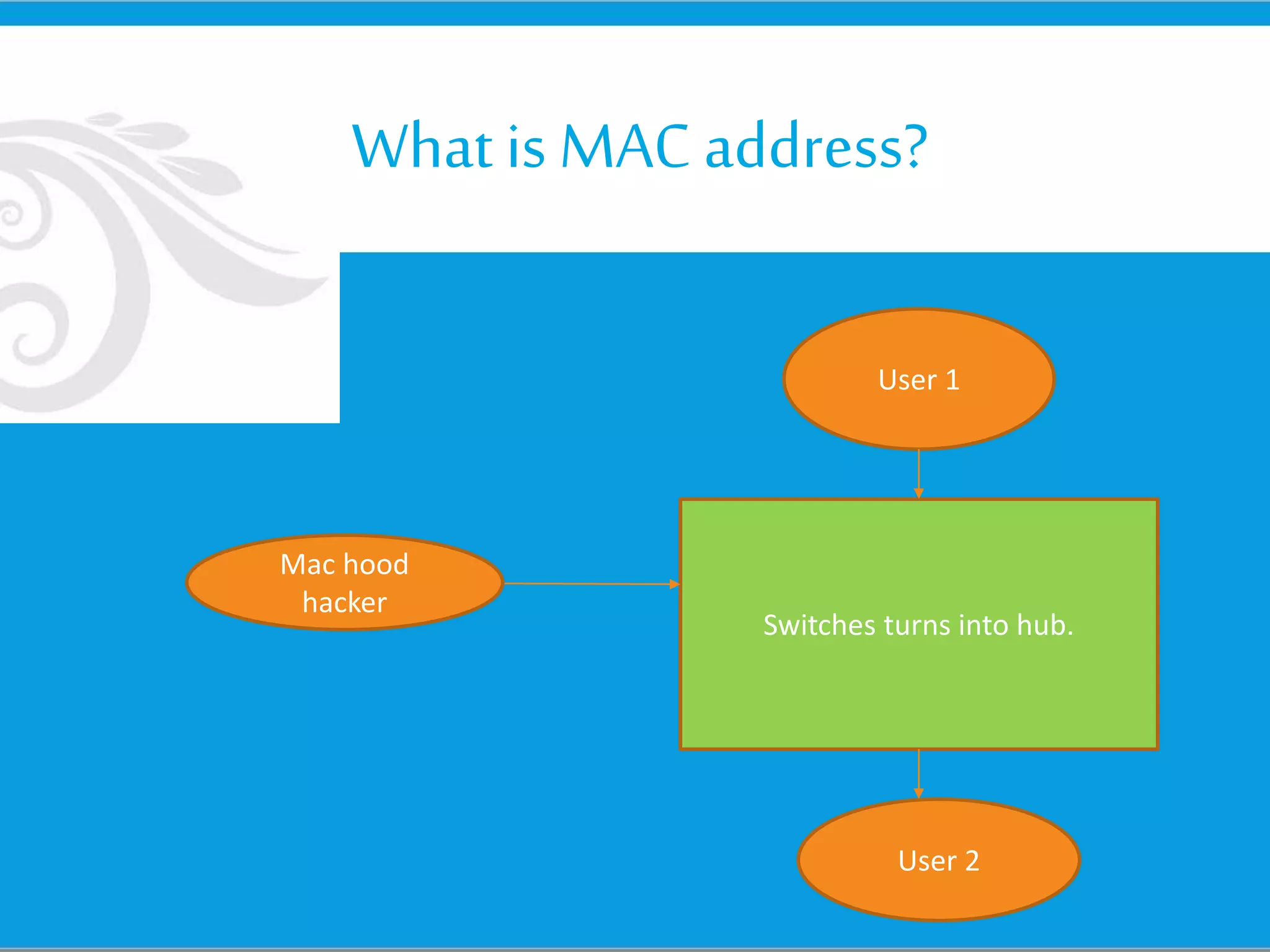
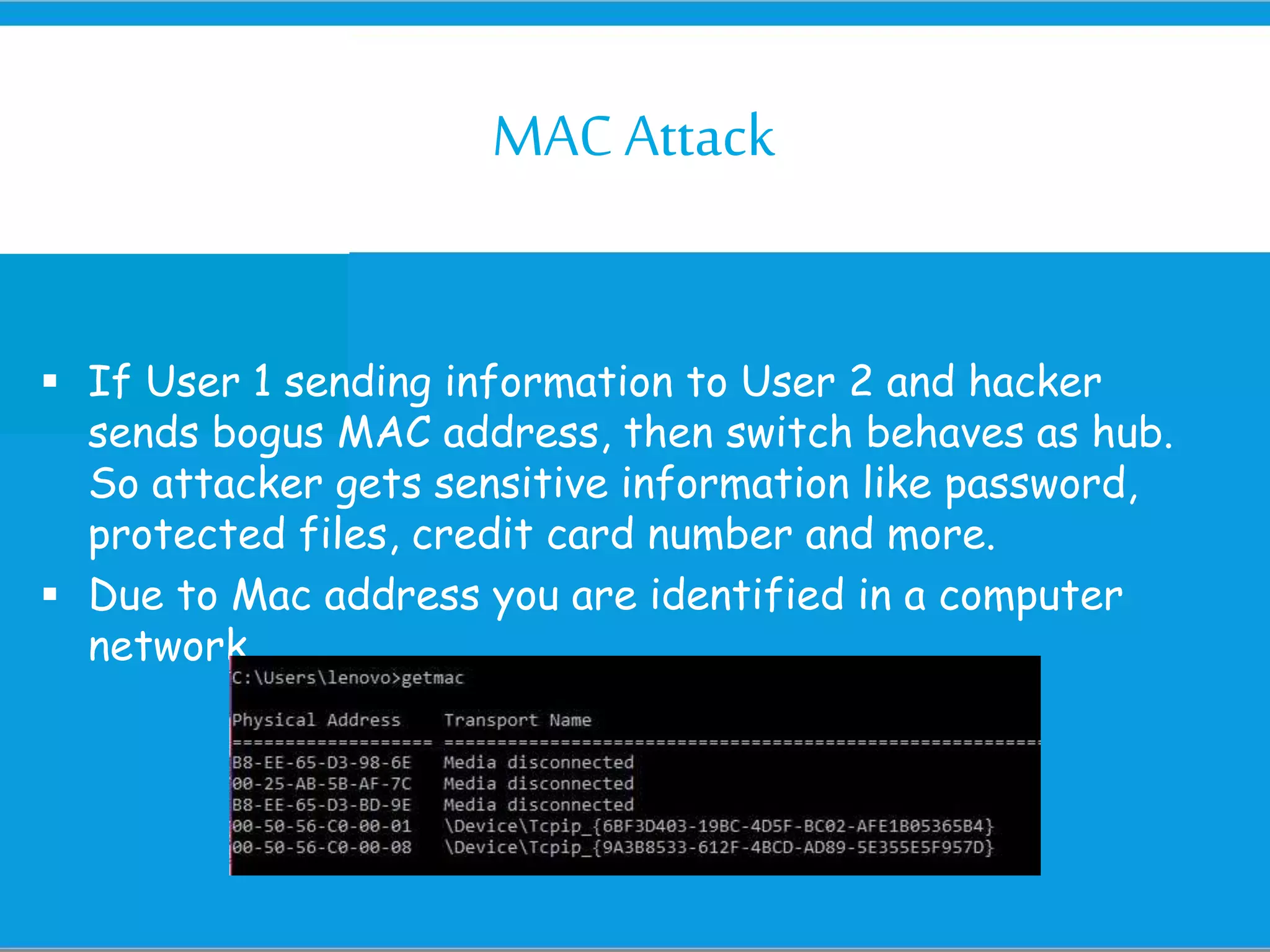
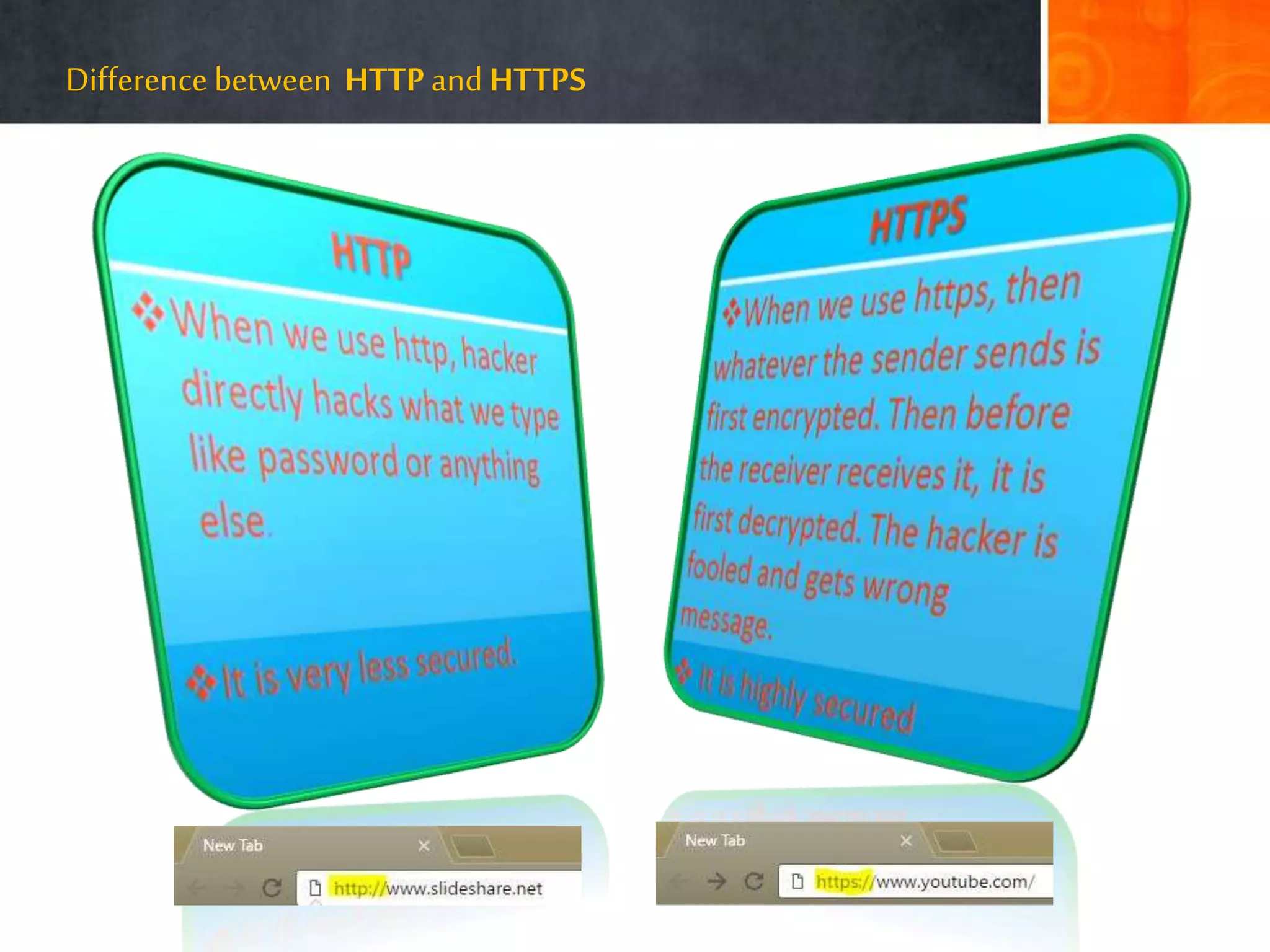
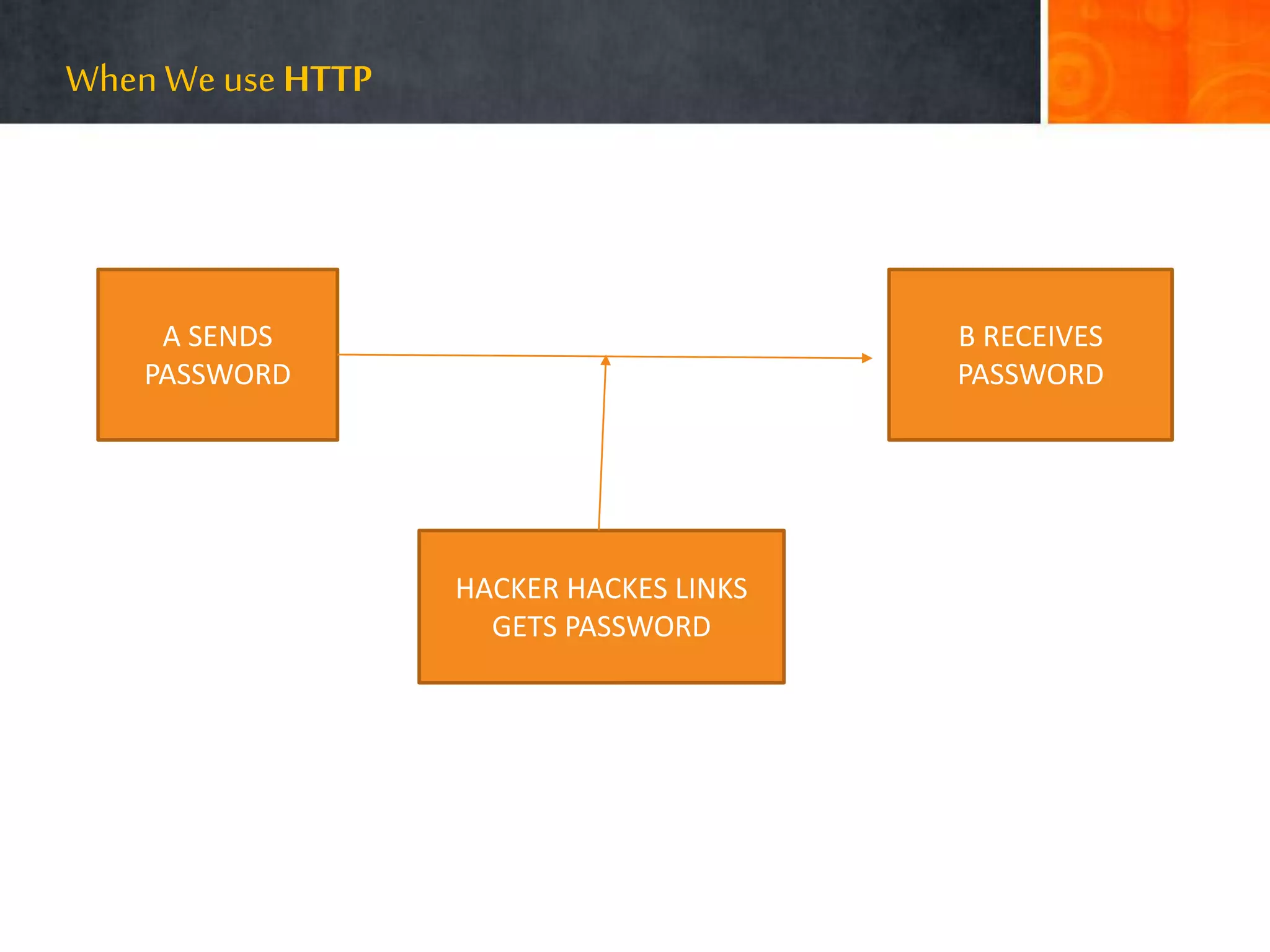
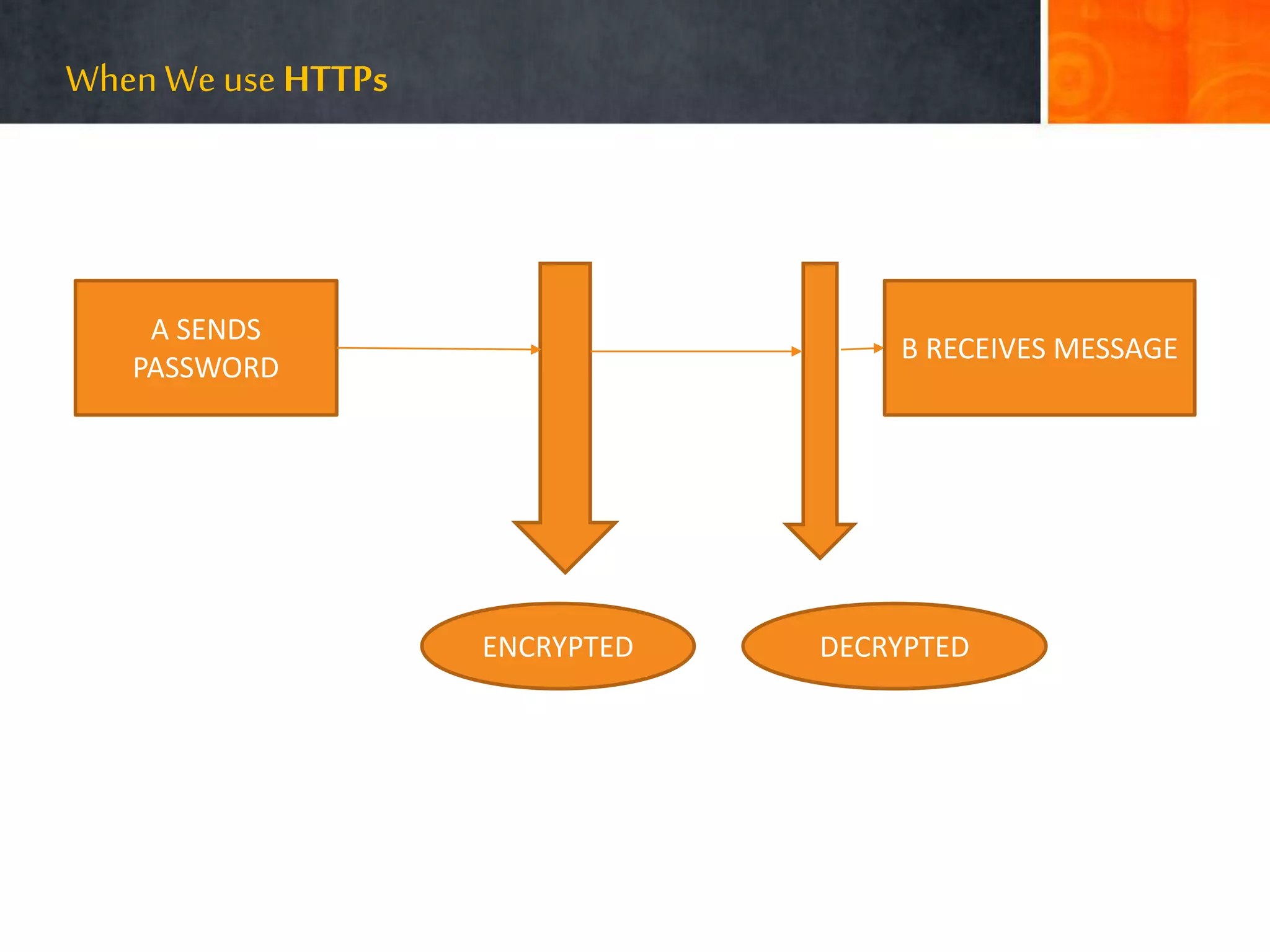
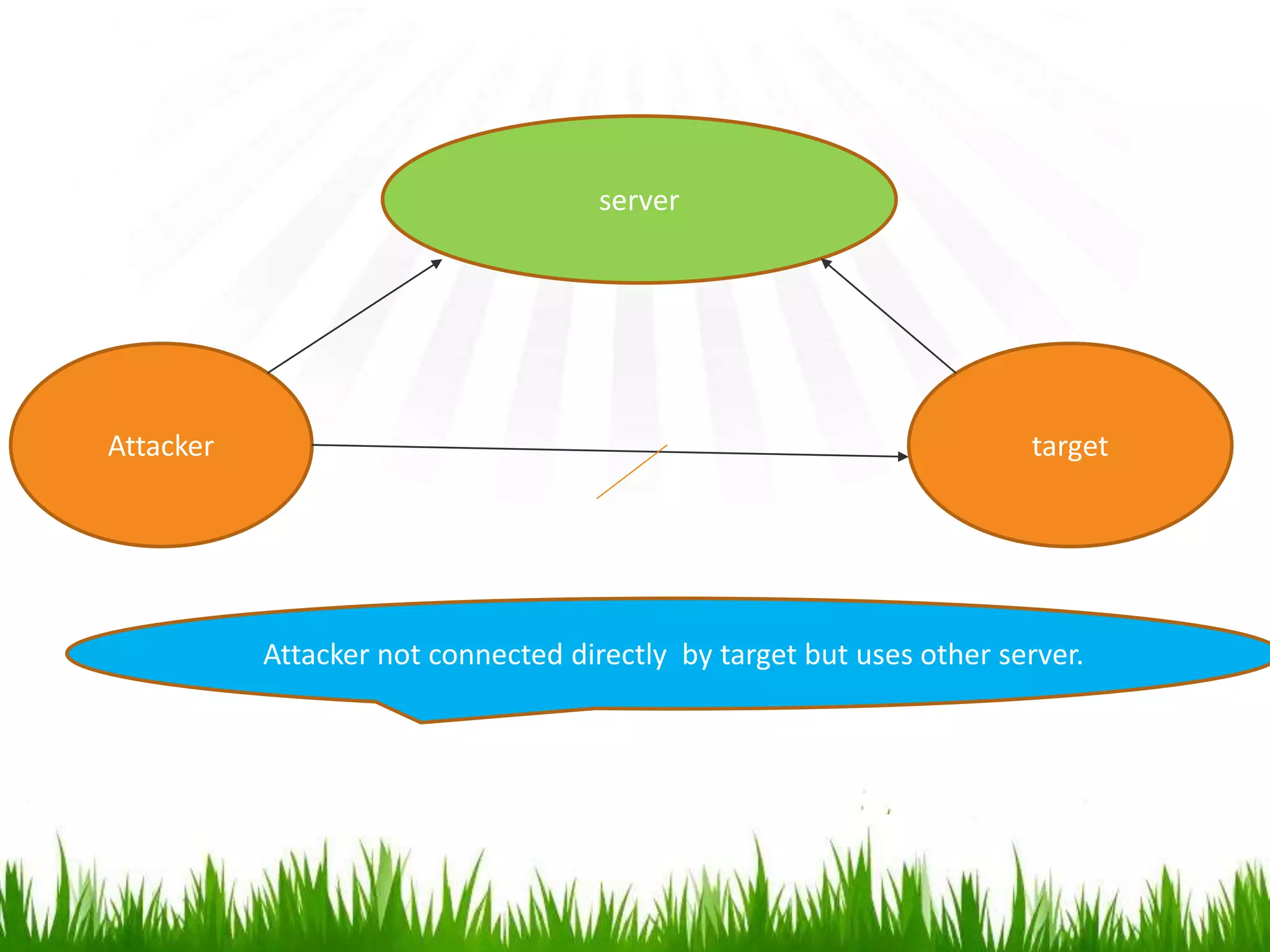
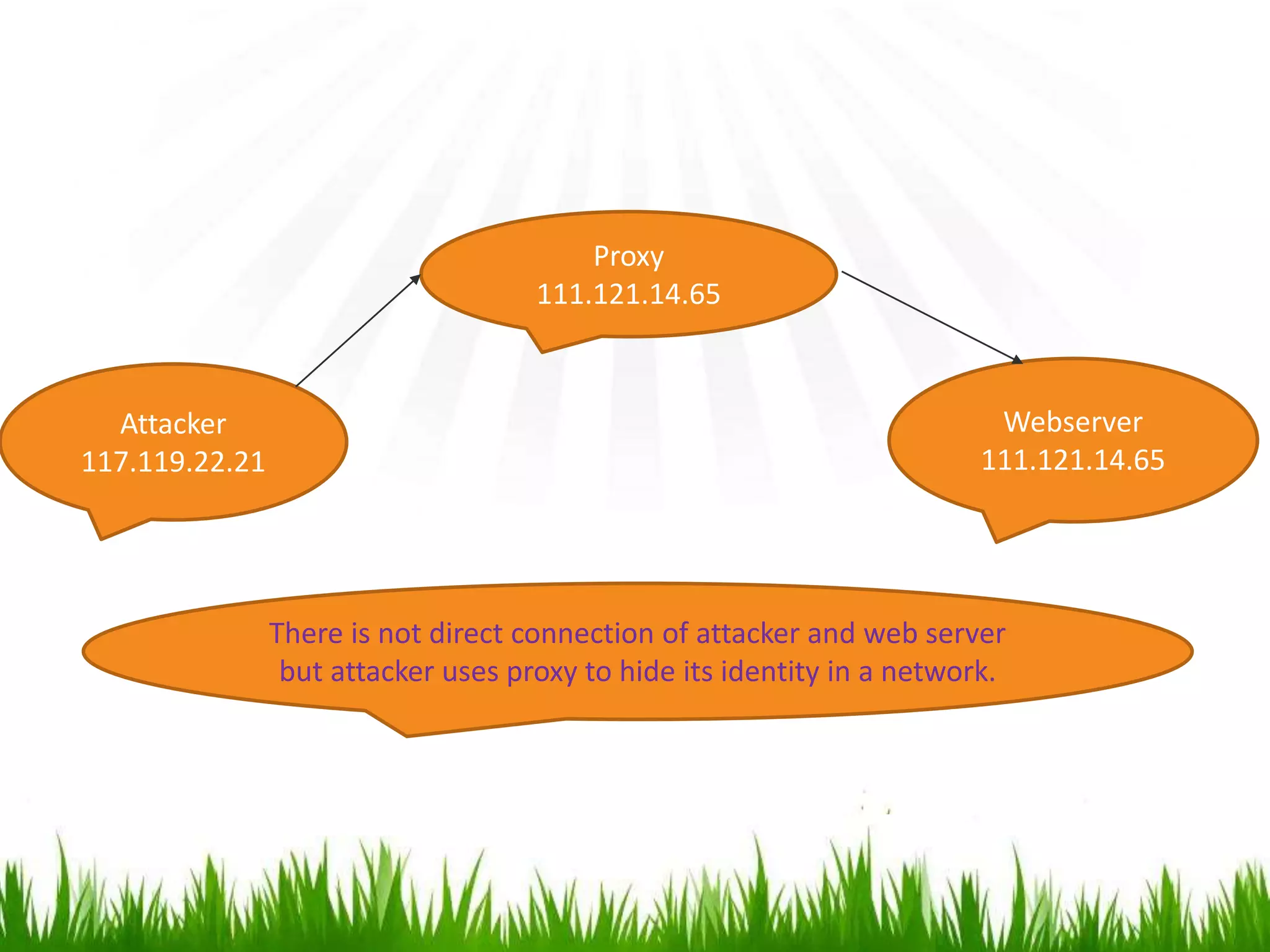
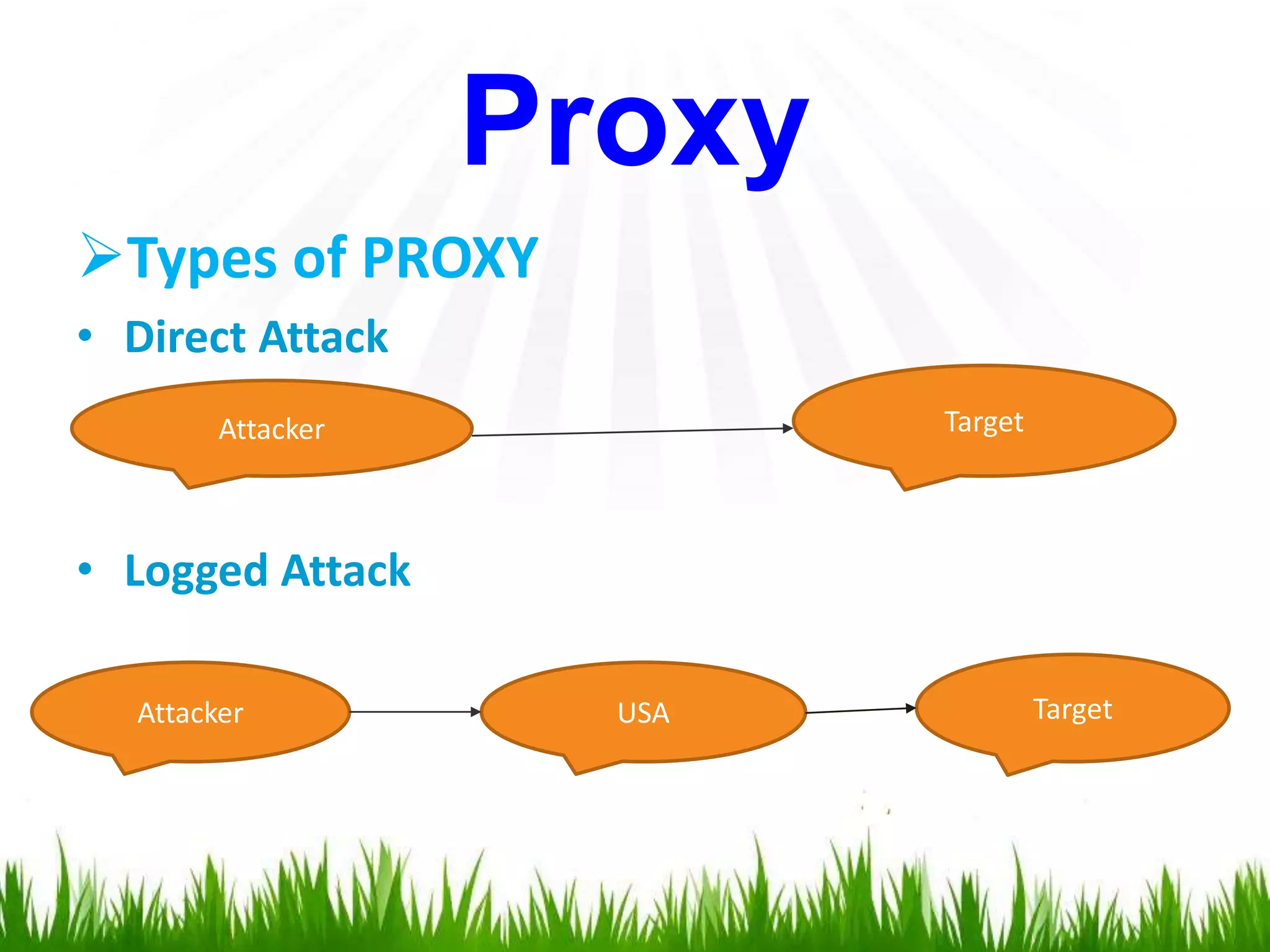
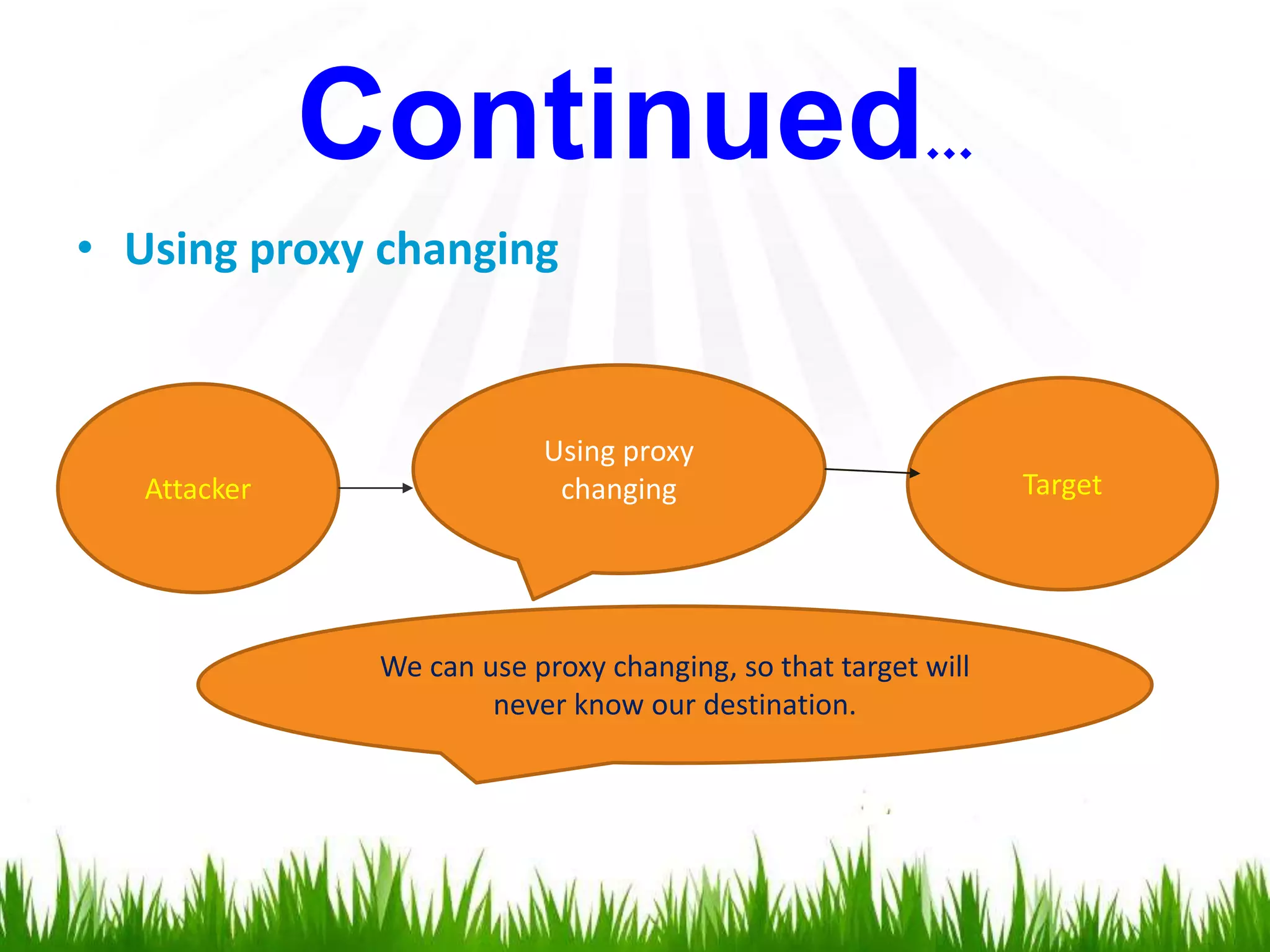
The document discusses hacking, defining hackers and exploring various motivations behind hacking, including fun, theft, and disruption. It highlights the role of ethical hackers and the skills required for a hacking career, along with potential job opportunities and salaries. Additionally, it covers social engineering tactics, IP addresses, MAC addresses, and the importance of security measures to protect against cyber threats.