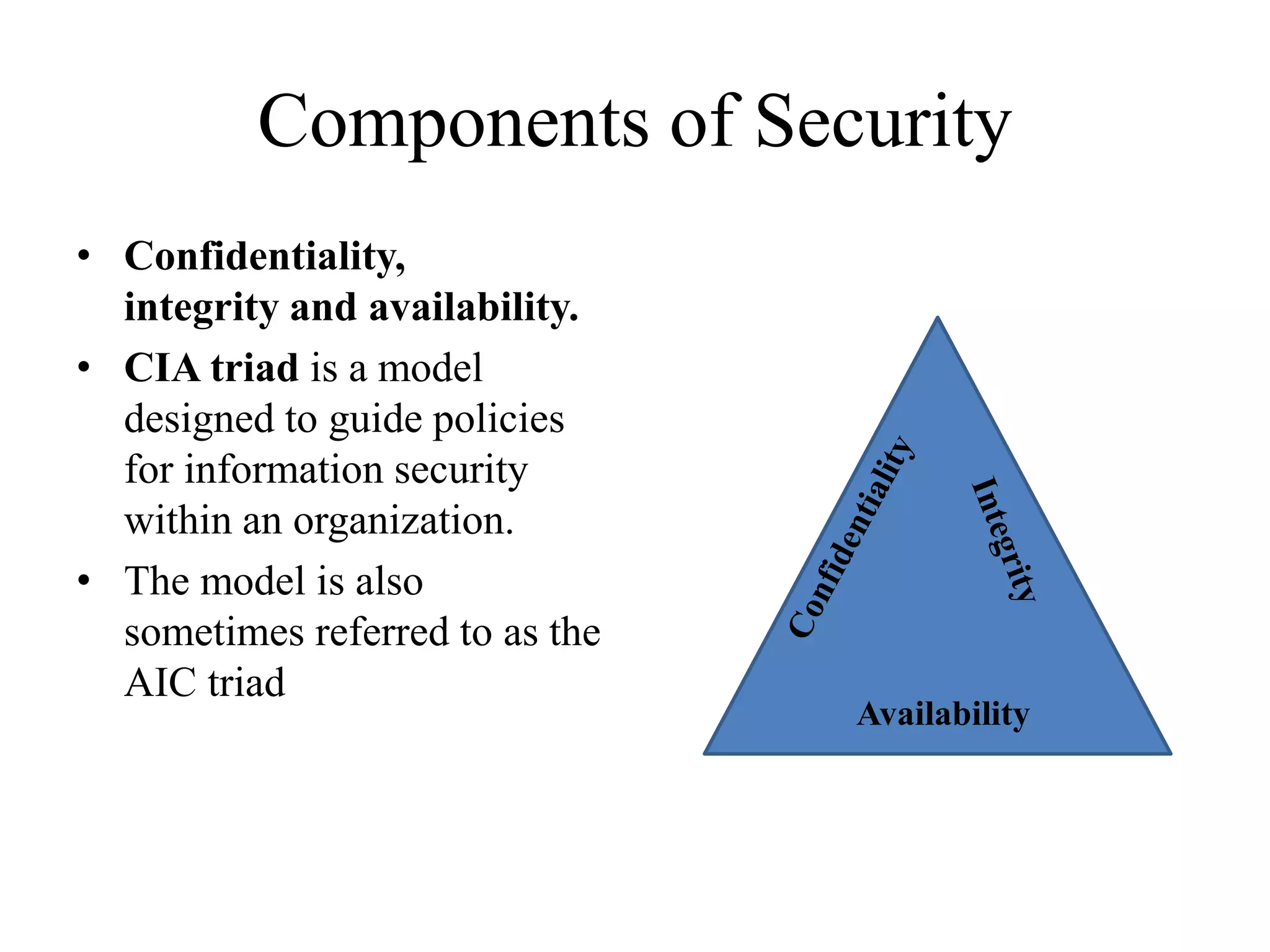
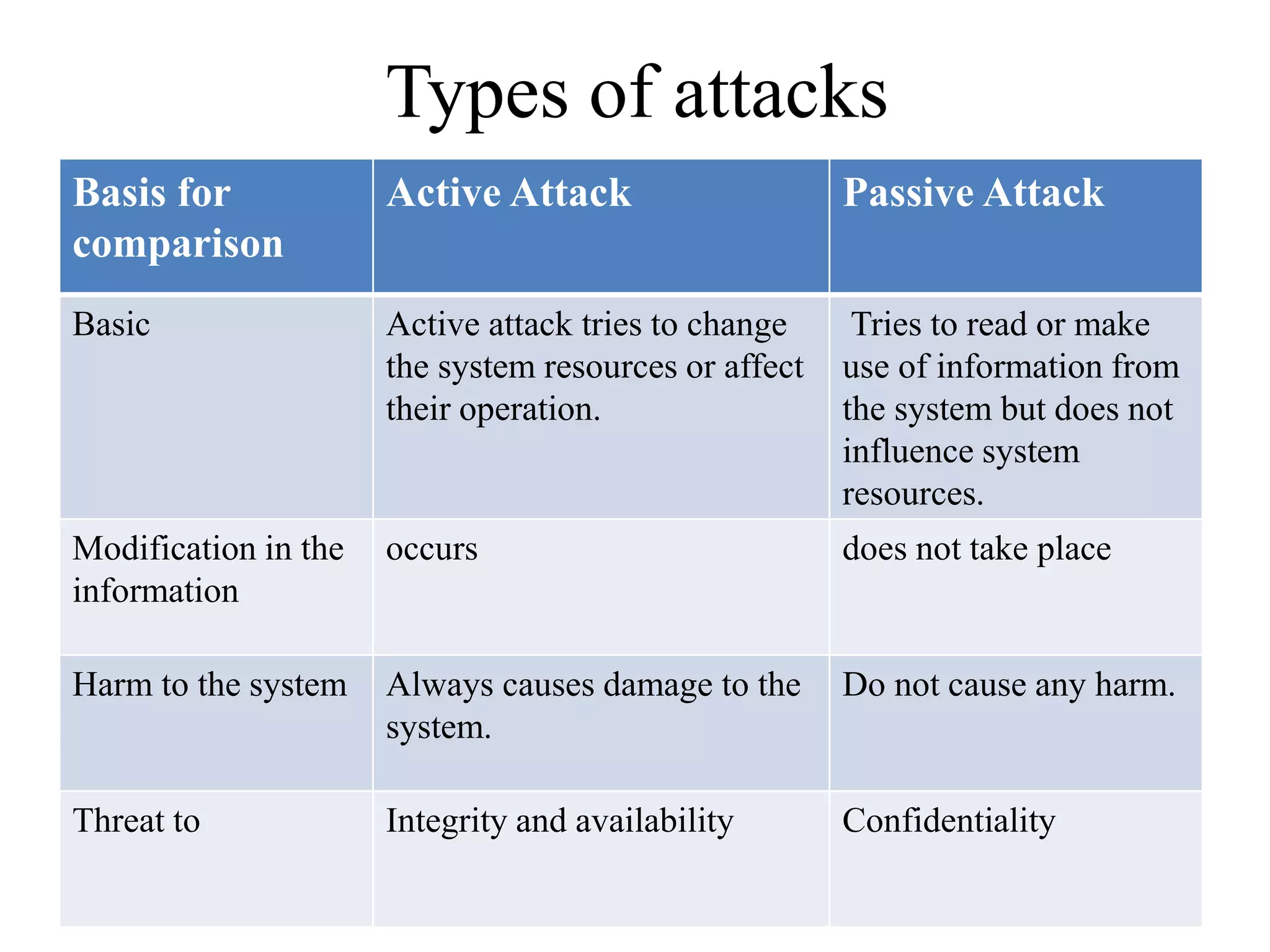
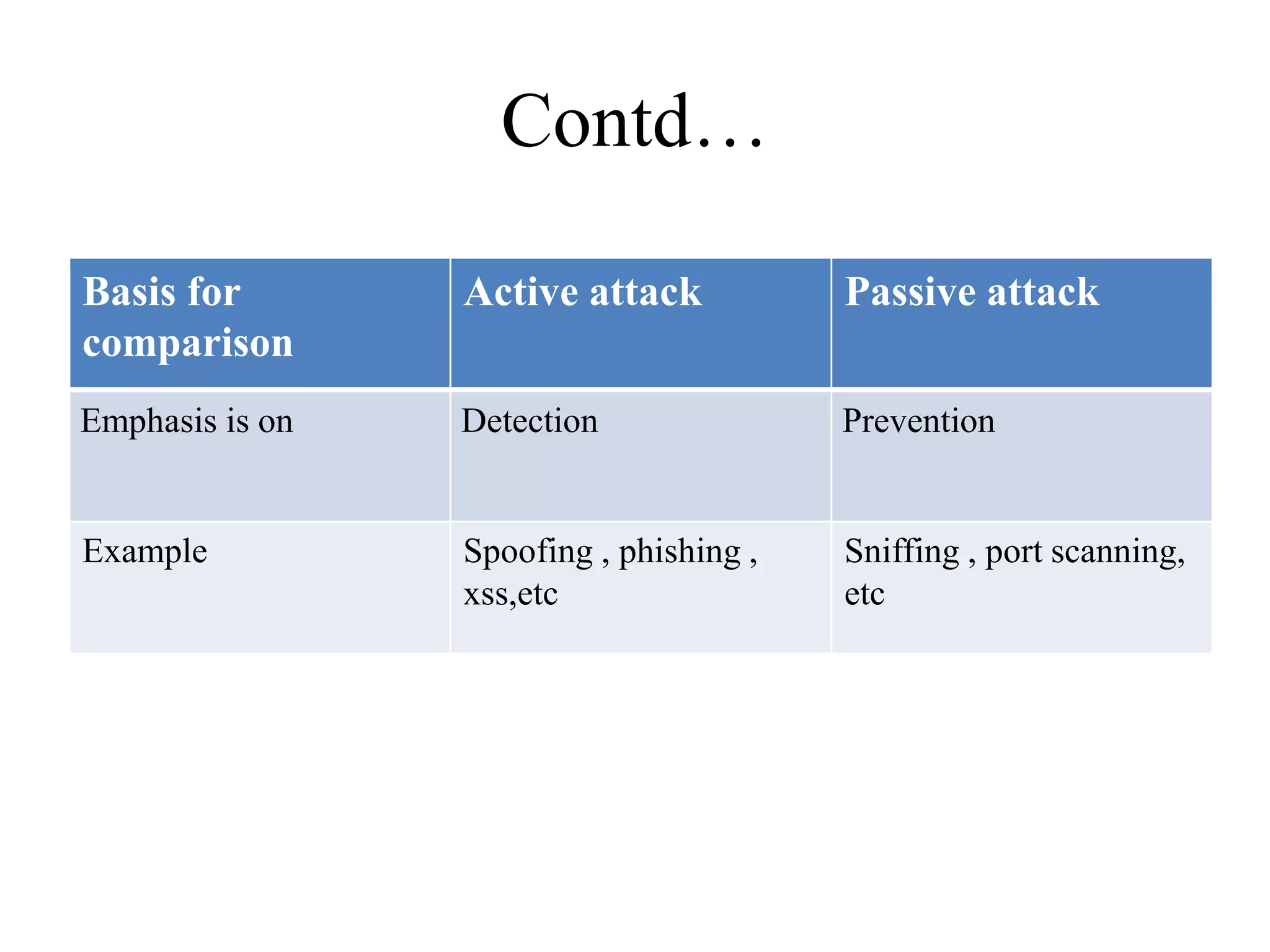
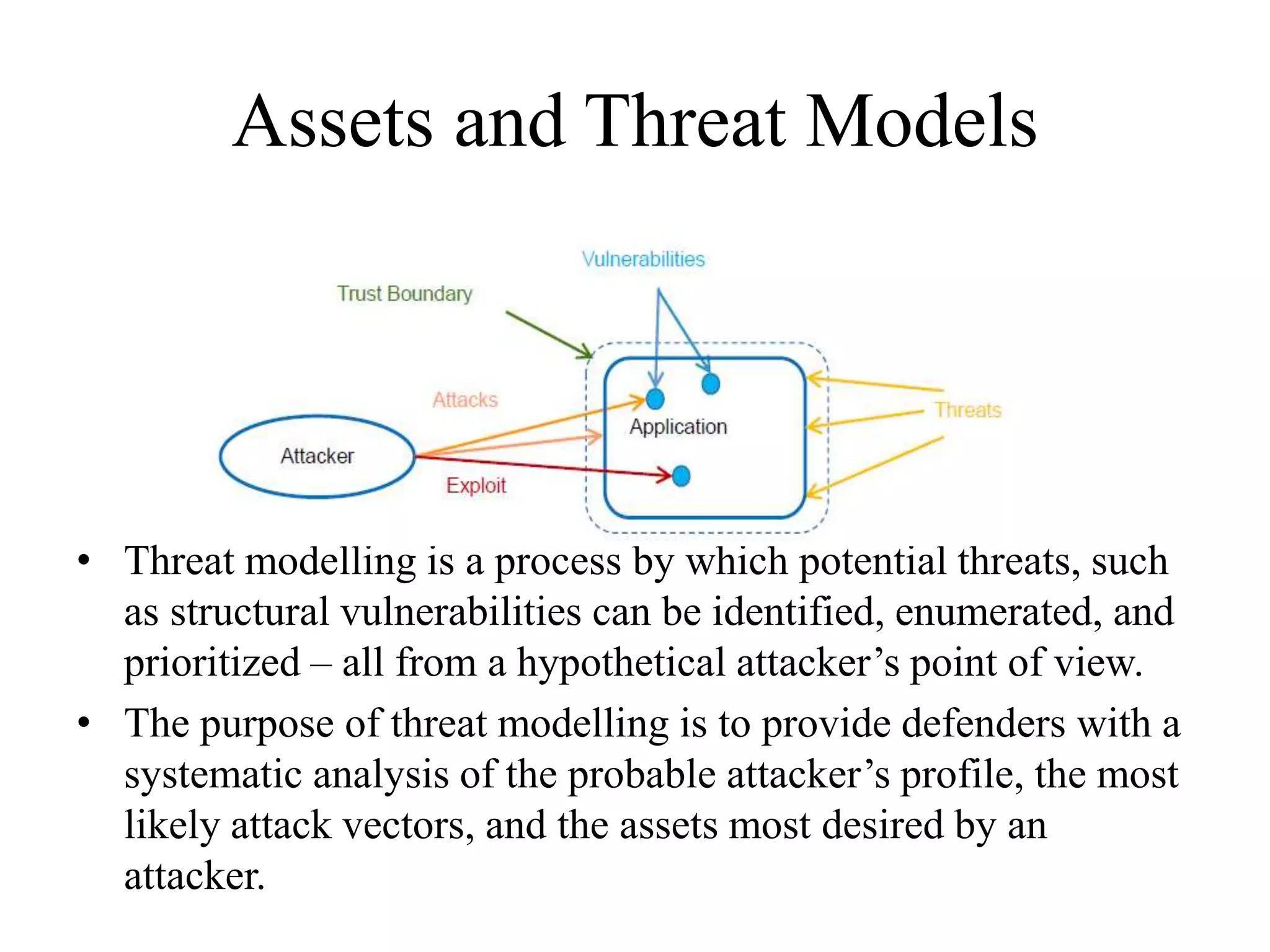
This document provides an overview of key concepts in computer and information security. It discusses cyber security, data security, network security, and authentication, authorization and accounting (AAA). It also covers the NIST FIPS 199 standard for categorizing information systems based on potential impact, and different methodologies for modeling assets and threats such as STRIDE, PASTA, Trike and VAST. The key topics are introduced at a high level with definitions and examples to provide the essential information about common computer security concepts and frameworks.