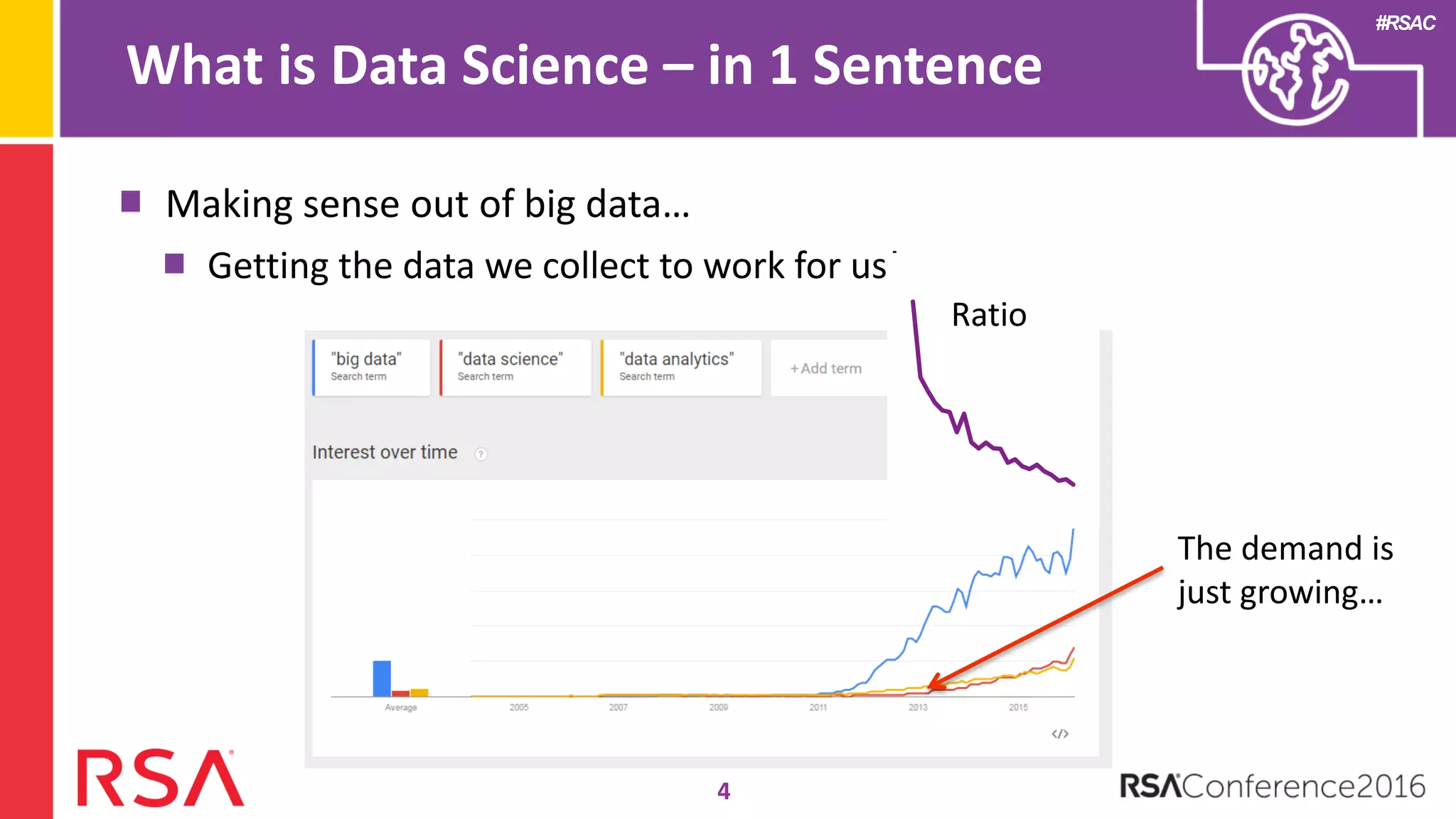
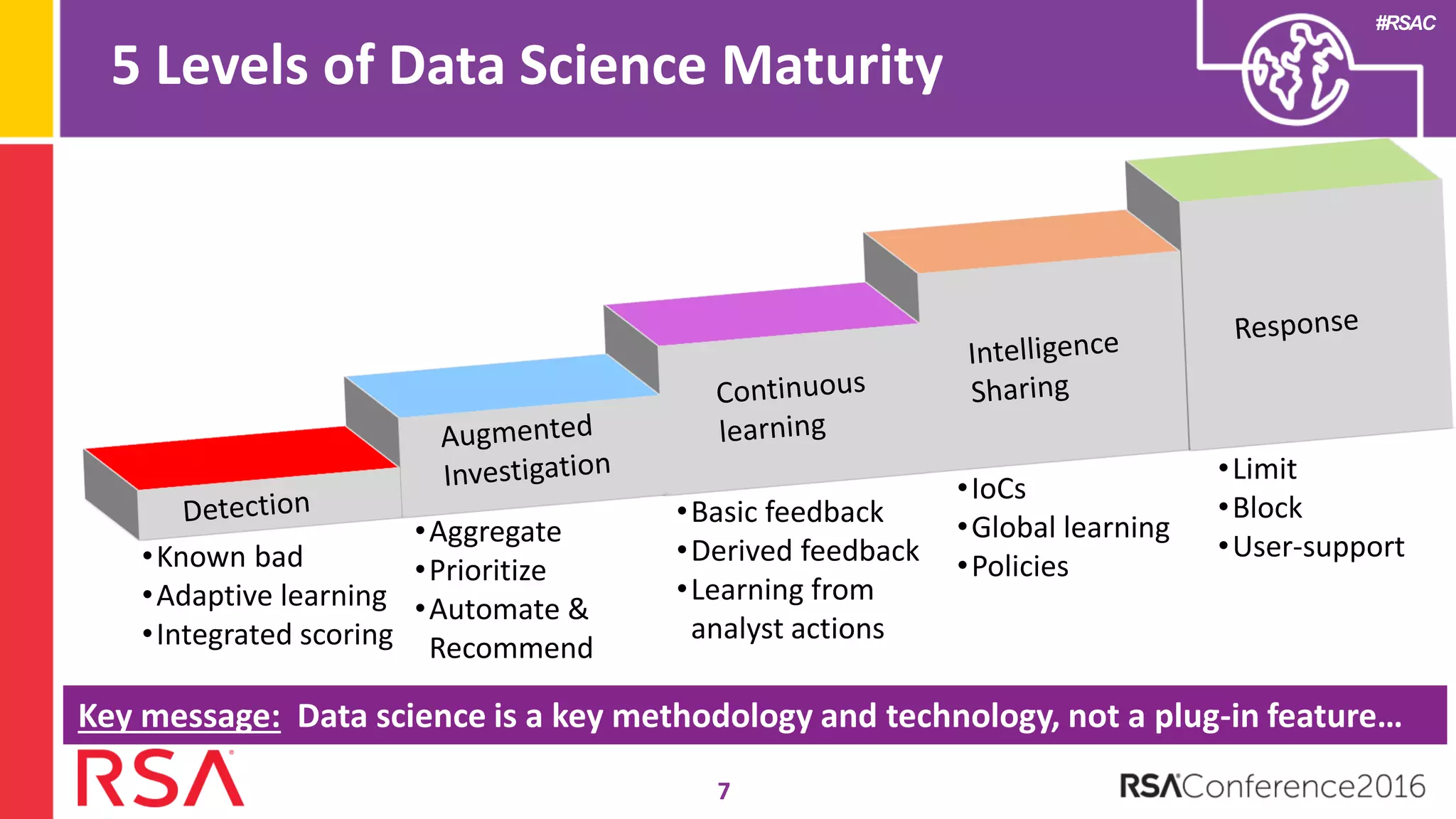
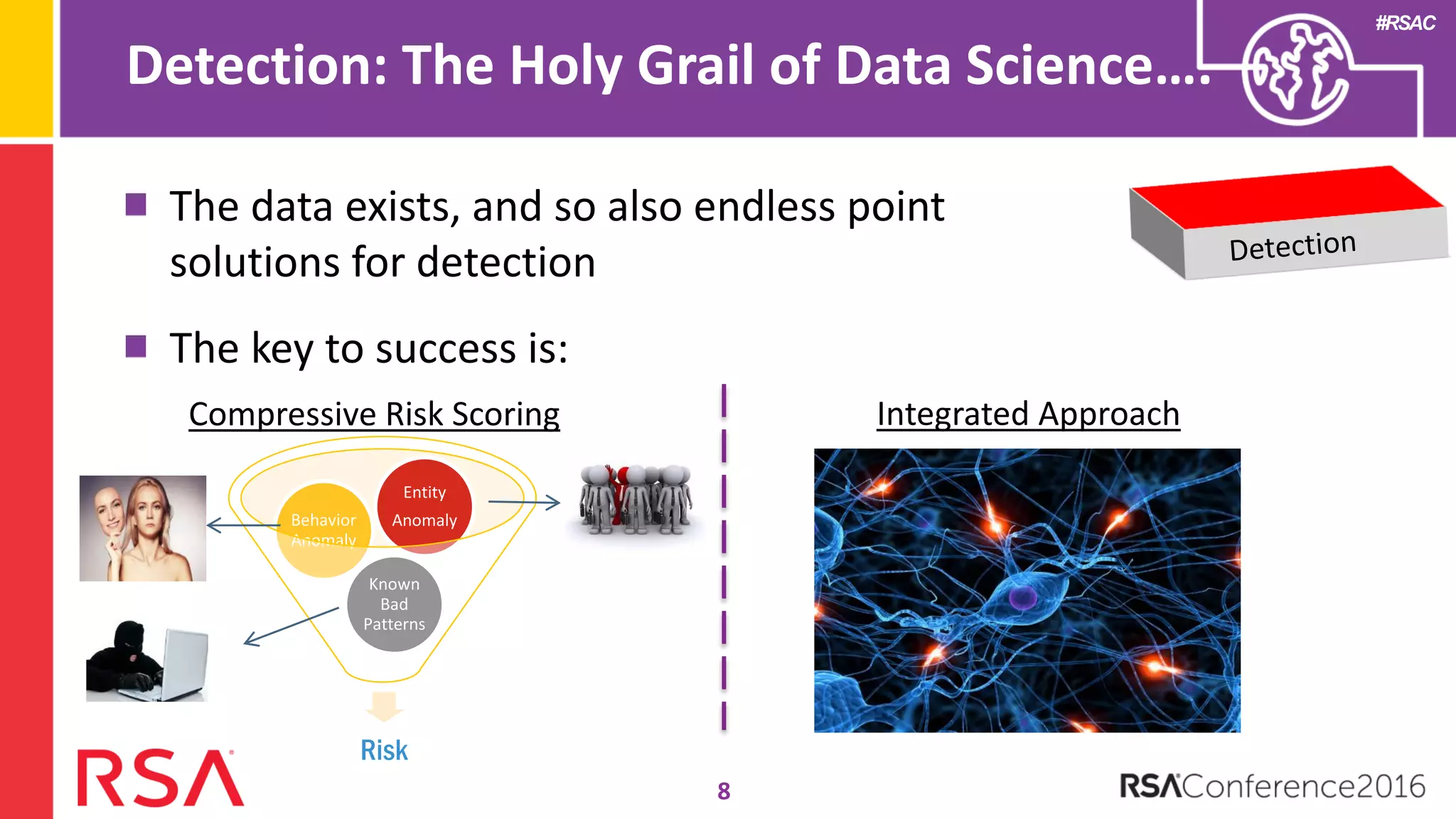
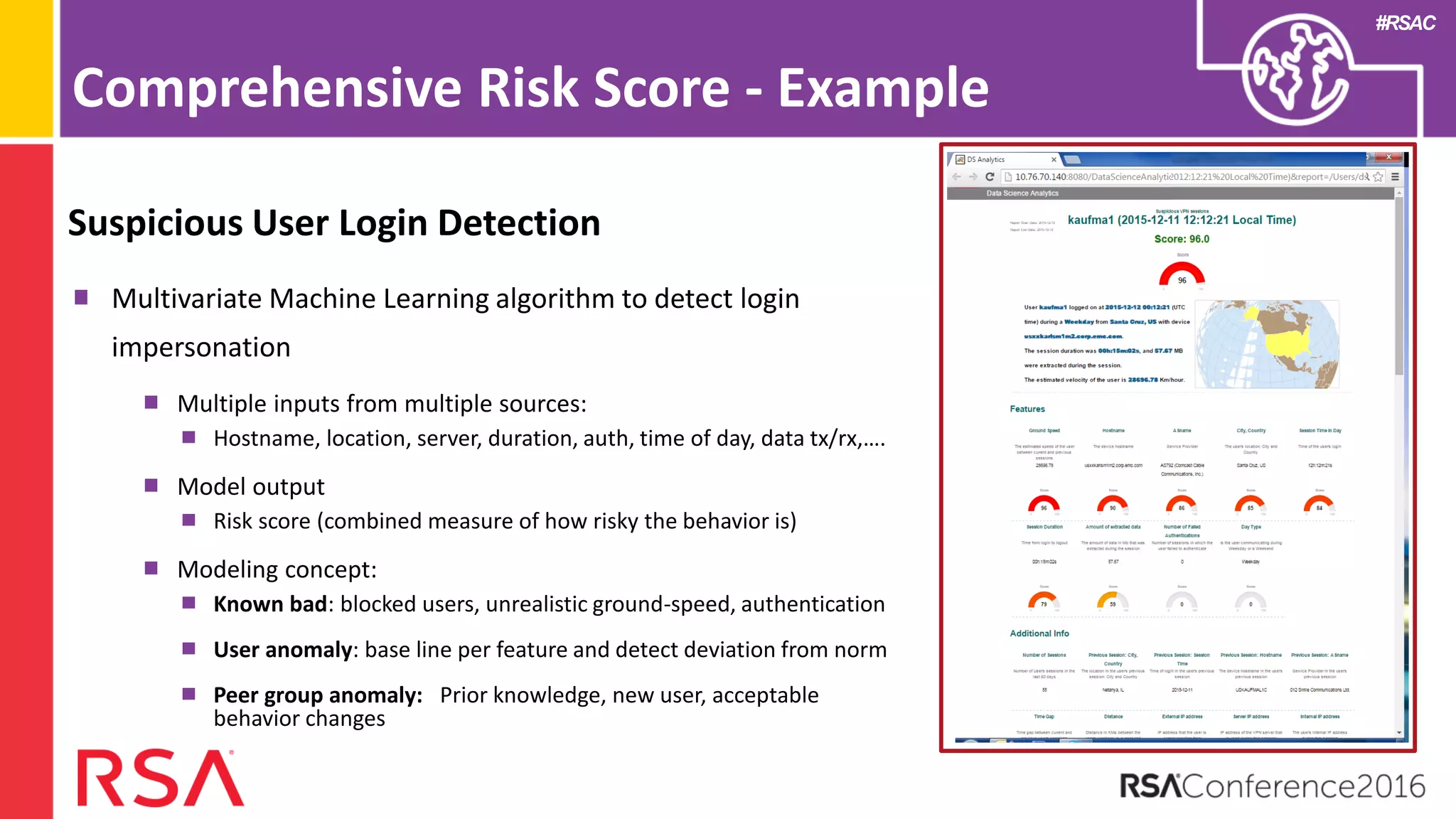
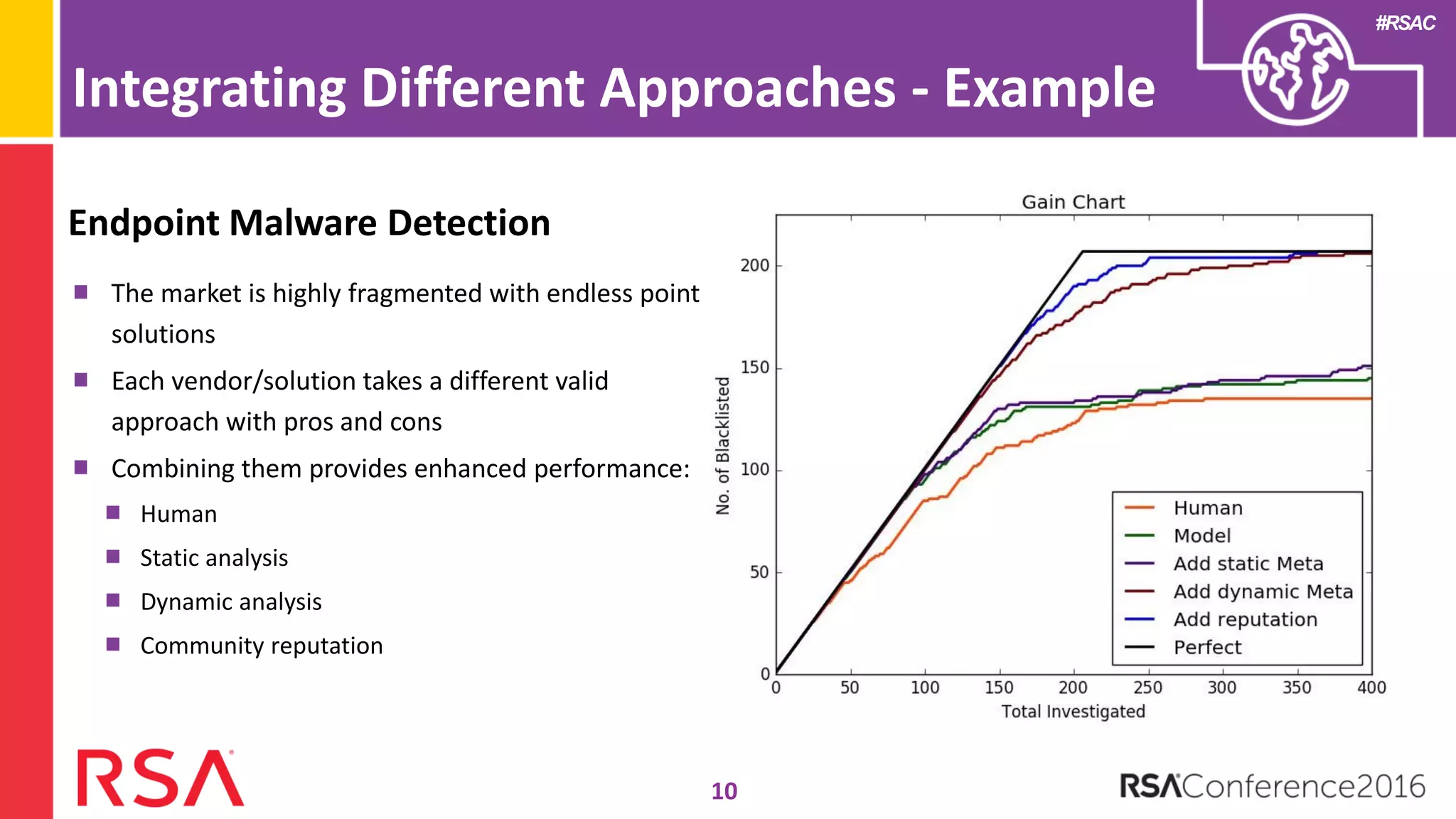
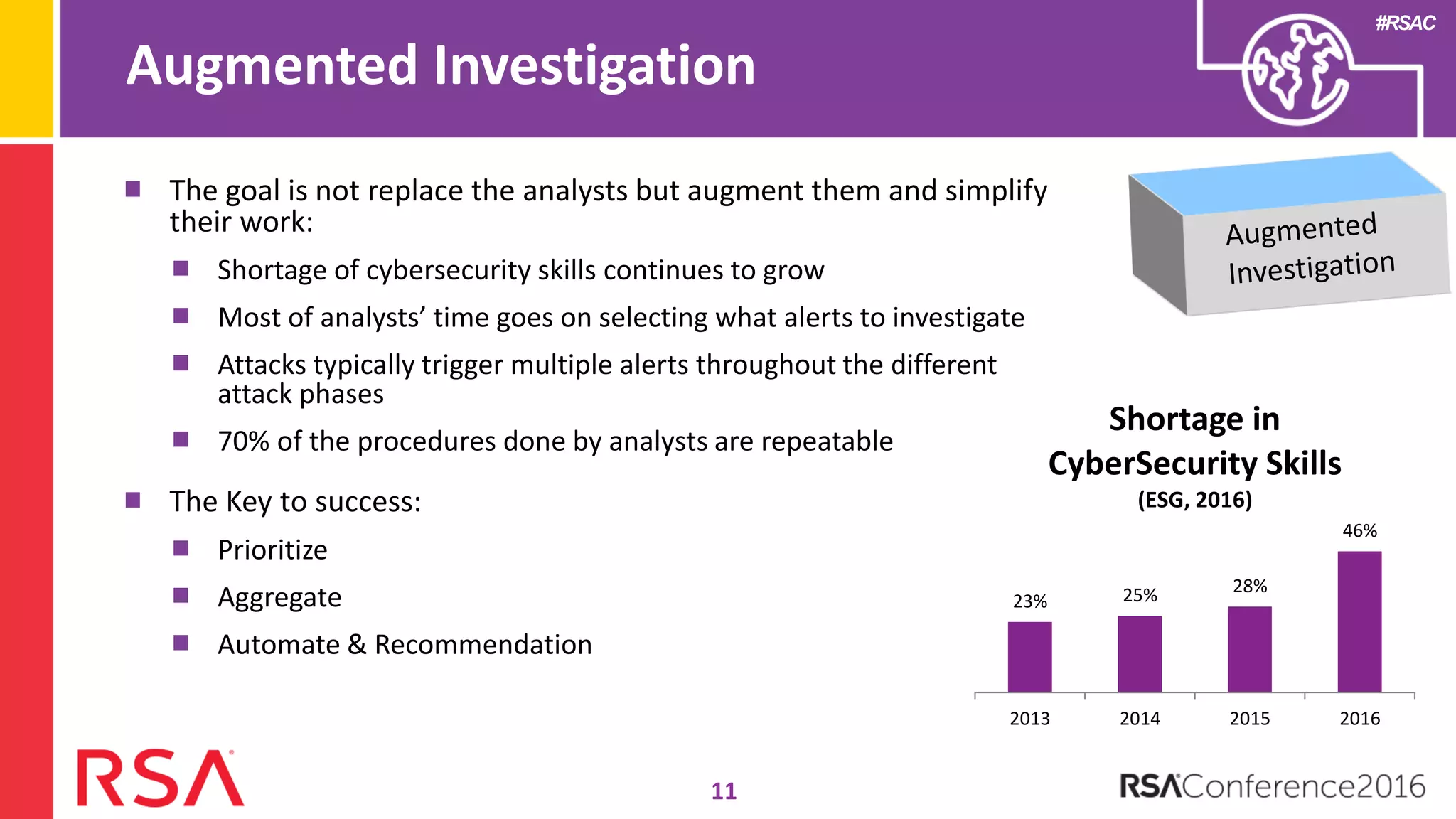
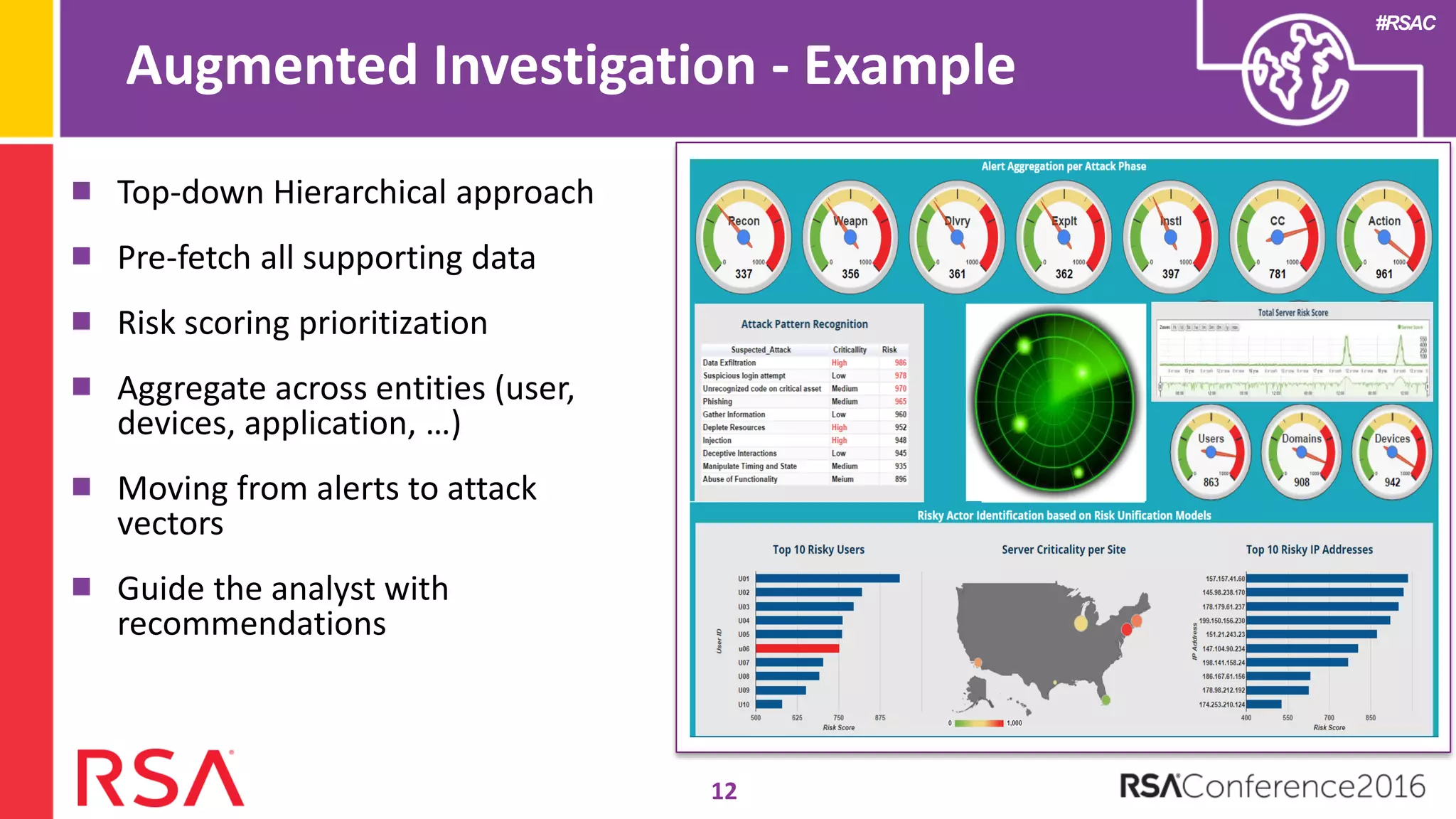
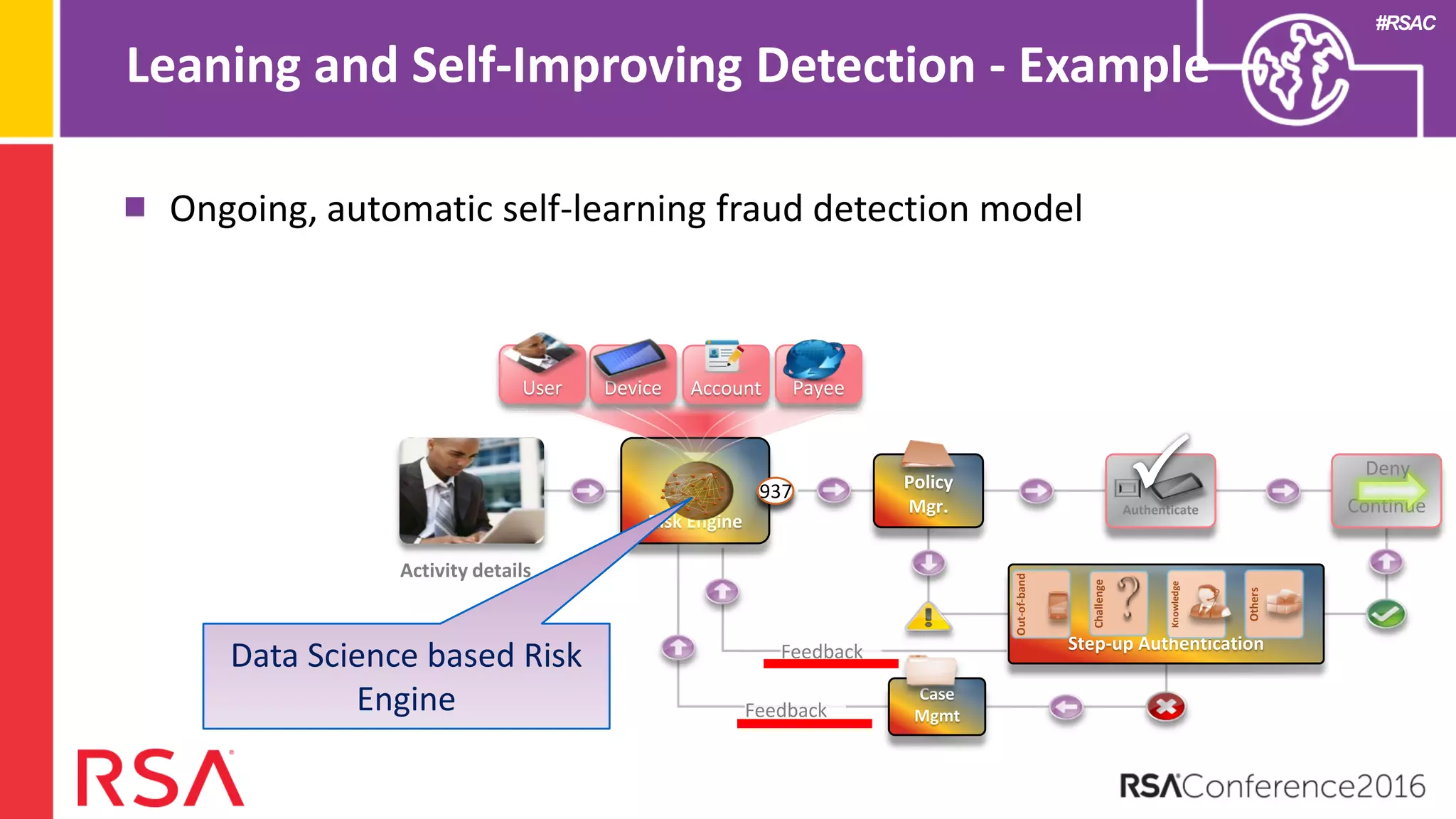
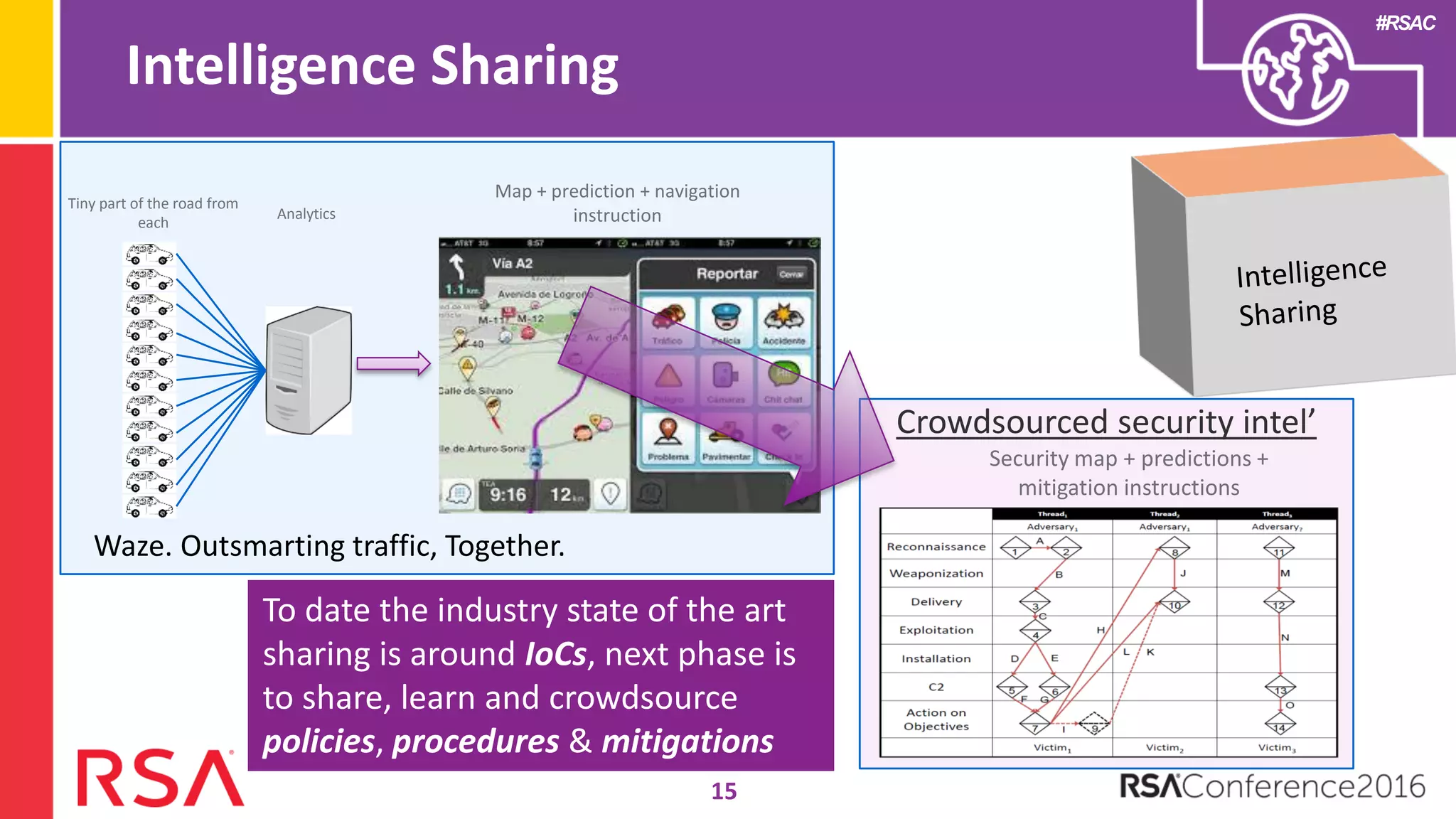
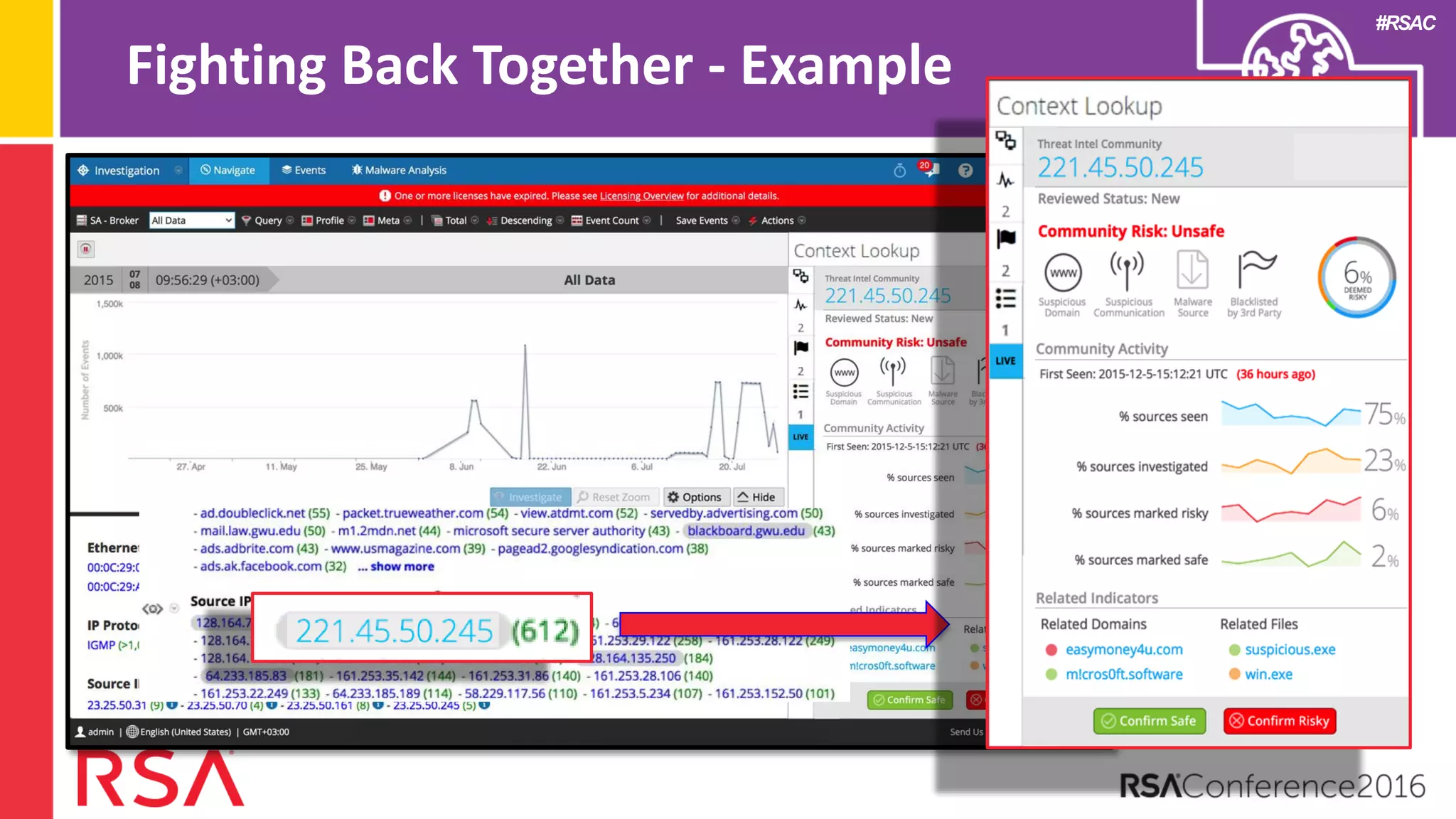
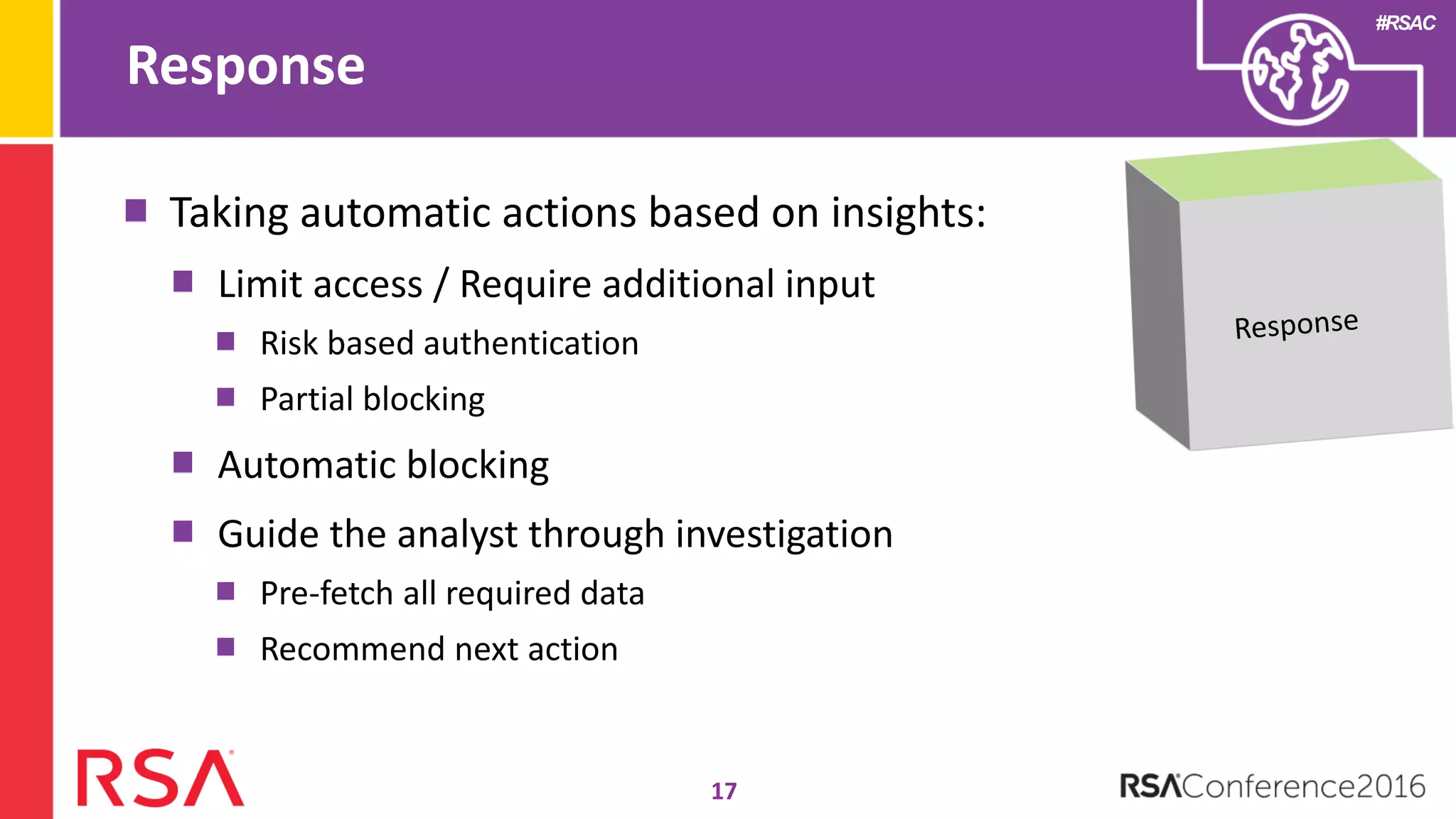
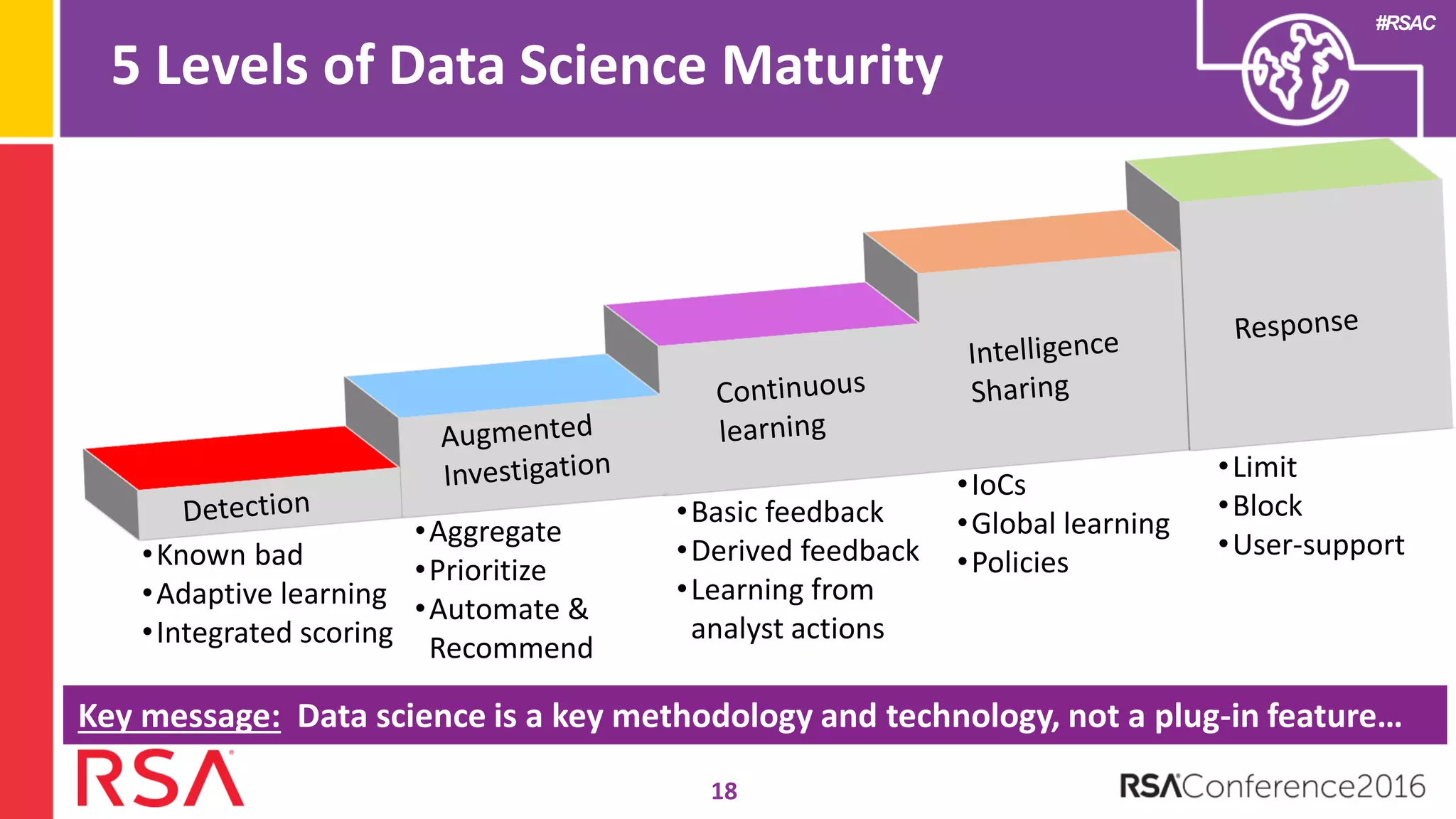
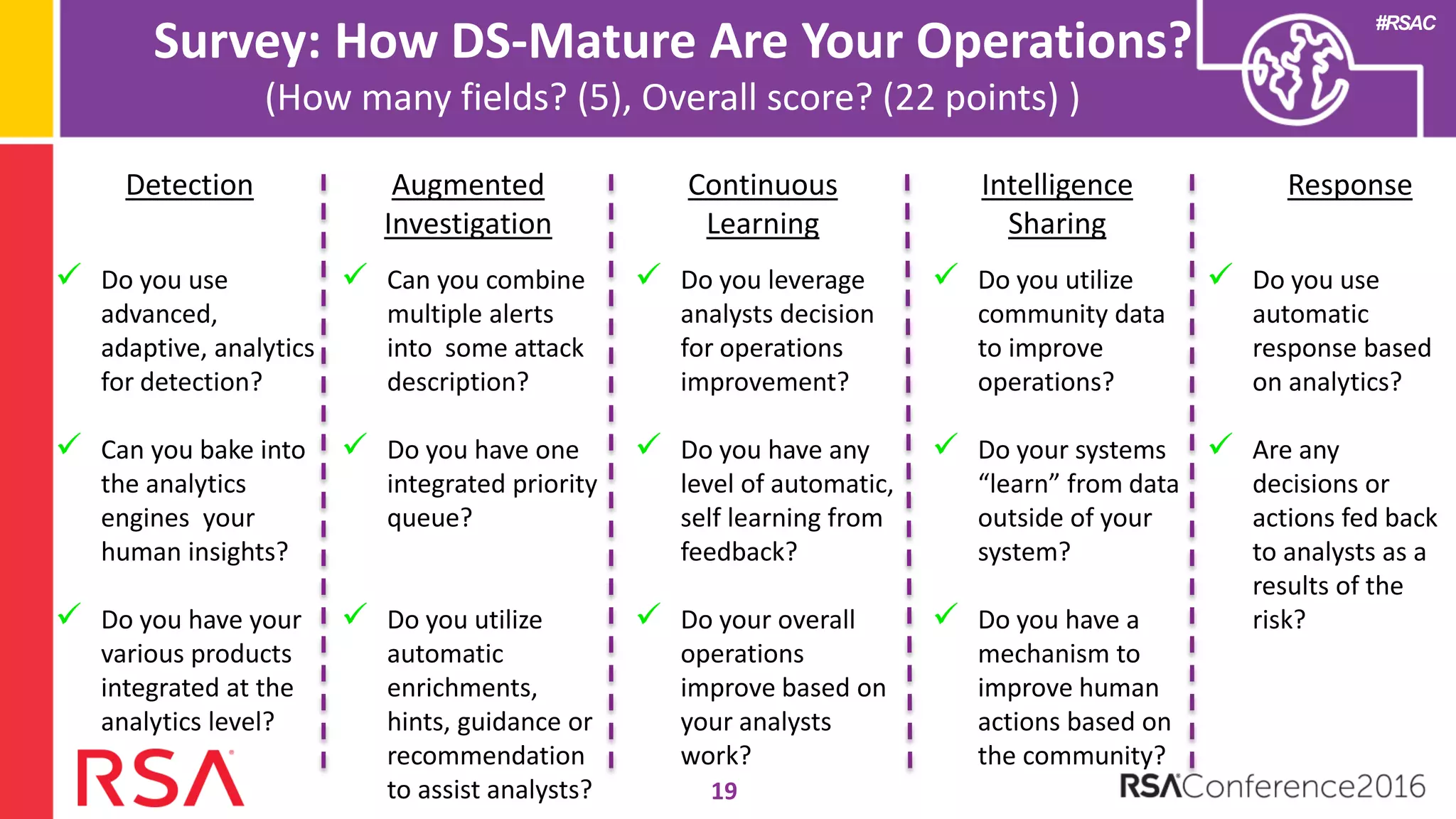
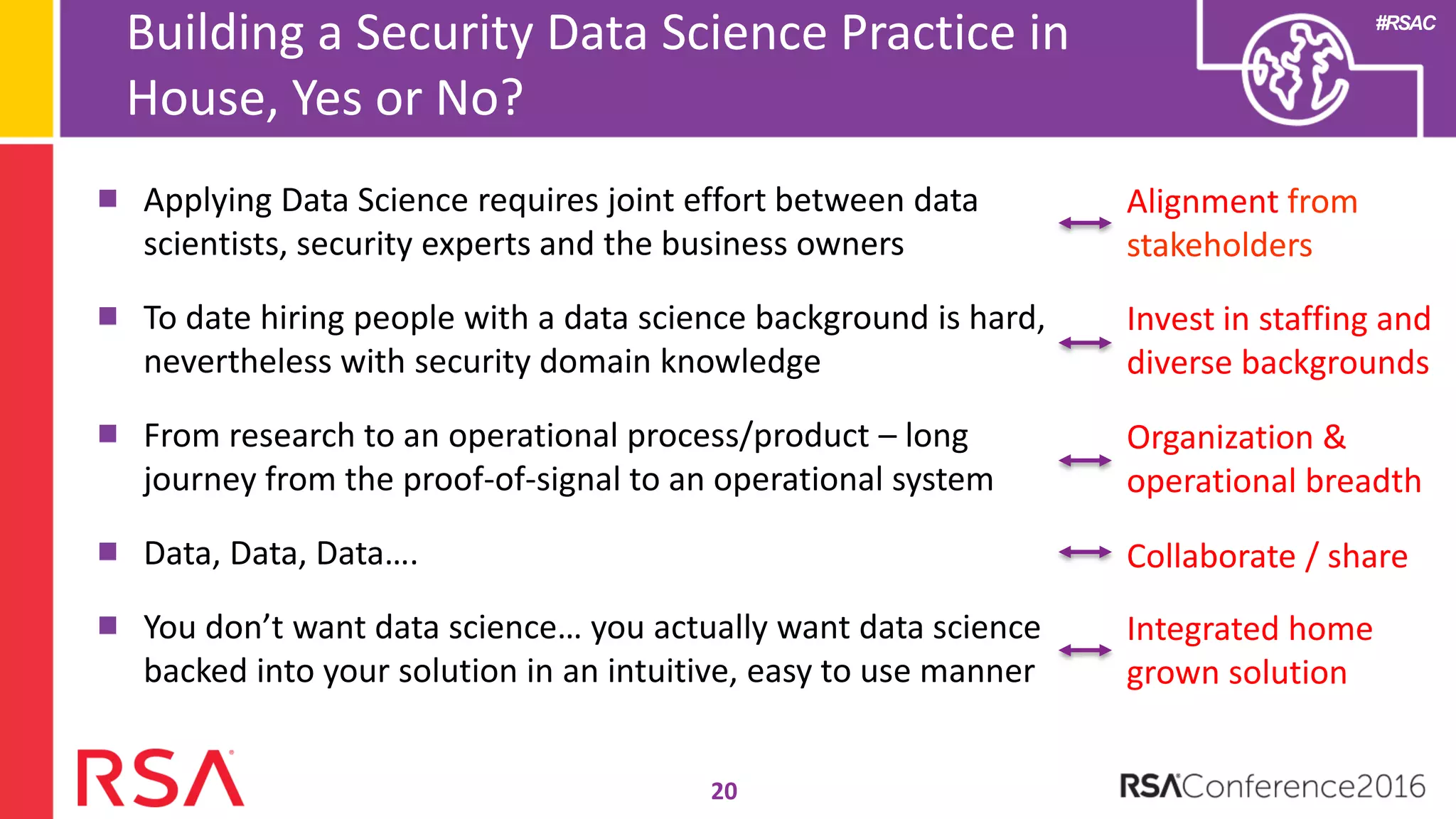
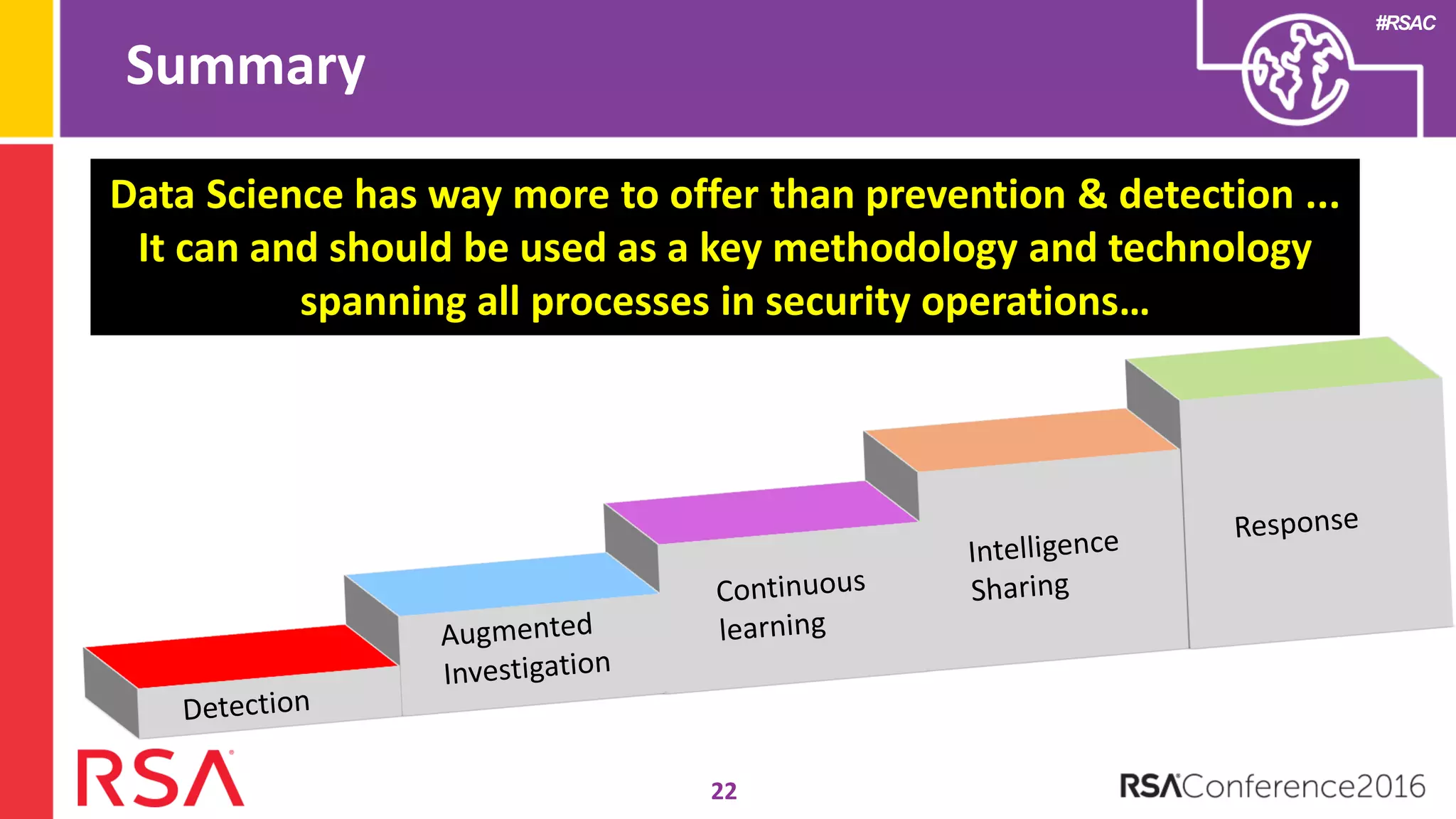
Data science can transform security operations by being applied across the entire process, beyond just prevention and detection. It can enhance detection through advanced analytics, augment investigations by aggregating alerts and prioritizing threats, improve continuously through feedback loops, enable intelligence sharing, and inform automated responses. Organizations should assess their data science maturity and focus on integrating it throughout their security operations rather than treating it as an isolated feature. Building an in-house data science practice requires alignment, strategic staffing, and a long-term commitment to maximize the benefits.