Downloaded 43 times


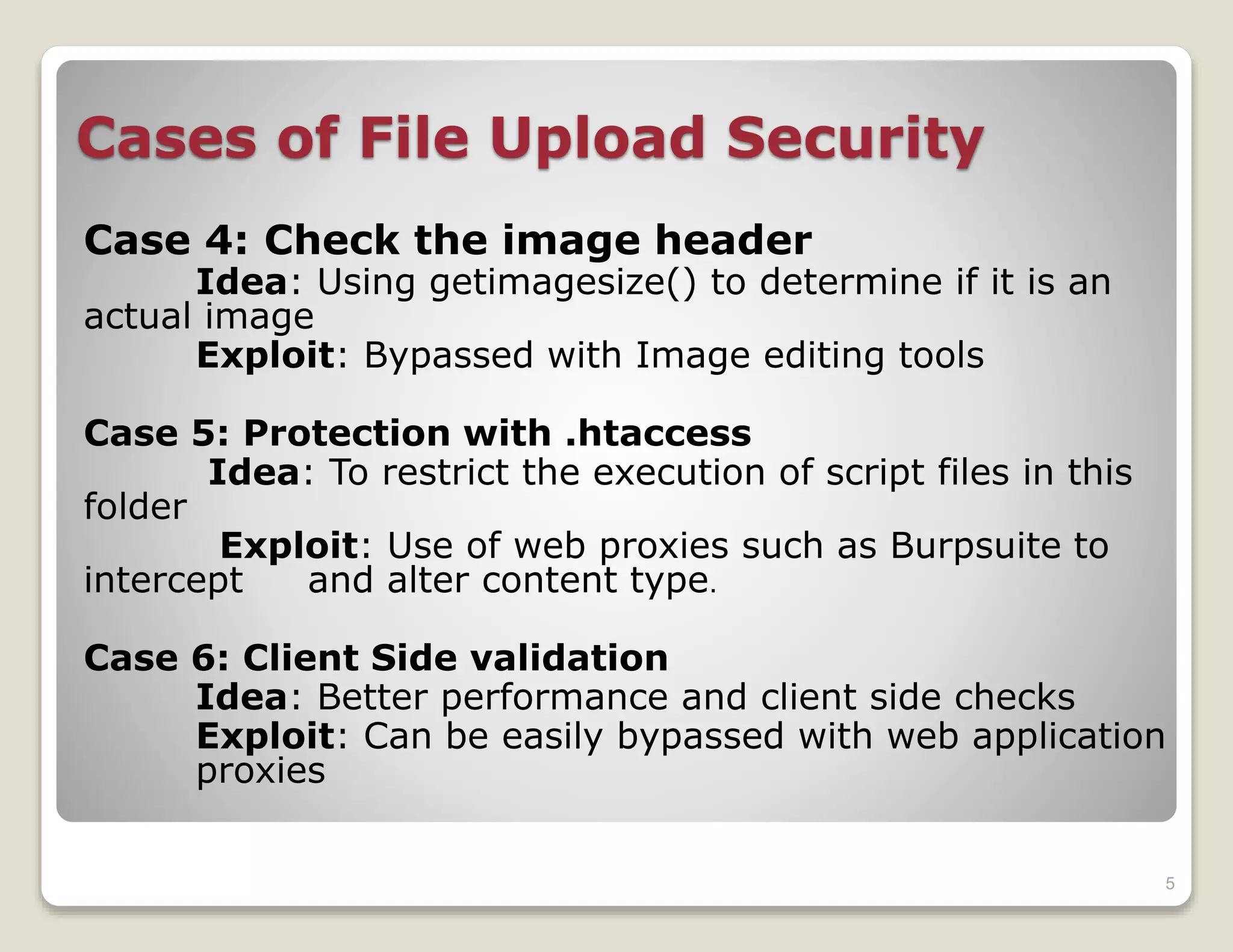
![Cases of File Upload Security
Case 1: Simple File upload form with no validation
Exploit: Simply upload shell (without any modification) in
server language format (asp, jsp, php, py)
Case 2: Mime Type Validation
Idea: This checks the content type. $_FILES[‘uploaded’][‘type’]
Exploit: Use of web proxies such as Burpsuite to intercept
and alter content type.
Case 3: Black listing extension types
Not good for hosted environment (running several scripting
languages)
Exploit: Impossible to predict all possible random
extensions (shell.php.345)
4](https://image.slidesharecdn.com/fileuploadvulnerabilitiesslideshare-140228112508-phpapp01/75/File-upload-vulnerabilities-mitigation-4-2048.jpg)





This document discusses file upload vulnerabilities, exploitation, and mitigation. It provides 6 cases of how file uploads can be exploited such as through simple uploads without validation or altering content types. Tools mentioned for exploitation include BurpSuite and proxies. The document recommends mitigation techniques like using .htaccess files outside the upload directory, storing uploads outside the server root, not relying on client-side validation, and renaming files with random names. It concludes with offering a proof of concept demonstration.
Introduction to file upload vulnerabilities and their exploitation and mitigation by Chinedu Onwukike.
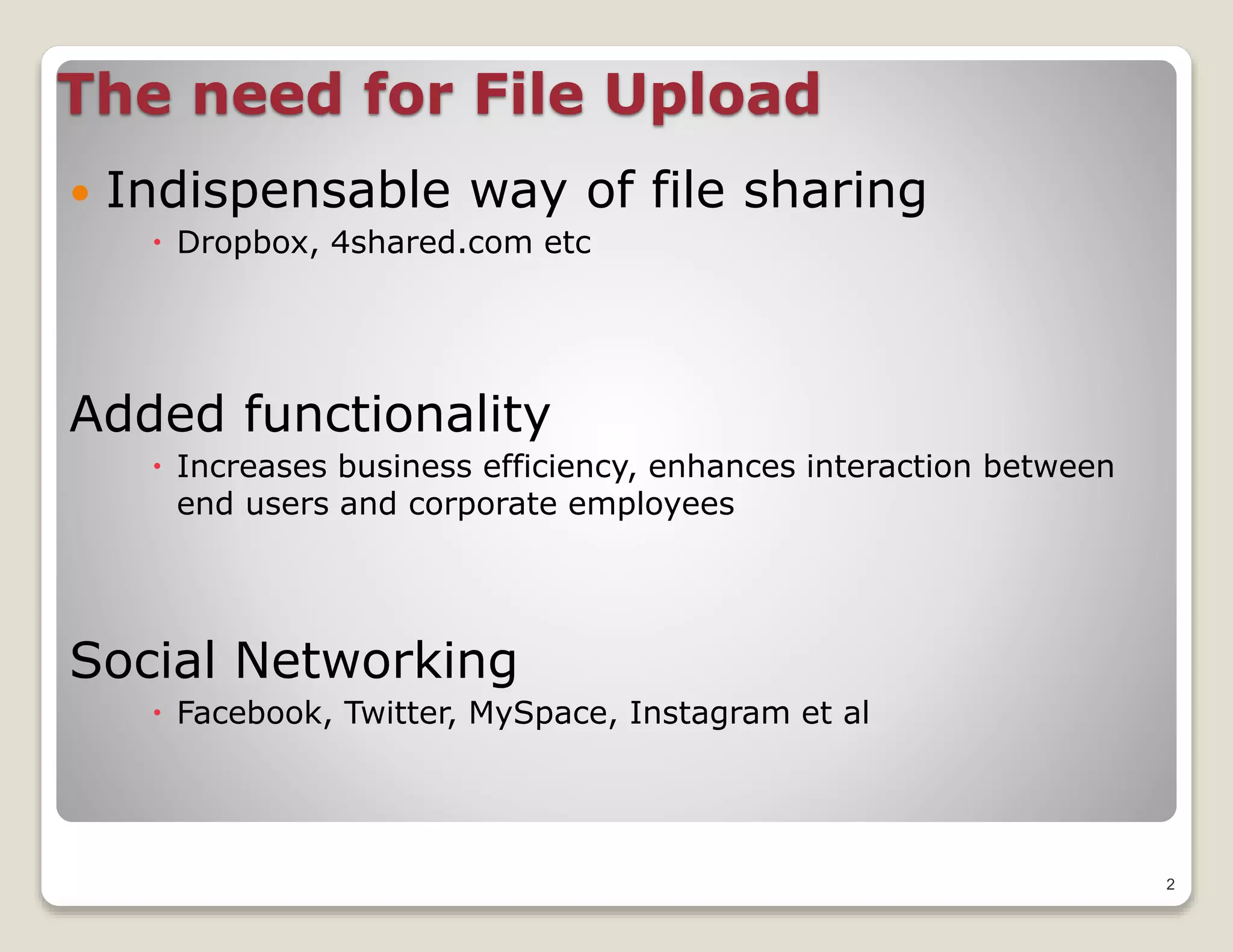
File uploads are essential for sharing on platforms like Dropbox and social media, enhancing efficiency.
File uploads provide an avenue for attacks, often due to a lack of expertise in securing upload interfaces.
Various exploits on file upload systems, including issues with validation and bypass strategies using tools.
Tools used for securing file uploads include BurpSuite, Apache PHP server, and web browsers.
Key strategies for improving file upload security, such as .htaccess usage and file directory management.
Demonstration of proof of concept (PoC) related to file upload vulnerabilities.
Open floor for questions regarding file upload vulnerabilities and discussed mitigation strategies.



![Cases of File Upload Security
Case 1: Simple File upload form with no validation
Exploit: Simply upload shell (without any modification) in
server language format (asp, jsp, php, py)
Case 2: Mime Type Validation
Idea: This checks the content type. $_FILES[‘uploaded’][‘type’]
Exploit: Use of web proxies such as Burpsuite to intercept
and alter content type.
Case 3: Black listing extension types
Not good for hosted environment (running several scripting
languages)
Exploit: Impossible to predict all possible random
extensions (shell.php.345)
4](https://image.slidesharecdn.com/fileuploadvulnerabilitiesslideshare-140228112508-phpapp01/75/File-upload-vulnerabilities-mitigation-4-2048.jpg)




